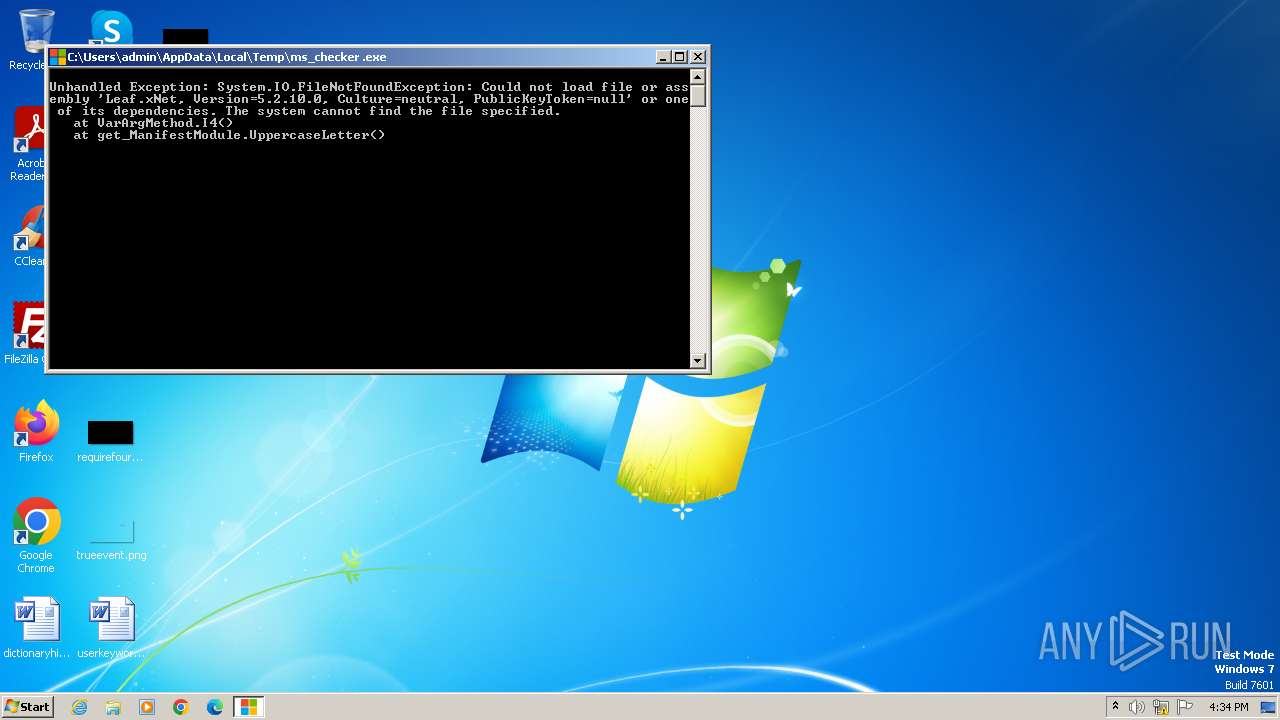
| File name: | ms_checker.exe |
| Full analysis: | https://app.any.run/tasks/d6e5f945-37ba-4ec0-a372-d60af83b5720 |
| Verdict: | Malicious activity |
| Analysis date: | December 02, 2023, 16:33:57 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | AE53A4D932EB1FD5364B6E3D2185C97A |
| SHA1: | A8E7C84CEF4E312BAAEF43550ABB6BE86F25FFF9 |
| SHA256: | B2C2EB4394981F5E31A7795C75DF519403C8B06C3776F3F9CFC9BAA65942823C |
| SSDEEP: | 6144:Gml7Bj9TL8haPe0oaE1fvvkYlLnmc5+ew+ndcXEb0lNXcmNdUgAYFTTQ9e:vJBdpPe0oazozndxOZTUgAYFX |
MALICIOUS
Drops the executable file immediately after the start
- ms_checker.exe (PID: 2980)
- Setup.exe (PID: 1236)
- svchost.exe (PID: 2464)
SUSPICIOUS
Process drops legitimate windows executable
- ms_checker.exe (PID: 2980)
- svchost.exe (PID: 2464)
- Setup.exe (PID: 1236)
Reads the Internet Settings
- ms_checker.exe (PID: 2980)
- svchost.exe (PID: 2464)
- Setup.exe (PID: 1236)
The process creates files with name similar to system file names
- Setup.exe (PID: 1236)
- svchost.exe (PID: 2464)
Reads settings of System Certificates
- svchost.exe (PID: 2464)
INFO
Checks supported languages
- ms_checker.exe (PID: 2980)
- Setup.exe (PID: 1236)
- Setup.exe (PID: 2740)
- ms_checker .exe (PID: 3816)
- svchost.exe (PID: 2464)
- wmpnscfg.exe (PID: 684)
- explorer.exe (PID: 2336)
Reads the computer name
- ms_checker.exe (PID: 2980)
- ms_checker .exe (PID: 3816)
- Setup.exe (PID: 2740)
- Setup.exe (PID: 1236)
- svchost.exe (PID: 2464)
- wmpnscfg.exe (PID: 684)
- explorer.exe (PID: 2336)
Create files in a temporary directory
- ms_checker.exe (PID: 2980)
- svchost.exe (PID: 2464)
Reads the machine GUID from the registry
- ms_checker.exe (PID: 2980)
- Setup.exe (PID: 1236)
- Setup.exe (PID: 2740)
- ms_checker .exe (PID: 3816)
- svchost.exe (PID: 2464)
- explorer.exe (PID: 2336)
Creates files or folders in the user directory
- Setup.exe (PID: 1236)
- svchost.exe (PID: 2464)
Manual execution by a user
- wmpnscfg.exe (PID: 684)
Reads Environment values
- svchost.exe (PID: 2464)
- explorer.exe (PID: 2336)
Reads product name
- explorer.exe (PID: 2336)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (45.1) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (19.2) |
| .exe | | | Win64 Executable (generic) (17) |
| .scr | | | Windows screen saver (8) |
| .dll | | | Win32 Dynamic Link Library (generic) (4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:02:26 12:22:38+01:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 631808 |
| InitializedDataSize: | 7168 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x9c35e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
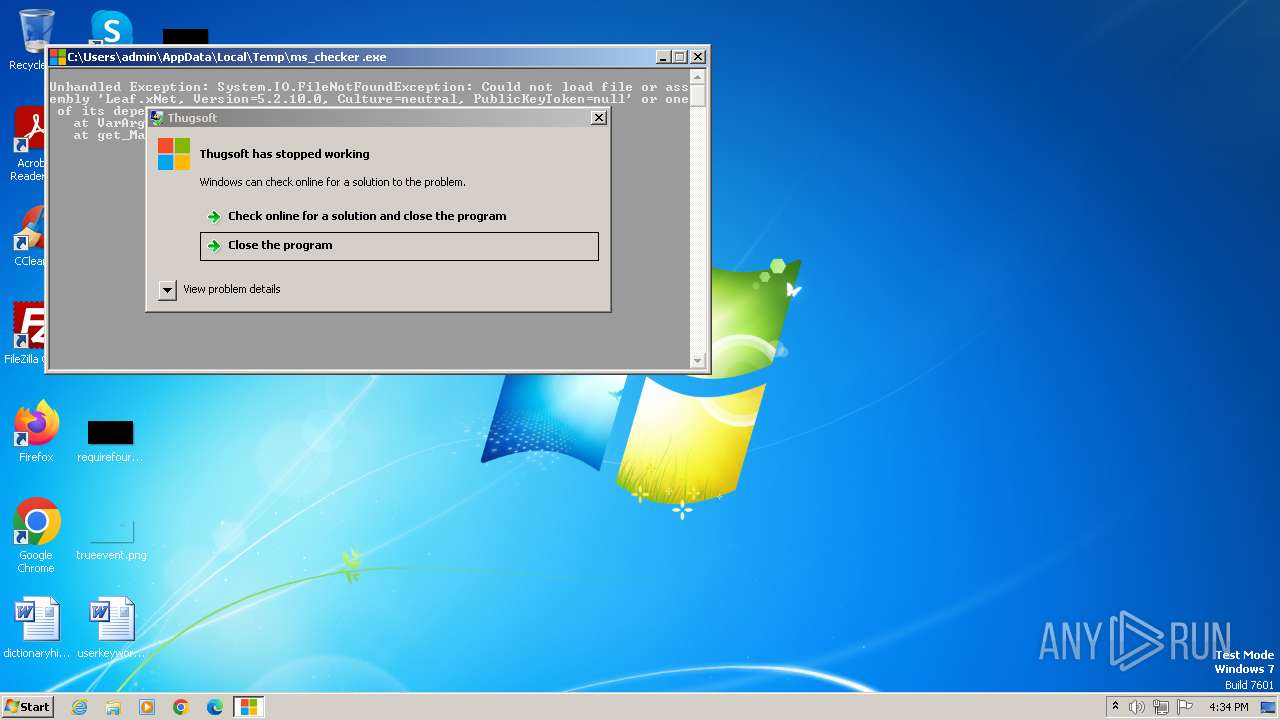
| Comments: | Thugsoft |
| FileDescription: | Thugsoft |
| FileVersion: | 1.0.0.0 |
| InternalName: | ms_checker.exe |
| LegalCopyright: | Copyright © 2022 |
| OriginalFileName: | ms_checker.exe |
| ProductName: | Thugxhunter#0064 |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
45
Monitored processes
7
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 684 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1236 | "C:\Users\admin\AppData\Local\Temp\Setup.exe" | C:\Users\admin\AppData\Local\Temp\Setup.exe | — | ms_checker.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2336 | "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Templates\explorer.exe" | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Templates\explorer.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 10.0.22621.2283 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2464 | "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Templates\svchost.exe" | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Templates\svchost.exe | Setup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Exit code: 0 Version: 8.1.1.7900 Modules
| |||||||||||||||
| 2740 | "C:\Users\admin\AppData\Local\Temp\Setup.exe" | C:\Users\admin\AppData\Local\Temp\Setup.exe | — | ms_checker.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2980 | "C:\Users\admin\AppData\Local\Temp\ms_checker.exe" | C:\Users\admin\AppData\Local\Temp\ms_checker.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Thugsoft Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3816 | "C:\Users\admin\AppData\Local\Temp\ms_checker .exe" | C:\Users\admin\AppData\Local\Temp\ms_checker .exe | ms_checker.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Thugsoft Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
6 033
Read events
5 998
Write events
35
Delete events
0
Modification events
| (PID) Process: | (2980) ms_checker.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2980) ms_checker.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2980) ms_checker.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2980) ms_checker.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1236) Setup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1236) Setup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1236) Setup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1236) Setup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2464) svchost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\181\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2464) svchost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
4
Suspicious files
2
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2980 | ms_checker.exe | C:\Users\admin\AppData\Local\Temp\ms_checker .exe | executable | |
MD5:2F56DFC5CE7B60DEE948898400A43089 | SHA256:05C95E3E773BA3AE846861FEFCCDFB33CAAED971B98DF57605615C39D0500A53 | |||
| 1236 | Setup.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Templates\svchost.exe | executable | |
MD5:23CE98B7618B4FEB3C10BEE606D171BD | SHA256:520D313DB85B0B768DF9AB47E1F13B8B38A2B77DB505A3BB268709E02ED1C881 | |||
| 2464 | svchost.exe | C:\Users\admin\AppData\Local\Temp\explorer.txt | text | |
MD5:2694465DFE4A5123F2A998366D7E488D | SHA256:9A7F4DEC22798E28AC786C06226197AEC1076962E4928B364AB0AF808D08E9F6 | |||
| 1236 | Setup.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Templates\svchost.zip | compressed | |
MD5:D2D9035C0AEB4CA5BA1A079DBA3C1710 | SHA256:1562959C5E47D9877668025EE56BEED0AD0306681F4F092C731A544FA4A4AD7D | |||
| 2464 | svchost.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Templates\explorer.zip | compressed | |
MD5:7ECA085E07E2426A3E07B977EAF19CEC | SHA256:865BE5E48FB179C6A76AF2774A528EF97F257E10622A836A5D6FA86557BC3B15 | |||
| 2464 | svchost.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Templates\explorer.exe | executable | |
MD5:A47C7D6D618A520262CF33BF54DD065A | SHA256:D8C5777404C492F67BAAF5BFC37C6C637065563829B6C1A1D7EAF004ACDC9B95 | |||
| 2980 | ms_checker.exe | C:\Users\admin\AppData\Local\Temp\Setup.exe | executable | |
MD5:9517D7244D78816CFF2AFAE70910108B | SHA256:04A0F8CF8ADD38E5826FAE2CDE3990A40482AE73BAD5E11D10739B7380086F55 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
8
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2464 | svchost.exe | GET | 200 | 107.180.41.239:80 | http://amazonhost.thedreamsop.com/2022/explorer.txt | unknown | text | 37 b | unknown |
2464 | svchost.exe | HEAD | 200 | 107.180.41.239:80 | http://amazonhost.thedreamsop.com/2022/explorer.txt | unknown | — | — | unknown |
2464 | svchost.exe | GET | 200 | 107.180.41.239:80 | http://amazonhost.thedreamsop.com/2022/explorer.txt | unknown | text | 37 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2464 | svchost.exe | 107.180.41.239:80 | amazonhost.thedreamsop.com | AS-26496-GO-DADDY-COM-LLC | US | unknown |
2464 | svchost.exe | 172.217.16.129:443 | 24-06-2022-8080.blogspot.com | GOOGLE | US | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
amazonhost.thedreamsop.com |
| unknown |
24-06-2022-8080.blogspot.com |
| unknown |