| File name: | install.exe |
| Full analysis: | https://app.any.run/tasks/fd8b1ec4-5aa6-4e7b-b749-2a5791703932 |
| Verdict: | Malicious activity |
| Analysis date: | February 02, 2024, 21:33:46 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 1A18DE8AB57662D8FAD95D737B1213A6 |
| SHA1: | F1D445FE3156DB83CD6AABBD181F34BB332FEFEB |
| SHA256: | B297E6EBBFCE504C34D038DE7B87771B382D868F9D5363EE7EA8058441EC782E |
| SSDEEP: | 49152:+oti3O8Yy0bt3pxHG+atvkmnD/DF+W+lIpFgMG/PcqAFhbGri2MrY3YFTnXKE38Z:RsYyUGLv5D8JlIpFdGoMi3rYoVnXh38a |
MALICIOUS
Drops the executable file immediately after the start
- install.exe (PID: 1392)
SUSPICIOUS
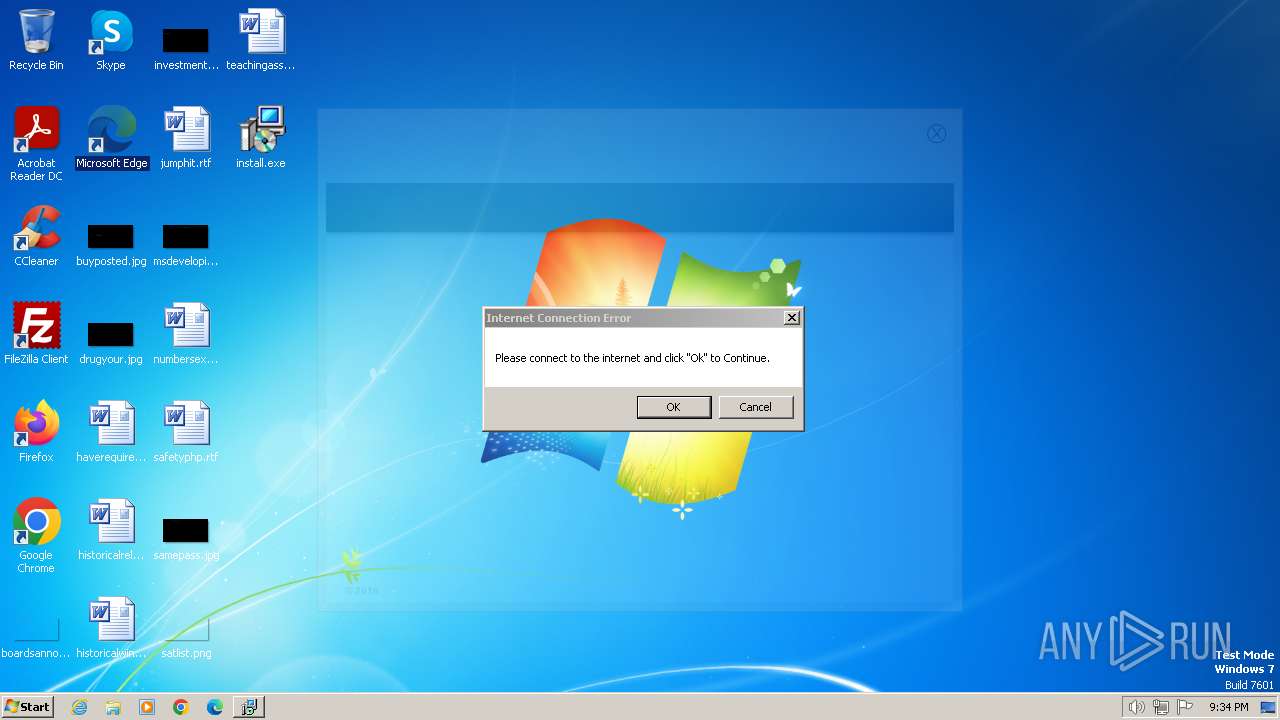
Reads the Internet Settings
- install.exe (PID: 1392)
- install.exe (PID: 2868)
Application launched itself
- install.exe (PID: 1392)
- install.exe (PID: 2868)
Reads the BIOS version
- install.exe (PID: 2868)
Reads Internet Explorer settings
- install.exe (PID: 2868)
Reads Microsoft Outlook installation path
- install.exe (PID: 2868)
INFO
Reads the machine GUID from the registry
- install.exe (PID: 1392)
- install.exe (PID: 2868)
- install.exe (PID: 3572)
Create files in a temporary directory
- install.exe (PID: 1392)
- install.exe (PID: 2868)
Checks supported languages
- install.exe (PID: 1392)
- install.exe (PID: 2868)
- install.exe (PID: 3572)
Process checks whether UAC notifications are on
- install.exe (PID: 1392)
- install.exe (PID: 2868)
Reads the computer name
- install.exe (PID: 1392)
- install.exe (PID: 2868)
Reads product name
- install.exe (PID: 2868)
Checks proxy server information
- install.exe (PID: 2868)
Reads CPU info
- install.exe (PID: 2868)
Reads Environment values
- install.exe (PID: 2868)
Reads Windows Product ID
- install.exe (PID: 2868)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (42.6) |
|---|---|---|
| .exe | | | Win16/32 Executable Delphi generic (19.5) |
| .exe | | | Generic Win/DOS Executable (18.9) |
| .exe | | | DOS Executable Generic (18.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:20 00:22:17+02:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 37888 |
| InitializedDataSize: | 17920 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x9c40 |
| OSVersion: | 1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Internet Application |
| FileDescription: | Installer Setup |
| FileVersion: | 3.2.1.8 |
| LegalCopyright: | Installer |
| ProductName: | Installer |
| ProductVersion: | 1.3.7 |
Total processes
44
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1392 | "C:\Users\admin\Desktop\install.exe" | C:\Users\admin\Desktop\install.exe | — | explorer.exe | |||||||||||
User: admin Company: Internet Application Integrity Level: MEDIUM Description: Installer Setup Exit code: 0 Version: 3.2.1.8 Modules
| |||||||||||||||
| 2868 | "C:\Users\admin\Desktop\install.exe" /RSF /ppn:YyhwYgxaFRAiP211FM5W /mnl | C:\Users\admin\Desktop\install.exe | install.exe | ||||||||||||
User: admin Company: Internet Application Integrity Level: HIGH Description: Installer Setup Exit code: 0 Version: 3.2.1.8 Modules
| |||||||||||||||
| 3572 | "C:\Users\admin\Desktop\install.exe" /_ShowProgress /PrTxt:TG9hZGluZy4uLg== | C:\Users\admin\Desktop\install.exe | — | install.exe | |||||||||||
User: admin Company: Internet Application Integrity Level: HIGH Description: Installer Setup Exit code: 0 Version: 3.2.1.8 Modules
| |||||||||||||||
Total events
1 787
Read events
1 315
Write events
472
Delete events
0
Modification events
| (PID) Process: | (1392) install.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1392) install.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1392) install.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1392) install.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2868) install.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2868) install.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2868) install.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2868) install.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2868) install.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2868) install.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
8
Suspicious files
2
Text files
92
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1392 | install.exe | C:\Users\admin\AppData\Local\Temp\INH145~1\css\mainDlm.css | text | |
MD5:87F5B206895781B2D28A517E97EFCD5E | SHA256:863F3DAF9BF6E87DFC4618FF563620CCDC6716089F223D5385D3856AAA899252 | |||
| 1392 | install.exe | C:\Users\admin\AppData\Local\Temp\INH145~1\css\sdk-ui\checkbox.css | text | |
MD5:64773C6B0E3413C81AEBC46CCE8C9318 | SHA256:B09504C1BF0486D3EC46500592B178A3A6C39284672AF8815C3687CC3D29560D | |||
| 1392 | install.exe | C:\Users\admin\AppData\Local\Temp\INH145~1\css\sdk-ui\progress-bar.css | text | |
MD5:5335F1C12201B5F7CF5F8B4F5692E3D1 | SHA256:974CD89E64BDAA85BF36ED2A50AF266D245D781A8139F5B45D7C55A0B0841DDA | |||
| 1392 | install.exe | C:\Users\admin\AppData\Local\Temp\00163741.log | text | |
MD5:BE40A6BD065D505C5A865A788996D644 | SHA256:C88668058F6AC92DA5B534D81541127D8126CF4F3A029340C0C06394D2E800FC | |||
| 1392 | install.exe | C:\Users\admin\AppData\Local\Temp\INH145~1\css\sdk-ui\images\progress-bg2.png | image | |
MD5:B582D9A67BFE77D523BA825FD0B9DAE3 | SHA256:AB4EEB3EA1EEF4E84CB61ECCB0BA0998B32108D70B3902DF3619F4D9393F74C3 | |||
| 1392 | install.exe | C:\Users\admin\AppData\Local\Temp\INH145~1\csshover3.htc | html | |
MD5:52FA0DA50BF4B27EE625C80D36C67941 | SHA256:E37E99DDFC73AC7BA774E23736B2EF429D9A0CB8C906453C75B14C029BDD5493 | |||
| 1392 | install.exe | C:\Users\admin\AppData\Local\Temp\INH145~1\css\sdk-ui\images\progress-bg-corner.png | image | |
MD5:608F1F20CD6CA9936EAA7E8C14F366BE | SHA256:86B6E6826BCDE2955D64D4600A4E01693522C1FDDF156CE31C4BA45B3653A7BD | |||
| 1392 | install.exe | C:\Users\admin\AppData\Local\Temp\INH145~1\images\Close_Hover.png | image | |
MD5:9D356DD702E8CC89C84682E7DA899AEA | SHA256:1B7D254408069AB82277A147A4AFBFAB871402D03A94CE735959CFBAD7E08DD1 | |||
| 1392 | install.exe | C:\Users\admin\AppData\Local\Temp\INH145~1\images\Color_Button_Hover.png | image | |
MD5:3DA57801E1AA51237D1A7A4C54D1C4D6 | SHA256:0C3C4F7DE98FE09E4D07AFE4BA2C88A38450E84472B3F7E3878057AE54706F66 | |||
| 1392 | install.exe | C:\Users\admin\AppData\Local\Temp\INH145~1\images\BGD.png | image | |
MD5:EF4807F71B1A16027309E0D289A63F24 | SHA256:CD0AA95A19252837C802FC72082470D2466675FBA7B269F70243AA8B5126CB50 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
4
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
rp.medabemidam.com |
| unknown |
info.medabemidam.com |
| unknown |
os.medabemidam.com |
| unknown |
os2.medabemidam.com |
| unknown |