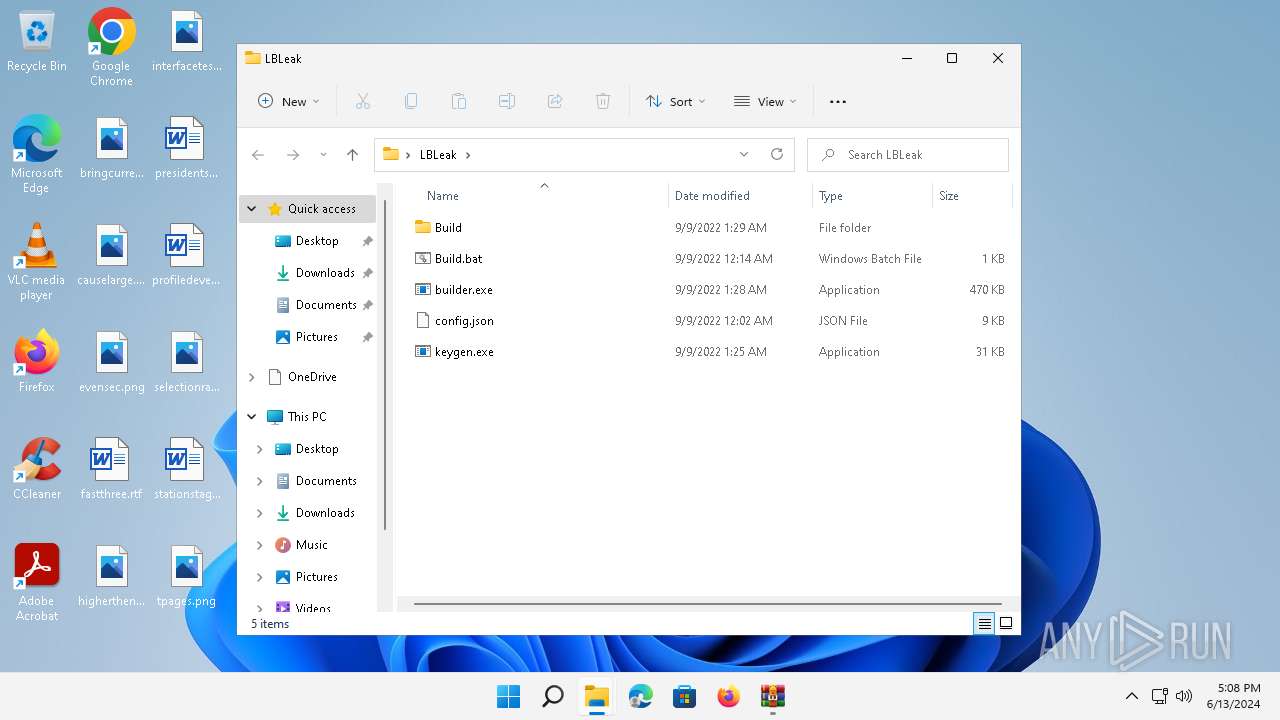
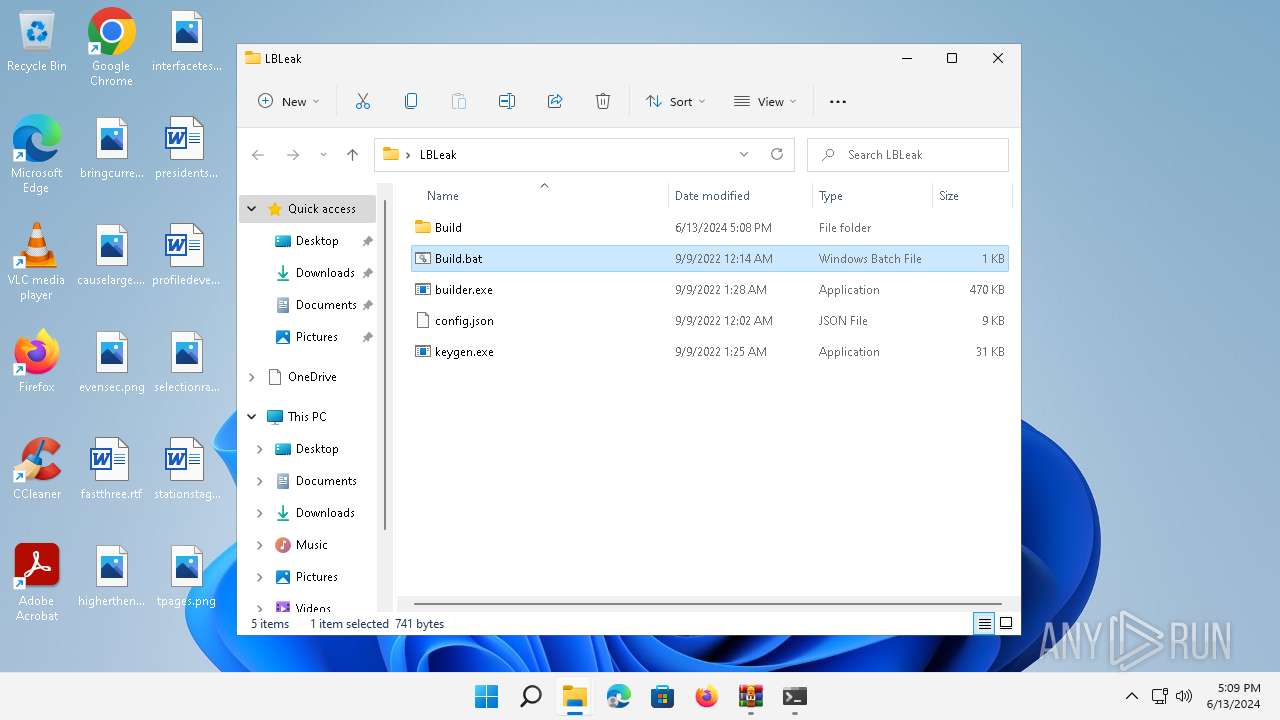
| File name: | Lockbit 3 Builder.7z |
| Full analysis: | https://app.any.run/tasks/2cb2f236-f62f-48ac-b931-2c8c649bc9fc |
| Verdict: | Malicious activity |
| Threats: | LockBit, a ransomware variant, encrypts data on infected machines, demanding a ransom payment for decryption. Used in targeted attacks, It's a significant risk to organizations. |
| Analysis date: | June 13, 2024, 17:05:54 |
| OS: | Windows 11 Professional (build: 22000, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | C9C2F3805F0012628E9D62E8F75AF4DD |
| SHA1: | B6269B1FC8813B93C11EC6066DC33D9F99F2E431 |
| SHA256: | B2C3BEDA4B000A3D9AF0A457D6D942EC81696F3ED485F7CF723B18008A5F3D10 |
| SSDEEP: | 3072:pYWJsCuSlRODbWhyyZZsZ77n4s31uZzd2ppyMPOLOcrgCz:pbuSlicZyx4W1uLYpyMPOLjhz |
MALICIOUS
Drops the executable file immediately after the start
- builder.exe (PID: 1864)
- builder.exe (PID: 3956)
- builder.exe (PID: 5228)
- builder.exe (PID: 4476)
- builder.exe (PID: 2748)
- LB3.exe (PID: 5244)
- builder.exe (PID: 1576)
Renames files like ransomware
- LB3.exe (PID: 5244)
[YARA] LockBit is detected
- LB3.exe (PID: 5244)
Known privilege escalation attack
- dllhost.exe (PID: 5708)
Steals credentials from Web Browsers
- LB3.exe (PID: 5244)
Creates a writable file in the system directory
- splwow64.exe (PID: 756)
- printfilterpipelinesvc.exe (PID: 4352)
Actions looks like stealing of personal data
- LB3.exe (PID: 5244)
Scans artifacts that could help determine the target
- ONENOTE.EXE (PID: 1216)
SUSPICIOUS
Detected use of alternative data streams (AltDS)
- WindowsTerminal.exe (PID: 2908)
Reads the date of Windows installation
- WindowsTerminal.exe (PID: 2908)
- C21D.tmp (PID: 1568)
- ONENOTE.EXE (PID: 1216)
Reads the Internet Settings
- powershell.exe (PID: 5024)
- WindowsTerminal.exe (PID: 2908)
- splwow64.exe (PID: 756)
- printfilterpipelinesvc.exe (PID: 4352)
- C21D.tmp (PID: 1568)
- Notepad.exe (PID: 4452)
- ONENOTE.EXE (PID: 1216)
Executing commands from a ".bat" file
- powershell.exe (PID: 5024)
Executable content was dropped or overwritten
- builder.exe (PID: 1576)
- builder.exe (PID: 1864)
- builder.exe (PID: 3956)
- builder.exe (PID: 5228)
- builder.exe (PID: 4476)
- builder.exe (PID: 2748)
- LB3.exe (PID: 5244)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 5024)
- C21D.tmp (PID: 1568)
Reads security settings of Internet Explorer
- WindowsTerminal.exe (PID: 2908)
- Notepad.exe (PID: 4452)
- C21D.tmp (PID: 1568)
- ONENOTE.EXE (PID: 1216)
Starts POWERSHELL.EXE for commands execution
- WindowsTerminal.exe (PID: 2908)
The process creates files with name similar to system file names
- builder.exe (PID: 4476)
Creates files like ransomware instruction
- LB3.exe (PID: 5244)
Write to the desktop.ini file (may be used to cloak folders)
- LB3.exe (PID: 5244)
Changes the desktop background image
- LB3.exe (PID: 5244)
Starts application with an unusual extension
- LB3.exe (PID: 5244)
Hides command output
- cmd.exe (PID: 5272)
Reads settings of System Certificates
- ONENOTE.EXE (PID: 1216)
Checks Windows Trust Settings
- ONENOTE.EXE (PID: 1216)
Creates file in the systems drive root
- LB3.exe (PID: 5244)
INFO
Drops the executable file immediately after the start
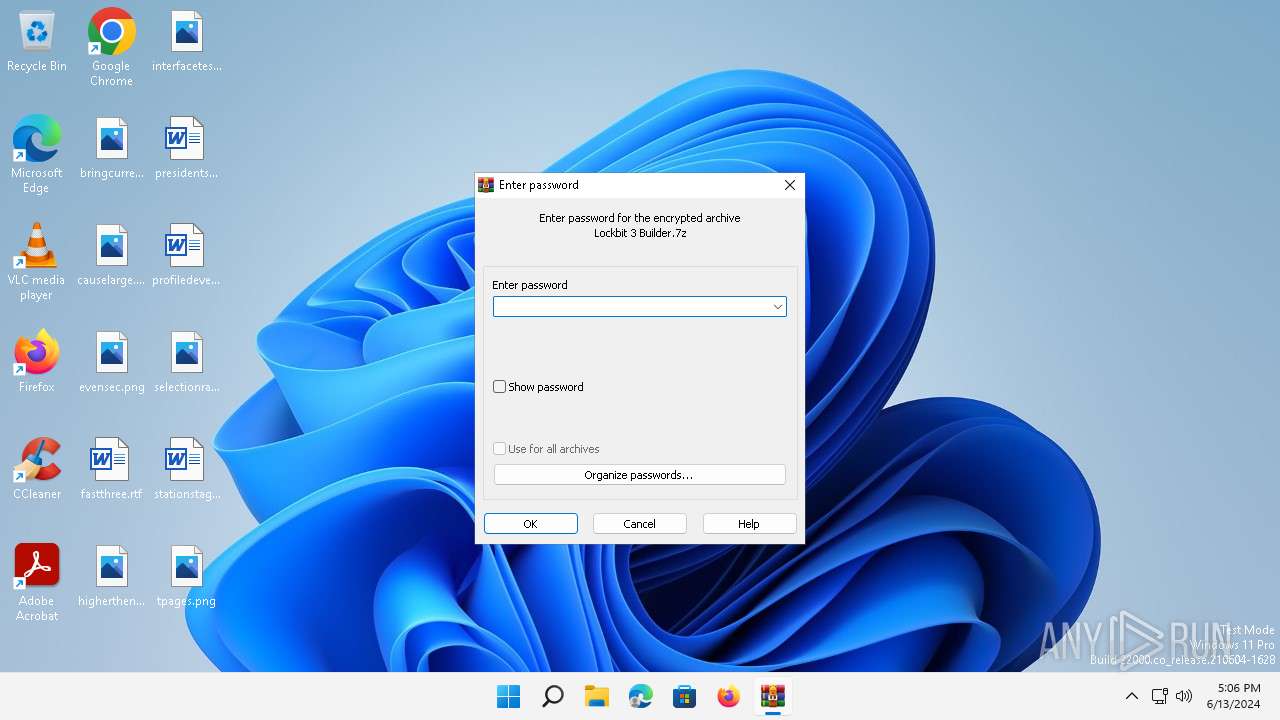
- WinRAR.exe (PID: 2412)
Dropped object may contain TOR URL's
- WinRAR.exe (PID: 2412)
- LB3.exe (PID: 5244)
Reads the computer name
- wt.exe (PID: 452)
- WindowsTerminal.exe (PID: 2908)
- Notepad.exe (PID: 4452)
- LB3.exe (PID: 4004)
- LB3.exe (PID: 5244)
- ONENOTE.EXE (PID: 1216)
- C21D.tmp (PID: 1568)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2412)
Checks supported languages
- WindowsTerminal.exe (PID: 2908)
- wt.exe (PID: 452)
- Notepad.exe (PID: 4452)
- OpenConsole.exe (PID: 1588)
- builder.exe (PID: 1864)
- keygen.exe (PID: 1480)
- builder.exe (PID: 1576)
- builder.exe (PID: 3956)
- builder.exe (PID: 4476)
- builder.exe (PID: 5228)
- LB3.exe (PID: 4004)
- builder.exe (PID: 2748)
- LB3.exe (PID: 5244)
- C21D.tmp (PID: 1568)
- ONENOTE.EXE (PID: 1216)
Manual execution by a user
- WinRAR.exe (PID: 2412)
- Notepad.exe (PID: 4452)
Checks current location (POWERSHELL)
- powershell.exe (PID: 5024)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 5024)
Gets data length (POWERSHELL)
- powershell.exe (PID: 5024)
Reads the machine GUID from the registry
- LB3.exe (PID: 4004)
- LB3.exe (PID: 5244)
- ONENOTE.EXE (PID: 1216)
Creates files or folders in the user directory
- LB3.exe (PID: 5244)
- WindowsTerminal.exe (PID: 2908)
- printfilterpipelinesvc.exe (PID: 4352)
- ONENOTE.EXE (PID: 1216)
Reads security settings of Internet Explorer
- dllhost.exe (PID: 5708)
- splwow64.exe (PID: 756)
- printfilterpipelinesvc.exe (PID: 4352)
Creates files in the program directory
- LB3.exe (PID: 5244)
Create files in a temporary directory
- LB3.exe (PID: 5244)
- ONENOTE.EXE (PID: 1216)
Reads Microsoft Office registry keys
- ONENOTE.EXE (PID: 1216)
Reads product name
- ONENOTE.EXE (PID: 1216)
Checks proxy server information
- ONENOTE.EXE (PID: 1216)
Reads the software policy settings
- ONENOTE.EXE (PID: 1216)
Reads CPU info
- ONENOTE.EXE (PID: 1216)
Reads Environment values
- ONENOTE.EXE (PID: 1216)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
129
Monitored processes
26
Malicious processes
8
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 452 | "C:\Users\admin\AppData\Local\Microsoft\WindowsApps\Microsoft.WindowsTerminal_8wekyb3d8bbwe\wt.exe" -d "C:\Users\admin\Desktop\LBLeak" | C:\Program Files\WindowsApps\Microsoft.WindowsTerminal_1.14.1963.0_x64__8wekyb3d8bbwe\wt.exe | — | dllhost.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 480 | \??\C:\Windows\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 756 | C:\Windows\splwow64.exe 12288 | C:\Windows\splwow64.exe | LB3.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Print driver host for applications Version: 10.0.22000.795 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1216 | /insertdoc "C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\{3389203F-67CA-4703-B2C2-46E1A9A8D5F4}.xps" 133627723532520000 | C:\Program Files\Microsoft Office\root\Office16\ONENOTE.EXE | printfilterpipelinesvc.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft OneNote Version: 16.0.16626.20134 Modules
| |||||||||||||||
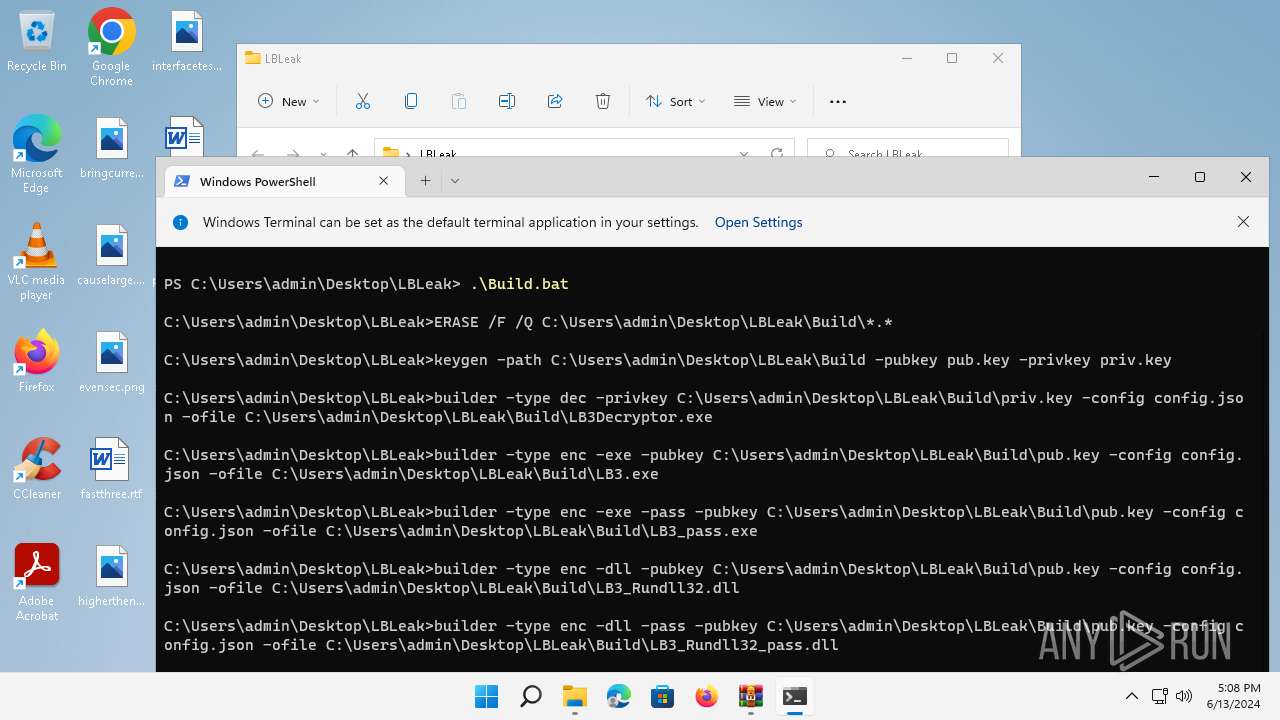
| 1480 | keygen -path C:\Users\admin\Desktop\LBLeak\Build -pubkey pub.key -privkey priv.key | C:\Users\admin\Desktop\LBLeak\keygen.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1568 | "C:\ProgramData\C21D.tmp" | C:\ProgramData\C21D.tmp | — | LB3.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
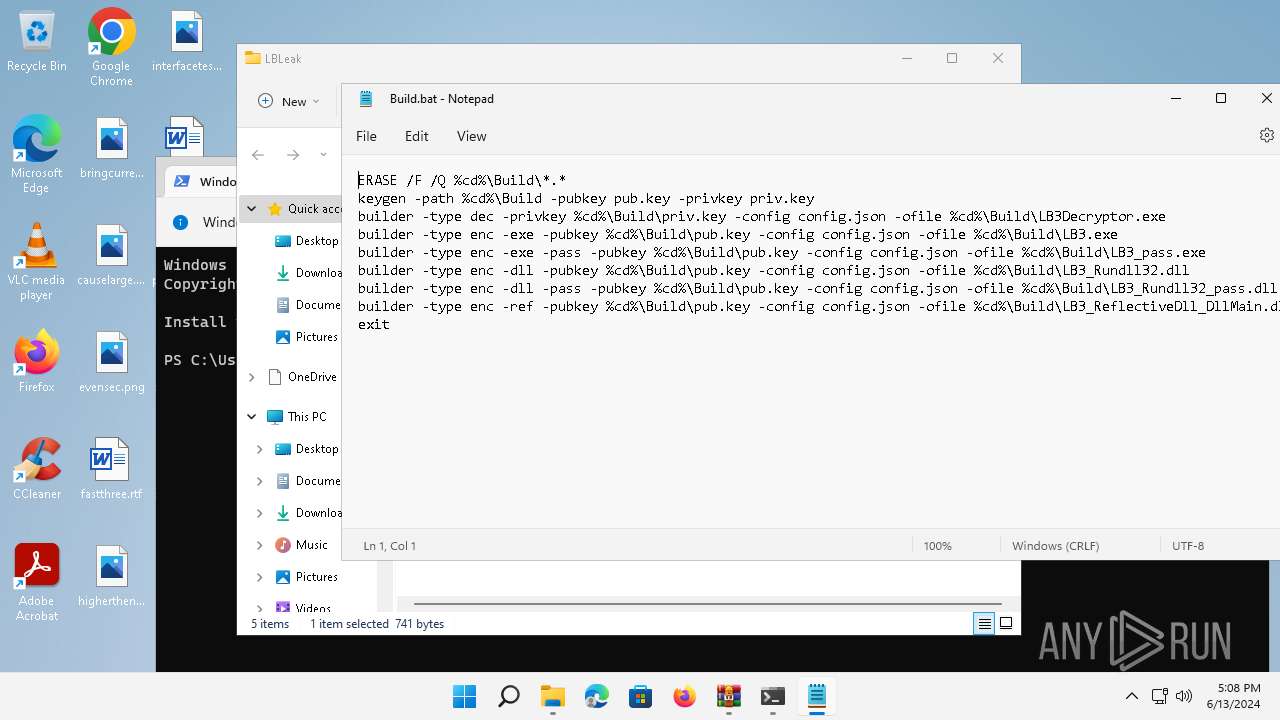
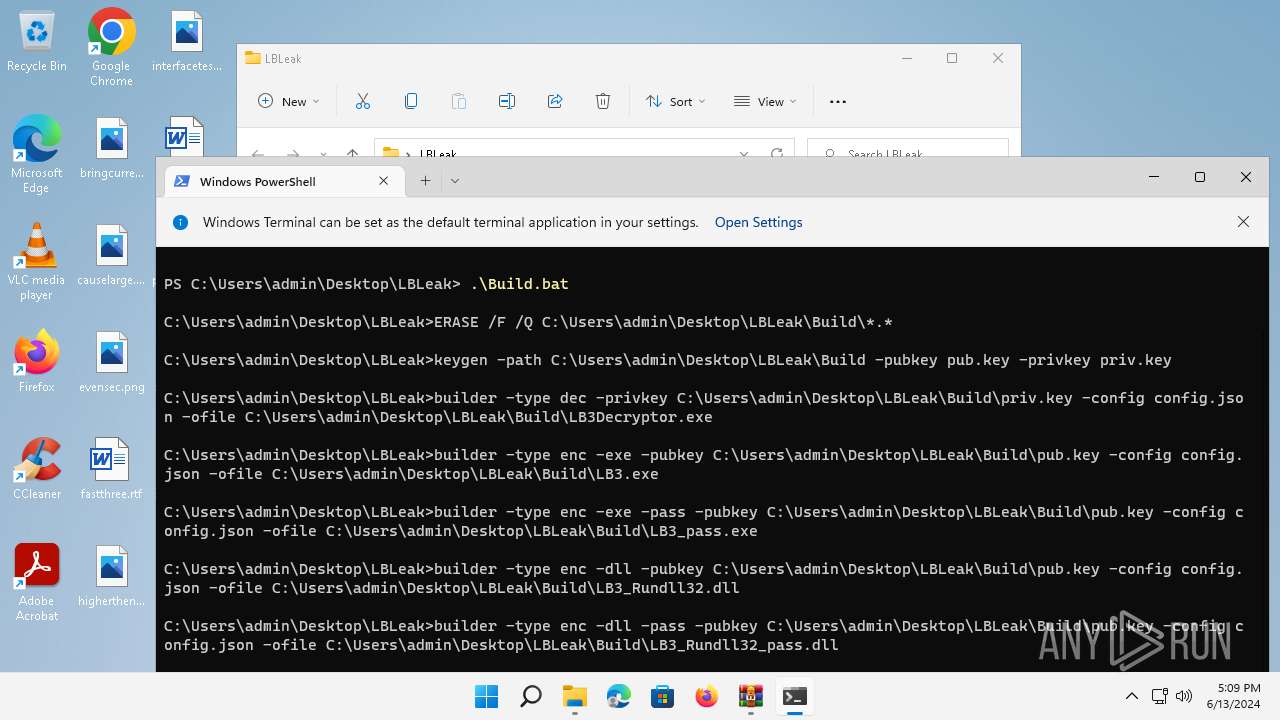
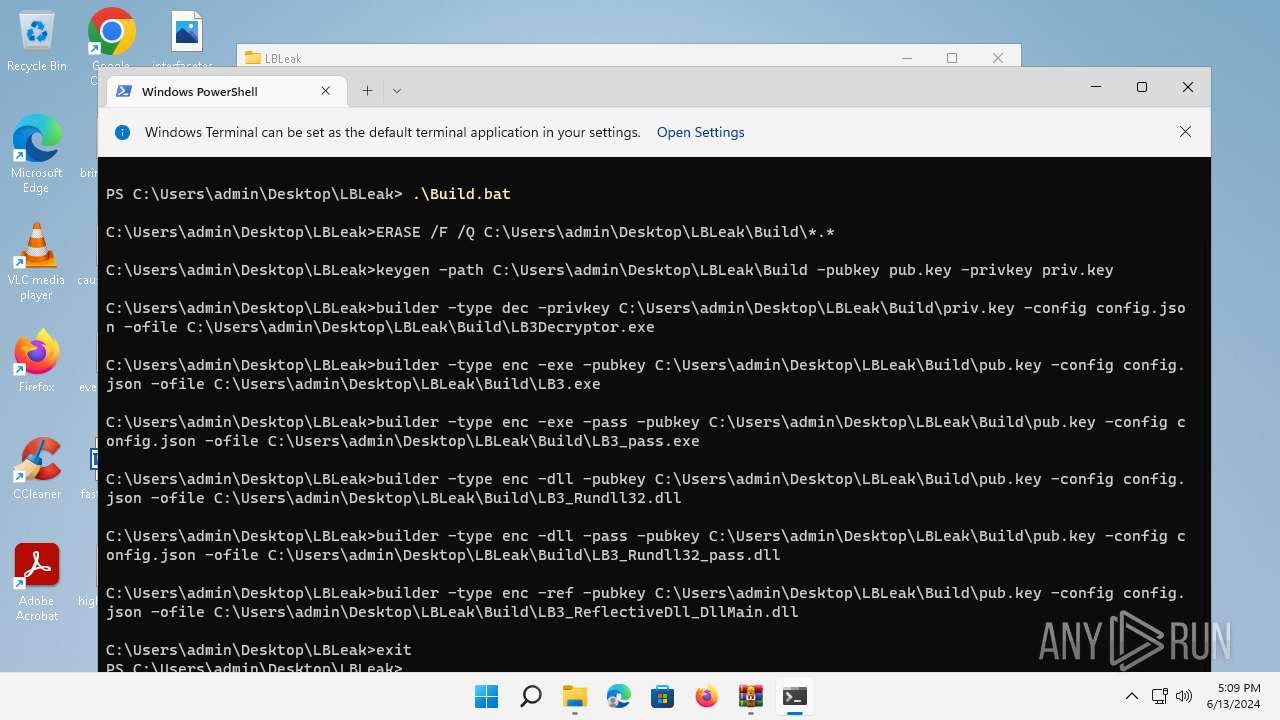
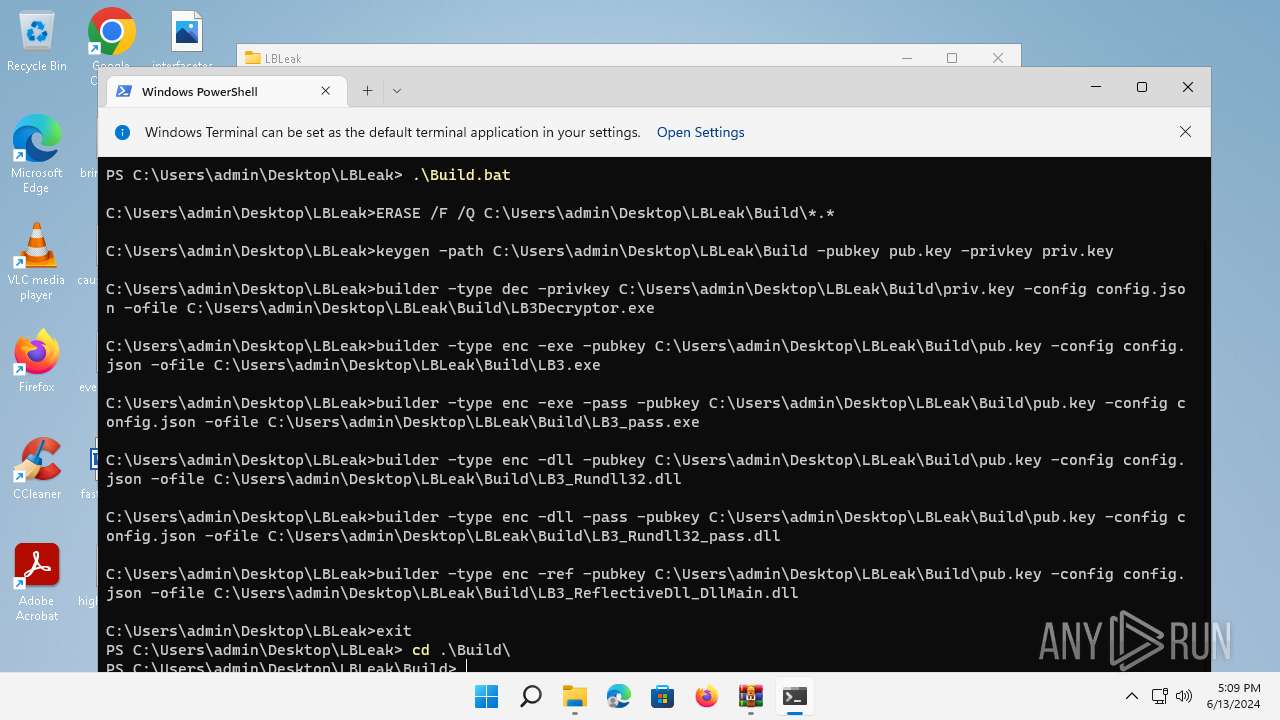
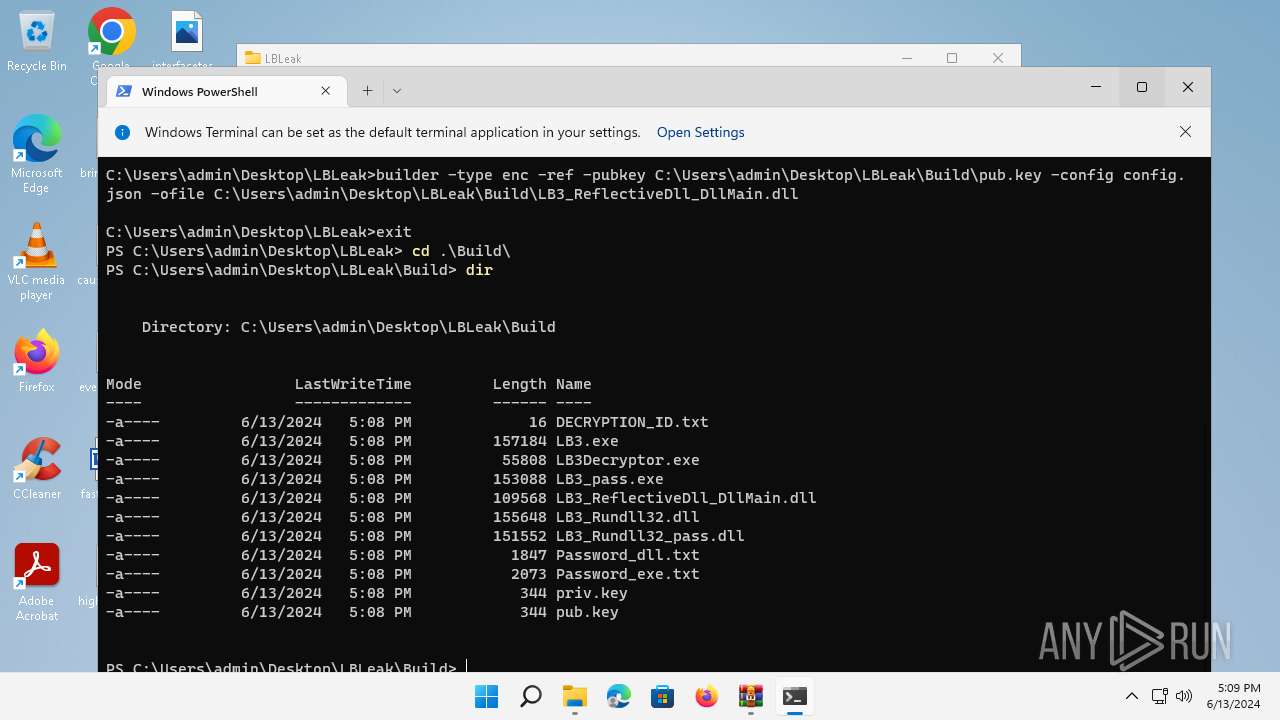
| 1576 | builder -type dec -privkey C:\Users\admin\Desktop\LBLeak\Build\priv.key -config config.json -ofile C:\Users\admin\Desktop\LBLeak\Build\LB3Decryptor.exe | C:\Users\admin\Desktop\LBLeak\builder.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1588 | "C:\Program Files\WindowsApps\Microsoft.WindowsTerminal_1.14.1963.0_x64__8wekyb3d8bbwe\OpenConsole.exe" --headless --win32input --resizeQuirk --width 120 --height 27 --signal 0x9e4 --server 0x9e0 | C:\Program Files\WindowsApps\Microsoft.WindowsTerminal_1.14.1963.0_x64__8wekyb3d8bbwe\OpenConsole.exe | — | WindowsTerminal.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 1864 | builder -type enc -exe -pubkey C:\Users\admin\Desktop\LBLeak\Build\pub.key -config config.json -ofile C:\Users\admin\Desktop\LBLeak\Build\LB3.exe | C:\Users\admin\Desktop\LBLeak\builder.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
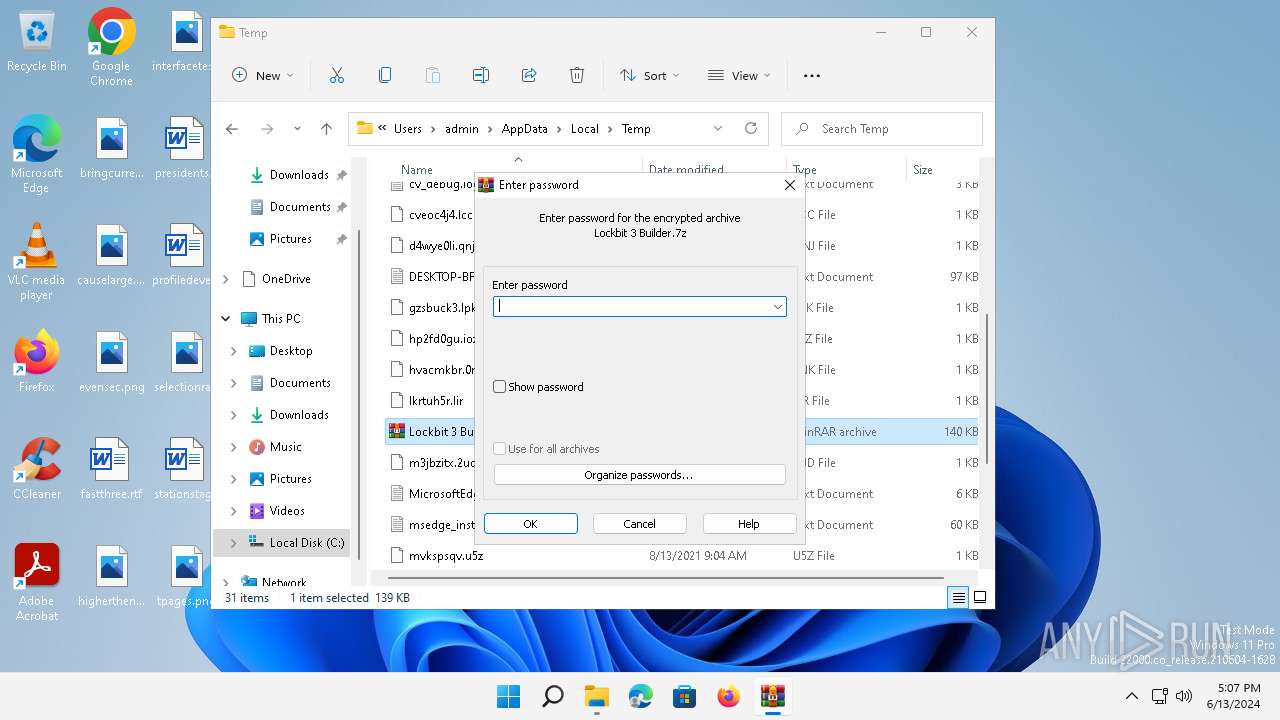
| 2412 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Lockbit 3 Builder.7z" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
40 689
Read events
38 159
Write events
2 487
Delete events
43
Modification events
| (PID) Process: | (5388) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | VerInfo |
Value: 005B0500667295FAB3BDDA01 | |||
| (PID) Process: | (5388) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (5388) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (5388) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (5388) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\AppData\Local\Temp | |||
| (PID) Process: | (5388) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5388) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5388) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5388) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5388) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General\Toolbar\Layout |
| Operation: | write | Name: | Band76_0 |
Value: 4C000000730100000402000000000000F0F0F00000000000000000000000000000000000000000004A00070000000000000000003B000000B402000000000000000000000000000001000000 | |||
Executable files
32
Suspicious files
1 733
Text files
2 348
Unknown types
79
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2412 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2412.28827\LBLeak\config.json | binary | |
MD5:A6BA7B662DE10B45EBE5B6B7EDAA62A9 | SHA256:3F7518D88AEFD4B1E0A1D6F9748F9A9960C1271D679600E34F5065D8DF8C9DC8 | |||
| 1480 | keygen.exe | C:\Users\admin\Desktop\LBLeak\Build\priv.key | text | |
MD5:C761C79FDA5DCAA5741E4BDCD1D9DD02 | SHA256:400465E7749916C8960D109D6B2D59C4679FC64F65C48472F505200E821D8050 | |||
| 3956 | builder.exe | C:\Users\admin\Desktop\LBLeak\Build\Password_exe.txt | text | |
MD5:C34633DF02F4386C649C010E06AE7A2D | SHA256:1AC3C68F54DC11D51BA6E151BB03EF0A3F52BFFBDA61128C36FFD4E41612793D | |||
| 1576 | builder.exe | C:\Users\admin\Desktop\LBLeak\Build\LB3Decryptor.exe | executable | |
MD5:D5005BD4E6B86FA2AD67300A0C267A97 | SHA256:D5658C10AF781E5697273BFD5F0CA2EEC8D7A5025DEC2F0FDB70B149D6F960B9 | |||
| 4476 | builder.exe | C:\Users\admin\Desktop\LBLeak\Build\LB3_Rundll32.dll | executable | |
MD5:A810E1D7B35925059FED291877DC166D | SHA256:7B8BB31F28FAD9CC9AC17602F152153E070F6F5915DAB0FC6054E5D85D9E0833 | |||
| 2908 | WindowsTerminal.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\JRS43J02L2YM54RBTX0M.temp | binary | |
MD5:01381A33F86649FB5AF55C60025E4507 | SHA256:78A445DFB4CD9CD4E4852CDC733D55712F57EA072F842FA91361ED7B4A320B0C | |||
| 5388 | WinRAR.exe | C:\USERS\ADMIN\APPDATA\ROAMING\WINRAR\VERSION.DAT | binary | |
MD5:933712A1B50E5E1F1293CCD0B7C3CC47 | SHA256:565AF8706A67FD7B6C84D0C41258906BC34E7E03979AE56F3B545FA7C5C59FA5 | |||
| 2412 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2412.28827\LBLeak\builder.exe | executable | |
MD5:8C689DC9E82C9356B990D2B67B4943E1 | SHA256:E8E2DEB0A83AEBB1E2CC14846BC71715343372103F279D2D1622E383FB26D6EF | |||
| 2412 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2412.28827\LBLeak\Build.bat | text | |
MD5:4E46E28B2E61643F6AF70A8B19E5CB1F | SHA256:8E83A1727696CED618289F79674B97305D88BEEEABF46BD25FC77AC53C1AE339 | |||
| 2908 | WindowsTerminal.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\16f2f0042ddbe0e8.customDestinations-ms~RF128313.TMP | binary | |
MD5:35F7CB74FE5446764D34580D180505B6 | SHA256:40526E2FC7874D00C634694249F85AB7E92A7F019FC97A950C1B452DD8195EA6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
26
DNS requests
12
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | POST | 403 | 23.53.113.159:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
— | — | POST | 403 | 23.53.113.159:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
— | — | POST | 403 | 23.53.113.159:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
— | — | POST | 403 | 23.53.113.159:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
2828 | svchost.exe | GET | 200 | 95.101.63.72:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/pinrulesstl.cab?3a3082f95a18b6d2 | unknown | — | — | unknown |
2828 | svchost.exe | GET | 200 | 95.101.63.72:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/pinrulesstl.cab?17b2b73c54e86f00 | unknown | — | — | unknown |
3444 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
— | — | POST | 403 | 23.53.113.159:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
— | — | POST | 403 | 23.53.113.159:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
— | — | POST | 403 | 23.53.113.159:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5880 | svchost.exe | 23.53.114.19:443 | fs.microsoft.com | AKAMAI-AS | US | unknown |
— | — | 23.53.113.159:80 | go.microsoft.com | AKAMAI-AS | US | unknown |
4552 | svchost.exe | 239.255.255.250:1900 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2868 | OfficeClickToRun.exe | 20.189.173.26:443 | self.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
2868 | OfficeClickToRun.exe | 192.229.221.95:80 | — | EDGECAST | US | whitelisted |
2828 | svchost.exe | 95.101.63.72:80 | ctldl.windowsupdate.com | Akamai International B.V. | GB | unknown |
2844 | svchost.exe | 52.182.143.213:443 | v20.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
2844 | svchost.exe | 13.89.179.11:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
1216 | ONENOTE.EXE | 52.109.32.97:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
fs.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
v20.events.data.microsoft.com |
| whitelisted |
dns.msftncsi.com |
| shared |
officeclient.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ecs.office.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET INFO Microsoft Connection Test |
Process | Message |
|---|---|
splwow64.exe | Invalid parameter passed to C runtime function.
|