| download: | radmin.exe |
| Full analysis: | https://app.any.run/tasks/cd7794e2-98b2-44ef-9f6d-a0e75e8c44b9 |
| Verdict: | No threats detected |
| Analysis date: | December 12, 2018, 18:15:55 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| MIME: | text/html |
| File info: | HTML document, UTF-8 Unicode text, with very long lines |
| MD5: | 13A849D40A33DDC82E087FB5DCF4C81A |
| SHA1: | 14E59DA8020A29CBF4D594C4CD20C45FC38CF0B4 |
| SHA256: | B2AD3F3CE8C9192EA7F670284AD46F3895A44E2C95738B6D253137208A837EC2 |
| SSDEEP: | 1536:osOq6/0GAkCAkUAkof6OMx2GwRtWLIPZU8GpLS+hHqoSkacSQz3Kpu7MnfTj5dTS:osOq6/9AkCAkUAkWTlGwRtWLIPZU8GpF |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
EXIF
HTML
| viewport: | width=device-width |
|---|---|
| Title: | kali-windows-binaries/radmin.exe at master · interference-security/kali-windows-binaries · GitHub |
| Description: | Windows binaries from Kali Linux : http://git.kali.org/gitweb/?p=packages/windows-binaries.git;a=summary - interference-security/kali-windows-binaries |
| pjaxTimeout: | 1000 |
| requestId: | A834:186B:11C1C07:213EED4:5C11505C |
| googleSiteVerification: | GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc |
| octolyticsHost: | collector.githubapp.com |
| octolyticsAppId: | github |
| octolyticsEventUrl: | https://collector.githubapp.com/github-external/browser_event |
| octolyticsDimensionRequest_id: | A834:186B:11C1C07:213EED4:5C11505C |
| octolyticsDimensionRegion_edge: | iad |
| octolyticsDimensionRegion_render: | iad |
| analyticsLocation: | /<user-name>/<repo-name>/blob/show |
| googleAnalytics: | UA-3769691-2 |
| dimension1: | Logged Out |
| hostname: | github.com |
| userLogin: | - |
| expectedHostname: | github.com |
| jsProxySiteDetectionPayload: | NWFmYzViZGUzY2IzOTMwMmJmMWMzZWU1NDFjY2U0MzFhMzczNTQyOGVjODk2NWUwNDQzODRkOGM0ZmY0YzFiNnx7InJlbW90ZV9hZGRyZXNzIjoiMTg1Ljc2LjkuNjciLCJyZXF1ZXN0X2lkIjoiQTgzNDoxODZCOjExQzFDMDc6MjEzRUVENDo1QzExNTA1QyIsInRpbWVzdGFtcCI6MTU0NDYzODU1NywiaG9zdCI6ImdpdGh1Yi5jb20ifQ== |
| enabledFeatures: | DASHBOARD_V2_LAYOUT_OPT_IN,EXPLORE_DISCOVER_REPOSITORIES,UNIVERSE_BANNER,MARKETPLACE_PLAN_RESTRICTION_EDITOR |
| htmlSafeNonce: | 5499cd90821aac1db4f080c87d4f976a81152538 |
| HTTPEquivXPjaxVersion: | a7a83253e3e62eb65b9aaa79234e1c6c |
| goImport: | github.com/interference-security/kali-windows-binaries git https://github.com/interference-security/kali-windows-binaries.git |
| octolyticsDimensionUser_id: | 5358495 |
| octolyticsDimensionUser_login: | interference-security |
| octolyticsDimensionRepository_id: | 50012706 |
| octolyticsDimensionRepository_nwo: | interference-security/kali-windows-binaries |
| octolyticsDimensionRepository_public: | |
| octolyticsDimensionRepository_is_fork: | - |
| octolyticsDimensionRepository_network_root_id: | 50012706 |
| octolyticsDimensionRepository_network_root_nwo: | interference-security/kali-windows-binaries |
| octolyticsDimensionRepository_explore_github_marketplace_ci_cta_shown: | - |
| browserStatsUrl: | https://api.github.com/_private/browser/stats |
| browserErrorsUrl: | https://api.github.com/_private/browser/errors |
| themeColor: | #1e2327 |
Total processes
31
Monitored processes
1
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
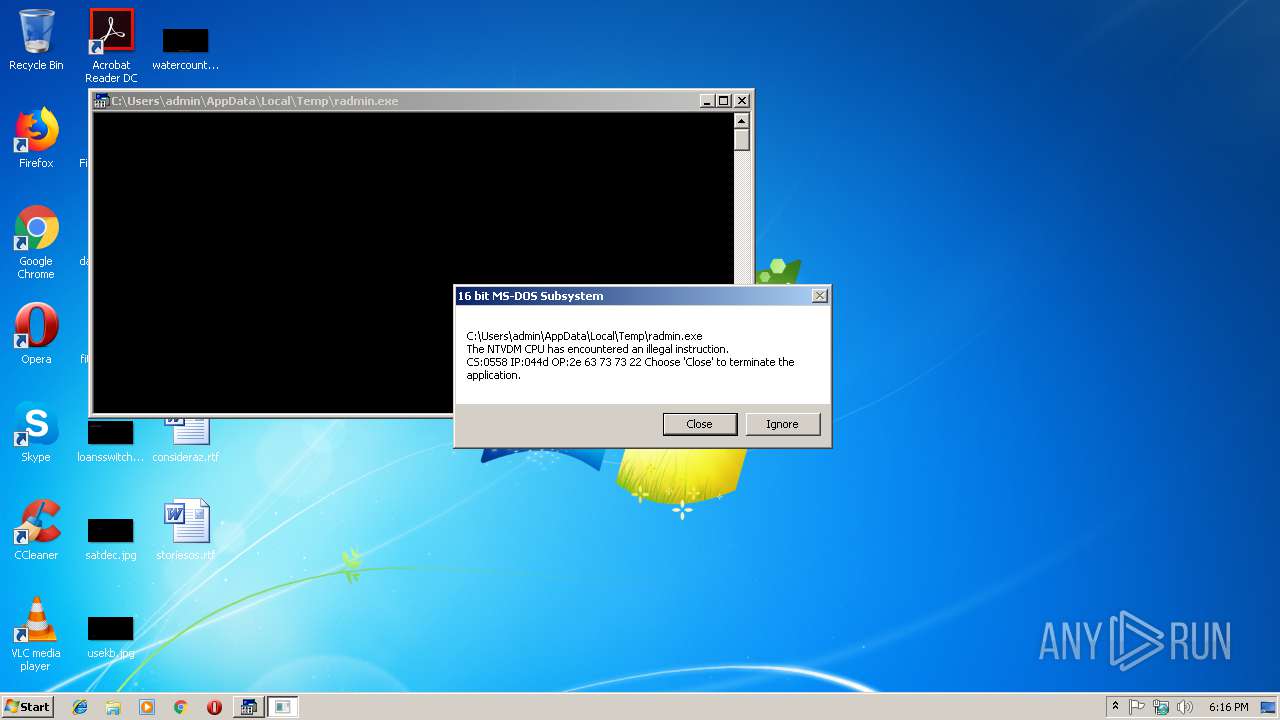
| 3188 | "C:\Windows\system32\ntvdm.exe" -i1 | C:\Windows\system32\ntvdm.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: NTVDM.EXE Exit code: 255 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
0
Read events
0
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3188 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scs92D0.tmp | — | |
MD5:— | SHA256:— | |||
| 3188 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scs92F0.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report