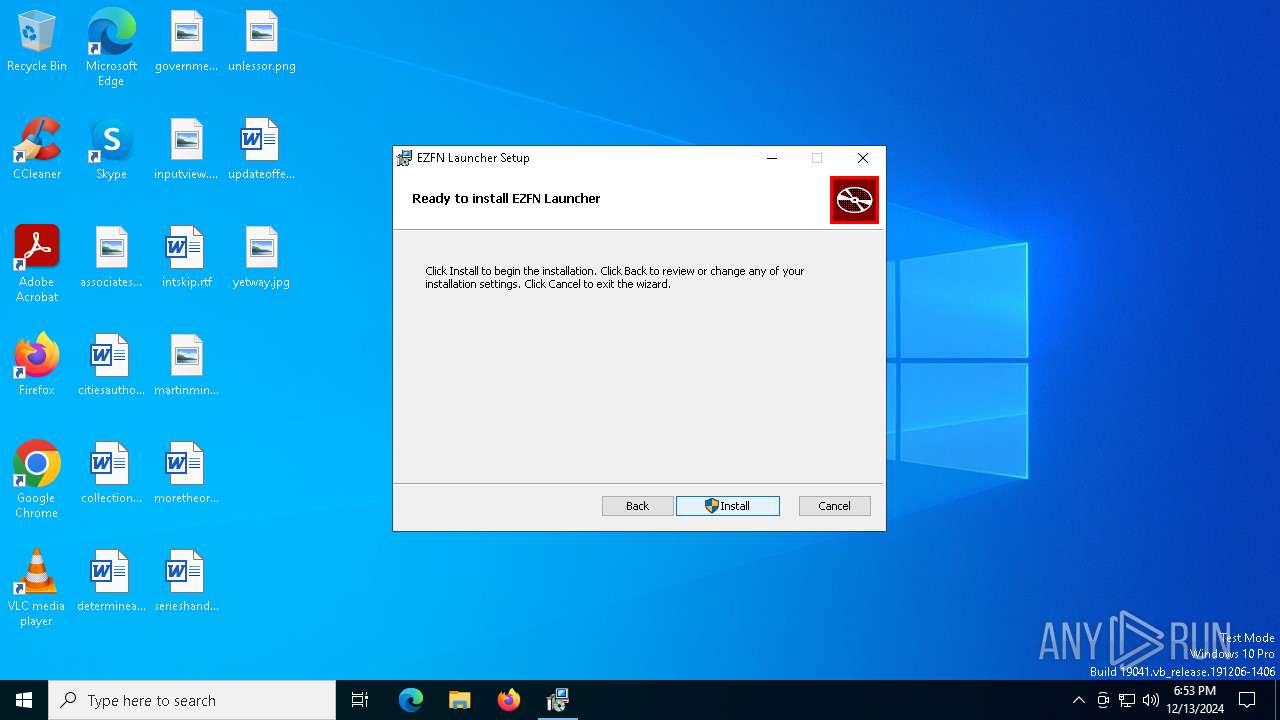
| File name: | EZFN Launcher_1.2.7_x64_en-US.msi |
| Full analysis: | https://app.any.run/tasks/233b7b5f-2972-45fc-9b34-19173f2b96f0 |
| Verdict: | Malicious activity |
| Analysis date: | December 13, 2024, 18:53:23 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, MSI Installer, Code page: 1252, Title: Installation Database, Subject: EZFN Launcher, Author: ezfn, Keywords: Installer, Comments: This installer database contains the logic and data required to install EZFN Launcher., Template: x64;0, Revision Number: {8E8ADF67-611A-418A-81D9-A15A7CD2D5D7}, Create Time/Date: Wed Nov 13 21:30:16 2024, Last Saved Time/Date: Wed Nov 13 21:30:16 2024, Number of Pages: 450, Number of Words: 2, Name of Creating Application: Windows Installer XML Toolset (3.11.2.4516), Security: 2 |
| MD5: | 1425A73D9D6DB003B57BFC2134EA9D70 |
| SHA1: | D31866A0CCC44F2DB6A17402F1219BF75E03B8E4 |
| SHA256: | B244361E1DAC8D917BE21D8E8453112C461F69FF3EC00E1844F6536379B8CD7F |
| SSDEEP: | 98304:QxIWsnjGEXs509D2E4ZlcXZ4qWav6MTvJs6O49zN0BFzdAFX+5UsgoUveJPg8EI2:+eD2Q3DKq//5 |
MALICIOUS
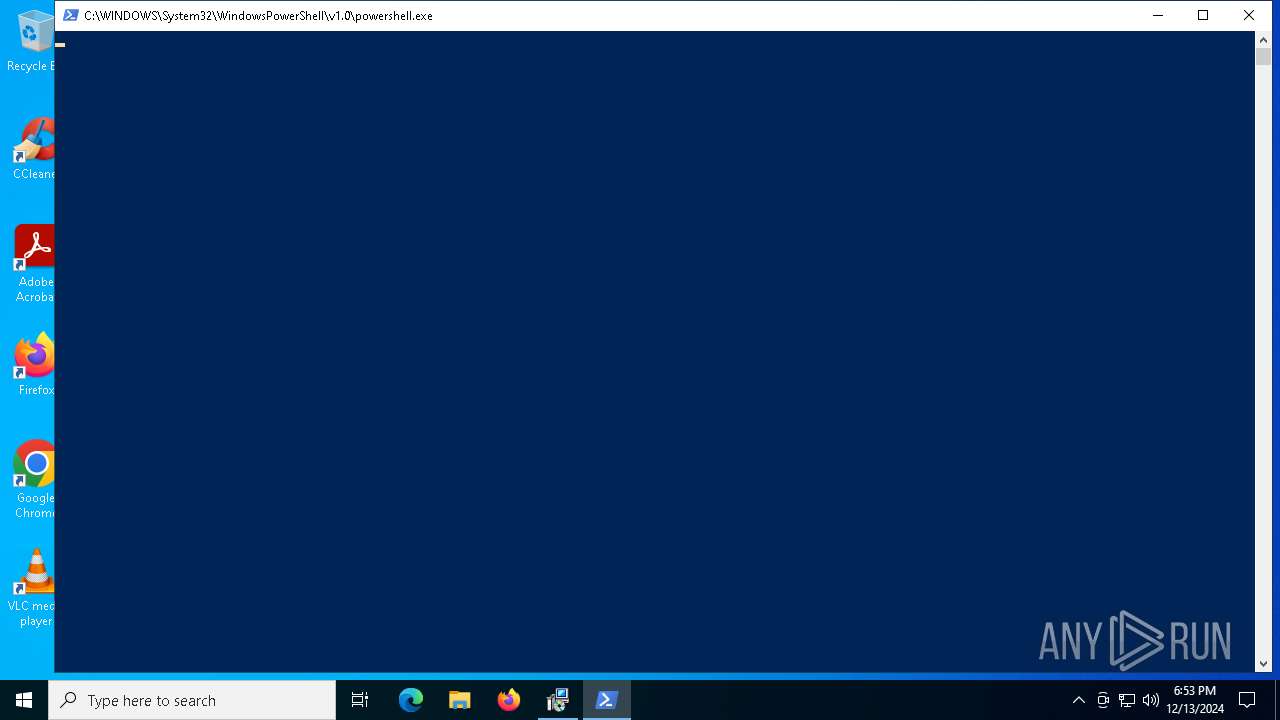
Run PowerShell with an invisible window
- powershell.exe (PID: 4400)
SUSPICIOUS
Executes as Windows Service
- VSSVC.exe (PID: 6912)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 6452)
Manipulates environment variables
- powershell.exe (PID: 4400)
Starts POWERSHELL.EXE for commands execution
- msiexec.exe (PID: 6452)
The process bypasses the loading of PowerShell profile settings
- msiexec.exe (PID: 6452)
Downloads file from URI via Powershell
- powershell.exe (PID: 4400)
Starts a Microsoft application from unusual location
- MicrosoftEdgeWebview2Setup.exe (PID: 6816)
- MicrosoftEdgeUpdate.exe (PID: 4536)
Starts process via Powershell
- powershell.exe (PID: 4400)
Executable content was dropped or overwritten
- powershell.exe (PID: 4400)
- MicrosoftEdgeWebview2Setup.exe (PID: 6816)
- MicrosoftEdgeUpdate.exe (PID: 4536)
Process drops legitimate windows executable
- powershell.exe (PID: 4400)
- MicrosoftEdgeUpdate.exe (PID: 4536)
- MicrosoftEdgeWebview2Setup.exe (PID: 6816)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 4400)
Starts itself from another location
- MicrosoftEdgeUpdate.exe (PID: 4536)
Creates/Modifies COM task schedule object
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 2060)
- MicrosoftEdgeUpdate.exe (PID: 6892)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 7136)
Potential Corporate Privacy Violation
- svchost.exe (PID: 2788)
Application launched itself
- MicrosoftEdgeUpdate.exe (PID: 4684)
Reads security settings of Internet Explorer
- MicrosoftEdgeUpdate.exe (PID: 4536)
INFO
Checks supported languages
- msiexec.exe (PID: 6860)
- msiexec.exe (PID: 6452)
- MicrosoftEdgeWebview2Setup.exe (PID: 6816)
- MicrosoftEdgeUpdate.exe (PID: 6892)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 2060)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 7136)
- MicrosoftEdgeUpdate.exe (PID: 3208)
- MicrosoftEdgeUpdate.exe (PID: 4536)
- MicrosoftEdgeUpdate.exe (PID: 4684)
- MicrosoftEdgeUpdate.exe (PID: 3544)
- MicrosoftEdgeUpdate.exe (PID: 6196)
An automatically generated document
- msiexec.exe (PID: 6280)
Executable content was dropped or overwritten
- msiexec.exe (PID: 6280)
- msiexec.exe (PID: 6452)
Reads the computer name
- msiexec.exe (PID: 6860)
- msiexec.exe (PID: 6452)
- MicrosoftEdgeUpdate.exe (PID: 4536)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 2060)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 7136)
- MicrosoftEdgeUpdate.exe (PID: 4684)
- MicrosoftEdgeUpdate.exe (PID: 3544)
Manages system restore points
- SrTasks.exe (PID: 3544)
Creates a software uninstall entry
- msiexec.exe (PID: 6452)
The executable file from the user directory is run by the Powershell process
- MicrosoftEdgeWebview2Setup.exe (PID: 6816)
The process uses the downloaded file
- powershell.exe (PID: 4400)
Create files in a temporary directory
- MicrosoftEdgeWebview2Setup.exe (PID: 6816)
- svchost.exe (PID: 2788)
The sample compiled with english language support
- powershell.exe (PID: 4400)
- MicrosoftEdgeUpdate.exe (PID: 4536)
- MicrosoftEdgeWebview2Setup.exe (PID: 6816)
Reads Environment values
- MicrosoftEdgeUpdate.exe (PID: 3208)
- MicrosoftEdgeUpdate.exe (PID: 6196)
Reads the software policy settings
- MicrosoftEdgeUpdate.exe (PID: 3208)
- MicrosoftEdgeUpdate.exe (PID: 4684)
- wermgr.exe (PID: 6668)
Checks proxy server information
- MicrosoftEdgeUpdate.exe (PID: 4684)
- MicrosoftEdgeUpdate.exe (PID: 3544)
- wermgr.exe (PID: 1740)
Creates files in the program directory
- MicrosoftEdgeUpdate.exe (PID: 4536)
Process checks computer location settings
- MicrosoftEdgeUpdate.exe (PID: 6196)
Creates files or folders in the user directory
- wermgr.exe (PID: 1740)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (98.5) |
|---|---|---|
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| CodePage: | Windows Latin 1 (Western European) |
|---|---|
| Title: | Installation Database |
| Subject: | EZFN Launcher |
| Author: | ezfn |
| Keywords: | Installer |
| Comments: | This installer database contains the logic and data required to install EZFN Launcher. |
| Template: | x64;0 |
| RevisionNumber: | {8E8ADF67-611A-418A-81D9-A15A7CD2D5D7} |
| CreateDate: | 2024:11:13 21:30:16 |
| ModifyDate: | 2024:11:13 21:30:16 |
| Pages: | 450 |
| Words: | 2 |
| Software: | Windows Installer XML Toolset (3.11.2.4516) |
| Security: | Read-only recommended |
Total processes
151
Monitored processes
21
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1740 | "C:\WINDOWS\system32\wermgr.exe" "-outproc" "0" "6196" "1148" "1072" "1144" "0" "0" "0" "0" "0" "0" "0" "0" | C:\Windows\SysWOW64\wermgr.exe | MicrosoftEdgeUpdate.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2060 | "C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\1.3.195.39\MicrosoftEdgeUpdateComRegisterShell64.exe" /user | C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\1.3.195.39\MicrosoftEdgeUpdateComRegisterShell64.exe | — | MicrosoftEdgeUpdate.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Update COM Registration Helper Exit code: 0 Version: 1.3.195.39 Modules
| |||||||||||||||
| 2432 | "C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\1.3.195.39\MicrosoftEdgeUpdateComRegisterShell64.exe" /user | C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\1.3.195.39\MicrosoftEdgeUpdateComRegisterShell64.exe | — | MicrosoftEdgeUpdate.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Update COM Registration Helper Exit code: 0 Version: 1.3.195.39 Modules
| |||||||||||||||
| 2788 | C:\WINDOWS\System32\svchost.exe -k netsvcs -p -s BITS | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3208 | "C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe" /ping PD94bWwgdmVyc2lvbj0iMS4wIiBlbmNvZGluZz0iVVRGLTgiPz48cmVxdWVzdCBwcm90b2NvbD0iMy4wIiB1cGRhdGVyPSJPbWFoYSIgdXBkYXRlcnZlcnNpb249IjEuMy4xOTUuMzkiIHNoZWxsX3ZlcnNpb249IjEuMy4xOTUuMzkiIGlzbWFjaGluZT0iMCIgc2Vzc2lvbmlkPSJ7NjI0RTc3OUQtNTIzOC00NTU1LUIxN0EtNkQwRjMxQ0VEM0E0fSIgdXNlcmlkPSJ7N0UyQ0NCMDktNjVFRS00NTE1LUIzMEYtQzAxNzFGNDUyMjBDfSIgaW5zdGFsbHNvdXJjZT0ib3RoZXJpbnN0YWxsY21kIiByZXF1ZXN0aWQ9Ins5QTRERDNDQS0zMjVELTRBRjUtOEYyOS1GRDJCODZBQjVGOUZ9IiBkZWR1cD0iY3IiIGRvbWFpbmpvaW5lZD0iMCI-PGh3IGxvZ2ljYWxfY3B1cz0iNCIgcGh5c21lbW9yeT0iNCIgZGlza190eXBlPSIyIiBzc2U9IjEiIHNzZTI9IjEiIHNzZTM9IjEiIHNzc2UzPSIxIiBzc2U0MT0iMSIgc3NlNDI9IjEiIGF2eD0iMSIvPjxvcyBwbGF0Zm9ybT0id2luIiB2ZXJzaW9uPSIxMC4wLjE5MDQ1LjQwNDYiIHNwPSIiIGFyY2g9Ing2NCIgcHJvZHVjdF90eXBlPSI0OCIgaXNfd2lwPSIwIiBpc19pbl9sb2NrZG93bl9tb2RlPSIwIi8-PG9lbSBwcm9kdWN0X21hbnVmYWN0dXJlcj0iREVMTCIgcHJvZHVjdF9uYW1lPSJERUxMIi8-PGV4cCBldGFnPSIiLz48YXBwIGFwcGlkPSJ7RjNDNEZFMDAtRUZENS00MDNCLTk1NjktMzk4QTIwRjFCQTRBfSIgdmVyc2lvbj0iIiBuZXh0dmVyc2lvbj0iMS4zLjE5NS4zOSIgbGFuZz0iIiBicmFuZD0iIiBjbGllbnQ9IiI-PGV2ZW50IGV2ZW50dHlwZT0iMiIgZXZlbnRyZXN1bHQ9IjEiIGVycm9yY29kZT0iMCIgZXh0cmFjb2RlMT0iMCIgc3lzdGVtX3VwdGltZV90aWNrcz0iMTI5ODc4MDIwNTAiIGluc3RhbGxfdGltZV9tcz0iNjEwIi8-PC9hcHA-PC9yZXF1ZXN0Pg | C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe | MicrosoftEdgeUpdate.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Update Exit code: 0 Version: 1.3.195.39 Modules
| |||||||||||||||
| 3544 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3544 | "C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe" /ping PD94bWwgdmVyc2lvbj0iMS4wIiBlbmNvZGluZz0iVVRGLTgiPz48cmVxdWVzdCBwcm90b2NvbD0iMy4wIiB1cGRhdGVyPSJPbWFoYSIgdXBkYXRlcnZlcnNpb249IjEuMy4xOTUuMzkiIHNoZWxsX3ZlcnNpb249IjEuMy4xOTUuMzkiIGlzbWFjaGluZT0iMCIgc2Vzc2lvbmlkPSJ7NjI0RTc3OUQtNTIzOC00NTU1LUIxN0EtNkQwRjMxQ0VEM0E0fSIgdXNlcmlkPSJ7N0UyQ0NCMDktNjVFRS00NTE1LUIzMEYtQzAxNzFGNDUyMjBDfSIgaW5zdGFsbHNvdXJjZT0ib3RoZXJpbnN0YWxsY21kIiByZXF1ZXN0aWQ9InsxRjY0MDUxQi0wRERBLTRFNTUtOUYyOS0wQzI5MEM5M0FBM0V9IiBkZWR1cD0iY3IiIGRvbWFpbmpvaW5lZD0iMCI-PGh3IGxvZ2ljYWxfY3B1cz0iNCIgcGh5c21lbW9yeT0iNCIgZGlza190eXBlPSIyIiBzc2U9IjEiIHNzZTI9IjEiIHNzZTM9IjEiIHNzc2UzPSIxIiBzc2U0MT0iMSIgc3NlNDI9IjEiIGF2eD0iMSIvPjxvcyBwbGF0Zm9ybT0id2luIiB2ZXJzaW9uPSIxMC4wLjE5MDQ1LjQwNDYiIHNwPSIiIGFyY2g9Ing2NCIgcHJvZHVjdF90eXBlPSI0OCIgaXNfd2lwPSIwIiBpc19pbl9sb2NrZG93bl9tb2RlPSIwIi8-PG9lbSBwcm9kdWN0X21hbnVmYWN0dXJlcj0iREVMTCIgcHJvZHVjdF9uYW1lPSJERUxMIi8-PGV4cCBldGFnPSImcXVvdDtzemxOQkp1OXlEc3pmazlCUWdobWhFMmJCN00yekcvQzFCWjh5QS9rWWI0PSZxdW90OyIvPjxhcHAgYXBwaWQ9IntGMzAxNzIyNi1GRTJBLTQyOTUtOEJERi0wMEMzQTlBN0U0QzV9IiB2ZXJzaW9uPSIiIG5leHR2ZXJzaW9uPSIxMzEuMC4yOTAzLjk5IiBsYW5nPSIiIGJyYW5kPSIiIGNsaWVudD0iIiBleHBlcmltZW50cz0iY29uc2VudD1mYWxzZSIgaW5zdGFsbGFnZT0iLTEiIGluc3RhbGxkYXRlPSItMSI-PHVwZGF0ZWNoZWNrLz48ZXZlbnQgZXZlbnR0eXBlPSI5IiBldmVudHJlc3VsdD0iMSIgZXJyb3Jjb2RlPSIwIiBleHRyYWNvZGUxPSIwIiBzeXN0ZW1fdXB0aW1lX3RpY2tzPSIxMjk5NjM5NzM4OCIgZG9uZV9iZWZvcmVfb29iZV9jb21wbGV0ZT0iMCIvPjxldmVudCBldmVudHR5cGU9IjUiIGV2ZW50cmVzdWx0PSIxIiBlcnJvcmNvZGU9IjAiIGV4dHJhY29kZTE9IjAiIHN5c3RlbV91cHRpbWVfdGlja3M9IjEyOTk2NTUzODQ5IiBkb25lX2JlZm9yZV9vb2JlX2NvbXBsZXRlPSIwIi8-PGV2ZW50IGV2ZW50dHlwZT0iMiIgZXZlbnRyZXN1bHQ9IjQiIGVycm9yY29kZT0iLTIxNDcyMTk0NDAiIGV4dHJhY29kZTE9IjI2ODQzNTQ2MyIgc3lzdGVtX3VwdGltZV90aWNrcz0iMTQ0NzM5NDQyODMiIGlzX2J1bmRsZWQ9IjAiIHN0YXRlX2NhbmNlbGxlZD0iNyIgdGltZV9zaW5jZV91cGRhdGVfYXZhaWxhYmxlX21zPSIxNDc3NTUiIHRpbWVfc2luY2VfZG93bmxvYWRfc3RhcnRfbXM9IjE0NzczOSIvPjxldmVudCBldmVudHR5cGU9IjEiIGV2ZW50cmVzdWx0PSIwIiBlcnJvcmNvZGU9Ii0yMTQ3MjE5NDQwIiBleHRyYWNvZGUxPSIwIiBzeXN0ZW1fdXB0aW1lX3RpY2tzPSIxNDQ3NDEwMDUwNCIgc291cmNlX3VybF9pbmRleD0iMCIgZG9uZV9iZWZvcmVfb29iZV9jb21wbGV0ZT0iMCIgZG93bmxvYWRlcj0iYml0cyIgdXJsPSJodHRwOi8vbXNlZGdlLmYudGx1LmRsLmRlbGl2ZXJ5Lm1wLm1pY3Jvc29mdC5jb20vZmlsZXN0cmVhbWluZ3NlcnZpY2UvZmlsZXMvMGY2YTZkZDMtMGIyMi00ZTc4LWIwNGYtNjA0OTRlYjRjNGU4P1AxPTE3MzQ3MjA4NDUmYW1wO1AyPTQwNCZhbXA7UDM9MiZhbXA7UDQ9Y2xEYmZ2V0ZicGNPbEdZeiUyYllpTSUyZiUyZjlkQWFpR29NT1VUS2szYSUyYiUyYjV3TEF0Umt4VDFGRHFPVmQ2bVQyTlVNakVJaURMS0N5TVhDZzBYaWFqY1VRU1hRJTNkJTNkIiBzZXJ2ZXJfaXBfaGludD0iIiBjZG5fY2lkPSItMSIgY2RuX2NjYz0iIiBjZG5fbXNlZGdlX3JlZj0iIiBjZG5fYXp1cmVfcmVmX29yaWdpbl9zaGllbGQ9IiIgY2RuX2NhY2hlPSIiIGNkbl9wM3A9IiIgZG93bmxvYWRlZD0iNTYzNzY4MTAiIHRvdGFsPSIxNzY4NTU2NDgiIGRvd25sb2FkX3RpbWVfbXM9IjE0NzI0MCIvPjwvYXBwPjwvcmVxdWVzdD4 | C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe | MicrosoftEdgeUpdate.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Update Exit code: 0 Version: 1.3.195.39 Modules
| |||||||||||||||
| 4400 | powershell.exe -NoProfile -windowstyle hidden try { [Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12 } catch {}; Invoke-WebRequest -Uri "https://go.microsoft.com/fwlink/p/?LinkId=2124703" -OutFile "$env:TEMP\MicrosoftEdgeWebview2Setup.exe" ; Start-Process -FilePath "$env:TEMP\MicrosoftEdgeWebview2Setup.exe" -ArgumentList ( '/install') -Wait | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4444 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4536 | C:\Users\admin\AppData\Local\Temp\EUC95E.tmp\MicrosoftEdgeUpdate.exe /install "appguid={F3017226-FE2A-4295-8BDF-00C3A9A7E4C5}&appname=Microsoft%20Edge%20Webview2%20Runtime&needsadmin=prefers" | C:\Users\admin\AppData\Local\Temp\EUC95E.tmp\MicrosoftEdgeUpdate.exe | MicrosoftEdgeWebview2Setup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Update Exit code: 2147747856 Version: 1.3.195.39 Modules
| |||||||||||||||
Total events
22 180
Read events
17 697
Write events
4 431
Delete events
52
Modification events
| (PID) Process: | (6452) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 480000000000000062A92352904DDB0134190000F41A0000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6452) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 480000000000000062A92352904DDB0134190000F41A0000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6452) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 48000000000000008BB3E551904DDB0134190000F41A0000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6452) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 48000000000000008BB3E551904DDB0134190000F41A0000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6452) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 11 | |||
| (PID) Process: | (6452) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000F366A452904DDB0134190000681B0000E8030000010000000000000000000000DF89B4401218394CB8C4BF92EE32A8A900000000000000000000000000000000 | |||
| (PID) Process: | (6912) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 480000000000000088D4B952904DDB01001B0000201B0000E80300000000000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6452) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 4800000000000000C80D2652904DDB0134190000F41A0000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6452) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 480000000000000064382D52904DDB0134190000F41A0000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6452) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 4800000000000000C19F9F52904DDB0134190000F41A0000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
204
Suspicious files
30
Text files
24
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6452 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 6452 | msiexec.exe | C:\Windows\Installer\13aa5c.msi | — | |
MD5:— | SHA256:— | |||
| 6452 | msiexec.exe | C:\Program Files\EZFN Launcher\EZFN Launcher.exe | executable | |
MD5:31E71C821BD9EE93C135711542481840 | SHA256:49BF997C7C1B051828AC8F30467EB0E5E12FEE50CEBE34C9B2F8C938A2A6481D | |||
| 6452 | msiexec.exe | C:\Windows\Installer\MSIAF00.tmp | binary | |
MD5:E92D236D323427C411E593B827E7840D | SHA256:AE7A94D2336B4579AA69843887E0D1C508FC71C331DBBD064C24F700D4AD10FE | |||
| 6452 | msiexec.exe | C:\Program Files\EZFN Launcher\_up_\public\season_images\Season7.webp | image | |
MD5:B112139E396EE16AC6F8D7F5DC5D10F7 | SHA256:1E51EBB0C98EE8CC6A194DC5B08C940573C65BDE2B580E88C0449658C49267F1 | |||
| 6452 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{40b489df-1812-4c39-b8c4-bf92ee32a8a9}_OnDiskSnapshotProp | binary | |
MD5:54ED2EF0B188F6A7015D6F12CDF638C1 | SHA256:548BD9360EB1768682E4F7871E4935B71B4A111293D749E15E8BE52B98DEE2CA | |||
| 6452 | msiexec.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:54ED2EF0B188F6A7015D6F12CDF638C1 | SHA256:548BD9360EB1768682E4F7871E4935B71B4A111293D749E15E8BE52B98DEE2CA | |||
| 6452 | msiexec.exe | C:\Program Files\EZFN Launcher\_up_\public\season_images\Season9.webp | image | |
MD5:1FC5AFAD336EBAF0D613D556FD6DE9BC | SHA256:0D216CCC8196B2BDB8C2633257EEF40F80918459190B98BE069A9737C246CC84 | |||
| 6452 | msiexec.exe | C:\Program Files\EZFN Launcher\_up_\public\certs\placeholder.txt | text | |
MD5:81A3276E378F08CF4E7F9FA0B01008BB | SHA256:875E537B2012BB4A7F462C01A7D35AA8BCEE456DC46E139C5187A8DCEB6B0571 | |||
| 6452 | msiexec.exe | C:\Program Files\EZFN Launcher\_up_\public\season_images\Season2.webp | image | |
MD5:265393414B5BC850A63E3856D3158FD6 | SHA256:CAF02B9121C474E6422A2FA674DF79BA1F35F60BD516A015D689CD01FDD80579 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
46
DNS requests
28
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2788 | svchost.exe | GET | — | 217.20.57.20:80 | http://msedge.f.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/0f6a6dd3-0b22-4e78-b04f-60494eb4c4e8?P1=1734720845&P2=404&P3=2&P4=clDbfvWFbpcOlGYz%2bYiM%2f%2f9dAaiGoMOUTKk3a%2b%2b5wLAtRkxT1FDqOVd6mT2NUMjEIiDLKCyMXCg0XiajcUQSXQ%3d%3d | unknown | — | — | whitelisted |
1740 | wermgr.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1740 | wermgr.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3688 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5208 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
2788 | svchost.exe | HEAD | 200 | 217.20.57.20:80 | http://msedge.f.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/0f6a6dd3-0b22-4e78-b04f-60494eb4c4e8?P1=1734720845&P2=404&P3=2&P4=clDbfvWFbpcOlGYz%2bYiM%2f%2f9dAaiGoMOUTKk3a%2b%2b5wLAtRkxT1FDqOVd6mT2NUMjEIiDLKCyMXCg0XiajcUQSXQ%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2356 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5064 | SearchApp.exe | 2.23.209.189:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
— | — | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2788 | svchost.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |