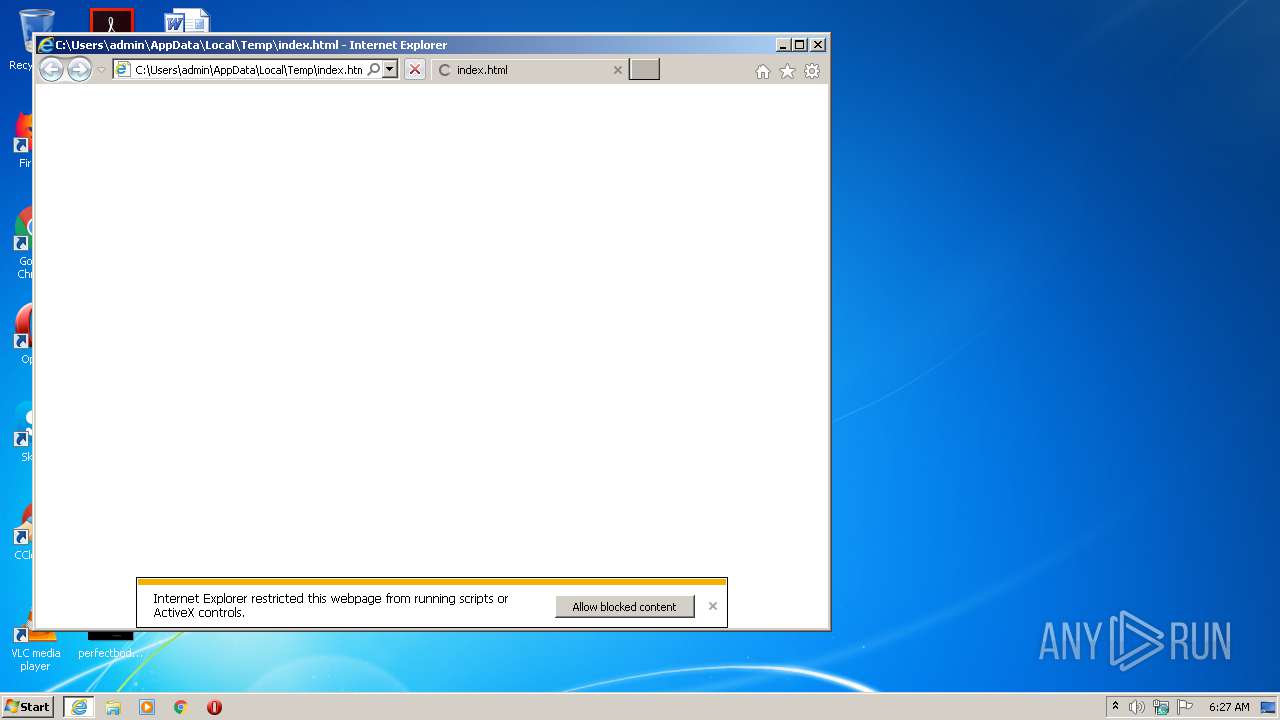
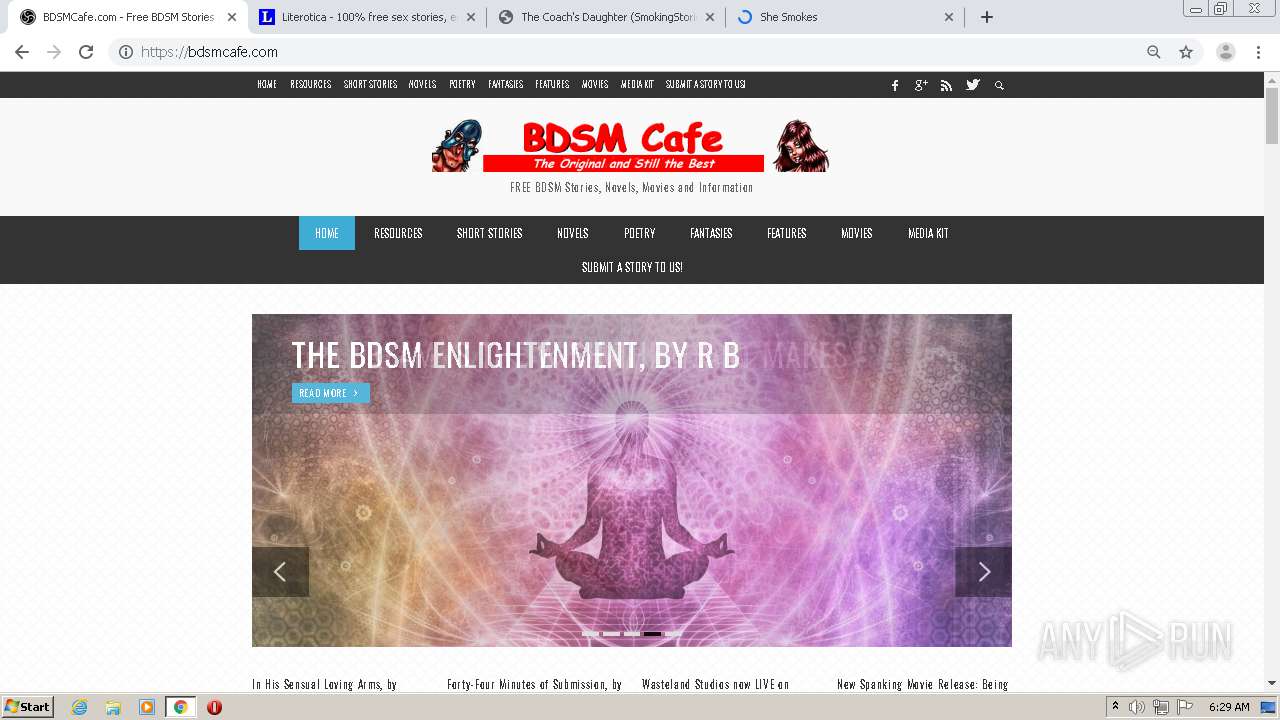
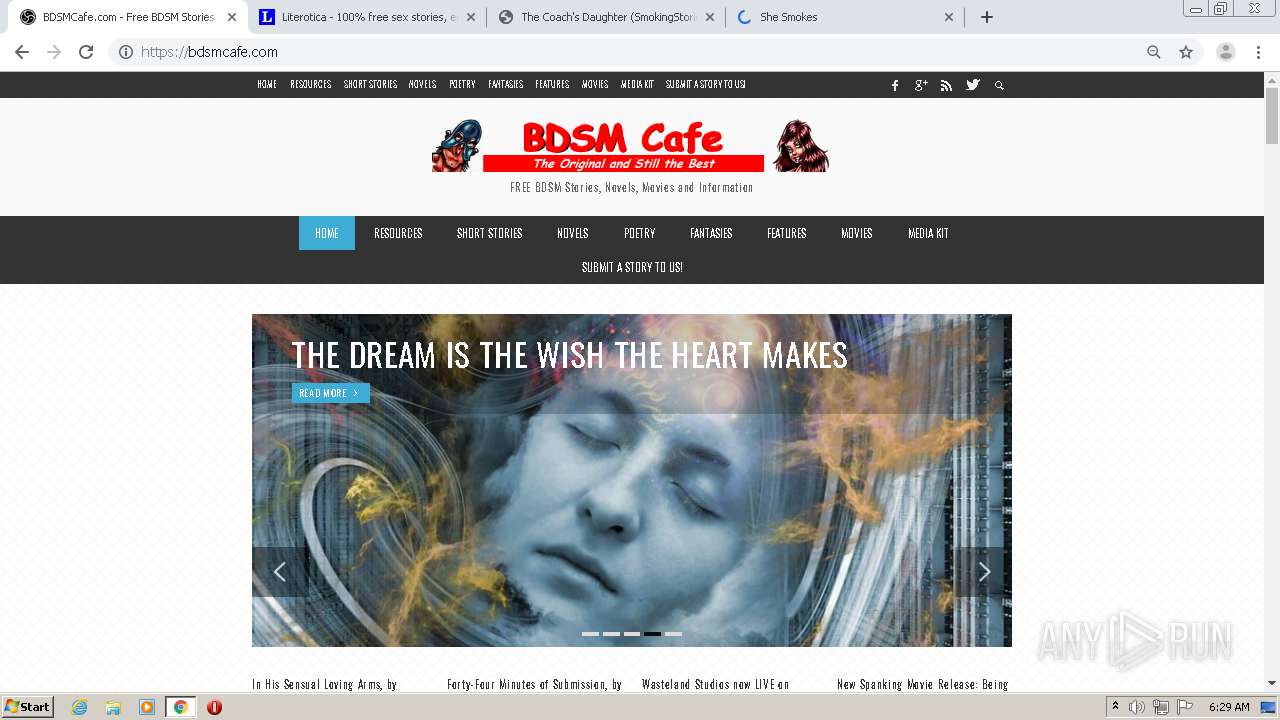
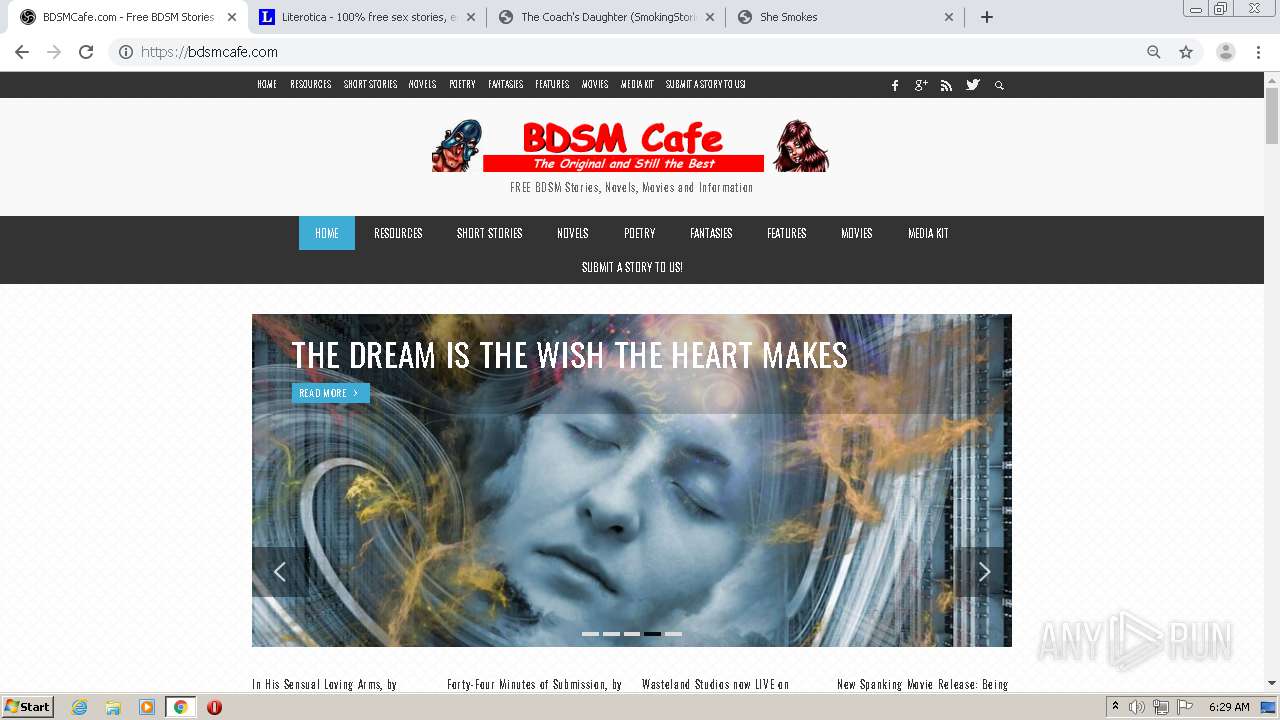
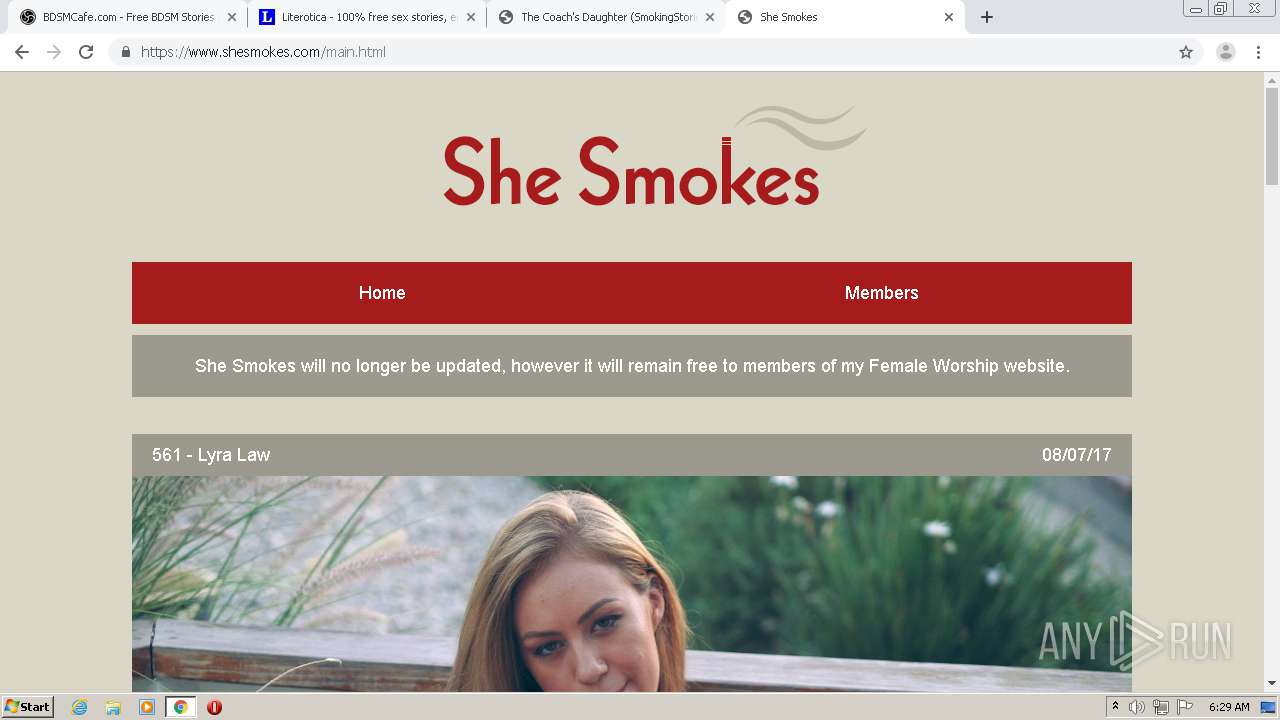
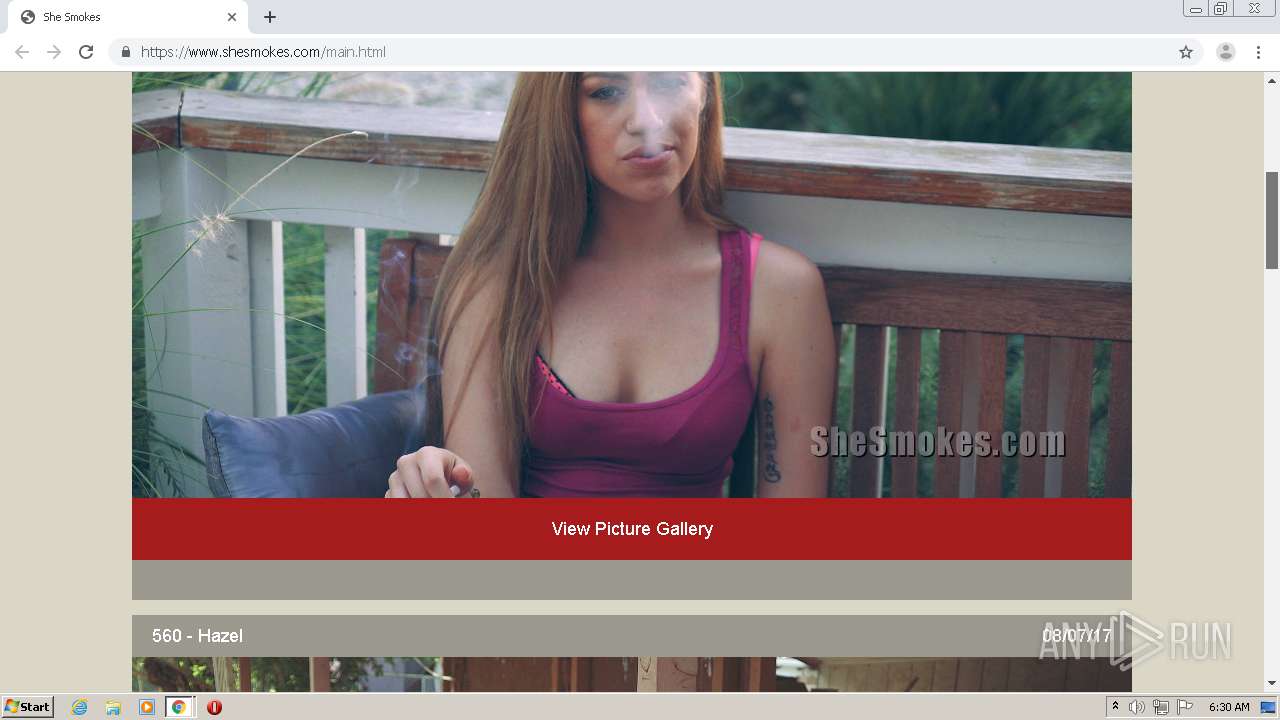
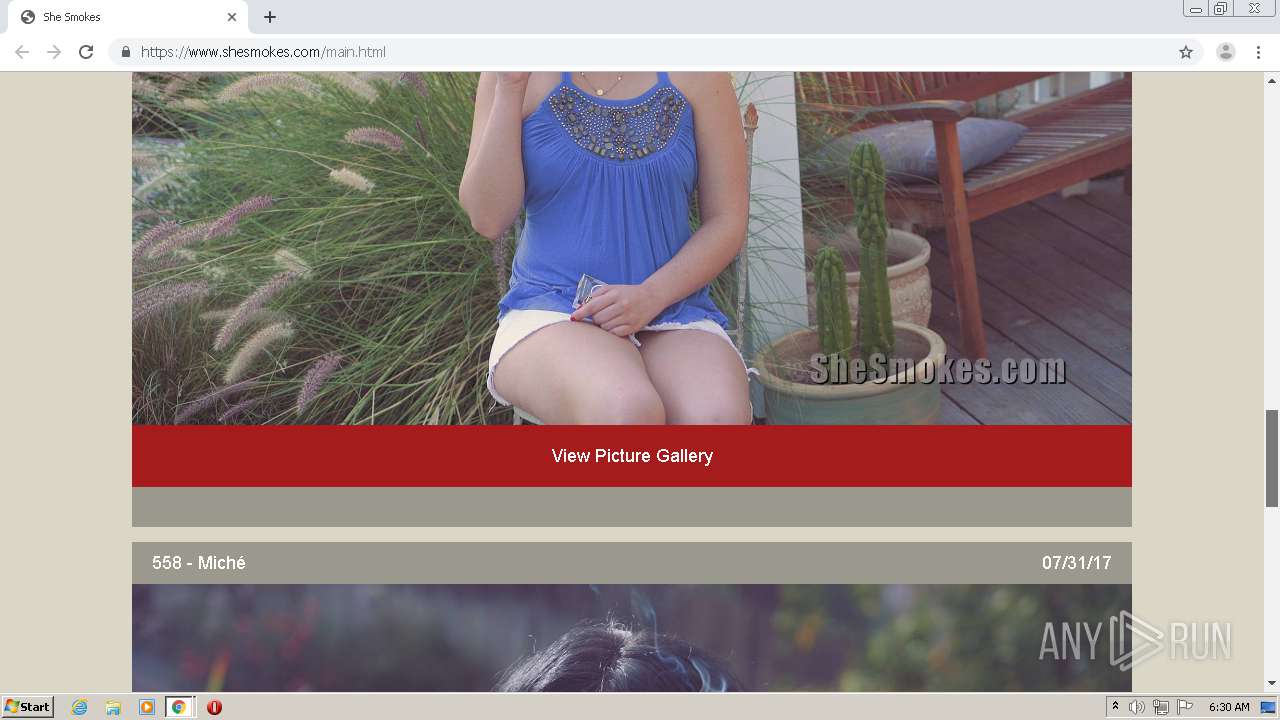
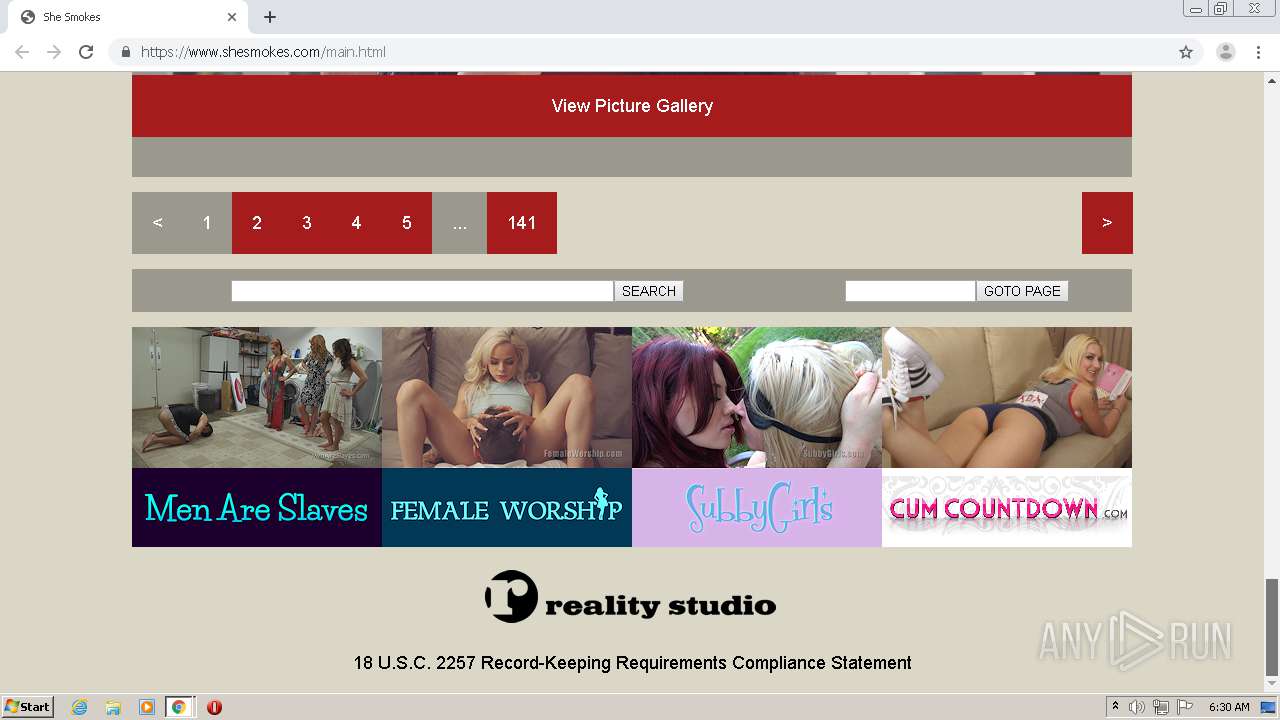
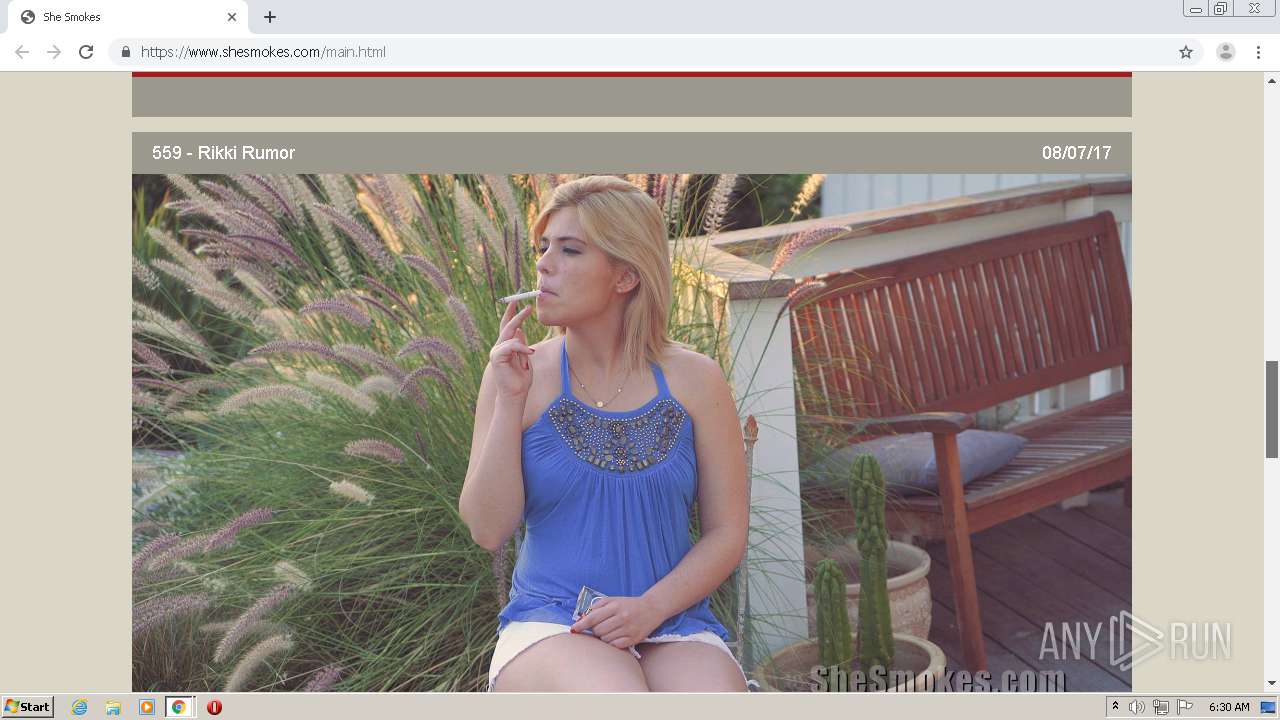
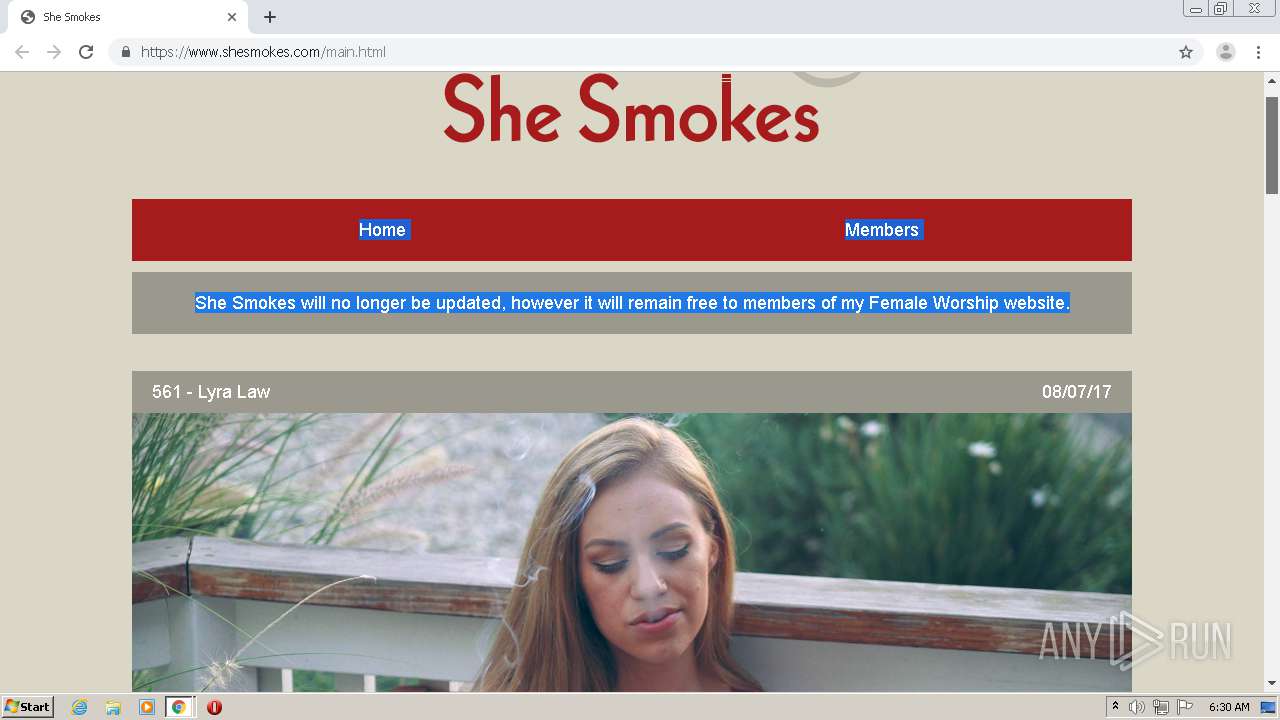
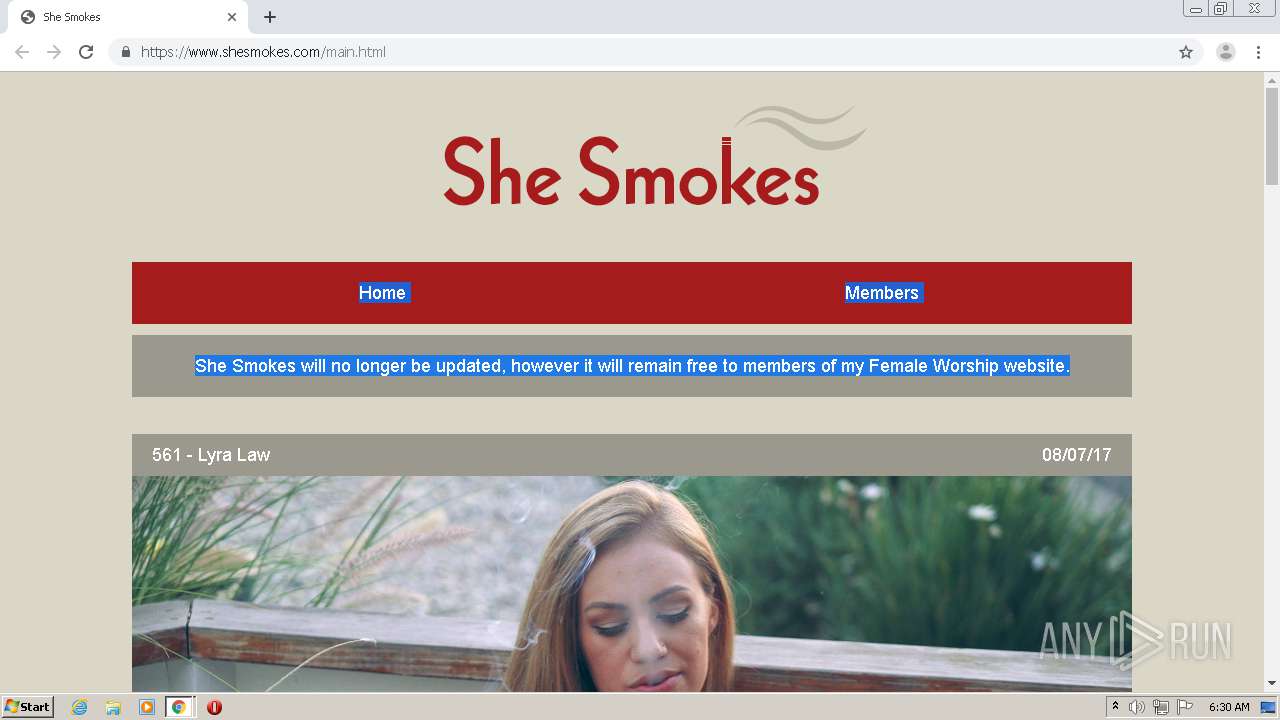
| download: | index.html |
| Full analysis: | https://app.any.run/tasks/9dbc704c-6dd9-4004-a644-a25d1ebd5fd6 |
| Verdict: | Malicious activity |
| Analysis date: | July 13, 2020, 05:27:10 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, Non-ISO extended-ASCII text, with very long lines, with CRLF, LF line terminators |
| MD5: | 66014229F10B30072BAB4D6F078EF2B5 |
| SHA1: | FEFC00C26181BE3C77A67BCA799A51666C1DD8A6 |
| SHA256: | B30F841DD1A116500CF68E8CF2C15041342EE7F83A4C5EAE2CC2DF6B45BF4446 |
| SSDEEP: | 384:x97Ru66oOgLAQS6PtCSImDiLauMkWTuHoeKu317hgLPqx:xxfXCSImDiLa7fuWch |
MALICIOUS
No malicious indicators.SUSPICIOUS
Modifies files in Chrome extension folder
- chrome.exe (PID: 2820)
INFO
Application launched itself
- iexplore.exe (PID: 2136)
- chrome.exe (PID: 2820)
Reads the hosts file
- chrome.exe (PID: 3316)
- chrome.exe (PID: 2820)
Manual execution by user
- chrome.exe (PID: 2820)
Reads Internet Cache Settings
- iexplore.exe (PID: 2136)
Changes internet zones settings
- iexplore.exe (PID: 2136)
Reads internet explorer settings
- iexplore.exe (PID: 2392)
Reads settings of System Certificates
- chrome.exe (PID: 3316)
- iexplore.exe (PID: 2392)
Changes settings of System certificates
- iexplore.exe (PID: 2392)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2392)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .htm/html | | | HyperText Markup Language with DOCTYPE (80.6) |
|---|---|---|
| .html | | | HyperText Markup Language (19.3) |
EXIF
HTML
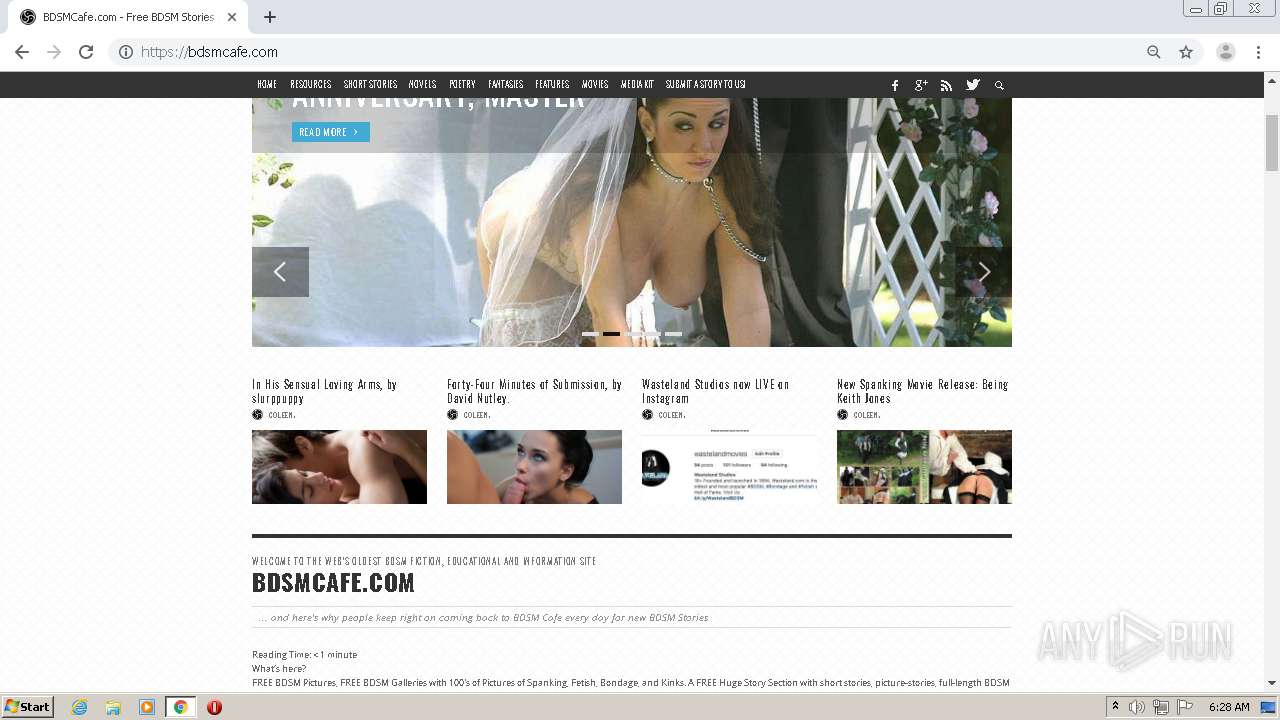
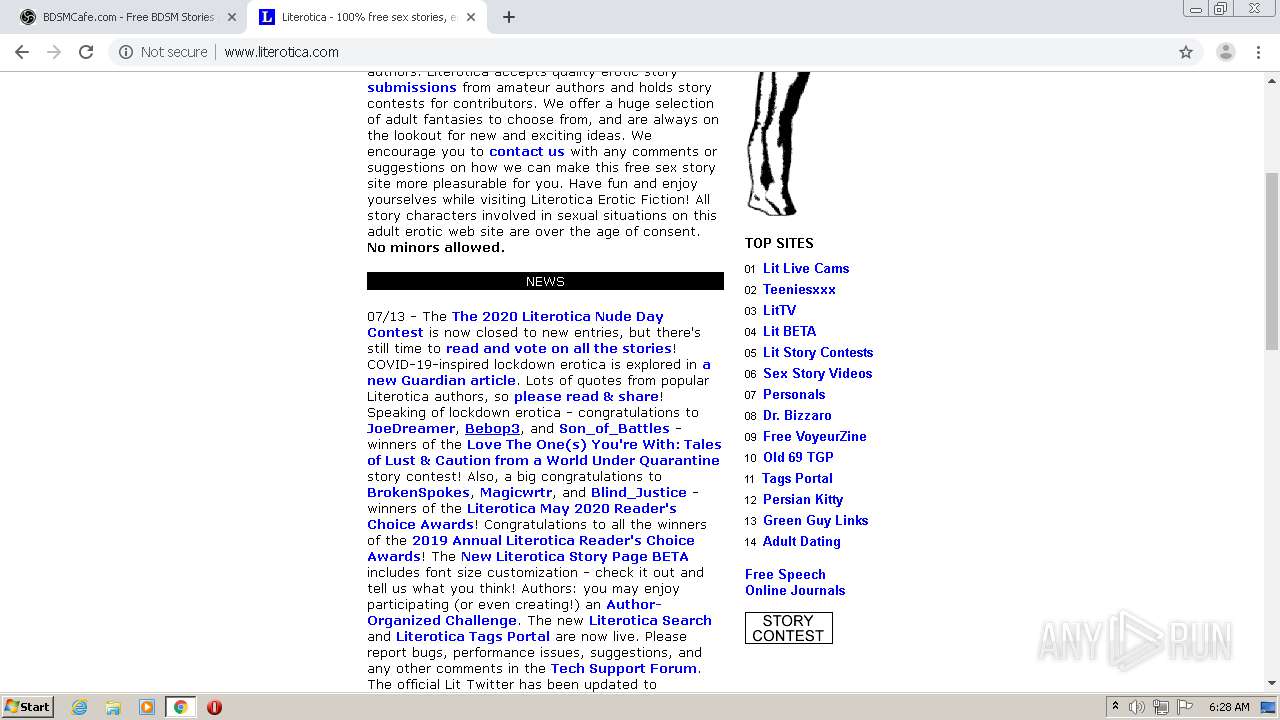
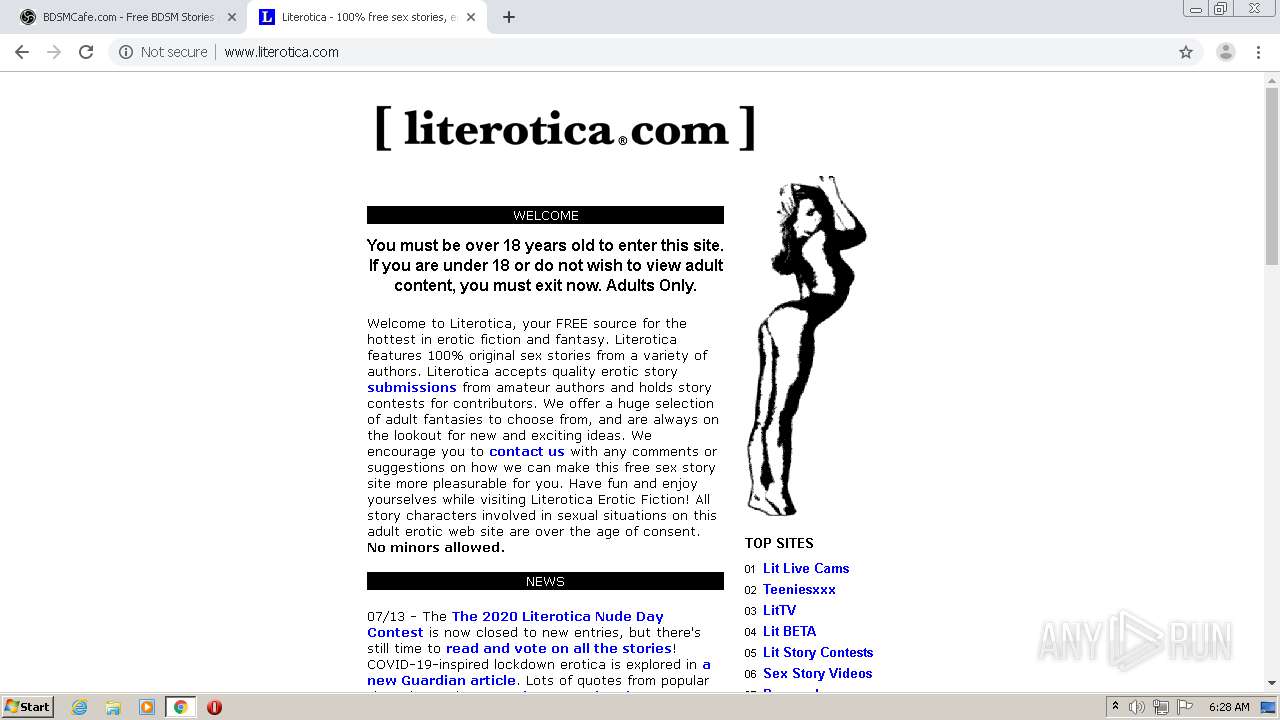
| Title: | Literotica - 100% free sex stories, erotic audio, adult fiction with wifeslut, bdsm, etc! |
|---|---|
| HTTPEquivXUACompatible: | IE=7 |
| ContentType: | text/html; charset=iso-8859-1 |
| Description: | Literotica free sex stories, erotic fiction and adult audio. Wifeslut, bdsm, xxx, fetish, mature, and free sexual fantasies. Porn storys updated daily! Story submissions accepted. |
| Keywords: | sex stories, erotic fiction, adult, free, sexy, literotica, literotic, chat, storys, wifeslut, erotica, sexual, real audio, xxx, porno, porn, romance, text, fantasies, poetry |
| Pragma: | no-cache |
| referrer: | origin |
| googleSiteVerification: | k2K6jLh8YJkmWurNFzUf2SkFHcRK6Cgcvq2sAfgOEl0 |
| PicsLabel: | (pics-1.1 "http://www.icra.org/pics/vocabularyv03/" l gen true for "http://literotica.com" r (n 2 s 3 v 2 l 3 oa 2 ob 2 oc 0 od 0 oe 0 of 0 og 0 oh 0 c 3) gen true for "http://www.literotica.com" r (n 2 s 3 v 2 l 3 oa 2 ob 2 oc 0 od 0 oe 0 of 0 og 0 oh 0 c 3)) |
Total processes
88
Monitored processes
53
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 660 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=75.0.3770.100 --initial-client-data=0x7c,0x80,0x84,0x78,0x88,0x6ee0a9d0,0x6ee0a9e0,0x6ee0a9ec | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 692 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1004,6516374284440118409,4881533335300310440,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=11550950984820371532 --mojo-platform-channel-handle=3820 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 832 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1004,6516374284440118409,4881533335300310440,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=2523432249349959786 --renderer-client-id=45 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1356 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 904 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1004,6516374284440118409,4881533335300310440,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=11916334989528976437 --renderer-client-id=30 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4436 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1204 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1004,6516374284440118409,4881533335300310440,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=7760611452153572032 --mojo-platform-channel-handle=4228 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1492 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1004,6516374284440118409,4881533335300310440,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=8638563150909234228 --renderer-client-id=48 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3592 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1520 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1004,6516374284440118409,4881533335300310440,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=12659766229452885228 --mojo-platform-channel-handle=2704 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1536 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1004,6516374284440118409,4881533335300310440,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=942102908589451297 --mojo-platform-channel-handle=4196 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1800 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1004,6516374284440118409,4881533335300310440,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=10993540807316252613 --mojo-platform-channel-handle=3612 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1824 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1004,6516374284440118409,4881533335300310440,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=10850950743499004004 --mojo-platform-channel-handle=1408 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
5 510
Read events
1 468
Write events
2 733
Delete events
1 309
Modification events
| (PID) Process: | (2136) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 1524272298 | |||
| (PID) Process: | (2136) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30824662 | |||
| (PID) Process: | (2136) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2136) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2136) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2136) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2136) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2136) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A1000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2136) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2136) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
0
Suspicious files
95
Text files
350
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2136 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2136 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF0815F79CD465E731.TMP | — | |
MD5:— | SHA256:— | |||
| 2136 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF37219DB1EF560244.TMP | — | |
MD5:— | SHA256:— | |||
| 2136 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFE02A207AE42ED611.TMP | — | |
MD5:— | SHA256:— | |||
| 2136 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\RecoveryStore.{869989C3-C4C9-11EA-B03F-5254004A04AF}.dat | — | |
MD5:— | SHA256:— | |||
| 2136 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF851FD33FEF6A1AD6.TMP | — | |
MD5:— | SHA256:— | |||
| 2820 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-5F0BF0C7-B04.pma | — | |
MD5:— | SHA256:— | |||
| 2820 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\9c194163-1a51-4dcb-81b2-99389bfb3e06.tmp | — | |
MD5:— | SHA256:— | |||
| 2820 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000028.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2136 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Last Active\{8CEA041E-C4C9-11EA-B03F-5254004A04AF}.dat | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
43
TCP/UDP connections
129
DNS requests
83
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3316 | chrome.exe | GET | 301 | 216.150.65.200:80 | http://literotica.com/nfo/piwik.js | US | — | — | whitelisted |
3316 | chrome.exe | GET | 302 | 99.192.154.195:80 | http://bdsmcafe.com/favicon.ico | US | html | 227 b | unknown |
3316 | chrome.exe | GET | 302 | 172.217.23.174:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvY2Y1QUFXUjZlVjI5UldyLVpDTFJFcEx6QQ/7719.805.0.2_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx | US | html | 525 b | whitelisted |
3316 | chrome.exe | GET | 302 | 172.217.23.174:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOTRmQUFXVHlhaGJaUTdMLWtCSkNJUl9ZQQ/1.0.0.5_nmmhkkegccagdldgiimedpiccmgmieda.crx | US | html | 520 b | whitelisted |
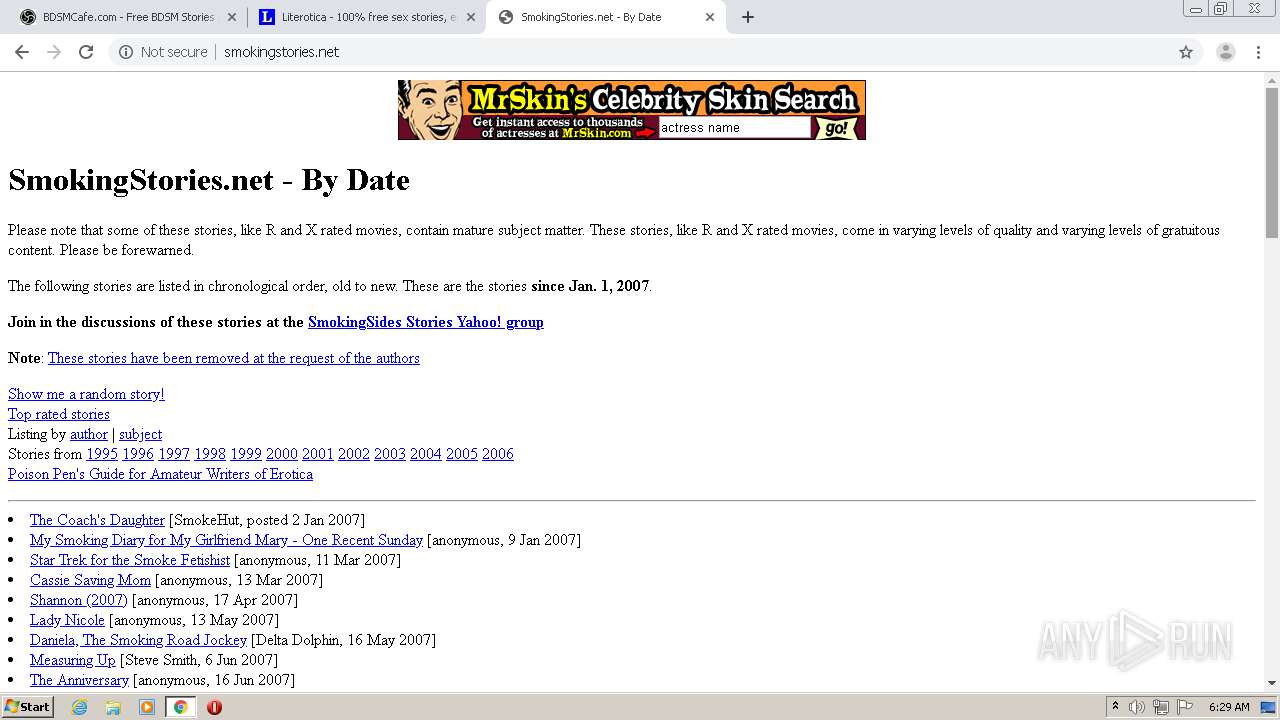
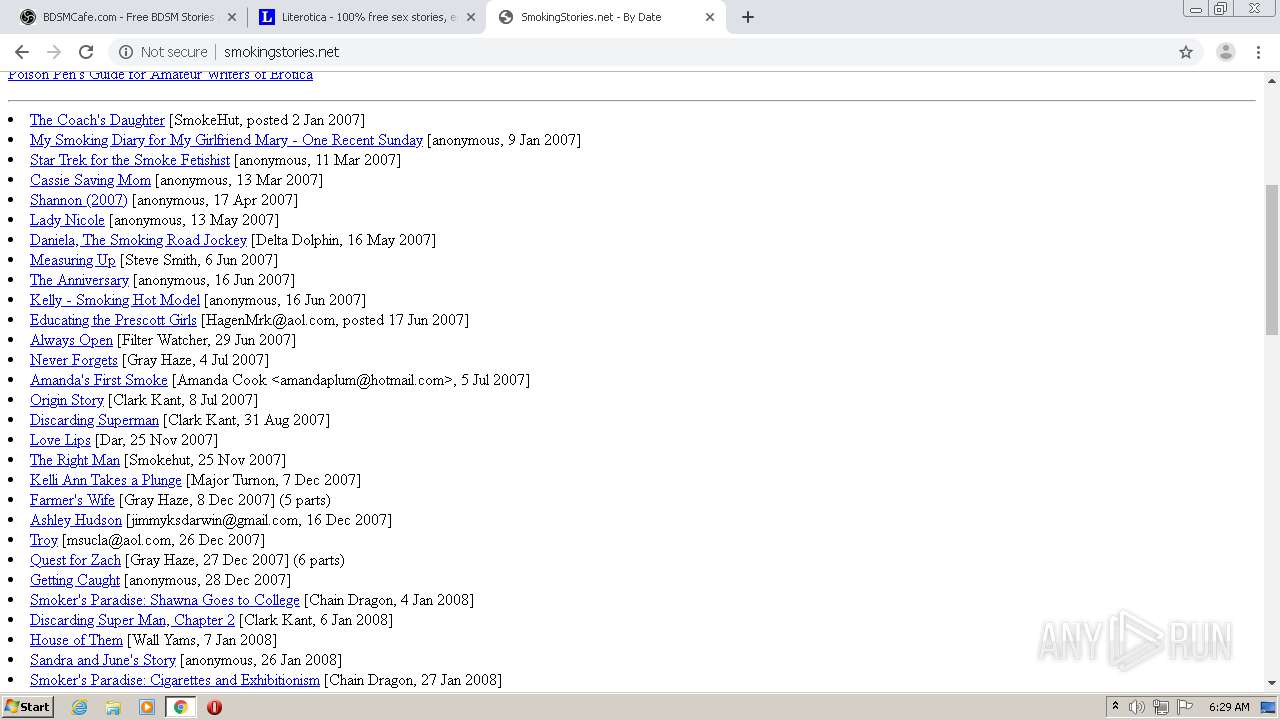
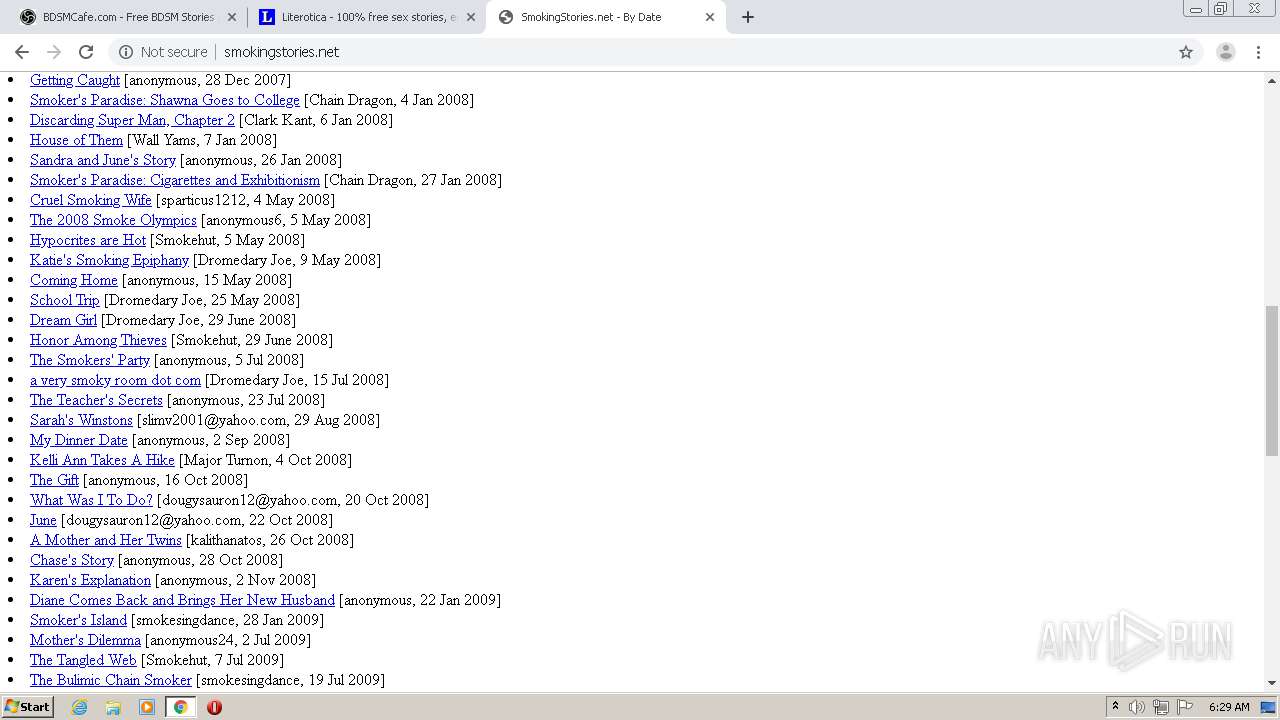
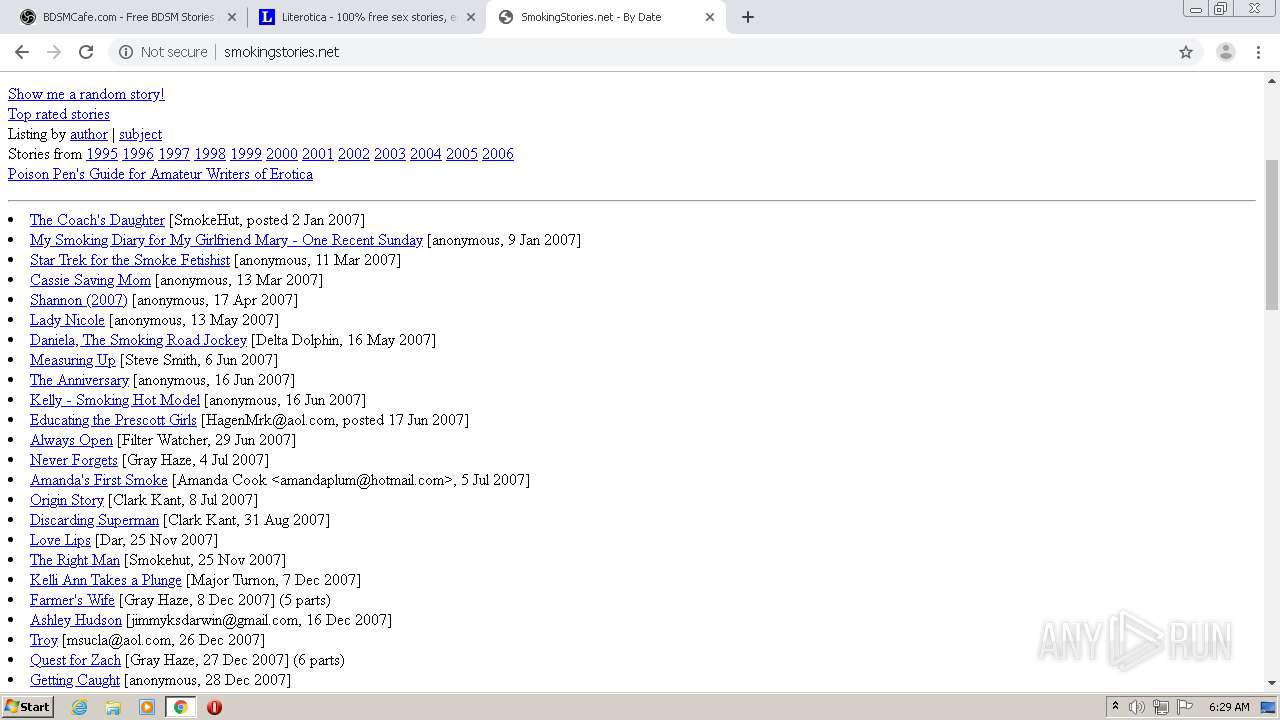
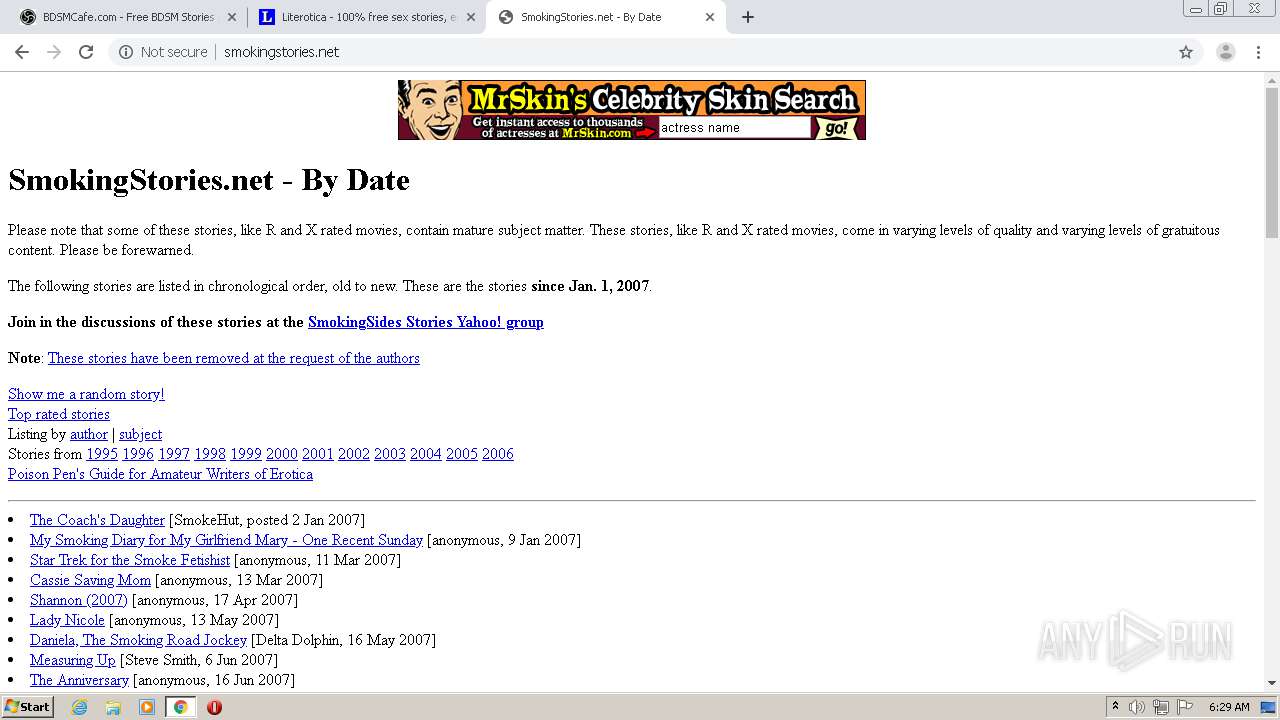
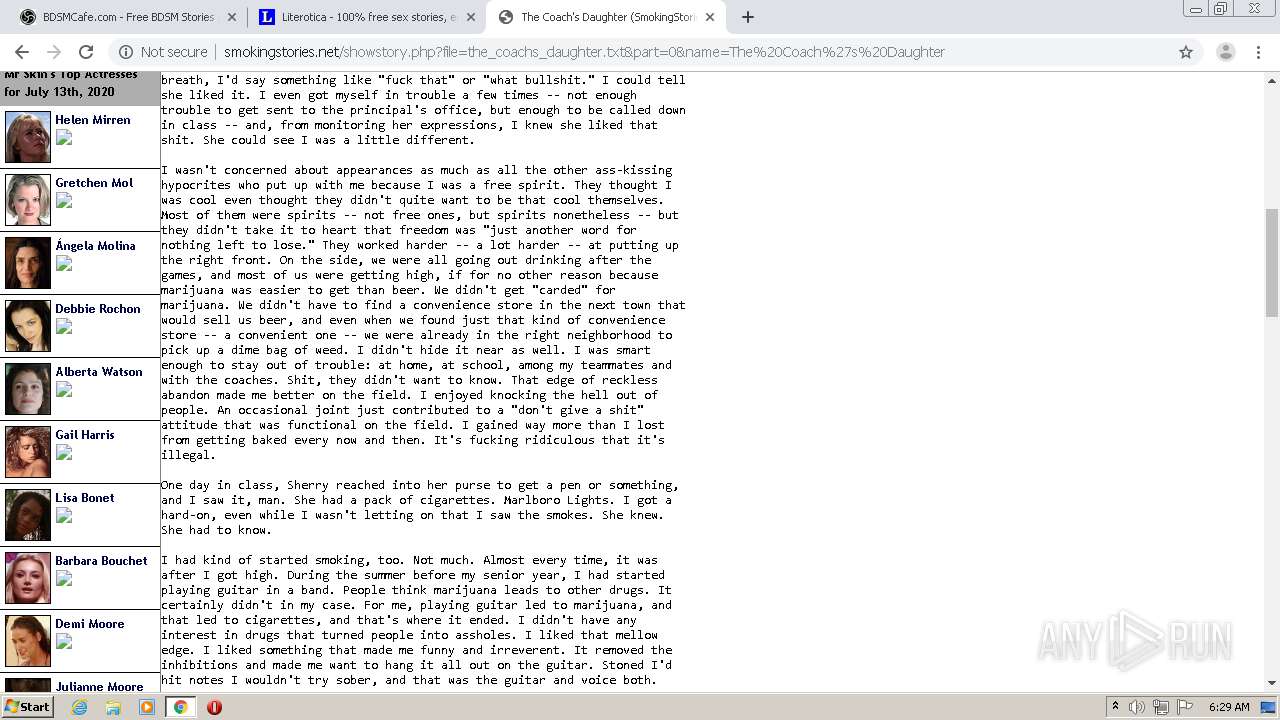
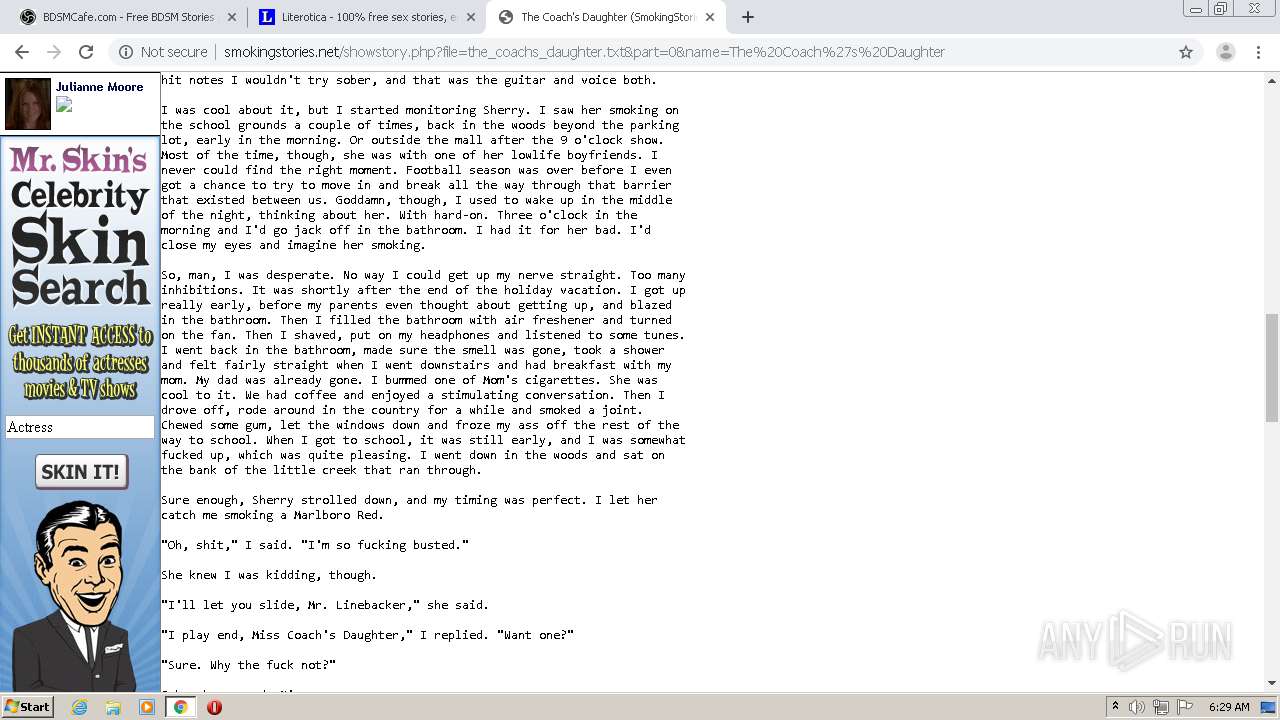
3316 | chrome.exe | GET | 200 | 50.87.150.205:80 | http://smokingstories.net/ | US | xml | 4.56 Kb | unknown |
3316 | chrome.exe | GET | 200 | 50.87.150.205:80 | http://smokingstories.net/glamfeed.js | US | html | 2.59 Kb | unknown |
3316 | chrome.exe | GET | 200 | 69.16.175.42:80 | http://cdnp.kink.com/kd/41496_DB_300x250.jpg | US | image | 76.0 Kb | malicious |
3316 | chrome.exe | GET | 200 | 50.87.150.205:80 | http://smokingstories.net/banner.js | US | text | 321 b | unknown |
3316 | chrome.exe | GET | 200 | 205.234.175.105:80 | http://images.mrskincash.com/mrskin/halfpage/imx2/03.gif | US | image | 2.23 Kb | unknown |
3316 | chrome.exe | GET | 200 | 205.234.175.105:80 | http://images.mrskincash.com/mrskin/halfpage/imx2/04.gif | US | image | 138 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 216.58.206.4:443 | www.google.com | Google Inc. | US | whitelisted |
2392 | iexplore.exe | 62.113.194.2:443 | speedy.literotica.com | 23media GmbH | DE | malicious |
4 | System | 216.150.65.190:445 | literotica.com | Access Integrated Technologies, Inc. | US | unknown |
— | — | 216.150.65.200:137 | literotica.com | Access Integrated Technologies, Inc. | US | unknown |
4 | System | 216.150.65.200:445 | literotica.com | Access Integrated Technologies, Inc. | US | unknown |
2136 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3316 | chrome.exe | 216.58.207.35:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
3316 | chrome.exe | 172.217.16.195:443 | www.google.com.ua | Google Inc. | US | whitelisted |
3316 | chrome.exe | 216.58.208.42:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
3316 | chrome.exe | 172.217.18.163:443 | www.gstatic.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
speedy.literotica.com |
| malicious |
literotica.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com.ua |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1056 | svchost.exe | Potential Corporate Privacy Violation | ET POLICY DNS Query For XXX Adult Site Top Level Domain |
3316 | chrome.exe | Generic Protocol Command Decode | SURICATA HTTP unable to match response to request |