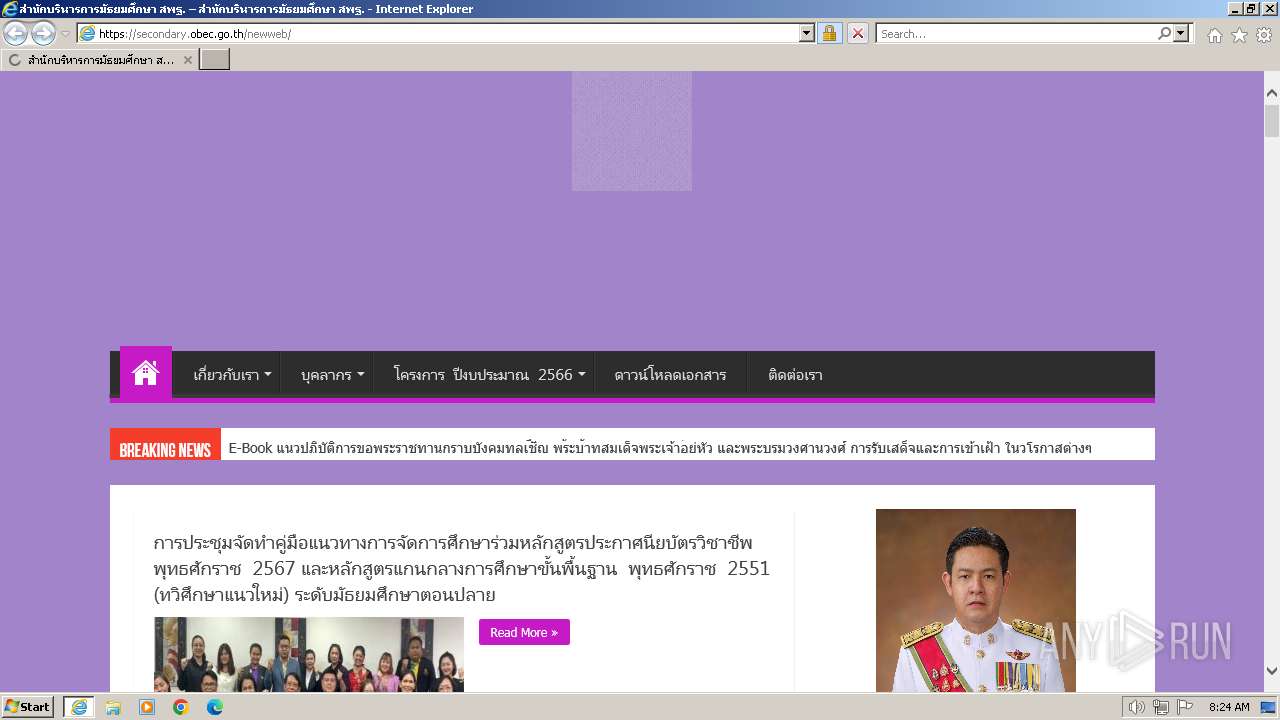
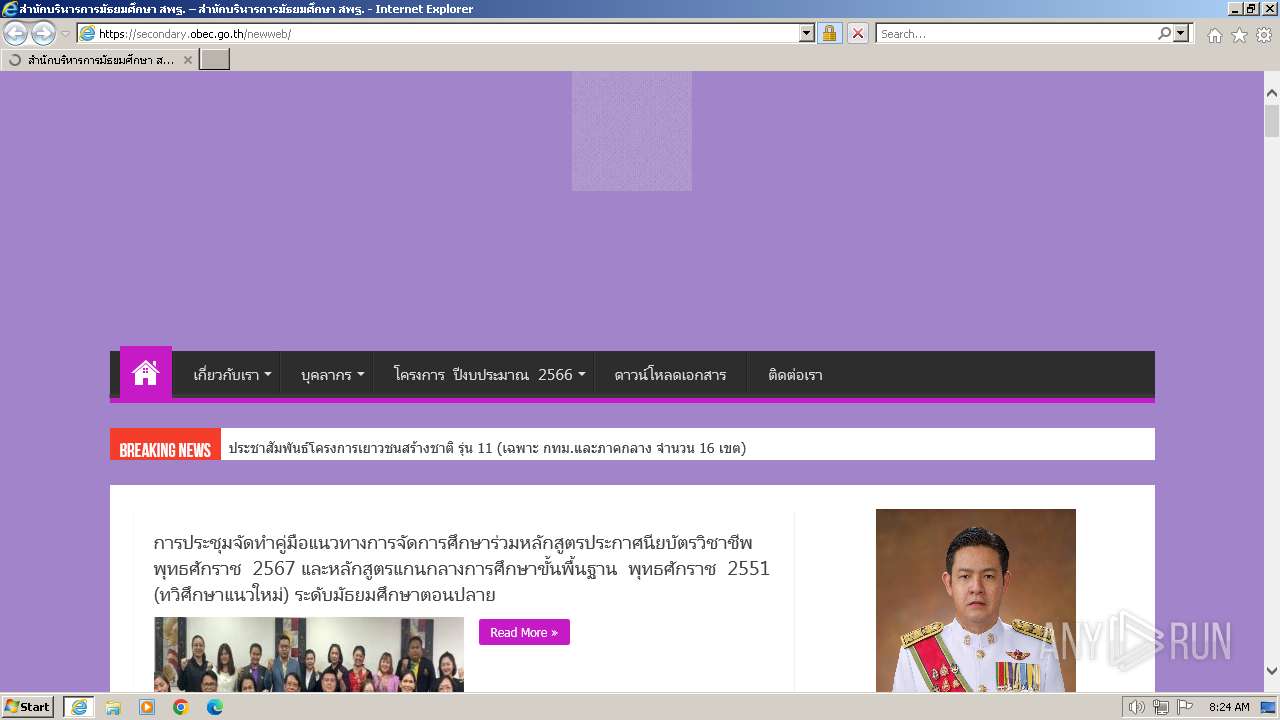
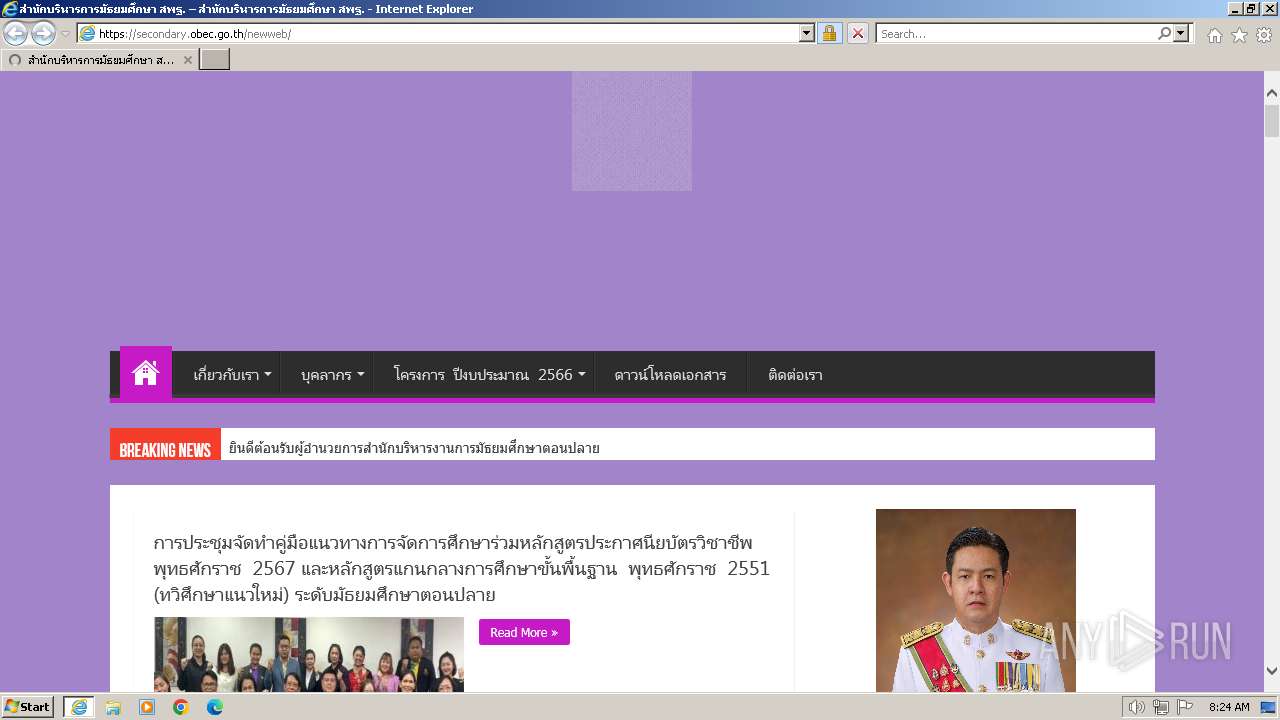
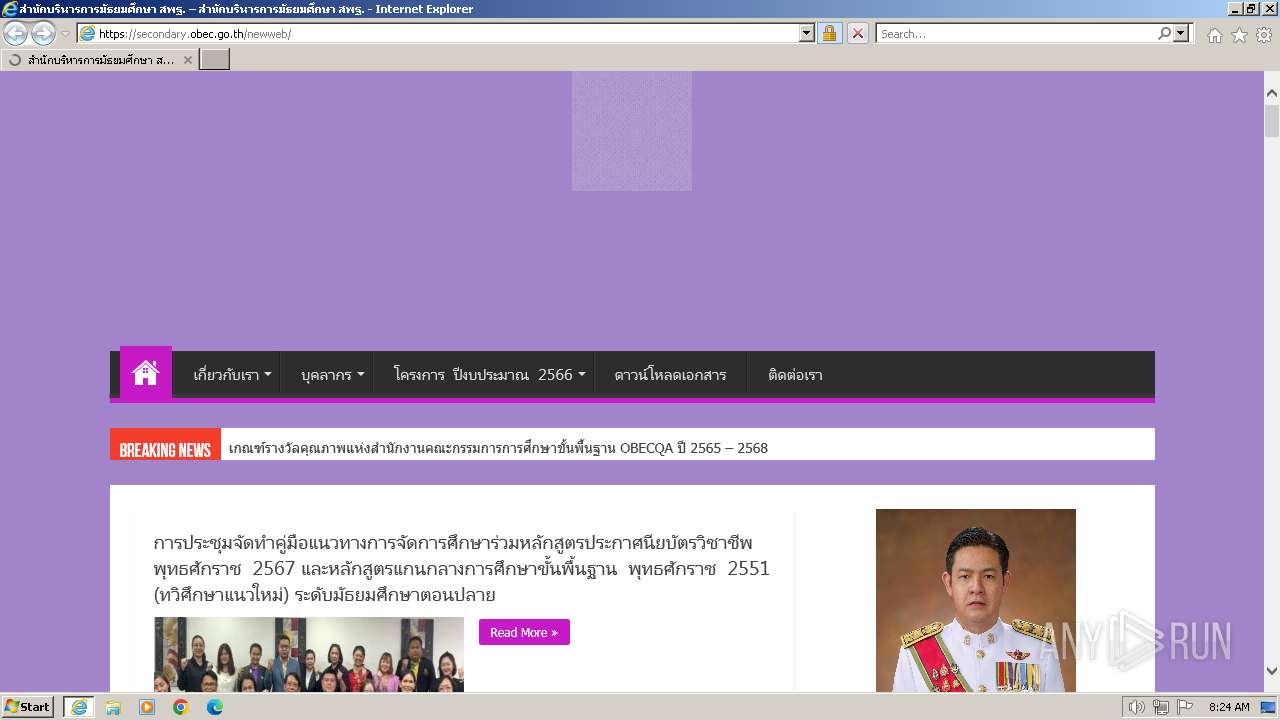
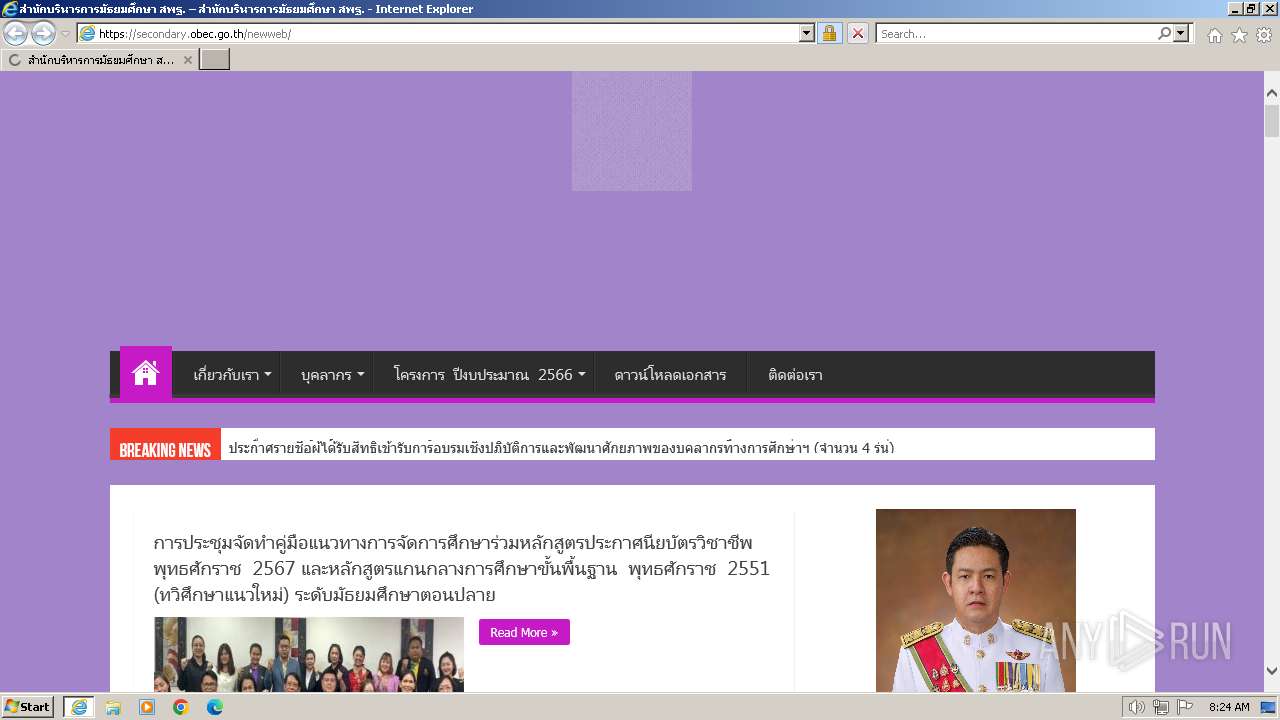
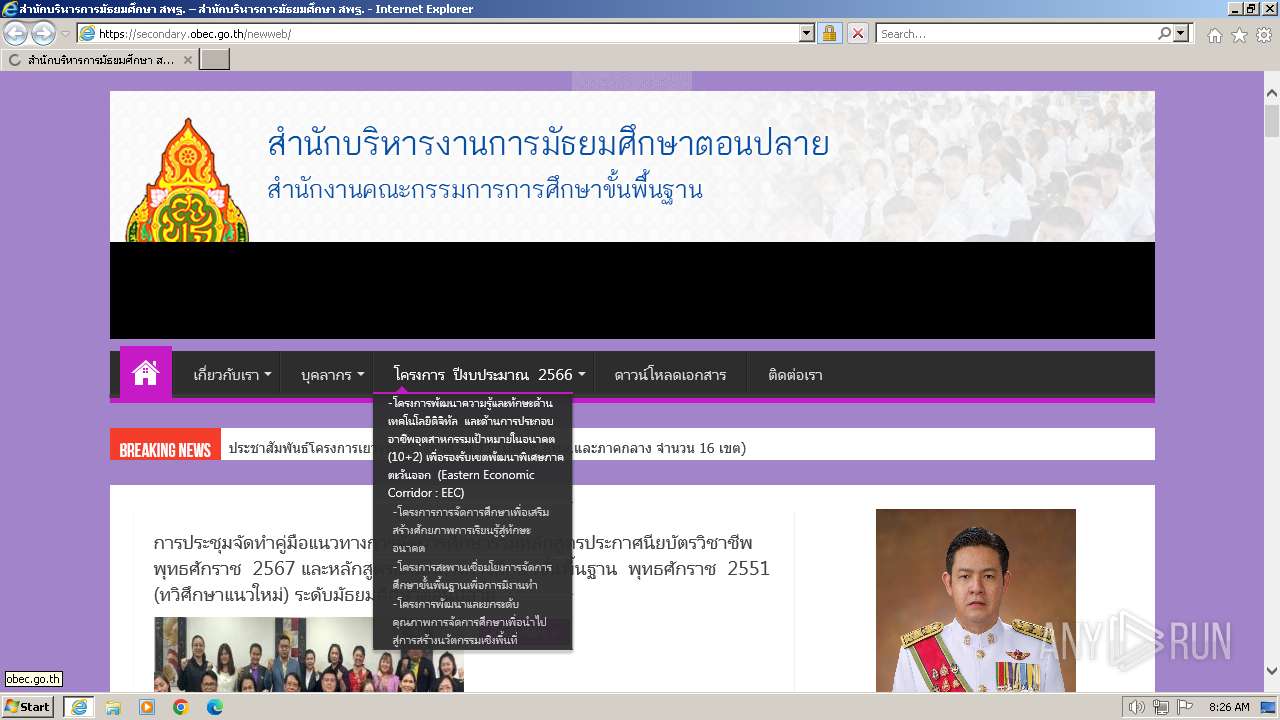
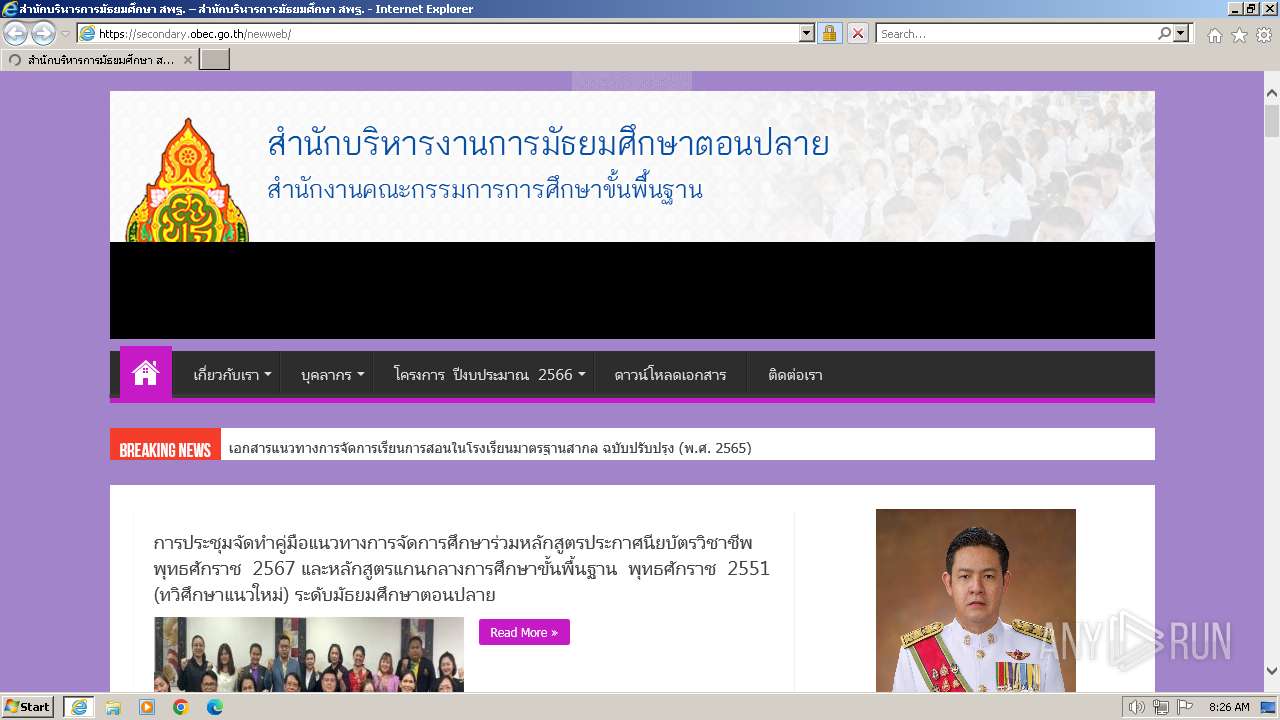
| URL: | secondary.obec.go.th |
| Full analysis: | https://app.any.run/tasks/bc68f830-e85f-4fa9-8f85-809e07b94d50 |
| Verdict: | Malicious activity |
| Analysis date: | February 13, 2024, 08:23:07 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | D0BA81730F49630404633E1BC666F371 |
| SHA1: | C9893FE3E58EE098EC4F168FBC3CCB7FCA0C3619 |
| SHA256: | B275826B7E171C806D315BB3F8A2557C10F56E37799BCFDE444F524DCFE755A8 |
| SSDEEP: | 3:v3KHA8rn:iHAon |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- iexplore.exe (PID: 3672)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
38
Monitored processes
2
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3672 | "C:\Program Files\Internet Explorer\iexplore.exe" "secondary.obec.go.th" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3972 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3672 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
17 681
Read events
17 547
Write events
98
Delete events
36
Modification events
| (PID) Process: | (3672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31088213 | |||
| (PID) Process: | (3672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31088213 | |||
| (PID) Process: | (3672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
20
Text files
72
Unknown types
15
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3972 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:4DA6126CA38F29B8FCAC20220F4AAB9F | SHA256:A3548E7D7B08DE28AFC75CB2E77E283B676CF9BC1F6351D5263E054ECA517C1A | |||
| 3972 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\103621DE9CD5414CC2538780B4B75751 | der | |
MD5:822467B728B7A66B081C91795373789A | SHA256:AF2343382B88335EEA72251AD84949E244FF54B6995063E24459A7216E9576B9 | |||
| 3972 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\TarF657.tmp | cat | |
MD5:9C0C641C06238516F27941AA1166D427 | SHA256:4276AF3669A141A59388BC56A87F6614D9A9BDDDF560636C264219A7EB11256F | |||
| 3972 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\D08593C793127C501A7E9F21177C91A4 | der | |
MD5:3D88A6FA7C50A772394060152C7AA06E | SHA256:78F6CBBA8898A9C4639C585DEA459E146DF1185F9649605CB3A4693671581F5A | |||
| 3972 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | der | |
MD5:D3D0F4D15D84DB215902B46E90192295 | SHA256:3922653BAEA808DC631EBBE586BF526226CC7B4A5E5D694AA6F2C215708F66C7 | |||
| 3972 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\265C0DEB29181DD1891051371C5F863A_8CFD0F060456F65ABC9E95E41A1F781C | binary | |
MD5:BD2EFFA696AB5AB4D50C2F8F8128AE51 | SHA256:FFB3C5CD5F2713EBB397326E7A731791671F19B1EF222C3D699184D9EE47AE35 | |||
| 3972 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | der | |
MD5:AC89A852C2AAA3D389B2D2DD312AD367 | SHA256:0B720E19270C672F9B6E0EC40B468AC49376807DE08A814573FE038779534F45 | |||
| 3972 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\newweb[1].htm | html | |
MD5:92E20DBFBEDC1AF5BD55866619C08FC5 | SHA256:5DDB55B20D991D27F9BCF7DF801C152DFE27D644A0AA9D3EFCF25DD89555C6CF | |||
| 3972 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | binary | |
MD5:29A72F3236D4CBAB39203680194493F5 | SHA256:71168FFC24ED397CFD39ACD51FCE9E6ECD3C426D1326F81CC495CE968F7B5690 | |||
| 3972 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\265C0DEB29181DD1891051371C5F863A_8CFD0F060456F65ABC9E95E41A1F781C | der | |
MD5:76E6910E5A84E5AC595D8A7FC41DE0AB | SHA256:6323985CF95F4070B25DE82E4AF772643808D2350E2BD2D27C5D8E59FCB03B6D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
16
TCP/UDP connections
54
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3972 | iexplore.exe | GET | 301 | 202.29.173.3:80 | http://secondary.obec.go.th/ | unknown | html | 237 b | unknown |
3972 | iexplore.exe | GET | 304 | 23.72.36.112:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?14266dff8470122f | unknown | — | — | unknown |
3972 | iexplore.exe | GET | 200 | 23.72.36.112:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?c9f2b763ba05a2db | unknown | compressed | 65.2 Kb | unknown |
3972 | iexplore.exe | GET | 200 | 23.206.4.242:80 | http://x1.c.lencr.org/ | unknown | binary | 717 b | unknown |
3972 | iexplore.exe | GET | 200 | 142.250.185.195:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
3972 | iexplore.exe | GET | 200 | 23.72.36.24:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgPdzAr%2BkPYhVSrrssjFOzaEzw%3D%3D | unknown | binary | 503 b | unknown |
3972 | iexplore.exe | GET | 200 | 142.250.185.195:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEGbSiPAo8Qj1CbnbR%2FpRjKM%3D | unknown | binary | 471 b | unknown |
3972 | iexplore.exe | GET | 200 | 142.250.185.195:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | unknown | binary | 724 b | unknown |
3672 | iexplore.exe | GET | 304 | 23.72.36.112:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a973ebecfe8ccbeb | unknown | — | — | unknown |
3672 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAxq6XzO1ZmDhpCgCp6lMhQ%3D | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3972 | iexplore.exe | 202.29.173.3:80 | secondary.obec.go.th | Office of the basic education commission | TH | unknown |
3972 | iexplore.exe | 202.29.173.3:443 | secondary.obec.go.th | Office of the basic education commission | TH | unknown |
3972 | iexplore.exe | 23.72.36.112:80 | ctldl.windowsupdate.com | Akamai International B.V. | IE | unknown |
3972 | iexplore.exe | 23.206.4.242:80 | x1.c.lencr.org | AKAMAI-AS | FR | unknown |
3972 | iexplore.exe | 23.72.36.24:80 | r3.o.lencr.org | Akamai International B.V. | IE | unknown |
3972 | iexplore.exe | 142.250.186.74:443 | fonts.googleapis.com | GOOGLE | US | whitelisted |
3972 | iexplore.exe | 142.250.185.195:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
secondary.obec.go.th |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
r3.o.lencr.org |
| shared |
fonts.googleapis.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |