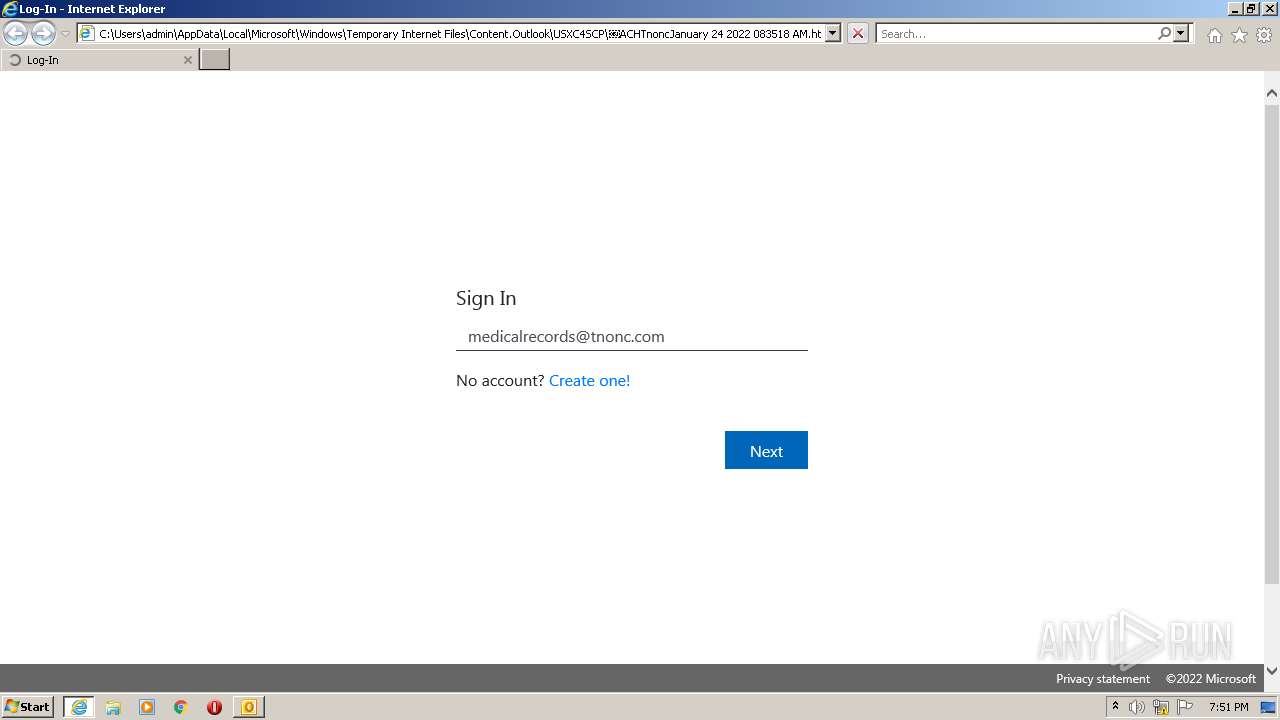
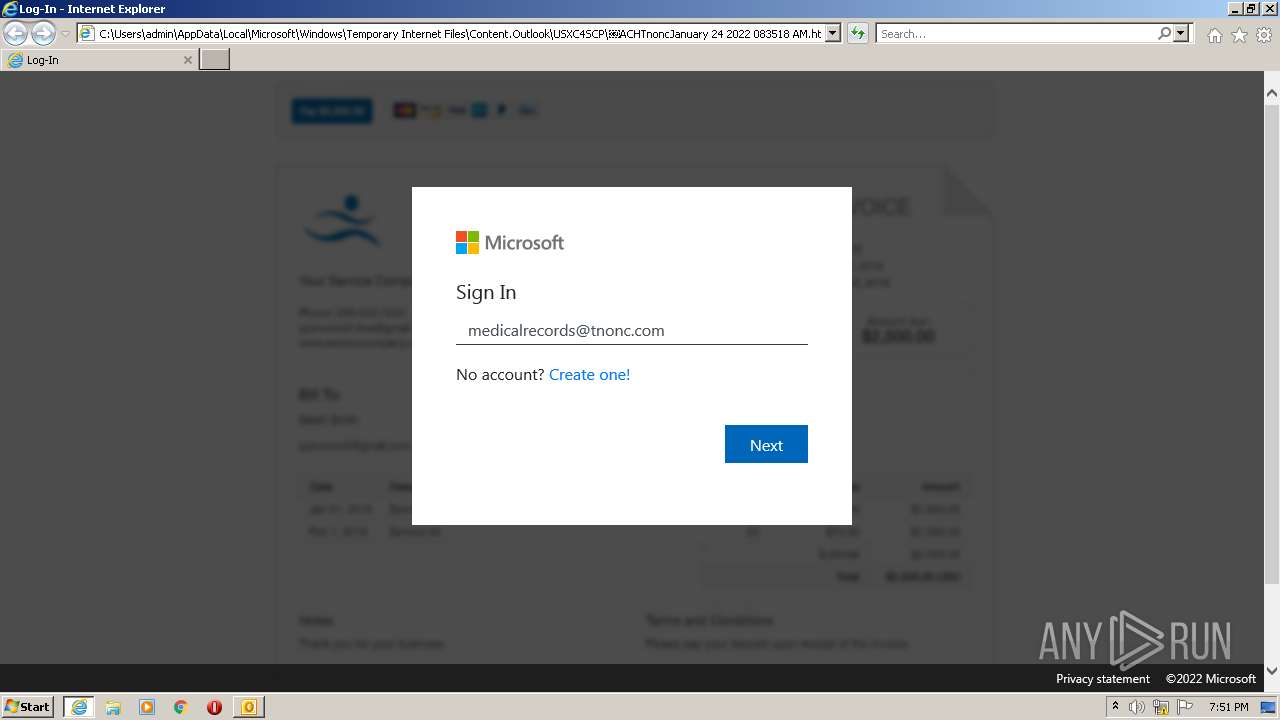
| File name: | (Automatic Clearing House Payment Completed on 1242022 083518 AM).msg |
| Full analysis: | https://app.any.run/tasks/059beb55-b9c7-4a4b-b5ec-e24ab4887089 |
| Verdict: | Malicious activity |
| Analysis date: | January 24, 2022, 19:50:39 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | F140E37574BC89D1E4F6E460713649E5 |
| SHA1: | 75AC316D46951A23B4F631EAD9D626F635F19028 |
| SHA256: | B2CC7C084371A0B8D9BE267265BF1606650010DC36AE3AF0000AA47CB5C3157C |
| SSDEEP: | 768:0TjEpHwooqcfvZg2ybKEKYlrtfh3GOOf4bXdry2WsKfWsKh+onNd44/ylu3b3OD+:7qv9yb1rtfhvpbxy2WHWp9KlujyUP |
MALICIOUS
Unusual execution from Microsoft Office
- OUTLOOK.EXE (PID: 3528)
SUSPICIOUS
Starts Internet Explorer
- OUTLOOK.EXE (PID: 3528)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 3536)
INFO
Checks supported languages
- OUTLOOK.EXE (PID: 3528)
- iexplore.exe (PID: 3140)
- iexplore.exe (PID: 3536)
Searches for installed software
- OUTLOOK.EXE (PID: 3528)
Reads the computer name
- OUTLOOK.EXE (PID: 3528)
- iexplore.exe (PID: 3140)
- iexplore.exe (PID: 3536)
Creates files in the user directory
- OUTLOOK.EXE (PID: 3528)
- iexplore.exe (PID: 3140)
Changes internet zones settings
- iexplore.exe (PID: 3140)
Application launched itself
- iexplore.exe (PID: 3140)
Reads settings of System Certificates
- iexplore.exe (PID: 3536)
- iexplore.exe (PID: 3140)
Reads internet explorer settings
- iexplore.exe (PID: 3536)
Checks Windows Trust Settings
- iexplore.exe (PID: 3140)
- iexplore.exe (PID: 3536)
Dropped object may contain Bitcoin addresses
- iexplore.exe (PID: 3140)
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 3528)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3140)
Changes settings of System certificates
- iexplore.exe (PID: 3140)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msg | | | Outlook Message (58.9) |
|---|---|---|
| .oft | | | Outlook Form Template (34.4) |
Total processes
41
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3140 | "C:\Program Files\Internet Explorer\iexplore.exe" C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\USXC4SCP\??ACHTnoncJanuary 24 2022 083518 AM.html | C:\Program Files\Internet Explorer\iexplore.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3528 | "C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE" /f "C:\Users\admin\AppData\Local\Temp\(Automatic Clearing House Payment Completed on 1242022 083518 AM).msg" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 3536 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3140 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
21 426
Read events
20 704
Write events
698
Delete events
24
Modification events
| (PID) Process: | (3528) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3528) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (3528) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (3528) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (3528) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (3528) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (3528) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (3528) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (3528) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
| (PID) Process: | (3528) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: Off | |||
Executable files
0
Suspicious files
20
Text files
43
Unknown types
17
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3528 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVRC888.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3528 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook Data File - NoMail.pst | — | |
MD5:— | SHA256:— | |||
| 3528 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3528 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\outlook logging\firstrun.log | text | |
MD5:— | SHA256:— | |||
| 3528 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_AvailabilityOptions_2_870CB50AE9E5594B981105FE0A8F5E75.dat | xml | |
MD5:EEAA832C12F20DE6AAAA9C7B77626E72 | SHA256:C4C9A90F2C961D9EE79CF08FBEE647ED7DE0202288E876C7BAAD00F4CA29CA16 | |||
| 3528 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\mapisvc.inf | text | |
MD5:F3B25701FE362EC84616A93A45CE9998 | SHA256:B3D510EF04275CA8E698E5B3CBB0ECE3949EF9252F0CDC839E9EE347409A2209 | |||
| 3528 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\USXC4SCP\??ACHTnoncJanuary 24 2022 083518 AM.html | html | |
MD5:— | SHA256:— | |||
| 3528 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\USXC4SCP\??ACHTnoncJanuary 24 2022 083518 AM (2).html | html | |
MD5:— | SHA256:— | |||
| 3536 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:— | SHA256:— | |||
| 3536 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
19
TCP/UDP connections
54
DNS requests
29
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3528 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
3536 | iexplore.exe | GET | 200 | 104.18.30.182:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | US | der | 727 b | whitelisted |
3536 | iexplore.exe | GET | 200 | 104.18.31.182:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | US | der | 471 b | whitelisted |
3140 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
3536 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 1.47 Kb | whitelisted |
3536 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAGC%2BAmOouYmuRo7J4Qfua8%3D | US | der | 1.47 Kb | whitelisted |
3536 | iexplore.exe | GET | 200 | 23.32.238.201:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?47571dd90f7266b4 | US | compressed | 4.70 Kb | whitelisted |
3536 | iexplore.exe | GET | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | US | der | 1.41 Kb | whitelisted |
3536 | iexplore.exe | GET | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCrvyQ4GllugQoAAAABK4Az | US | der | 472 b | whitelisted |
3536 | iexplore.exe | GET | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | US | der | 724 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3536 | iexplore.exe | 142.250.186.131:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
3536 | iexplore.exe | 23.32.238.201:80 | ctldl.windowsupdate.com | XO Communications | US | suspicious |
3536 | iexplore.exe | 104.18.31.182:80 | ocsp.comodoca.com | Cloudflare Inc | US | unknown |
3536 | iexplore.exe | 104.18.10.207:443 | maxcdn.bootstrapcdn.com | Cloudflare Inc | US | suspicious |
3536 | iexplore.exe | 104.18.30.182:80 | ocsp.comodoca.com | Cloudflare Inc | US | suspicious |
3528 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
3536 | iexplore.exe | 142.250.186.42:443 | ajax.googleapis.com | Google Inc. | US | whitelisted |
3536 | iexplore.exe | 104.18.22.52:443 | kit.fontawesome.com | Cloudflare Inc | US | unknown |
3536 | iexplore.exe | 104.16.19.94:443 | cdnjs.cloudflare.com | Cloudflare Inc | US | suspicious |
3536 | iexplore.exe | 13.225.84.66:80 | o.ss2.us | — | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
ajax.googleapis.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
code.jquery.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
maxcdn.bootstrapcdn.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |