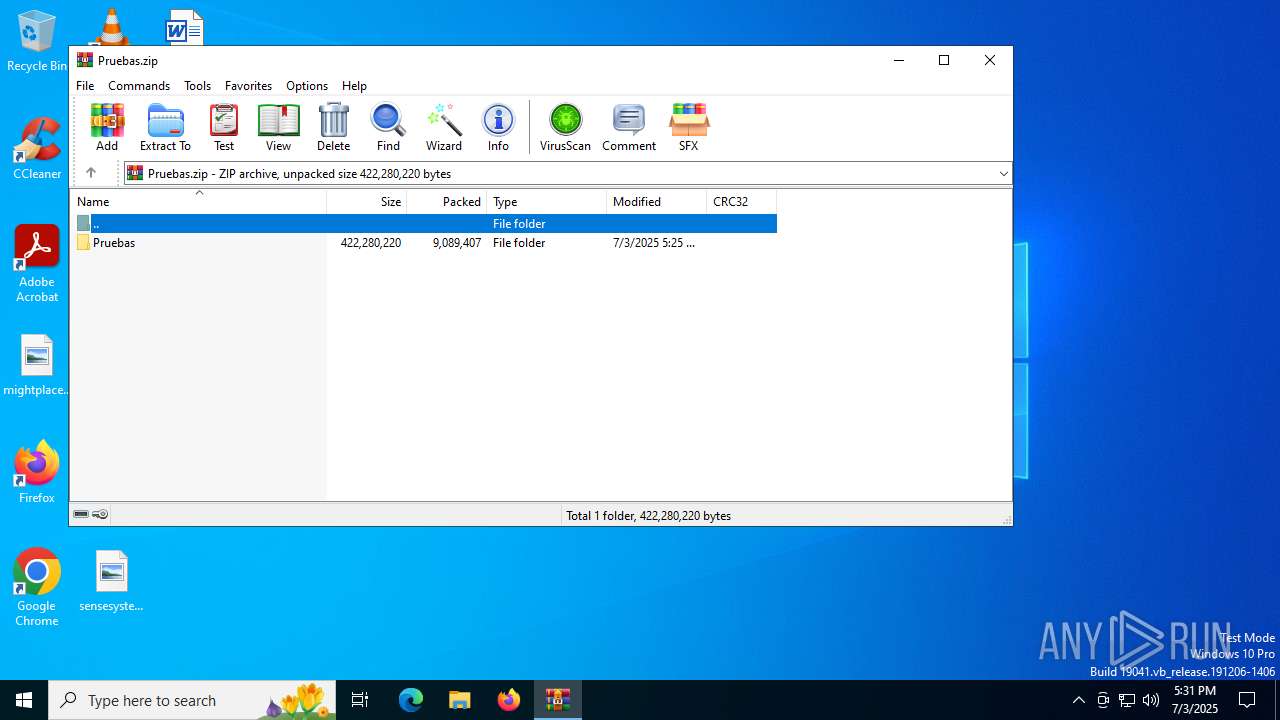
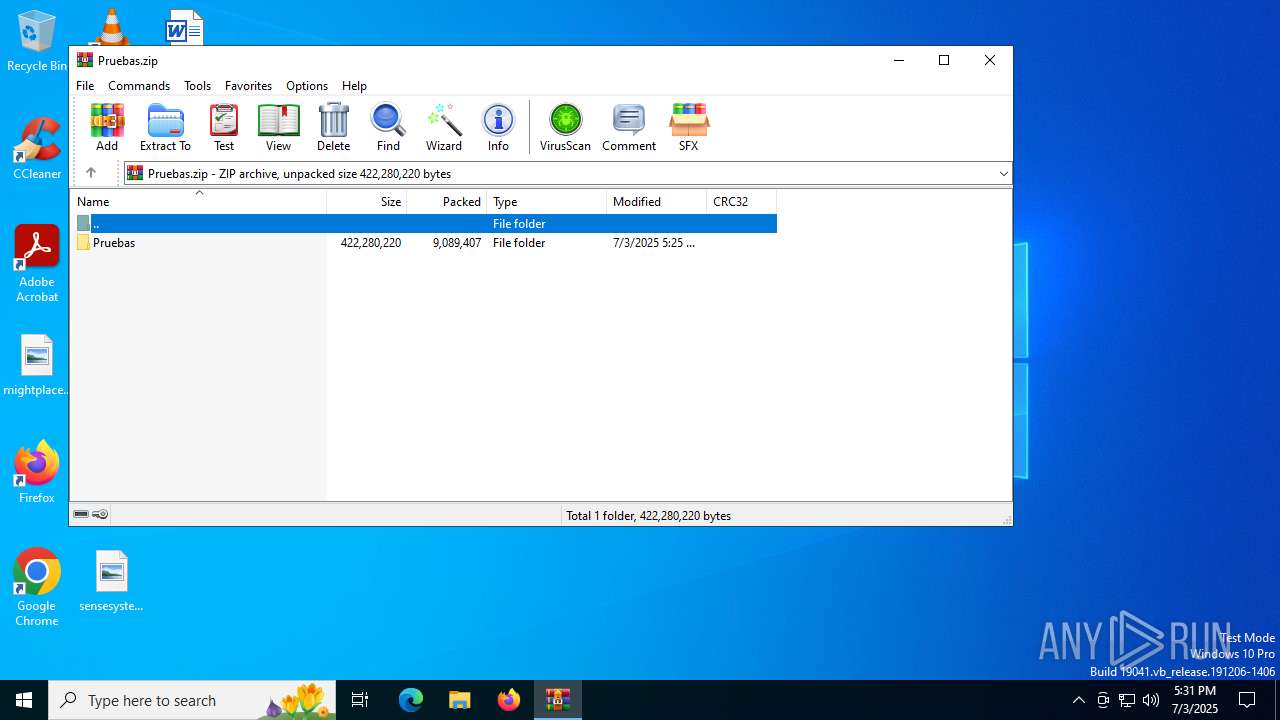
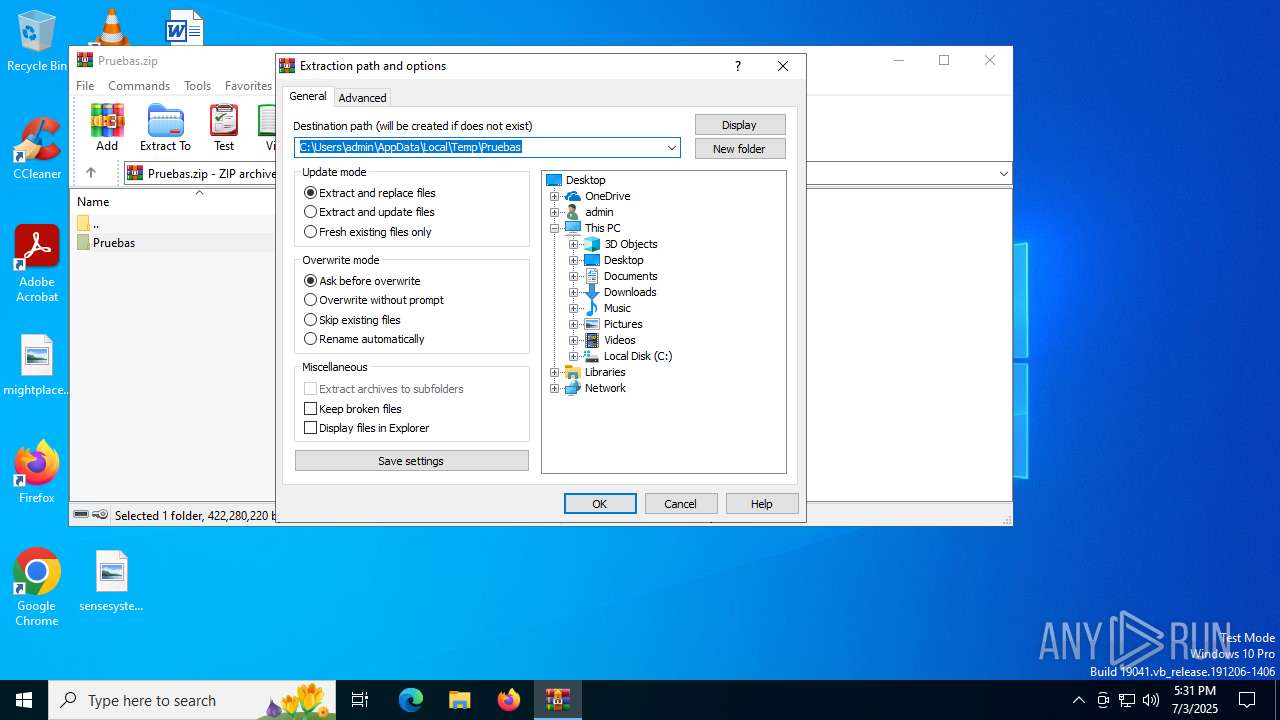
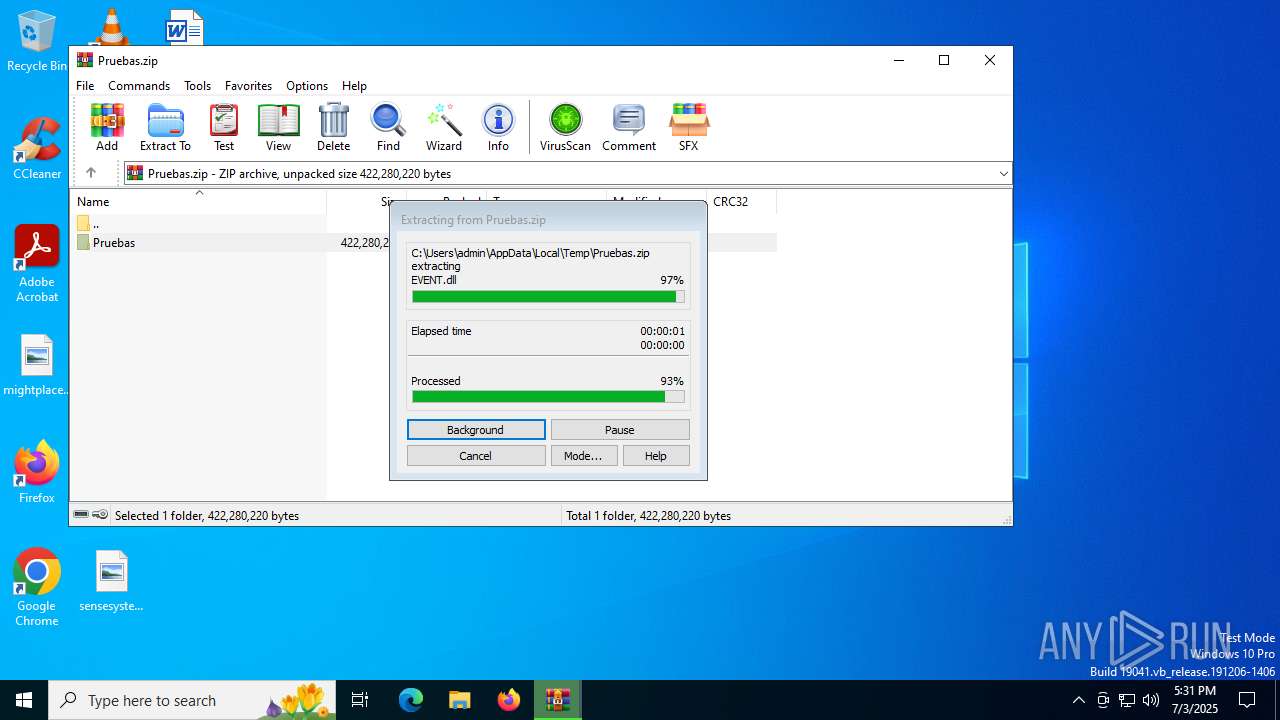
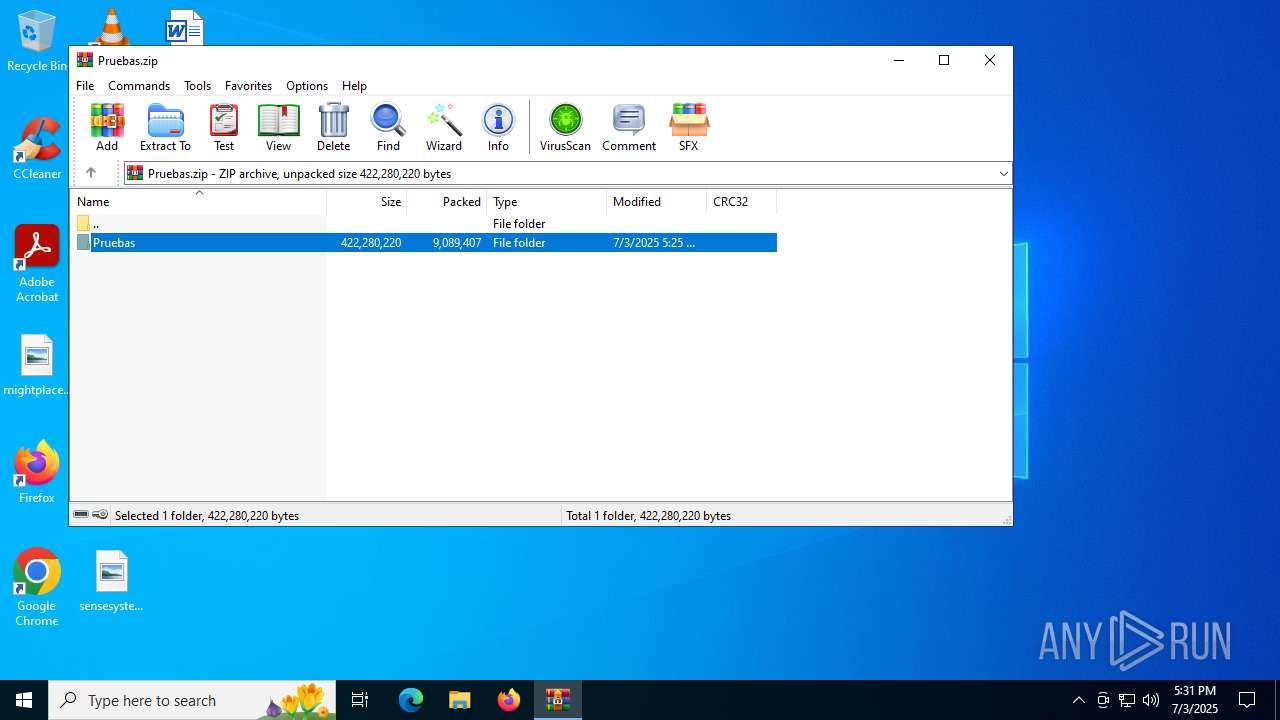
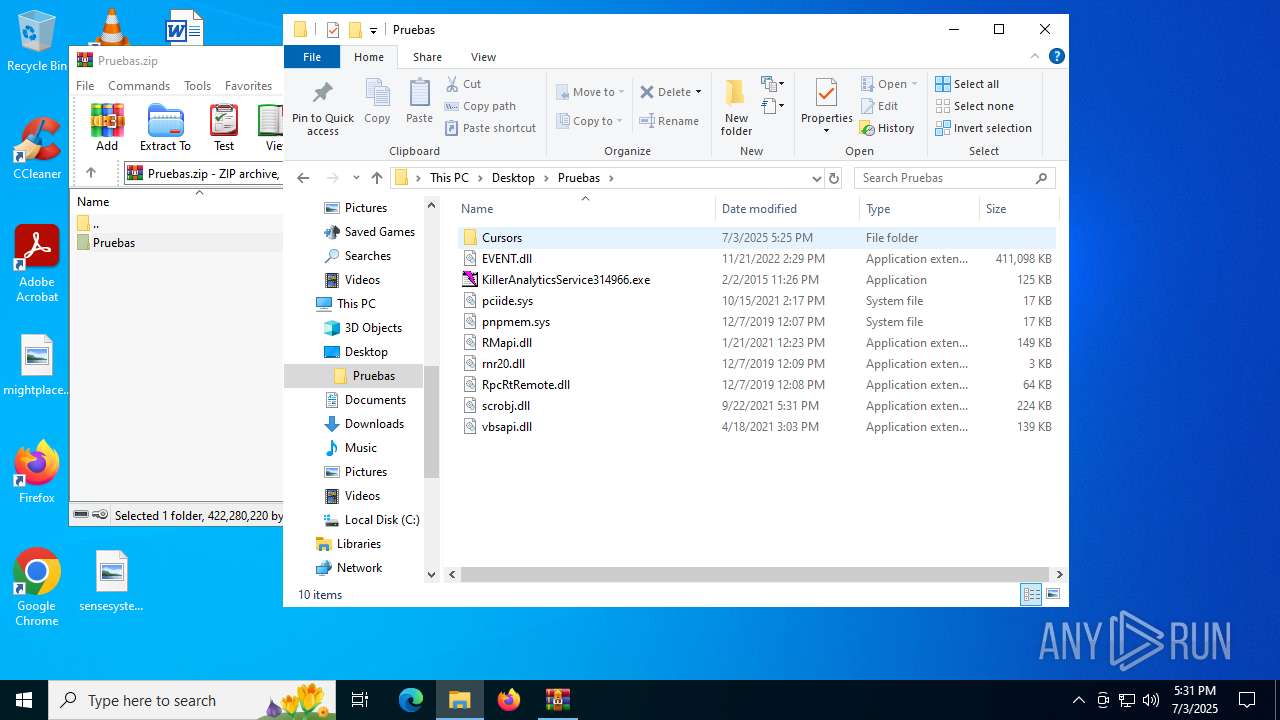
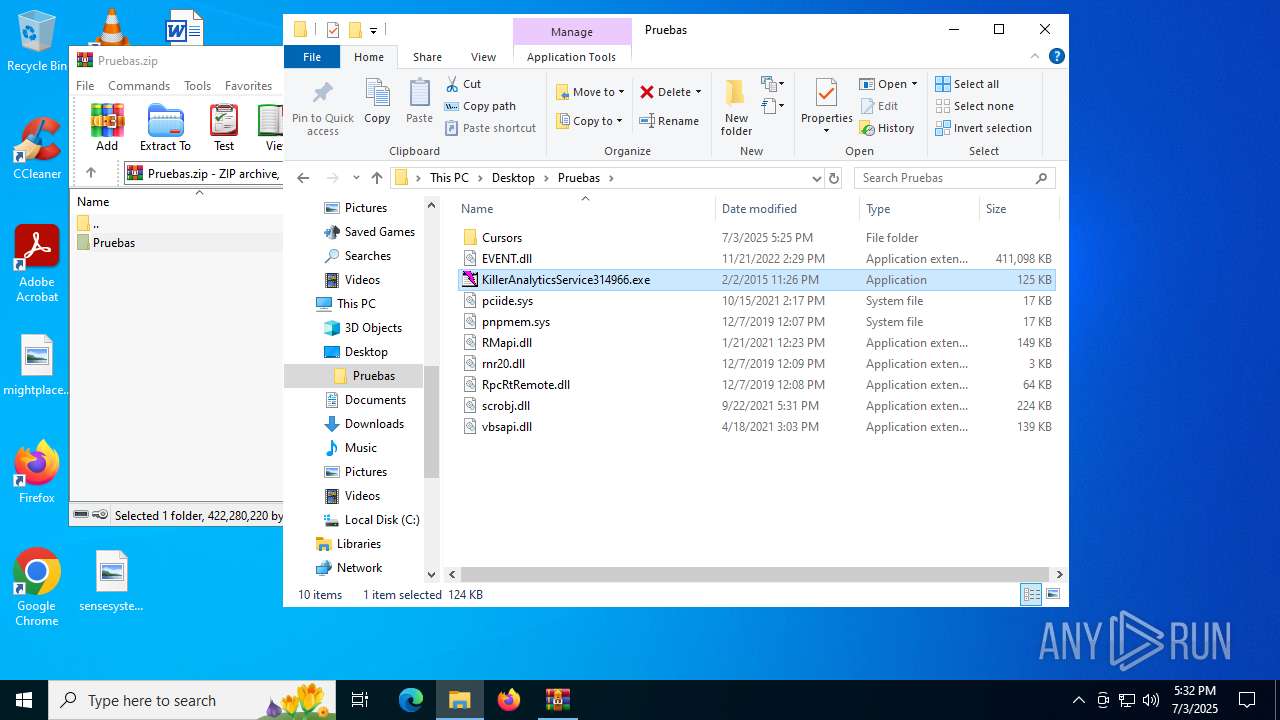
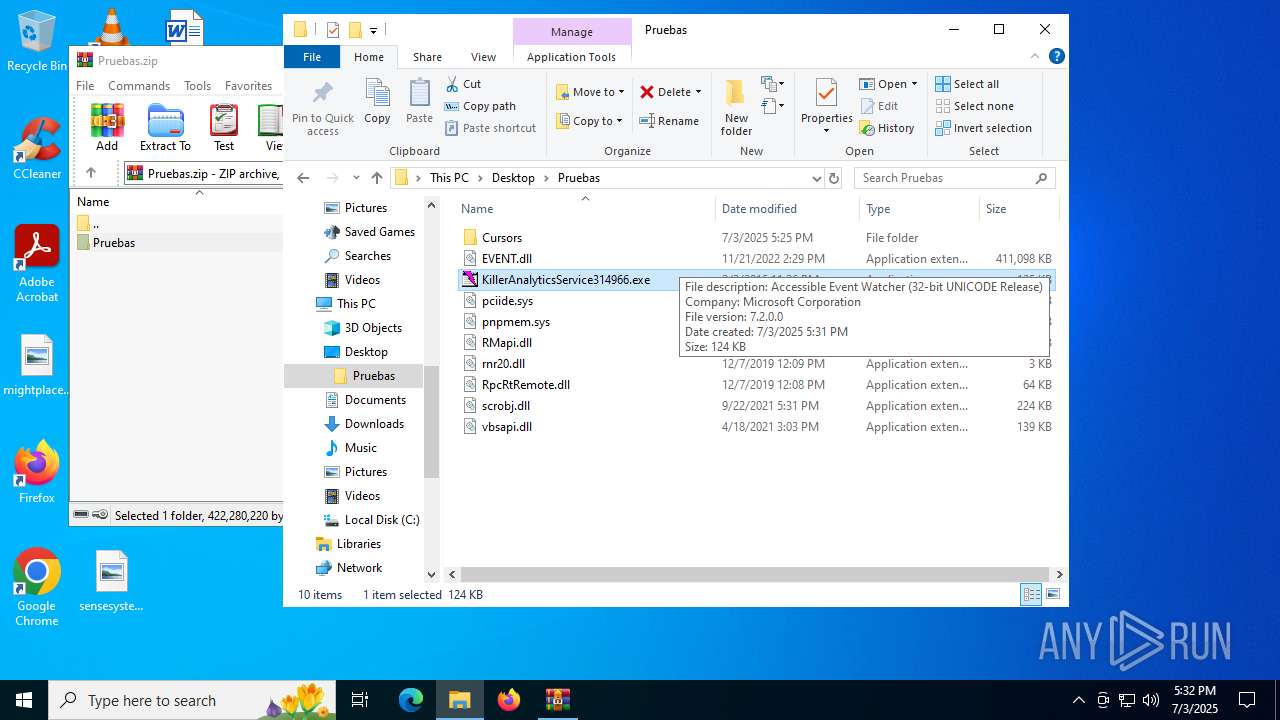
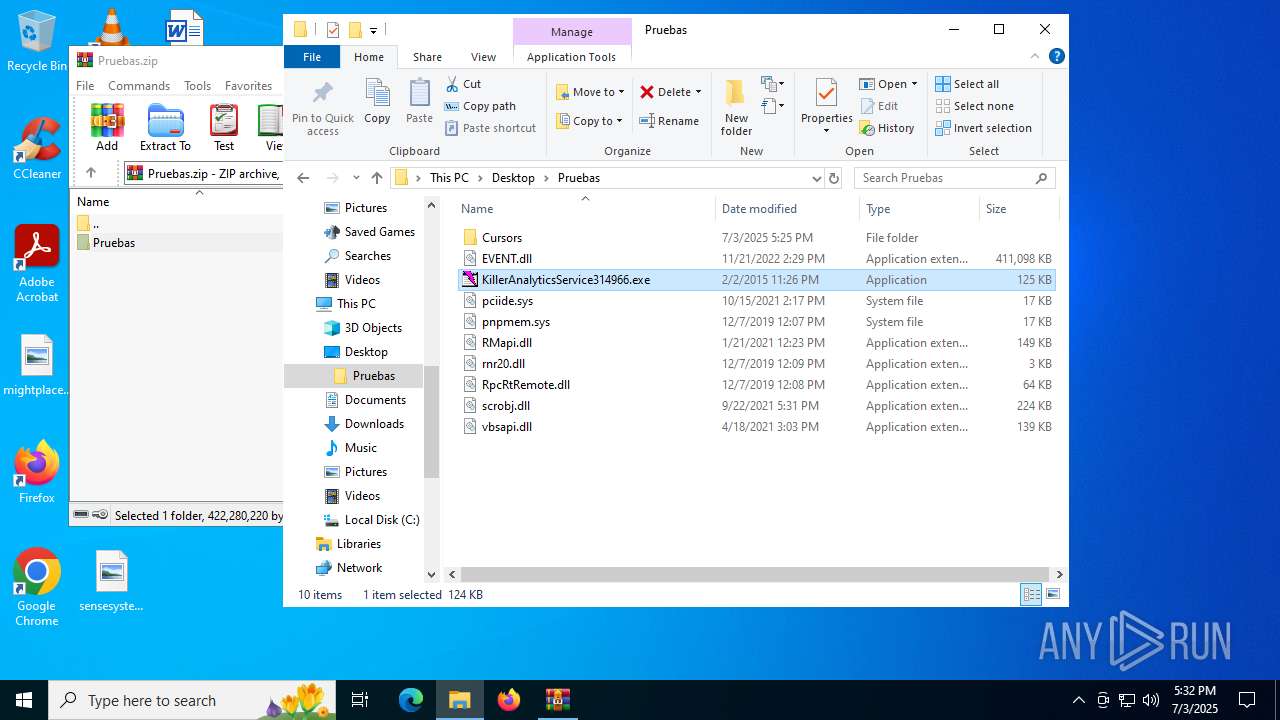
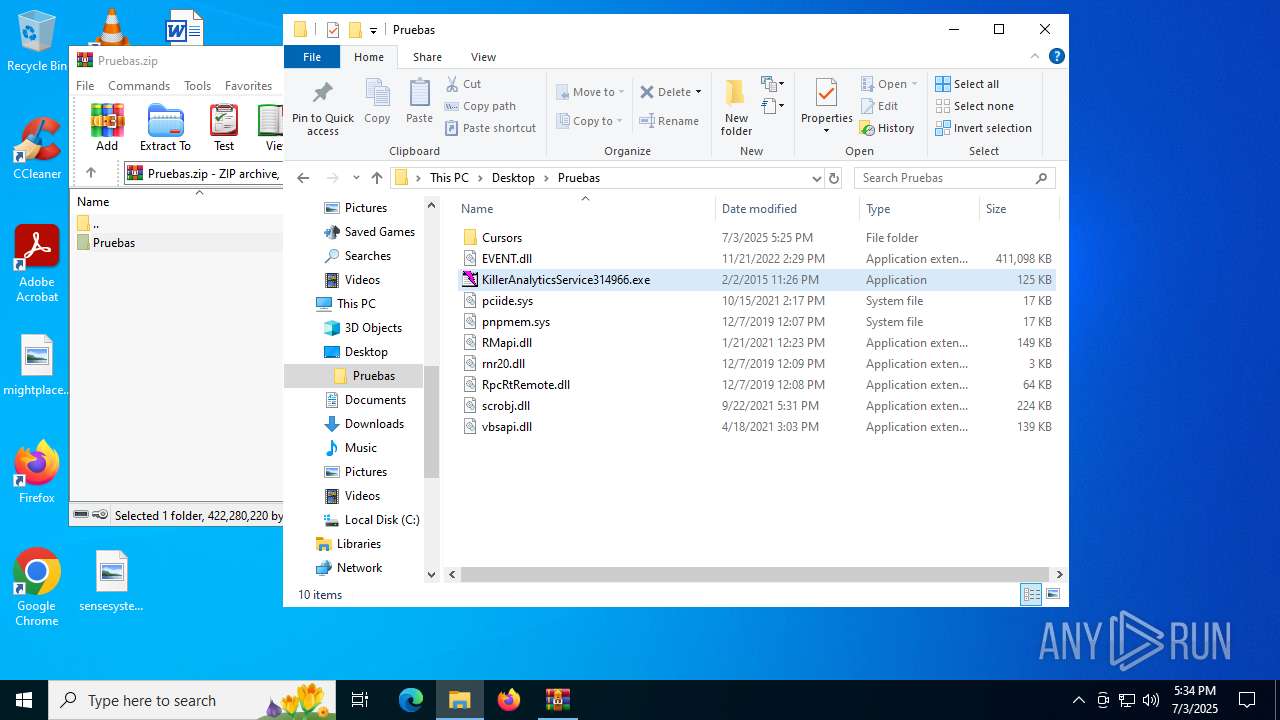
| File name: | Pruebas.zip |
| Full analysis: | https://app.any.run/tasks/1623e723-b580-4e4e-9b73-d8d93b8aa5f8 |
| Verdict: | Malicious activity |
| Analysis date: | July 03, 2025, 17:31:26 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | D3F1320AB3B1CF00A739F823D80A7425 |
| SHA1: | 99B944DA69C294A8596EDD940304222793747B0F |
| SHA256: | B3728E7E8F284B54113FBD9A22E8E2FD1BB2867436F3F26F581D5D0E355B6A88 |
| SSDEEP: | 98304:XUtM7uiNqXcqavFG2bJ6FGkDje36sEhwWqvKEVAPlTQkBkOcqZuCX0WFmnt5RDaF:AG4Xg4v0ZKp9fgexD |
MALICIOUS
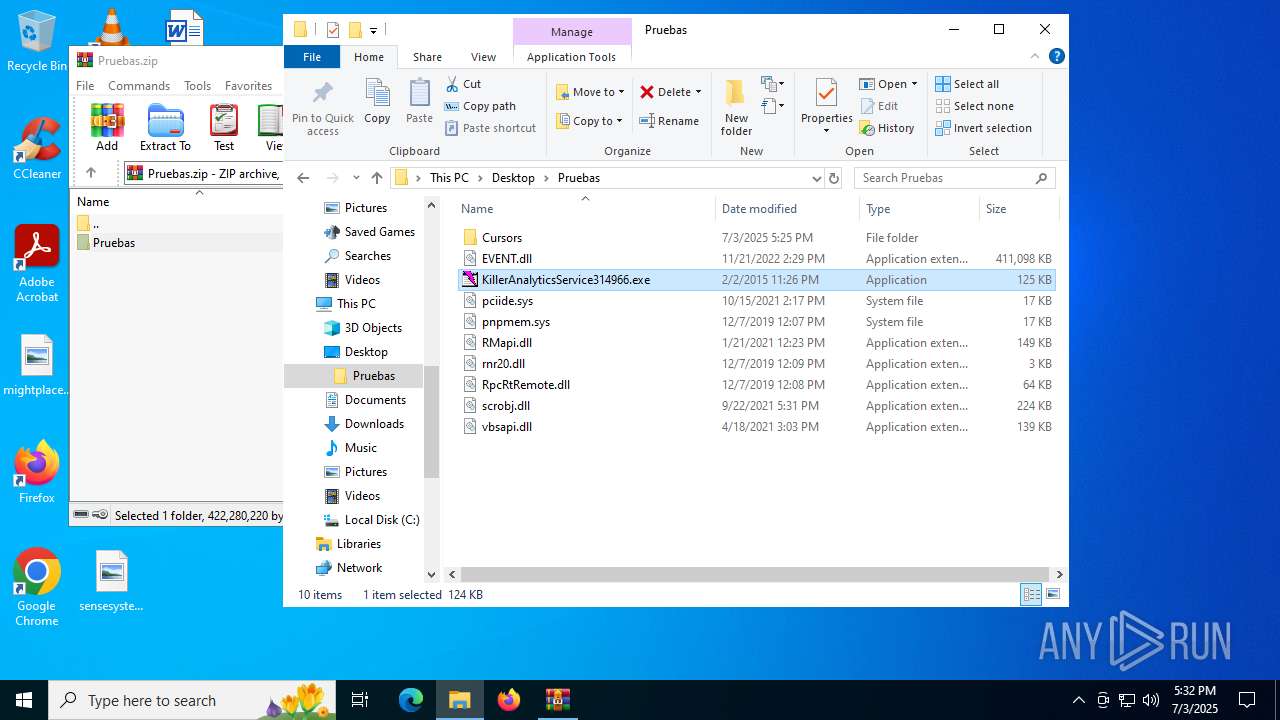
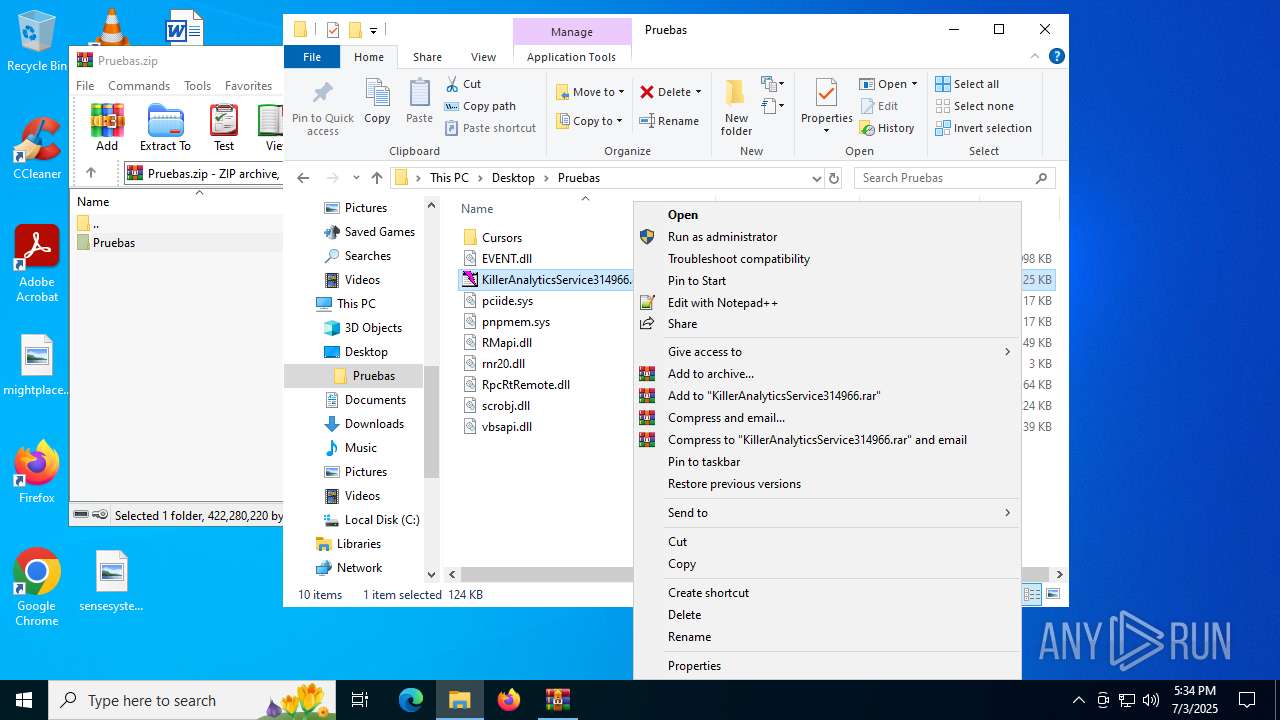
Executing a file with an untrusted certificate
- KillerAnalyticsService314966.exe (PID: 6940)
- KillerAnalyticsService314966.exe (PID: 4456)
- KillerAnalyticsService314966.exe (PID: 4760)
- KillerAnalyticsService314966.exe (PID: 3400)
