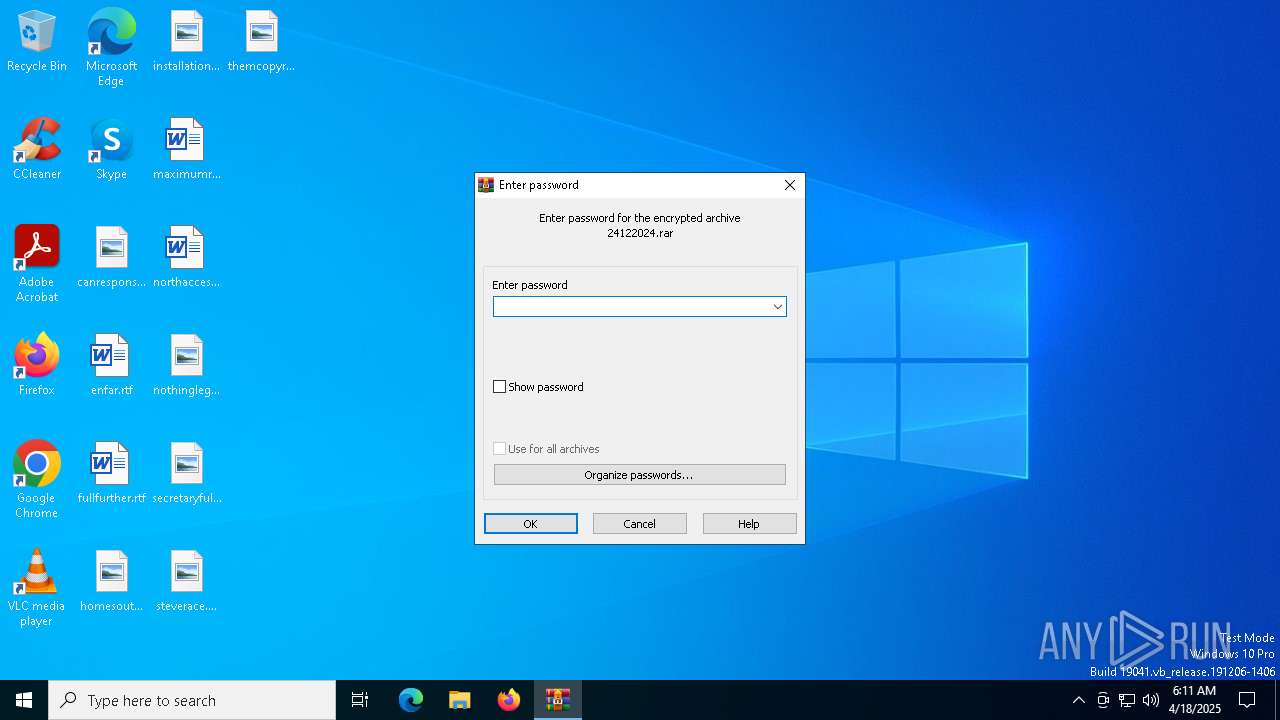
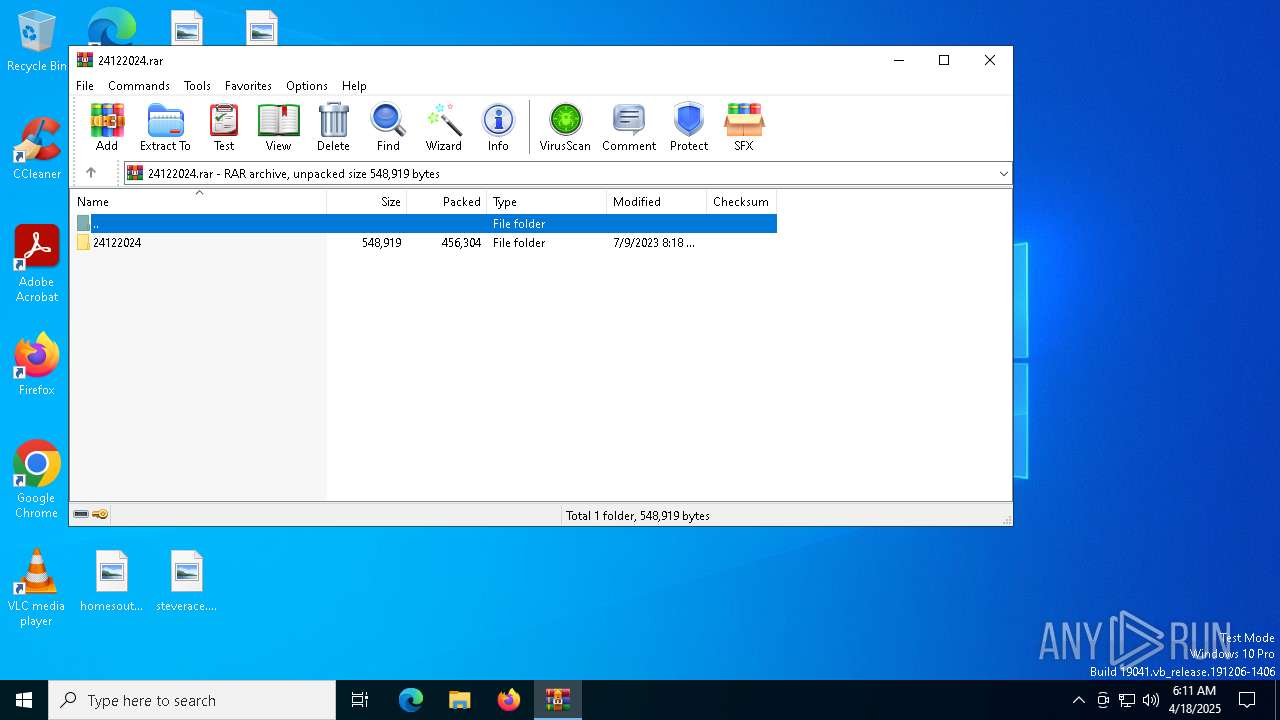
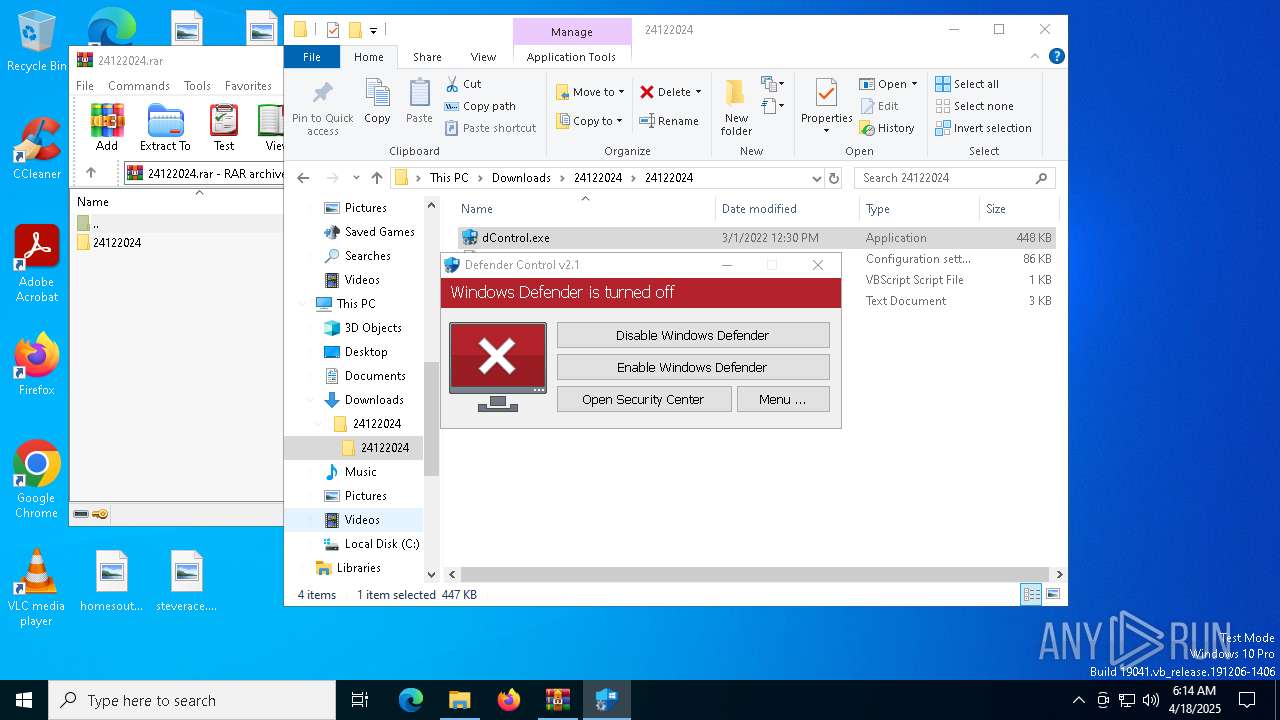
| File name: | 24122024.rar |
| Full analysis: | https://app.any.run/tasks/671a161c-bb8a-4f70-a4f5-b6481390a5be |
| Verdict: | Malicious activity |
| Analysis date: | April 18, 2025, 06:11:32 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 96B5933DE9FC36D0385CDD41F2955FE0 |
| SHA1: | C457E29BC8638C9E2E1E10203BC00F19DA1A8CA6 |
| SHA256: | B378D7F1FA1CFFA05B55917225232224FF0B13A1D739FEAC017C7FE56F1B3ADB |
| SSDEEP: | 24576:MOWOLvSnMMXIMkcLxpviyRJsGXSm+2Yh8daGpw3:MOWOLvSnMM4M9LxpviyRJsGXSm+2Yh8I |
MALICIOUS
Executing a file with an untrusted certificate
- dControl.exe (PID: 1228)
- dControl.exe (PID: 680)
- dControl.exe (PID: 6248)
- dControl.exe (PID: 660)
Creates or modifies Windows services
- dControl.exe (PID: 660)
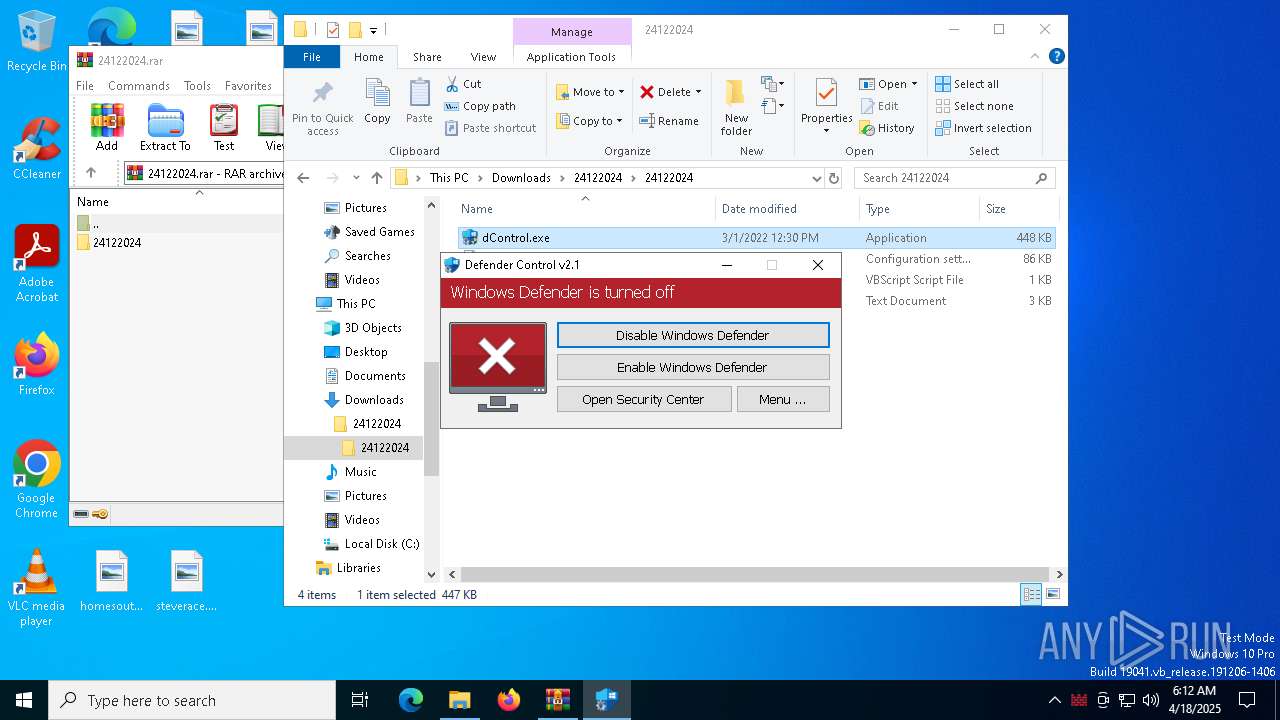
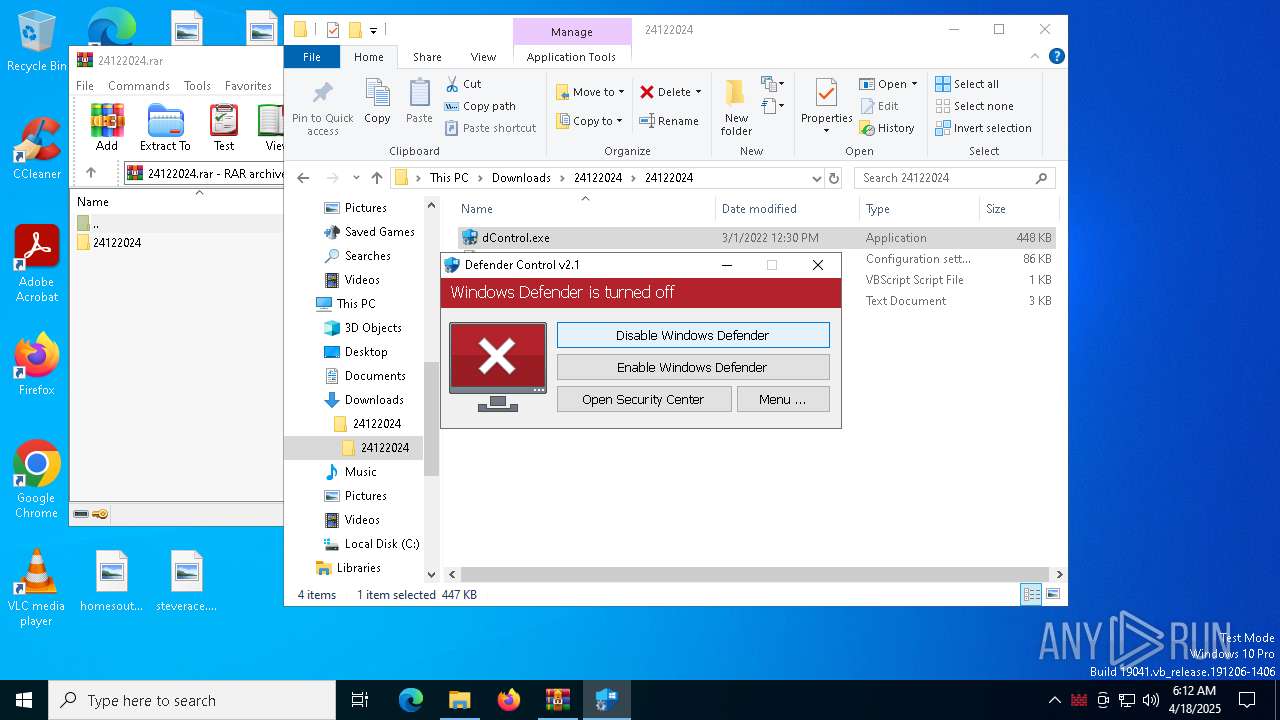
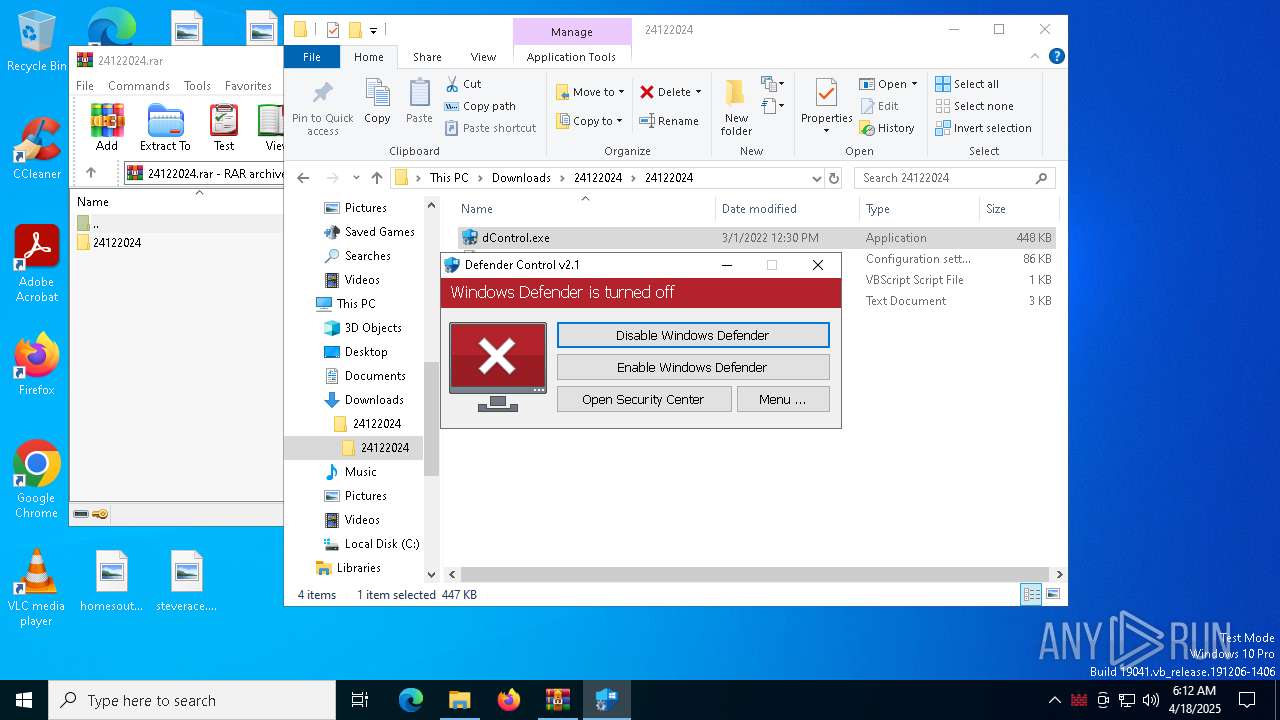
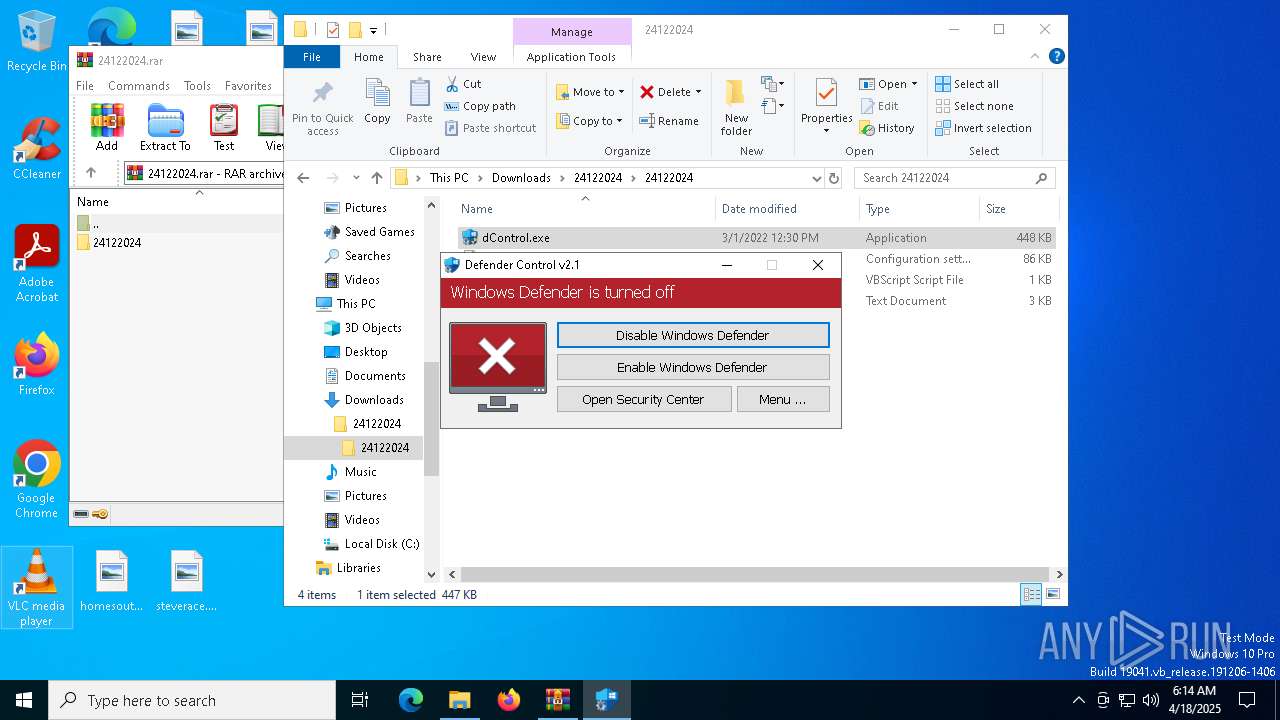
Disables Windows Defender
- dControl.exe (PID: 660)
Changes image file execution options
- dControl.exe (PID: 660)
SUSPICIOUS
Application launched itself
- dControl.exe (PID: 1228)
- dControl.exe (PID: 6248)
There is functionality for taking screenshot (YARA)
- dControl.exe (PID: 660)
Creates or modifies Windows services
- dControl.exe (PID: 660)
INFO
Manual execution by a user
- dControl.exe (PID: 680)
- dControl.exe (PID: 1228)
- msedge.exe (PID: 5352)
The sample compiled with english language support
- WinRAR.exe (PID: 6708)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6708)
Checks supported languages
- dControl.exe (PID: 1228)
- dControl.exe (PID: 6248)
- dControl.exe (PID: 660)
- identity_helper.exe (PID: 2516)
Reads mouse settings
- dControl.exe (PID: 1228)
- dControl.exe (PID: 6248)
- dControl.exe (PID: 660)
Create files in a temporary directory
- dControl.exe (PID: 1228)
Reads the computer name
- dControl.exe (PID: 1228)
- dControl.exe (PID: 6248)
- dControl.exe (PID: 660)
- identity_helper.exe (PID: 2516)
DEFENDERCONTROL has been detected
- dControl.exe (PID: 1228)
- dControl.exe (PID: 6248)
The process uses AutoIt
- dControl.exe (PID: 660)
Reads the software policy settings
- slui.exe (PID: 6632)
- slui.exe (PID: 3300)
UPX packer has been detected
- dControl.exe (PID: 660)
Checks proxy server information
- slui.exe (PID: 3300)
Application launched itself
- msedge.exe (PID: 5352)
Reads Environment values
- identity_helper.exe (PID: 2516)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|
Total processes
207
Monitored processes
55
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
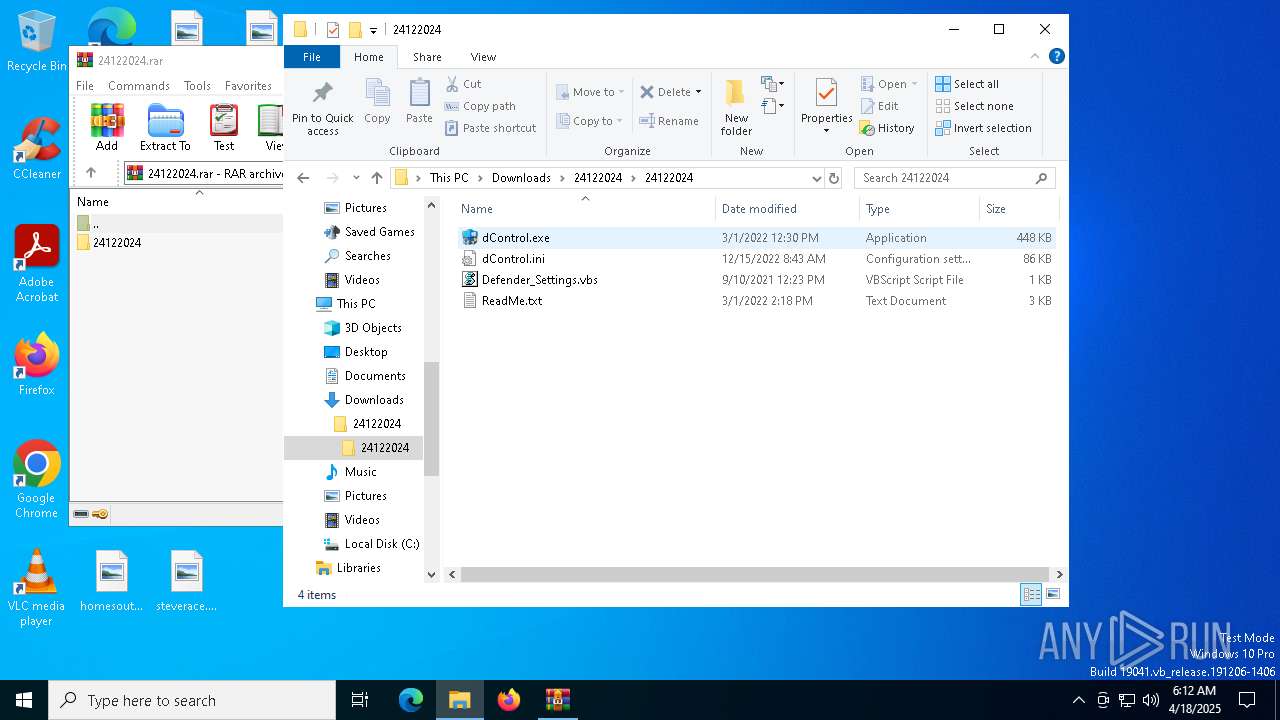
| 660 | "C:\Users\admin\Downloads\24122024\24122024\dControl.exe" /TI | C:\Users\admin\Downloads\24122024\24122024\dControl.exe | dControl.exe | ||||||||||||
User: SYSTEM Company: www.sordum.org Integrity Level: SYSTEM Description: dControl v2.1 Version: 2.1.0.0 Modules
| |||||||||||||||
| 664 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=3612 --field-trial-handle=1440,i,3171982866531441693,11212585518573216534,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 680 | "C:\Users\admin\Downloads\24122024\24122024\dControl.exe" | C:\Users\admin\Downloads\24122024\24122024\dControl.exe | — | explorer.exe | |||||||||||
User: admin Company: www.sordum.org Integrity Level: MEDIUM Description: dControl v2.1 Exit code: 3221226540 Version: 2.1.0.0 Modules
| |||||||||||||||
| 732 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --instant-process --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=3540 --field-trial-handle=1440,i,3171982866531441693,11212585518573216534,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 872 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=entity_extraction_service.mojom.Extractor --lang=en-US --service-sandbox-type=entity_extraction --onnx-enabled-for-ee --no-appcompat-clear --mojo-platform-channel-handle=5456 --field-trial-handle=1440,i,3171982866531441693,11212585518573216534,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1228 | "C:\Users\admin\Downloads\24122024\24122024\dControl.exe" | C:\Users\admin\Downloads\24122024\24122024\dControl.exe | explorer.exe | ||||||||||||
User: admin Company: www.sordum.org Integrity Level: HIGH Description: dControl v2.1 Exit code: 0 Version: 2.1.0.0 Modules
| |||||||||||||||
| 1244 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6640 --field-trial-handle=1440,i,3171982866531441693,11212585518573216534,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2088 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5992 --field-trial-handle=1440,i,3171982866531441693,11212585518573216534,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2108 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2408 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5996 --field-trial-handle=1440,i,3171982866531441693,11212585518573216534,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
8 187
Read events
8 088
Write events
84
Delete events
15
Modification events
| (PID) Process: | (6708) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (6708) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6708) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6708) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6708) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\24122024.rar | |||
| (PID) Process: | (6708) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6708) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6708) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6708) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6708) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
Executable files
40
Suspicious files
599
Text files
93
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6708 | WinRAR.exe | C:\Users\admin\Downloads\24122024\24122024\dControl.ini | text | |
MD5:05450FF06366AE22654B63A6E27D1624 | SHA256:8E9A84DA243905685CA77B6EF71841E610B88B7963D4DE59F6DCBDD1621ECACD | |||
| 660 | dControl.exe | C:\Windows\Temp\aut1E93.tmp | binary | |
MD5:ECFFD3E81C5F2E3C62BCDC122442B5F2 | SHA256:9874AB363B07DCC7E9CD6022A380A64102C1814343642295239A9F120CB941C5 | |||
| 1228 | dControl.exe | C:\Users\admin\AppData\Local\Temp\1v2x2i8s.tmp | text | |
MD5:E00DCC76E4DCD90994587375125DE04B | SHA256:C8709F5A8B971D136E2273D66E65449791CA8EBA1F47DD767733EA52EE635447 | |||
| 1228 | dControl.exe | C:\Users\admin\AppData\Local\Temp\aut1BE3.tmp | binary | |
MD5:EFE44D9F6E4426A05E39F99AD407D3E7 | SHA256:5EA3B26C6B1B71EDAEF17CE365D50BE963AE9F4CB79B39EC723FE6E9E4054366 | |||
| 6248 | dControl.exe | C:\Windows\Temp\aut1DA7.tmp | binary | |
MD5:9D5A0EF18CC4BB492930582064C5330F | SHA256:8F5BBCC572BC62FEB13A669F856D21886A61888FD6288AFD066272A27EA79BB3 | |||
| 5352 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF134aa8.TMP | — | |
MD5:— | SHA256:— | |||
| 5352 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5352 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF134aa8.TMP | — | |
MD5:— | SHA256:— | |||
| 5352 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5352 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF134aa8.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
23
TCP/UDP connections
115
DNS requests
126
Threats
17
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6800 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.72:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6800 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7512 | svchost.exe | HEAD | 200 | 208.89.74.27:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9b9f8fb4-8a65-41e4-bda3-5416858f0aeb?P1=1745356197&P2=404&P3=2&P4=OnAHXexy4zOHLy01FZ4f5MGztcmm636GVpUWntA8mqhyem1kRdkm2I1S5wyvZAL3uTKnF8B6ujUpLvdh0vwByw%3d%3d | unknown | — | — | whitelisted |
7512 | svchost.exe | GET | 206 | 208.89.74.27:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9b9f8fb4-8a65-41e4-bda3-5416858f0aeb?P1=1745356197&P2=404&P3=2&P4=OnAHXexy4zOHLy01FZ4f5MGztcmm636GVpUWntA8mqhyem1kRdkm2I1S5wyvZAL3uTKnF8B6ujUpLvdh0vwByw%3d%3d | unknown | — | — | whitelisted |
