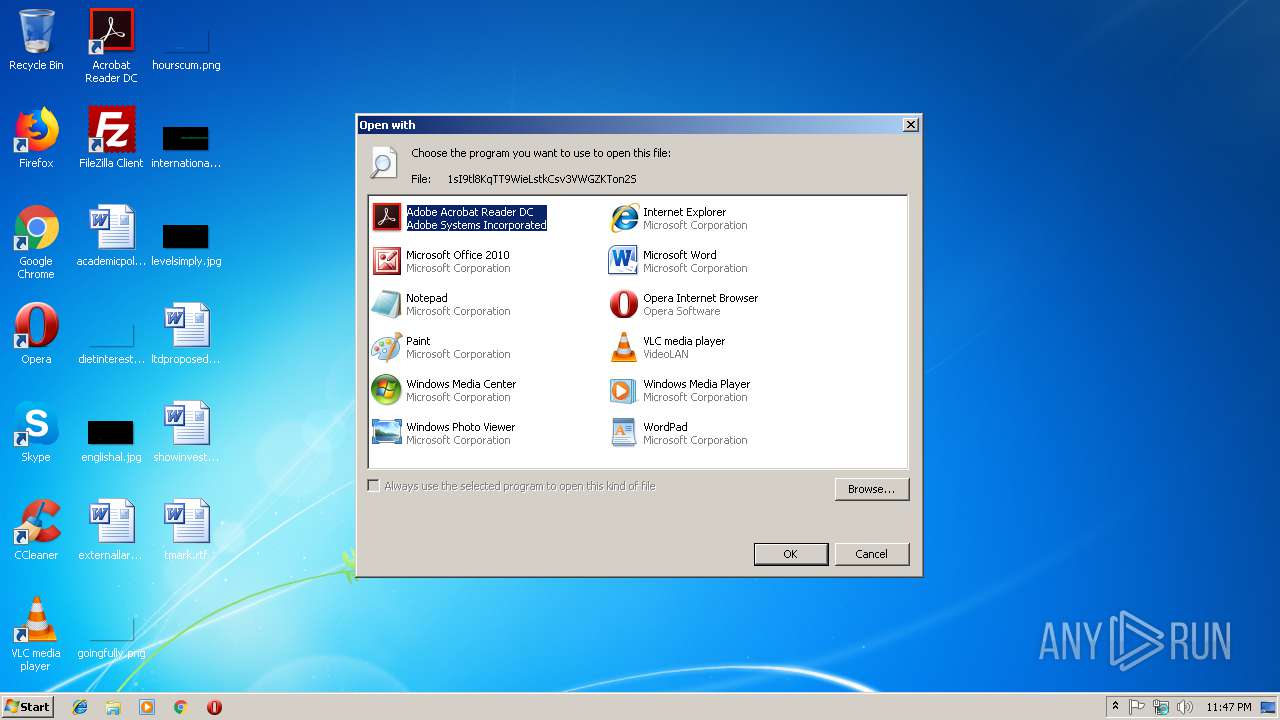
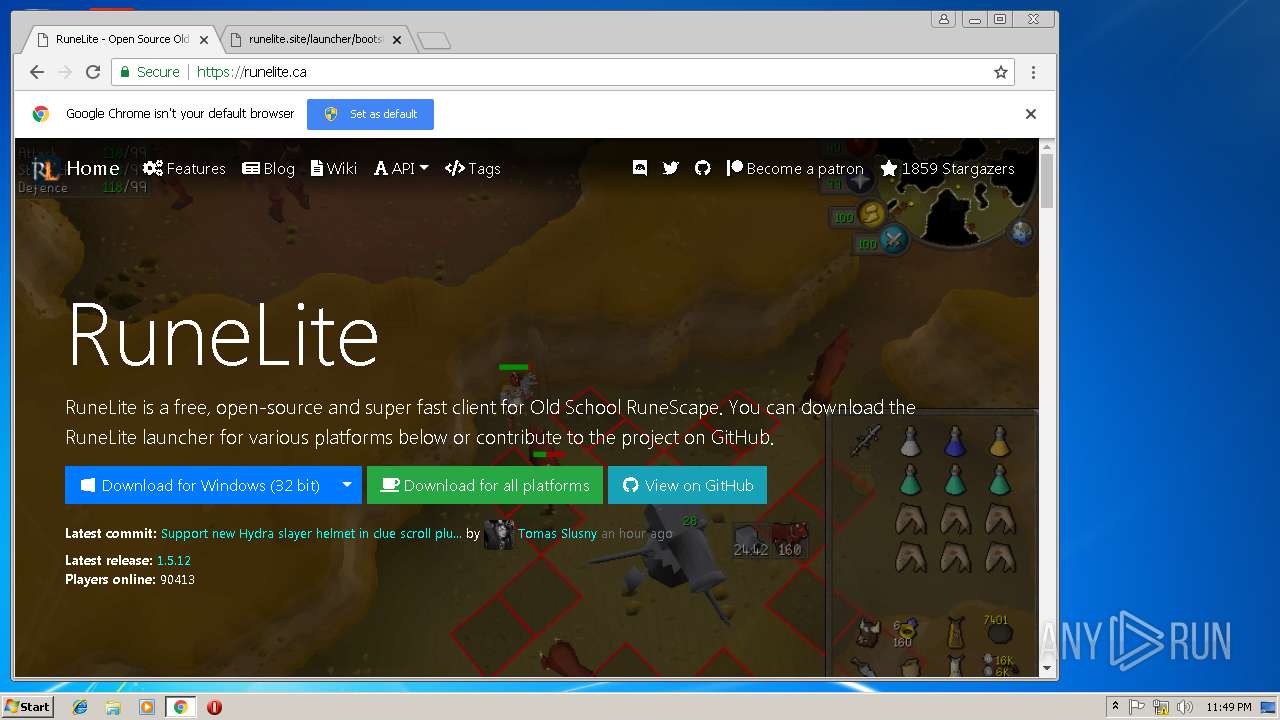
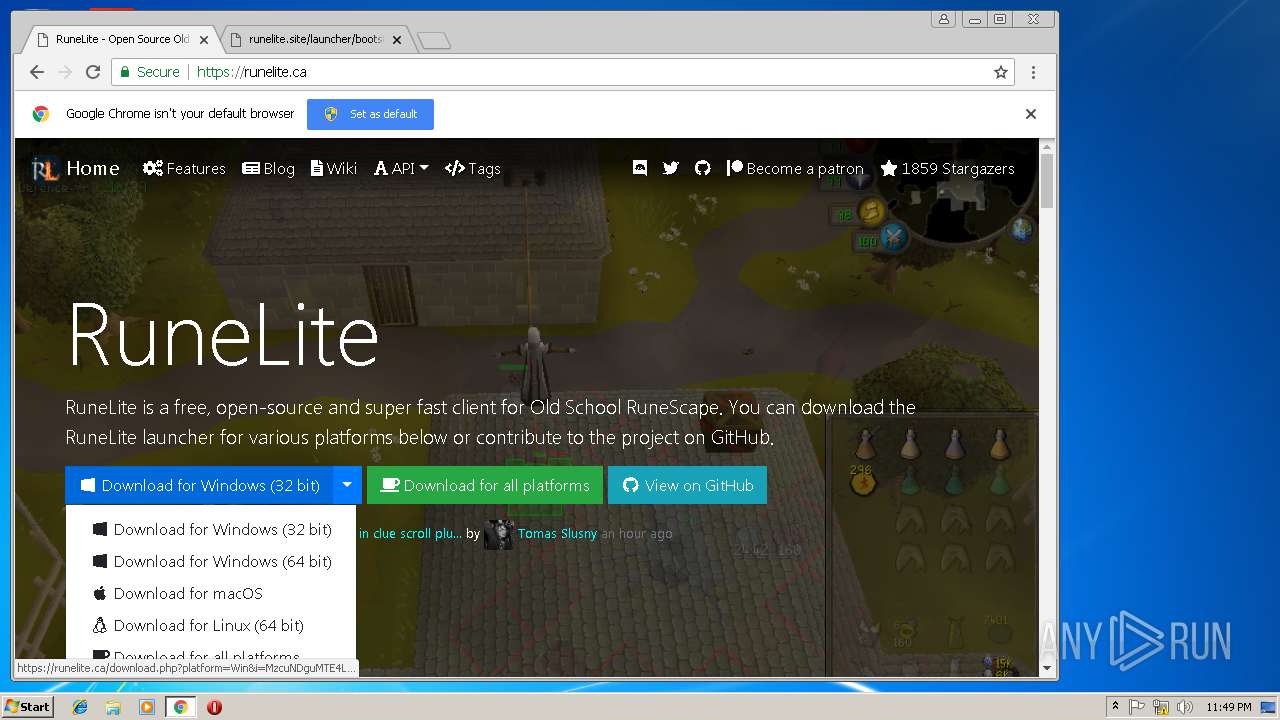
| File name: | 1sI9tl8KqTT9WieLstkCsv3VWGZKTon2S |
| Full analysis: | https://app.any.run/tasks/56b398c2-eb5b-4933-80e0-1c9c939399fe |
| Verdict: | Malicious activity |
| Analysis date: | February 18, 2019, 23:46:50 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, UTF-8 Unicode text, with very long lines |
| MD5: | F3F688A0FA3BDC3C593ACA20323793F3 |
| SHA1: | DBDD1A0CD0E4DBDEB181891E9CD4858D3C9F8997 |
| SHA256: | B2C9EB2A96BBDBADFBACF81A12D96278DBDA6D6A8A4A68085DBFB38956EA8EF7 |
| SSDEEP: | 1536:T7fn2jSu+TXFJVNFY00QiOQz3WyXTmSBcogZ:TajSu+ZdKGQzmrSBxgZ |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executes JAVA applets
- chrome.exe (PID: 3004)
INFO
Creates files in the user directory
- chrome.exe (PID: 3004)
Application launched itself
- chrome.exe (PID: 3004)
Reads Internet Cache Settings
- chrome.exe (PID: 3004)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
EXIF
HTML
| viewport: | width=300, initial-scale=1 |
|---|---|
| Description: | Google Drive is a free way to keep your files backed up and easy to reach from any phone, tablet or computer. Start with 15 GB of Google storage – free. |
| googleSiteVerification: | LrdTUW9psUAMbh4Ia074-BPEVmcpBxF6Gwf0MSgQXZs |
| Title: | Meet Google Drive – One place for all your files |
Total processes
53
Monitored processes
22
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1364 | "C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe" -jar "C:\Users\admin\Downloads\RuneLite (1).jar" | C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe | chrome.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 4294967295 Version: 8.0.920.14 Modules
| |||||||||||||||
| 2052 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=992,2711759363646038479,13200592699440873029,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=B92D8335551D8C3FCB4B828988CEC8E8 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=B92D8335551D8C3FCB4B828988CEC8E8 --renderer-client-id=13 --mojo-platform-channel-handle=3276 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2180 | "C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe" -jar "C:\Users\admin\Downloads\RuneLite.jar" | C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe | chrome.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 4294967295 Version: 8.0.920.14 Modules
| |||||||||||||||
| 2240 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=992,2711759363646038479,13200592699440873029,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAACAAwBAAQAAAAAAAAAAAGAAEAAAAAAAAAAAAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAKAAAAEAAAAAAAAAAAAAAACwAAABAAAAAAAAAAAQAAAAoAAAAQAAAAAAAAAAEAAAALAAAA --service-request-channel-token=8D20C2F4628B2E9CA5558AC1EF2EE3D2 --mojo-platform-channel-handle=1012 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2356 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=992,2711759363646038479,13200592699440873029,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=5112D78A49CC6284A32D78CFEC185A5C --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=5112D78A49CC6284A32D78CFEC185A5C --renderer-client-id=8 --mojo-platform-channel-handle=3772 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2420 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=992,2711759363646038479,13200592699440873029,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=47B17BC1AECB327821F54865D2D74C35 --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=47B17BC1AECB327821F54865D2D74C35 --renderer-client-id=6 --mojo-platform-channel-handle=3544 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2692 | "C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe" -jar "C:\Users\admin\Downloads\RuneLite (1).jar" | C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe | chrome.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 4294967295 Version: 8.0.920.14 Modules
| |||||||||||||||
| 2712 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=992,2711759363646038479,13200592699440873029,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=361B32D1888F7F1F16787269431B050E --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=361B32D1888F7F1F16787269431B050E --renderer-client-id=7 --mojo-platform-channel-handle=3652 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2760 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=992,2711759363646038479,13200592699440873029,131072 --enable-features=PasswordImport --service-pipe-token=E4A745658BBD781D30A94E673EA59142 --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=E4A745658BBD781D30A94E673EA59142 --renderer-client-id=5 --mojo-platform-channel-handle=1912 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2960 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Local\Temp\1sI9tl8KqTT9WieLstkCsv3VWGZKTon2S | C:\Windows\system32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 088
Read events
992
Write events
92
Delete events
4
Modification events
| (PID) Process: | (2960) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe |
Value: Adobe Acrobat Reader DC | |||
| (PID) Process: | (2960) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\eHome\ehshell.exe |
Value: Windows Media Center | |||
| (PID) Process: | (2960) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\system32\mspaint.exe |
Value: Paint | |||
| (PID) Process: | (2960) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\system32\NOTEPAD.EXE |
Value: Notepad | |||
| (PID) Process: | (2960) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\PROGRA~1\MICROS~1\Office14\OIS.EXE |
Value: Microsoft Office 2010 | |||
| (PID) Process: | (2960) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Opera\Opera.exe |
Value: Opera Internet Browser | |||
| (PID) Process: | (2960) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Windows Photo Viewer\PhotoViewer.dll |
Value: Windows Photo Viewer | |||
| (PID) Process: | (2960) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\VideoLAN\VLC\vlc.exe |
Value: VLC media player | |||
| (PID) Process: | (2960) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE |
Value: Microsoft Word | |||
| (PID) Process: | (2960) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
5
Suspicious files
109
Text files
135
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3004 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\8efaae2b-2473-45c3-9106-3078fab0d1c8.tmp | — | |
MD5:— | SHA256:— | |||
| 3004 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Download Service\EntryDB\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 3004 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 3004 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Thumbnails\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3004 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\2319023a-b96b-4bca-a90f-1ba2a415e4e6.tmp | — | |
MD5:— | SHA256:— | |||
| 3004 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Service Worker\CacheStorage\e6622492fa163609ddd4212f54512baa07929ed3\caecb3bd-7969-4305-84d6-3a376453ec73\index-dir\temp-index | — | |
MD5:— | SHA256:— | |||
| 3004 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Last Version | text | |
MD5:— | SHA256:— | |||
| 3004 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Service Worker\Database\LOG.old | text | |
MD5:— | SHA256:— | |||
| 3004 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old~RF248137.TMP | text | |
MD5:— | SHA256:— | |||
| 3004 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
19
TCP/UDP connections
43
DNS requests
25
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
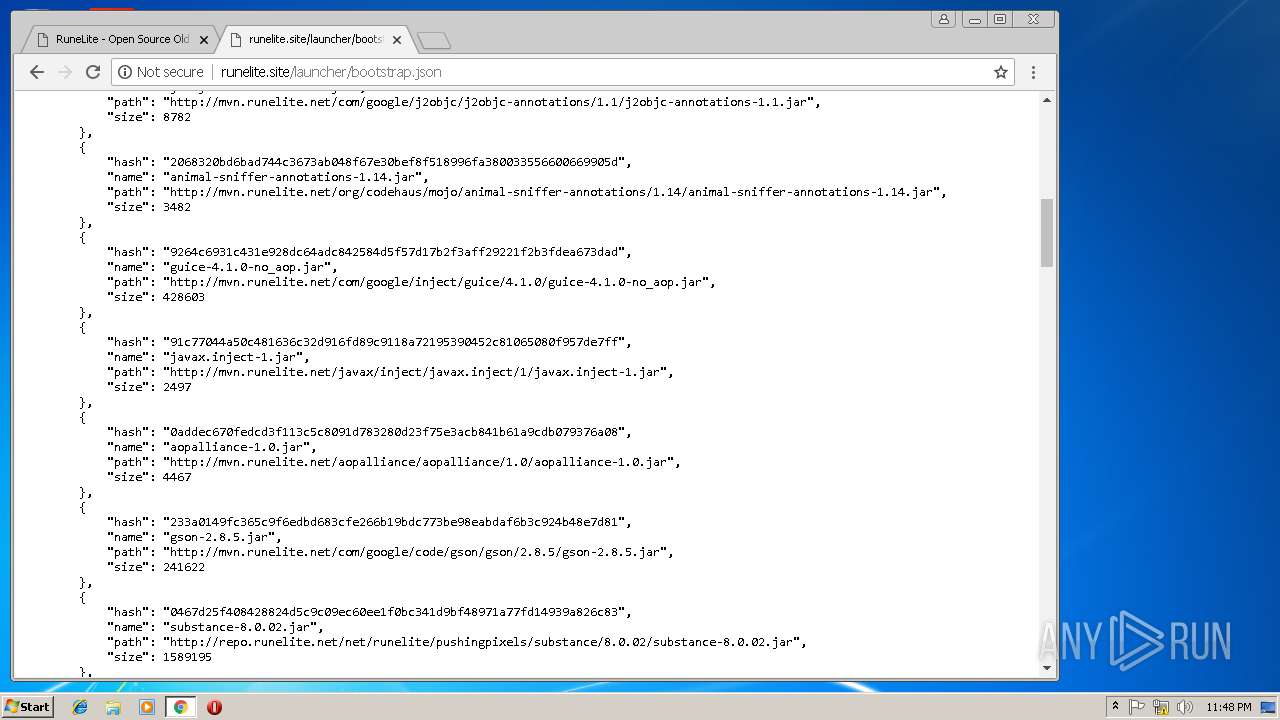
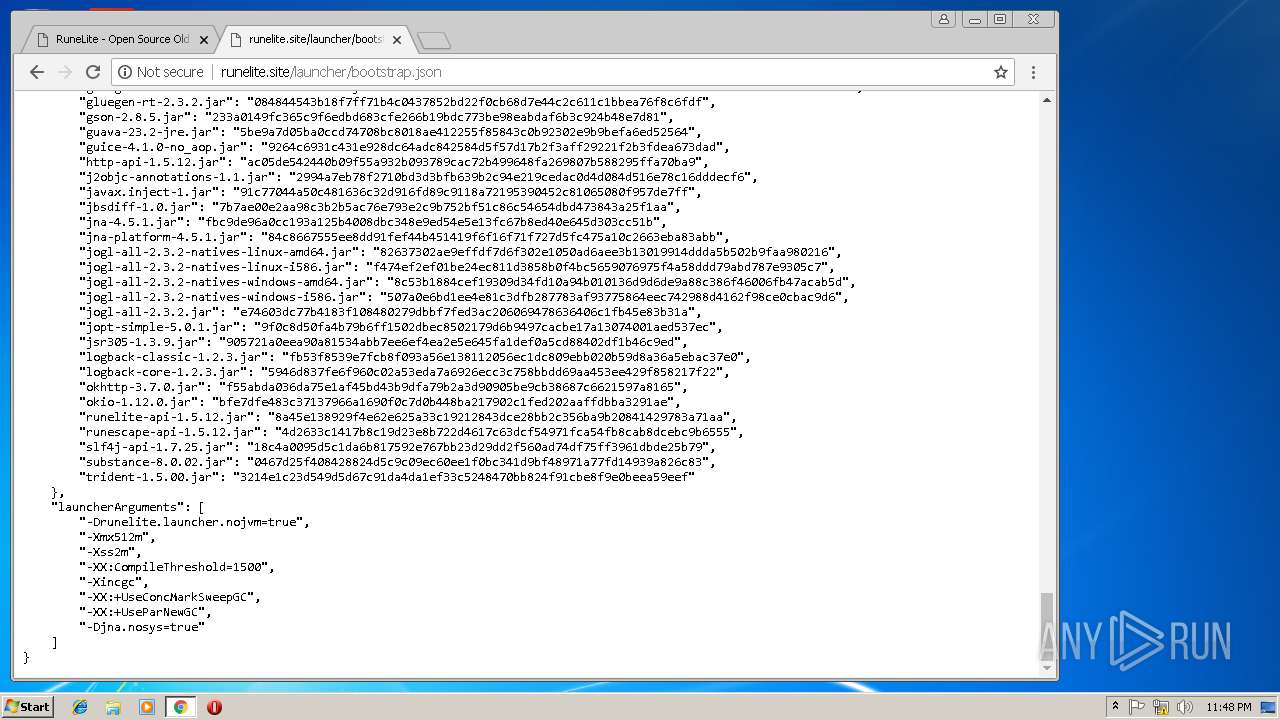
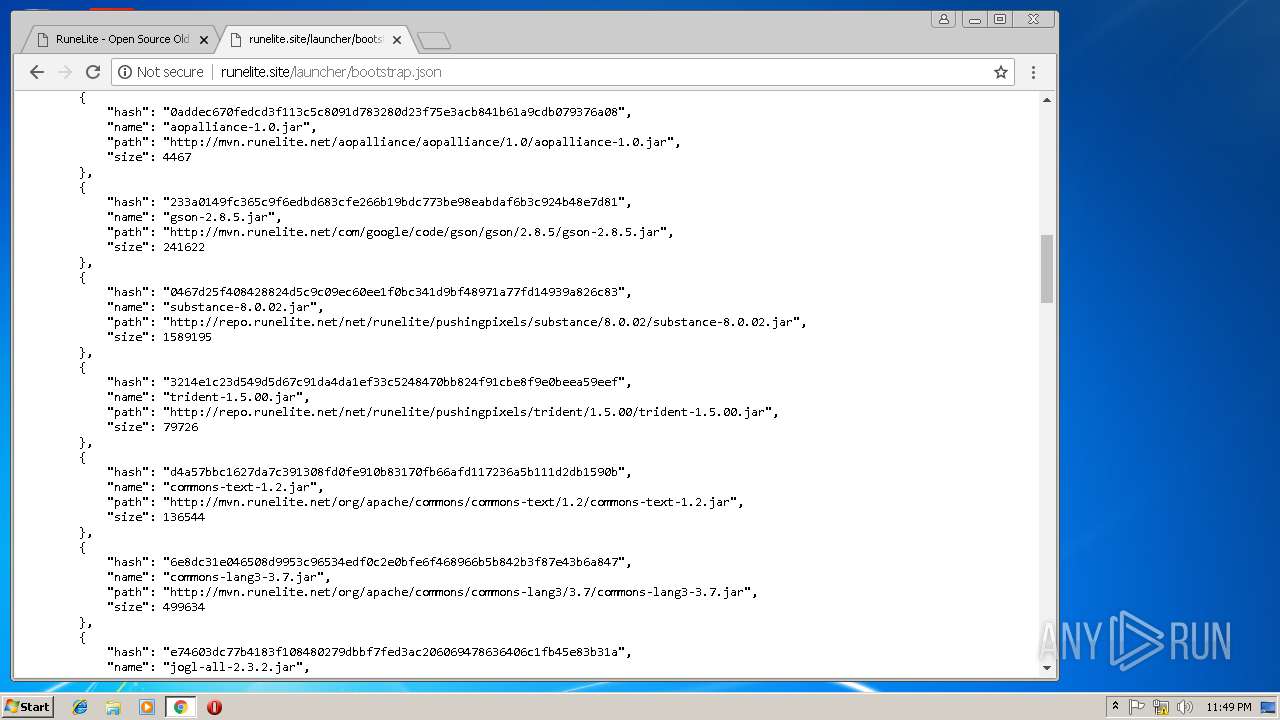
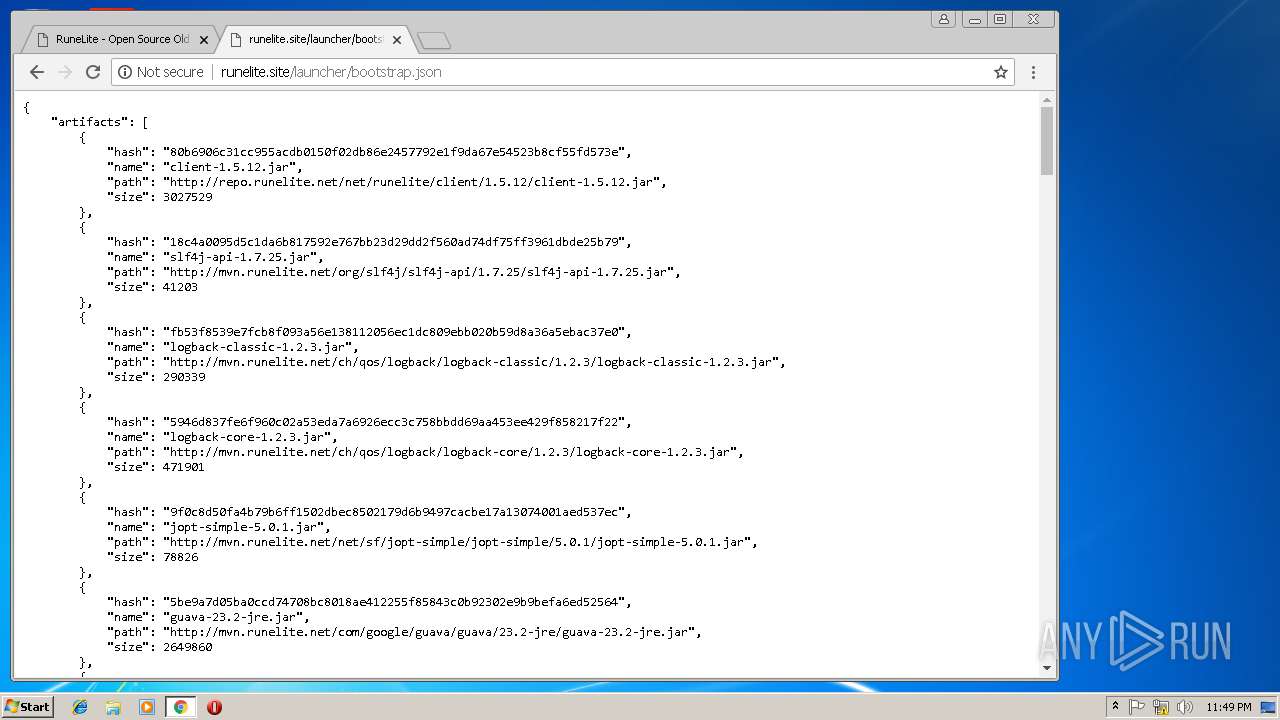
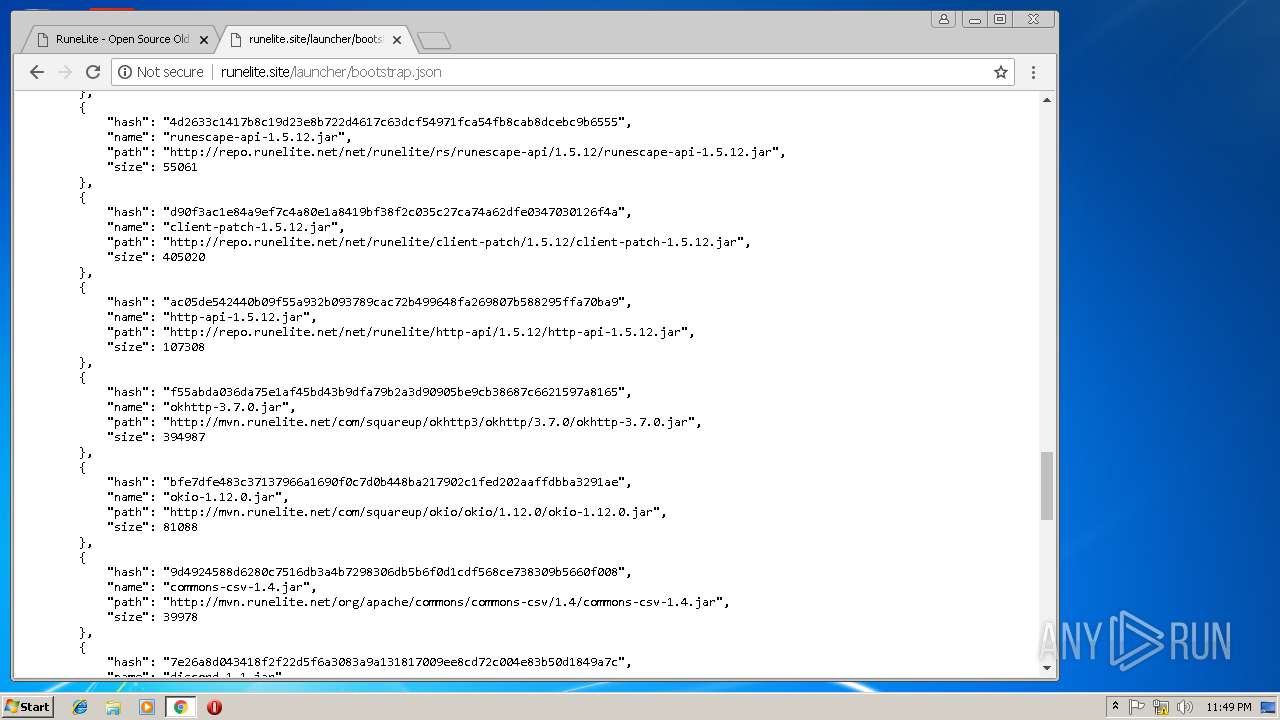
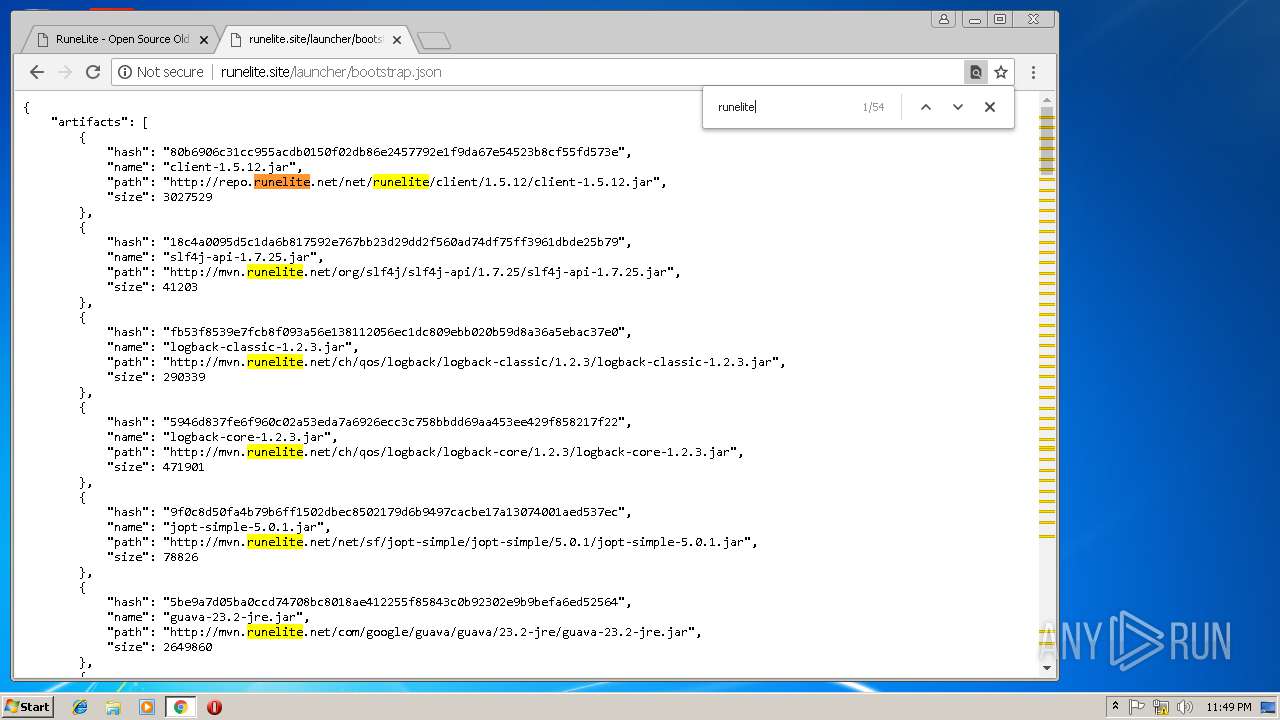
3352 | javaw.exe | GET | 403 | 185.178.208.164:80 | http://runelite.site/launcher/bootstrap.json | RU | html | 9.34 Kb | suspicious |
2180 | javaw.exe | GET | 403 | 185.178.208.164:80 | http://runelite.site/launcher/bootstrap.json | RU | html | 9.34 Kb | suspicious |
3656 | javaw.exe | GET | 403 | 185.178.208.164:80 | http://runelite.site/launcher/bootstrap.json | RU | html | 9.34 Kb | suspicious |
3736 | javaw.exe | GET | 403 | 185.178.208.164:80 | http://runelite.site/launcher/bootstrap.json | RU | html | 9.34 Kb | suspicious |
3004 | chrome.exe | GET | 301 | 104.28.27.223:80 | http://runelite.ca/ | US | html | 1.14 Kb | shared |
3004 | chrome.exe | POST | 301 | 185.129.100.99:80 | http://ddgu.ddos-guard.net/ddgu/ | RU | html | 183 b | whitelisted |
3004 | chrome.exe | GET | 403 | 185.178.208.164:80 | http://runelite.site/favicon.ico | RU | html | 3.22 Kb | suspicious |
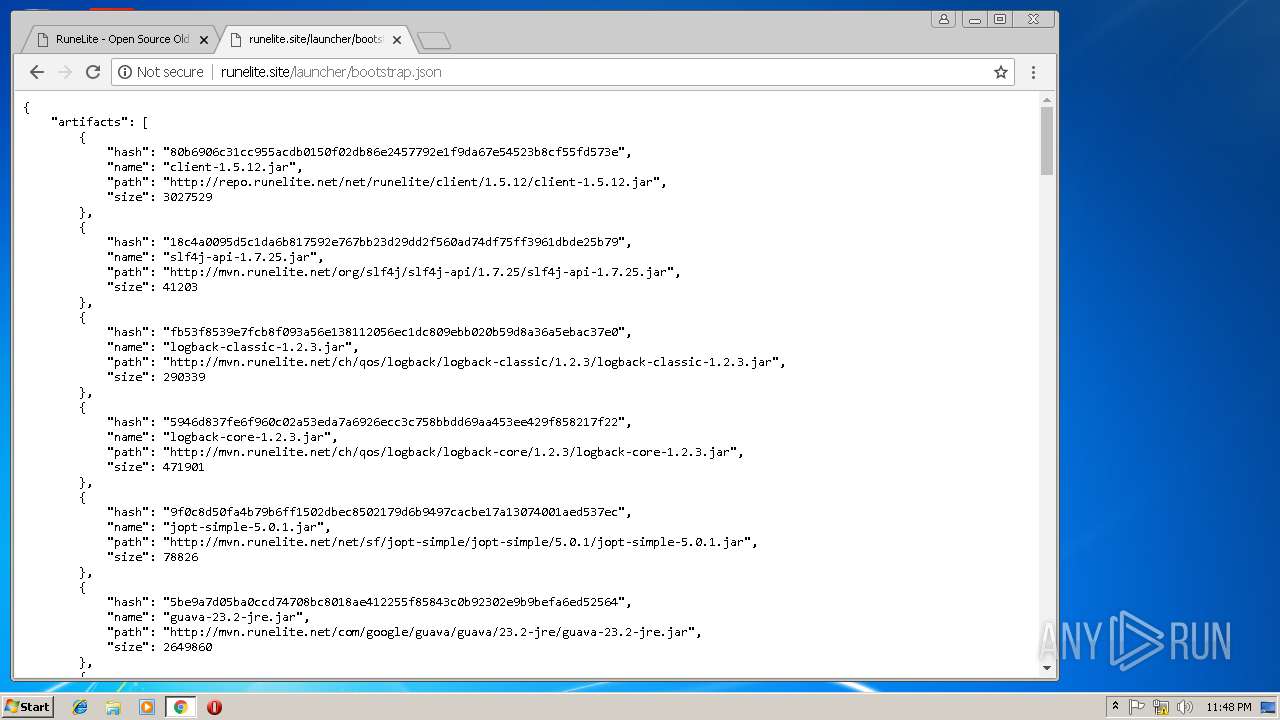
3004 | chrome.exe | GET | 200 | 185.178.208.164:80 | http://runelite.site/asm.jar | RU | html | 136 b | suspicious |
3004 | chrome.exe | GET | 301 | 185.178.208.164:80 | http://runelite.site/ddgu_JQ9Xi8A/?u=L2FzbS5qYXI=&i=YTcwNzlmMmMxYjRjYTM1NTkxN2M1OTQ5ODk5NTBlZGQuNDM3ODI5NDM0&s=Buk0vj0C6MhznCEhOhGzgxxf8DI | RU | html | 136 b | suspicious |
1364 | javaw.exe | GET | 403 | 185.178.208.164:80 | http://runelite.site/launcher/bootstrap.json | RU | html | 9.34 Kb | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3004 | chrome.exe | 172.217.16.131:443 | www.google.de | Google Inc. | US | whitelisted |
3004 | chrome.exe | 172.217.22.35:443 | www.gstatic.com | Google Inc. | US | whitelisted |
3004 | chrome.exe | 172.217.21.234:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
3004 | chrome.exe | 216.58.207.67:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
3004 | chrome.exe | 216.58.208.35:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
3004 | chrome.exe | 216.58.208.46:443 | apis.google.com | Google Inc. | US | whitelisted |
3004 | chrome.exe | 216.58.206.13:443 | accounts.google.com | Google Inc. | US | whitelisted |
3004 | chrome.exe | 104.28.27.223:80 | runelite.ca | Cloudflare Inc | US | shared |
3004 | chrome.exe | 172.217.19.196:443 | www.google.com | Google Inc. | US | whitelisted |
3004 | chrome.exe | 172.64.201.9:443 | api.runelite.net | Cloudflare Inc | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.google.de |
| whitelisted |
www.gstatic.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
safebrowsing.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
ssl.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
www.google.com |
| malicious |
runelite.ca |
| unknown |
cdn.polyfill.io |
| whitelisted |