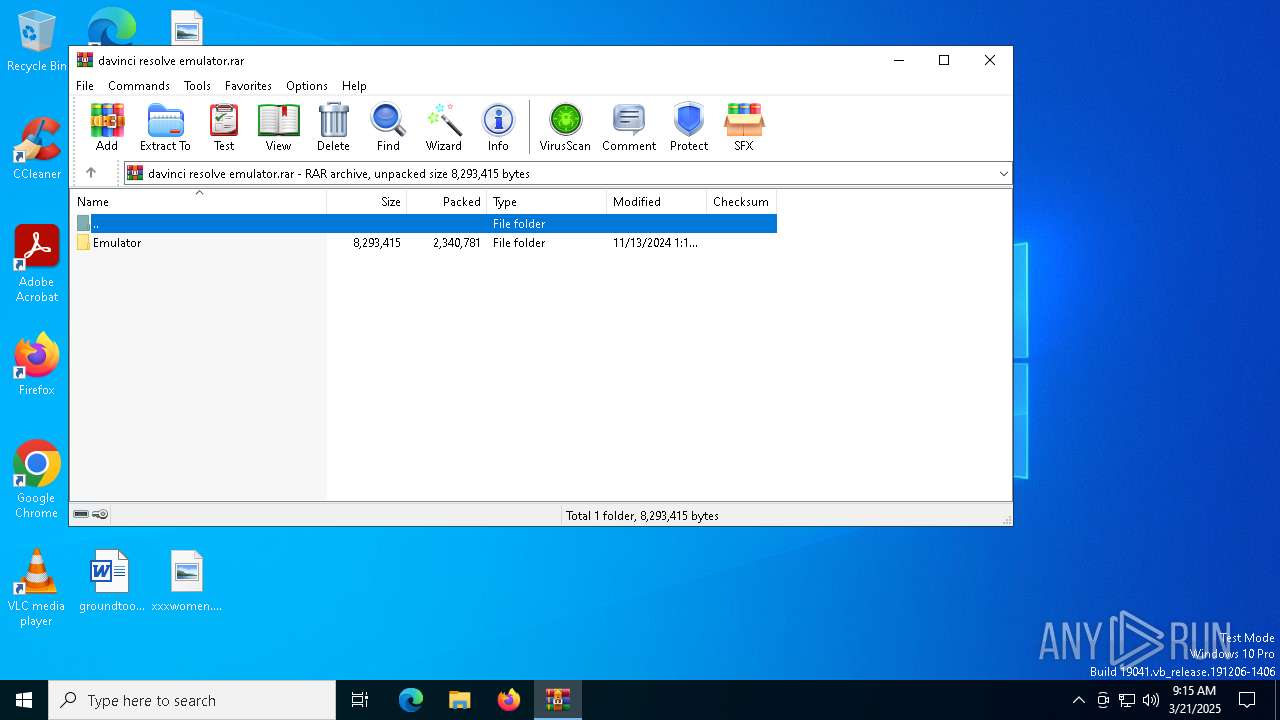
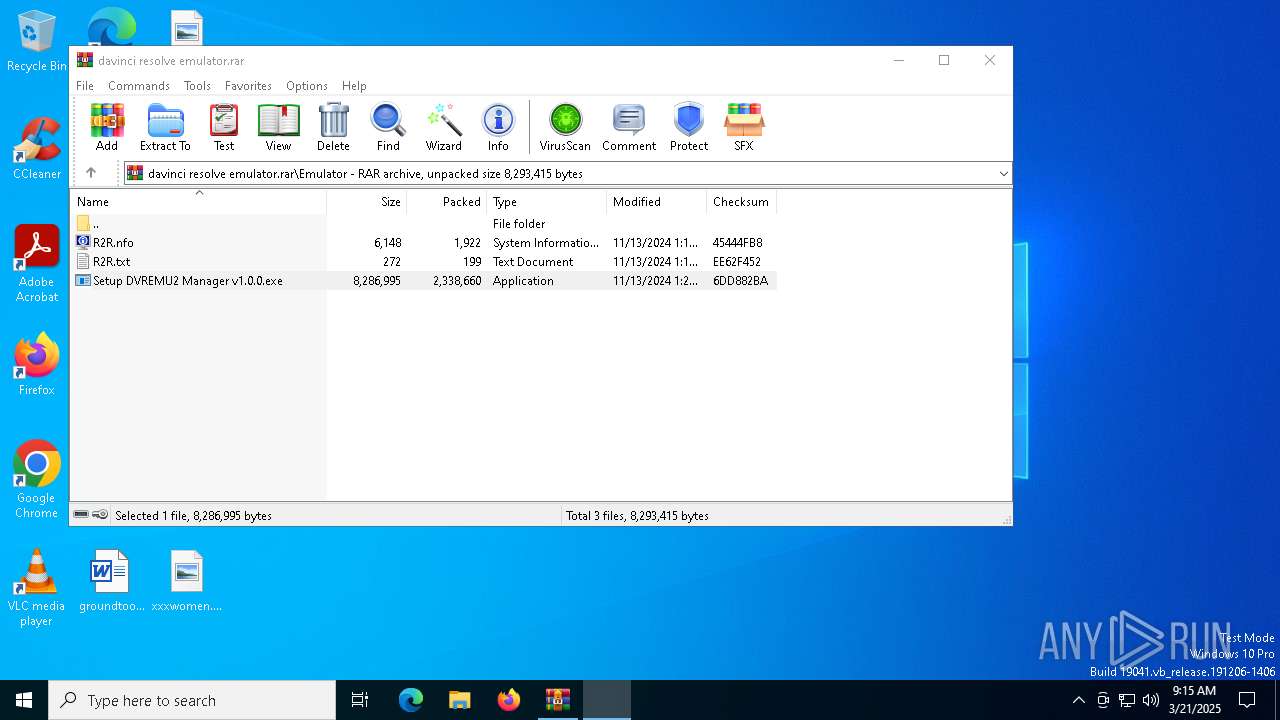
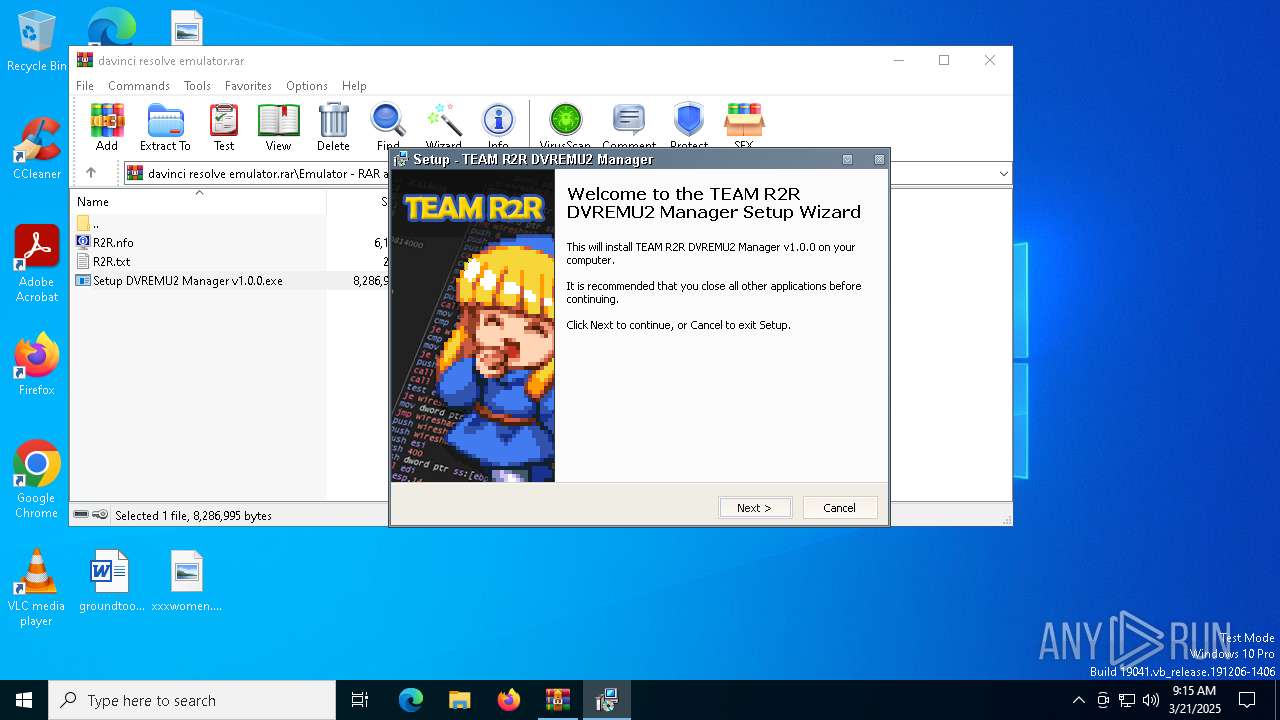
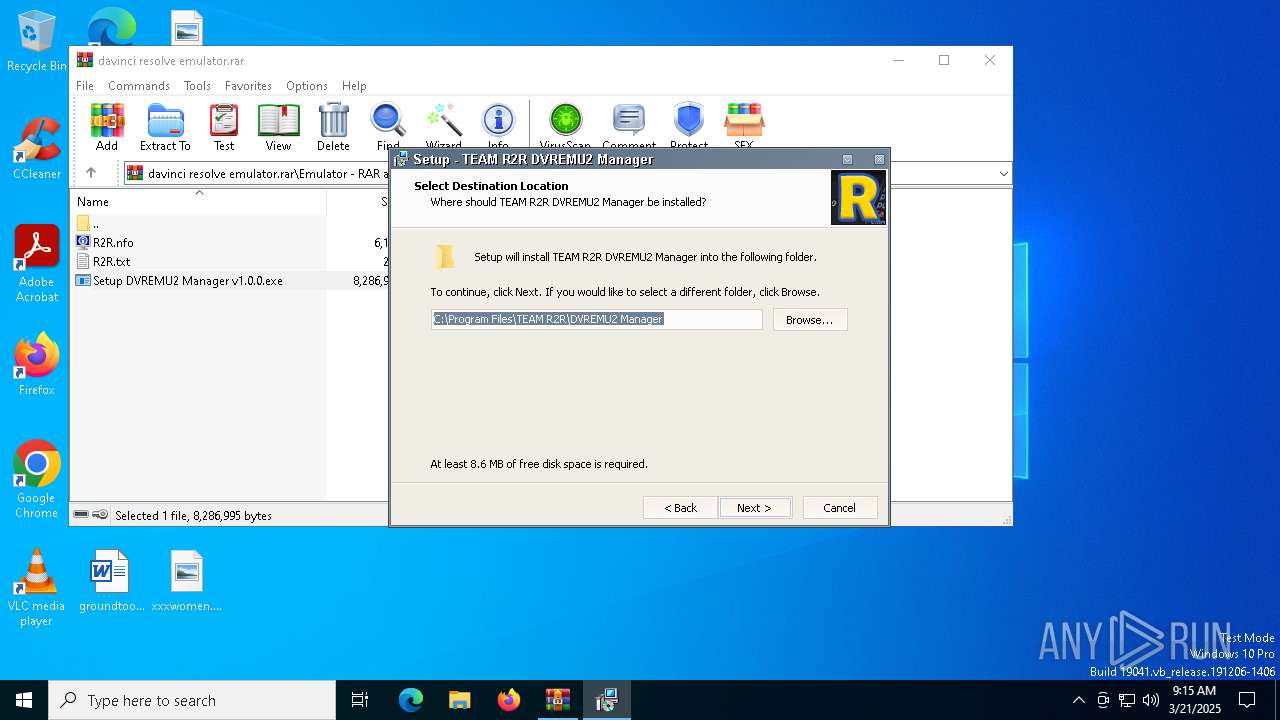
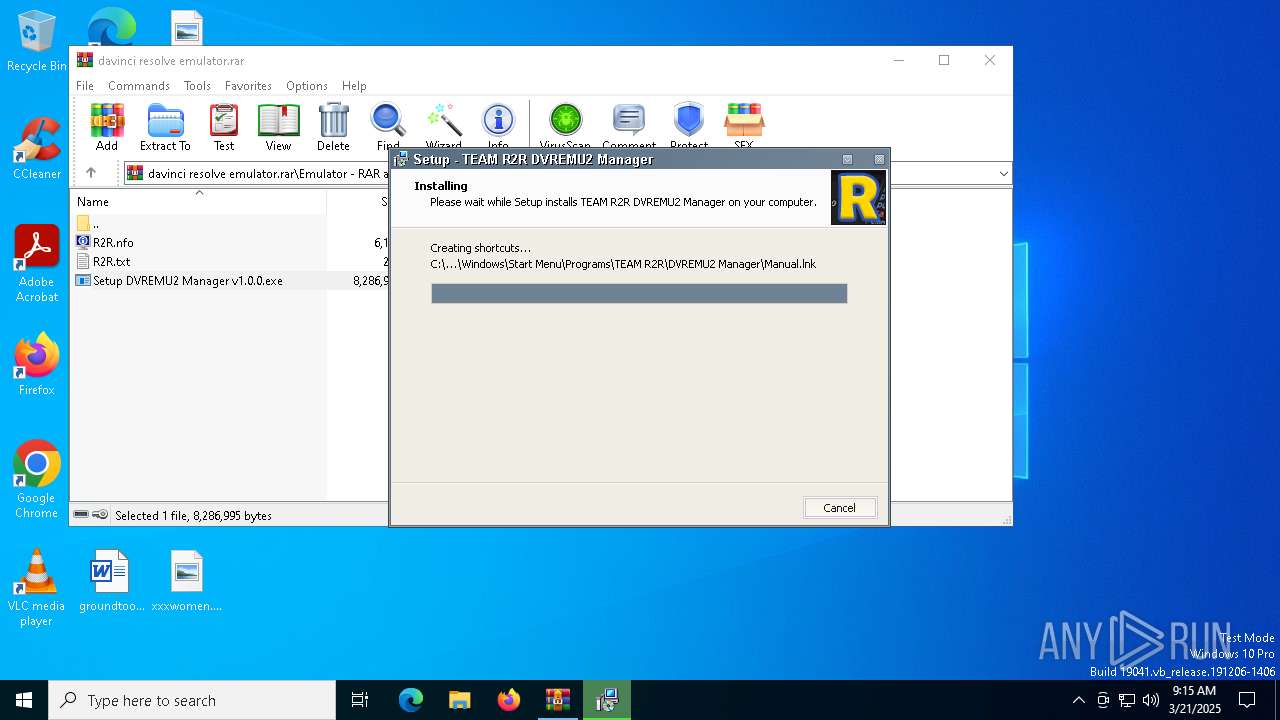
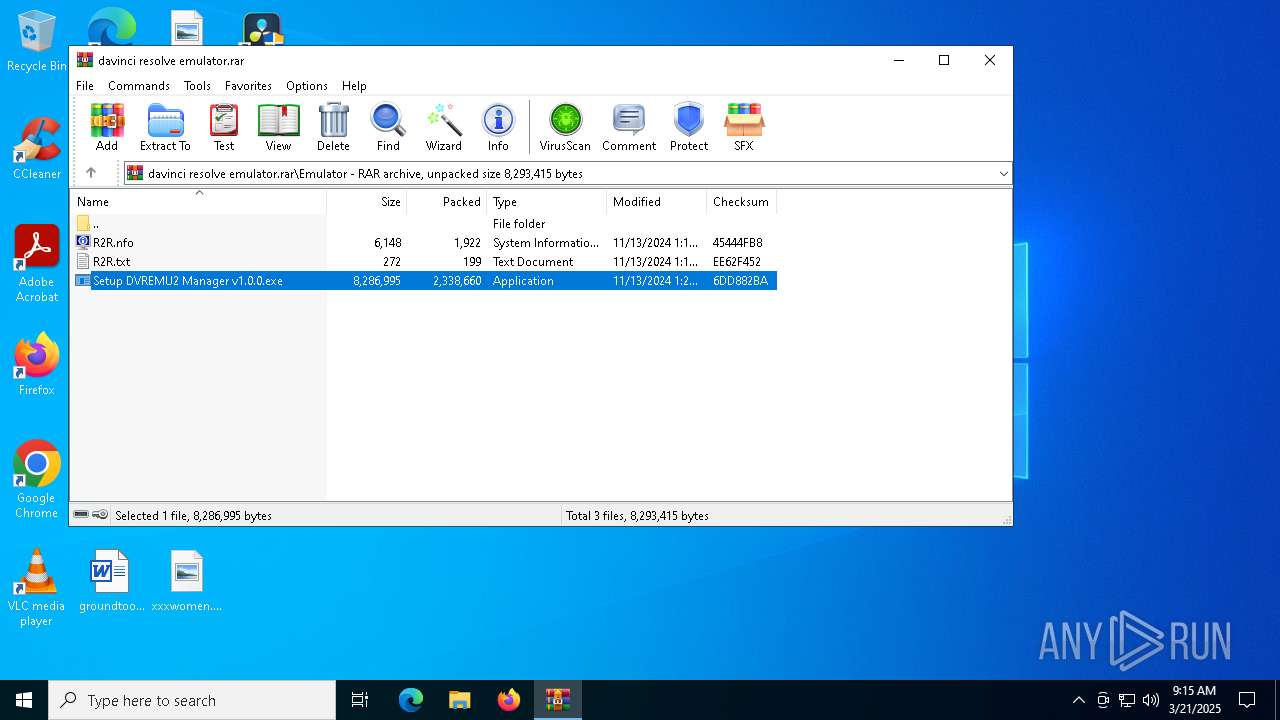
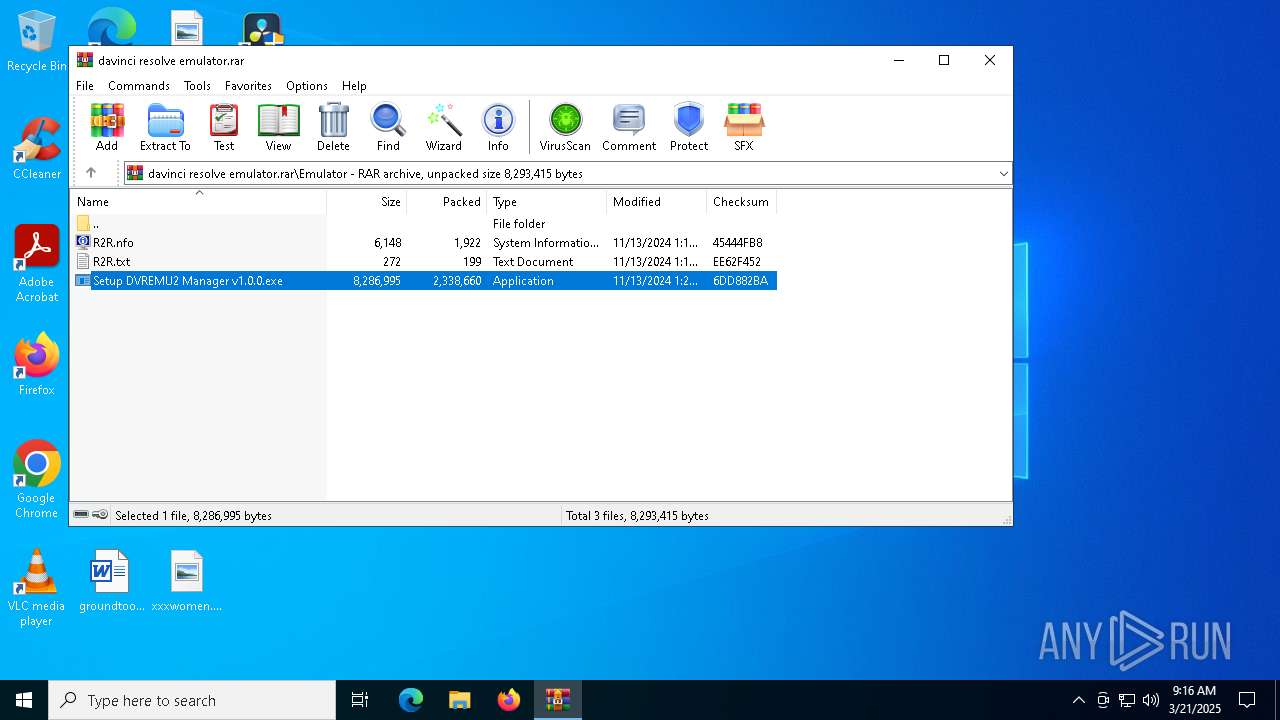
| File name: | davinci resolve emulator.rar |
| Full analysis: | https://app.any.run/tasks/740f3794-4d4d-45cb-844a-9f0fc34e65fa |
| Verdict: | Malicious activity |
| Analysis date: | March 21, 2025, 09:15:35 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 7FE027821EF93EF9E43AEAD8746944E4 |
| SHA1: | 2F60AAE76CEC85C21E765121E32A88177872D32A |
| SHA256: | B342E9BE7342CD3C5F40441DDAAC5D5620B4DEF753A06EB87450178B09853511 |
| SSDEEP: | 98304:Hm+Axl54+XZywe3Cyv3wegPInZ1HTRYJUPgSrI7i9IoRsZEGodU3x3iKNYn7bljC:G0P9Y |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 5072)
Executing a file with an untrusted certificate
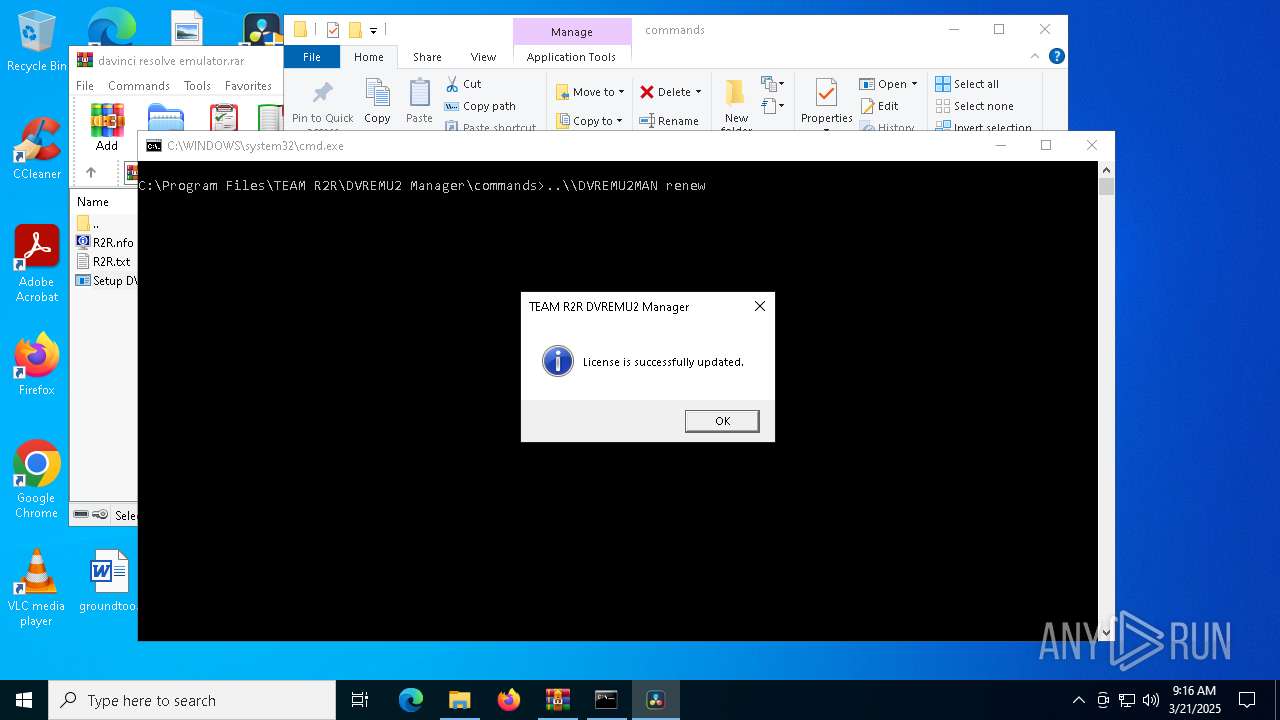
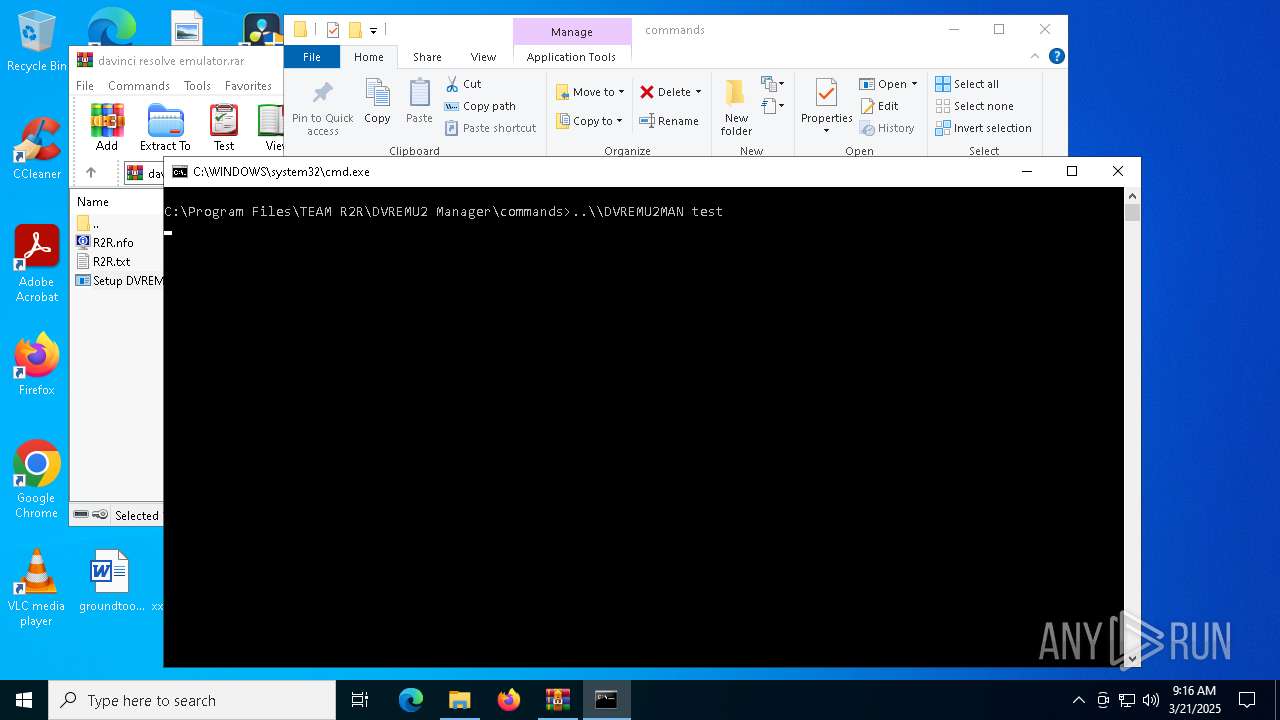
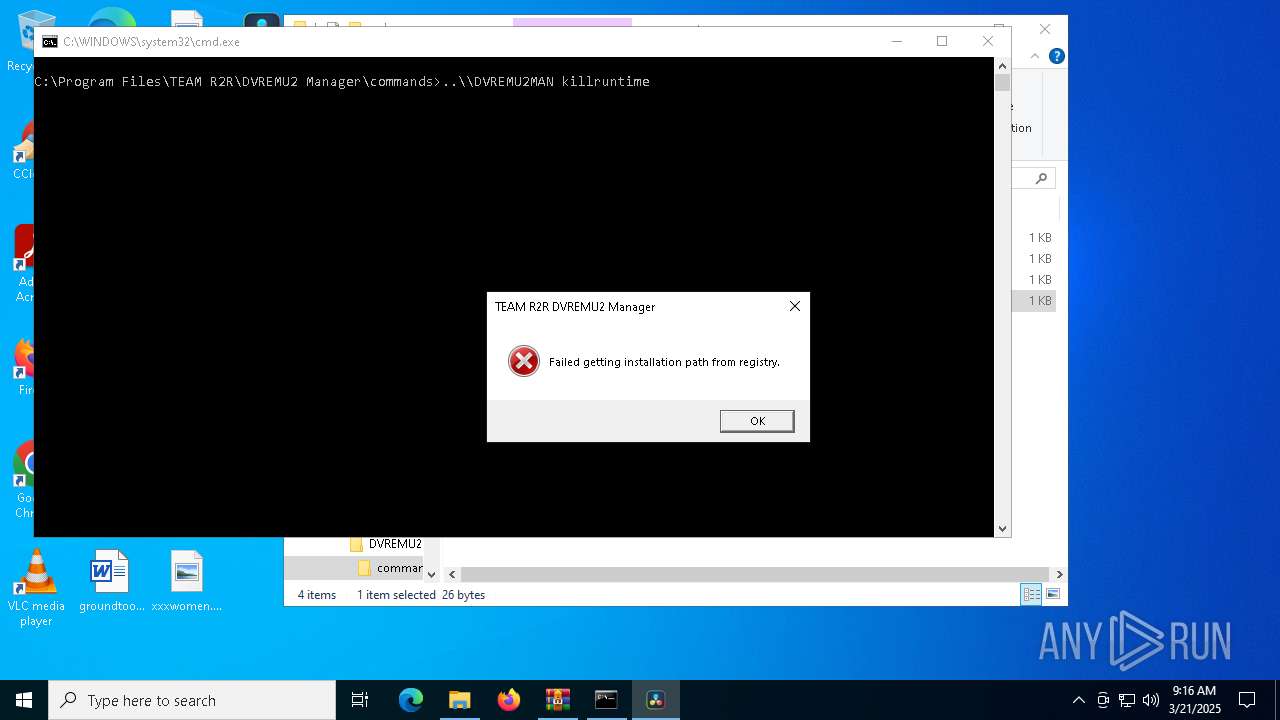
- DVREMU2MAN.exe (PID: 2148)
- DVREMU2MAN.exe (PID: 5544)
- DVREMU2MAN.exe (PID: 4428)
- DVREMU2MAN.exe (PID: 7600)
- DVREMU2MAN.exe (PID: 5936)
- DVREMU2MAN.exe (PID: 900)
- DVREMU2MAN.exe (PID: 6404)
- DVREMU2MAN.exe (PID: 5680)
- DVREMU2MAN.exe (PID: 2420)
- DVREMU2MAN.exe (PID: 7932)
- DVREMU2MAN.exe (PID: 3008)
- DVREMU2MAN.exe (PID: 5064)
- DVREMU2MAN.exe (PID: 5956)
- DVREMU2MAN.exe (PID: 3676)
- DVREMU2MAN.exe (PID: 6244)
- DVREMU2MAN.exe (PID: 7084)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 5072)
- Setup DVREMU2 Manager v1.0.0.tmp (PID: 7960)
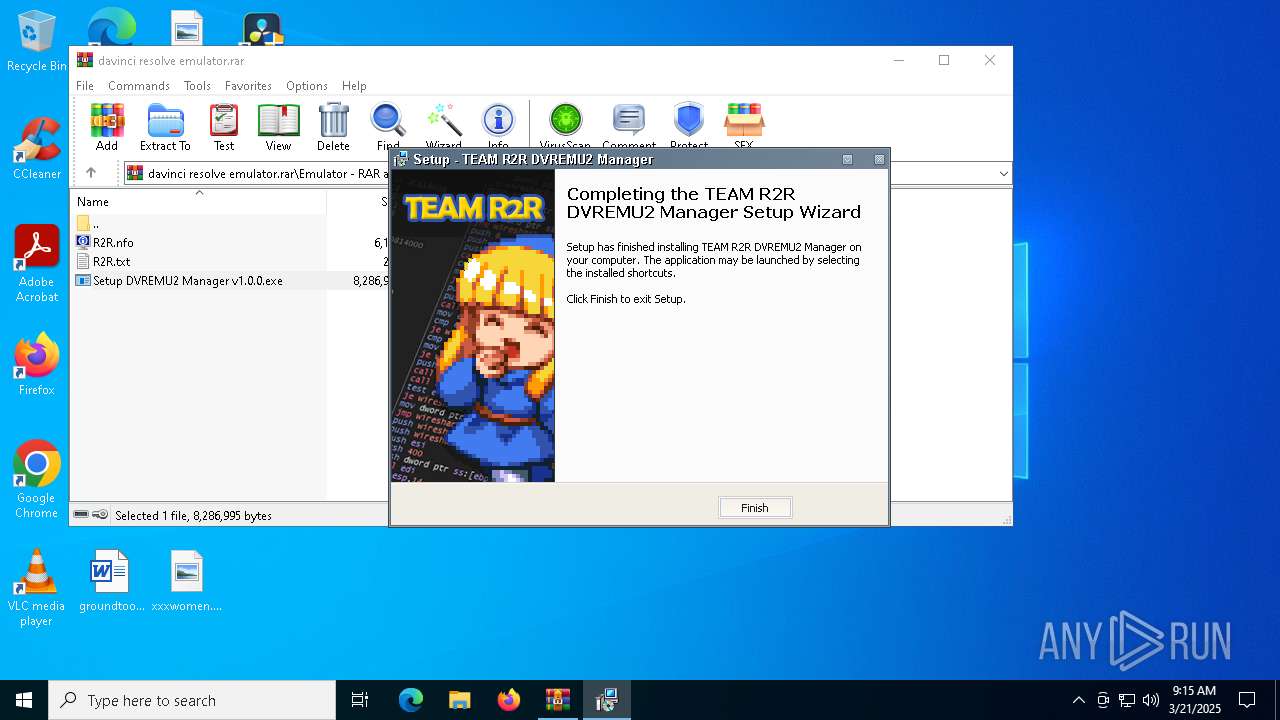
Executable content was dropped or overwritten
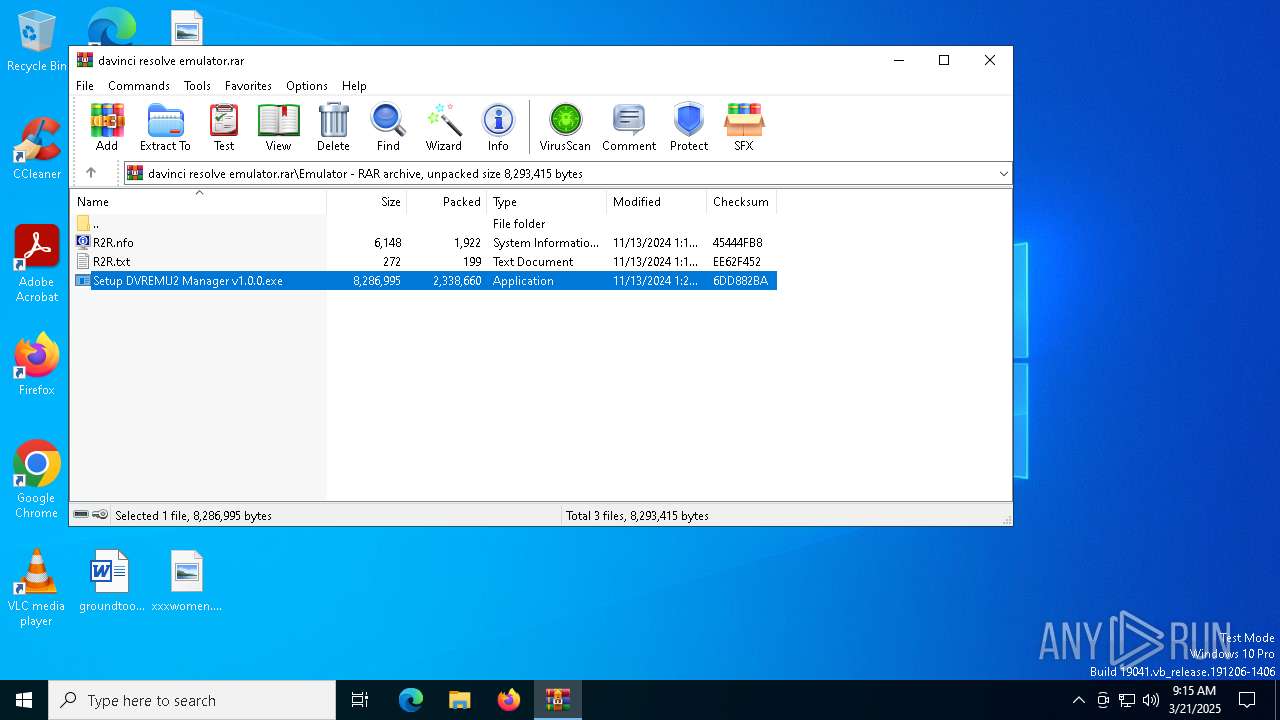
- Setup DVREMU2 Manager v1.0.0.exe (PID: 7800)
- Setup DVREMU2 Manager v1.0.0.tmp (PID: 7960)
- Setup DVREMU2 Manager v1.0.0.exe (PID: 7940)
Reads the Windows owner or organization settings
- Setup DVREMU2 Manager v1.0.0.tmp (PID: 7960)
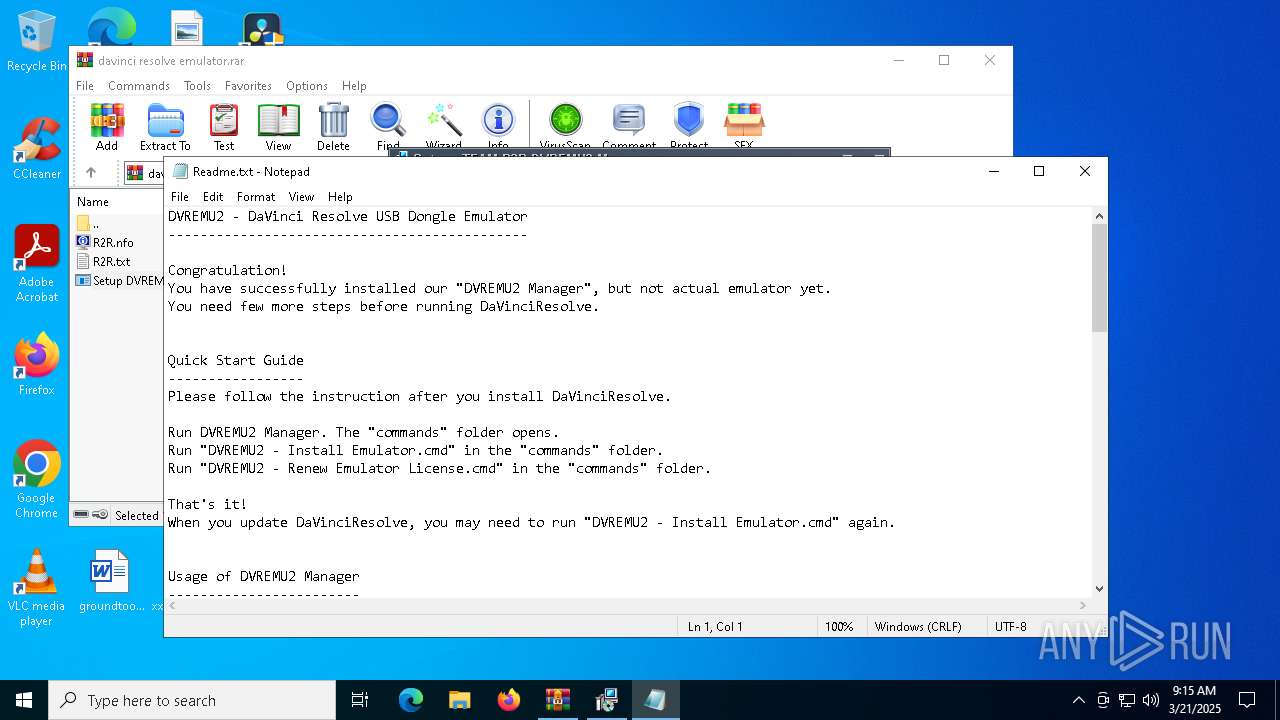
Start notepad (likely ransomware note)
- Setup DVREMU2 Manager v1.0.0.tmp (PID: 7960)
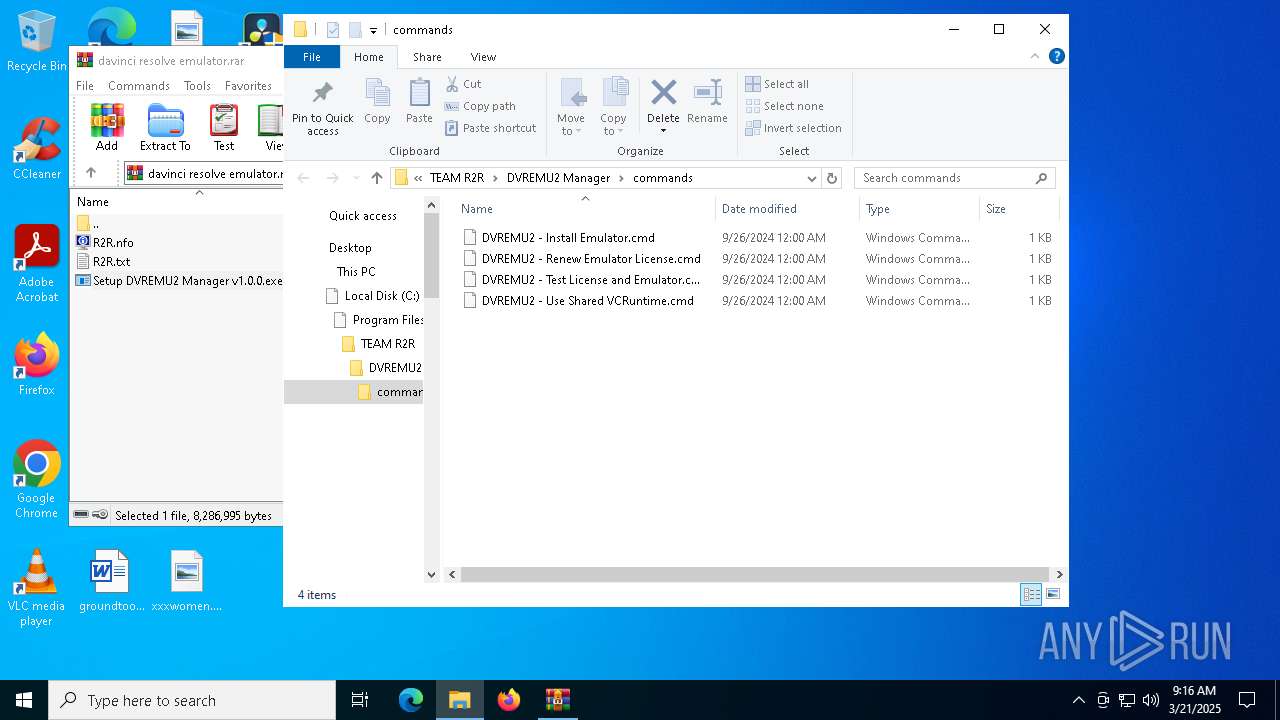
Starts CMD.EXE for commands execution
- explorer.exe (PID: 5156)
Reads the date of Windows installation
- DVREMU2MAN.exe (PID: 2148)
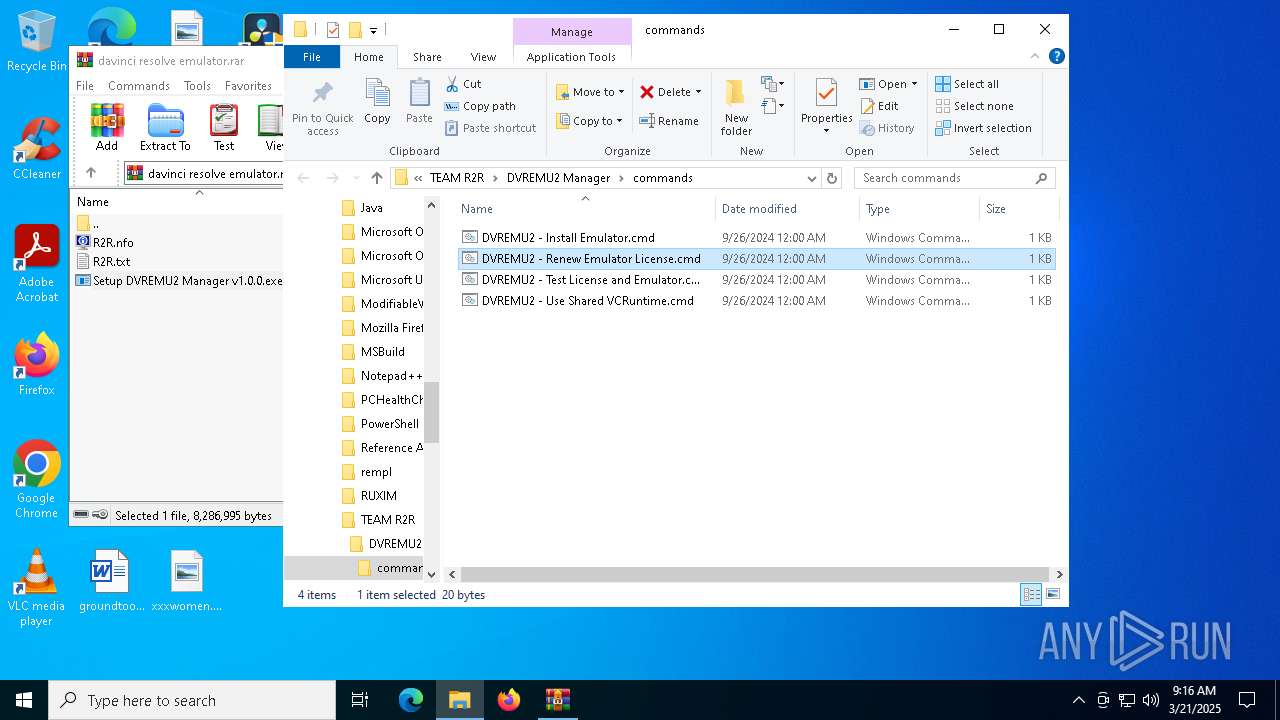
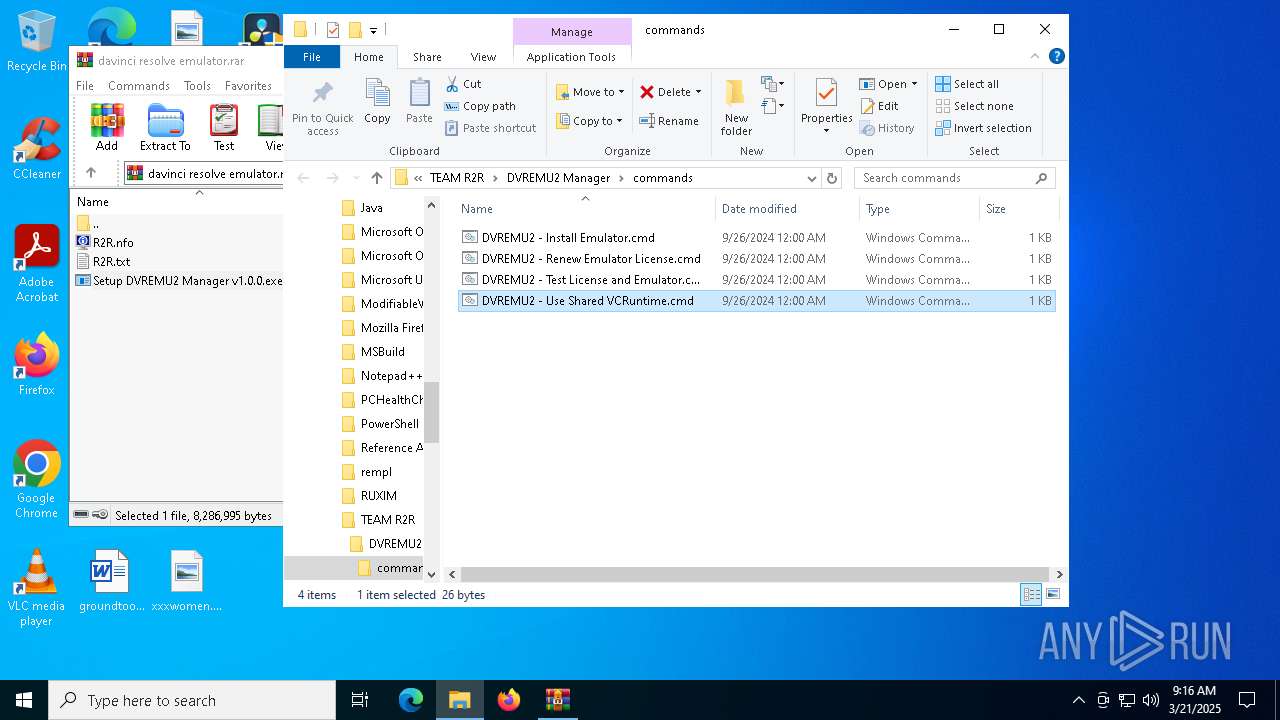
Executing commands from ".cmd" file
- explorer.exe (PID: 5156)
INFO
Checks supported languages
- Setup DVREMU2 Manager v1.0.0.exe (PID: 7800)
- Setup DVREMU2 Manager v1.0.0.exe (PID: 7940)
- Setup DVREMU2 Manager v1.0.0.tmp (PID: 7868)
- Setup DVREMU2 Manager v1.0.0.tmp (PID: 7960)
- DVREMU2MAN.exe (PID: 2148)
- DVREMU2MAN.exe (PID: 900)
- DVREMU2MAN.exe (PID: 3676)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5072)
Creates files in the program directory
- Setup DVREMU2 Manager v1.0.0.tmp (PID: 7960)
Create files in a temporary directory
- Setup DVREMU2 Manager v1.0.0.exe (PID: 7940)
- Setup DVREMU2 Manager v1.0.0.tmp (PID: 7960)
The sample compiled with english language support
- Setup DVREMU2 Manager v1.0.0.tmp (PID: 7960)
Process checks computer location settings
- Setup DVREMU2 Manager v1.0.0.tmp (PID: 7868)
- DVREMU2MAN.exe (PID: 2148)
Reads the computer name
- Setup DVREMU2 Manager v1.0.0.tmp (PID: 7868)
- Setup DVREMU2 Manager v1.0.0.tmp (PID: 7960)
- DVREMU2MAN.exe (PID: 2148)
Manual execution by a user
- DVREMU2MAN.exe (PID: 5544)
- DVREMU2MAN.exe (PID: 2148)
- DVREMU2MAN.exe (PID: 3676)
- DVREMU2MAN.exe (PID: 6244)
Reads security settings of Internet Explorer
- explorer.exe (PID: 5156)
Creates files or folders in the user directory
- BackgroundTransferHost.exe (PID: 4120)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 1922 |
| UncompressedSize: | 6148 |
| OperatingSystem: | Win32 |
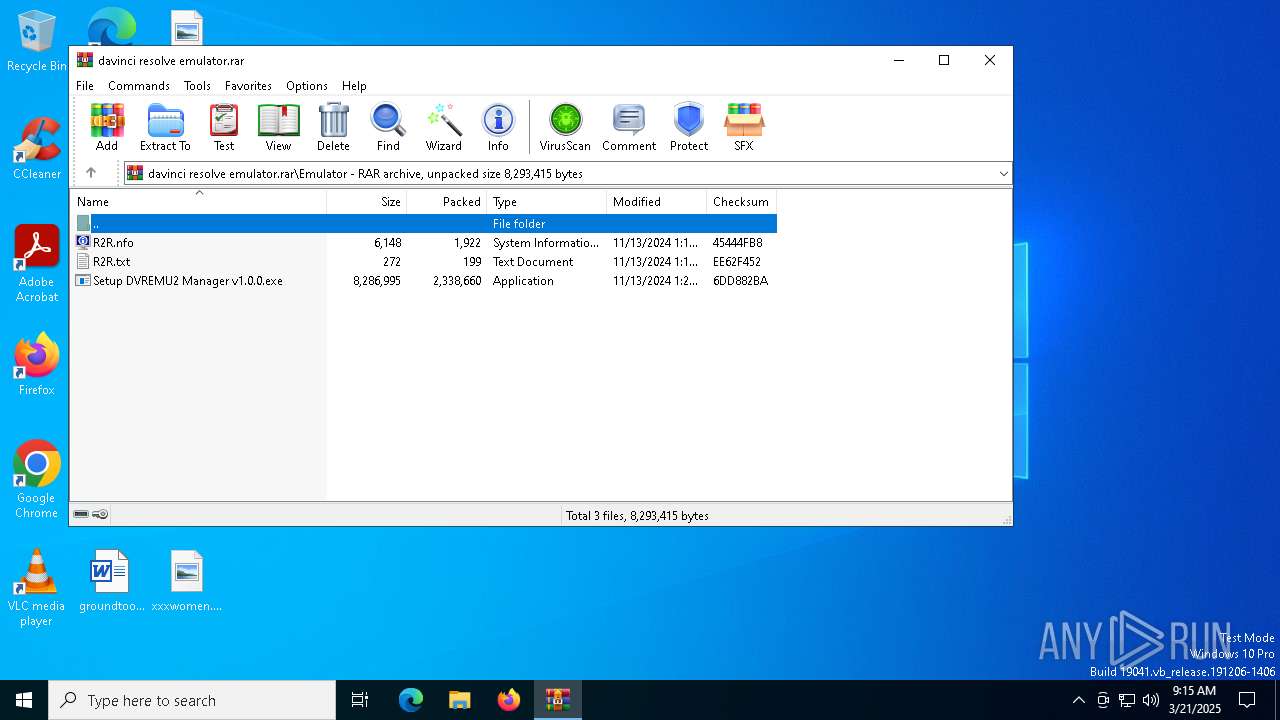
| ArchivedFileName: | Emulator/R2R.nfo |
Total processes
190
Monitored processes
42
Malicious processes
5
Suspicious processes
18
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
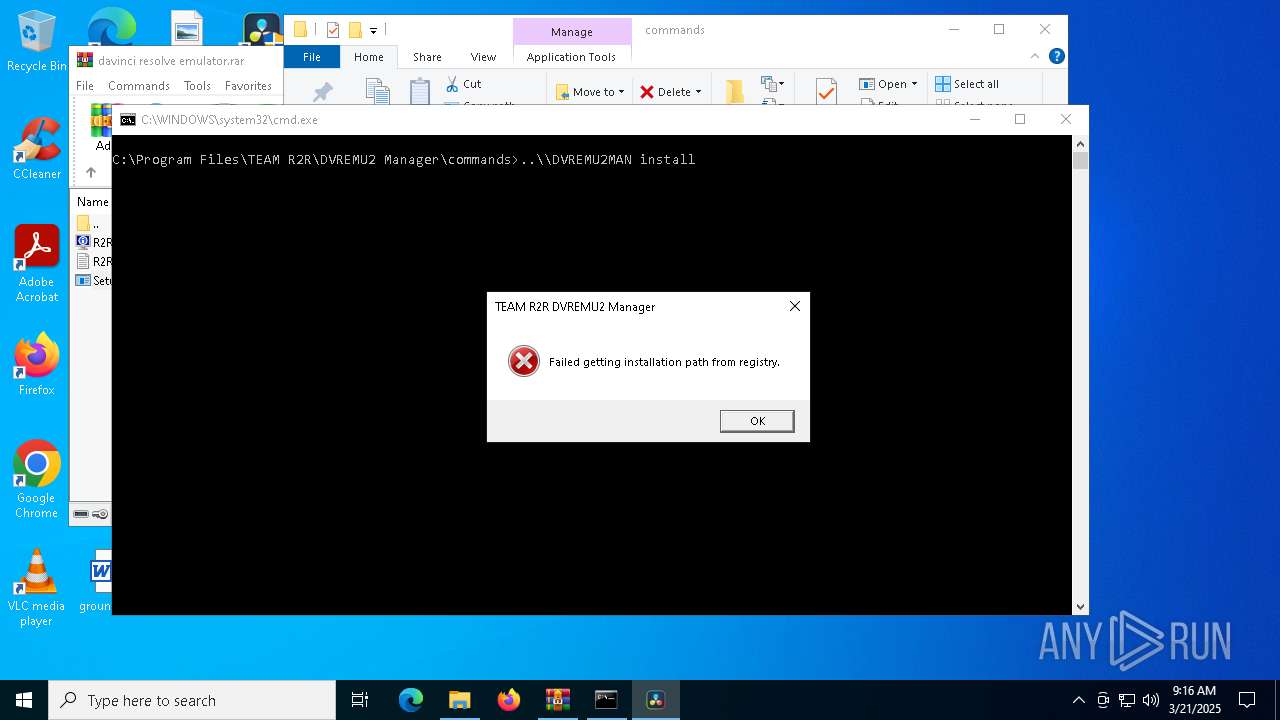
| 900 | "C:\Program Files\TEAM R2R\DVREMU2 Manager\DVREMU2MAN.exe" install | C:\Program Files\TEAM R2R\DVREMU2 Manager\DVREMU2MAN.exe | cmd.exe | ||||||||||||
User: admin Company: TEAM R2R Integrity Level: HIGH Description: DVREMU2 Manager Exit code: 0 Version: 1.0.0.1 Modules
| |||||||||||||||
| 1096 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
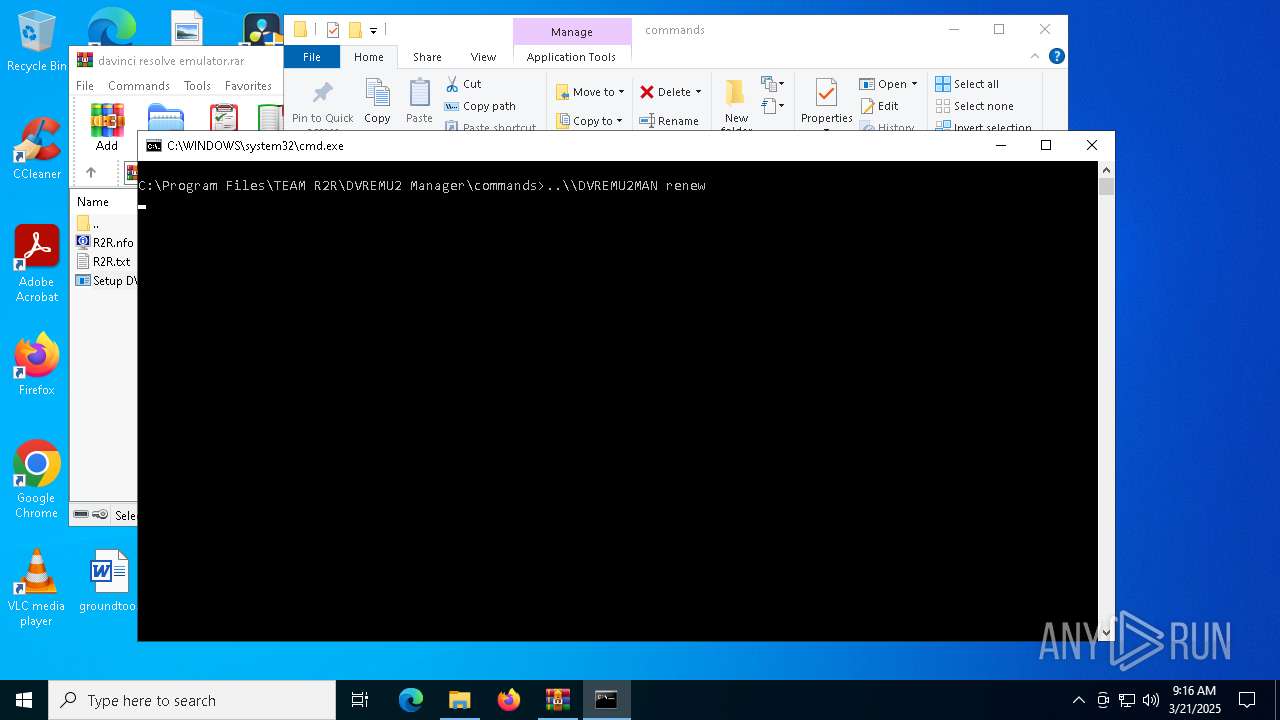
| 2096 | C:\WINDOWS\system32\cmd.exe /c ""C:\Program Files\TEAM R2R\DVREMU2 Manager\commands\DVREMU2 - Renew Emulator License.cmd" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2148 | "C:\Program Files\TEAM R2R\DVREMU2 Manager\DVREMU2MAN.exe" | C:\Program Files\TEAM R2R\DVREMU2 Manager\DVREMU2MAN.exe | explorer.exe | ||||||||||||
User: admin Company: TEAM R2R Integrity Level: HIGH Description: DVREMU2 Manager Exit code: 0 Version: 1.0.0.1 Modules
| |||||||||||||||
| 2320 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
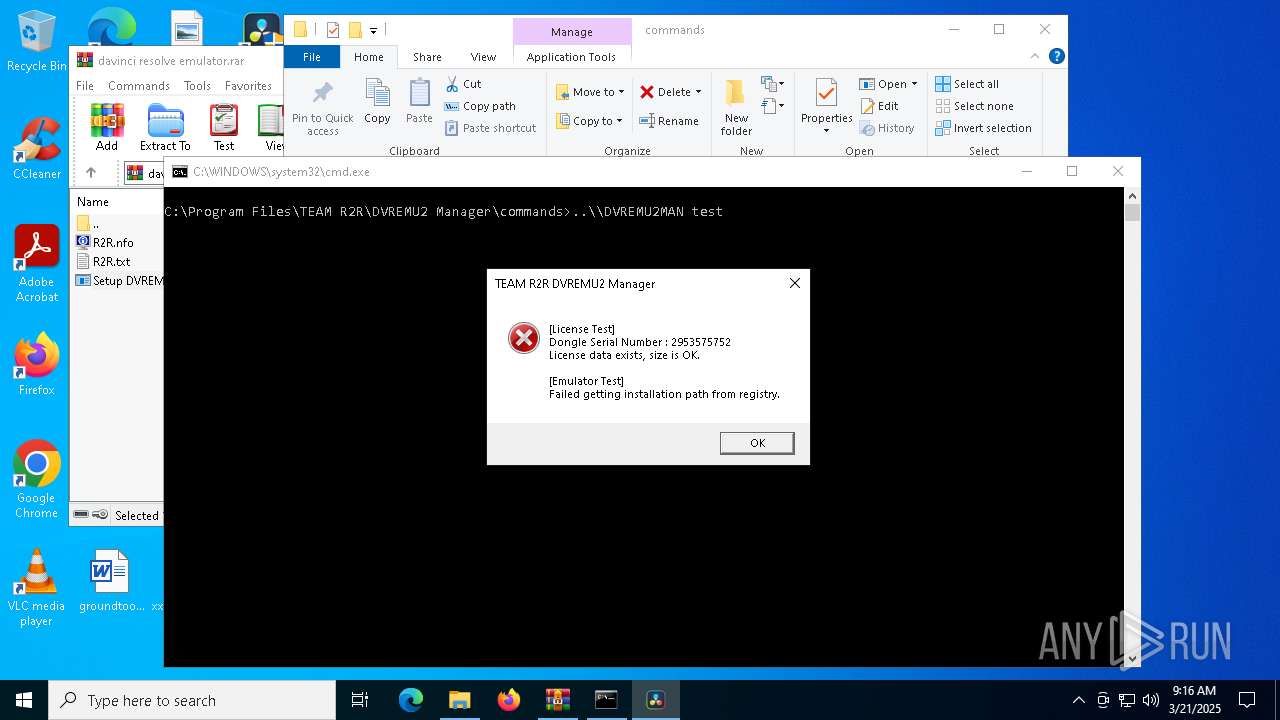
| 2420 | ..\\DVREMU2MAN test | C:\Program Files\TEAM R2R\DVREMU2 Manager\DVREMU2MAN.exe | — | cmd.exe | |||||||||||
User: admin Company: TEAM R2R Integrity Level: MEDIUM Description: DVREMU2 Manager Exit code: 3221226540 Version: 1.0.0.1 Modules
| |||||||||||||||
| 3008 | "C:\Program Files\TEAM R2R\DVREMU2 Manager\DVREMU2MAN.exe" test | C:\Program Files\TEAM R2R\DVREMU2 Manager\DVREMU2MAN.exe | cmd.exe | ||||||||||||
User: admin Company: TEAM R2R Integrity Level: HIGH Description: DVREMU2 Manager Exit code: 0 Version: 1.0.0.1 Modules
| |||||||||||||||
| 3676 | "C:\Program Files\TEAM R2R\DVREMU2 Manager\DVREMU2MAN.exe" | C:\Program Files\TEAM R2R\DVREMU2 Manager\DVREMU2MAN.exe | explorer.exe | ||||||||||||
User: admin Company: TEAM R2R Integrity Level: HIGH Description: DVREMU2 Manager Exit code: 0 Version: 1.0.0.1 Modules
| |||||||||||||||
| 4120 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4428 | ..\\DVREMU2MAN install | C:\Program Files\TEAM R2R\DVREMU2 Manager\DVREMU2MAN.exe | — | cmd.exe | |||||||||||
User: admin Company: TEAM R2R Integrity Level: MEDIUM Description: DVREMU2 Manager Exit code: 3221226540 Version: 1.0.0.1 Modules
| |||||||||||||||
Total events
24 926
Read events
24 797
Write events
125
Delete events
4
Modification events
| (PID) Process: | (5072) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5072) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5072) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5072) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\davinci resolve emulator.rar | |||
| (PID) Process: | (5072) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5072) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5072) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5072) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7960) Setup DVREMU2 Manager v1.0.0.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.txt\OpenWithProgids |
| Operation: | write | Name: | txtfile |
Value: | |||
| (PID) Process: | (7960) Setup DVREMU2 Manager v1.0.0.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\TEAM R2R DVREMU2 Manager_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 5.6.1 (u) | |||
Executable files
15
Suspicious files
10
Text files
12
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7940 | Setup DVREMU2 Manager v1.0.0.exe | C:\Users\admin\AppData\Local\Temp\is-H0KA2.tmp\Setup DVREMU2 Manager v1.0.0.tmp | executable | |
MD5:34ACC2BDB45A9C436181426828C4CB49 | SHA256:9C81817ACD4982632D8C7F1DF3898FCA1477577738184265D735F49FC5480F07 | |||
| 7960 | Setup DVREMU2 Manager v1.0.0.tmp | C:\Users\admin\AppData\Local\Temp\is-VQIER.tmp\SKIN.CJSTYLES | executable | |
MD5:5F87CAF3F7CF63DDE8E6AF53BDF31289 | SHA256:4731982B02B067D3F5A5A7518279A9265A49FB0F7B3F8DC3D61B82A5359D4940 | |||
| 5072 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5072.35891\Emulator\R2R.nfo | text | |
MD5:AB7333C8347D8DEDF40AD37B8AA793E1 | SHA256:02DBEF0AD7800BC54F9BCCF50E9197A646D7EB8E5BA459775EAD6DD1898EB843 | |||
| 5072 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5072.35891\Emulator\R2R.txt | text | |
MD5:A2ADBEFC72AE91451926424CE7A1105D | SHA256:8E06520969D5A5D747FFC74EA63B270744FC9CF22E90DFE918A797800FC4BD1E | |||
| 7800 | Setup DVREMU2 Manager v1.0.0.exe | C:\Users\admin\AppData\Local\Temp\is-HI2LH.tmp\Setup DVREMU2 Manager v1.0.0.tmp | executable | |
MD5:34ACC2BDB45A9C436181426828C4CB49 | SHA256:9C81817ACD4982632D8C7F1DF3898FCA1477577738184265D735F49FC5480F07 | |||
| 7960 | Setup DVREMU2 Manager v1.0.0.tmp | C:\Program Files\TEAM R2R\DVREMU2 Manager\is-NF0SJ.tmp | executable | |
MD5:908F64B344BCE85C344E88DB0C4C334F | SHA256:6BDC1C8F0A1BD5951E94F575E6B693D0150D25F3B62BC7314567B2C4C3A8F009 | |||
| 5072 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5072.35891\Emulator\Setup DVREMU2 Manager v1.0.0.exe | executable | |
MD5:712694288F0A36EFEAD1B9BA8B4C0AB0 | SHA256:8D31D34083335DC0CC3C76BD5F418846E8F4DAAD5A437CEFD8E47DF332401B08 | |||
| 7960 | Setup DVREMU2 Manager v1.0.0.tmp | C:\Users\admin\AppData\Local\Temp\is-VQIER.tmp\ISSKINU.DLL | executable | |
MD5:F30AFCCD6FAFC1CAD4567ADA824C9358 | SHA256:E28D16FAD16BCA8198C47D7DD44ACFD362DD6BA1654F700ADD8AAF2C0732622D | |||
| 7960 | Setup DVREMU2 Manager v1.0.0.tmp | C:\Program Files\TEAM R2R\DVREMU2 Manager\unins000.exe | executable | |
MD5:908F64B344BCE85C344E88DB0C4C334F | SHA256:6BDC1C8F0A1BD5951E94F575E6B693D0150D25F3B62BC7314567B2C4C3A8F009 | |||
| 7960 | Setup DVREMU2 Manager v1.0.0.tmp | C:\Program Files\TEAM R2R\DVREMU2 Manager\DVREMU2MAN.exe | executable | |
MD5:2A052D9B7BDD115E24B7BC4B8475EDCE | SHA256:2083BEB78B4CEBA4A8FE819ED2307B4C0A22622F32CAEA60FCEA7DE0BCBD76B8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
27
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2656 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7488 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
2656 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4120 | BackgroundTransferHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2516 | RUXIMICS.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 20.190.160.3:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
www.bing.com |
| whitelisted |
fp.msedge.net |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |