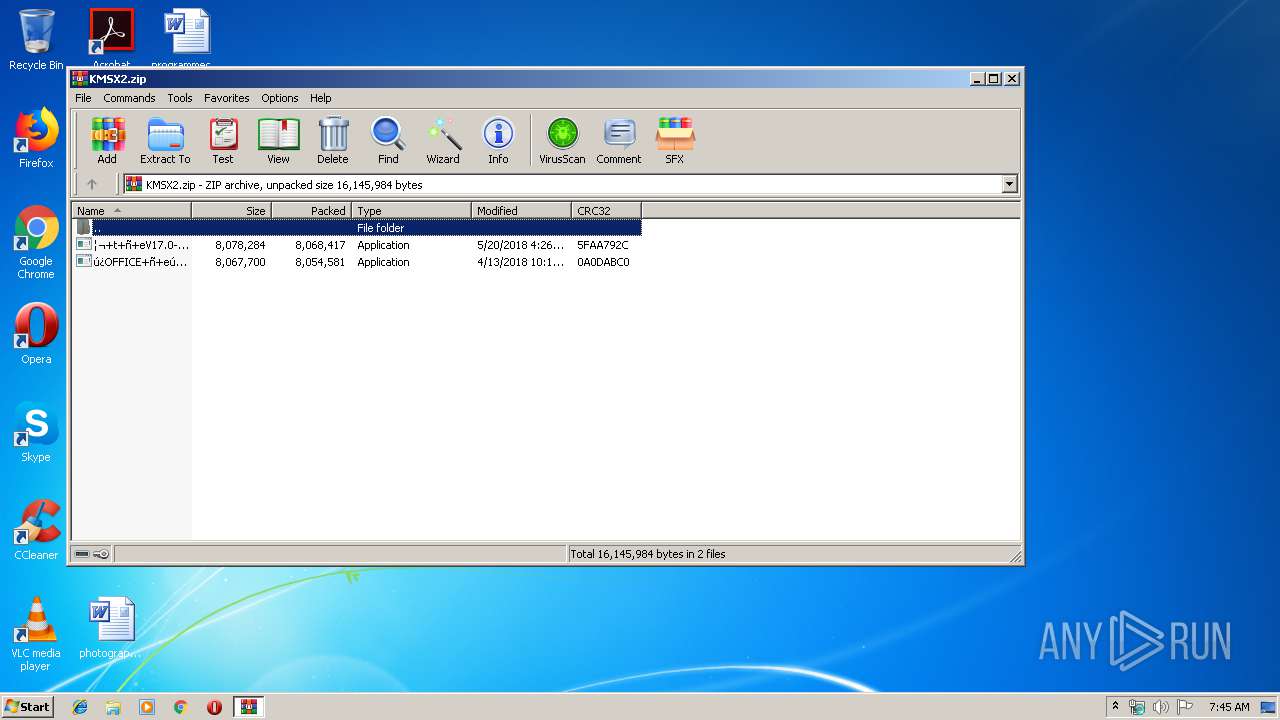
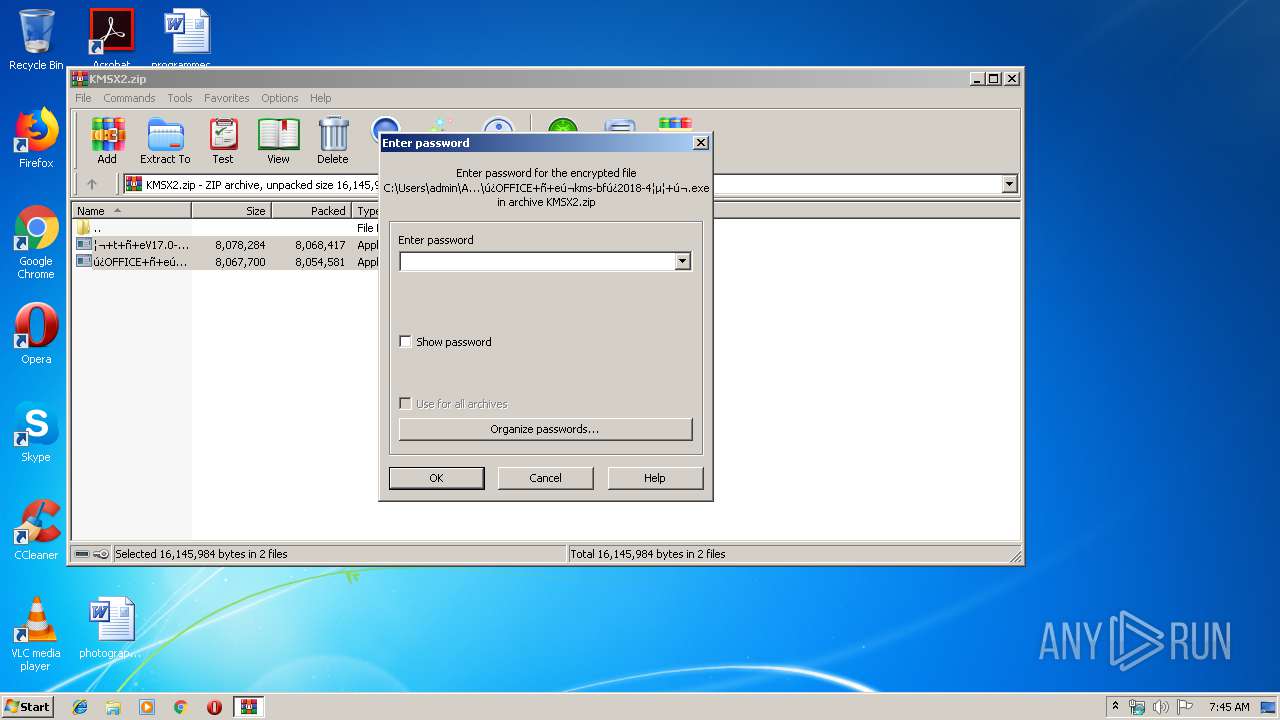
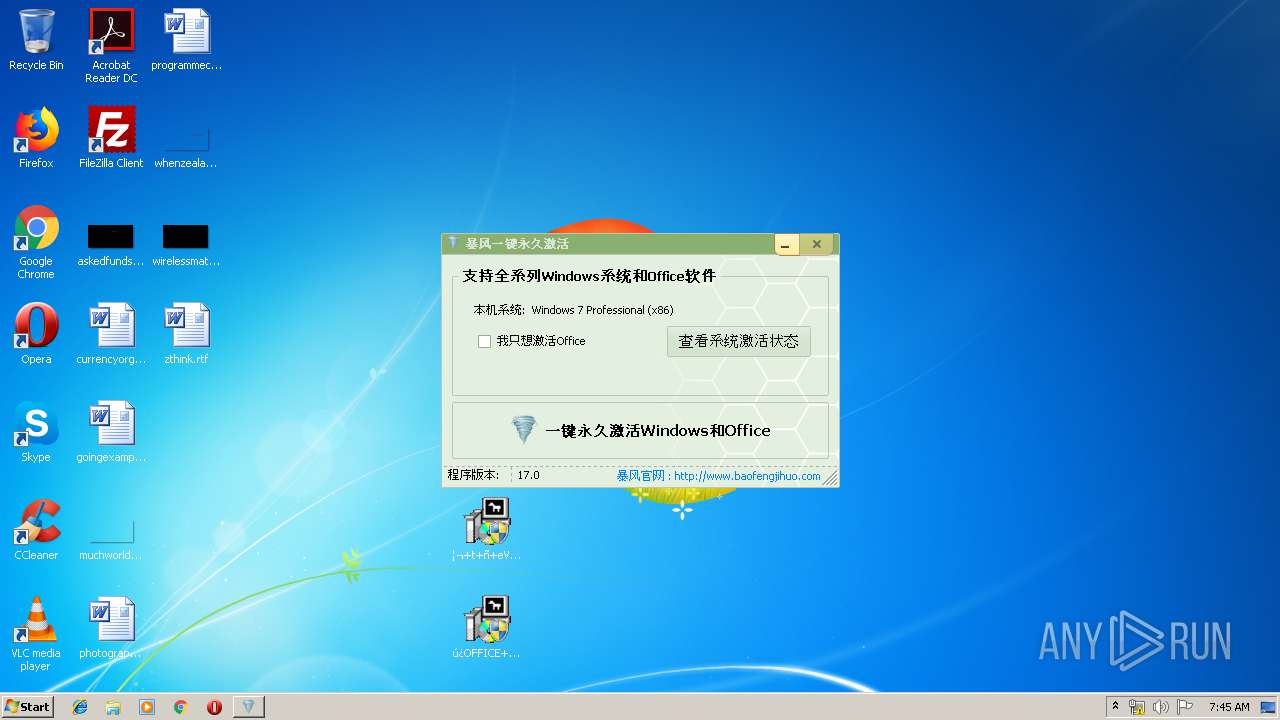
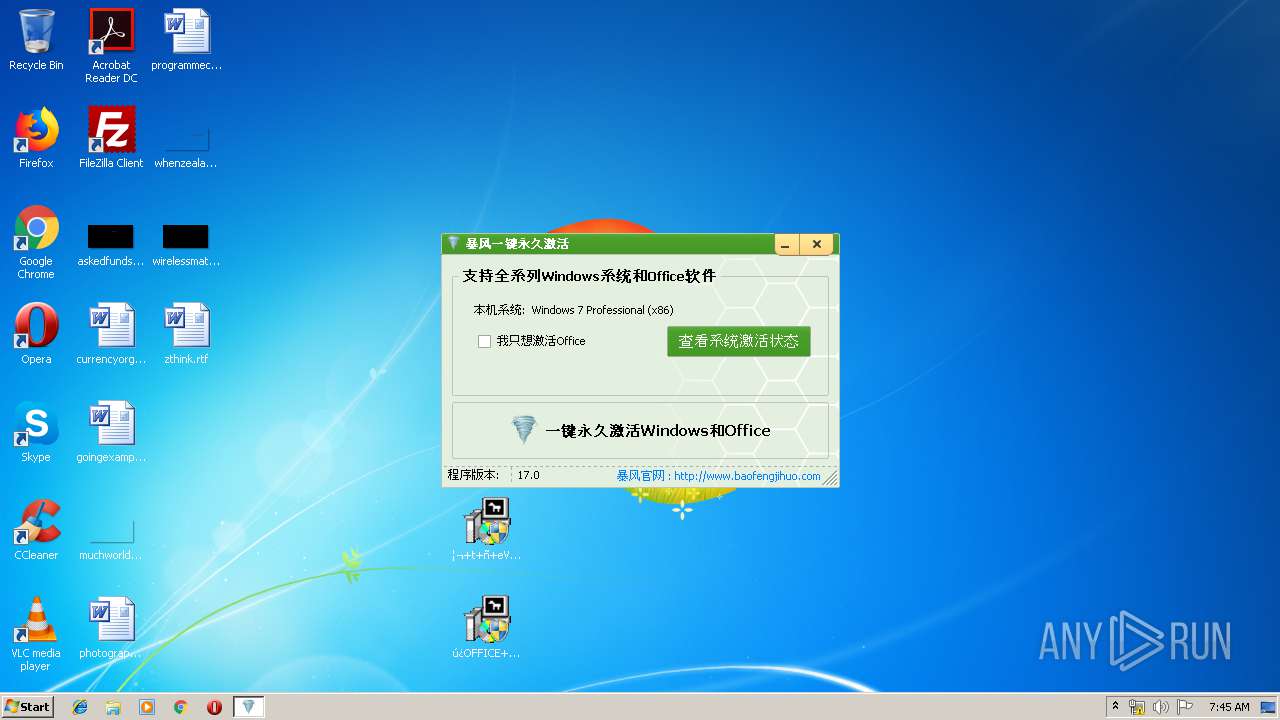
| File name: | KMSX2.zip |
| Full analysis: | https://app.any.run/tasks/9b879911-8f21-40aa-bb64-96a6e0edb736 |
| Verdict: | Malicious activity |
| Analysis date: | July 18, 2019, 06:44:34 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | ACD20E9E26C18B888A09A703220CAF72 |
| SHA1: | EFB3895CD3B9BB8D91FBABA5954DE5E9A92E50B2 |
| SHA256: | B366F923B9ACC9D80DE8B075F21EA4AB60333DDAE3EB22F9115A4BC7342A8166 |
| SSDEEP: | 393216:6J6XfBqGh2okF4tkRa9MTCMQyfpGeoEnTw8Ye1C2MIbHTISa:w4f9co04tkVCMEhETwS11M4zO |
MALICIOUS
Application was dropped or rewritten from another process
- ¦¬+t+ñ+eV17.0-2019-6-22¦µ¦+.exe (PID: 2232)
- ¦¬+t+ñ+eV17.0-2019-6-22¦µ¦+.exe (PID: 452)
- ns4BAE.tmp (PID: 3516)
- ns4D07.tmp (PID: 2648)
- ns56EB.tmp (PID: 2828)
- ns5863.tmp (PID: 1828)
- ns59FA.tmp (PID: 2284)
- ns5B91.tmp (PID: 2448)
- ns5C8C.tmp (PID: 3404)
- ns5D78.tmp (PID: 2704)
- 7z.exe (PID: 2932)
- 7z.exe (PID: 3204)
- 7z.exe (PID: 4004)
- ns5F0F.tmp (PID: 3616)
- 7z.exe (PID: 3360)
- 7z.exe (PID: 3412)
- 7z.exe (PID: 3052)
- 7z.exe (PID: 3368)
- 7z.exe (PID: 3052)
- 7z.exe (PID: 3368)
- KMSpico1.exe (PID: 792)
- SppExtComObjPatcher.exe (PID: 3580)
- ú¿OFFICE+ñ+eú¬kms-bfú¿2018-4¦µ¦+ú¬.exe (PID: 2372)
- ú¿OFFICE+ñ+eú¬kms-bfú¿2018-4¦µ¦+ú¬.exe (PID: 2836)
- 7z.exe (PID: 3372)
- KMSService.exe (PID: 2976)
- 7z.exe (PID: 3144)
- 7z.exe (PID: 4000)
- nsA9AC.tmp (PID: 2492)
- KMSpico1.exe (PID: 3096)
- 7z.exe (PID: 3336)
- 7z.exe (PID: 2736)
- nsAC7D.tmp (PID: 3768)
- 7z.exe (PID: 3796)
- nsAB05.tmp (PID: 2720)
- nsAD69.tmp (PID: 3308)
- nsB358.tmp (PID: 2288)
- 7z.exe (PID: 3012)
- nsB3C7.tmp (PID: 3280)
- 7z.exe (PID: 452)
- ú¿OFFICE+ñ+eú¬kms-bfú¿2018-4¦µ¦+ú¬.exe (PID: 2392)
- ú¿OFFICE+ñ+eú¬kms-bfú¿2018-4¦µ¦+ú¬.exe (PID: 3308)
- nsE1D3.tmp (PID: 3576)
- 7z.exe (PID: 3716)
- nsAF2F.tmp (PID: 2380)
- nsB181.tmp (PID: 2536)
- nsB2DA.tmp (PID: 2628)
- 7z.exe (PID: 3544)
- nsE32C.tmp (PID: 3284)
- 7z.exe (PID: 2432)
- nsE418.tmp (PID: 4004)
- 7z.exe (PID: 3352)
- nsE92B.tmp (PID: 3300)
- nsE570.tmp (PID: 1468)
- KMSpico1.exe (PID: 3532)
- nsE6D9.tmp (PID: 2604)
- 7z.exe (PID: 3200)
- 7z.exe (PID: 2744)
- 7z.exe (PID: 3692)
- nsEA94.tmp (PID: 2216)
- 7z.exe (PID: 3312)
- nsEB70.tmp (PID: 2812)
- 7z.exe (PID: 3388)
- nsEC5B.tmp (PID: 3544)
- 7z.exe (PID: 1632)
- KMSService.exe (PID: 2292)
- SppExtComObjPatcher.exe (PID: 3668)
Loads dropped or rewritten executable
- ¦¬+t+ñ+eV17.0-2019-6-22¦µ¦+.exe (PID: 2232)
- 7z.exe (PID: 3052)
- 7z.exe (PID: 4004)
- 7z.exe (PID: 3052)
- 7z.exe (PID: 2932)
- 7z.exe (PID: 3204)
- 7z.exe (PID: 3360)
- OSPPSVC.EXE (PID: 2208)
- ú¿OFFICE+ñ+eú¬kms-bfú¿2018-4¦µ¦+ú¬.exe (PID: 2836)
- 7z.exe (PID: 3144)
- 7z.exe (PID: 3336)
- 7z.exe (PID: 4000)
- 7z.exe (PID: 2736)
- 7z.exe (PID: 3372)
- ú¿OFFICE+ñ+eú¬kms-bfú¿2018-4¦µ¦+ú¬.exe (PID: 2392)
- 7z.exe (PID: 3716)
- 7z.exe (PID: 452)
- 7z.exe (PID: 2432)
- 7z.exe (PID: 3352)
- 7z.exe (PID: 2744)
