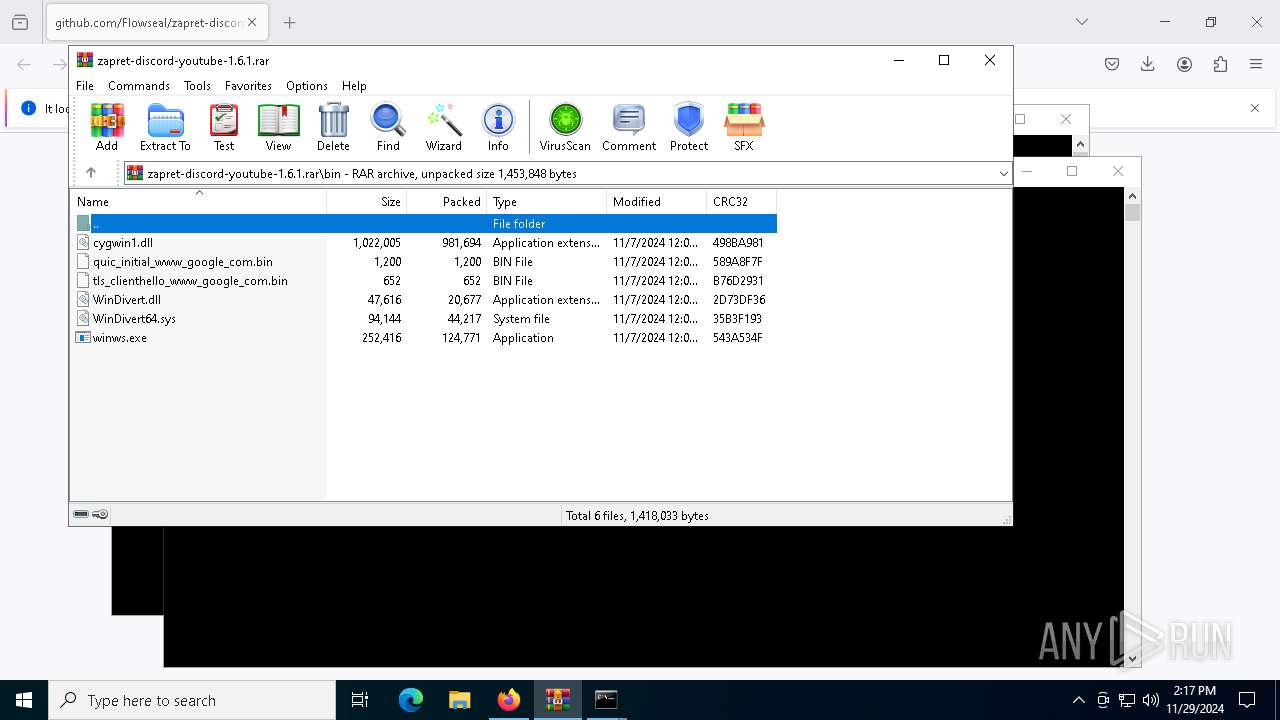
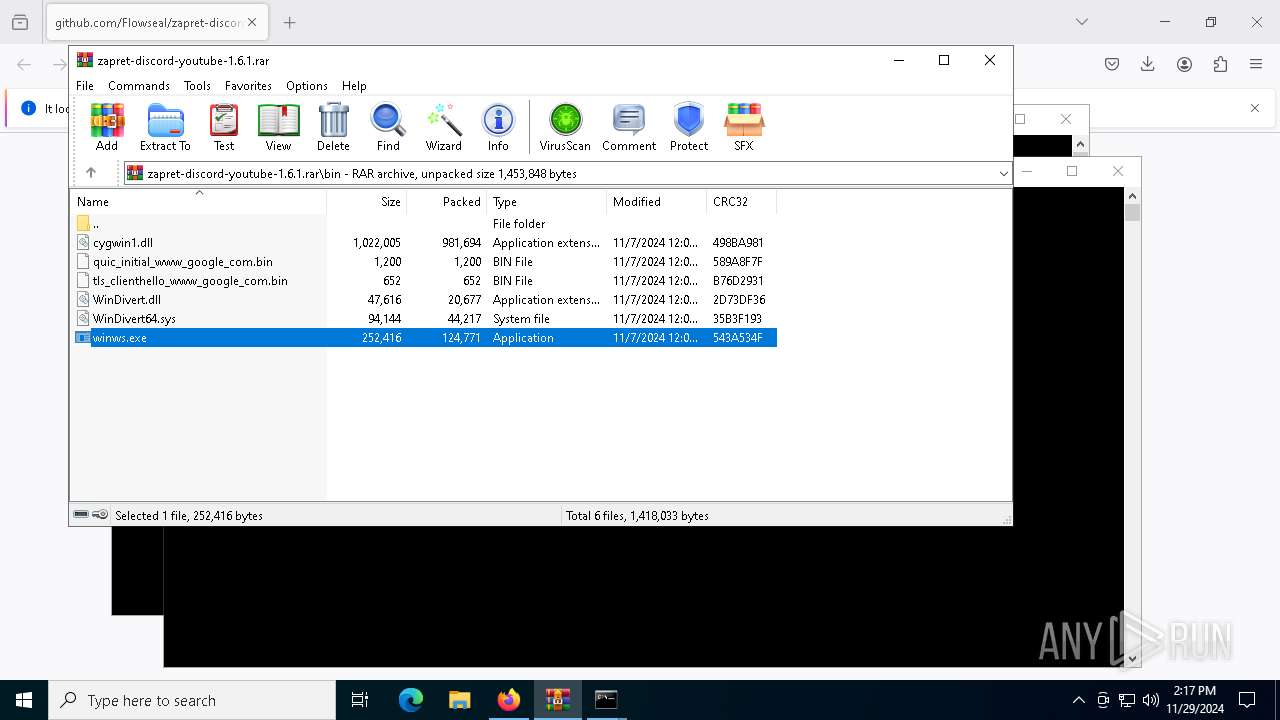
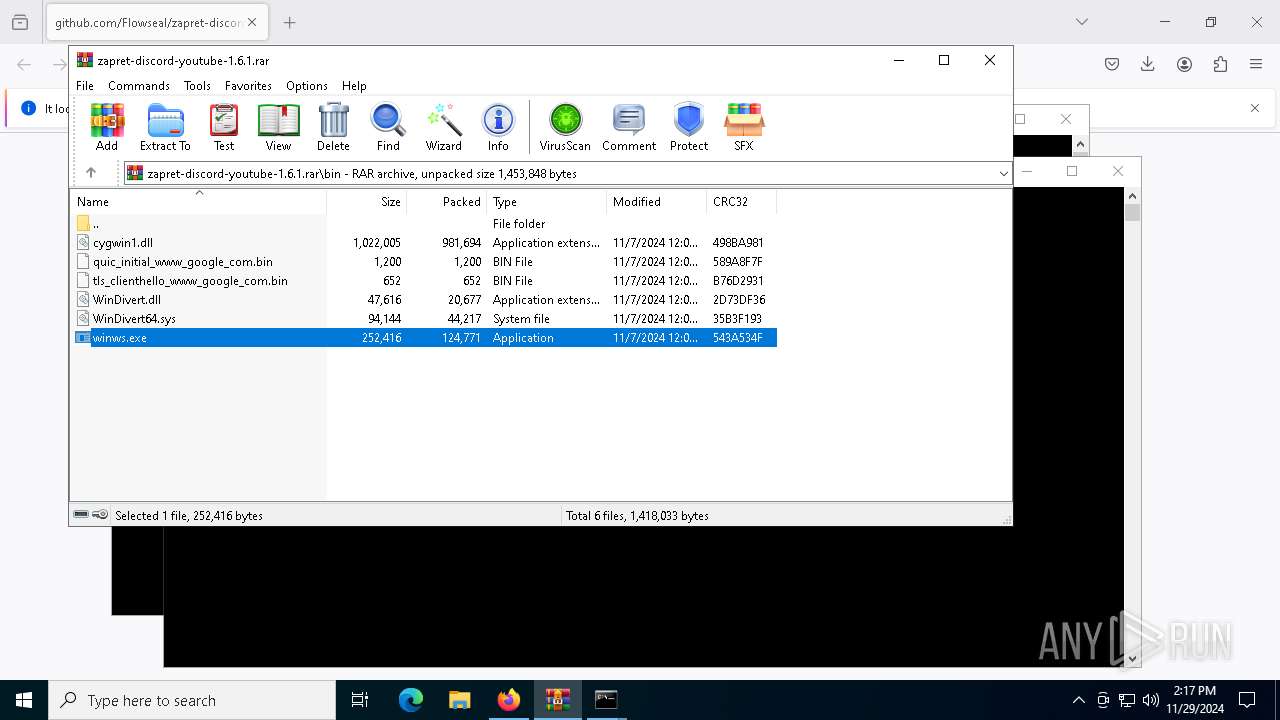
| URL: | https://github.com/Flowseal/zapret-discord-youtube/releases/download/1.6.1/zapret-discord-youtube-1.6.1.rar |
| Full analysis: | https://app.any.run/tasks/bb04aa42-b22a-46a0-9bdb-04d42ddf5f2c |
| Verdict: | Malicious activity |
| Analysis date: | November 29, 2024, 14:15:36 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 043E330932A4F85CAEA4610CE97CEF34 |
| SHA1: | D5A32E7EB68B5171D5E00D327971094A22587B0F |
| SHA256: | B296AA5AF0118CE50FAAD1FD0C91A80C2667457A9F39274C976907905AA30AA5 |
| SSDEEP: | 3:N8tEdFtE2Eyd8WPtkCUPu0d8WNPO:2uBE2BdFl6Pu0dFw |
MALICIOUS
No malicious indicators.SUSPICIOUS
Application launched itself
- cmd.exe (PID: 5740)
Hides command output
- cmd.exe (PID: 6288)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 6288)
- cmd.exe (PID: 5536)
- cmd.exe (PID: 1804)
- cmd.exe (PID: 8120)
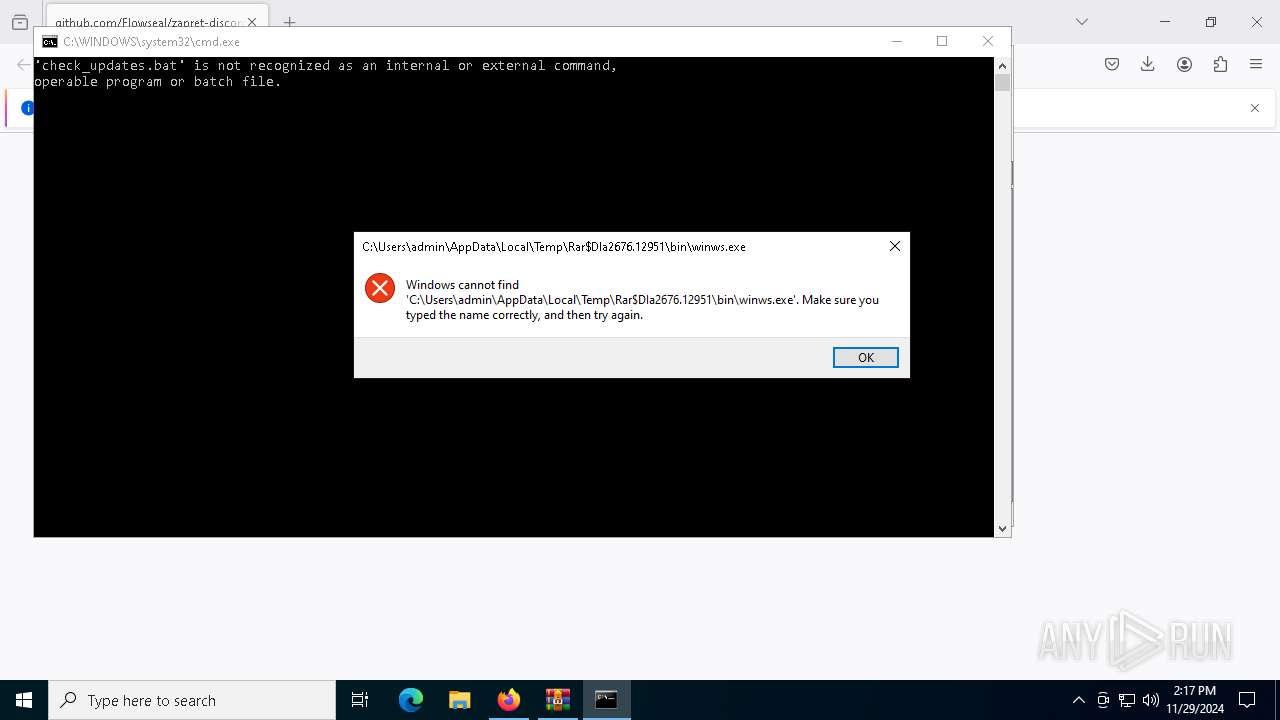
Starts application with an unusual extension
- cmd.exe (PID: 7640)
- cmd.exe (PID: 1804)
- cmd.exe (PID: 848)
- cmd.exe (PID: 7596)
- cmd.exe (PID: 8120)
- cmd.exe (PID: 6964)
- cmd.exe (PID: 5740)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 2224)
- powershell.exe (PID: 5340)
- WinRAR.exe (PID: 2676)
- cmd.exe (PID: 5740)
Starts process via Powershell
- powershell.exe (PID: 2224)
- powershell.exe (PID: 5340)
Executing commands from a ".bat" file
- powershell.exe (PID: 2224)
- powershell.exe (PID: 5340)
- WinRAR.exe (PID: 2676)
Drops a system driver (possible attempt to evade defenses)
- WinRAR.exe (PID: 2676)
INFO
Application launched itself
- firefox.exe (PID: 4308)
- firefox.exe (PID: 5400)
Changes the display of characters in the console
- cmd.exe (PID: 5740)
- cmd.exe (PID: 1804)
- cmd.exe (PID: 7596)
- cmd.exe (PID: 7640)
- cmd.exe (PID: 848)
- cmd.exe (PID: 8120)
- cmd.exe (PID: 6964)
Manual execution by a user
- WinRAR.exe (PID: 2676)
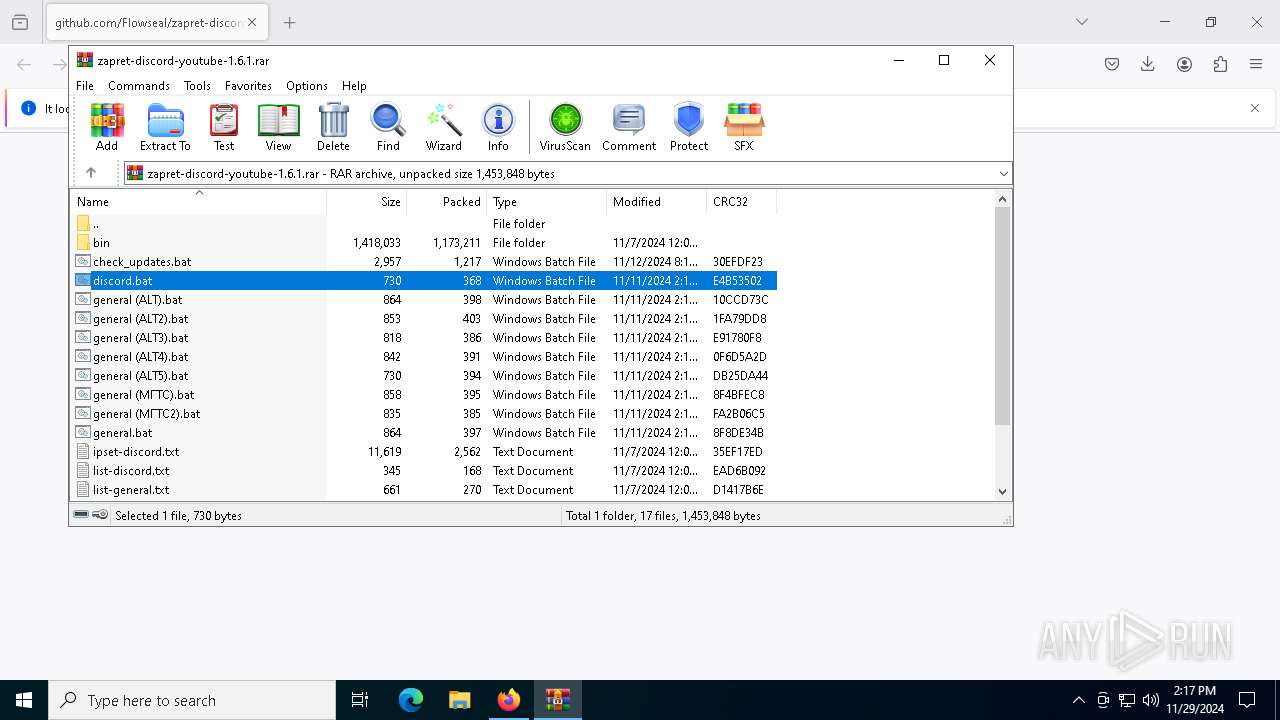
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2676)
- firefox.exe (PID: 5400)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
174
Monitored processes
42
Malicious processes
2
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 432 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 848 | "C:\WINDOWS\system32\cmd.exe" /k ""C:\Users\admin\AppData\Local\Temp\Rar$DIa2676.14830\service_install.bat" admin" | C:\Windows\System32\cmd.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1076 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | winws.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1216 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2676.18559\bin\winws.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2676.18559\bin\winws.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 1380 | powershell -command "(Invoke-WebRequest -Uri https://raw.githubusercontent.com/Flowseal/zapret-discord-youtube/refs/heads/main/.service/version.txt -Headers @{\"Cache-Control\"=\"no-cache\"} -TimeoutSec 5).Content" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1512 | chcp 65001 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Change CodePage Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1804 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$DIa2676.14830\service_install.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2224 | powershell -Command "Start-Process 'cmd.exe' -ArgumentList '/k \"\"C:\Users\admin\AppData\Local\Temp\Rar$DIa2676.14830\service_install.bat\" admin\"' -Verb RunAs" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2676 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\zapret-discord-youtube-1.6.1.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 2940 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
33 404
Read events
33 394
Write events
10
Delete events
0
Modification events
| (PID) Process: | (5400) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (2676) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2676) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2676) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2676) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\zapret-discord-youtube-1.6.1.rar | |||
| (PID) Process: | (2676) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2676) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2676) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2676) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1216) winws.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Cygwin\Installations |
| Operation: | write | Name: | ade7769bf36acebf |
Value: \??\C:\Users\admin\AppData\Local\Temp\Rar$EXa2676.18559 | |||
Executable files
6
Suspicious files
174
Text files
74
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5400 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 5400 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 5400 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs-1.js | text | |
MD5:2C99A16AED3906D92FFE3EF1808E2753 | SHA256:08412578CC3BB4922388F8FF8C23962F616B69A1588DA720ADE429129C73C452 | |||
| 5400 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\1657114595AmcateirvtiSty.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 5400 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\datareporting\glean\db\data.safe.tmp | dbf | |
MD5:F759EB25271E6A6F0A3500520813E5FE | SHA256:015E515D432DD64FDC9502ABE9C723EEF544E7AF11C36BDFE8B38412597CA1EC | |||
| 5400 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 5400 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\2823318777ntouromlalnodry--naod.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 5400 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 5400 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\SiteSecurityServiceState.bin | binary | |
MD5:3C5F35A49A20CCEA37A0BC8590B06435 | SHA256:9AC36F5277858DC99143C3257611515B8D62C24EA1F2FB996C33E1A970D5B7D8 | |||
| 5400 | firefox.exe | C:\Users\admin\Downloads\zapret-discord-youtube-1.p3g4nENb.6.1.rar.part | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
29
TCP/UDP connections
89
DNS requests
122
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.24:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5400 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
5400 | firefox.exe | POST | 200 | 172.64.149.23:80 | http://ocsp.sectigo.com/ | unknown | — | — | whitelisted |
5400 | firefox.exe | POST | 200 | 2.16.168.11:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
5400 | firefox.exe | POST | 200 | 142.250.185.99:80 | http://o.pki.goog/s/wr3/yvU | unknown | — | — | whitelisted |
5400 | firefox.exe | POST | 200 | 142.250.185.99:80 | http://o.pki.goog/wr2 | unknown | — | — | whitelisted |
5400 | firefox.exe | POST | 200 | 2.16.168.11:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
5400 | firefox.exe | POST | 200 | 2.16.168.6:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1356 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5064 | SearchApp.exe | 2.23.209.179:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.164.24:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5400 | firefox.exe | 140.82.121.4:443 | github.com | GITHUB | US | shared |
5400 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
2804 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
github.com |
| shared |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |