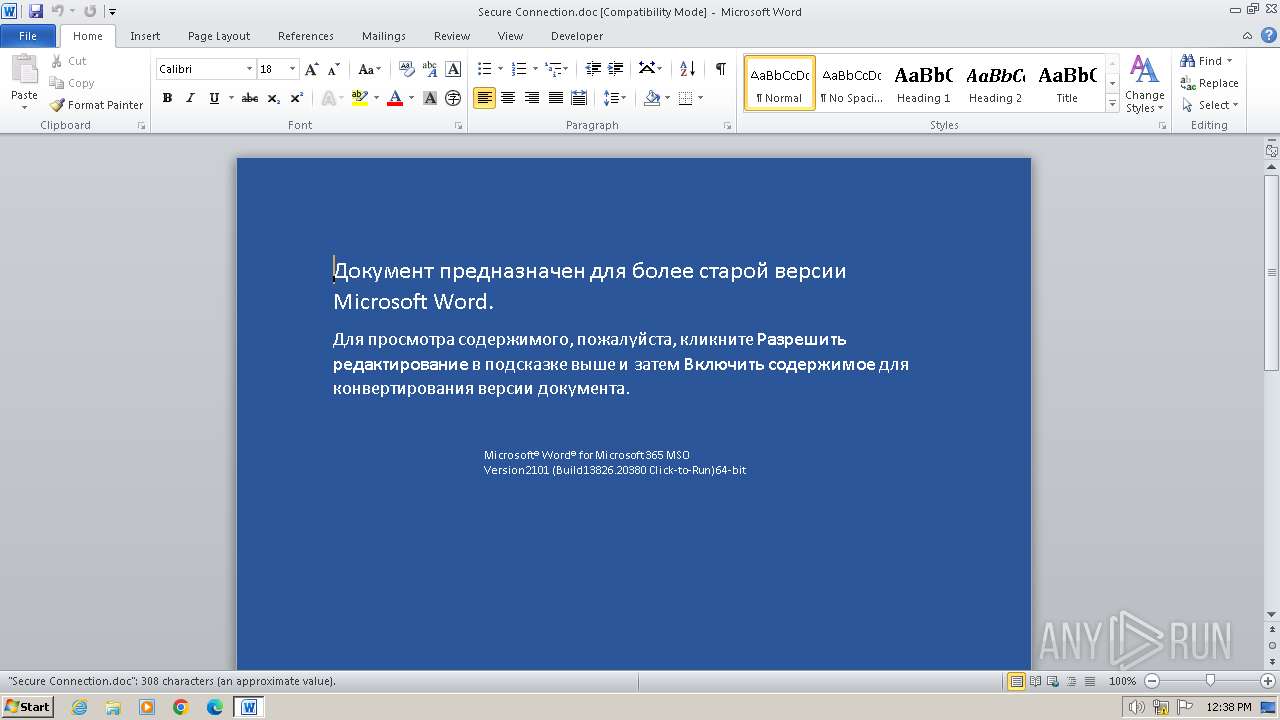
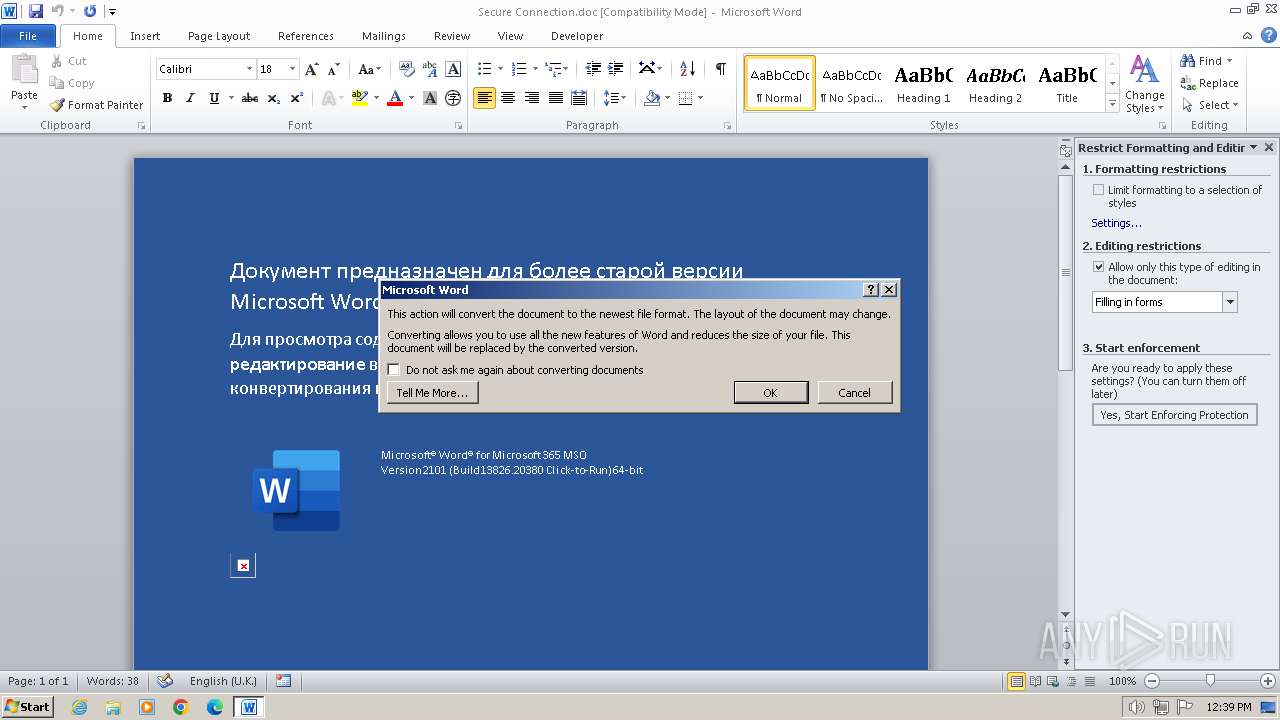
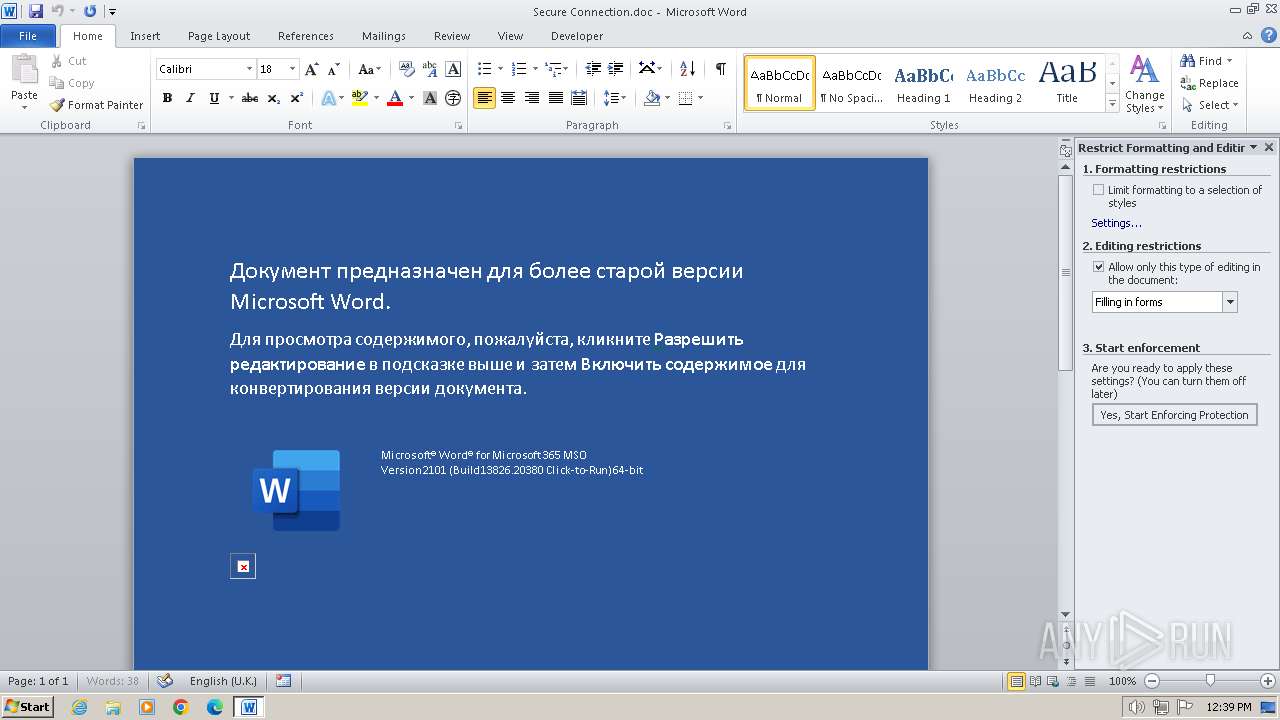
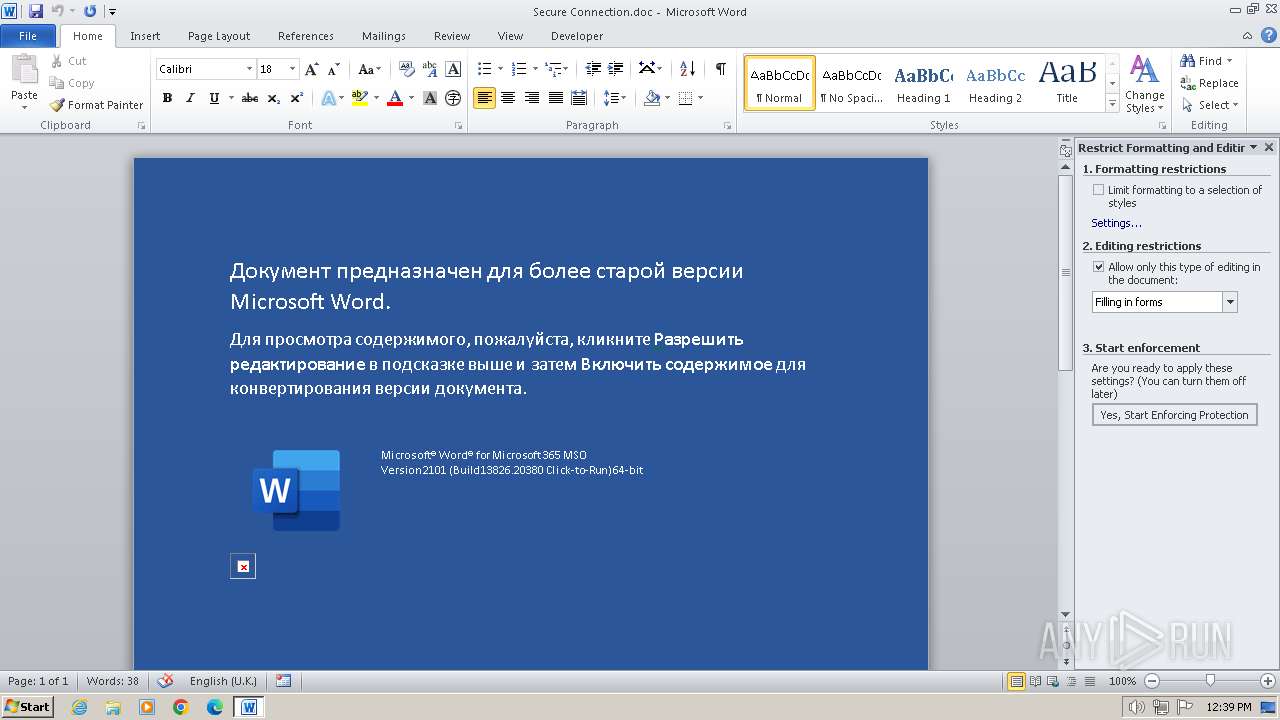
| File name: | Secure Connection.doc |
| Full analysis: | https://app.any.run/tasks/e2235afb-d89e-4793-b71e-ce7e8321e2bf |
| Verdict: | Malicious activity |
| Analysis date: | September 02, 2024, 11:38:35 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, Code page: 1251, Template: Normal.dotm, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Thu Aug 22 14:51:00 2024, Last Saved Time/Date: Fri Aug 23 07:28:00 2024, Number of Pages: 1, Number of Words: 55, Number of Characters: 319, Security: 0 |
| MD5: | 971534C8A32EC19D471408C748920F98 |
| SHA1: | 992419269FCF459A6246BBCF665A24F8B4B99875 |
| SHA256: | B3837698D31A81714C09845274F80542687F98A32DE8A44998FE184ACA8A59B9 |
| SSDEEP: | 3072:LFfG9KXujF7weNAkZ60/WcV3VV4a9T0Ysw:LxG9qE7/Z6jg3Vqy |
MALICIOUS
Sends HTTP request (SCRIPT)
- WINWORD.EXE (PID: 2788)
Opens an HTTP connection (SCRIPT)
- WINWORD.EXE (PID: 2788)
Creates internet connection object (SCRIPT)
- WINWORD.EXE (PID: 2788)
SUSPICIOUS
No suspicious indicators.INFO
Checks supported languages
- wmpnscfg.exe (PID: 3628)
Manual execution by a user
- wmpnscfg.exe (PID: 3628)
The process uses the downloaded file
- WINWORD.EXE (PID: 2788)
Reads the computer name
- wmpnscfg.exe (PID: 3628)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Identification: | Word 8.0 |
|---|---|
| LanguageCode: | Russian |
| DocFlags: | Has picture, 1Table, ExtChar |
| System: | Windows |
| Word97: | No |
| Title: | - |
| Subject: | - |
| Author: | - |
| Keywords: | - |
| Comments: | - |
| Template: | Normal.dotm |
| LastModifiedBy: | - |
| Software: | Microsoft Office Word |
| CreateDate: | 2024:08:22 14:51:00 |
| ModifyDate: | 2024:08:23 07:28:00 |
| Security: | None |
| CodePage: | Windows Cyrillic |
| Company: | - |
| CharCountWithSpaces: | 373 |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | |
| HeadingPairs: |
|
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | ???????? Microsoft Word 97-2003 |
| LastPrinted: | 0000:00:00 00:00:00 |
| RevisionNumber: | 1 |
| TotalEditTime: | - |
| Words: | 55 |
| Characters: | 319 |
| Pages: | 1 |
| Paragraphs: | 1 |
| Lines: | 2 |
Total processes
38
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2788 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\Secure Connection.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3628 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
14 043
Read events
13 168
Write events
616
Delete events
259
Modification events
| (PID) Process: | (2788) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | >s0 |
Value: 3E733000E40A0000010000000000000000000000 | |||
| (PID) Process: | (2788) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2788) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2788) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2788) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2788) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2788) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2788) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2788) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2788) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
0
Suspicious files
3
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2788 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR239E.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2788 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\UProof\ExcludeDictionaryEN0809.lex | text | |
MD5:F3B25701FE362EC84616A93A45CE9998 | SHA256:B3D510EF04275CA8E698E5B3CBB0ECE3949EF9252F0CDC839E9EE347409A2209 | |||
| 2788 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$cure Connection.doc | binary | |
MD5:64CD5627AF6391347CB4EDC03961DEFB | SHA256:B15613475AA3B11BBD8FA87D09FFC64F662580DB99079BF83F8E6993A1322360 | |||
| 2788 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\Word8.0\MSForms.exd | binary | |
MD5:CD593FA29B707629B2AD02ADB6C78560 | SHA256:646FDC38657E7AC46FB1AD377C5D4E255EF7C7C374691228534FABC794C57D9B | |||
| 2788 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\UProof\ExcludeDictionaryRU0419.lex | text | |
MD5:F3B25701FE362EC84616A93A45CE9998 | SHA256:B3D510EF04275CA8E698E5B3CBB0ECE3949EF9252F0CDC839E9EE347409A2209 | |||
| 2788 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:157BE70D8F760DB7DF8ABDFD131B2EF9 | SHA256:24796B39FF0150DFBA1A5853FDD11B98A11B095CCC3EEC5013C78BFFE6E5C7EC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
15
DNS requests
9
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2788 | WINWORD.EXE | POST | 302 | 23.35.238.131:80 | http://go.microsoft.com/fwlink/?LinkID=120752 | unknown | — | — | whitelisted |
2788 | WINWORD.EXE | GET | 401 | 176.53.180.69:80 | http://kasperski.com.ru/api | unknown | — | — | unknown |
2788 | WINWORD.EXE | POST | 302 | 23.35.238.131:80 | http://go.microsoft.com/fwlink/?LinkID=120751 | unknown | — | — | whitelisted |
2788 | WINWORD.EXE | GET | 401 | 176.53.180.69:80 | http://kasperski.com.ru/api | unknown | — | — | unknown |
2788 | WINWORD.EXE | GET | 200 | 176.53.180.69:80 | http://kasperski.com.ru/api | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1372 | svchost.exe | GET | 304 | 23.50.131.200:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | whitelisted |
1060 | svchost.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?67a3611ec3c0260d | unknown | — | — | whitelisted |
2788 | WINWORD.EXE | POST | 302 | 23.35.238.131:80 | http://go.microsoft.com/fwlink/?LinkID=120750 | unknown | — | — | whitelisted |
1372 | svchost.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 239.255.255.250:3702 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1372 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
2788 | WINWORD.EXE | 176.53.180.69:80 | kasperski.com.ru | LLC Flex | RU | suspicious |
2788 | WINWORD.EXE | 23.35.238.131:80 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
2788 | WINWORD.EXE | 20.83.72.98:443 | activation.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1372 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
kasperski.com.ru |
| unknown |
go.microsoft.com |
| whitelisted |
activation.sls.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2788 | WINWORD.EXE | Generic Protocol Command Decode | SURICATA HTTP Request unrecognized authorization method |
2788 | WINWORD.EXE | Generic Protocol Command Decode | SURICATA HTTP Request unrecognized authorization method |