- 7z.exe (PID: 3200)
- 7z.exe (PID: 1632)
- OSPPSVC.EXE (PID: 2400)
Changes Image File Execution Options
- KMSpico1.exe (PID: 792)
- KMSpico1.exe (PID: 3532)
Loads the Task Scheduler COM API
- OSPPSVC.EXE (PID: 2208)
- OSPPSVC.EXE (PID: 2400)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3224)
- ¦¬+t+ñ+eV17.0-2019-6-22¦µ¦+.exe (PID: 2232)
- 7z.exe (PID: 3204)
- 7z.exe (PID: 3360)
- ú¿OFFICE+ñ+eú¬kms-bfú¿2018-4¦µ¦+ú¬.exe (PID: 2836)
- KMSpico1.exe (PID: 792)
- ú¿OFFICE+ñ+eú¬kms-bfú¿2018-4¦µ¦+ú¬.exe (PID: 2392)
- 7z.exe (PID: 3352)
- KMSpico1.exe (PID: 3532)
Starts application with an unusual extension
- ¦¬+t+ñ+eV17.0-2019-6-22¦µ¦+.exe (PID: 2232)
- ú¿OFFICE+ñ+eú¬kms-bfú¿2018-4¦µ¦+ú¬.exe (PID: 2836)
- ú¿OFFICE+ñ+eú¬kms-bfú¿2018-4¦µ¦+ú¬.exe (PID: 2392)
Creates files in the Windows directory
- 7z.exe (PID: 3204)
- KMSpico1.exe (PID: 792)
- KMSpico1.exe (PID: 3532)
Creates files in the user directory
- 7z.exe (PID: 3052)
- 7z.exe (PID: 2736)
- 7z.exe (PID: 2744)
Uses WMIC.EXE to obtain a system information
- KMSpico1.exe (PID: 792)
- KMSpico1.exe (PID: 3532)
Creates files in the program directory
- 7z.exe (PID: 3052)
- 7z.exe (PID: 452)
- 7z.exe (PID: 1632)
Uses NETSH.EXE for network configuration
- KMSpico1.exe (PID: 792)
- KMSpico1.exe (PID: 3532)
Executed as Windows Service
- KMSService.exe (PID: 2976)
- SppExtComObjPatcher.exe (PID: 3580)
- KMSService.exe (PID: 2292)
- SppExtComObjPatcher.exe (PID: 3668)
Executes scripts
- KMSpico1.exe (PID: 792)
- KMSpico1.exe (PID: 3532)
Removes files from Windows directory
- KMSpico1.exe (PID: 3532)
Uses TASKKILL.EXE to kill process
- KMSpico1.exe (PID: 3532)
INFO
Manual execution by user
- ¦¬+t+ñ+eV17.0-2019-6-22¦µ¦+.exe (PID: 2232)
- ¦¬+t+ñ+eV17.0-2019-6-22¦µ¦+.exe (PID: 452)
- ú¿OFFICE+ñ+eú¬kms-bfú¿2018-4¦µ¦+ú¬.exe (PID: 2836)
- ú¿OFFICE+ñ+eú¬kms-bfú¿2018-4¦µ¦+ú¬.exe (PID: 2372)
- ú¿OFFICE+ñ+eú¬kms-bfú¿2018-4¦µ¦+ú¬.exe (PID: 2392)
- ú¿OFFICE+ñ+eú¬kms-bfú¿2018-4¦µ¦+ú¬.exe (PID: 3308)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2018:04:13 17:16:14 |
| ZipCRC: | 0x0a0dabc0 |
| ZipCompressedSize: | 8054581 |
| ZipUncompressedSize: | 8067700 |
| ZipFileName: | ??OFFICE???kms-bf??2018-4?汾??.exe |
Total processes
179
Monitored processes
89
Malicious processes
10
Suspicious processes
18
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 452 | "C:\Users\admin\Desktop\¦¬+t+ñ+eV17.0-2019-6-22¦µ¦+.exe" | C:\Users\admin\Desktop\¦¬+t+ñ+eV17.0-2019-6-22¦µ¦+.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 452 | "C:\Users\admin\AppData\Local\Temp\7z.exe" x -aoa -paabbccdd "C:\Users\admin\AppData\Local\Temp\Play6.dat" -o"C:\Program Files\Mozilla Firefox" | C:\Users\admin\AppData\Local\Temp\7z.exe | — | nsB3C7.tmp | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: HIGH Description: 7-Zip Console Exit code: 0 Version: 16.02 Modules
| |||||||||||||||
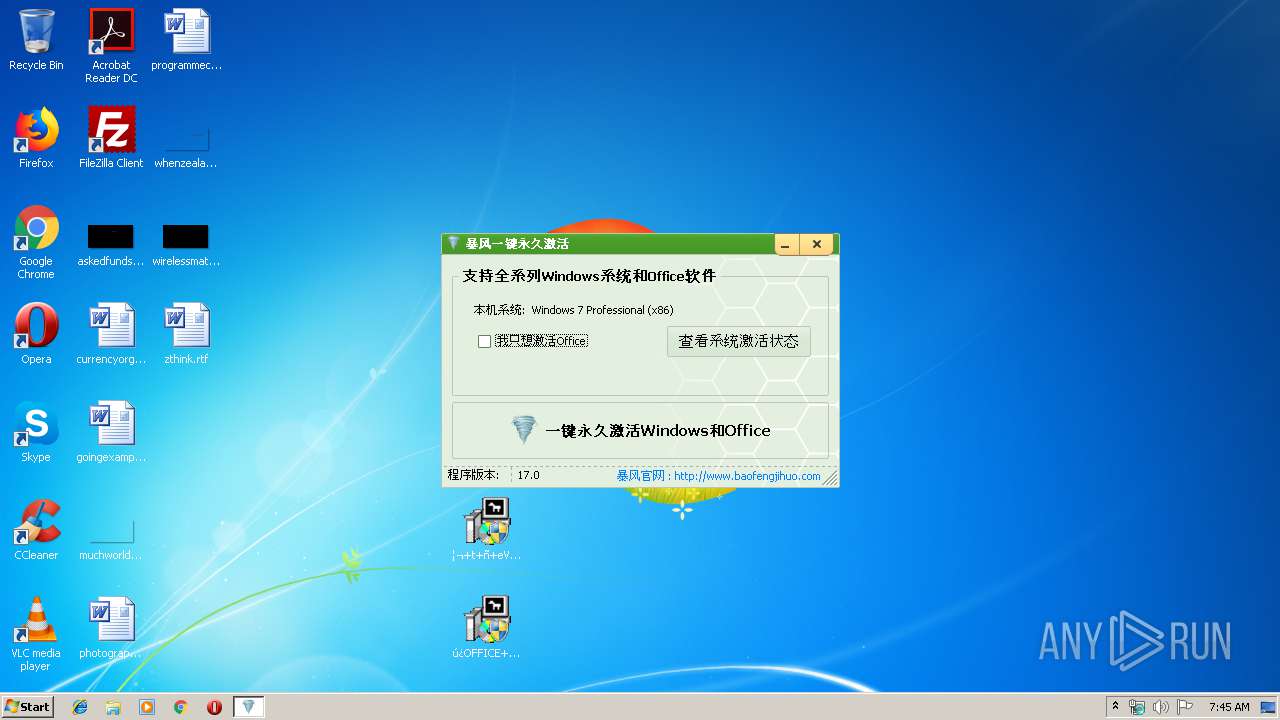
| 792 | C:\Users\admin\AppData\Local\Temp\KMSpico1.exe | C:\Users\admin\AppData\Local\Temp\KMSpico1.exe | ¦¬+t+ñ+eV17.0-2019-6-22¦µ¦+.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: 暴风一键激活工具 Exit code: 0 Version: 16.0.0.0 Modules
| |||||||||||||||
| 1468 | "C:\Users\admin\AppData\Local\Temp\nsiE127.tmp\nsE570.tmp" "C:\Users\admin\AppData\Local\Temp\7z.exe" x -aoa -paabbccdd "C:\Users\admin\AppData\Local\Temp\Play1.dat" -o"C:\Users\admin\AppData\Local" | C:\Users\admin\AppData\Local\Temp\nsiE127.tmp\nsE570.tmp | — | ú¿OFFICE+ñ+eú¬kms-bfú¿2018-4¦µ¦+ú¬.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1632 | "C:\Users\admin\AppData\Local\Temp\7z.exe" x -aoa -paabbccdd "C:\Users\admin\AppData\Local\Temp\Play6.dat" -o"C:\Program Files\Mozilla Firefox" | C:\Users\admin\AppData\Local\Temp\7z.exe | — | nsEC5B.tmp | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: HIGH Description: 7-Zip Console Exit code: 0 Version: 16.02 Modules
| |||||||||||||||
| 1828 | "C:\Users\admin\AppData\Local\Temp\nsd4B20.tmp\ns5863.tmp" "C:\Users\admin\AppData\Local\Temp\7z.exe" x -aoa -paabbccdd "C:\Users\admin\AppData\Local\Temp\Play1.dat" -o"C:\Users\admin\AppData\Local" | C:\Users\admin\AppData\Local\Temp\nsd4B20.tmp\ns5863.tmp | — | ¦¬+t+ñ+eV17.0-2019-6-22¦µ¦+.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1952 | wmic path SoftwareLicensingService where version='6.1.7601.17514' call SetVLActivationTypeEnabled 2 | C:\Windows\System32\Wbem\wmic.exe | — | KMSpico1.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 44028 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2016 | wmic path SoftwareLicensingService where version='6.1.7601.17514' call SetVLActivationTypeEnabled 2 | C:\Windows\System32\Wbem\wmic.exe | — | KMSpico1.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 44028 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2208 | "C:\Program Files\Common Files\Microsoft Shared\OfficeSoftwareProtectionPlatform\OSPPSVC.EXE" | C:\Program Files\Common Files\Microsoft Shared\OfficeSoftwareProtectionPlatform\OSPPSVC.EXE | — | SppExtComObjPatcher.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Office Software Protection Platform Service Exit code: 0 Version: 14.0.0370.400 (longhorn(wmbla).090811-1833) Modules
| |||||||||||||||
| 2216 | "C:\Users\admin\AppData\Local\Temp\nsiE127.tmp\nsEA94.tmp" "C:\Users\admin\AppData\Local\Temp\7z.exe" x -aoa -paabbccdd "C:\Users\admin\AppData\Local\Temp\Play3.dat" -o"" | C:\Users\admin\AppData\Local\Temp\nsiE127.tmp\nsEA94.tmp | — | ú¿OFFICE+ñ+eú¬kms-bfú¿2018-4¦µ¦+ú¬.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 7 Modules
| |||||||||||||||
Total events
2 239
Read events
1 944
Write events
295
Delete events
0
Modification events
| (PID) Process: | (3224) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3224) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3224) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\70\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3224) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\KMSX2.zip | |||
| (PID) Process: | (3224) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3224) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3224) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3224) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3224) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (3224) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
Executable files
51
Suspicious files
36
Text files
27
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4004 | 7z.exe | C:\Users\admin\AppData\Local\Temp\Play32.dat.tmp | — | |
MD5:— | SHA256:— | |||
| 2232 | ¦¬+t+ñ+eV17.0-2019-6-22¦µ¦+.exe | C:\Users\admin\AppData\Local\Temp\nsd4B20.tmp\ns4D07.tmp | — | |
MD5:— | SHA256:— | |||
| 3224 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3224.30988\¦¬+t+ñ+eV17.0-2019-6-22¦µ¦+.exe | executable | |
MD5:— | SHA256:— | |||
| 2232 | ¦¬+t+ñ+eV17.0-2019-6-22¦µ¦+.exe | C:\Users\admin\AppData\Local\Temp\nsd4B20.tmp\ns56EB.tmp | — | |
MD5:— | SHA256:— | |||
| 3224 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3224.30988\ú¿OFFICE+ñ+eú¬kms-bfú¿2018-4¦µ¦+ú¬.exe | executable | |
MD5:— | SHA256:— | |||
| 2232 | ¦¬+t+ñ+eV17.0-2019-6-22¦µ¦+.exe | C:\Users\admin\AppData\Local\Temp\Play1.dat | compressed | |
MD5:— | SHA256:— | |||
| 2232 | ¦¬+t+ñ+eV17.0-2019-6-22¦µ¦+.exe | C:\Users\admin\AppData\Local\Temp\Play32.dat | compressed | |
MD5:— | SHA256:— | |||
| 2232 | ¦¬+t+ñ+eV17.0-2019-6-22¦µ¦+.exe | C:\Users\admin\AppData\Local\Temp\Play2.dat | compressed | |
MD5:713C7B3AEA6167F69457C8C9FE1CBC93 | SHA256:D6D75387580B2FB3E0C2A7488F2F140CC6C69FDC31C6E05D857DBB355AA56B67 | |||
| 2232 | ¦¬+t+ñ+eV17.0-2019-6-22¦µ¦+.exe | C:\Users\admin\AppData\Local\Temp\Play5.dat | compressed | |
MD5:86CBDC67B7F520C41DF8193507CDAF43 | SHA256:38C0BEA6DCA4E6CDB2517CDE831140758E9C261EC4C05BE9321ADAE7BF19F45D | |||
| 2232 | ¦¬+t+ñ+eV17.0-2019-6-22¦µ¦+.exe | C:\Users\admin\AppData\Local\Temp\Play4.dat | compressed | |
MD5:C6B59214C6ABC60BE59659756F154422 | SHA256:4CDB3149B03682EB455CA02673B0D9963E72564F57203FD930C99F7A209D54B2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
3
DNS requests
1
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2232 | ¦¬+t+ñ+eV17.0-2019-6-22¦µ¦+.exe | GET | — | 42.51.38.18:80 | http://win3.zhfcxd.com/bs4-200-4.mp3 | CN | — | — | suspicious |
2392 | ú¿OFFICE+ñ+eú¬kms-bfú¿2018-4¦µ¦+ú¬.exe | GET | — | 42.51.38.18:80 | http://win3.zhfcxd.com/bs4-300-4.mp3 | CN | — | — | suspicious |
2836 | ú¿OFFICE+ñ+eú¬kms-bfú¿2018-4¦µ¦+ú¬.exe | GET | — | 42.51.38.18:80 | http://win3.zhfcxd.com/bs4-300-4.mp3 | CN | — | — | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2232 | ¦¬+t+ñ+eV17.0-2019-6-22¦µ¦+.exe | 42.51.38.18:80 | win3.zhfcxd.com | Henan Telcom Union Technology Co., LTD | CN | suspicious |
2836 | ú¿OFFICE+ñ+eú¬kms-bfú¿2018-4¦µ¦+ú¬.exe | 42.51.38.18:80 | win3.zhfcxd.com | Henan Telcom Union Technology Co., LTD | CN | suspicious |
2392 | ú¿OFFICE+ñ+eú¬kms-bfú¿2018-4¦µ¦+ú¬.exe | 42.51.38.18:80 | win3.zhfcxd.com | Henan Telcom Union Technology Co., LTD | CN | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
win3.zhfcxd.com |
| suspicious |
Threats
2 ETPRO signatures available at the full report