7512 | svchost.exe | GET | 206 | 208.89.74.27:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9b9f8fb4-8a65-41e4-bda3-5416858f0aeb?P1=1745356197&P2=404&P3=2&P4=OnAHXexy4zOHLy01FZ4f5MGztcmm636GVpUWntA8mqhyem1kRdkm2I1S5wyvZAL3uTKnF8B6ujUpLvdh0vwByw%3d%3d | unknown | — | — | whitelisted |
7512 | svchost.exe | GET | 206 | 208.89.74.27:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9b9f8fb4-8a65-41e4-bda3-5416858f0aeb?P1=1745356197&P2=404&P3=2&P4=OnAHXexy4zOHLy01FZ4f5MGztcmm636GVpUWntA8mqhyem1kRdkm2I1S5wyvZAL3uTKnF8B6ujUpLvdh0vwByw%3d%3d | unknown | — | — | whitelisted |
7512 | svchost.exe | GET | 206 | 208.89.74.27:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9b9f8fb4-8a65-41e4-bda3-5416858f0aeb?P1=1745356197&P2=404&P3=2&P4=OnAHXexy4zOHLy01FZ4f5MGztcmm636GVpUWntA8mqhyem1kRdkm2I1S5wyvZAL3uTKnF8B6ujUpLvdh0vwByw%3d%3d | unknown | — | — | whitelisted |
7512 | svchost.exe | GET | 200 | 208.89.74.27:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/23e5dd61-e224-4d56-858f-6ee086574ada?P1=1745356199&P2=404&P3=2&P4=IUoZGrNl5UNTPxIvEc0AqfT8xCZzv44%2fLHXS8sI%2f7q53oOJPCu55JYf7%2fuUxRtV37cz2eSOM7iRaFI1BaFG1uA%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.164.72:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.32.72:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6800 | SIHClient.exe | 4.245.163.56:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6800 | SIHClient.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7144 | msedge.exe | Potentially Bad Traffic | ET FILE_SHARING Online File Storage Domain in DNS Lookup (gofile .io) |
7144 | msedge.exe | Potentially Bad Traffic | ET FILE_SHARING Online File Storage Domain in DNS Lookup (gofile .io) |
7144 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in TLS SNI (gofile .io) |
7144 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in TLS SNI (gofile .io) |
7144 | msedge.exe | Potentially Bad Traffic | ET FILE_SHARING Online File Storage Domain in DNS Lookup (gofile .io) |
7144 | msedge.exe | Potentially Bad Traffic | ET FILE_SHARING Online File Storage Domain in DNS Lookup (gofile .io) |
7144 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in TLS SNI (gofile .io) |
7144 | msedge.exe | Potentially Bad Traffic | ET FILE_SHARING Online File Storage Domain in DNS Lookup (gofile .io) |
7144 | msedge.exe | Potentially Bad Traffic | ET FILE_SHARING Online File Storage Domain in DNS Lookup (gofile .io) |
7144 | msedge.exe | Potentially Bad Traffic | ET FILE_SHARING Online File Storage Domain in DNS Lookup (gofile .io) |