- KillerAnalyticsService314966.exe (PID: 1700)
- KillerAnalyticsService314966.exe (PID: 424)
- KillerAnalyticsService314966.exe (PID: 1652)
SUSPICIOUS
Starts a Microsoft application from unusual location
- KillerAnalyticsService314966.exe (PID: 4456)
- KillerAnalyticsService314966.exe (PID: 6940)
- KillerAnalyticsService314966.exe (PID: 4760)
- KillerAnalyticsService314966.exe (PID: 424)
- KillerAnalyticsService314966.exe (PID: 3400)
- KillerAnalyticsService314966.exe (PID: 1700)
- KillerAnalyticsService314966.exe (PID: 1652)
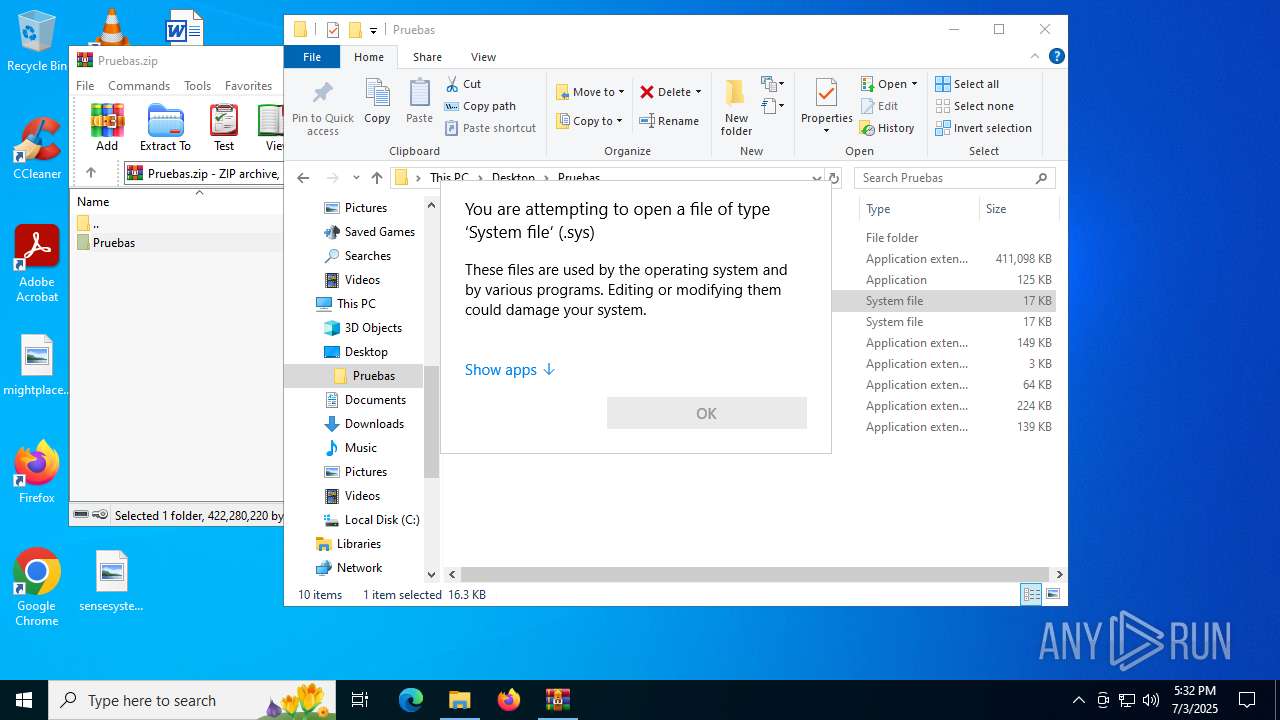
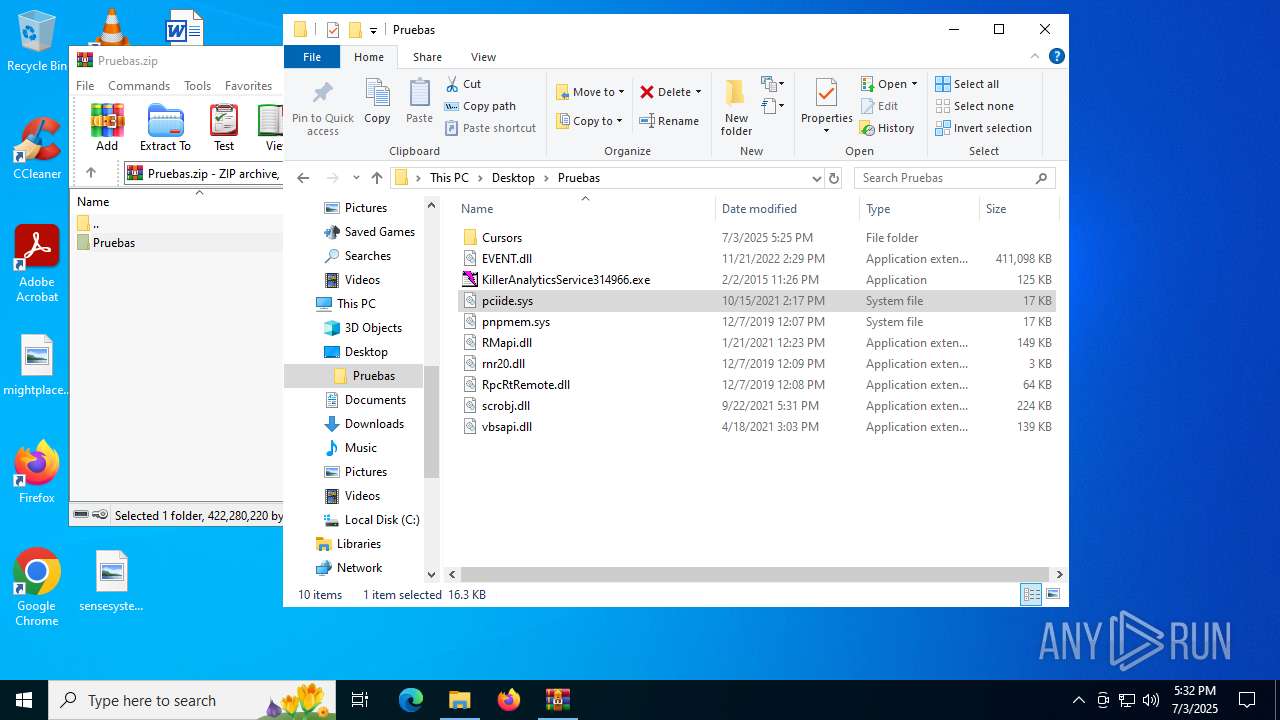
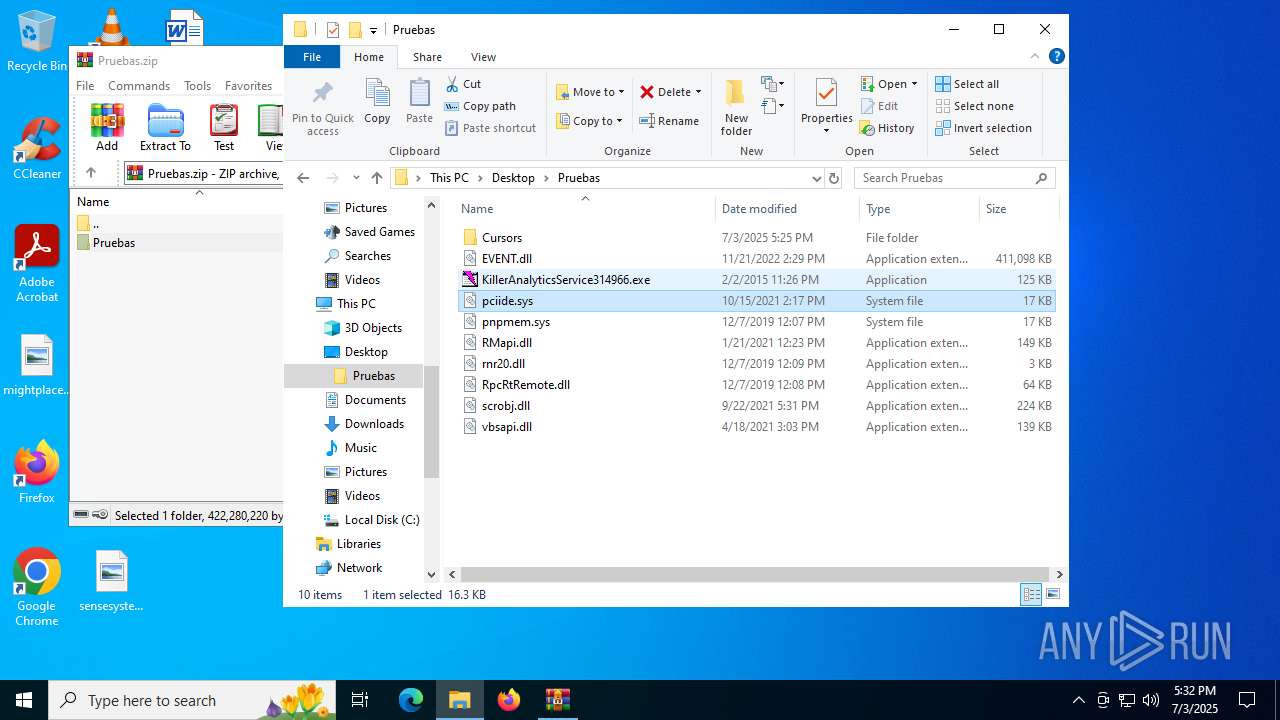
Process drops legitimate windows executable
- WinRAR.exe (PID: 6648)
Drops a system driver (possible attempt to evade defenses)
- WinRAR.exe (PID: 6648)
Reads the date of Windows installation
- KillerAnalyticsService314966.exe (PID: 4456)
- KillerAnalyticsService314966.exe (PID: 424)
- KillerAnalyticsService314966.exe (PID: 1700)
- KillerAnalyticsService314966.exe (PID: 1652)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6648)
The sample compiled with english language support
- WinRAR.exe (PID: 6648)
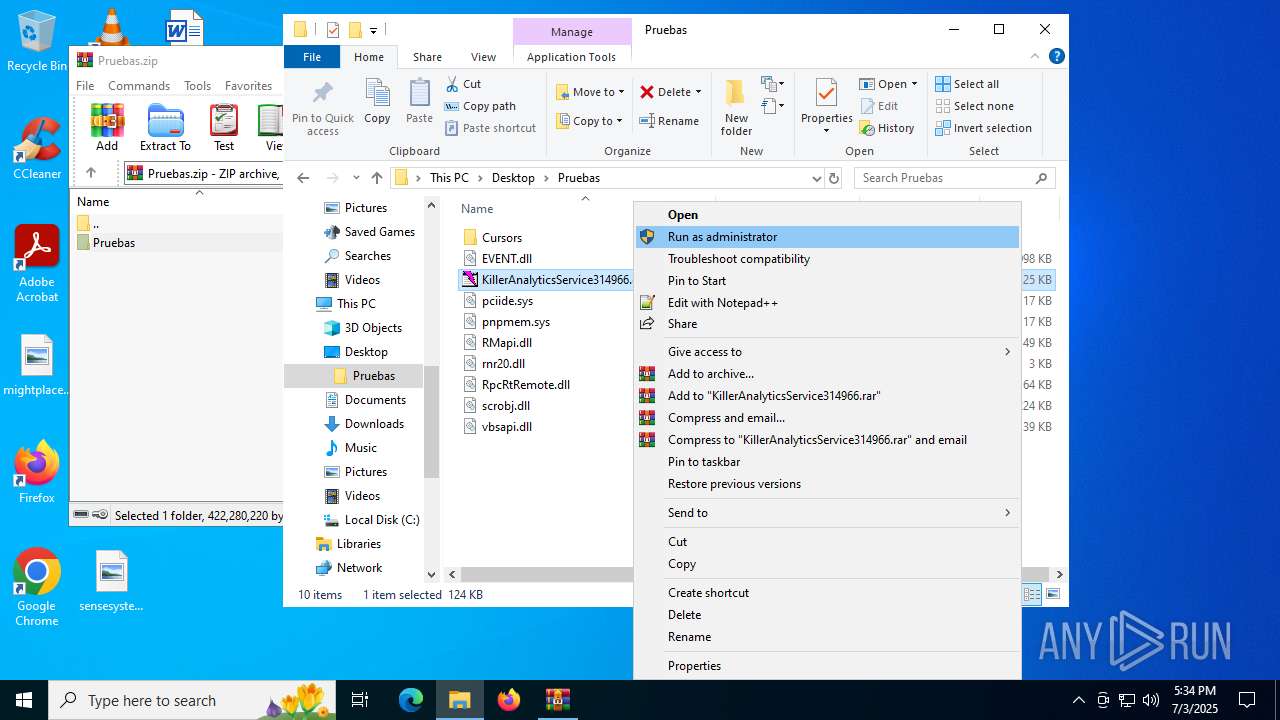
Manual execution by a user
- KillerAnalyticsService314966.exe (PID: 6940)
- KillerAnalyticsService314966.exe (PID: 4456)
- KillerAnalyticsService314966.exe (PID: 4760)
- KillerAnalyticsService314966.exe (PID: 424)
- KillerAnalyticsService314966.exe (PID: 3400)
- KillerAnalyticsService314966.exe (PID: 1700)
- KillerAnalyticsService314966.exe (PID: 1652)
Checks supported languages
- KillerAnalyticsService314966.exe (PID: 4456)
- KillerAnalyticsService314966.exe (PID: 424)
- KillerAnalyticsService314966.exe (PID: 1652)
- KillerAnalyticsService314966.exe (PID: 1700)
Reads the computer name
- KillerAnalyticsService314966.exe (PID: 4456)
- KillerAnalyticsService314966.exe (PID: 424)
- KillerAnalyticsService314966.exe (PID: 1652)
- KillerAnalyticsService314966.exe (PID: 1700)
Reads Environment values
- KillerAnalyticsService314966.exe (PID: 4456)
- KillerAnalyticsService314966.exe (PID: 424)
- KillerAnalyticsService314966.exe (PID: 1700)
- KillerAnalyticsService314966.exe (PID: 1652)
Reads CPU info
- KillerAnalyticsService314966.exe (PID: 4456)
- KillerAnalyticsService314966.exe (PID: 424)
- KillerAnalyticsService314966.exe (PID: 1652)
- KillerAnalyticsService314966.exe (PID: 1700)
Reads product name
- KillerAnalyticsService314966.exe (PID: 4456)
- KillerAnalyticsService314966.exe (PID: 424)
- KillerAnalyticsService314966.exe (PID: 1700)
- KillerAnalyticsService314966.exe (PID: 1652)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 4580)
- OpenWith.exe (PID: 2792)
- OpenWith.exe (PID: 868)
Reads the software policy settings
- slui.exe (PID: 6336)
Checks proxy server information
- slui.exe (PID: 6336)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:07:03 11:25:38 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Pruebas/ |
Total processes
159
Monitored processes
13
Malicious processes
5
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 424 | "C:\Users\admin\Desktop\Pruebas\KillerAnalyticsService314966.exe" | C:\Users\admin\Desktop\Pruebas\KillerAnalyticsService314966.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Accessible Event Watcher (32-bit UNICODE Release) Exit code: 0 Version: 7.2.0.0 Modules
| |||||||||||||||
| 868 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1652 | "C:\Users\admin\Desktop\Pruebas\KillerAnalyticsService314966.exe" | C:\Users\admin\Desktop\Pruebas\KillerAnalyticsService314966.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Accessible Event Watcher (32-bit UNICODE Release) Exit code: 0 Version: 7.2.0.0 Modules
| |||||||||||||||
| 1700 | "C:\Users\admin\Desktop\Pruebas\KillerAnalyticsService314966.exe" | C:\Users\admin\Desktop\Pruebas\KillerAnalyticsService314966.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Accessible Event Watcher (32-bit UNICODE Release) Exit code: 0 Version: 7.2.0.0 Modules
| |||||||||||||||
| 2792 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3400 | "C:\Users\admin\Desktop\Pruebas\KillerAnalyticsService314966.exe" | C:\Users\admin\Desktop\Pruebas\KillerAnalyticsService314966.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Accessible Event Watcher (32-bit UNICODE Release) Exit code: 3221226540 Version: 7.2.0.0 Modules
| |||||||||||||||
| 4156 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4456 | "C:\Users\admin\Desktop\Pruebas\KillerAnalyticsService314966.exe" | C:\Users\admin\Desktop\Pruebas\KillerAnalyticsService314966.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Accessible Event Watcher (32-bit UNICODE Release) Exit code: 0 Version: 7.2.0.0 Modules
| |||||||||||||||
| 4580 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4760 | "C:\Users\admin\Desktop\Pruebas\KillerAnalyticsService314966.exe" | C:\Users\admin\Desktop\Pruebas\KillerAnalyticsService314966.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Accessible Event Watcher (32-bit UNICODE Release) Exit code: 3221226540 Version: 7.2.0.0 Modules
| |||||||||||||||
Total events
7 126
Read events
7 099
Write events
14
Delete events
13
Modification events
| (PID) Process: | (6648) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6648) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6648) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6648) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Pruebas.zip | |||
| (PID) Process: | (6648) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6648) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6648) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6648) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6648) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (6648) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
Executable files
8
Suspicious files
0
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6648 | WinRAR.exe | C:\Users\admin\Desktop\Pruebas\EVENT.dll | — | |
MD5:— | SHA256:— | |||
| 6648 | WinRAR.exe | C:\Users\admin\Desktop\Pruebas\Cursors\aero_nesw.cur | image | |
MD5:B6DEEA348966D73380190E4A2E166E0B | SHA256:18108C75EEC4CDE840614716C828C16912549BF18E0EDC610F15B0236B0512EA | |||
| 6648 | WinRAR.exe | C:\Users\admin\Desktop\Pruebas\Cursors\aero_link_im.cur | image | |
MD5:EB7BDB524F8D2DF5EE518F09E74BC915 | SHA256:C0A68DD5BF81DA430F18E658AA83A4D7FA544F71B927438DA1C9424EEF6A156A | |||
| 6648 | WinRAR.exe | C:\Users\admin\Desktop\Pruebas\Cursors\aero_nesw_l.cur | image | |
MD5:94AF75728CB0E587EB63A9FA20A7731A | SHA256:FB59C5F1B02CCB8DFD0CAD9F1DDE148D43F998D24C170FB25D3C8645E8333B8C | |||
| 6648 | WinRAR.exe | C:\Users\admin\Desktop\Pruebas\Cursors\aero_move_xl.cur | image | |
MD5:D15C6E4FB162CE0A0135E0090189BC5D | SHA256:3B98BC63B042047ECE450C86C89B2D54005690DBFC95B33C3BA028FECFE0EA8E | |||
| 6648 | WinRAR.exe | C:\Users\admin\Desktop\Pruebas\Cursors\aero_link_il.cur | image | |
MD5:5A0B467C743F191328A0E89BE34216B7 | SHA256:60B9BE4867B547D57AFA8B1856FAB95A55F7C246FFD8578CEC811287F14912EC | |||
| 6648 | WinRAR.exe | C:\Users\admin\Desktop\Pruebas\rnr20.dll | executable | |
MD5:B7EE4EA3A902F9D6B45C3DAA17952555 | SHA256:84E206B915F5BF1CB79A336B659B7550373AC621A1EE0F9E20D8B074D024F5E6 | |||
| 6648 | WinRAR.exe | C:\Users\admin\Desktop\Pruebas\scrobj.dll | executable | |
MD5:3BAC5E5C39B9787E3672ACBFABE438D1 | SHA256:164EA0913EF910084147CAB550C12B8F12C710A3F1BADF4A26C6691517A031C4 | |||
| 6648 | WinRAR.exe | C:\Users\admin\Desktop\Pruebas\pnpmem.sys | executable | |
MD5:2769F200292C0F941A10BD60C33EA4A6 | SHA256:B8345C32585C45E6248D7194B1071F2B8617718E7C9B270AAF44C132D029DB4C | |||
| 6648 | WinRAR.exe | C:\Users\admin\Desktop\Pruebas\RpcRtRemote.dll | executable | |
MD5:9A6998EBD24026A139567EE52E76AE34 | SHA256:B893B3C7DA30429015B506E42E905288CE8D1A95B2B211F56441CBC11D09D47A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
25
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.48.23.166:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2764 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6516 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6516 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 23.209.209.135:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4832 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 23.48.23.166:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2764 | svchost.exe | 40.126.31.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2764 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
6516 | SIHClient.exe | 4.245.163.56:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |