| URL: | amazoon.online |
| Full analysis: | https://app.any.run/tasks/08fde849-ead1-4743-bf6a-d75fbf6a6eaf |
| Verdict: | Malicious activity |
| Analysis date: | April 22, 2024, 18:54:12 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 3D4832E702C01040BB8D736A696D74D3 |
| SHA1: | 7F57162378A0E1972B4F3F8C577CA0E11439ED73 |
| SHA256: | B3466C161F4E92D6CA5654A4422196CDD7529349EBB331E73F4D65B2E84C9C4C |
| SSDEEP: | 3:h4LLpAn:+A |
MALICIOUS
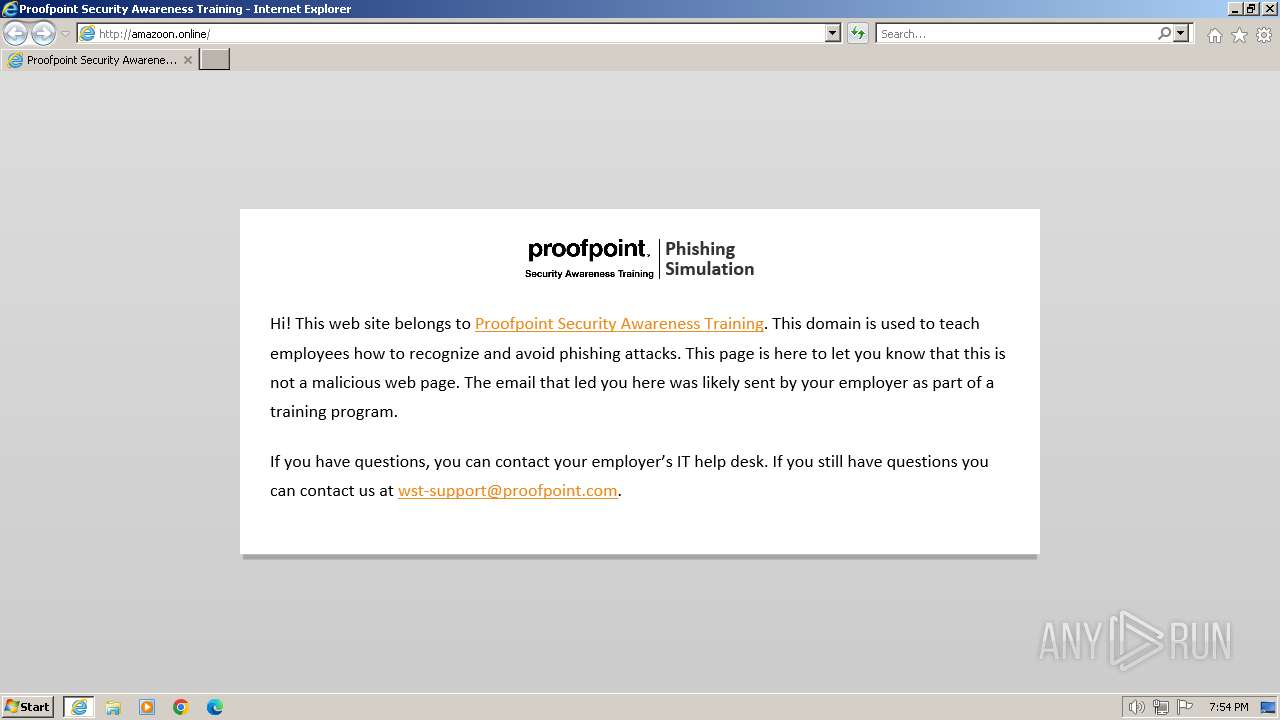
PHISHING has been detected (SURICATA)
- iexplore.exe (PID: 2928)
SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- iexplore.exe (PID: 2032)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
37
Monitored processes
2
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2032 | "C:\Program Files\Internet Explorer\iexplore.exe" "amazoon.online" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2928 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2032 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
10 346
Read events
10 209
Write events
100
Delete events
37
Modification events
| (PID) Process: | (2032) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (2032) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (2032) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31102182 | |||
| (PID) Process: | (2032) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (2032) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31102182 | |||
| (PID) Process: | (2032) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2032) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2032) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2032) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2032) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
6
Text files
10
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2928 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\56MA6H7L.htm | html | |
MD5:CF0AE9D292AC3C2D9C565AC15BCACC77 | SHA256:C0623A98220D6586761A01BC71F85279D1893F40E75400864B0F9048BC2B0BFE | |||
| 2928 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\psat_logo[1].png | image | |
MD5:C510B40B57C8DE8C431E25E89EAC656F | SHA256:313AC720267E0D852F0B17055B68087B1D1CC4CE24F075864D4AB57A7F83B199 | |||
| 2928 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\DOMStore\DOTBATAV\amazoon[1].xml | text | |
MD5:C1DDEA3EF6BBEF3E7060A1A9AD89E4C5 | SHA256:B71E4D17274636B97179BA2D97C742735B6510EB54F22893D3A2DAFF2CEB28DB | |||
| 2928 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\all[1].js | text | |
MD5:097F74FC8F861ECE148262A652AB806A | SHA256:39B4614F1C87CF0CFD1BC3375642E95825CB2018E0318A36AAD766DDB5A8CBE9 | |||
| 2032 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\favicon[1].ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 2928 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\jquery.min[1].js | text | |
MD5:8FC25E27D42774AEAE6EDBC0A18B72AA | SHA256:B294E973896F8F874E90A8EB1A8908AC790980D034C4C4BDF0FC3D37B8ABF682 | |||
| 2032 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | der | |
MD5:3C306EEF3600E13AB3F9294F5337836F | SHA256:BACA6039DB0F154DC0D7F628499010D6F447BCD6D13AEEA9B52C32A9A1945844 | |||
| 2032 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\VersionManager\versionlist.xml | xml | |
MD5:CBD0581678FA40F0EDCBC7C59E0CAD10 | SHA256:159BD4343F344A08F6AF3B716B6FA679859C1BD1D7030D26FF5EF0255B86E1D9 | |||
| 2032 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\VersionManager\ver4C14.tmp | xml | |
MD5:CBD0581678FA40F0EDCBC7C59E0CAD10 | SHA256:159BD4343F344A08F6AF3B716B6FA679859C1BD1D7030D26FF5EF0255B86E1D9 | |||
| 2032 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\favicon[1].ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
35
TCP/UDP connections
21
DNS requests
12
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2928 | iexplore.exe | GET | 200 | 44.213.150.88:80 | http://amazoon.online/assets/ajax/libs/jquery/1.11.0/jquery.min.js | unknown | — | — | unknown |
2928 | iexplore.exe | GET | 200 | 44.213.150.88:80 | http://amazoon.online/trace?id=infopage&msg=BrowserDetect%20-%20os_version%20%3D%206.1&correlation_id=undefined | unknown | — | — | unknown |
2928 | iexplore.exe | GET | 200 | 44.213.150.88:80 | http://amazoon.online/trace?id=infopage&msg=BrowserDetect%20-%20language%20%3D%20en-US&correlation_id=undefined | unknown | — | — | unknown |
2032 | iexplore.exe | GET | 200 | 44.213.150.88:80 | http://amazoon.online/favicon.ico | unknown | — | — | unknown |
2928 | iexplore.exe | GET | 200 | 44.213.150.88:80 | http://amazoon.online/ | unknown | — | — | unknown |
2928 | iexplore.exe | GET | 200 | 44.213.150.88:80 | http://amazoon.online/assets/psat_logo.png | unknown | — | — | unknown |
2928 | iexplore.exe | GET | 200 | 44.213.150.88:80 | http://amazoon.online/assets/all.js?g=infopage | unknown | — | — | unknown |
2928 | iexplore.exe | GET | 200 | 44.213.150.88:80 | http://amazoon.online/trace?id=infopage&msg=BrowserDetect%20-%20sessionStorage%20%3D%20true&correlation_id=undefined | unknown | — | — | unknown |
2928 | iexplore.exe | GET | 200 | 44.213.150.88:80 | http://amazoon.online/log?id=infopage&sev=1&msg='PluginDetect'%20is%20undefined&correlation_id=undefined | unknown | — | — | unknown |
2928 | iexplore.exe | GET | 200 | 44.213.150.88:80 | http://amazoon.online/trace?id=infopage&msg=Skipping%20java%20detection&correlation_id=undefined | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2928 | iexplore.exe | 44.213.150.88:80 | amazoon.online | AMAZON-AES | US | unknown |
2032 | iexplore.exe | 44.213.150.88:80 | amazoon.online | AMAZON-AES | US | unknown |
2032 | iexplore.exe | 184.30.150.107:443 | www.bing.com | Akamai International B.V. | CA | unknown |
2032 | iexplore.exe | 87.248.205.0:80 | ctldl.windowsupdate.com | LLNW | US | unknown |
2032 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
2032 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | EDGECAST | US | whitelisted |
1080 | svchost.exe | 87.248.205.0:80 | ctldl.windowsupdate.com | LLNW | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
amazoon.online |
| unknown |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2928 | iexplore.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Proofpoint Security Awareness Training |
— | — | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Proofpoint Security Awareness Training |