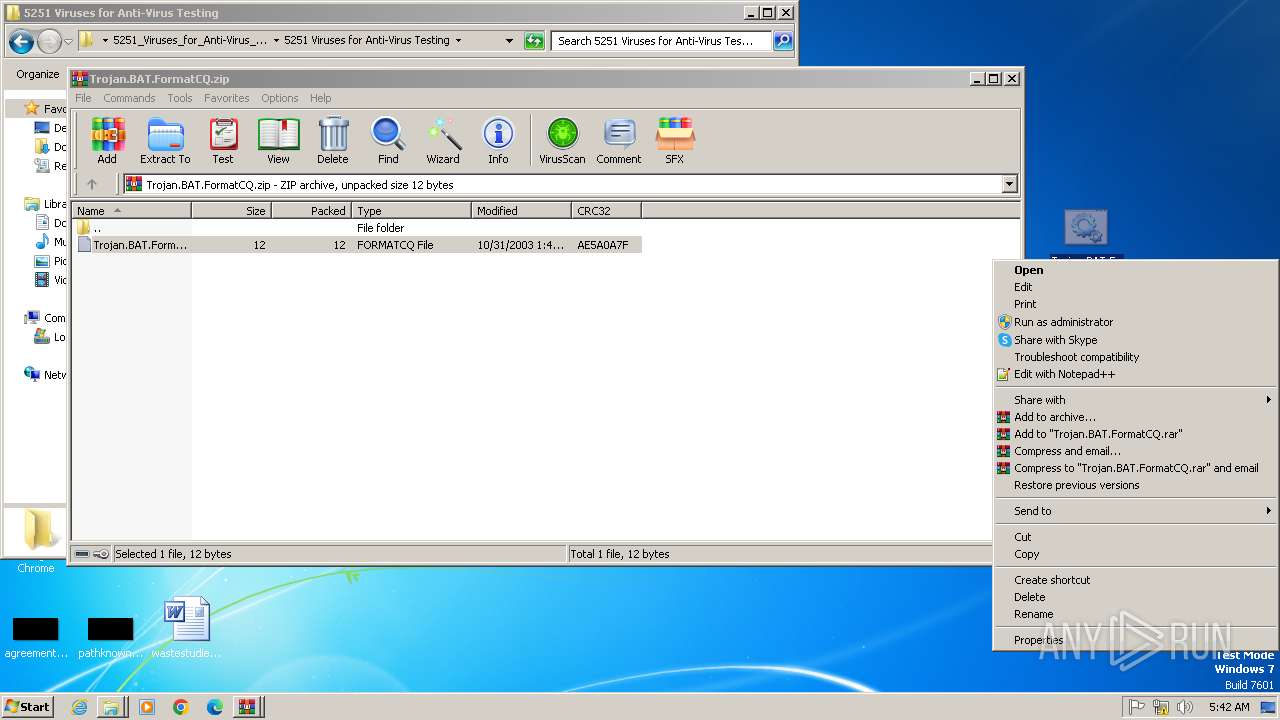
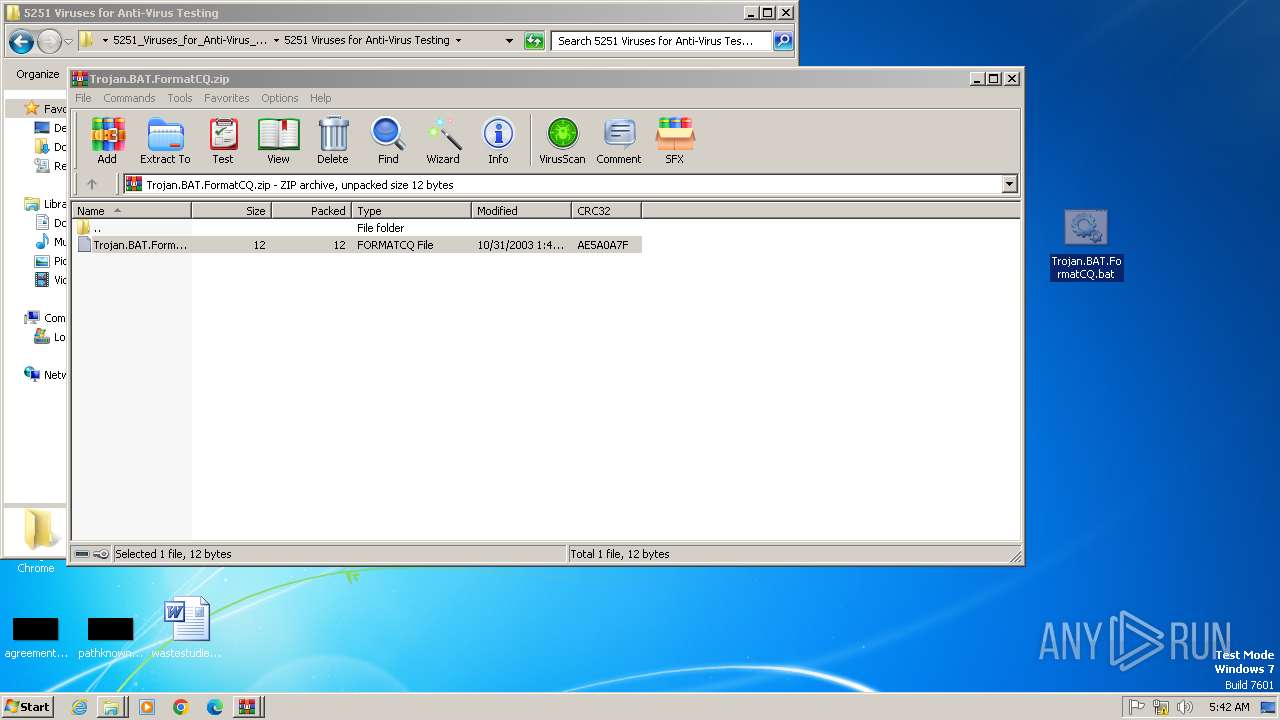
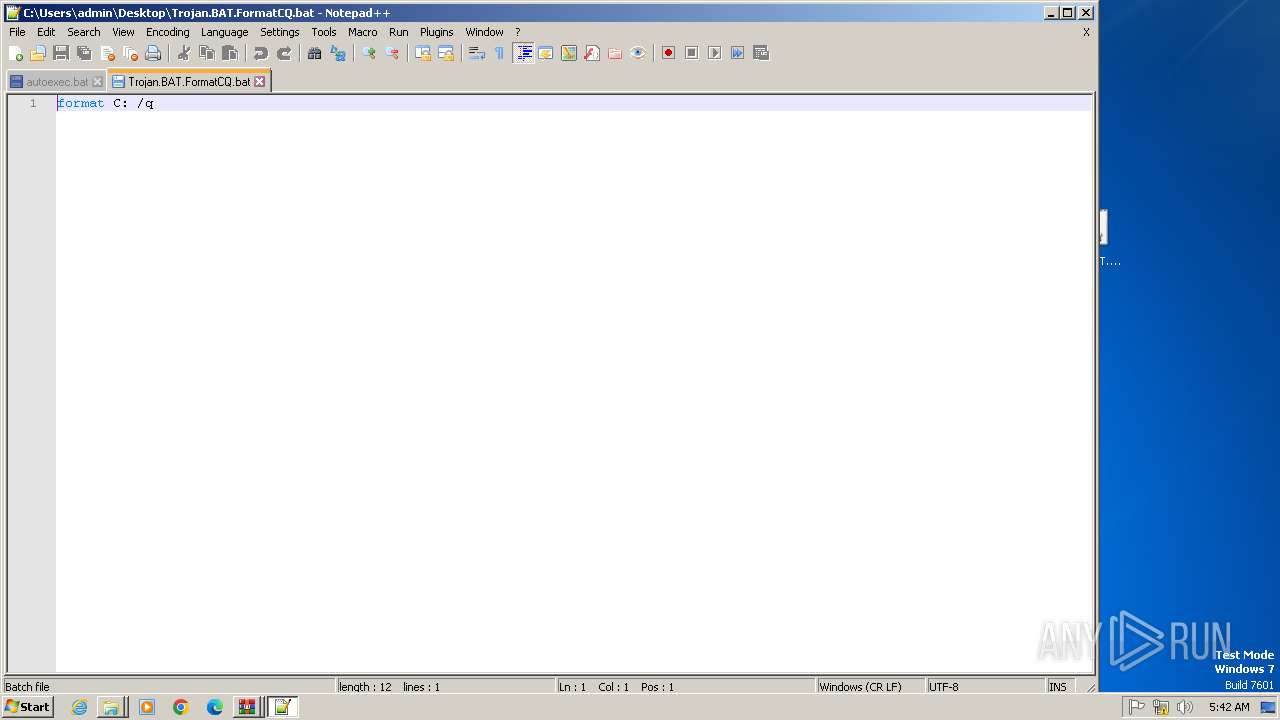
| File name: | Email-Worm.VBS.LoveLetter.vbs |
| Full analysis: | https://app.any.run/tasks/59c0b699-a9f4-406b-8353-e143ce18c9a7 |
| Verdict: | Malicious activity |
| Analysis date: | March 04, 2025, 05:38:26 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
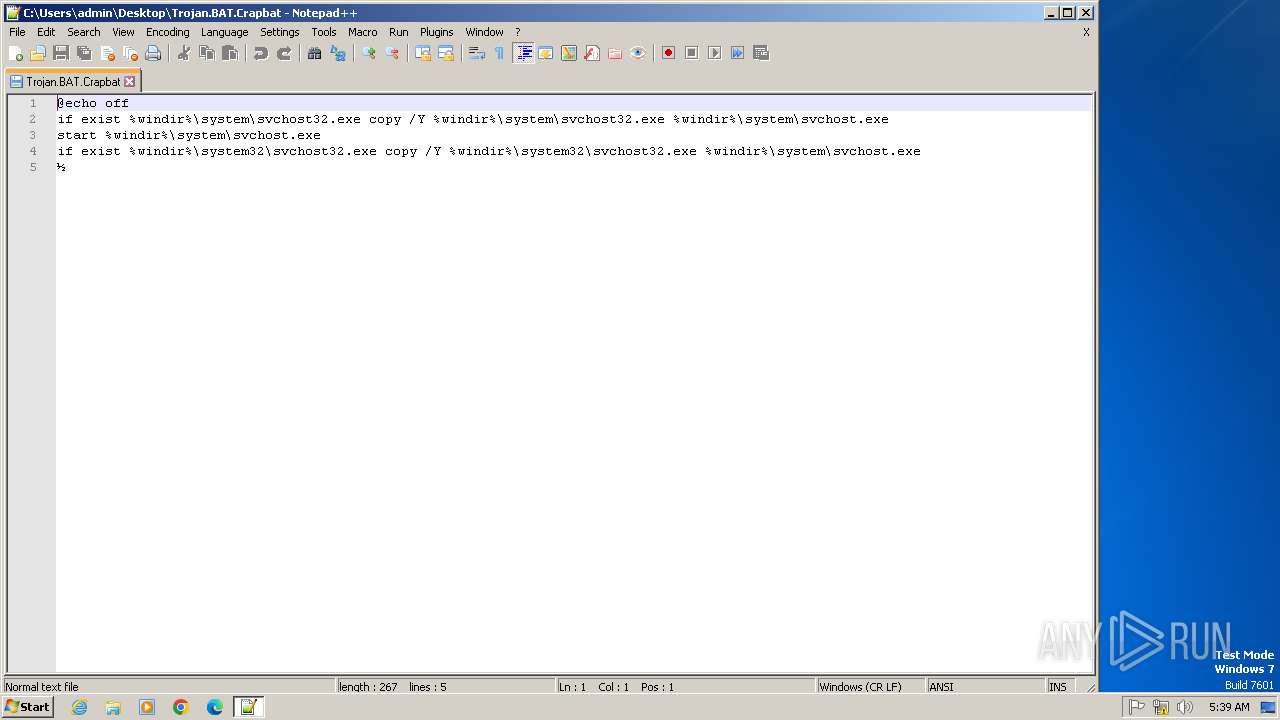
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text, with CRLF line terminators |
| MD5: | 23CD4244FD4EB14CA42F4AF89F576DAC |
| SHA1: | DF38F78F1C73B0996BA04DBCA849057BDA60FC1F |
| SHA256: | B283ED862DE0CEA47EAF84AA3F6B37000AE512FFC87A7A7799850EBA6CE130D4 |
| SSDEEP: | 12:05rIqXECnqA7DhccwLZdZBhfAy8wzyMakGLGy1:05UIE8FEZdZBhj8wzQkx4 |
MALICIOUS
The EICAR Standard Anti-Virus Test File is detected
- WinRAR.exe (PID: 3076)
SUSPICIOUS
Creates file in the systems drive root
- notepad++.exe (PID: 3352)
- notepad++.exe (PID: 944)
- ntvdm.exe (PID: 960)
INFO
Manual execution by a user
- WinRAR.exe (PID: 3076)
- notepad++.exe (PID: 1880)
- cmd.exe (PID: 268)
- explorer.exe (PID: 3640)
- cmd.exe (PID: 1276)
- notepad++.exe (PID: 3352)
- WinRAR.exe (PID: 3580)
- notepad++.exe (PID: 944)
- ntvdm.exe (PID: 960)
- ntvdm.exe (PID: 1332)
- rundll32.exe (PID: 1772)
- WinRAR.exe (PID: 2308)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3076)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
70
Monitored processes
17
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 268 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\Desktop\Trojan.BAT.Crapbat.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 944 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\Desktop\Trojan.BAT.FormatCQ.bat" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.91 Modules
| |||||||||||||||
| 960 | "C:\Windows\system32\ntvdm.exe" -i1 | C:\Windows\System32\ntvdm.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: NTVDM.EXE Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1276 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\Desktop\Virus.BAT.Ctty.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1332 | "C:\Windows\system32\ntvdm.exe" -i2 | C:\Windows\System32\ntvdm.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: NTVDM.EXE Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1772 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\Desktop\5251_Viruses_for_Anti-Virus_Testing\5251 Viruses for Anti-Virus Testing\Dutch_Tiny.163.b | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1880 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\Desktop\Trojan.BAT.Crapbat" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.91 Modules
| |||||||||||||||
| 2308 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\5251_Viruses_for_Anti-Virus_Testing\5251 Viruses for Anti-Virus Testing\Email-Worm.Win32.Alcaul.ak.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
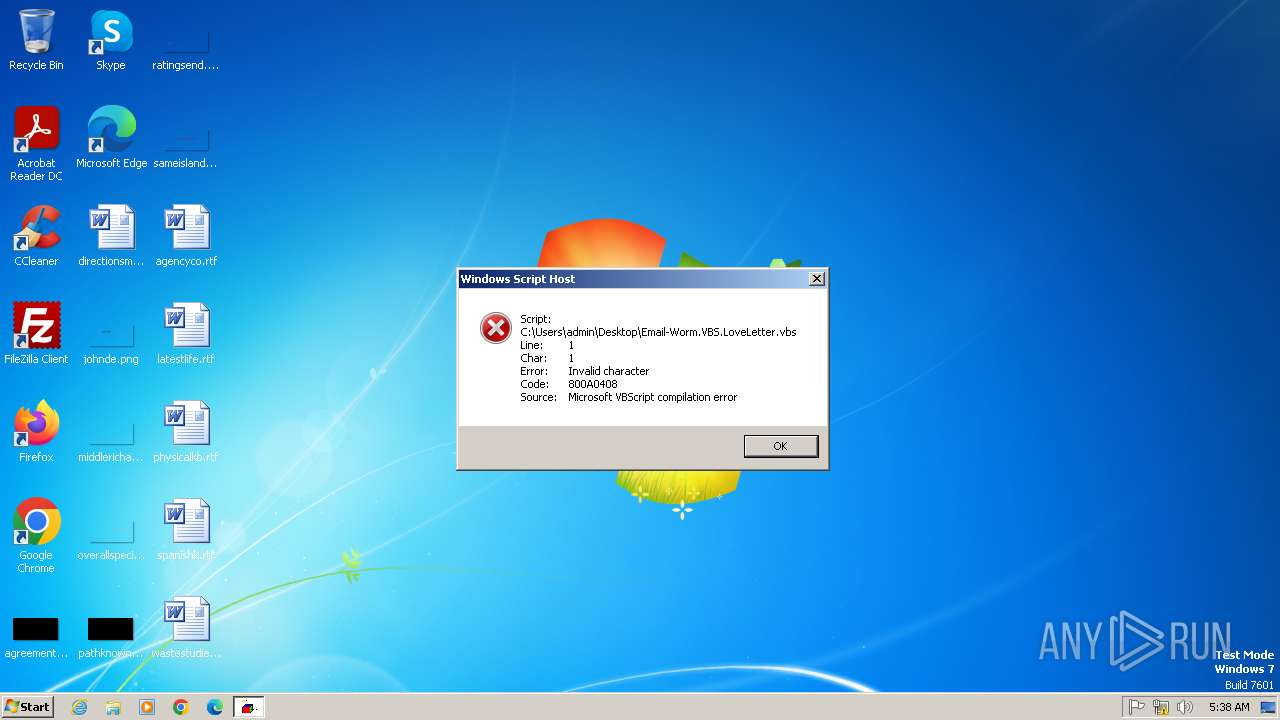
| 2448 | "C:\Windows\System32\WScript.exe" C:\Users\admin\Desktop\Email-Worm.VBS.LoveLetter.vbs | C:\Windows\System32\wscript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 1 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2760 | find /c "!" Virus.BAT.Ctty.bat | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (grep) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 970
Read events
2 889
Write events
81
Delete events
0
Modification events
| (PID) Process: | (1880) notepad++.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3076) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3076) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3352) notepad++.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3580) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3580) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3580) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3580) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3580) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (3580) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Trojan.BAT.FormatCQ.zip | |||
Executable files
53
Suspicious files
3 392
Text files
176
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3076 | WinRAR.exe | C:\Users\admin\Desktop\5251_Viruses_for_Anti-Virus_Testing\5251 Viruses for Anti-Virus Testing\7son.350 | binary | |
MD5:E49C13D6B953DC6CCA566B9F4C76479A | SHA256:FF14CE9E6E2EA079179F6B84B2A7EB000B3C8D95A155C19C78C2BCBBF81A98D2 | |||
| 3076 | WinRAR.exe | C:\Users\admin\Desktop\5251_Viruses_for_Anti-Virus_Testing\5251 Viruses for Anti-Virus Testing\7son.286 | binary | |
MD5:3152B368FFD5AF947BEB743BE06476F0 | SHA256:75AE6F7397EEA6B1EFC4EC0334B0920D3CCB5F5D91B3162B49972CA4F0068AE1 | |||
| 3076 | WinRAR.exe | C:\Users\admin\Desktop\5251_Viruses_for_Anti-Virus_Testing\5251 Viruses for Anti-Virus Testing\7son.334 | binary | |
MD5:DB516862B3B3A15A8DAF0426ADCAF0D3 | SHA256:82FAF0869B33C5594A9E9BF781E553B917C7041E4C0EAF89D787D082139A610B | |||
| 3076 | WinRAR.exe | C:\Users\admin\Desktop\5251_Viruses_for_Anti-Virus_Testing\5251 Viruses for Anti-Virus Testing\7son.284.e | binary | |
MD5:E73B6C2C2FD89BEF79DCF349EECA797F | SHA256:BB2BB70B0659A6E3CC568F45F33827449B064E2FEF5AE14B64C1DC4373222073 | |||
| 3076 | WinRAR.exe | C:\Users\admin\Desktop\5251_Viruses_for_Anti-Virus_Testing\5251 Viruses for Anti-Virus Testing\7son.284.a | binary | |
MD5:6BACB88A242312208BF35F821F2F9A4A | SHA256:C62B56F3E39EE54320B054607659244807B2830F5CEF0D40EB30DA5666AA86D6 | |||
| 3076 | WinRAR.exe | C:\Users\admin\Desktop\5251_Viruses_for_Anti-Virus_Testing\5251 Viruses for Anti-Virus Testing\10past3.b | binary | |
MD5:11C8B7CB1CAC301AC807AD7B6C1C1C3F | SHA256:17F8C4BAD3AF16C5FDA1697ED958559A30CA778608E0E298FADA02F11ABF8B32 | |||
| 3076 | WinRAR.exe | C:\Users\admin\Desktop\5251_Viruses_for_Anti-Virus_Testing\5251 Viruses for Anti-Virus Testing\1_COM | binary | |
MD5:19E14970DF9FEB1CFE3AA285171AB192 | SHA256:0C6E5AEF79152438869D451773C47D5E0BE0036E5A5C669919ADDBE87D658955 | |||
| 3076 | WinRAR.exe | C:\Users\admin\Desktop\5251_Viruses_for_Anti-Virus_Testing\5251 Viruses for Anti-Virus Testing\Ac-330.com | binary | |
MD5:BB2AB0F79D2D4122622CA6E232FFB4BF | SHA256:63BB1F14688E86CF05AB2F77F4D9AD356613E0671CF429E3E5ECC6422F0EBCEC | |||
| 3076 | WinRAR.exe | C:\Users\admin\Desktop\5251_Viruses_for_Anti-Virus_Testing\5251 Viruses for Anti-Virus Testing\ACDC.499 | binary | |
MD5:8561E3AAA203B91B39A8927AF2E5B068 | SHA256:378B7B0BA4B7C716EDFED02DD6F272BA145270C7889B1A7C2592349EEC7FA3DE | |||
| 3076 | WinRAR.exe | C:\Users\admin\Desktop\5251_Viruses_for_Anti-Virus_Testing\5251 Viruses for Anti-Virus Testing\09log | text | |
MD5:100428FCA645F08F792E45B0B3BF24A7 | SHA256:84C35115E8046B0FA36FF98C65A0B505C8AE114606EE0A4259F14310D3EBB1DA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
Threats
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\plugins\Config\nppPluginList.dll
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|