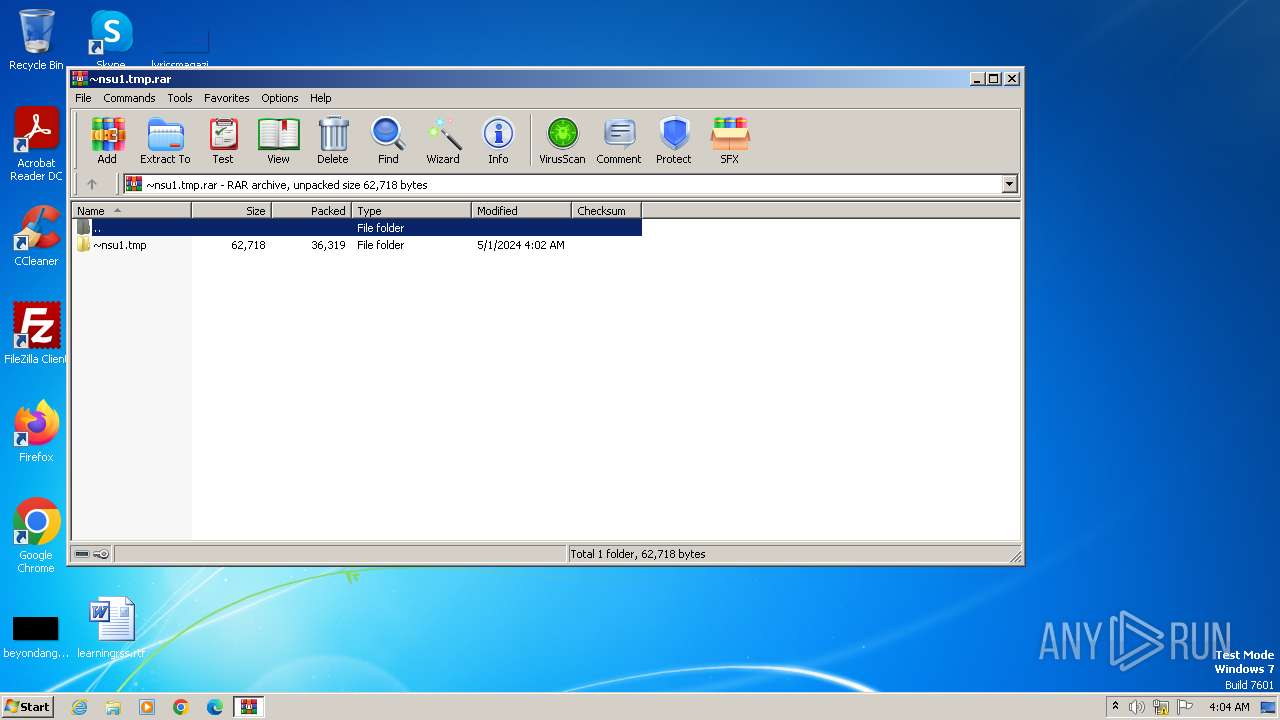
| File name: | ~nsu1.tmp.rar |
| Full analysis: | https://app.any.run/tasks/79746eb0-168e-44ed-b5f6-60a1370dfe04 |
| Verdict: | Malicious activity |
| Analysis date: | May 01, 2024, 03:04:08 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | D45878889E4B2E6ED4F59DC6DA30434C |
| SHA1: | 9F365D27242071D8EF37A19115EB7985B724263C |
| SHA256: | B3AB64CE4C73AEFED162A0F9A52C5EE06BD2A279D5E7B47F6EE76DB3B6977007 |
| SSDEEP: | 768:/1pzqtF6ddzpUGBSEaqGA73xSS7CgWwDtomYbaDqSzebBMs7mLD:dp2763pKEbGW3Jm+x8hSztMKD |
MALICIOUS
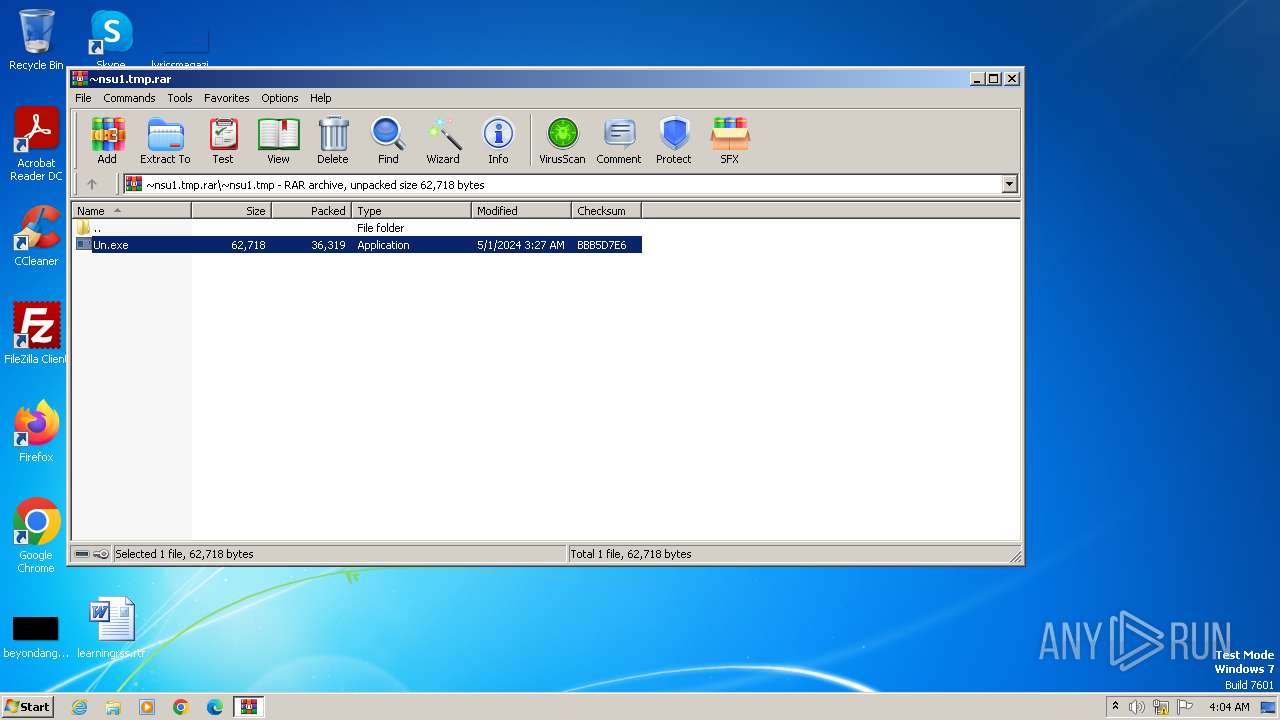
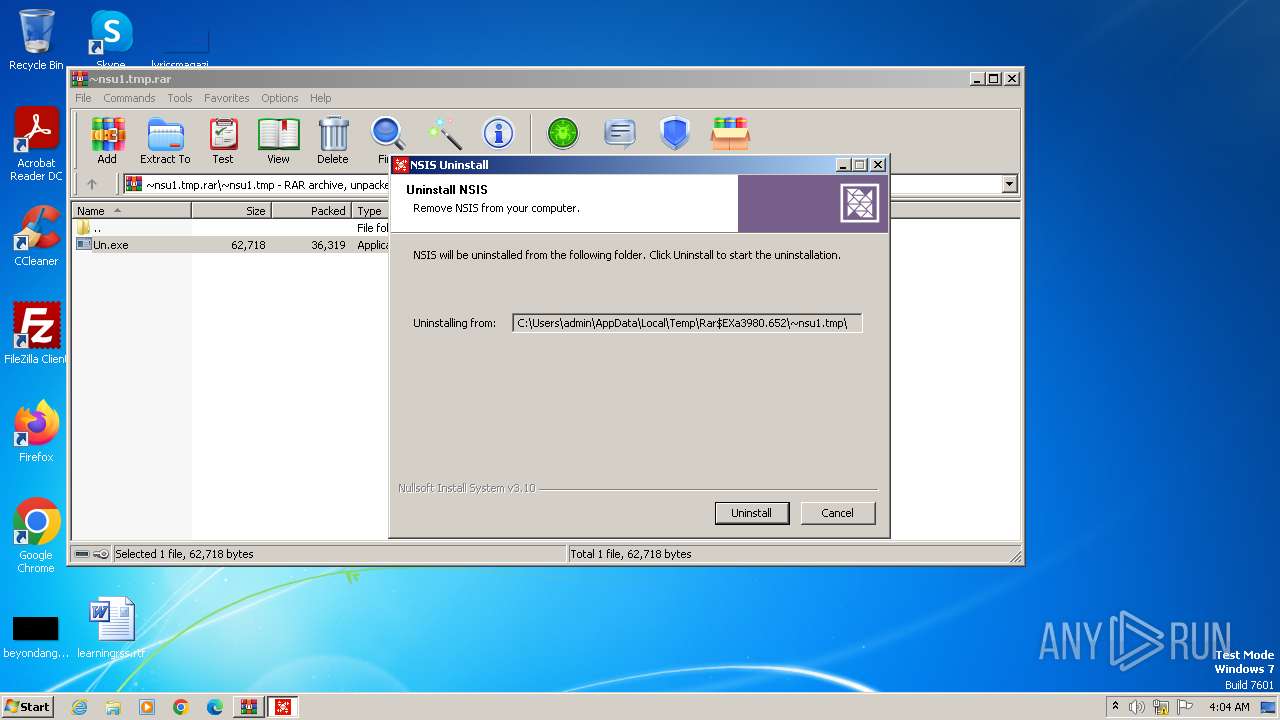
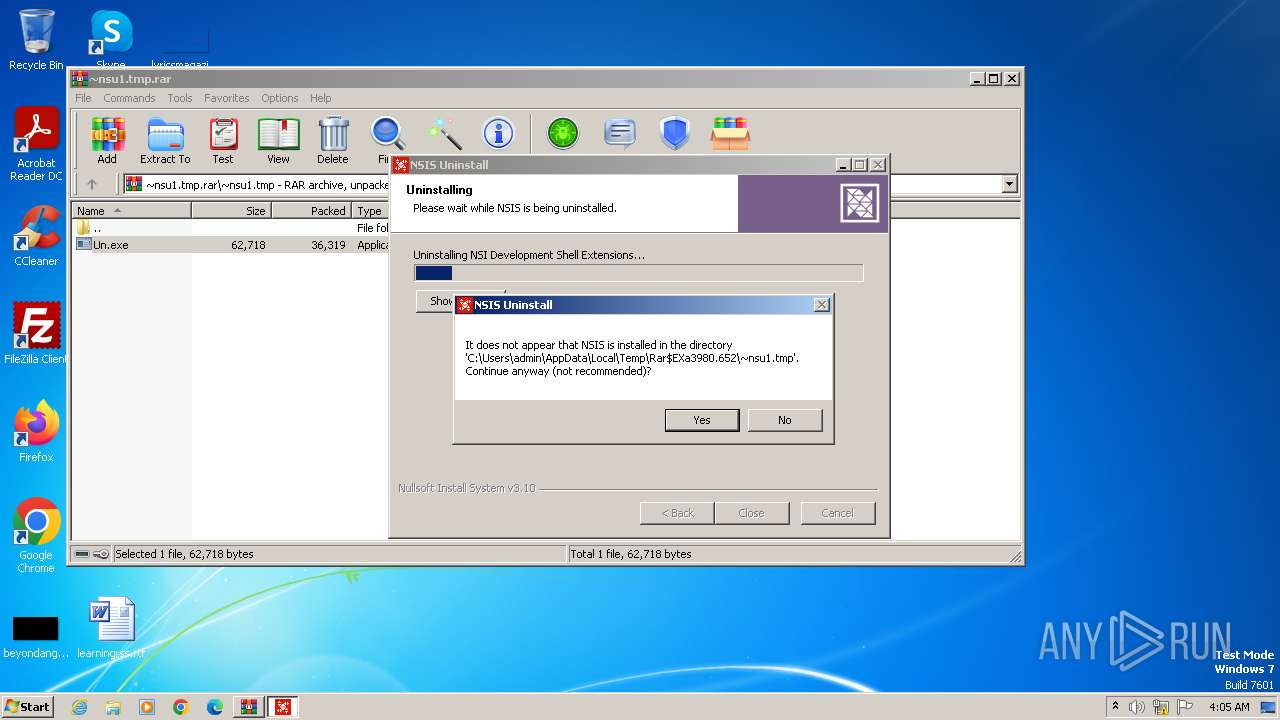
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3980)
- Un.exe (PID: 748)
- Un.exe (PID: 112)
- Un.exe (PID: 2064)
- Un.exe (PID: 2092)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3980)
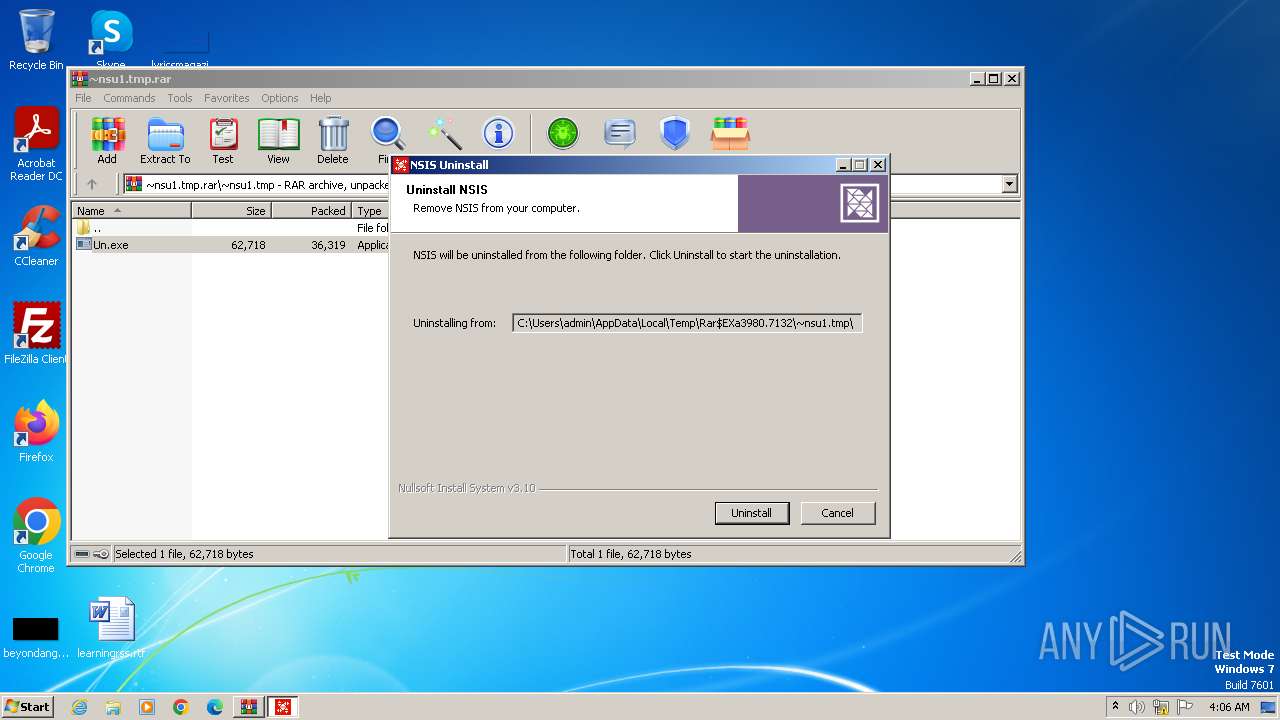
Starts itself from another location
- Un.exe (PID: 748)
- Un.exe (PID: 2064)
Executable content was dropped or overwritten
- Un.exe (PID: 748)
- Un.exe (PID: 2092)
- Un.exe (PID: 112)
- Un.exe (PID: 2064)
Malware-specific behavior (creating "System.dll" in Temp)
- Un.exe (PID: 112)
- Un.exe (PID: 2092)
The process creates files with name similar to system file names
- Un.exe (PID: 112)
- Un.exe (PID: 2092)
Reads the Internet Settings
- rundll32.exe (PID: 2372)
Process uses IPCONFIG to get network configuration information
- cmd.exe (PID: 1644)
INFO
Checks supported languages
- Un.exe (PID: 748)
- Un.exe (PID: 112)
- Un.exe (PID: 2092)
- Un.exe (PID: 2064)
Reads the computer name
- Un.exe (PID: 748)
- Un.exe (PID: 112)
- Un.exe (PID: 2092)
- Un.exe (PID: 2064)
Create files in a temporary directory
- Un.exe (PID: 748)
- Un.exe (PID: 112)
- Un.exe (PID: 2092)
- Un.exe (PID: 2064)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3980)
Reads security settings of Internet Explorer
- rundll32.exe (PID: 2372)
Manual execution by a user
- explorer.exe (PID: 2240)
- rundll32.exe (PID: 2372)
- cmd.exe (PID: 1644)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
53
Monitored processes
12
Malicious processes
2
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 112 | "C:\Users\admin\AppData\Local\Temp\~nsu1.tmp\Un.exe" _?=C:\Users\admin\AppData\Local\Temp\Rar$EXa3980.652\~nsu1.tmp\ | C:\Users\admin\AppData\Local\Temp\~nsu1.tmp\Un.exe | Un.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: NSIS Setup Exit code: 0 Version: 3.10 Modules
| |||||||||||||||
| 748 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3980.652\~nsu1.tmp\Un.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3980.652\~nsu1.tmp\Un.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: NSIS Setup Exit code: 0 Version: 3.10 Modules
| |||||||||||||||
| 1488 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3980.7132\~nsu1.tmp\Un.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3980.7132\~nsu1.tmp\Un.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: NSIS Setup Exit code: 3221226540 Version: 3.10 Modules
| |||||||||||||||
| 1644 | "C:\Windows\system32\cmd.exe" | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2064 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3980.7132\~nsu1.tmp\Un.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3980.7132\~nsu1.tmp\Un.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: NSIS Setup Exit code: 0 Version: 3.10 Modules
| |||||||||||||||
| 2092 | "C:\Users\admin\AppData\Local\Temp\~nsu1.tmp\Un.exe" _?=C:\Users\admin\AppData\Local\Temp\Rar$EXa3980.7132\~nsu1.tmp\ | C:\Users\admin\AppData\Local\Temp\~nsu1.tmp\Un.exe | Un.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: NSIS Setup Version: 3.10 Modules
| |||||||||||||||
| 2240 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2372 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Windows\System32\drivers\etc\hosts | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2432 | "C:\Windows\system32\NOTEPAD.EXE" C:\Windows\System32\drivers\etc\hosts | C:\Windows\System32\notepad.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2748 | ipconfig | C:\Windows\System32\ipconfig.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: IP Configuration Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
15 334
Read events
15 234
Write events
100
Delete events
0
Modification events
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\~nsu1.tmp.rar | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
6
Suspicious files
3
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 112 | Un.exe | C:\Users\admin\AppData\Local\Temp\nshE2F0.tmp | binary | |
MD5:6B076201087B5B6009D6A4CD545D71E7 | SHA256:ECF33C2A605DD57936E97630EF0B8973E4D08325DBF290E60102A7DC9B7FAE76 | |||
| 112 | Un.exe | C:\Users\admin\AppData\Local\Temp\nsxE301.tmp\modern-header.bmp | image | |
MD5:BE6DF031317AA93B0F4EEF0CC183B0B1 | SHA256:0F3B85A4A7BD2C6BAA7B2B24590EA69E656384130FA8212E944016C46AC7E7D1 | |||
| 748 | Un.exe | C:\Users\admin\AppData\Local\Temp\~nsu1.tmp\Un.exe | executable | |
MD5:89A1E4BBAD3DA80E45A9E1B44E8DBC5C | SHA256:9347E8BC7F0EF54A54C2749BE0CF477B49F52AC5269D7B4EDF02EC827ADCA15E | |||
| 748 | Un.exe | C:\Users\admin\AppData\Local\Temp\nssE293.tmp | binary | |
MD5:6B076201087B5B6009D6A4CD545D71E7 | SHA256:ECF33C2A605DD57936E97630EF0B8973E4D08325DBF290E60102A7DC9B7FAE76 | |||
| 2064 | Un.exe | C:\Users\admin\AppData\Local\Temp\~nsu1.tmp\Un.exe | executable | |
MD5:89A1E4BBAD3DA80E45A9E1B44E8DBC5C | SHA256:9347E8BC7F0EF54A54C2749BE0CF477B49F52AC5269D7B4EDF02EC827ADCA15E | |||
| 3980 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3980.7132\~nsu1.tmp\Un.exe | executable | |
MD5:89A1E4BBAD3DA80E45A9E1B44E8DBC5C | SHA256:9347E8BC7F0EF54A54C2749BE0CF477B49F52AC5269D7B4EDF02EC827ADCA15E | |||
| 2092 | Un.exe | C:\Users\admin\AppData\Local\Temp\nslDDEB.tmp\modern-header.bmp | image | |
MD5:BE6DF031317AA93B0F4EEF0CC183B0B1 | SHA256:0F3B85A4A7BD2C6BAA7B2B24590EA69E656384130FA8212E944016C46AC7E7D1 | |||
| 2064 | Un.exe | C:\Users\admin\AppData\Local\Temp\nsgDD7D.tmp | binary | |
MD5:6B076201087B5B6009D6A4CD545D71E7 | SHA256:ECF33C2A605DD57936E97630EF0B8973E4D08325DBF290E60102A7DC9B7FAE76 | |||
| 2092 | Un.exe | C:\Users\admin\AppData\Local\Temp\nslDDEB.tmp\System.dll | executable | |
MD5:192639861E3DC2DC5C08BB8F8C7260D5 | SHA256:23D618A0293C78CE00F7C6E6DD8B8923621DA7DD1F63A070163EF4C0EC3033D6 | |||
| 112 | Un.exe | C:\Users\admin\AppData\Local\Temp\nsxE301.tmp\System.dll | executable | |
MD5:192639861E3DC2DC5C08BB8F8C7260D5 | SHA256:23D618A0293C78CE00F7C6E6DD8B8923621DA7DD1F63A070163EF4C0EC3033D6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
3
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |