| URL: | https://softmany.com/zapya-windows/ |
| Full analysis: | https://app.any.run/tasks/0fa2318b-7968-4709-9e70-f89aa6185ea3 |
| Verdict: | Malicious activity |
| Analysis date: | May 13, 2024, 08:19:49 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 251F9B532F0B1A33252B3B2F5C9EE6C0 |
| SHA1: | 9DEFEEA0D884ADC942981875FABA273B0C0FA048 |
| SHA256: | B340D89689D17FF88B07A0C82979BC1C4DBC204F4F8C069434AF06A0DFB05D53 |
| SSDEEP: | 3:N8HPoLGKIn1IvN:2v5+N |
MALICIOUS
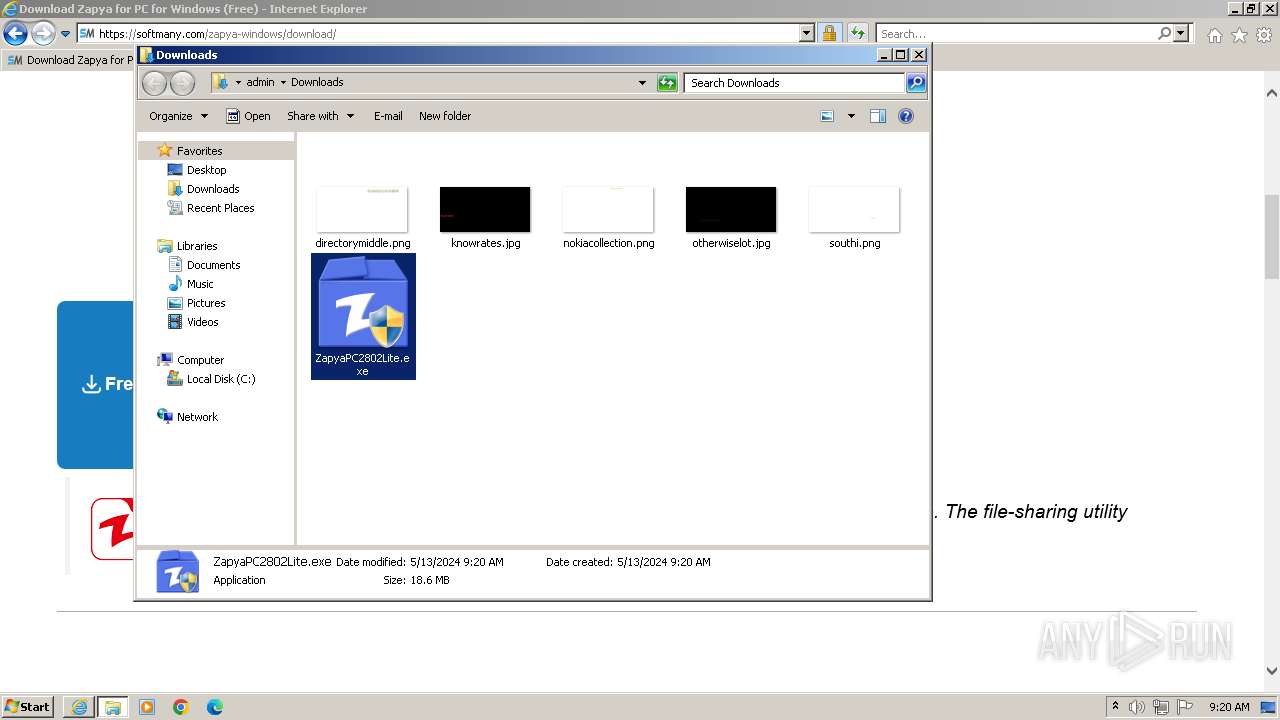
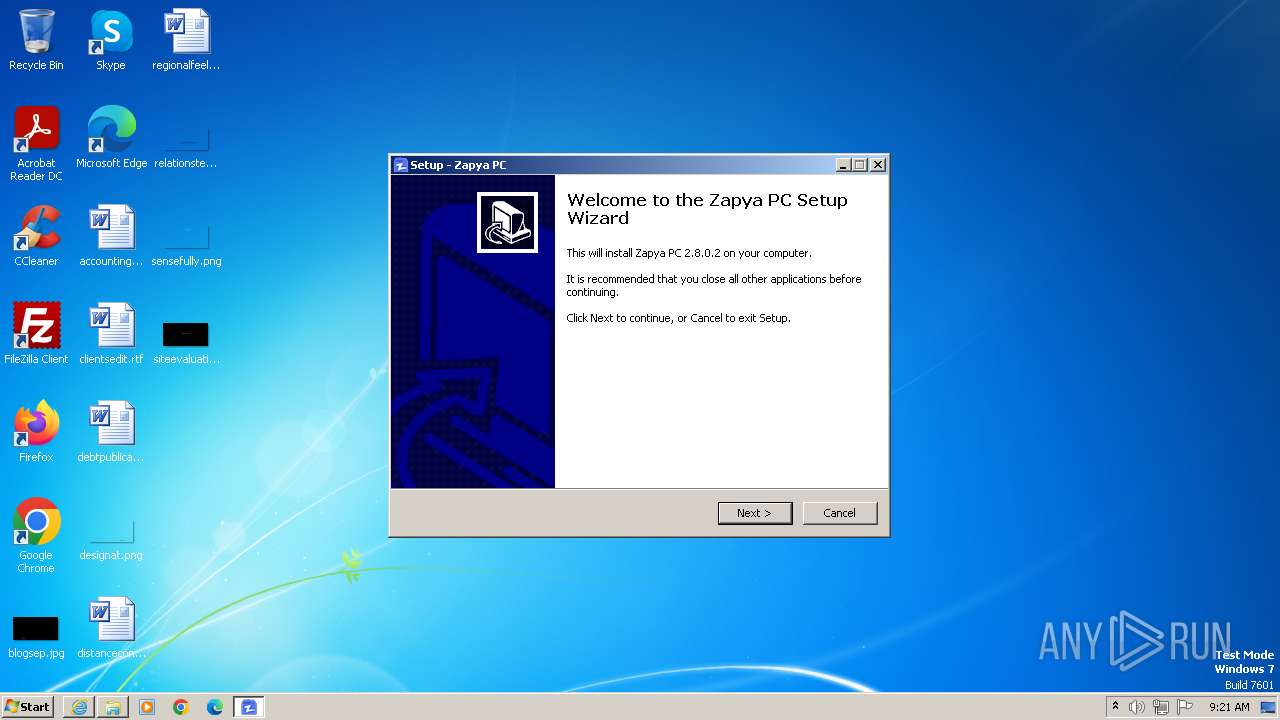
Drops the executable file immediately after the start
- ZapyaPC2802Lite.exe (PID: 860)
- ZapyaPC2802Lite.tmp (PID: 1940)
Actions looks like stealing of personal data
- ZapyaPC2802Lite.tmp (PID: 1940)
Changes the autorun value in the registry
- ZapyaPC2802Lite.tmp (PID: 1940)
Creates a writable file in the system directory
- ZapyaService.exe (PID: 3836)
SUSPICIOUS
Executable content was dropped or overwritten
- ZapyaPC2802Lite.exe (PID: 860)
- ZapyaPC2802Lite.tmp (PID: 1940)
Process drops legitimate windows executable
- ZapyaPC2802Lite.tmp (PID: 1940)
Reads the Windows owner or organization settings
- ZapyaPC2802Lite.tmp (PID: 1940)
Starts CMD.EXE for commands execution
- ZapyaPC2802Lite.tmp (PID: 1940)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 188)
- cmd.exe (PID: 1332)
- cmd.exe (PID: 1468)
- cmd.exe (PID: 2076)
- cmd.exe (PID: 2484)
- cmd.exe (PID: 1996)
- cmd.exe (PID: 2428)
- cmd.exe (PID: 2808)
- cmd.exe (PID: 916)
- cmd.exe (PID: 1312)
Reads the Internet Settings
- ZapyaPC2802Lite.tmp (PID: 1940)
- InstallUtil.exe (PID: 3424)
- Zapya.exe (PID: 1616)
Reads Microsoft Outlook installation path
- ZapyaPC2802Lite.tmp (PID: 1940)
Reads Internet Explorer settings
- ZapyaPC2802Lite.tmp (PID: 1940)
Reads security settings of Internet Explorer
- ZapyaPC2802Lite.tmp (PID: 1940)
- InstallUtil.exe (PID: 3424)
- ZapyaAdaptor.exe (PID: 3480)
Executes as Windows Service
- ZapyaService.exe (PID: 3836)
Checks Windows Trust Settings
- ZapyaAdaptor.exe (PID: 3480)
Reads settings of System Certificates
- ZapyaAdaptor.exe (PID: 3480)
- Zapya.exe (PID: 1616)
INFO
Application launched itself
- iexplore.exe (PID: 3976)
- msedge.exe (PID: 3884)
- msedge.exe (PID: 616)
Manual execution by a user
- wmpnscfg.exe (PID: 328)
- ZapyaPC2802Lite.exe (PID: 1640)
- ZapyaPC2802Lite.exe (PID: 860)
- msedge.exe (PID: 616)
- Zapya.exe (PID: 1616)
Checks supported languages
- wmpnscfg.exe (PID: 328)
- ZapyaPC2802Lite.exe (PID: 860)
- ZapyaPC2802Lite.tmp (PID: 1940)
- ZsSetup.exe (PID: 3468)
- InstallUtil.exe (PID: 3424)
- ZapyaService.exe (PID: 3836)
- Zapya.exe (PID: 1616)
- ZapyaAdaptor.exe (PID: 3480)
Reads the computer name
- wmpnscfg.exe (PID: 328)
- ZapyaPC2802Lite.tmp (PID: 1940)
- ZsSetup.exe (PID: 3468)
- InstallUtil.exe (PID: 3424)
- ZapyaService.exe (PID: 3836)
- Zapya.exe (PID: 1616)
- ZapyaAdaptor.exe (PID: 3480)
Executable content was dropped or overwritten
- iexplore.exe (PID: 4036)
- iexplore.exe (PID: 3976)
Drops the executable file immediately after the start
- iexplore.exe (PID: 4036)
- iexplore.exe (PID: 3976)
Modifies the phishing filter of IE
- iexplore.exe (PID: 3976)
The process uses the downloaded file
- iexplore.exe (PID: 3976)
- ZapyaPC2802Lite.tmp (PID: 1940)
Create files in a temporary directory
- ZapyaPC2802Lite.exe (PID: 860)
- ZapyaPC2802Lite.tmp (PID: 1940)
Checks Windows language
- ZapyaPC2802Lite.tmp (PID: 1940)
Checks proxy server information
- ZapyaPC2802Lite.tmp (PID: 1940)
Reads Environment values
- ZapyaPC2802Lite.tmp (PID: 1940)
- Zapya.exe (PID: 1616)
Creates files in the program directory
- ZapyaPC2802Lite.tmp (PID: 1940)
- InstallUtil.exe (PID: 3424)
- ZapyaService.exe (PID: 3836)
Creates a software uninstall entry
- ZapyaPC2802Lite.tmp (PID: 1940)
Reads the machine GUID from the registry
- ZsSetup.exe (PID: 3468)
- ZapyaPC2802Lite.tmp (PID: 1940)
- InstallUtil.exe (PID: 3424)
- ZapyaService.exe (PID: 3836)
- Zapya.exe (PID: 1616)
- ZapyaAdaptor.exe (PID: 3480)
Creates files or folders in the user directory
- ZsSetup.exe (PID: 3468)
- Zapya.exe (PID: 1616)
- ZapyaAdaptor.exe (PID: 3480)
Reads product name
- ZapyaPC2802Lite.tmp (PID: 1940)
Reads the software policy settings
- ZapyaAdaptor.exe (PID: 3480)
- Zapya.exe (PID: 1616)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
107
Monitored processes
52
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | "cmd.exe" /c taskkill /F /IM hh.exe | C:\Windows\System32\cmd.exe | — | ZapyaPC2802Lite.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 128 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 328 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 616 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --flag-switches-begin --flag-switches-end --do-not-de-elevate "C:\Program Files\Zapya\ZapyaPC\tools\en-us\help_english.html" | C:\Program Files\Microsoft\Edge\Application\msedge.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 860 | "C:\Users\admin\Downloads\ZapyaPC2802Lite.exe" | C:\Users\admin\Downloads\ZapyaPC2802Lite.exe | explorer.exe | ||||||||||||
User: admin Company: DewMobile,Inc. Integrity Level: HIGH Description: Zapya Exit code: 0 Version: 2.8.0.2 Modules
| |||||||||||||||
| 916 | "cmd.exe" /c taskkill /F /IM ZapyaInternetSharing.exe | C:\Windows\System32\cmd.exe | — | ZapyaPC2802Lite.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 128 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1060 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=1012 --field-trial-handle=868,i,11573957106394497114,5686996122874492149,131072 /prefetch:3 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1072 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=16 --mojo-platform-channel-handle=3856 --field-trial-handle=1276,i,16564751475687004626,9871659166097606660,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1312 | "cmd.exe" /c taskkill /F /IM WiFiDirectLegacyAP.exe | C:\Windows\System32\cmd.exe | — | ZapyaPC2802Lite.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 128 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1312 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=3312 --field-trial-handle=1276,i,16564751475687004626,9871659166097606660,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1332 | "cmd.exe" /c taskkill /F /IM UninstallWin32.exe | C:\Windows\System32\cmd.exe | — | ZapyaPC2802Lite.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 128 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
49 565
Read events
49 184
Write events
303
Delete events
78
Modification events
| (PID) Process: | (3976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31106318 | |||
| (PID) Process: | (3976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31106318 | |||
| (PID) Process: | (3976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
108
Suspicious files
150
Text files
494
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4036 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | der | |
MD5:3E549B5389BC9C0837D865F0FD5E6F76 | SHA256:FFF9D6642902E0E72199831F2EFA86DEF70CC12C3647DC7907A1F10F07F37E01 | |||
| 4036 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:531C893D7F4BA7908EA8997EEC0A5143 | SHA256:0E2FF3A45806695DEE8D36CF3A805B04AEE3D5F0D848526DB864D9CAE6DE3D27 | |||
| 4036 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:0B4BDAA9BA0DEA7A3E9394F28E4C3D90 | SHA256:37CABA727AEEC61A5A926C3CCEF56287A2190586658CDEC83D31E3793C51C0AB | |||
| 4036 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CAF4703619713E3F18D8A9D5D88D6288_F2DAF19C1F776537105D08FC8D978464 | binary | |
MD5:173EE8593AF6104923C7F170C0C3B70E | SHA256:41232C54968C93E56379E6720019899ECF4D753EADC9529E8FB9DBC81A5D8451 | |||
| 4036 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_F2DAF19C1F776537105D08FC8D978464 | der | |
MD5:8202A1CD02E7D69597995CABBE881A12 | SHA256:58F381C3A0A0ACE6321DA22E40BD44A597BD98B9C9390AB9258426B5CF75A7A5 | |||
| 4036 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\jquery.min[1].js | text | |
MD5:826EB77E86B02AB7724FE3D0141FF87C | SHA256:CB6F2D32C49D1C2B25E9FFC9AAAFA3F83075346C01BCD4AE6EB187392A4292CF | |||
| 4036 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\zapya-windows[1].htm | html | |
MD5:D09AAC6BE1620037FA25194D94924211 | SHA256:283E8E81C3B006115E0E382D779DCD47F87C2DB45D62C6A55057A4907322DAA9 | |||
| 4036 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\offside.min[1].js | text | |
MD5:2C8D926D887909904DAB4316508BACC6 | SHA256:50FE1014E82DD9ACEA2F5B26061C8F135CB11EA0AA5D5AD5985E6B265B7F50A8 | |||
| 4036 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\embed-count-scroll.min[1].js | text | |
MD5:9D5B9F0DDC4B807B28BDE14DE26F4C6A | SHA256:DA82D5638ED73ACE79F3F850E1AB80F414BD3FBB18F9554B8BB71A1CCCC1909A | |||
| 3976 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\EAF8AA29A62AB29E614331747385D816_F9E4DC0B9D5C777357D7DB8DEF51118A | der | |
MD5:726E3850700A33F9AA360CEE4E2EDE33 | SHA256:DBF1C8110A2E52DE01271F6CAAE2F0C8E9018114497A395E510DB54CF219E2A8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
25
TCP/UDP connections
88
DNS requests
55
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4036 | iexplore.exe | GET | 304 | 23.220.73.6:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?aa27c982be707355 | unknown | — | — | unknown |
4036 | iexplore.exe | GET | 304 | 23.220.73.6:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?30bfcba95dc85498 | unknown | — | — | unknown |
4036 | iexplore.exe | GET | 200 | 142.250.184.227:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | — | — | unknown |
3976 | iexplore.exe | GET | 304 | 23.220.73.6:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?5fc92888093a54f7 | unknown | — | — | unknown |
4036 | iexplore.exe | GET | 200 | 142.250.184.227:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFCjJ1PwkYAi7fE%3D | unknown | — | — | unknown |
3976 | iexplore.exe | GET | 304 | 23.220.73.6:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?260f79dbb405aab9 | unknown | — | — | unknown |
4036 | iexplore.exe | GET | 200 | 142.250.184.227:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | unknown | — | — | unknown |
4036 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | unknown | — | — | unknown |
4036 | iexplore.exe | GET | 200 | 142.250.184.227:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEEn9UPPGUtnUEjctHzGvXDE%3D | unknown | — | — | unknown |
4036 | iexplore.exe | GET | 200 | 142.250.184.227:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEAFWoeiRoD5nEA9wbC%2FqWOc%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4036 | iexplore.exe | 104.25.149.12:443 | softmany.com | CLOUDFLARENET | US | shared |
4036 | iexplore.exe | 23.220.73.6:80 | ctldl.windowsupdate.com | Akamai International B.V. | US | unknown |
4036 | iexplore.exe | 142.250.184.227:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
3976 | iexplore.exe | 23.222.16.26:443 | www.bing.com | Akamai International B.V. | US | unknown |
3976 | iexplore.exe | 23.220.73.6:80 | ctldl.windowsupdate.com | Akamai International B.V. | US | unknown |
4036 | iexplore.exe | 142.250.186.40:443 | www.googletagmanager.com | GOOGLE | US | unknown |
4036 | iexplore.exe | 142.250.185.226:443 | pagead2.googlesyndication.com | GOOGLE | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
softmany.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
pagead2.googlesyndication.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
cdnjs.cloudflare.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.youtube.com |
| whitelisted |
Threats
Process | Message |
|---|---|
ZsSetup.exe | 2024-05-13 09:21:51.039 | [info] | [file: ] | [func: App_Startup] | [line: 0] | [col: 0] | C:\Program Files\Zapya\ZapyaPC
|
ZsSetup.exe | 2024-05-13 09:21:51.492 | [info] | [file: ] | [func: App_Startup] | [line: 0] | [col: 0] | ZapyaService installed
|
ZsSetup.exe | 2024-05-13 09:21:51.492 | [info] | [file: ] | [func: RunInstallUtil] | [line: 0] | [col: 0] | Microsoft (R) .NET Framework Installation utility Version 2.0.50727.7905
Copyright (c) Microsoft Corporation. All rights reserved.
Running a transacted installation.
Beginning the Install phase of the installation.
See the contents of the log file for the C:\Program Files\Zapya\ZapyaPC\ZapyaService.exe assembly's progress.
The file is located at .
Installing assembly 'C:\Program Files\Zapya\ZapyaPC\ZapyaService.exe'.
Affected parameters are:
logtoconsole =
logfile =
assemblypath = C:\Program Files\Zapya\ZapyaPC\ZapyaService.exe
Installing service ZapyaService...
Service ZapyaService has been successfully installed.
Creating EventLog source ZapyaService in log Application...
The Install phase completed successfully, and the Commit phase is beginning.
See the contents of the log file for the C:\Program Files\Zapya\ZapyaPC\ZapyaService.exe assembly's progress.
The file is located at .
Committing assembly 'C:\Program Files\Zapya\ZapyaPC\ZapyaService.exe'.
Affected parameters are:
logtoconsole =
logfile =
assemblypath = C:\Program Files\Zapya\ZapyaPC\ZapyaService.exe
The Commit phase completed successfully.
The transacted install has completed.
|
ZapyaService.exe | 2024-05-13 09:21:51.617 | [debug] | [file: ] | [func: Main] | [line: 0] | [col: 0] | Main() Start
|
ZapyaService.exe | 2024-05-13 09:21:51.664 | [info] | [file: ] | [func: .ctor] | [line: 0] | [col: 0] | ZapyaService() End
|
ZapyaService.exe | 2024-05-13 09:21:51.664 | [info] | [file: ] | [func: .ctor] | [line: 0] | [col: 0] | ZapyaService() Start
|
ZapyaService.exe | 2024-05-13 09:21:51.695 | [info] | [file: ] | [func: Start] | [line: 0] | [col: 0] | CmdServer.Start()
|
ZapyaService.exe | 2024-05-13 09:21:51.695 | [info] | [file: ] | [func: Start] | [line: 0] | [col: 0] | C:\Program Files\Zapya\ZapyaPC
|
ZapyaService.exe | 2024-05-13 09:21:51.711 | [info] | [file: ] | [func: Run] | [line: 0] | [col: 0] | CmdServer.Run() Start
|
ZapyaService.exe | 2024-05-13 09:21:51.711 | [error] | [file: ] | [func: .cctor] | [line: 0] | [col: 0] | The service has not been started
|