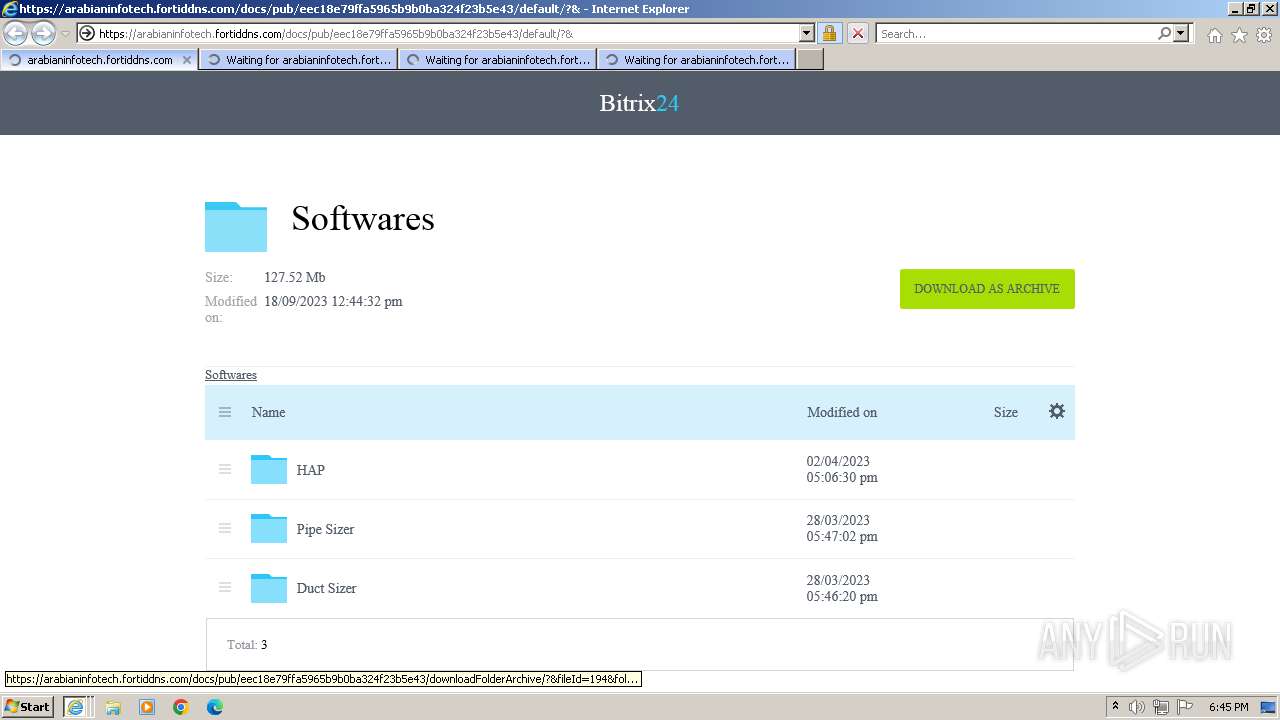
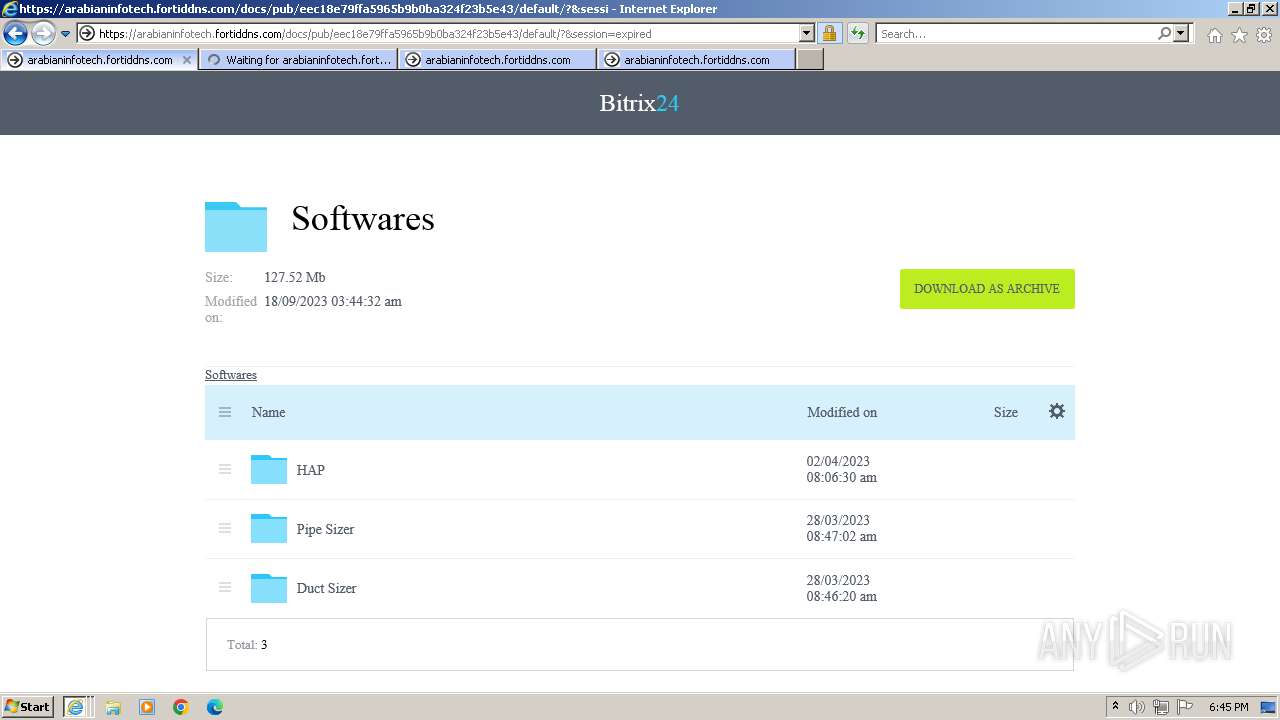
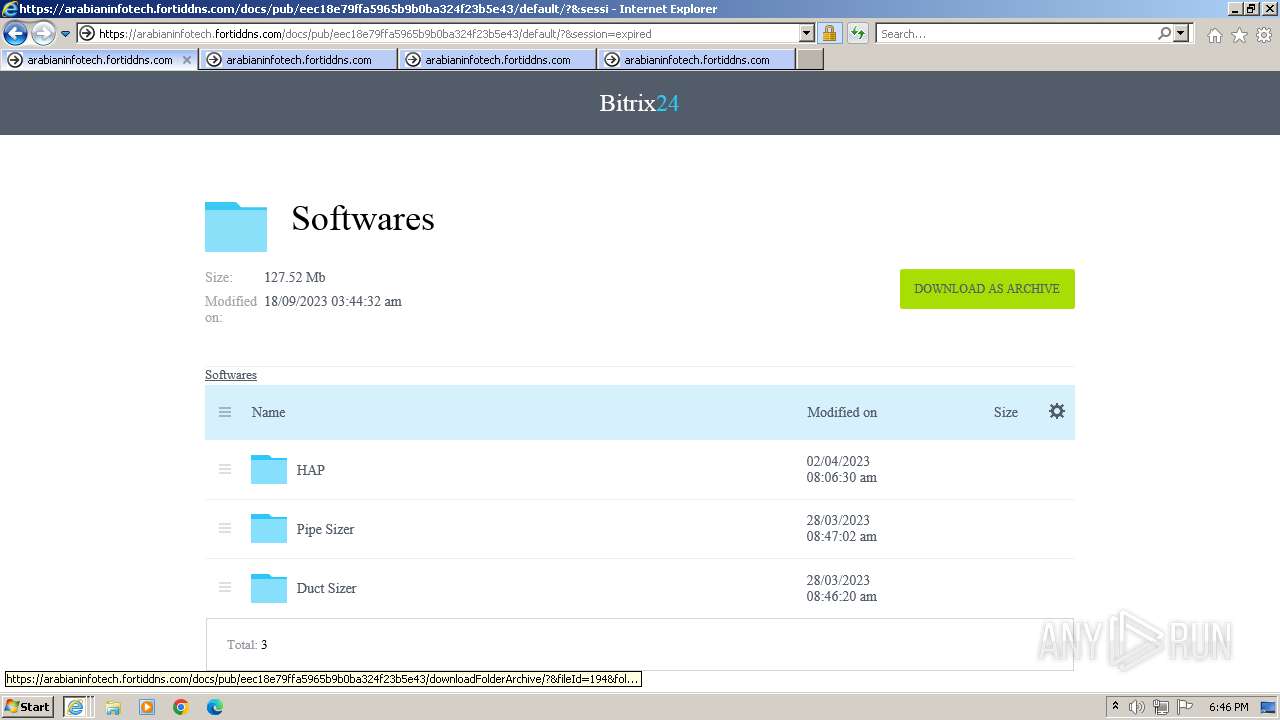
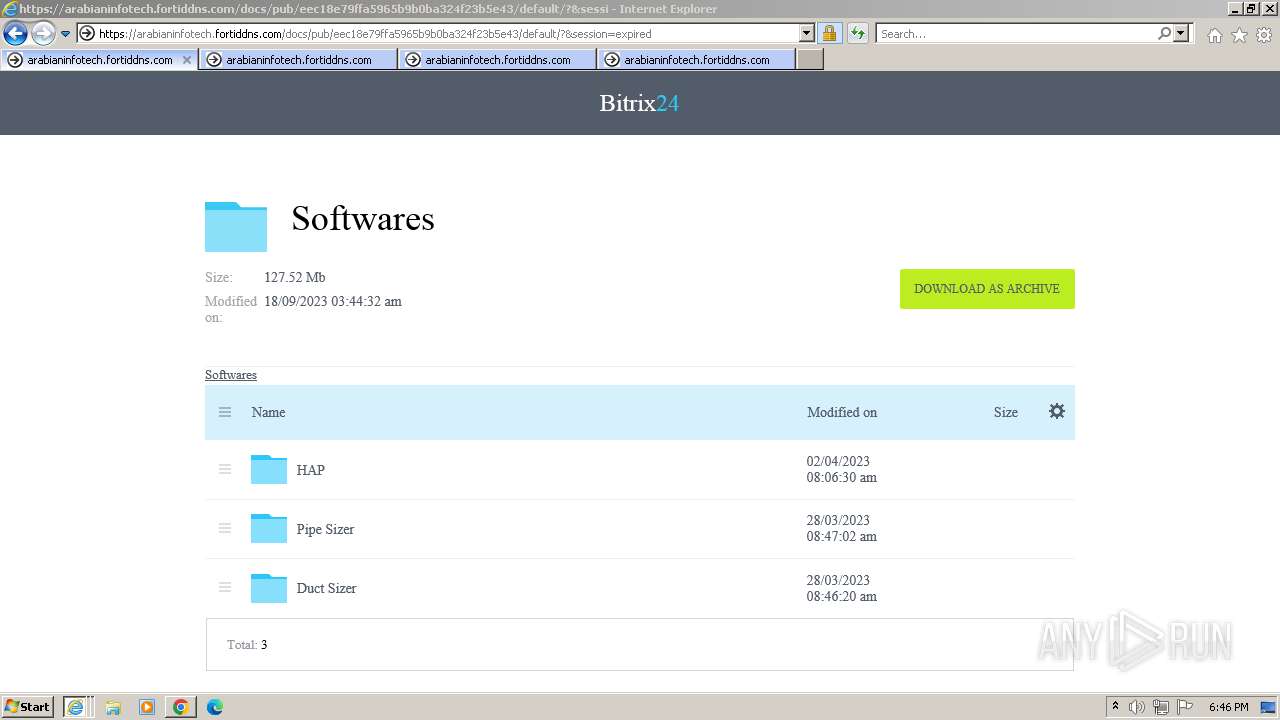
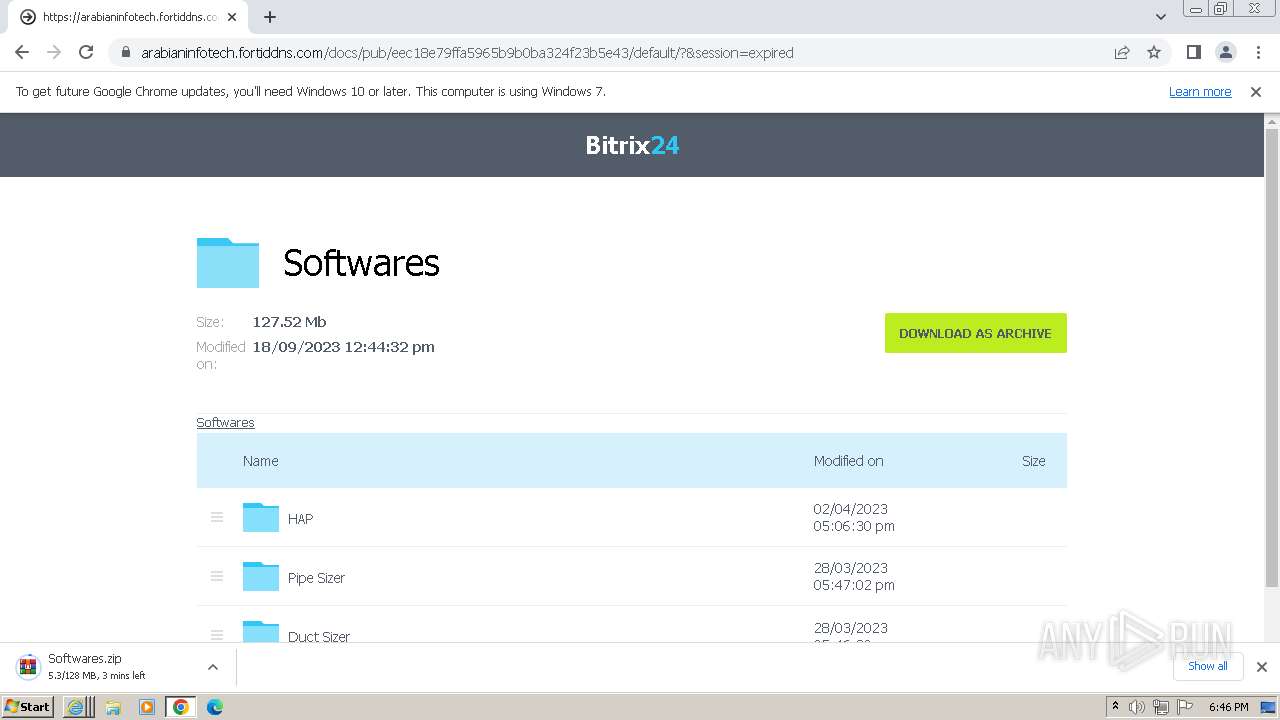
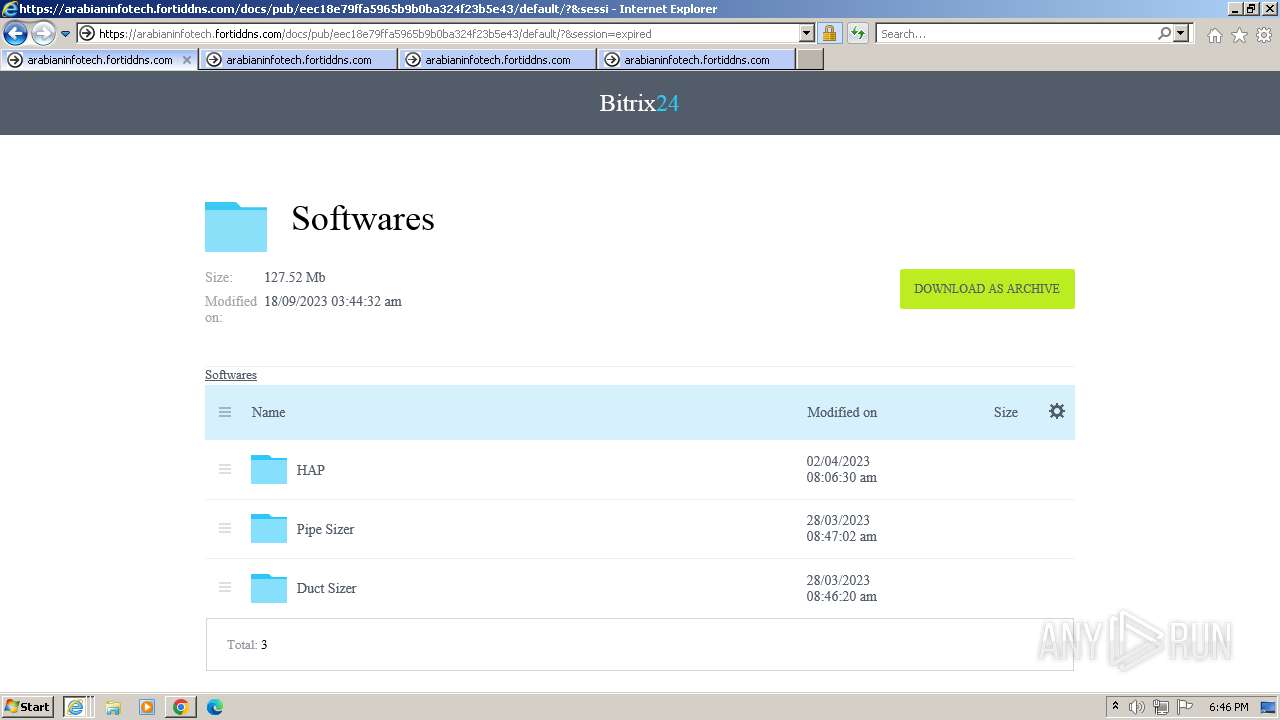
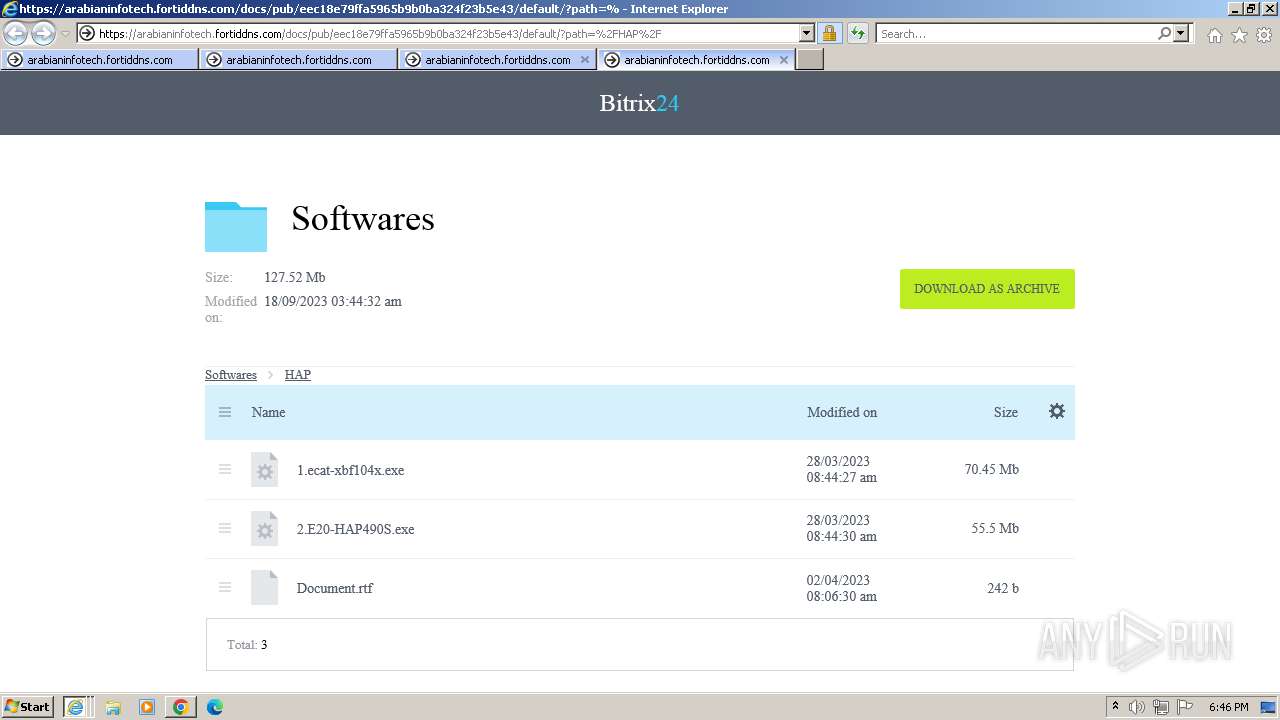
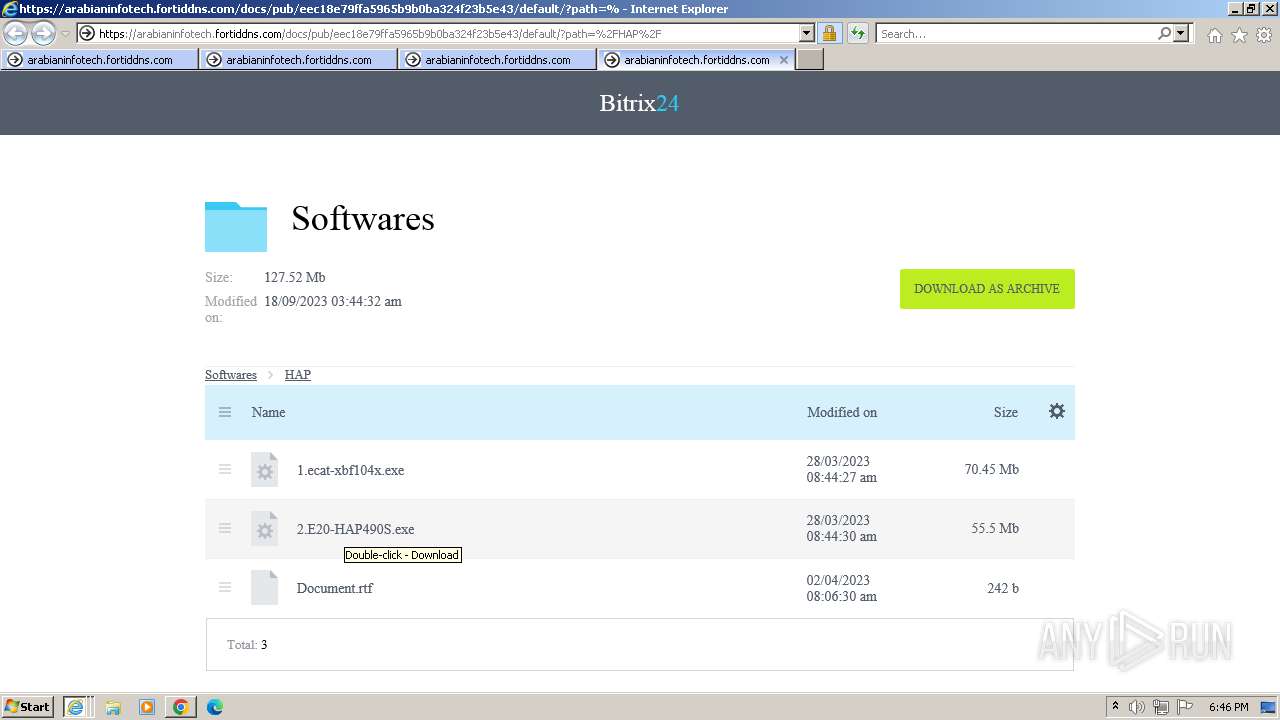
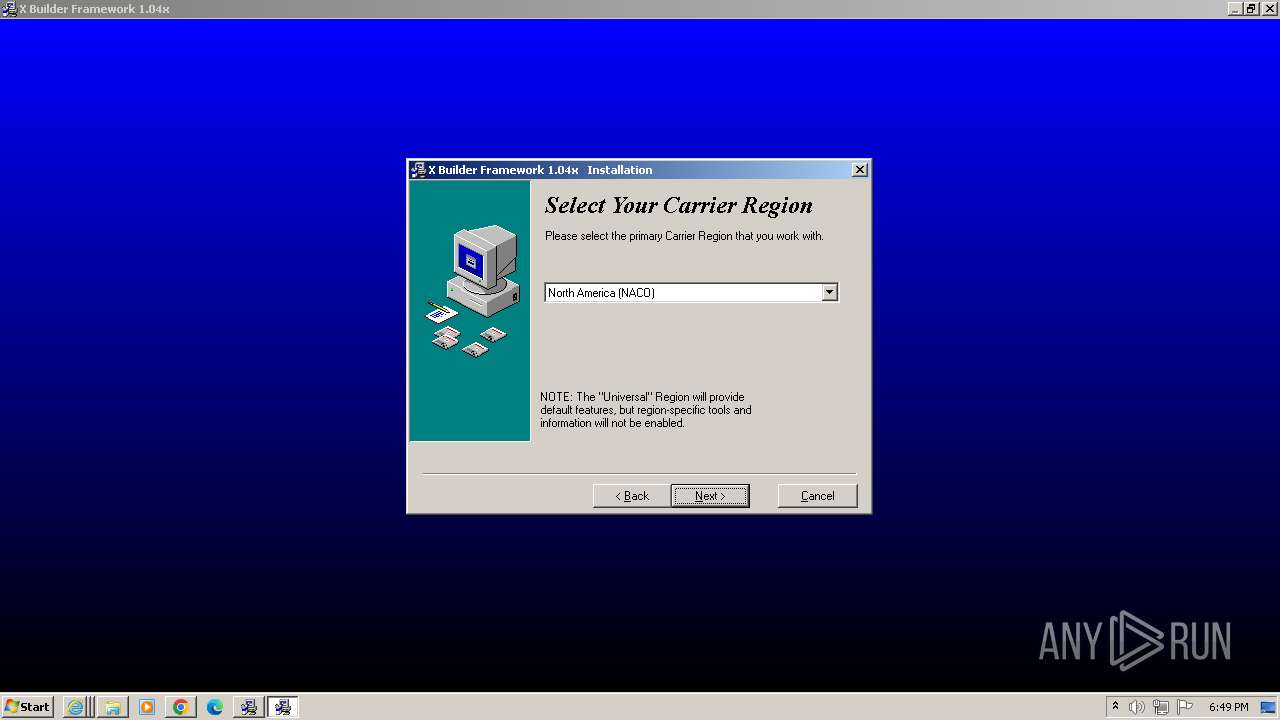
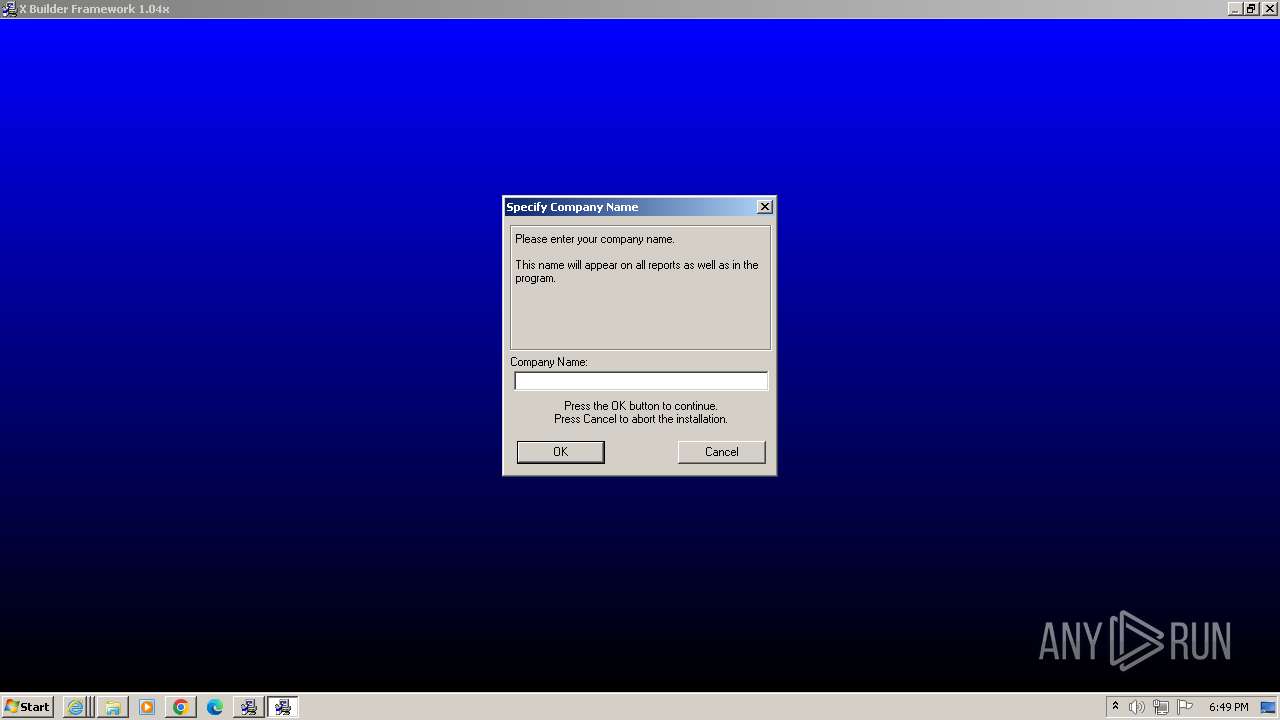
| URL: | https://arabianinfotech.fortiddns.com/~ROlah |
| Full analysis: | https://app.any.run/tasks/b250dd64-105d-4555-a70d-b2dc5cb004de |
| Verdict: | Malicious activity |
| Analysis date: | December 10, 2023, 18:45:28 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 4EE14B2042B7A86856ACBFB71E30B49D |
| SHA1: | 90AF7B530926320585726E18F9283487B64CC5F6 |
| SHA256: | B337907132B40600B644BB7039883718CB700A4D2530576BD928969D405AB9ED |
| SSDEEP: | 3:N8fma8q7saW:2fL1tW |
MALICIOUS
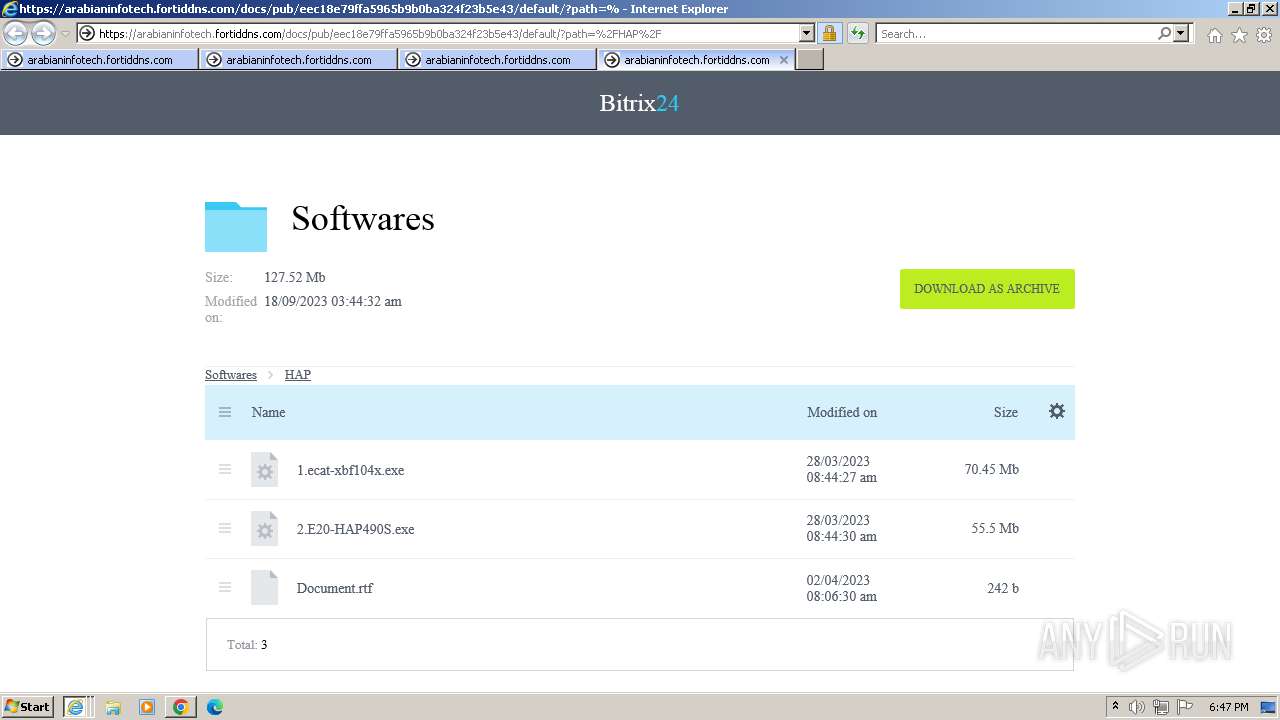
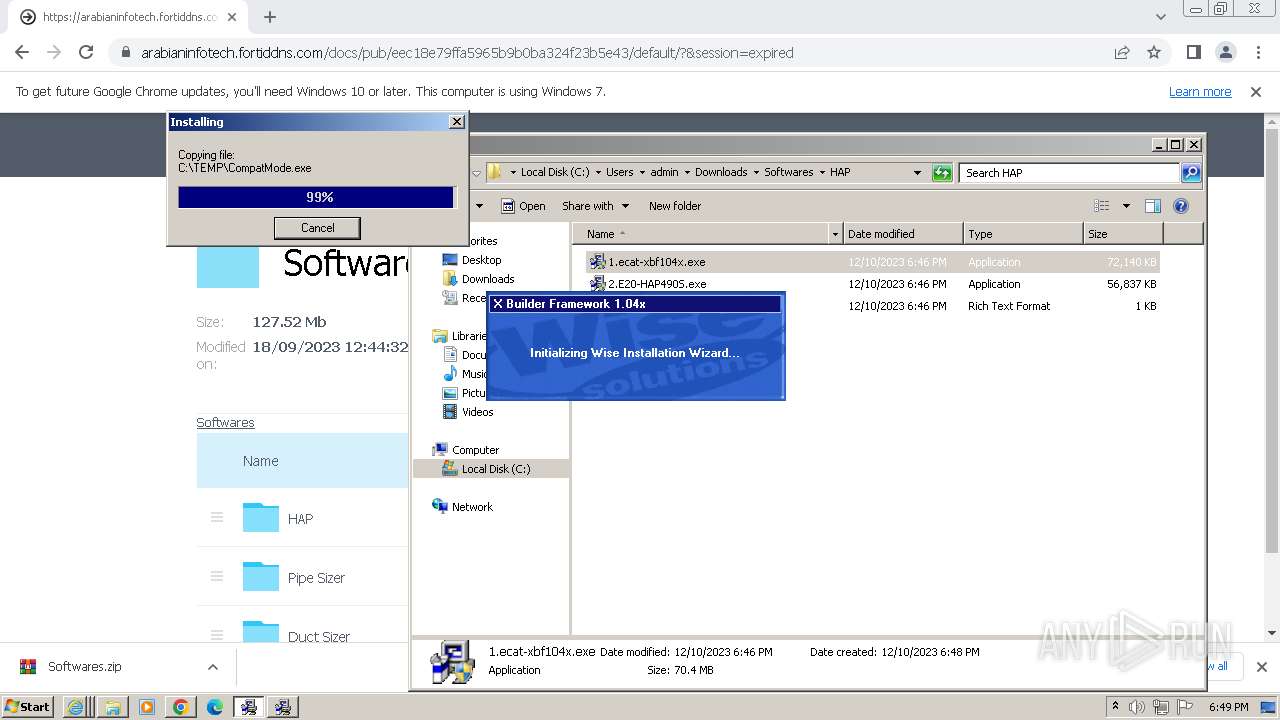
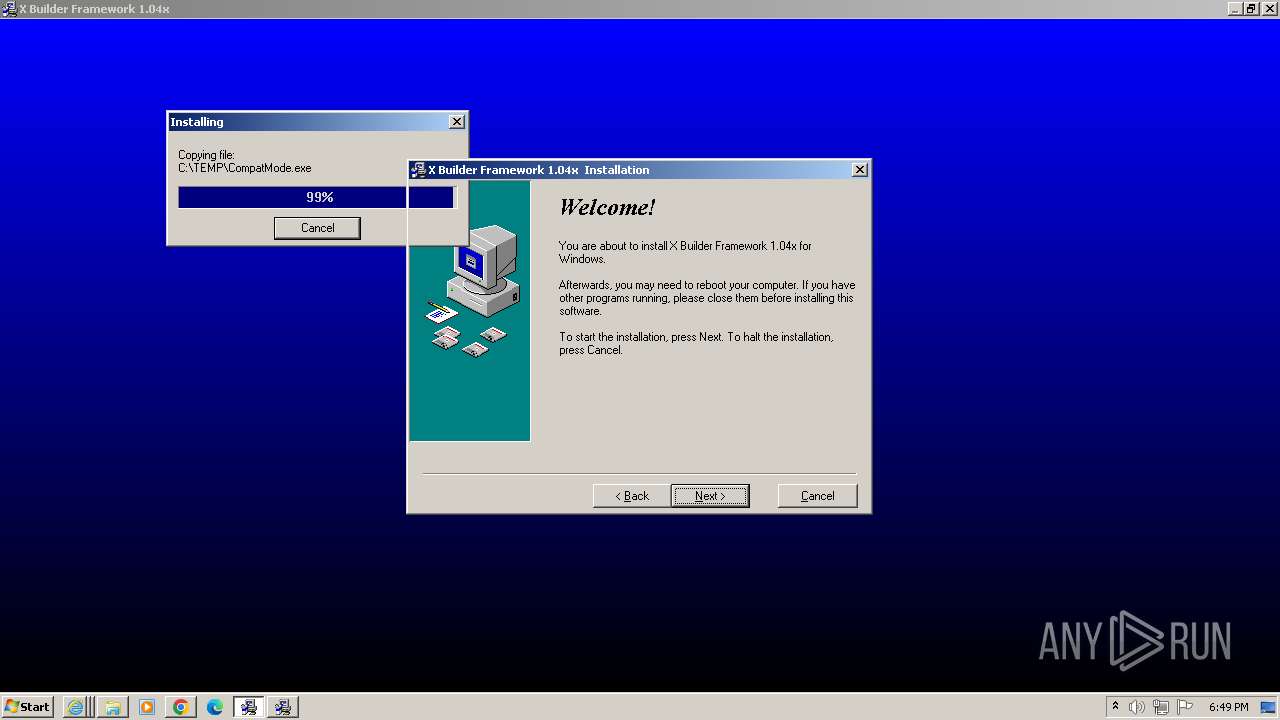
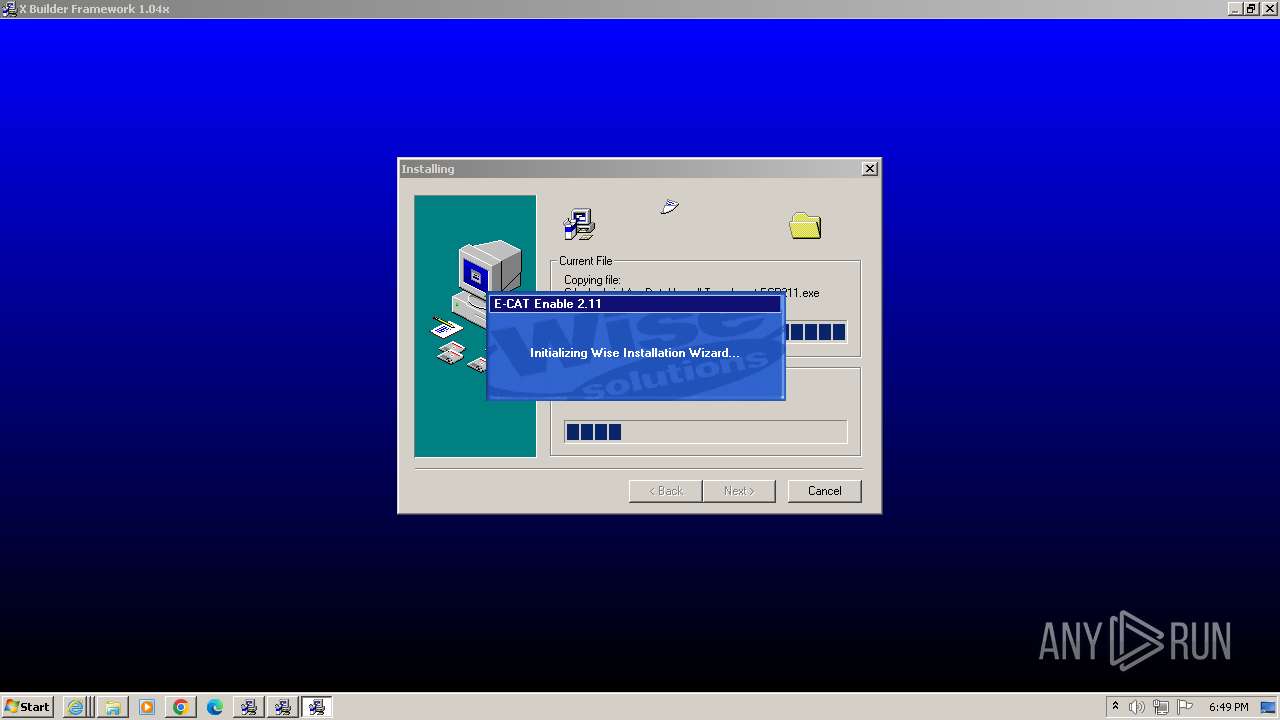
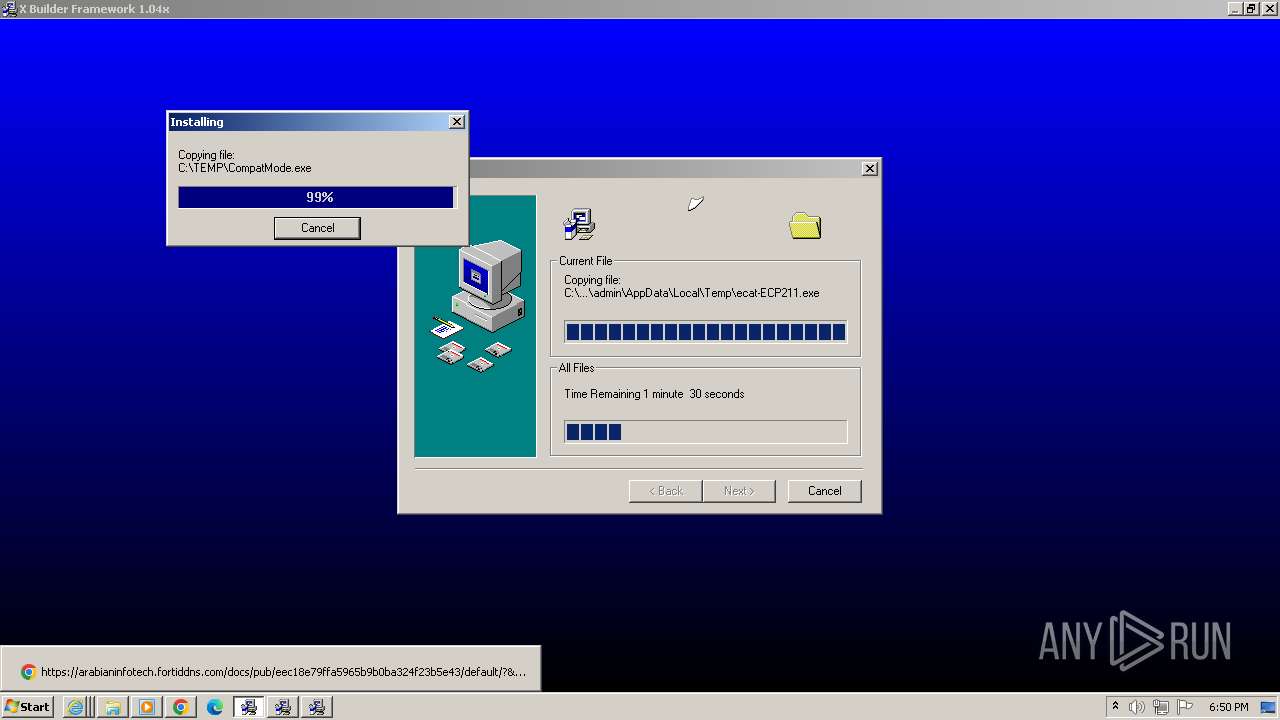
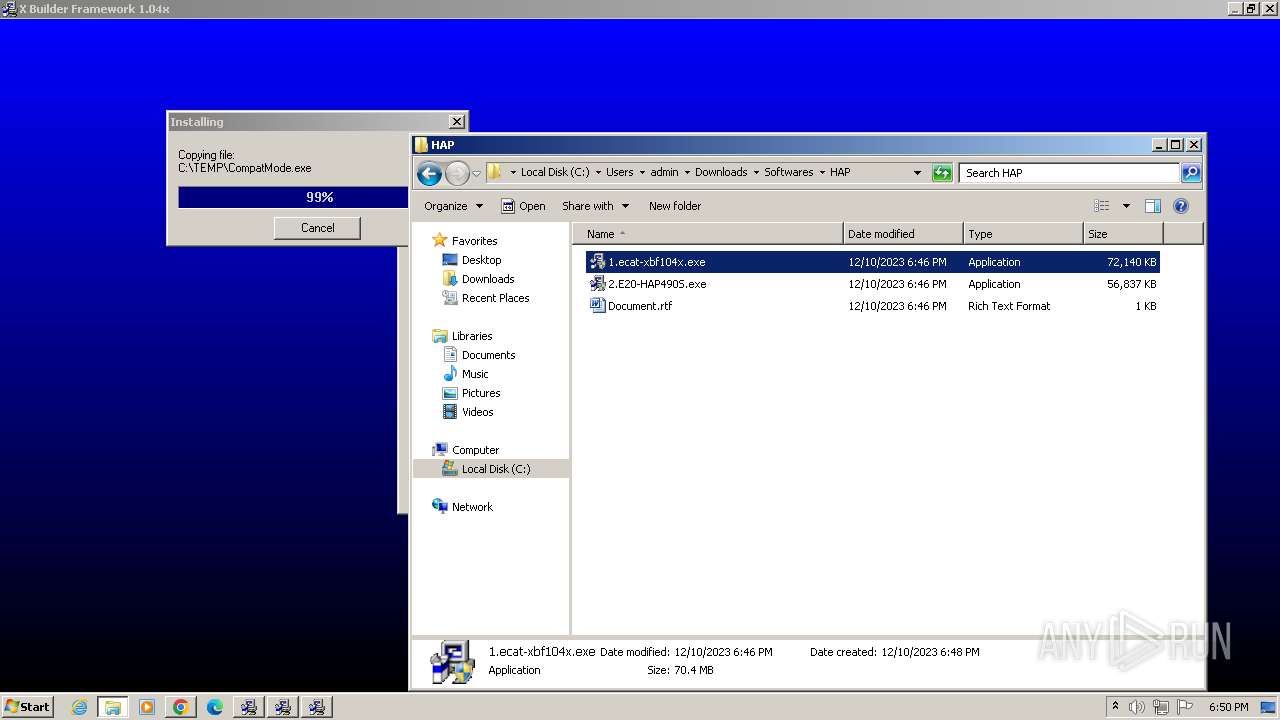
Drops the executable file immediately after the start
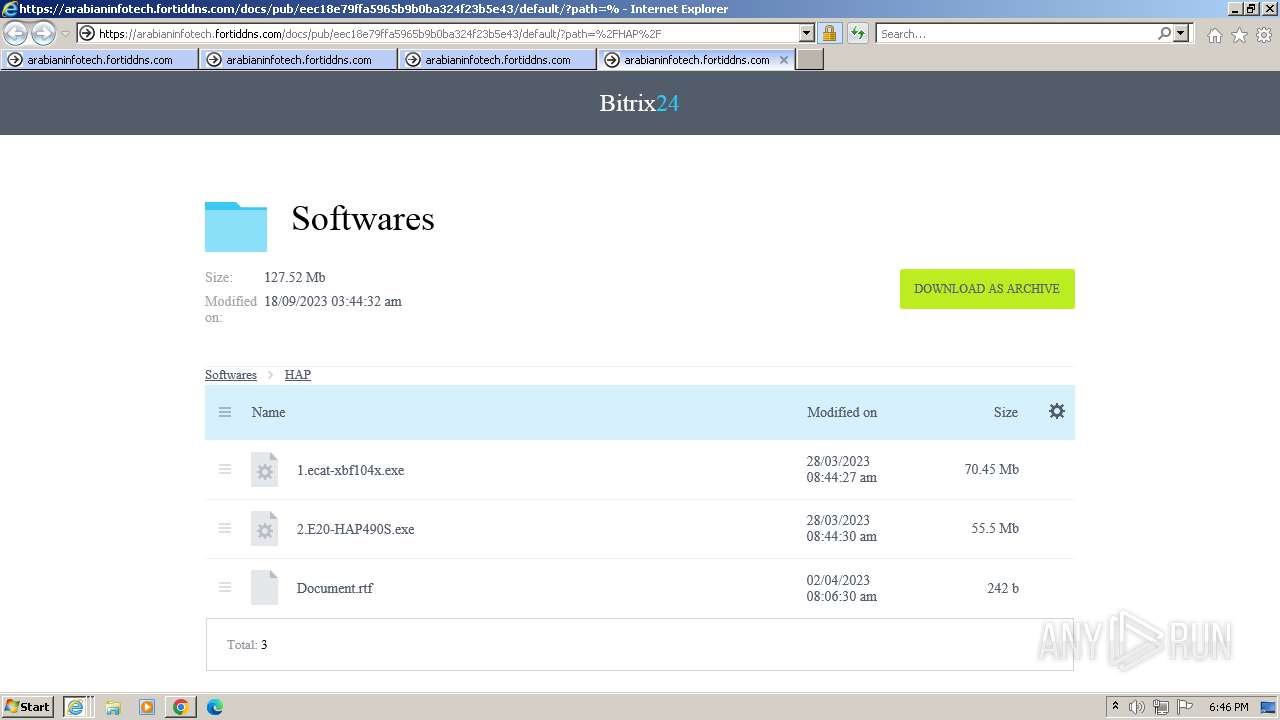
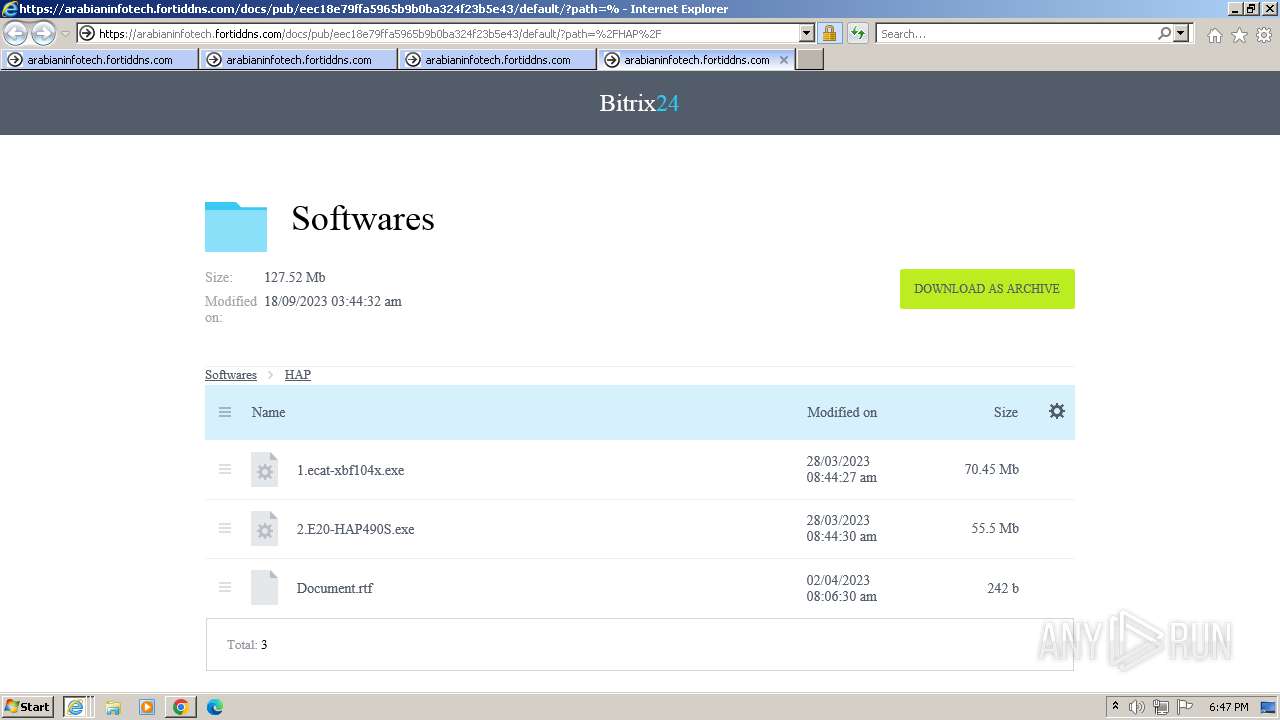
- 2.E20-HAP490S.exe (PID: 2300)
- HAP4.90S-[RC1]-unwrappered.exe (PID: 3388)
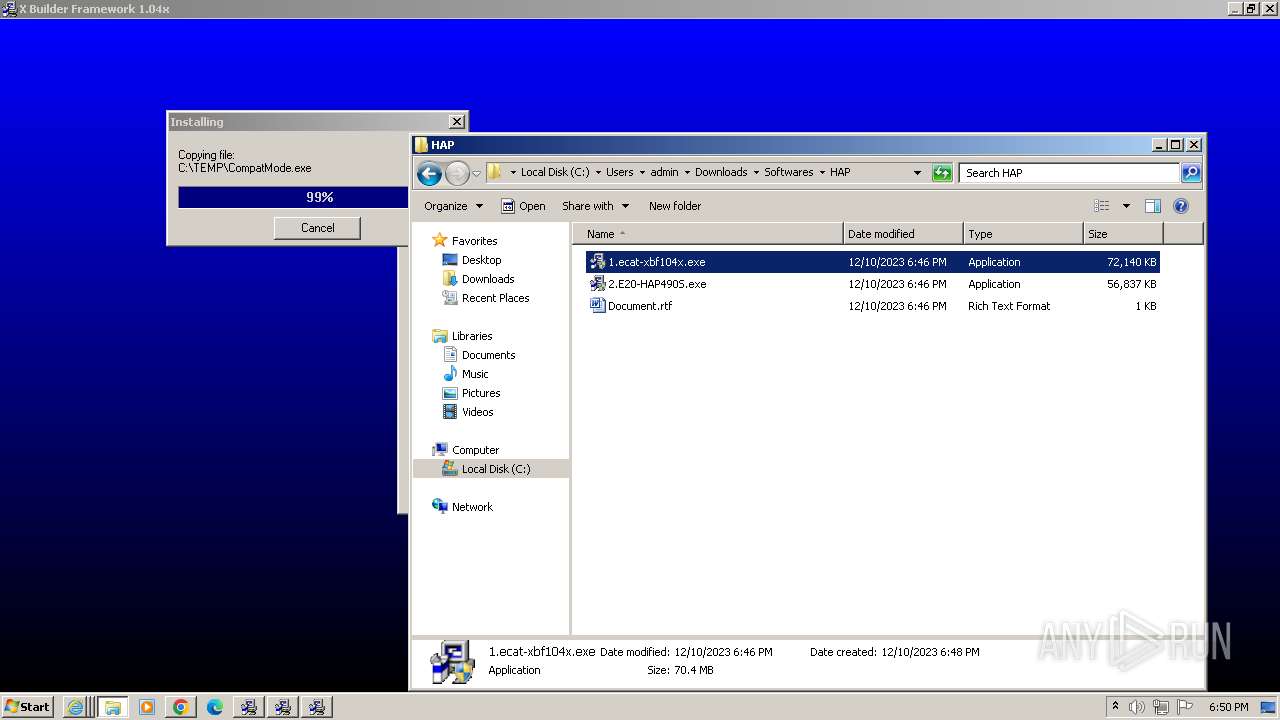
- 1.ecat-xbf104x.exe (PID: 1660)
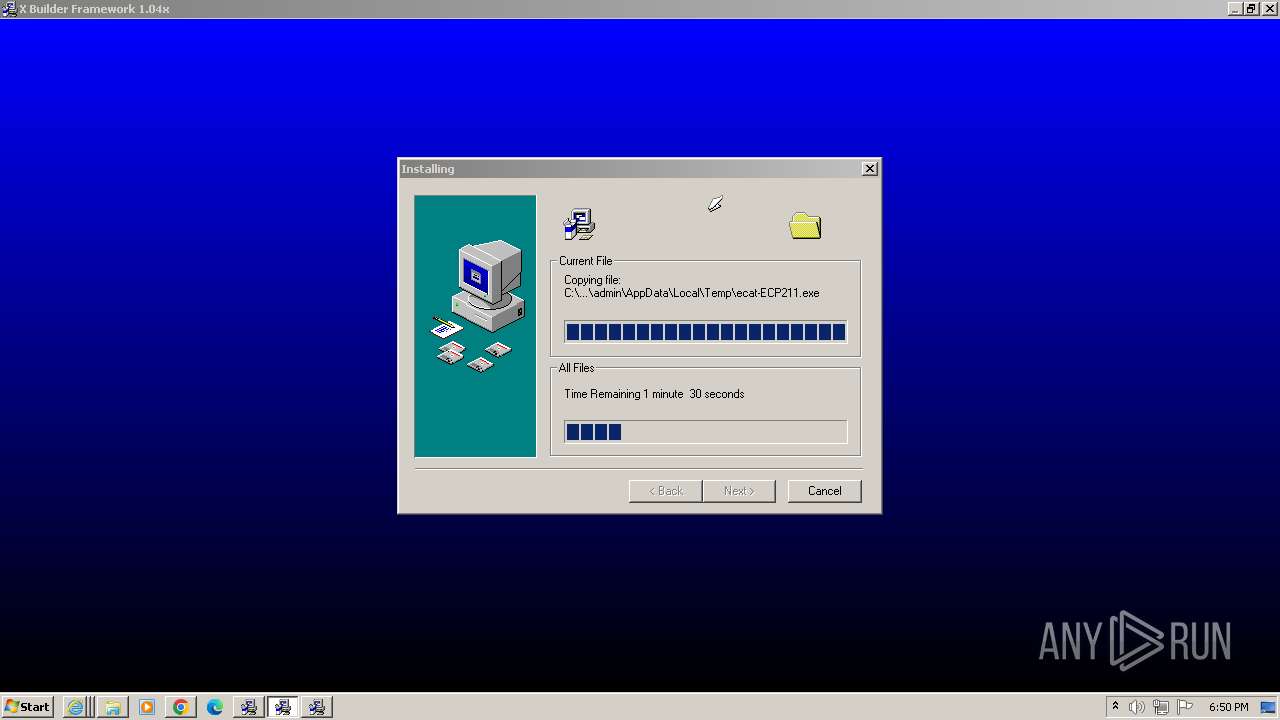
- ecat-ECP211.exe (PID: 1376)
- cat-xbf104x.exe (PID: 2960)
Creates a writable file in the system directory
- HAP4.90S-[RC1]-unwrappered.exe (PID: 3388)
- cat-xbf104x.exe (PID: 2960)
- ecat-ECP211.exe (PID: 1376)
SUSPICIOUS
Process drops legitimate windows executable
- chrome.exe (PID: 3848)
- cat-xbf104x.exe (PID: 2960)
Reads the Internet Settings
- 2.E20-HAP490S.exe (PID: 2300)
- 1.ecat-xbf104x.exe (PID: 1660)
- cat-xbf104x.exe (PID: 2960)
Starts application with an unusual extension
- ecat-ECP211.exe (PID: 1376)
- cat-xbf104x.exe (PID: 2960)
The process drops C-runtime libraries
- cat-xbf104x.exe (PID: 2960)
Creates/Modifies COM task schedule object
- GLJAEA1.tmp (PID: 3056)
INFO
Manual execution by a user
- wmpnscfg.exe (PID: 2764)
- chrome.exe (PID: 3848)
- msedge.exe (PID: 3536)
- WinRAR.exe (PID: 3456)
- WINWORD.EXE (PID: 2716)
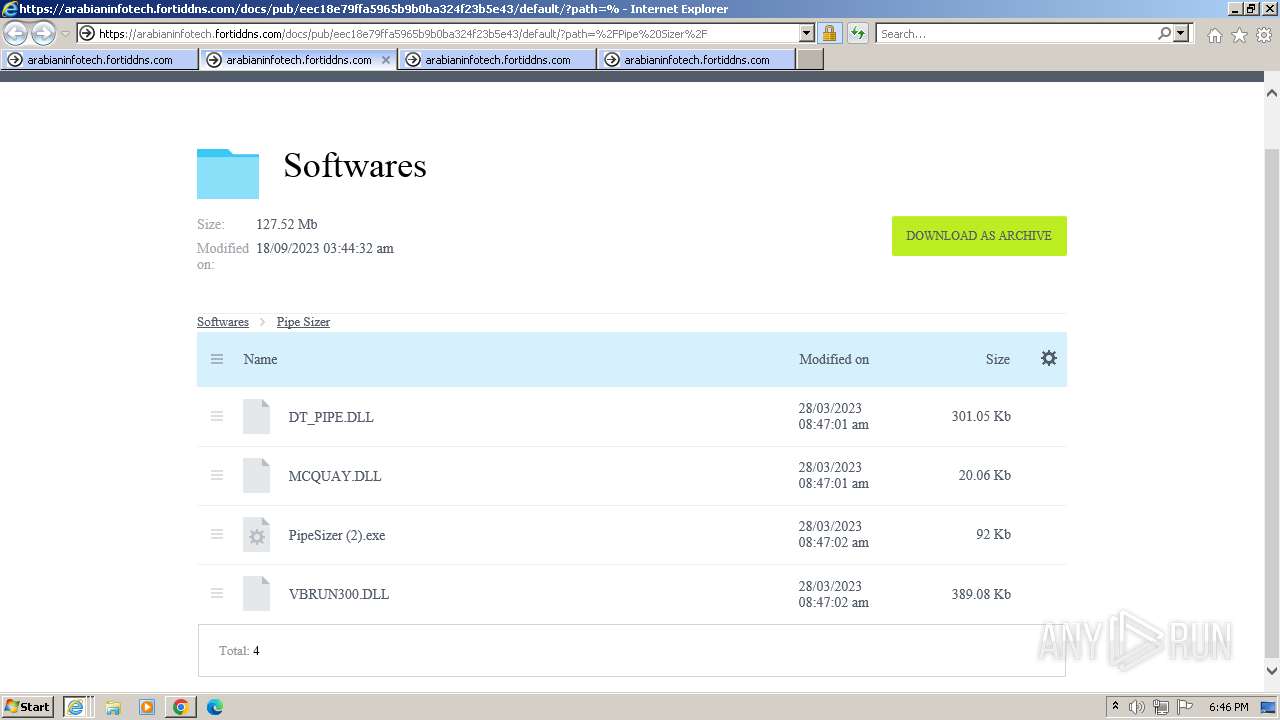
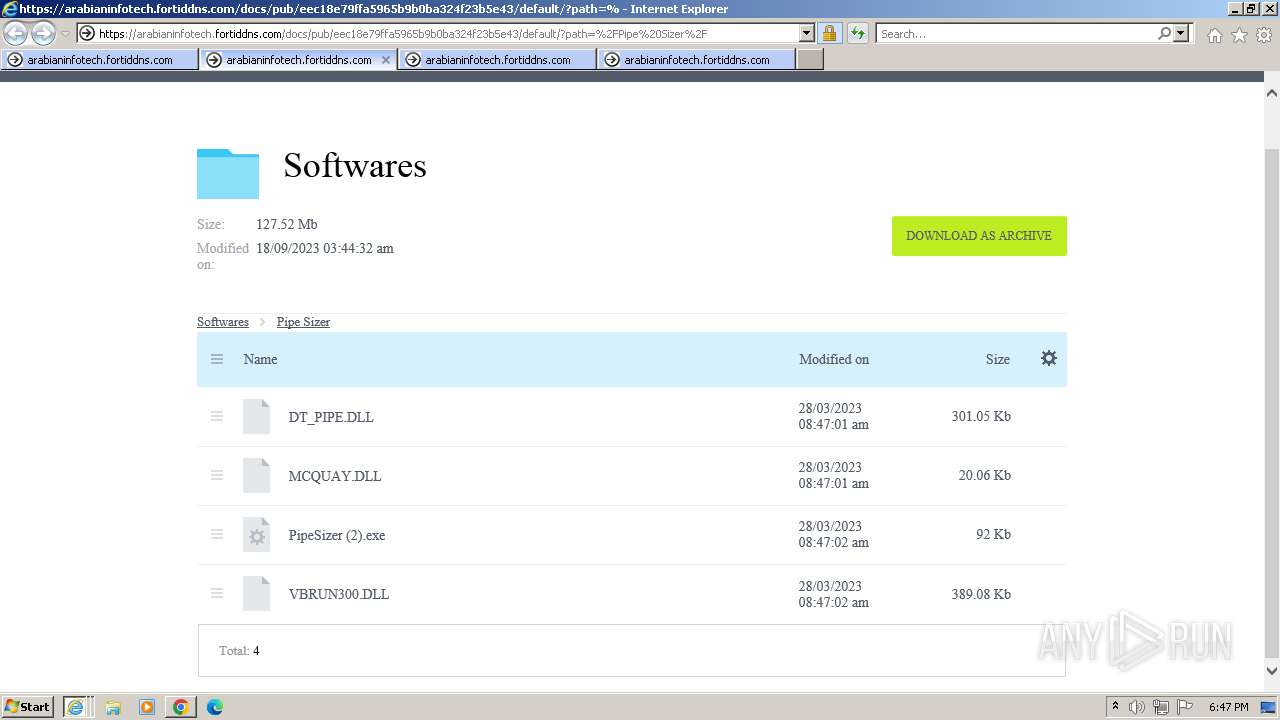
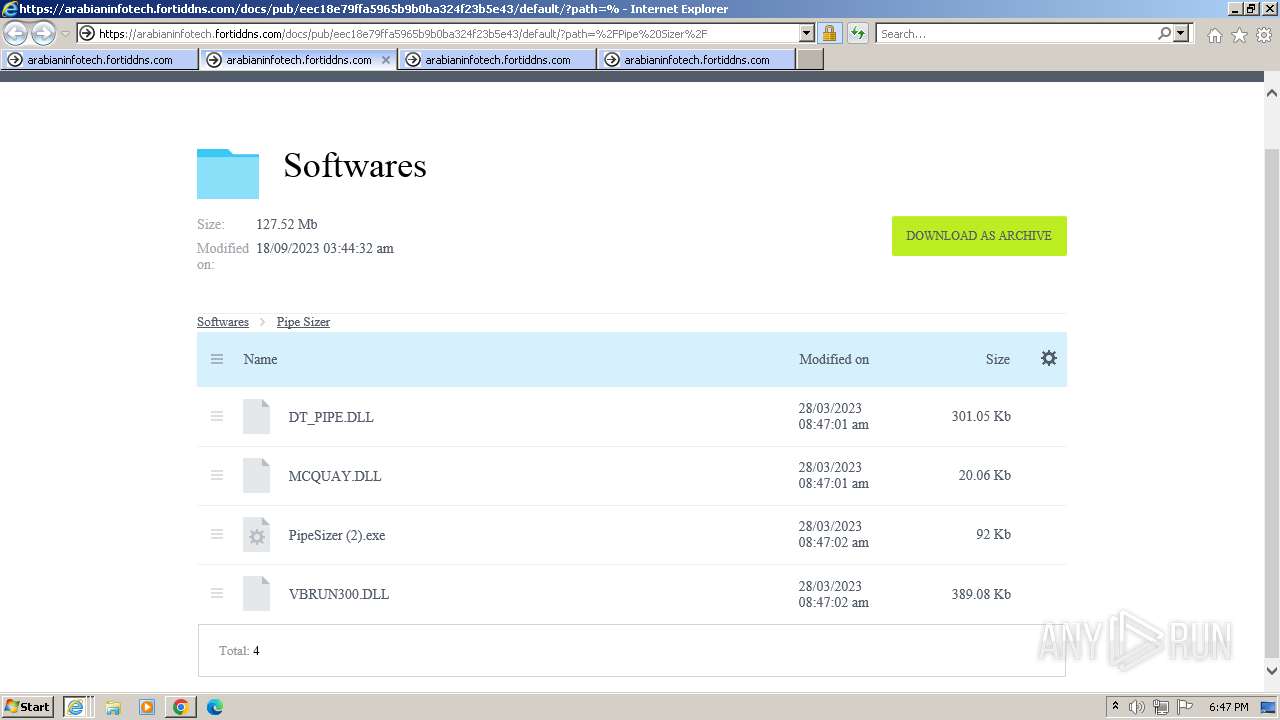
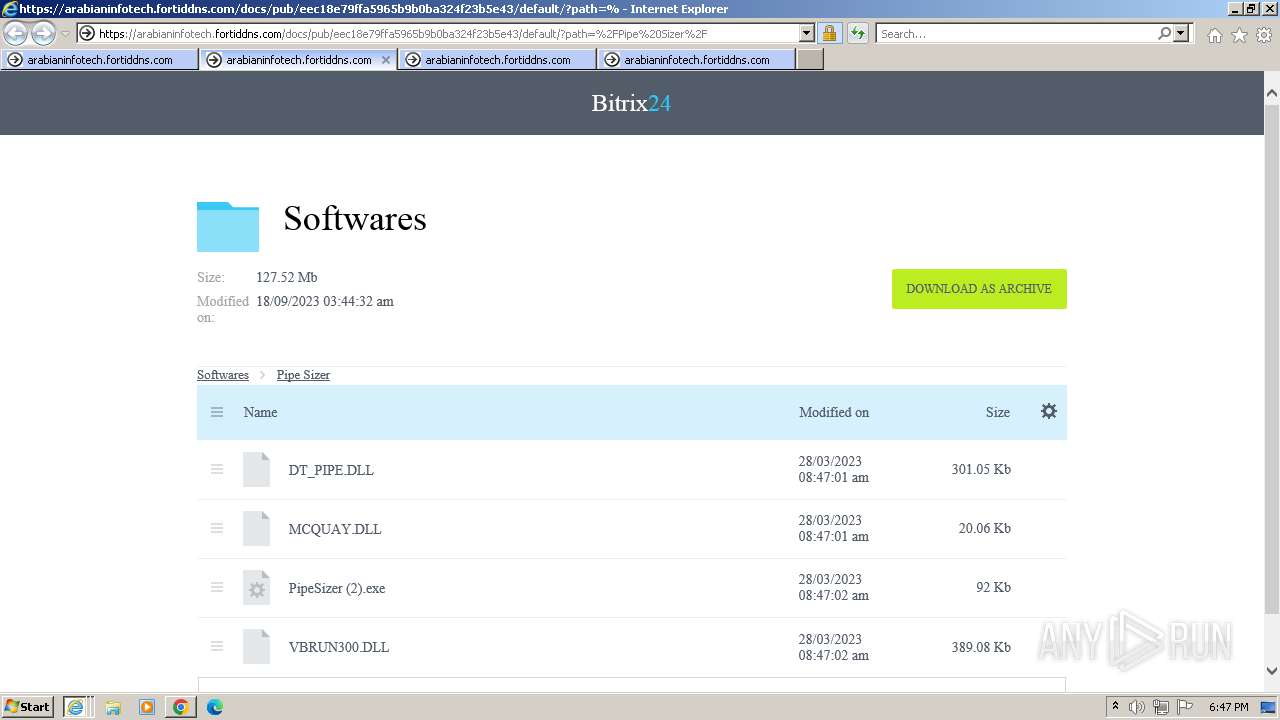
- PipeSizer (2).exe (PID: 2576)
- 2.E20-HAP490S.exe (PID: 2300)
- 1.ecat-xbf104x.exe (PID: 552)
- 1.ecat-xbf104x.exe (PID: 1660)
- 2.E20-HAP490S.exe (PID: 3508)
- PipeSizer (2).exe (PID: 3468)
Application launched itself
- iexplore.exe (PID: 280)
- chrome.exe (PID: 3848)
- msedge.exe (PID: 3536)
Reads the computer name
- wmpnscfg.exe (PID: 2764)
- 2.E20-HAP490S.exe (PID: 2300)
- HAP4.90S-[RC1]-unwrappered.exe (PID: 3388)
- 1.ecat-xbf104x.exe (PID: 1660)
- cat-xbf104x.exe (PID: 2960)
- ecat-ECP211.exe (PID: 1376)
- GLJ5D9.tmp (PID: 2308)
- GLJAEA1.tmp (PID: 2364)
- GLJAEA1.tmp (PID: 3944)
- GLJAEA1.tmp (PID: 2196)
- GLJAEA1.tmp (PID: 1600)
- GLJAEA1.tmp (PID: 1328)
- SSNDBU10.exe (PID: 1636)
- SSNDBU10.exe (PID: 2736)
- SSNDBU10.exe (PID: 2576)
- SSNDBU10.exe (PID: 2536)
- SSNDBU10.exe (PID: 3940)
- SSNDBU10.exe (PID: 3164)
- SSNDBU10.exe (PID: 600)
- GLJAEA1.tmp (PID: 1164)
- GLJAEA1.tmp (PID: 3660)
- GLJAEA1.tmp (PID: 2384)
- GLJAEA1.tmp (PID: 2236)
- GLJAEA1.tmp (PID: 3056)
- GLJAEA1.tmp (PID: 3148)
- GLJAEA1.tmp (PID: 3460)
- GLJAEA1.tmp (PID: 3452)
- GLJAEA1.tmp (PID: 2944)
- GLJAEA1.tmp (PID: 2088)
- GLJAEA1.tmp (PID: 2056)
- SSNDBU10.exe (PID: 1612)
- GLJAEA1.tmp (PID: 2516)
Checks supported languages
- wmpnscfg.exe (PID: 2764)
- PipeSizer (2).exe (PID: 2576)
- 2.E20-HAP490S.exe (PID: 2300)
- HAP4.90S-[RC1]-unwrappered.exe (PID: 3388)
- ECAT602.exe (PID: 2676)
- CompatMode.exe (PID: 3200)
- 1.ecat-xbf104x.exe (PID: 1660)
- ECAT271.exe (PID: 2448)
- CompatMode.exe (PID: 2072)
- FWRunning.exe (PID: 3124)
- XBGetRegion10.exe (PID: 1432)
- CompatMode.exe (PID: 3356)
- ecat-ECP211.exe (PID: 1376)
- GLJ5D9.tmp (PID: 2308)
- PipeSizer (2).exe (PID: 3468)
- GLJAEA1.tmp (PID: 2364)
- GLJAEA1.tmp (PID: 3396)
- GLJAEA1.tmp (PID: 3944)
- GLJAEA1.tmp (PID: 4012)
- GLJAEA1.tmp (PID: 3716)
- GLJAEA1.tmp (PID: 3812)
- GLJAEA1.tmp (PID: 4040)
- GLJAEA1.tmp (PID: 4004)
- GLJAEA1.tmp (PID: 3108)
- GLJAEA1.tmp (PID: 2468)
- GLJAEA1.tmp (PID: 3372)
- cat-xbf104x.exe (PID: 2960)
- GLJAEA1.tmp (PID: 1696)
- GLJAEA1.tmp (PID: 3412)
- GLJAEA1.tmp (PID: 3228)
- GLJAEA1.tmp (PID: 3728)
- GLJAEA1.tmp (PID: 2060)
- GLJAEA1.tmp (PID: 2196)
- GLJAEA1.tmp (PID: 1600)
- GLJAEA1.tmp (PID: 3572)
- GLJAEA1.tmp (PID: 1328)
- SSNDBU10.exe (PID: 1636)
- SSNDBU10.exe (PID: 2736)
- GLJAEA1.tmp (PID: 2876)
- SSNDBU10.exe (PID: 2536)
- SSNDBU10.exe (PID: 600)
- SSNDBU10.exe (PID: 2576)
- GLJAEA1.tmp (PID: 2952)
- SSNDBU10.exe (PID: 3940)
- SSNDBU10.exe (PID: 1612)
- CompatMode.exe (PID: 2500)
- GLJAEA1.tmp (PID: 3660)
- GLJAEA1.tmp (PID: 3892)
- GLJAEA1.tmp (PID: 2516)
- GLJAEA1.tmp (PID: 1164)
- GLJAEA1.tmp (PID: 1668)
- GLJAEA1.tmp (PID: 2916)
- GLJAEA1.tmp (PID: 2384)
- GLJAEA1.tmp (PID: 3056)
- GLJAEA1.tmp (PID: 3148)
- GLJAEA1.tmp (PID: 3460)
- GLJAEA1.tmp (PID: 1072)
- GLJAEA1.tmp (PID: 900)
- GLJAEA1.tmp (PID: 2236)
- GLJAEA1.tmp (PID: 3224)
- GLJAEA1.tmp (PID: 3452)
- GLJAEA1.tmp (PID: 1756)
- GLJAEA1.tmp (PID: 2944)
- GLJAEA1.tmp (PID: 2088)
- GLJAEA1.tmp (PID: 2996)
- GLJAEA1.tmp (PID: 1900)
- GLJAEA1.tmp (PID: 3868)
- GLJAEA1.tmp (PID: 3904)
- GLJAEA1.tmp (PID: 3960)
- GLJAEA1.tmp (PID: 2056)
- GLJAEA1.tmp (PID: 3144)
- GLJAEA1.tmp (PID: 1296)
- RemovePDSG.exe (PID: 3656)
- SSNDBU10.exe (PID: 3164)
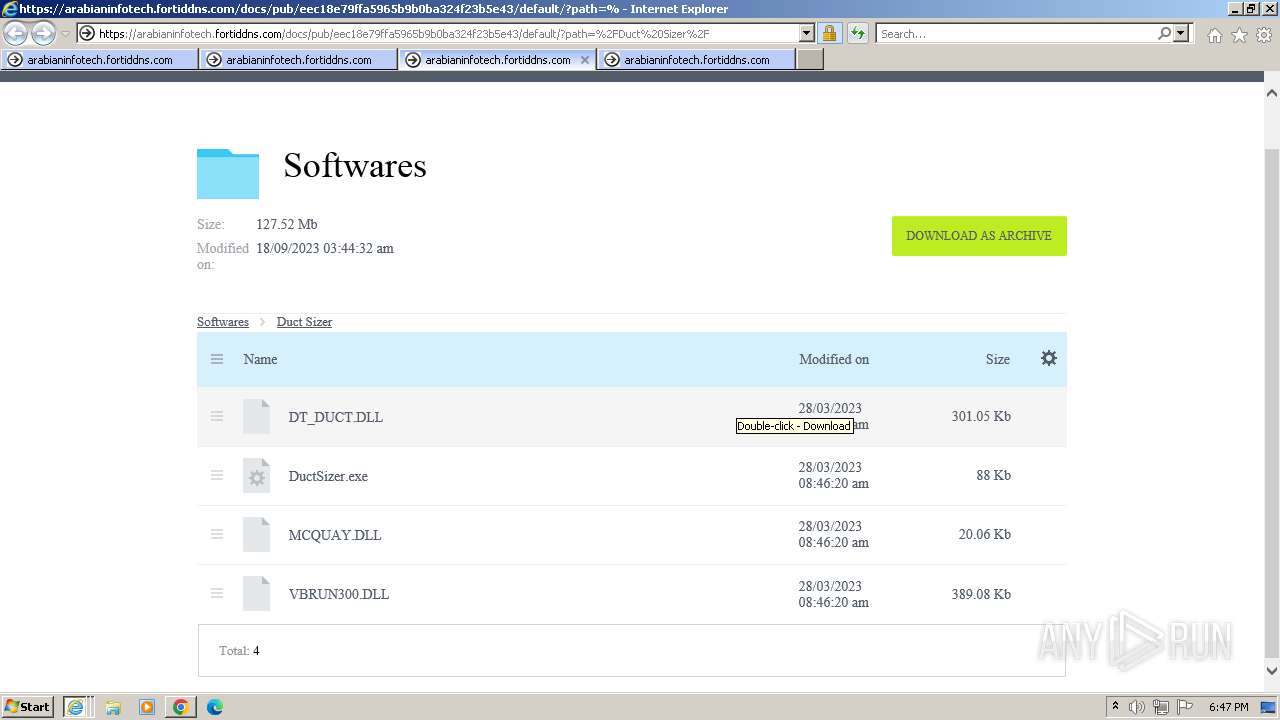
The process uses the downloaded file
- WinRAR.exe (PID: 3456)
- chrome.exe (PID: 3812)
Drops the executable file immediately after the start
- chrome.exe (PID: 3848)
- WinRAR.exe (PID: 3456)
- chrome.exe (PID: 3028)
Create files in a temporary directory
- PipeSizer (2).exe (PID: 2576)
- 2.E20-HAP490S.exe (PID: 2300)
- HAP4.90S-[RC1]-unwrappered.exe (PID: 3388)
- 1.ecat-xbf104x.exe (PID: 1660)
- cat-xbf104x.exe (PID: 2960)
- ecat-ECP211.exe (PID: 1376)
- PipeSizer (2).exe (PID: 3468)
- SSNDBU10.exe (PID: 2736)
- SSNDBU10.exe (PID: 1636)
- SSNDBU10.exe (PID: 3940)
- SSNDBU10.exe (PID: 600)
- SSNDBU10.exe (PID: 2576)
- SSNDBU10.exe (PID: 2536)
- GLJAEA1.tmp (PID: 3144)
- SSNDBU10.exe (PID: 3164)
- SSNDBU10.exe (PID: 1612)
Reads the machine GUID from the registry
- PipeSizer (2).exe (PID: 2576)
- PipeSizer (2).exe (PID: 3468)
Creates files in the program directory
- cat-xbf104x.exe (PID: 2960)
Reads mouse settings
- GLJAEA1.tmp (PID: 3148)
- GLJAEA1.tmp (PID: 3056)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
166
Monitored processes
114
Malicious processes
7
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 280 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://arabianinfotech.fortiddns.com/~ROlah" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 328 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=10 --mojo-platform-channel-handle=3412 --field-trial-handle=1196,i,13918228077457387822,2871952095311760365,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 372 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=109.0.5414.120 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd4,0x68778b38,0x68778b48,0x68778b54 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
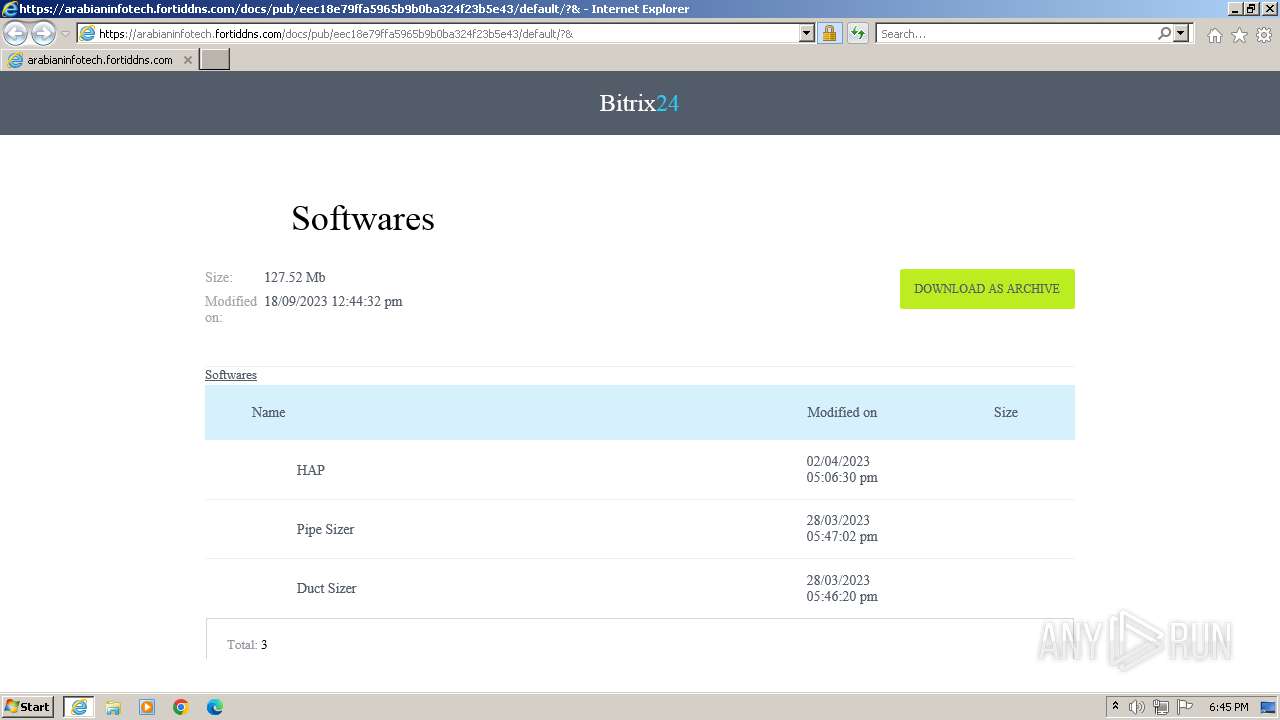
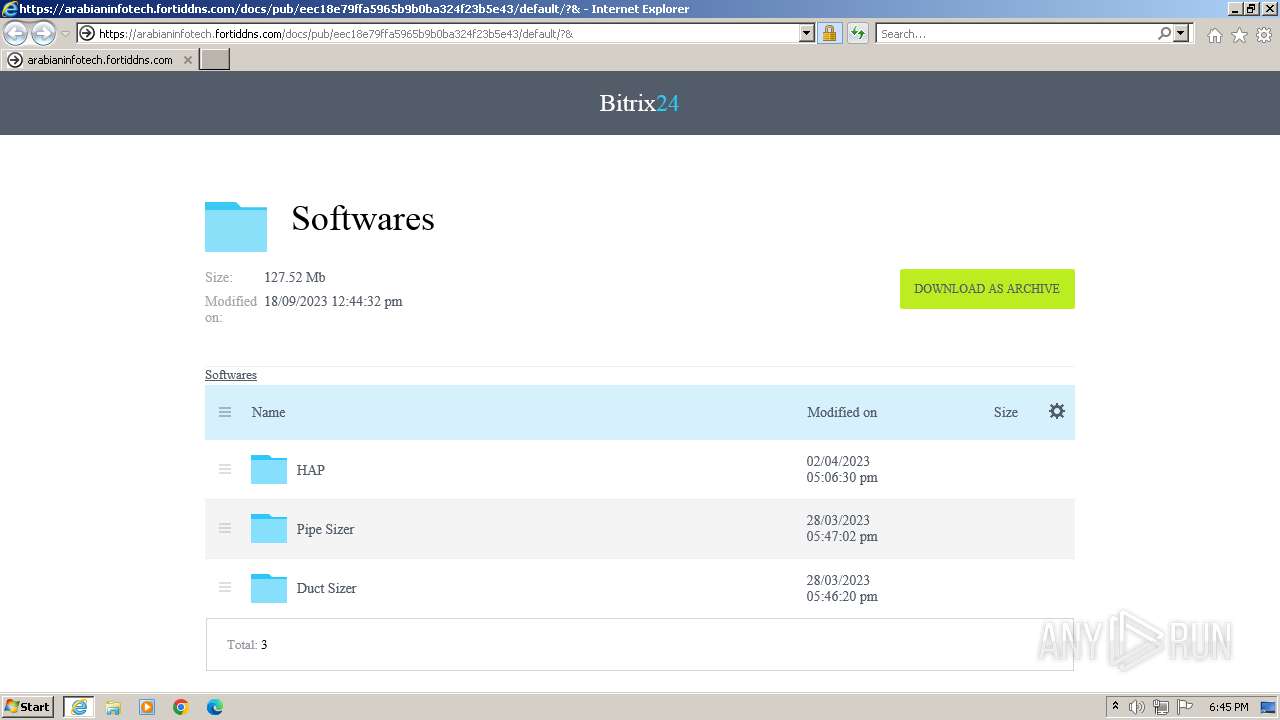
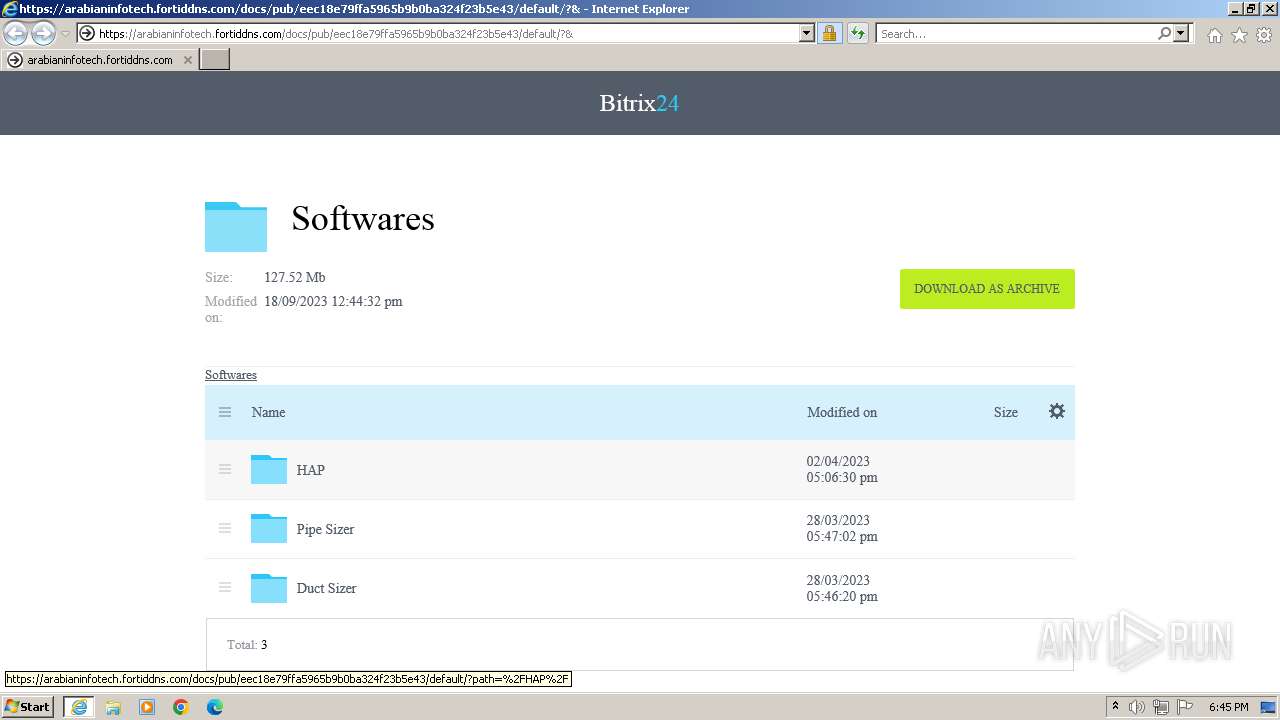
| 552 | "C:\Users\admin\Downloads\Softwares\HAP\1.ecat-xbf104x.exe" | C:\Users\admin\Downloads\Softwares\HAP\1.ecat-xbf104x.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 600 | "C:\E20-II\SSNDBU10.exe" C:\E20-II\CSI11INS.INI | C:\E20-II\SSNDBU10.exe | cat-xbf104x.exe | ||||||||||||
User: admin Company: Carrier Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 644 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:280 CREDAT:529674 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 756 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=1664 --field-trial-handle=1136,i,1208315743500171429,967208159774883709,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 900 | "C:\Users\admin\AppData\Local\Temp\GLJAEA1.tmp" C:\Windows\System32\comcat.dll | C:\Users\admin\AppData\Local\Temp\GLJAEA1.tmp | cat-xbf104x.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1072 | "C:\Users\admin\AppData\Local\Temp\GLJAEA1.tmp" C:\Windows\System32\msxml3.dll | C:\Users\admin\AppData\Local\Temp\GLJAEA1.tmp | cat-xbf104x.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1164 | "C:\Users\admin\AppData\Local\Temp\GLJAEA1.tmp" C:\E20-II\ENVIRO\CSI11.dll | C:\Users\admin\AppData\Local\Temp\GLJAEA1.tmp | cat-xbf104x.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
48 590
Read events
48 003
Write events
322
Delete events
265
Modification events
| (PID) Process: | (280) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (280) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (280) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (280) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (280) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (280) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (280) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (280) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (280) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (280) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
468
Suspicious files
535
Text files
206
Unknown types
107
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2136 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CE7B026C819922EDB9B7ED78605E20A3_AF7F10BA33CEEF74214EEC8D707EB0CD | binary | |
MD5:35E8464A1CE2BD3D67A1662673799932 | SHA256:0B09B7E6BF88A211C6BA964074859A77122CDBB77BE9D808F9E97D40959D4570 | |||
| 2136 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 2136 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\ui.design-tokens.min[1].css | text | |
MD5:8178992021C7160F587A2BFB4EE68011 | SHA256:82B3457E90BC5418C672127C440E8A8A9BDC72CBCDE7672ADC98BA94A7CE0334 | |||
| 2136 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\54C62B182F5BF07FA8427C07B0A3AAF8_786EA6C36BF7ABFF201B638497282D19 | binary | |
MD5:BDEEF42C63C4642B2259FC3AA1427FDC | SHA256:E77D8350CDA2185BB4802E779599E85E1AC8F35D083341E872875DF542D2AC96 | |||
| 2136 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\main.popup.bundle.min[1].css | text | |
MD5:5881391F45CAFD2FC858E3F14E54B9F4 | SHA256:0E9B826DEA54F30650091A0547B60614C8D8C90203724AAC05F07461C68C234C | |||
| 2136 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\ui.font.opensans.min[1].css | text | |
MD5:82527A21ACABA47E5E9D367437D64428 | SHA256:47D42F9F412D0C8854BFED1C7B1B433EAF6DF4D0D67E7619EE6C9CB7B0289C90 | |||
| 2136 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\54C62B182F5BF07FA8427C07B0A3AAF8_786EA6C36BF7ABFF201B638497282D19 | der | |
MD5:1731B881960AC78FBBC0FFE5ACDCD598 | SHA256:E8C9CB8012AA47F312FF30B97CD254470E1494D511EE1DB9E31FE7722D68AA7C | |||
| 2136 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\kernel_ui_actionpanel_v1[1].css | text | |
MD5:875D4914EA93C59B6FEED4F206DB1042 | SHA256:5D760BD8F4FCB14DFDEF39A2745DFF4D11CBBAE14324AAC875E1ED23CC41749F | |||
| 2136 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\style.min[1].css | text | |
MD5:94C7D305D33C2DD3AA19E8C46E80EA99 | SHA256:5CD2D41C7C8FBD543AD56E250EACC31C3C639CC608E7C85EF5D2F683D60AFC39 | |||
| 2136 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\kernel_ui_notification_v1[1].css | text | |
MD5:B8F681C8712865BF66D858192F28276E | SHA256:703F8B75727E28D225519AB0FAD531BCD731CBF7145C3CC2434D2CBA90DF936D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
78
TCP/UDP connections
76
DNS requests
84
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
280 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
2136 | iexplore.exe | GET | 200 | 52.6.97.148:80 | http://ocsps.ssl.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTUkpS%2BK0oZhSMx%2FmmCZ76UqdjUxQQUJhR%2B4NzXpvfi1AQn32HxwuznMsoCEEzIi4BfbVSq%2Fo8GLSr%2FMe4%3D | unknown | binary | 1.77 Kb | unknown |
280 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | binary | 313 b | unknown |
280 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | binary | 471 b | unknown |
868 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ad3rm3ciqs3fjr4bc4x5vwuildeq_9.49.1/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.49.1_all_ixzyrcu7pvmgu5pjv6enfqq6wa.crx3 | unknown | — | — | unknown |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ad3rm3ciqs3fjr4bc4x5vwuildeq_9.49.1/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.49.1_all_ixzyrcu7pvmgu5pjv6enfqq6wa.crx3 | unknown | binary | 5.40 Kb | unknown |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ad3rm3ciqs3fjr4bc4x5vwuildeq_9.49.1/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.49.1_all_ixzyrcu7pvmgu5pjv6enfqq6wa.crx3 | unknown | binary | 7.62 Kb | unknown |
280 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAqvpsXKY8RRQeo74ffHUxc%3D | unknown | binary | 471 b | unknown |
280 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA177el9ggmWelJjG4vdGL0%3D | unknown | binary | 471 b | unknown |
1080 | svchost.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?d3beddd762d67162 | unknown | compressed | 65.2 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2136 | iexplore.exe | 86.98.52.11:443 | arabianinfotech.fortiddns.com | Emirates Telecommunications Corporation | AE | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2136 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2136 | iexplore.exe | 52.6.97.148:80 | ocsps.ssl.com | AMAZON-AES | US | unknown |
280 | iexplore.exe | 86.98.52.11:443 | arabianinfotech.fortiddns.com | Emirates Telecommunications Corporation | AE | unknown |
280 | iexplore.exe | 2.16.100.24:443 | www.bing.com | Akamai International B.V. | DE | unknown |
280 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
arabianinfotech.fortiddns.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsps.ssl.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
ntp.msn.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
Threats
Process | Message |
|---|---|
HAP4.90S-[RC1]-unwrappered.exe | FTH: (3388): *** Fault tolerant heap shim applied to current process. This is usually due to previous crashes. ***
|
cat-xbf104x.exe | FTH: (2960): *** Fault tolerant heap shim applied to current process. This is usually due to previous crashes. ***
|
FWRunning.exe | FTH: (3124): *** Fault tolerant heap shim applied to current process. This is usually due to previous crashes. ***
|
XBGetRegion10.exe | FTH: (1432): *** Fault tolerant heap shim applied to current process. This is usually due to previous crashes. ***
|
CompatMode.exe | FTH: (3356): *** Fault tolerant heap shim applied to current process. This is usually due to previous crashes. ***
|
ecat-ECP211.exe | FTH: (1376): *** Fault tolerant heap shim applied to current process. This is usually due to previous crashes. ***
|
GLJ5D9.tmp | FTH: (2308): *** Fault tolerant heap shim applied to current process. This is usually due to previous crashes. ***
|
GLJAEA1.tmp | FTH: (2364): *** Fault tolerant heap shim applied to current process. This is usually due to previous crashes. ***
|
GLJAEA1.tmp | FTH: (2952): *** Fault tolerant heap shim applied to current process. This is usually due to previous crashes. ***
|
GLJAEA1.tmp | FTH: (3396): *** Fault tolerant heap shim applied to current process. This is usually due to previous crashes. ***
|