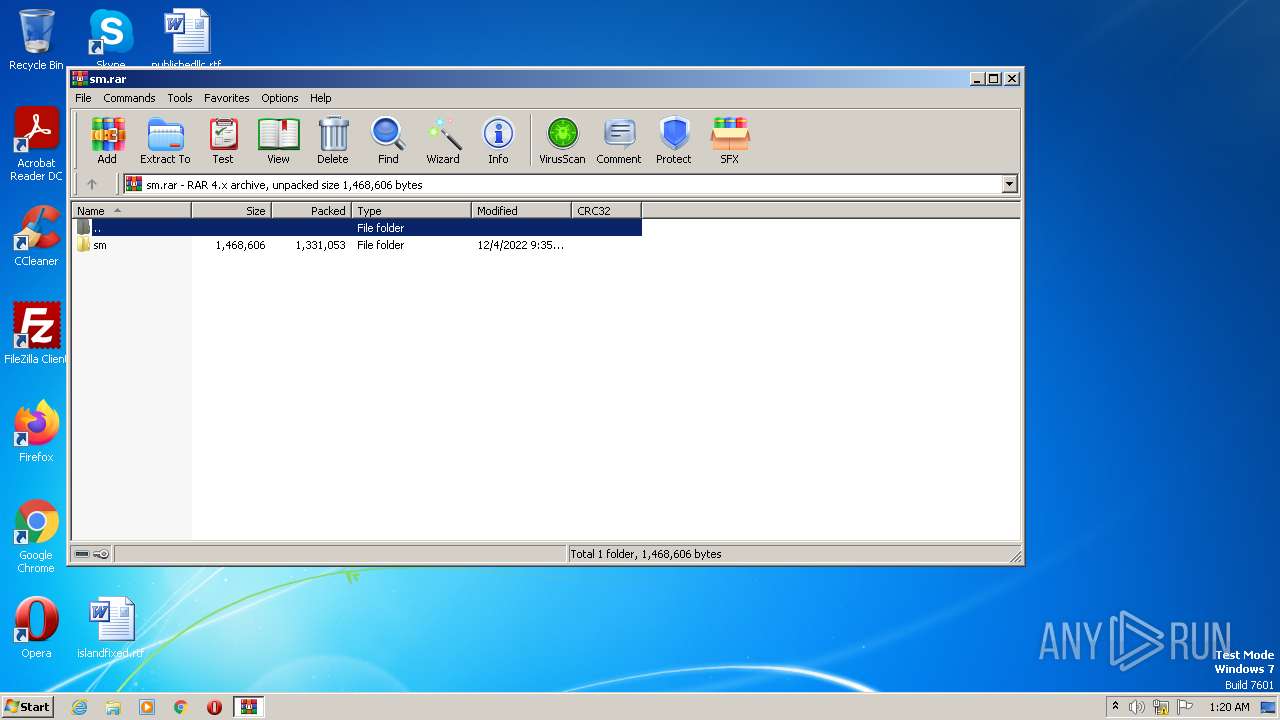
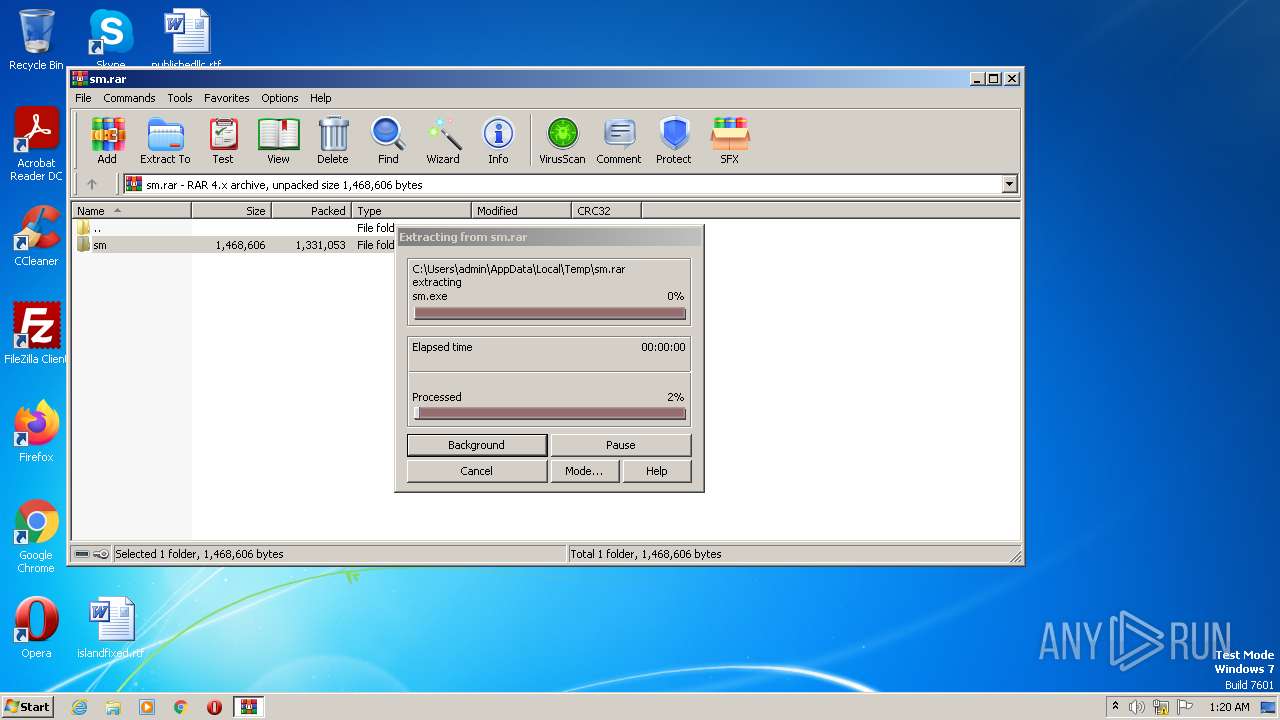
| File name: | sm.rar |
| Full analysis: | https://app.any.run/tasks/e4861087-11c7-4e16-bf06-534ece9d31cc |
| Verdict: | Malicious activity |
| Analysis date: | April 01, 2023, 00:20:03 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32, flags: RecoveryRecordPresent |
| MD5: | 546331BD7A1ABD37750A4A3F5C226379 |
| SHA1: | 1B6A2DA471AE52EB08F1D69EBE38D3E100887D7A |
| SHA256: | B266F235794AF5D05EBBD0A327EF1590A832EF8057A8D657744602842A48A856 |
| SSDEEP: | 24576:xrjyM2jvyFjn/qWLKau3jz+kdVQIGwr6ZqBLpY1yaw8Swb2J1hGizqZCp5zKh19l:xreMwveCWLKaaeAVQIGwnpY1yo/qhG8U |
MALICIOUS
Application was dropped or rewritten from another process
- sm.exe (PID: 3808)
- crack.exe (PID: 1964)
- crack.exe (PID: 3100)
- crack.exe (PID: 3540)
Create files in the Startup directory
- crack.exe (PID: 1964)
SUSPICIOUS
Reads Microsoft Outlook installation path
- sm.exe (PID: 3808)
Reads the Internet Settings
- sm.exe (PID: 3808)
Reads Internet Explorer settings
- sm.exe (PID: 3808)
Executable content was dropped or overwritten
- sm.exe (PID: 3808)
- crack.exe (PID: 1964)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2512)
Manual execution by a user
- sm.exe (PID: 3808)
- crack.exe (PID: 3100)
- crack.exe (PID: 3540)
Checks supported languages
- sm.exe (PID: 3808)
- crack.exe (PID: 1964)
- crack.exe (PID: 3100)
- crack.exe (PID: 3540)
The process checks LSA protection
- sm.exe (PID: 3808)
- crack.exe (PID: 1964)
- crack.exe (PID: 3100)
- crack.exe (PID: 3540)
Reads the computer name
- sm.exe (PID: 3808)
- crack.exe (PID: 1964)
- crack.exe (PID: 3100)
- crack.exe (PID: 3540)
Checks proxy server information
- sm.exe (PID: 3808)
Reads the machine GUID from the registry
- sm.exe (PID: 3808)
- crack.exe (PID: 1964)
- crack.exe (PID: 3100)
- crack.exe (PID: 3540)
Creates files or folders in the user directory
- crack.exe (PID: 1964)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| ArchivedFileName: | sm\sm.exe |
|---|---|
| PackingMethod: | Normal |
| ModifyDate: | 2022:12:04 21:35:48 |
| OperatingSystem: | Win32 |
| UncompressedSize: | 1468606 |
| CompressedSize: | 1331088 |
Total processes
42
Monitored processes
5
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1964 | "C:\Users\admin\Desktop\sm\crack.exe" | C:\Users\admin\Desktop\sm\crack.exe | sm.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2512 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\sm.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3100 | "C:\Users\admin\Desktop\sm\crack.exe" | C:\Users\admin\Desktop\sm\crack.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3540 | "C:\Users\admin\Desktop\sm\crack.exe" | C:\Users\admin\Desktop\sm\crack.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3808 | "C:\Users\admin\Desktop\sm\sm.exe" | C:\Users\admin\Desktop\sm\sm.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
3 202
Read events
3 144
Write events
58
Delete events
0
Modification events
| (PID) Process: | (2512) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2512) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2512) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2512) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2512) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2512) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2512) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2512) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2512) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (2512) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\Desktop | |||
Executable files
6
Suspicious files
4
Text files
646
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3808 | sm.exe | C:\Users\admin\Desktop\sm\modules\framer.txt | html | |
MD5:— | SHA256:— | |||
| 3808 | sm.exe | C:\Users\admin\Desktop\sm\index.css | text | |
MD5:— | SHA256:— | |||
| 3808 | sm.exe | C:\Users\admin\Desktop\sm\modules\htacess.txt | text | |
MD5:— | SHA256:— | |||
| 3808 | sm.exe | C:\Users\admin\Desktop\sm\css\ui-darkness\jquery-ui-1.8.23.custom.css | text | |
MD5:— | SHA256:— | |||
| 3808 | sm.exe | C:\Users\admin\Desktop\sm\js\jquery.qtip.min.css | text | |
MD5:— | SHA256:— | |||
| 3808 | sm.exe | C:\Users\admin\Desktop\sm\addons\chili\docs.js | text | |
MD5:— | SHA256:— | |||
| 3808 | sm.exe | C:\Users\admin\Desktop\sm\css\theme.blue.css | text | |
MD5:— | SHA256:— | |||
| 2512 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2512.39685\sm\sm.exe | executable | |
MD5:— | SHA256:— | |||
| 3808 | sm.exe | C:\Users\admin\Desktop\sm\modules\domain_searcher.txt | text | |
MD5:— | SHA256:— | |||
| 3808 | sm.exe | C:\Users\admin\Desktop\sm\js\jquery.jqplot.min.css | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report