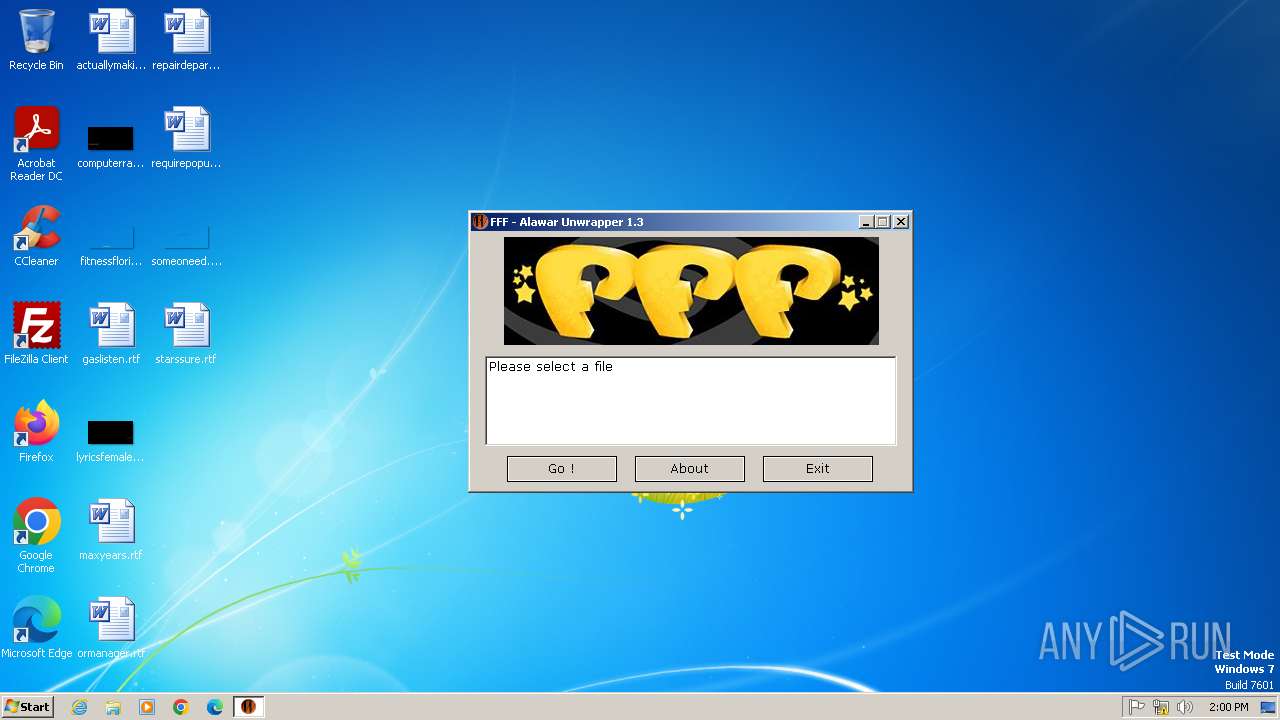
| File name: | Alawar_Crack_1.3.exe |
| Full analysis: | https://app.any.run/tasks/e97acb30-9695-45af-b675-2caf384d831a |
| Verdict: | Malicious activity |
| Analysis date: | June 21, 2025, 13:00:40 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | 8663C5A47468BD05A599BBE3B04AC66D |
| SHA1: | E9C39120A89DE6906399D38591A143706F985A3F |
| SHA256: | B2630C6DF1461992641C156F1C92BD50F51139B530F5A571C5D10F185B1A3DD8 |
| SSDEEP: | 12288:ntF5w/wyyfPU/7XoKGvIpgSvTKNX0zHidcLKf8Jinl:ntF5w4yWPG7XoRIpgSvTKNX0zCKLKf8s |
MALICIOUS
No malicious indicators.SUSPICIOUS
There is functionality for taking screenshot (YARA)
- Alawar_Crack_1.3.exe (PID: 2212)
Creates file in the systems drive root
- Alawar_Crack_1.3.exe (PID: 2212)
Executable content was dropped or overwritten
- CCleaner.exe (PID: 3460)
Reads settings of System Certificates
- CCleaner.exe (PID: 3460)
Reads security settings of Internet Explorer
- CCleaner.exe (PID: 3460)
Searches for installed software
- CCleaner.exe (PID: 3460)
Reads Internet Explorer settings
- CCleaner.exe (PID: 3460)
Reads the date of Windows installation
- CCleaner.exe (PID: 3460)
Reads the Internet Settings
- CCleaner.exe (PID: 3460)
Reads Microsoft Outlook installation path
- CCleaner.exe (PID: 3460)
Checks for external IP
- CCleaner.exe (PID: 3460)
INFO
Reads the computer name
- Alawar_Crack_1.3.exe (PID: 2212)
- CCleaner.exe (PID: 3460)
Reads the machine GUID from the registry
- Alawar_Crack_1.3.exe (PID: 2212)
- CCleaner.exe (PID: 3460)
Checks supported languages
- Alawar_Crack_1.3.exe (PID: 2212)
- CCleaner.exe (PID: 3460)
The sample compiled with english language support
- Alawar_Crack_1.3.exe (PID: 2212)
- CCleaner.exe (PID: 3460)
Reads product name
- CCleaner.exe (PID: 3460)
Creates files in the program directory
- CCleaner.exe (PID: 3460)
Reads CPU info
- CCleaner.exe (PID: 3460)
Reads Environment values
- CCleaner.exe (PID: 3460)
Reads the software policy settings
- CCleaner.exe (PID: 3460)
Checks proxy server information
- CCleaner.exe (PID: 3460)
Creates files or folders in the user directory
- CCleaner.exe (PID: 3460)
Detects AutoHotkey samples (YARA)
- CCleaner.exe (PID: 3460)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (42.6) |
|---|---|---|
| .exe | | | Clipper DOS Executable (19.1) |
| .exe | | | Generic Win/DOS Executable (18.9) |
| .exe | | | DOS Executable Generic (18.9) |
| .vxd | | | VXD Driver (0.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2012:09:13 21:22:42+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 5.12 |
| CodeSize: | 18432 |
| InitializedDataSize: | 145920 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x2d5b0 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.3.0.0 |
| ProductVersionNumber: | 1.3.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| Company: | FiGHTiNG FoR FuN TEAM |
| FileVersion: | 1.3 |
| FileDescription: | TROLOLOLOLO |
| ProductVersion: | 1.3 |
| ProductName: | Asprotect? wtf |
| LegalCopyright: | TEAM FFF (c) Since 2002 |
| InternalName: | AlawarNightmare.EXE |
Total processes
41
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2212 | "C:\Users\admin\AppData\Local\Temp\Alawar_Crack_1.3.exe" | C:\Users\admin\AppData\Local\Temp\Alawar_Crack_1.3.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: TROLOLOLOLO Exit code: 0 Version: 1.3 Modules
| |||||||||||||||
| 2784 | "C:\Users\admin\AppData\Local\Temp\Alawar_Crack_1.3.exe" | C:\Users\admin\AppData\Local\Temp\Alawar_Crack_1.3.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: TROLOLOLOLO Exit code: 3221226540 Version: 1.3 Modules
| |||||||||||||||
| 3460 | "C:\Program Files\CCleaner\CCleaner.exe" | C:\Program Files\CCleaner\CCleaner.exe | Alawar_Crack_1.3.exe | ||||||||||||
User: admin Company: Piriform Software Ltd Integrity Level: HIGH Description: CCleaner Exit code: 0 Version: 6.14.0.10584 Modules
| |||||||||||||||
Total events
25 171
Read events
24 773
Write events
317
Delete events
81
Modification events
| (PID) Process: | (2212) Alawar_Crack_1.3.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 02020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (2212) Alawar_Crack_1.3.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 020000000000000001000000070000000E0000000B000000060000000C0000000D0000000A0000000900000008000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (2212) Alawar_Crack_1.3.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlg |
| Operation: | write | Name: | TV_FolderType |
Value: {FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9} | |||
| (PID) Process: | (2212) Alawar_Crack_1.3.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlg |
| Operation: | write | Name: | TV_TopViewID |
Value: {82BA0782-5B7A-4569-B5D7-EC83085F08CC} | |||
| (PID) Process: | (2212) Alawar_Crack_1.3.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlg |
| Operation: | write | Name: | TV_TopViewVersion |
Value: 0 | |||
| (PID) Process: | (2212) Alawar_Crack_1.3.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2212) Alawar_Crack_1.3.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\AllFolders\ComDlg\{FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9}\{82BA0782-5B7A-4569-B5D7-EC83085F08CC} |
| Operation: | write | Name: | Mode |
Value: 4 | |||
| (PID) Process: | (2212) Alawar_Crack_1.3.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\AllFolders\ComDlg\{FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9}\{82BA0782-5B7A-4569-B5D7-EC83085F08CC} |
| Operation: | write | Name: | LogicalViewMode |
Value: 1 | |||
| (PID) Process: | (2212) Alawar_Crack_1.3.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\AllFolders\ComDlg\{FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9}\{82BA0782-5B7A-4569-B5D7-EC83085F08CC} |
| Operation: | write | Name: | FFlags |
Value: | |||
| (PID) Process: | (2212) Alawar_Crack_1.3.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\AllFolders\ComDlg\{FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9}\{82BA0782-5B7A-4569-B5D7-EC83085F08CC} |
| Operation: | write | Name: | IconSize |
Value: 16 | |||
Executable files
3
Suspicious files
22
Text files
10
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3460 | CCleaner.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\Z7GEJABLAFLD9UF1VLS0.temp | binary | |
MD5:B06EC5C057D268A252C74F9C4BBBBD1B | SHA256:515F852AB2DD1B05C317D635FD156D80D58404F7EA04802EDDE1895953042DFA | |||
| 3460 | CCleaner.exe | C:\Program Files\CCleaner\gcapi_dll.dll | executable | |
MD5:F637D5D3C3A60FDDB5DD397556FE9B1D | SHA256:641B843CB6EE7538EC267212694C9EF0616B9AC9AB14A0ABD7CF020678D50B02 | |||
| 3460 | CCleaner.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:8DDFB7713441691DCF9360582D520646 | SHA256:A89A8D9FB8D7DAD0AE1E1FC8D86A50387B5E1D1D3F44633F85F28E5B0003A453 | |||
| 3460 | CCleaner.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:A4D747749685F3229D116861B50A2019 | SHA256:1E9741FF3FC1992C9D44A81F735C83FF5D6655354E930FA5797EEDC1B3C5907D | |||
| 3460 | CCleaner.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\05DDC6AA91765AACACDB0A5F96DF8199 | binary | |
MD5:FE2726175B28FA9F0E47304C3D726F4A | SHA256:9EA0B0DF2049B5596CC2BD4A87A4DF9D48DB0EAB36A3D529C53AD2778A77006D | |||
| 3460 | CCleaner.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B398B80134F72209547439DB21AB308D_A4CF52CCA82D7458083F7280801A3A04 | binary | |
MD5:E7CCA0844D8D615BBA815D7AEB20D9EF | SHA256:D0FA402EB2804FB2876D66E762234F85D3BB8E6B50646B6947521770CA53587E | |||
| 3460 | CCleaner.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E573CDF4C6D731D56A665145182FD759_AFB3BE9383420FBAFF24AD413EEA555E | binary | |
MD5:49ABF72101B0842AC408F692CA9A11AE | SHA256:40A44218E504CE3F6C1FEF9BE21F960DFBC884966BD9094871B054E9915D2FC5 | |||
| 3460 | CCleaner.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E573CDF4C6D731D56A665145182FD759_AFB3BE9383420FBAFF24AD413EEA555E | binary | |
MD5:DA655B32488FD1B36E624C5EDB48A50F | SHA256:9500504F1E9D26968453BBB6113A3464C03650731FA339EC097F4D1879FDE9D1 | |||
| 3460 | CCleaner.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\D1BB4760A5593D9A6B163AD677242860_1B9E997B49F2FCF9EA2D08F5A999C340 | binary | |
MD5:EDFA033E676BFF2886EB4B7077C545C3 | SHA256:7FA1D4CF7DAED31083B826B4F791677895ED013E046E1850C12E1746A9EF5CD2 | |||
| 3460 | CCleaner.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\F44F0D8080C8C3429C5AB2379F33E907_36516A32D5B34401A68F7B7E010B64C8 | binary | |
MD5:80B9581BC3AAE8B9FEDE10F4FD01E058 | SHA256:964F6325775DCFE1EC8C85CC4872BF1CE97C9C2C9CDE6957B65EECDDBBE82E2D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
22
DNS requests
15
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3460 | CCleaner.exe | GET | 200 | 23.200.86.242:80 | http://ncc.avast.com/ncc.txt | unknown | — | — | whitelisted |
3460 | CCleaner.exe | GET | 200 | 2.19.11.178:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?4aa8bddf94683dd4 | unknown | — | — | whitelisted |
3460 | CCleaner.exe | GET | 200 | 2.19.11.178:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?13f8d32d5d0a02f5 | unknown | — | — | whitelisted |
3460 | CCleaner.exe | GET | 200 | 2.19.11.178:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?ba76936b4371c0d8 | unknown | — | — | whitelisted |
3460 | CCleaner.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | — | — | whitelisted |
3460 | CCleaner.exe | GET | 200 | 2.19.11.178:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?7425a981795f17e8 | unknown | — | — | whitelisted |
3460 | CCleaner.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTk45WiKdPUwcMf8JgMC07ACYqr2AQUt2ui6qiqhIx56rTaD5iyxZV2ufQCEAXfj0A2M0oL7zuU%2F%2F2jetU%3D | unknown | — | — | whitelisted |
3460 | CCleaner.exe | GET | 200 | 216.58.206.67:80 | http://o.pki.goog/s/wr3/BhM/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQSq0i5t2Pafi2Gw9uzwnc7KTctWgQUx4H1%2FY6I2QA8TWOiUDEkoM4j%2FiMCEAYTImF6xaxMEJAS2j2k4Ng%3D | unknown | — | — | whitelisted |
3460 | CCleaner.exe | GET | 200 | 142.250.184.195:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | — | — | whitelisted |
3460 | CCleaner.exe | GET | 200 | 172.217.16.195:80 | http://c.pki.goog/r/r1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3460 | CCleaner.exe | 23.200.86.242:80 | ncc.avast.com | Akamai International B.V. | FR | whitelisted |
3460 | CCleaner.exe | 34.117.223.223:443 | analytics.ff.avast.com | GOOGLE-CLOUD-PLATFORM | US | whitelisted |
3460 | CCleaner.exe | 34.111.24.1:443 | ipm-provider.ff.avast.com | GOOGLE | US | whitelisted |
3460 | CCleaner.exe | 2.19.225.128:443 | www.ccleaner.com | AKAMAI-AS | FR | whitelisted |
3460 | CCleaner.exe | 34.160.176.28:443 | shepherd.ff.avast.com | GOOGLE | US | whitelisted |
3460 | CCleaner.exe | 2.19.11.178:80 | ctldl.windowsupdate.com | Elisa Oyj | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
ncc.avast.com |
| whitelisted |
analytics.ff.avast.com |
| whitelisted |
www.ccleaner.com |
| whitelisted |
ipm-provider.ff.avast.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
shepherd.ff.avast.com |
| whitelisted |
ip-info.ff.avast.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Misc activity | ET INFO External IP Lookup Service in DNS Query (ip-info .ff .avast .com) |
3460 | CCleaner.exe | Misc activity | ET INFO Observed External IP Lookup Domain (ip-info .ff .avast .com) in TLS SNI |
Process | Message |
|---|---|
CCleaner.exe | [2025-06-21 13:01:10.514] [error ] [settings ] [ 3460: 3060] [6000C4: 356] Failed to get program directory
Exception: Unable to determine program folder of product 'piriform-cc'!
Code: 0x000000c0 (192)
|
CCleaner.exe | Failed to open log file 'C:\Program Files\CCleaner' |
CCleaner.exe | OnLanguage - en
|
CCleaner.exe | [2025-06-21 13:01:12.452] [error ] [settings ] [ 3460: 3424] [9434E9: 359] Failed to get program directory
Exception: Unable to determine program folder of product 'piriform-cc'!
Code: 0x000000c0 (192)
|
CCleaner.exe | [2025-06-21 13:01:12.483] [error ] [Burger ] [ 3460: 3424] [FDA25D: 244] [23.1.806.0] [BurgerReporter.cpp] [244] asw::standalone_svc::BurgerReporter::BurgerSwitch: Could not read property BURGER_SETTINGS_PANCAKE_HOSTNAME (0x00000003)
|
CCleaner.exe | [2025-06-21 13:01:12.483] [error ] [Burger ] [ 3460: 3424] [FDA25D: 244] [23.1.806.0] [BurgerReporter.cpp] [244] asw::standalone_svc::BurgerReporter::BurgerSwitch: Could not read property BURGER_SETTINGS_PANCAKE_HOSTNAME (0x00000003)
|
CCleaner.exe | startCheckingLicense()
|
CCleaner.exe | OnLanguage - en
|
CCleaner.exe | OnLanguage - en
|
CCleaner.exe | OnLanguage - en
|