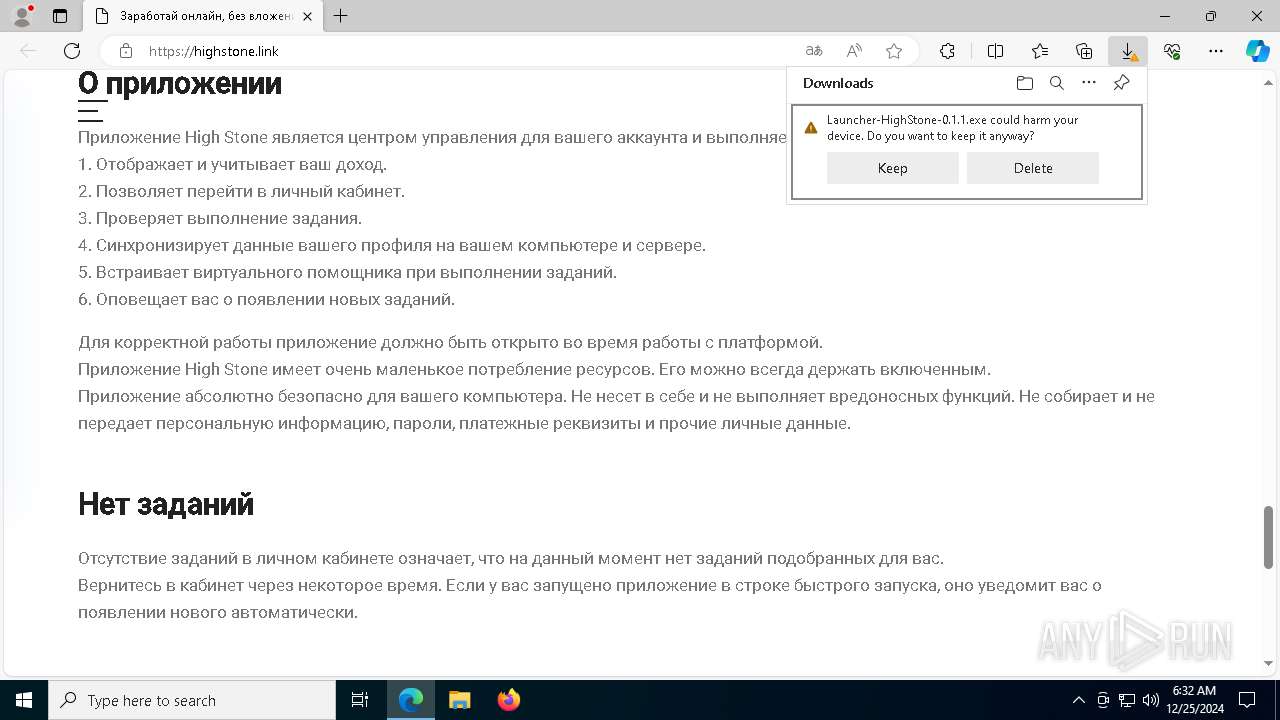
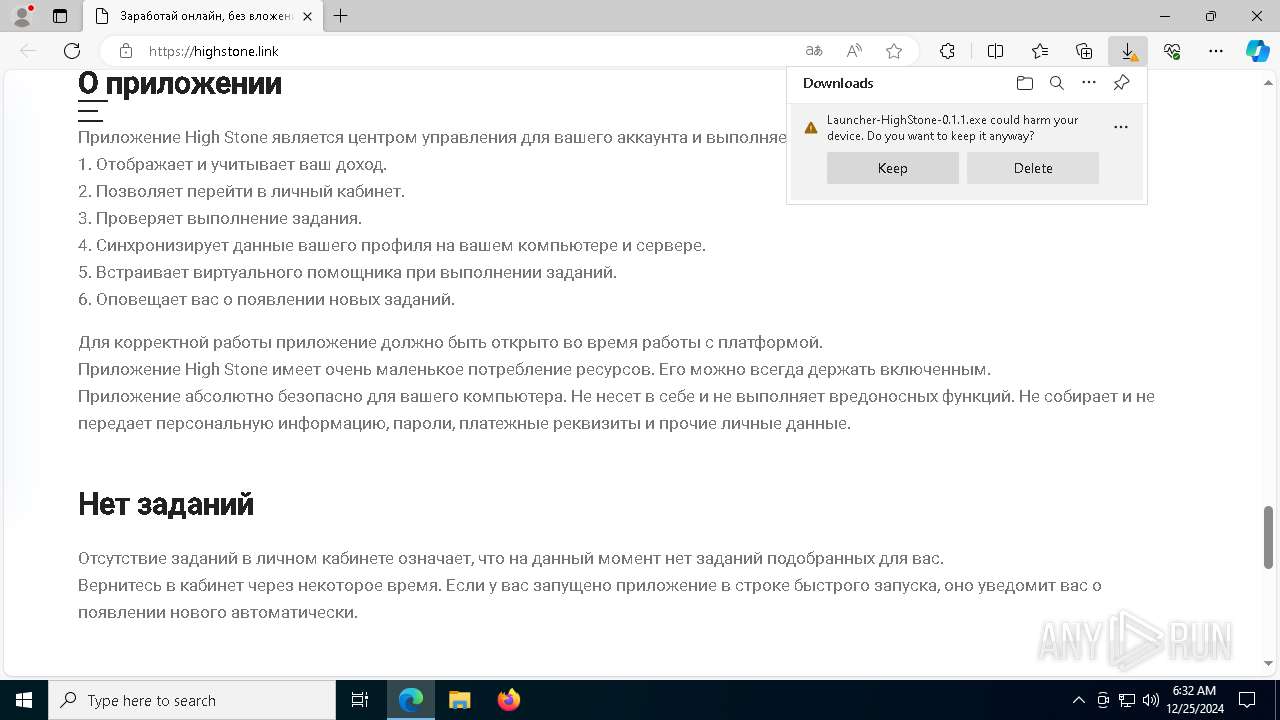
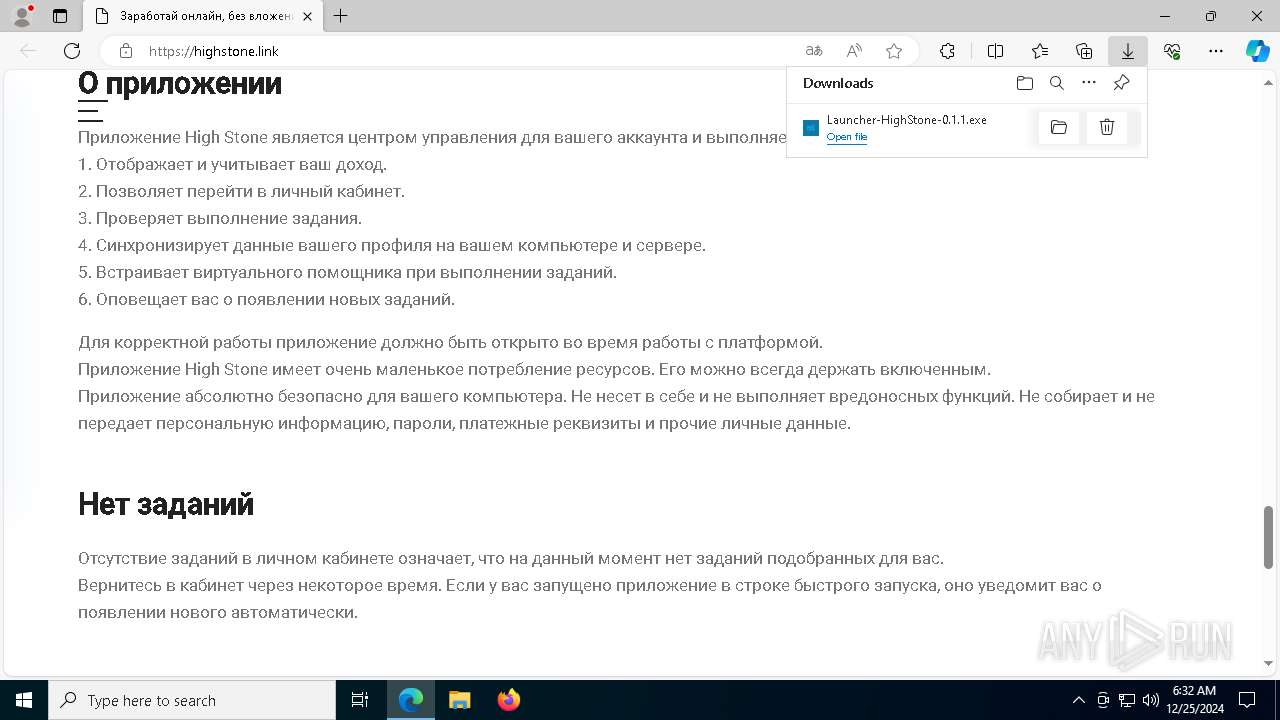
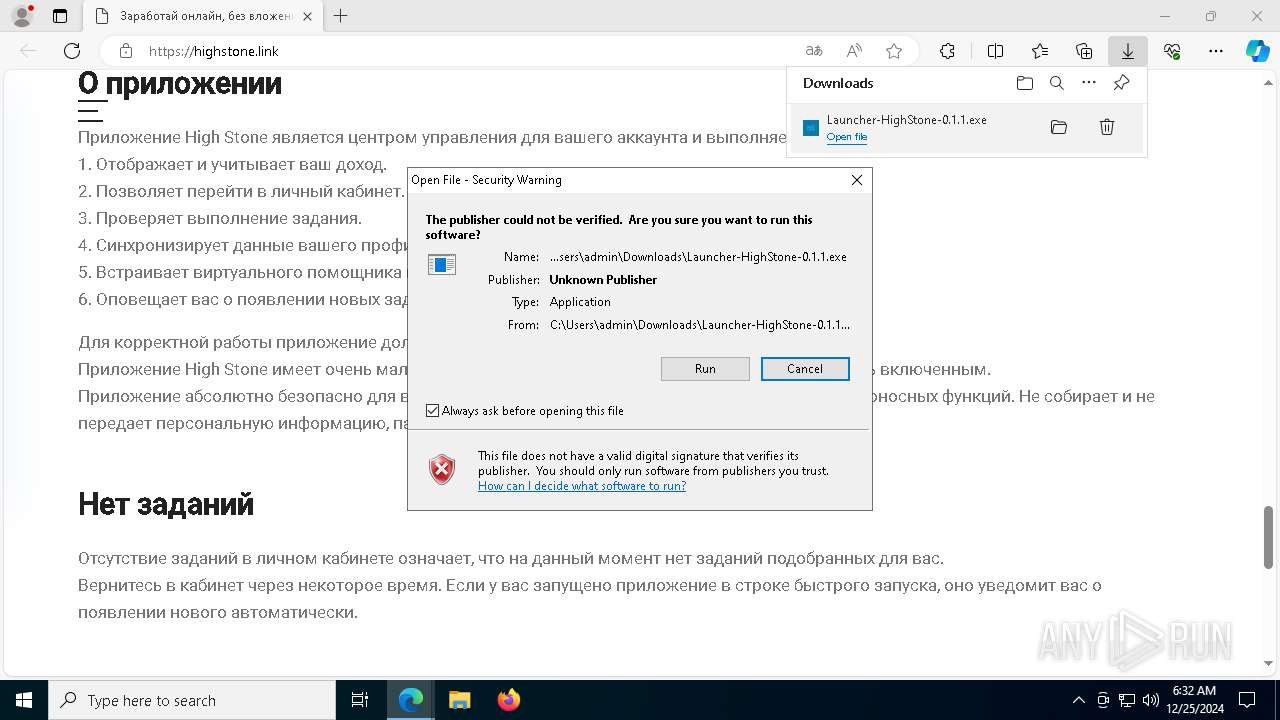
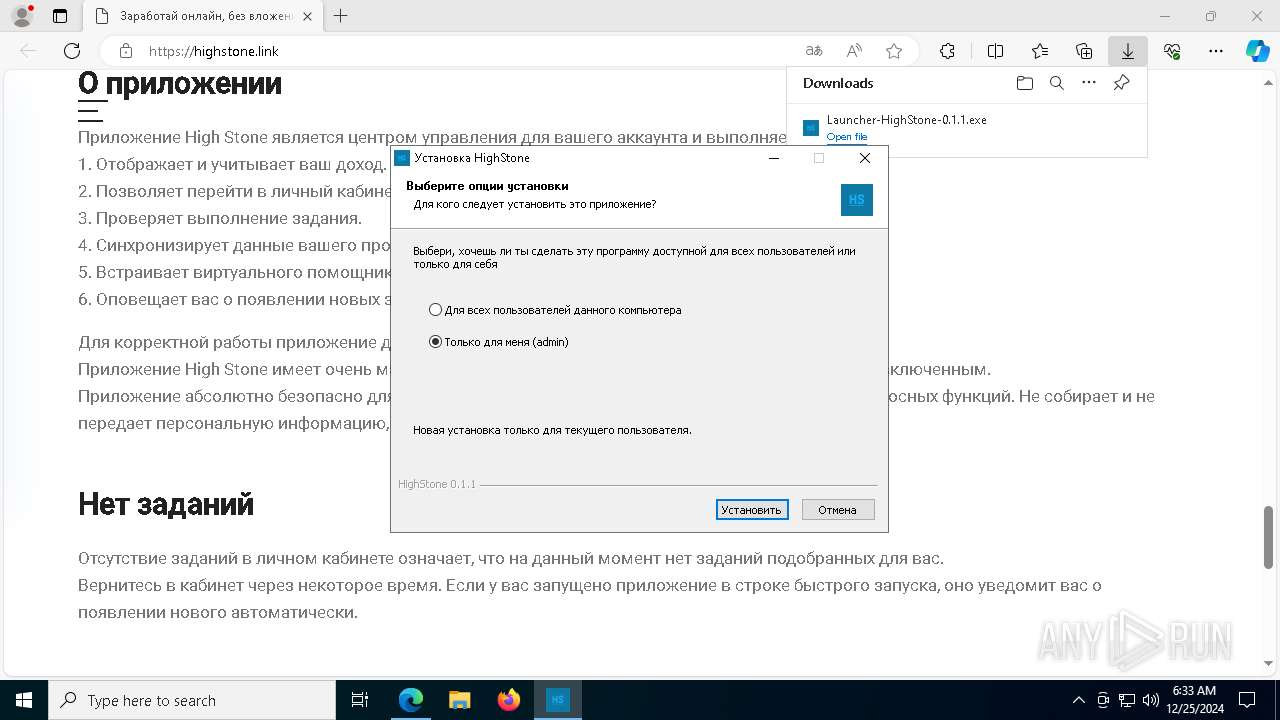
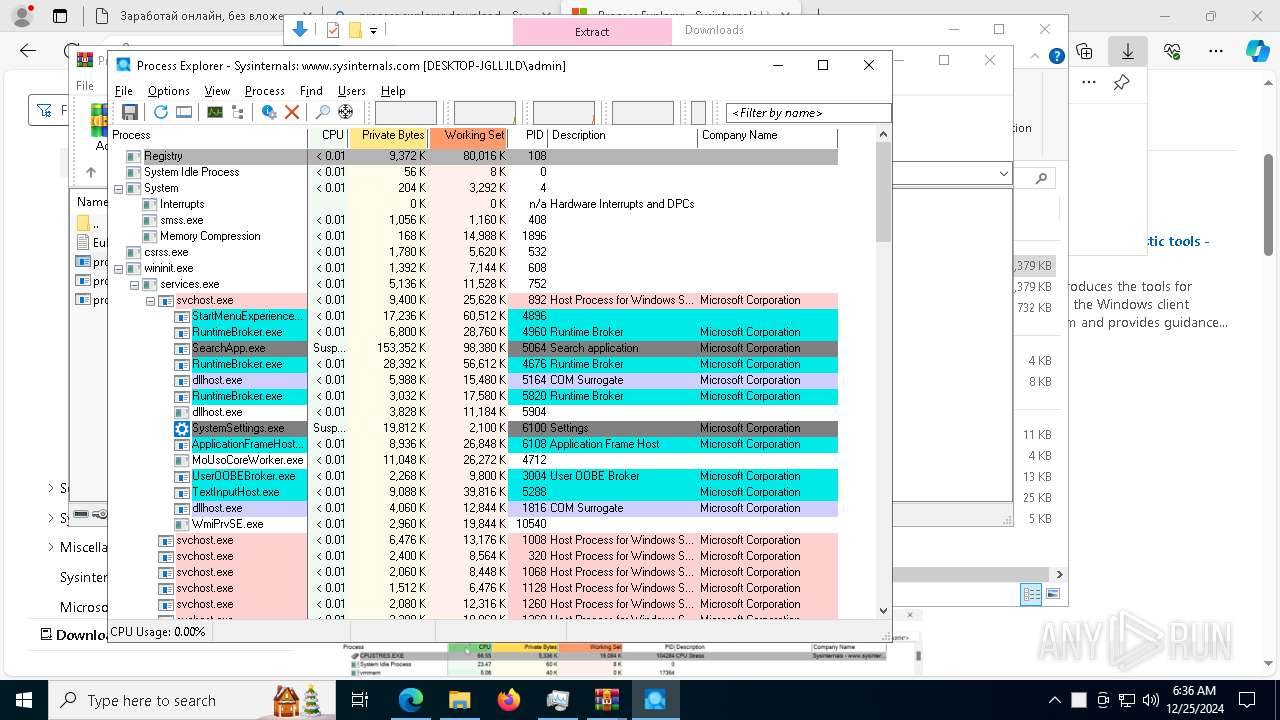
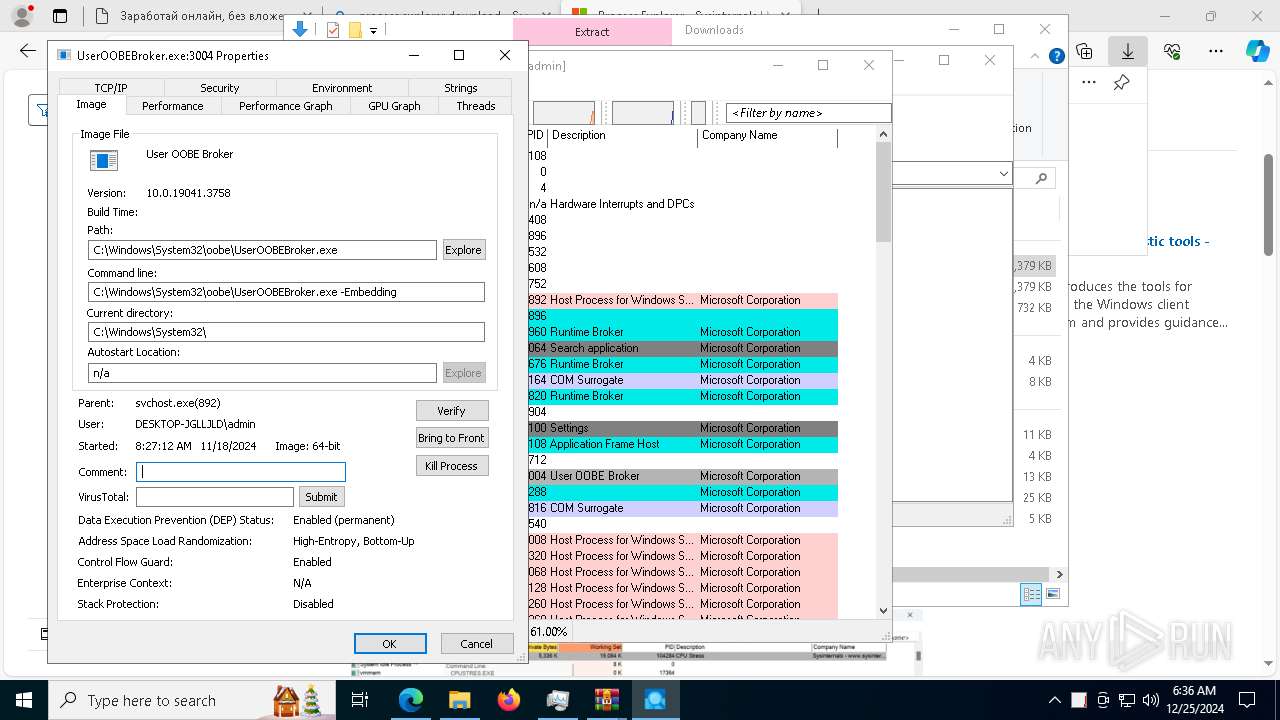
| URL: | https://highstone.link/i/win/Launcher-HighStone-0.1.1.exe |
| Full analysis: | https://app.any.run/tasks/10624020-be43-4248-9e3b-e1435e01167d |
| Verdict: | Malicious activity |
| Threats: | Stealers are a group of malicious software that are intended for gaining unauthorized access to users’ information and transferring it to the attacker. The stealer malware category includes various types of programs that focus on their particular kind of data, including files, passwords, and cryptocurrency. Stealers are capable of spying on their targets by recording their keystrokes and taking screenshots. This type of malware is primarily distributed as part of phishing campaigns. |
| Analysis date: | December 25, 2024, 06:32:15 |
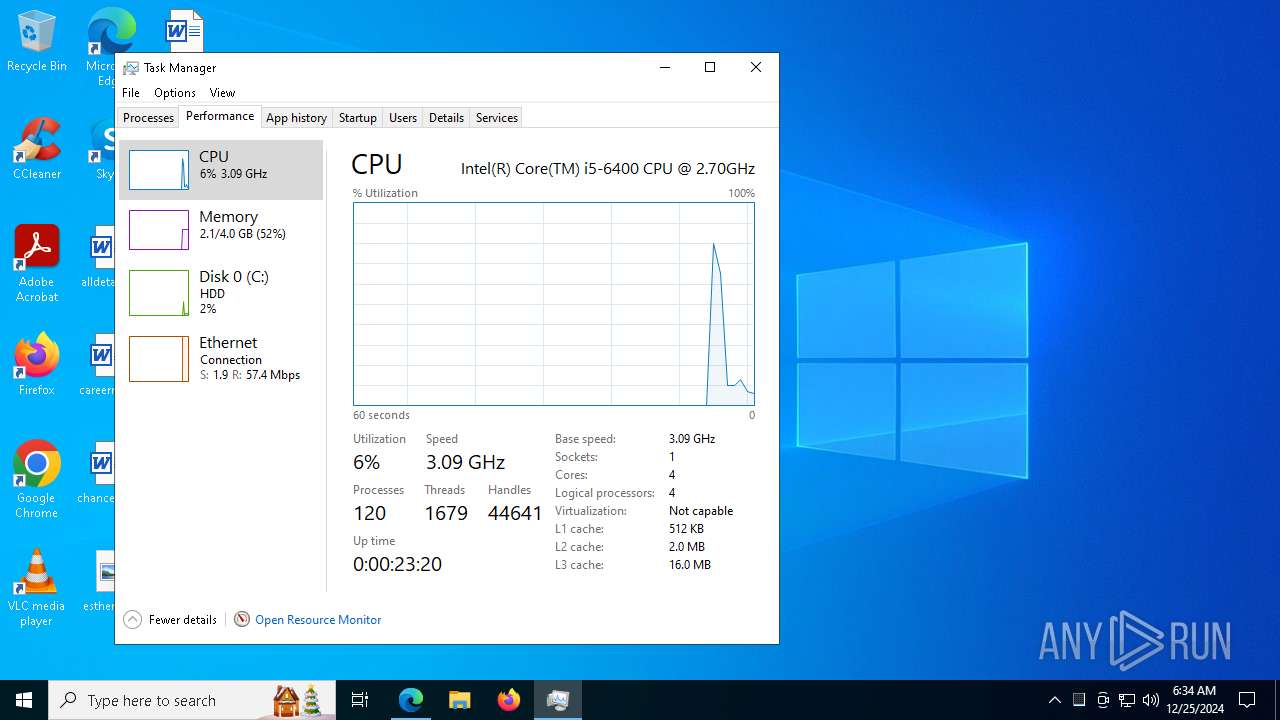
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 114826E7AA062A425D06F1640293133A |
| SHA1: | C55EF71B4B5F337A145889B48BD97C68D2DE6F52 |
| SHA256: | B2A5856A72020166F76C4B0777E5F1754A44092EE3554DB743487E72800FEF71 |
| SSDEEP: | 3:N8wONLAuLOK2ayRKHJn:2wYAuLl2j6n |
MALICIOUS
Changes the autorun value in the registry
- Launcher-HighStone-0.1.1.exe (PID: 7836)
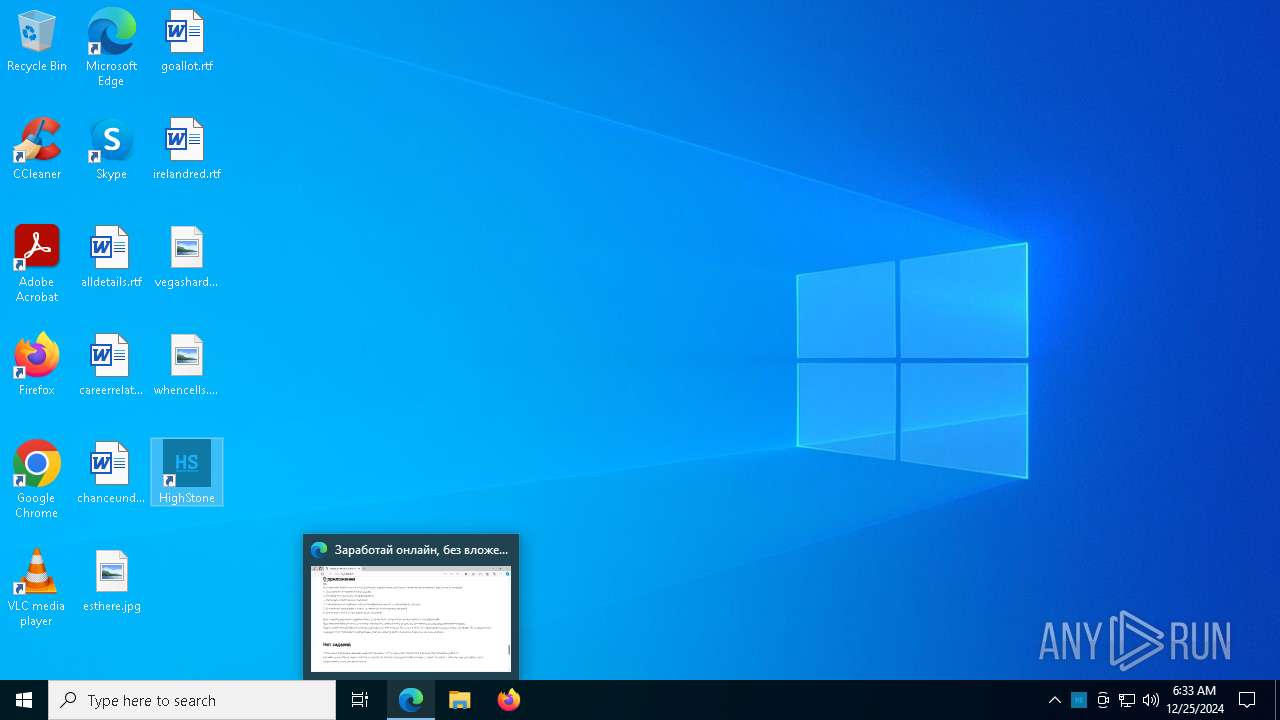
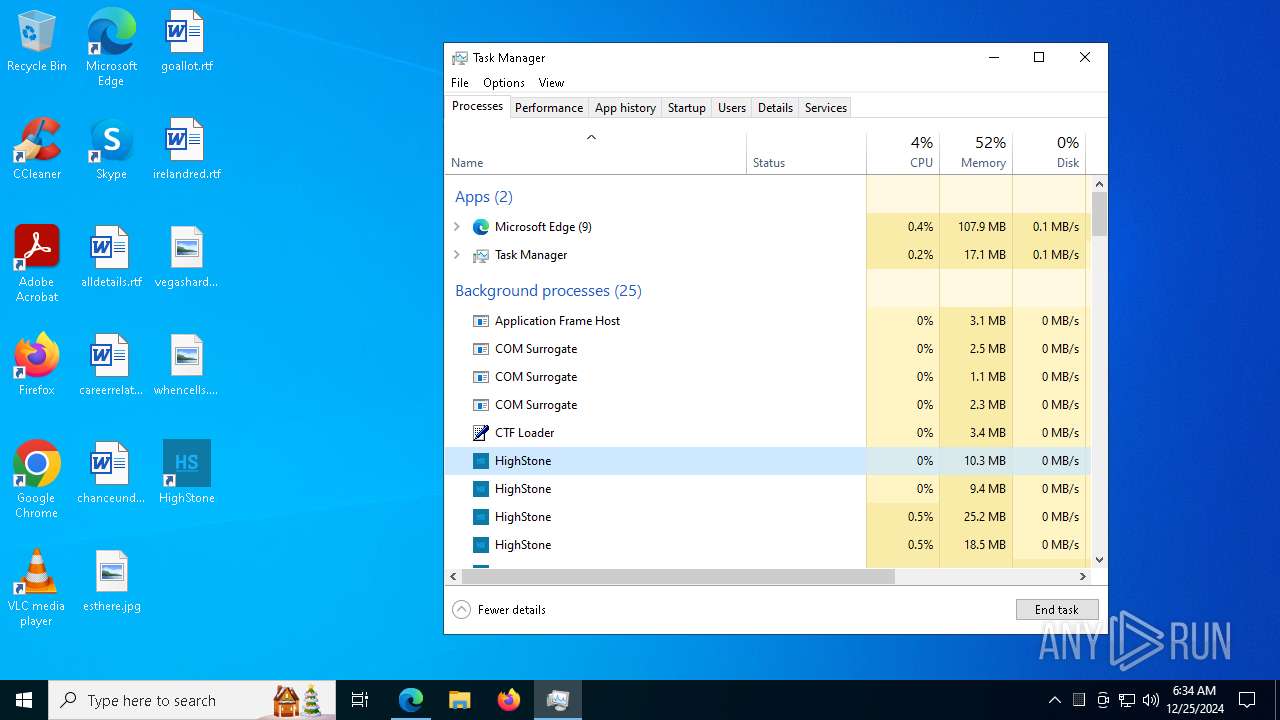
Actions looks like stealing of personal data
- HighStone.exe (PID: 3508)
Changes powershell execution policy (Unrestricted)
- HighStone.exe (PID: 3508)
SUSPICIOUS
Executable content was dropped or overwritten
- Launcher-HighStone-0.1.1.exe (PID: 7836)
- procexp.exe (PID: 10256)
- procexp64.exe (PID: 8484)
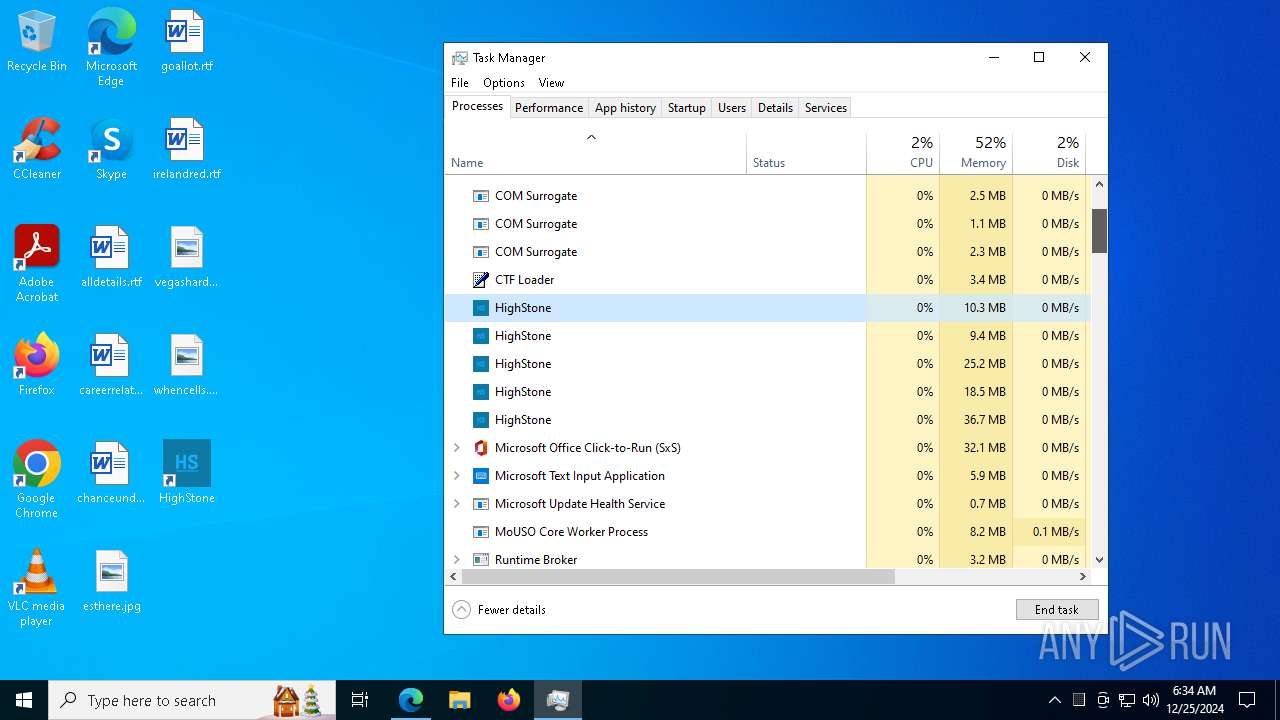
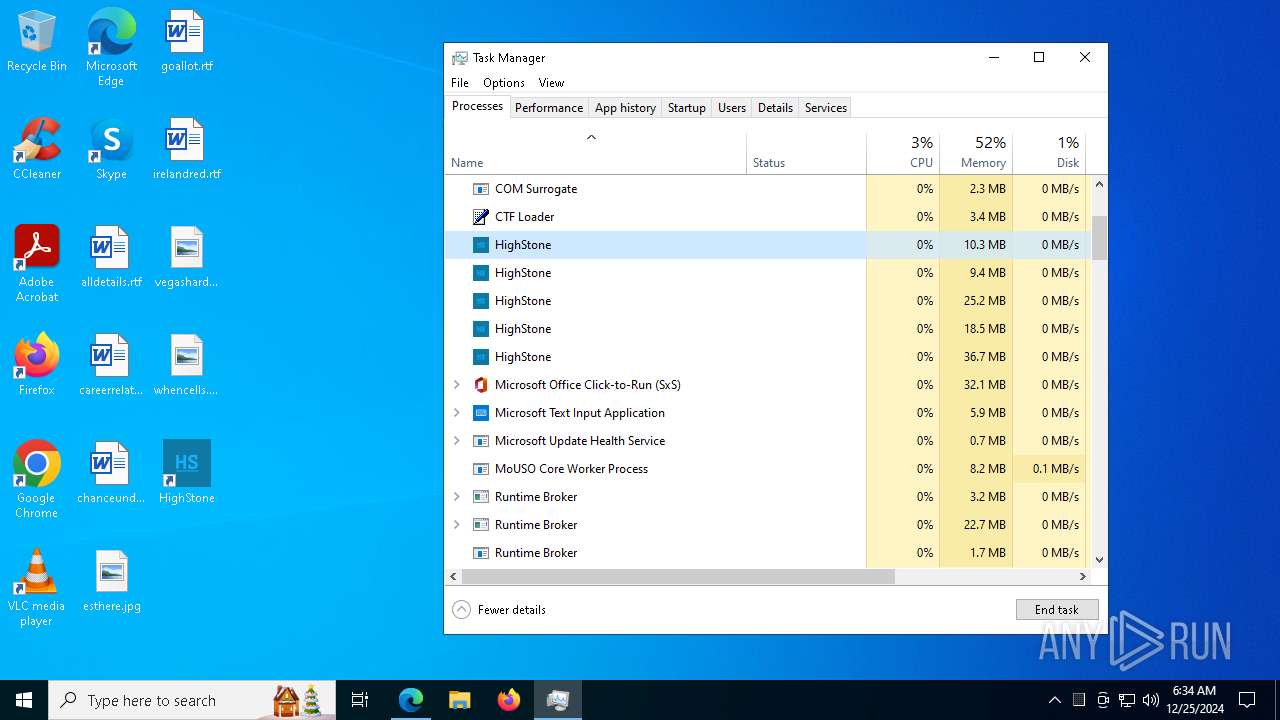
Get information on the list of running processes
- Launcher-HighStone-0.1.1.exe (PID: 7836)
- cmd.exe (PID: 7832)
Starts CMD.EXE for commands execution
- Launcher-HighStone-0.1.1.exe (PID: 7836)
- HighStone.exe (PID: 3508)
- NETSTAT.EXE (PID: 5240)
- HighStone.exe (PID: 8548)
- HighStone.exe (PID: 8096)
Malware-specific behavior (creating "System.dll" in Temp)
- Launcher-HighStone-0.1.1.exe (PID: 7836)
Reads security settings of Internet Explorer
- Launcher-HighStone-0.1.1.exe (PID: 7836)
- procexp64.exe (PID: 8484)
Checks Windows Trust Settings
- Launcher-HighStone-0.1.1.exe (PID: 7836)
- procexp64.exe (PID: 8484)
Drops 7-zip archiver for unpacking
- Launcher-HighStone-0.1.1.exe (PID: 7836)
Process drops legitimate windows executable
- Launcher-HighStone-0.1.1.exe (PID: 7836)
The process creates files with name similar to system file names
- Launcher-HighStone-0.1.1.exe (PID: 7836)
Creates a software uninstall entry
- Launcher-HighStone-0.1.1.exe (PID: 7836)
Starts application with an unusual extension
- cmd.exe (PID: 3988)
- cmd.exe (PID: 8508)
- cmd.exe (PID: 9224)
Application launched itself
- HighStone.exe (PID: 3508)
- HighStone.exe (PID: 8096)
- HighStone.exe (PID: 8548)
Uses ROUTE.EXE to obtain the routing table information
- cmd.exe (PID: 7404)
The process hides Powershell's copyright startup banner
- HighStone.exe (PID: 3508)
Executing commands from ".cmd" file
- HighStone.exe (PID: 3508)
Checks for Java to be installed
- java.exe (PID: 4128)
Starts POWERSHELL.EXE for commands execution
- HighStone.exe (PID: 3508)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 11104)
Uses NETSH.EXE to obtain data on the network
- cmd.exe (PID: 8804)
Process uses IPCONFIG to discover network configuration
- cmd.exe (PID: 10460)
The process checks if it is being run in the virtual environment
- procexp.exe (PID: 10256)
- procexp64.exe (PID: 8484)
Drops a system driver (possible attempt to evade defenses)
- procexp64.exe (PID: 8484)
Detected use of alternative data streams (AltDS)
- procexp64.exe (PID: 8484)
INFO
Reads the computer name
- identity_helper.exe (PID: 7032)
- Launcher-HighStone-0.1.1.exe (PID: 7836)
- HighStone.exe (PID: 3508)
- HighStone.exe (PID: 4952)
- HighStone.exe (PID: 1904)
- HighStone.exe (PID: 8096)
- HighStone.exe (PID: 8548)
- HighStone.exe (PID: 10468)
- HighStone.exe (PID: 10512)
- procexp.exe (PID: 10256)
Checks supported languages
- Launcher-HighStone-0.1.1.exe (PID: 7836)
- identity_helper.exe (PID: 7032)
- chcp.com (PID: 8)
- HighStone.exe (PID: 7444)
- HighStone.exe (PID: 3508)
- HighStone.exe (PID: 4952)
- HighStone.exe (PID: 8548)
- HighStone.exe (PID: 6812)
- java.exe (PID: 4128)
- HighStone.exe (PID: 1904)
- HighStone.exe (PID: 8096)
- chcp.com (PID: 9820)
- chcp.com (PID: 5544)
- HighStone.exe (PID: 8116)
- HighStone.exe (PID: 4980)
- HighStone.exe (PID: 7876)
- HighStone.exe (PID: 10468)
- HighStone.exe (PID: 10512)
- procexp.exe (PID: 10256)
Create files in a temporary directory
- Launcher-HighStone-0.1.1.exe (PID: 7836)
- HighStone.exe (PID: 3508)
- java.exe (PID: 4128)
- procexp.exe (PID: 10256)
- procexp64.exe (PID: 8484)
The sample compiled with english language support
- Launcher-HighStone-0.1.1.exe (PID: 7836)
- msedge.exe (PID: 9276)
- msedge.exe (PID: 6260)
- WinRAR.exe (PID: 9584)
- procexp.exe (PID: 10256)
- procexp64.exe (PID: 8484)
- msedge.exe (PID: 3736)
The sample compiled with russian language support
- msedge.exe (PID: 6260)
- msedge.exe (PID: 3736)
- Launcher-HighStone-0.1.1.exe (PID: 7836)
Reads Environment values
- identity_helper.exe (PID: 7032)
- HighStone.exe (PID: 3508)
- HighStone.exe (PID: 8548)
- HighStone.exe (PID: 6812)
- HighStone.exe (PID: 8096)
Executable content was dropped or overwritten
- msedge.exe (PID: 6260)
- msedge.exe (PID: 3736)
- msedge.exe (PID: 9276)
- WinRAR.exe (PID: 9584)
The process uses the downloaded file
- msedge.exe (PID: 7592)
- msedge.exe (PID: 3736)
- powershell.exe (PID: 7556)
- powershell.exe (PID: 7344)
- powershell.exe (PID: 7212)
- powershell.exe (PID: 3732)
- powershell.exe (PID: 9300)
- powershell.exe (PID: 7100)
- powershell.exe (PID: 7200)
- powershell.exe (PID: 6948)
- powershell.exe (PID: 7796)
- powershell.exe (PID: 5920)
- powershell.exe (PID: 4684)
- powershell.exe (PID: 4160)
- powershell.exe (PID: 1868)
- powershell.exe (PID: 4876)
- powershell.exe (PID: 9268)
- powershell.exe (PID: 7244)
- powershell.exe (PID: 6888)
- powershell.exe (PID: 1400)
- powershell.exe (PID: 7904)
- powershell.exe (PID: 4640)
- powershell.exe (PID: 7308)
- powershell.exe (PID: 3076)
- powershell.exe (PID: 2008)
- powershell.exe (PID: 9280)
- powershell.exe (PID: 1512)
- powershell.exe (PID: 10876)
- WinRAR.exe (PID: 9584)
- msedge.exe (PID: 7896)
- powershell.exe (PID: 7996)
Creates files or folders in the user directory
- Launcher-HighStone-0.1.1.exe (PID: 7836)
- HighStone.exe (PID: 7444)
- HighStone.exe (PID: 3508)
- HighStone.exe (PID: 1904)
- HighStone.exe (PID: 10512)
- procexp64.exe (PID: 8484)
Reads the machine GUID from the registry
- Launcher-HighStone-0.1.1.exe (PID: 7836)
- HighStone.exe (PID: 10512)
- procexp64.exe (PID: 8484)
Checks proxy server information
- Launcher-HighStone-0.1.1.exe (PID: 7836)
- HighStone.exe (PID: 3508)
- procexp64.exe (PID: 8484)
Reads the software policy settings
- Launcher-HighStone-0.1.1.exe (PID: 7836)
- procexp64.exe (PID: 8484)
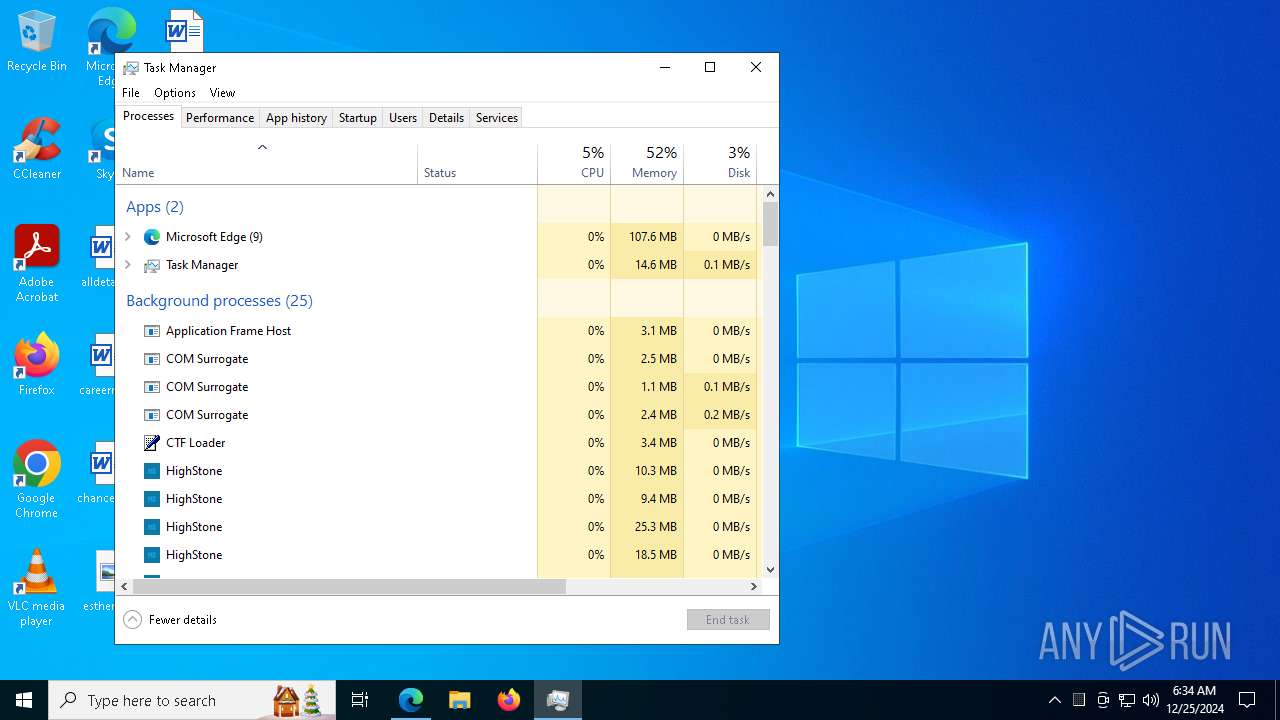
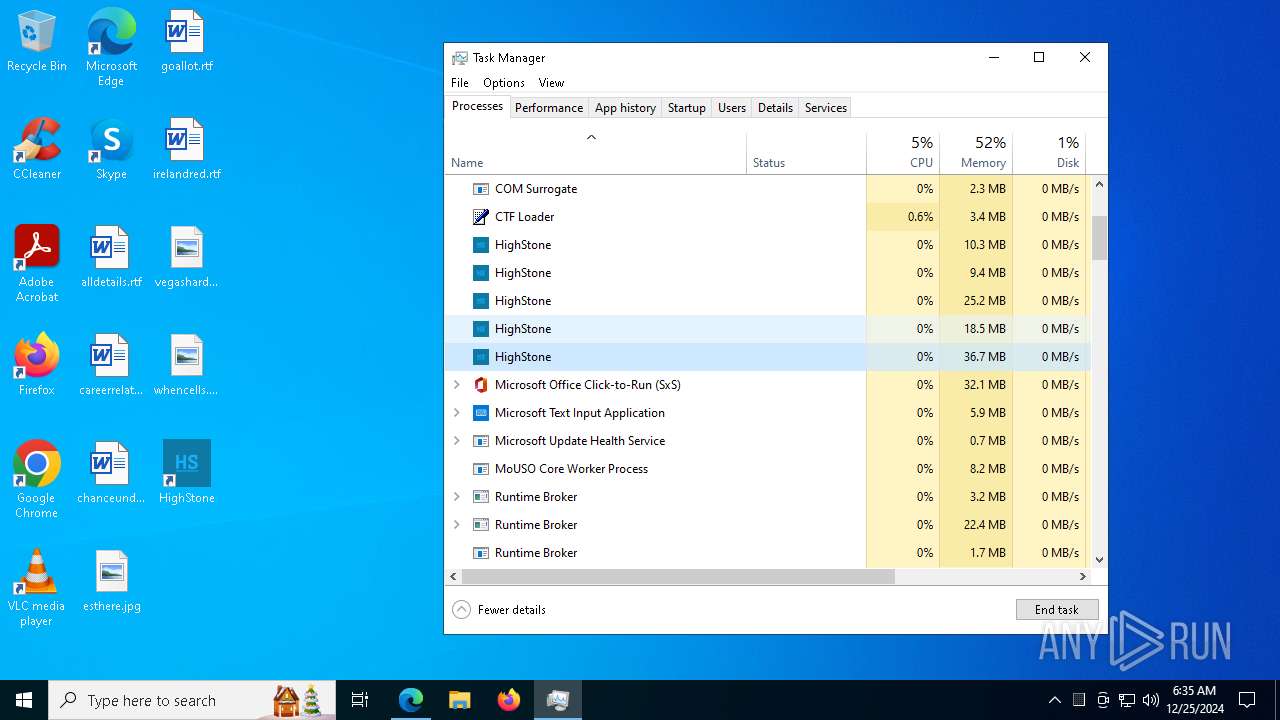
Manual execution by a user
- HighStone.exe (PID: 3508)
- HighStone.exe (PID: 8548)
- HighStone.exe (PID: 8096)
- Taskmgr.exe (PID: 9672)
- Taskmgr.exe (PID: 8732)
- WinRAR.exe (PID: 9584)
Reads product name
- HighStone.exe (PID: 3508)
- HighStone.exe (PID: 6812)
- HighStone.exe (PID: 8548)
- HighStone.exe (PID: 8096)
Changes the display of characters in the console
- cmd.exe (PID: 3988)
- cmd.exe (PID: 8508)
- cmd.exe (PID: 9224)
Process checks computer location settings
- HighStone.exe (PID: 3508)
- HighStone.exe (PID: 6812)
Prints a route via ROUTE.EXE
- ROUTE.EXE (PID: 6916)
Reads CPU info
- HighStone.exe (PID: 3508)
Application launched itself
- msedge.exe (PID: 3736)
Creates files in the program directory
- java.exe (PID: 4128)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 6948)
- powershell.exe (PID: 3732)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 8732)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 7100)
Reads Microsoft Office registry keys
- procexp64.exe (PID: 8484)
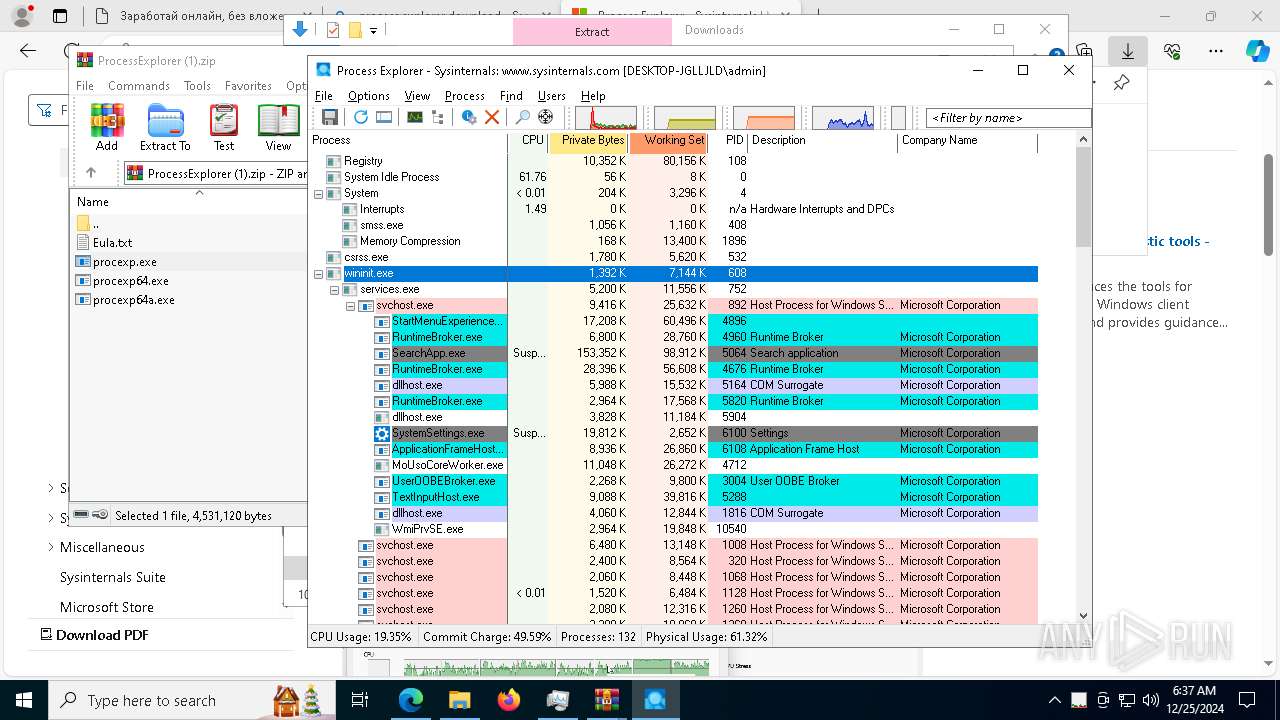
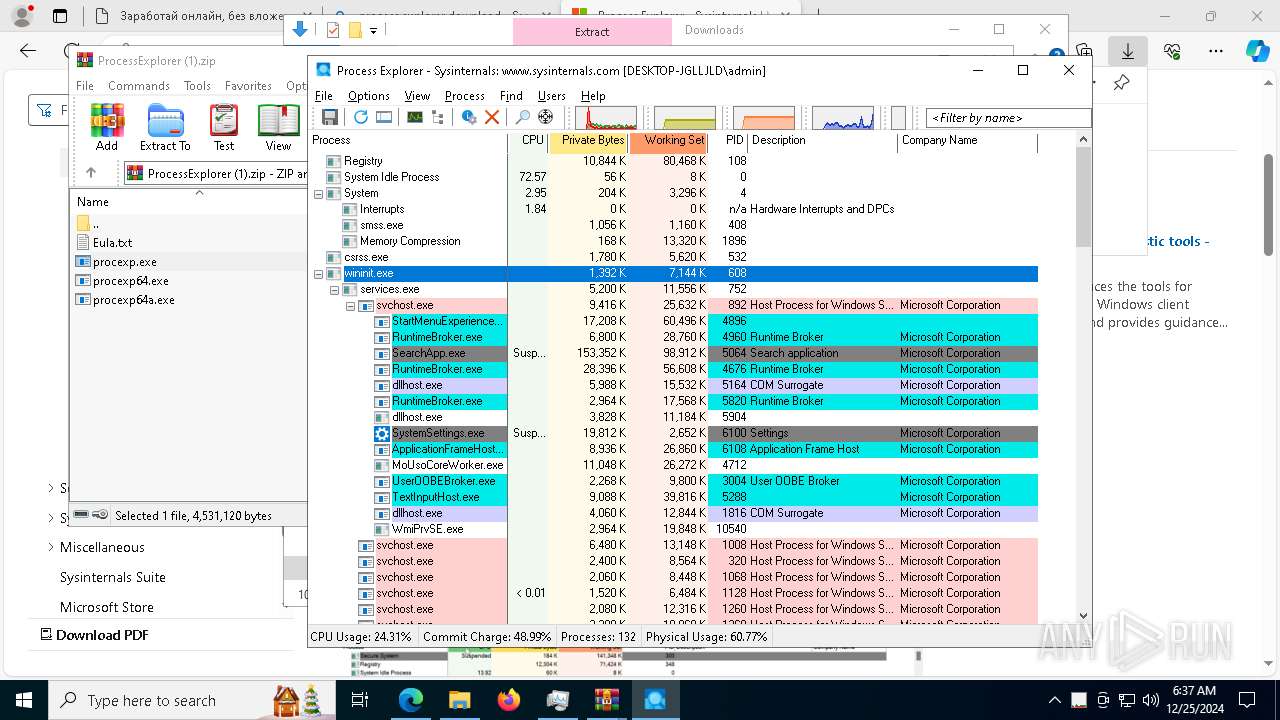
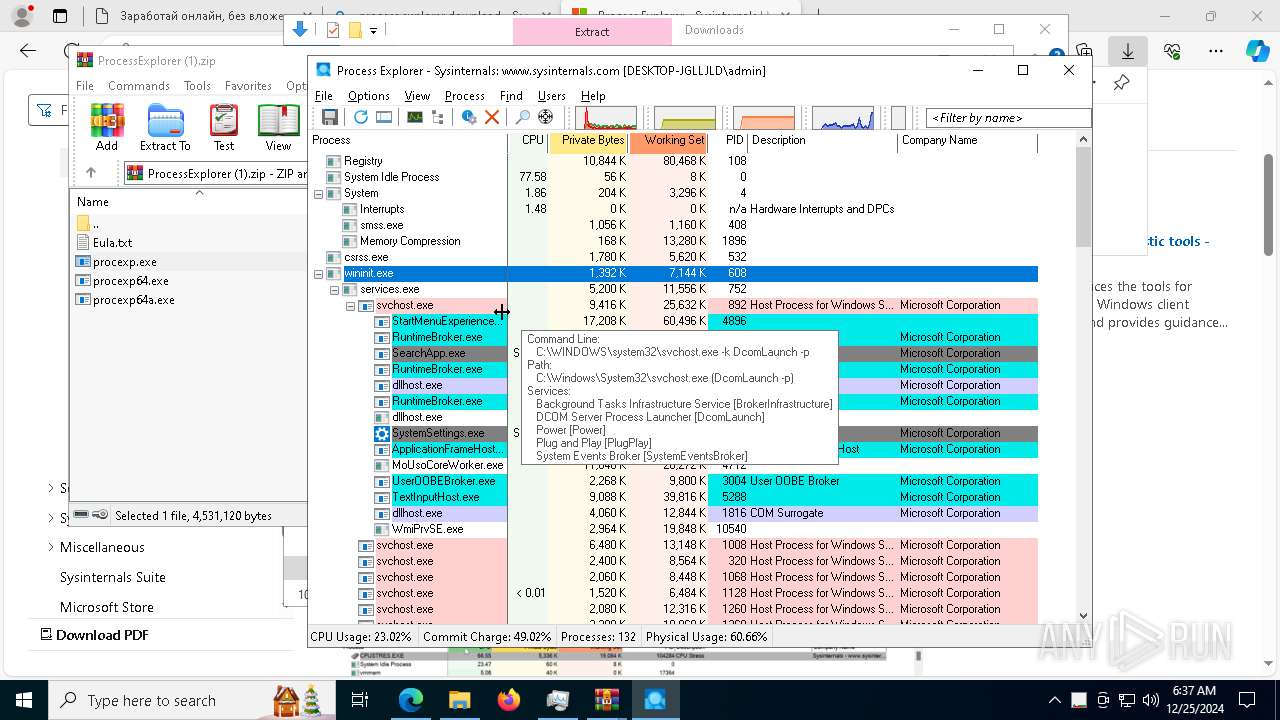
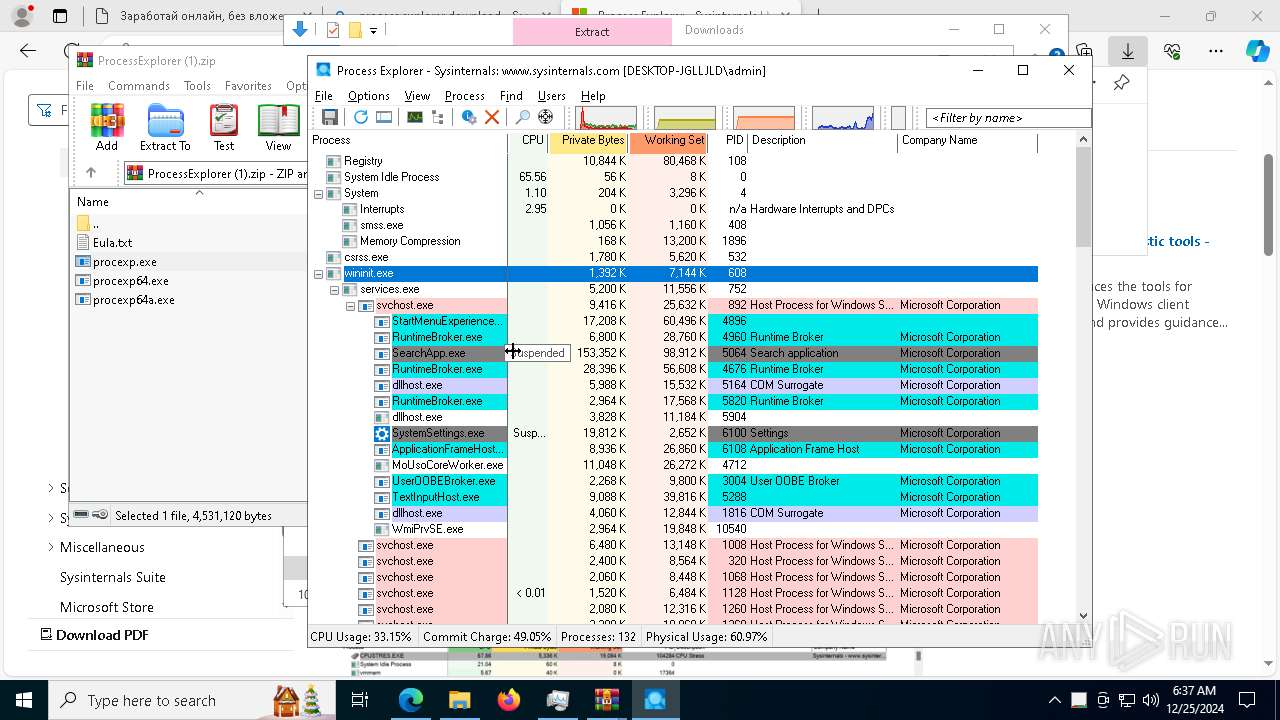
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
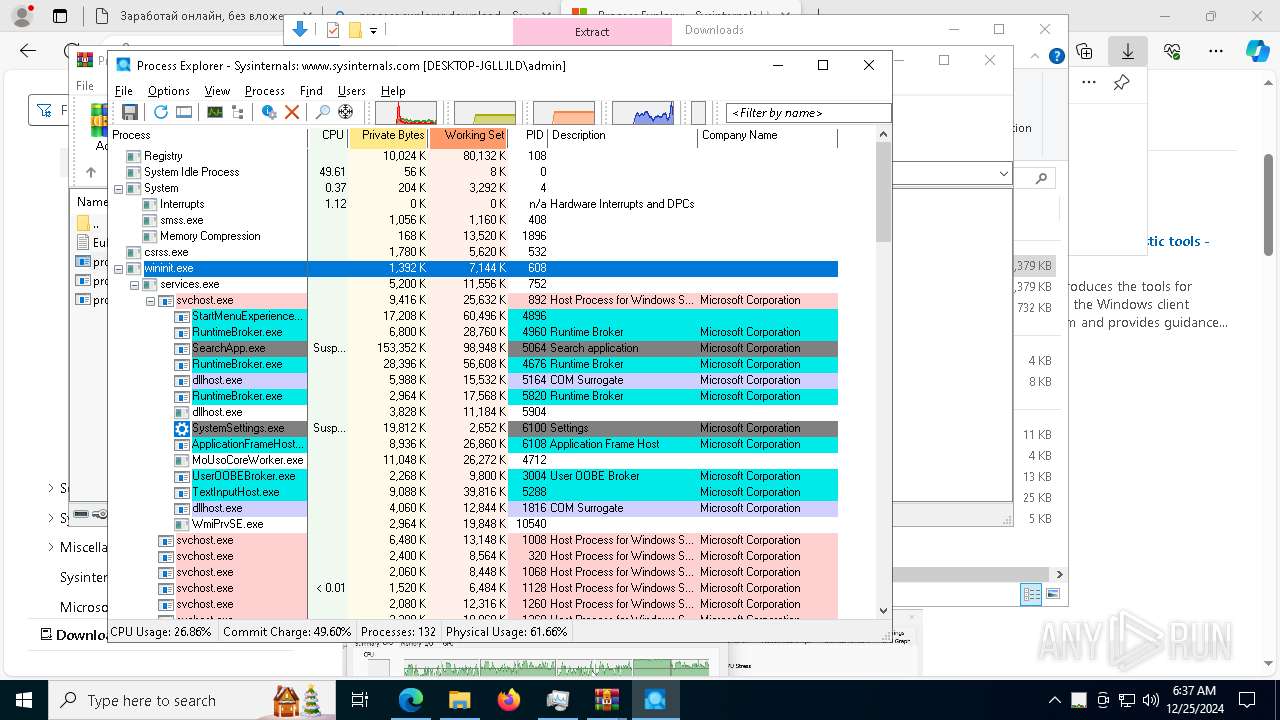
Total processes
416
Monitored processes
273
Malicious processes
7
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 8 | chcp | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Change CodePage Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 8 | C:\WINDOWS\system32\cmd.exe /d /s /c "WHERE smartctl 2>nul" | C:\Windows\System32\cmd.exe | — | HighStone.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 244 | C:\WINDOWS\system32\cmd.exe /d /s /c "gcc -dumpversion" | C:\Windows\System32\cmd.exe | — | HighStone.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 776 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 776 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --instant-process --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=47 --mojo-platform-channel-handle=5464 --field-trial-handle=2328,i,11866011289075779610,17409814308206462391,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1076 | C:\WINDOWS\system32\cmd.exe /d /s /c "reg query "HKEY_LOCAL_MACHINE\HARDWARE\DESCRIPTION\System\CentralProcessor\0" /v FeatureSet" | C:\Windows\System32\cmd.exe | — | HighStone.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1080 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1200 | C:\WINDOWS\system32\cmd.exe /d /s /c "java -version 2>&1" | C:\Windows\System32\cmd.exe | — | HighStone.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1216 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1328 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
209 858
Read events
209 752
Write events
87
Delete events
19
Modification events
| (PID) Process: | (3736) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3736) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3736) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3736) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (3736) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 8350AEACA8882F00 | |||
| (PID) Process: | (3736) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: E477B5ACA8882F00 | |||
| (PID) Process: | (3736) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\459544 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {B28728D2-EBF4-45C6-8740-A954912AF178} | |||
| (PID) Process: | (3736) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 8C4AC9ACA8882F00 | |||
| (PID) Process: | (3736) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | MicrosoftEdgeAutoLaunch_29EBC4579851B72EE312C449CF839B1A |
Value: "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --no-startup-window --win-session-start | |||
| (PID) Process: | (3736) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate\Clients\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\Commands\on-logon-autolaunch |
| Operation: | write | Name: | Enabled |
Value: 0 | |||
Executable files
72
Suspicious files
1 448
Text files
299
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3736 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF1351fb.TMP | — | |
MD5:— | SHA256:— | |||
| 3736 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF1351fb.TMP | — | |
MD5:— | SHA256:— | |||
| 3736 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3736 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3736 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF13520b.TMP | — | |
MD5:— | SHA256:— | |||
| 3736 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF13520b.TMP | — | |
MD5:— | SHA256:— | |||
| 3736 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3736 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3736 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF13522a.TMP | — | |
MD5:— | SHA256:— | |||
| 3736 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
92
TCP/UDP connections
195
DNS requests
209
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
8032 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/0c269ced-c74b-4e70-9b58-6e7999b292c0?P1=1735345431&P2=404&P3=2&P4=dhRaZCJ3C2EulkCnbK2CWQcpnvQllMdGaiLAExsaSmQi68F%2fgnhir4112IJVOPlSr3bISBLRMkXgG%2bsPmoGU1Q%3d%3d | unknown | — | — | whitelisted |
4328 | svchost.exe | GET | 200 | 23.216.77.37:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5640 | SIHClient.exe | GET | 200 | 2.18.69.217:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5640 | SIHClient.exe | GET | 200 | 2.18.69.217:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4328 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
8032 | svchost.exe | HEAD | 200 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/0c269ced-c74b-4e70-9b58-6e7999b292c0?P1=1735345431&P2=404&P3=2&P4=dhRaZCJ3C2EulkCnbK2CWQcpnvQllMdGaiLAExsaSmQi68F%2fgnhir4112IJVOPlSr3bISBLRMkXgG%2bsPmoGU1Q%3d%3d | unknown | — | — | whitelisted |
7836 | Launcher-HighStone-0.1.1.exe | GET | 200 | 142.250.186.163:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
8032 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/0c269ced-c74b-4e70-9b58-6e7999b292c0?P1=1735345431&P2=404&P3=2&P4=dhRaZCJ3C2EulkCnbK2CWQcpnvQllMdGaiLAExsaSmQi68F%2fgnhir4112IJVOPlSr3bISBLRMkXgG%2bsPmoGU1Q%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | unknown |
4328 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
488 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3736 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6260 | msedge.exe | 188.114.97.3:443 | highstone.link | — | — | unknown |
6260 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6260 | msedge.exe | 13.107.21.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6260 | msedge.exe | 13.107.246.45:443 | edge-mobile-static.azureedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
highstone.link |
| unknown |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
business.bing.com |
| whitelisted |
edgeservices.bing.com |
| whitelisted |
update.googleapis.com |
| whitelisted |
bzib.nelreports.net |
| whitelisted |
clients2.googleusercontent.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6260 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
6260 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |