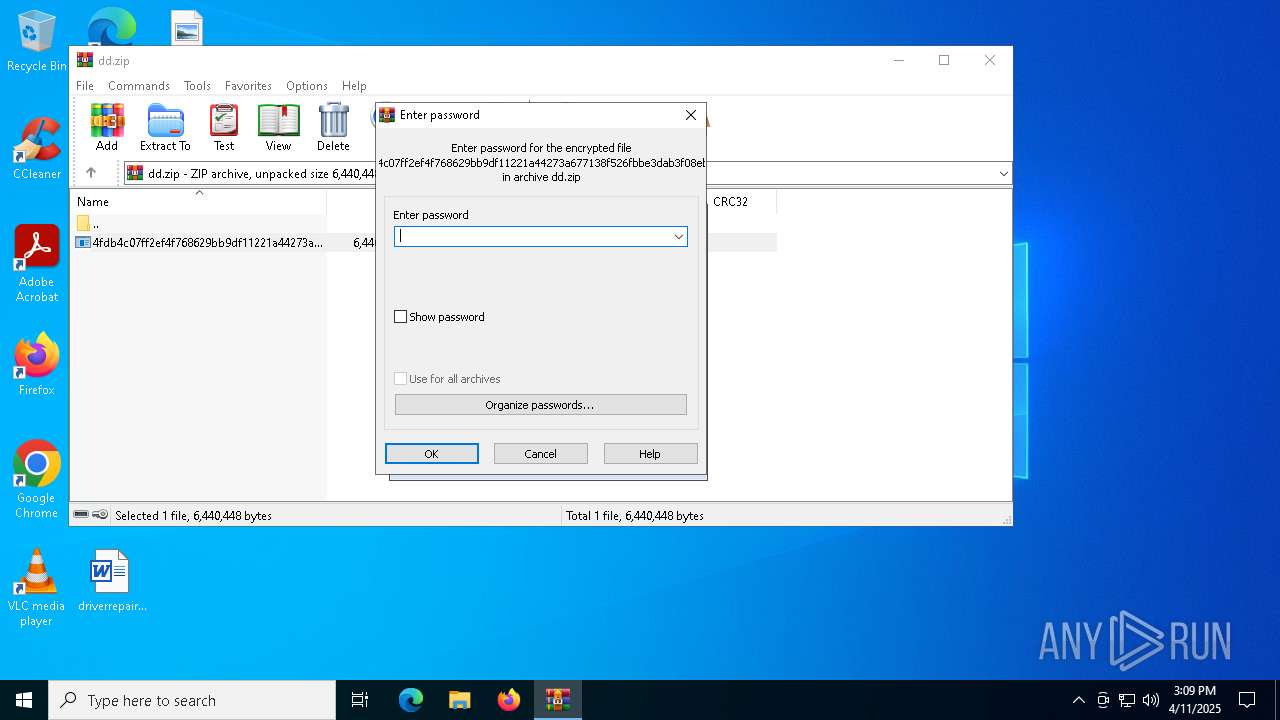
| File name: | dd.zip |
| Full analysis: | https://app.any.run/tasks/d556aacd-58f3-4743-9822-ef43ea419bd6 |
| Verdict: | Malicious activity |
| Analysis date: | April 11, 2025, 15:09:35 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | 38203E68D802AB52712972F1ED748CB6 |
| SHA1: | B06CF798C52099AD0DD1F43C811CD3E841939193 |
| SHA256: | B24250032DC9F8830411638795357DFAB65AEBCF675EB7FC0DEF058FCF76F0B6 |
| SSDEEP: | 98304:1Kmq016UZZuEKsdfP/pL83QEoSx1bvKyHJzsPwvkEvJAb4rjrg6EaU/UH3mcSTG3:2XSG |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 5256)
Adds path to the Windows Defender exclusion list
- alma.exe (PID: 856)
- alma.exe (PID: 4944)
Changes Windows Defender settings
- alma.exe (PID: 4944)
- alma.exe (PID: 856)
XORed URL has been found (YARA)
- alma.exe (PID: 4944)
- alma.exe (PID: 856)
SUSPICIOUS
Reads security settings of Internet Explorer
- alma.exe (PID: 680)
- alma.exe (PID: 3008)
- alma.exe (PID: 856)
- alma.exe (PID: 4944)
Application launched itself
- alma.exe (PID: 680)
- alma.exe (PID: 3008)
Script adds exclusion path to Windows Defender
- alma.exe (PID: 856)
- alma.exe (PID: 4944)
Likely accesses (executes) a file from the Public directory
- powershell.exe (PID: 5936)
- powershell.exe (PID: 5640)
- cmd.exe (PID: 2320)
- cmd.exe (PID: 5596)
Starts POWERSHELL.EXE for commands execution
- alma.exe (PID: 856)
- alma.exe (PID: 4944)
There is functionality for taking screenshot (YARA)
- alma.exe (PID: 856)
- alma.exe (PID: 4944)
Starts CMD.EXE for commands execution
- alma.exe (PID: 856)
Lists all scheduled tasks
- schtasks.exe (PID: 8028)
- schtasks.exe (PID: 7484)
- schtasks.exe (PID: 7852)
- schtasks.exe (PID: 7540)
- schtasks.exe (PID: 8108)
- schtasks.exe (PID: 7864)
- schtasks.exe (PID: 7484)
- schtasks.exe (PID: 7948)
- schtasks.exe (PID: 3968)
- schtasks.exe (PID: 8748)
- schtasks.exe (PID: 7864)
- schtasks.exe (PID: 8076)
- schtasks.exe (PID: 6392)
- schtasks.exe (PID: 8348)
- schtasks.exe (PID: 8572)
- schtasks.exe (PID: 8984)
- schtasks.exe (PID: 8404)
- schtasks.exe (PID: 9144)
- schtasks.exe (PID: 8620)
- schtasks.exe (PID: 9168)
- schtasks.exe (PID: 9028)
- schtasks.exe (PID: 8684)
- schtasks.exe (PID: 8240)
- schtasks.exe (PID: 8888)
- schtasks.exe (PID: 4172)
- schtasks.exe (PID: 8064)
- schtasks.exe (PID: 9564)
- schtasks.exe (PID: 9400)
- schtasks.exe (PID: 9812)
- schtasks.exe (PID: 9972)
- schtasks.exe (PID: 9220)
- schtasks.exe (PID: 8460)
- schtasks.exe (PID: 8984)
- schtasks.exe (PID: 8460)
- schtasks.exe (PID: 10104)
- schtasks.exe (PID: 9388)
- schtasks.exe (PID: 10044)
- schtasks.exe (PID: 9448)
- schtasks.exe (PID: 9440)
- schtasks.exe (PID: 9852)
- schtasks.exe (PID: 9836)
- schtasks.exe (PID: 10636)
- schtasks.exe (PID: 9880)
- schtasks.exe (PID: 9848)
- schtasks.exe (PID: 10376)
- schtasks.exe (PID: 10172)
- schtasks.exe (PID: 11032)
- schtasks.exe (PID: 10632)
- schtasks.exe (PID: 10776)
- schtasks.exe (PID: 11176)
- schtasks.exe (PID: 10408)
- schtasks.exe (PID: 11048)
- schtasks.exe (PID: 10712)
- schtasks.exe (PID: 11112)
- schtasks.exe (PID: 11288)
- schtasks.exe (PID: 3796)
- schtasks.exe (PID: 3800)
- schtasks.exe (PID: 3016)
- schtasks.exe (PID: 11436)
- schtasks.exe (PID: 11536)
- schtasks.exe (PID: 12240)
- schtasks.exe (PID: 11680)
- schtasks.exe (PID: 11840)
- schtasks.exe (PID: 12088)
- schtasks.exe (PID: 11004)
- schtasks.exe (PID: 11220)
- schtasks.exe (PID: 10696)
- schtasks.exe (PID: 10748)
- schtasks.exe (PID: 11912)
- schtasks.exe (PID: 11316)
- schtasks.exe (PID: 11444)
- schtasks.exe (PID: 11656)
- schtasks.exe (PID: 11624)
- schtasks.exe (PID: 13096)
- schtasks.exe (PID: 12456)
- schtasks.exe (PID: 12696)
- schtasks.exe (PID: 12856)
- schtasks.exe (PID: 12552)
- schtasks.exe (PID: 13256)
- schtasks.exe (PID: 12776)
- schtasks.exe (PID: 13144)
- schtasks.exe (PID: 6068)
- schtasks.exe (PID: 11792)
- schtasks.exe (PID: 12156)
- schtasks.exe (PID: 11328)
- schtasks.exe (PID: 11928)
- schtasks.exe (PID: 12304)
- schtasks.exe (PID: 12320)
- schtasks.exe (PID: 13152)
- schtasks.exe (PID: 12808)
- schtasks.exe (PID: 12464)
- schtasks.exe (PID: 13540)
- schtasks.exe (PID: 13700)
- schtasks.exe (PID: 13944)
- schtasks.exe (PID: 14104)
- schtasks.exe (PID: 13100)
- schtasks.exe (PID: 13600)
- schtasks.exe (PID: 13852)
- schtasks.exe (PID: 14056)
- schtasks.exe (PID: 13464)
- schtasks.exe (PID: 13828)
- schtasks.exe (PID: 12856)
- schtasks.exe (PID: 12476)
- schtasks.exe (PID: 13916)
- schtasks.exe (PID: 5352)
- schtasks.exe (PID: 4244)
- schtasks.exe (PID: 6404)
- schtasks.exe (PID: 1132)
- schtasks.exe (PID: 7384)
- schtasks.exe (PID: 7584)
- schtasks.exe (PID: 4188)
- schtasks.exe (PID: 12464)
- schtasks.exe (PID: 7664)
- schtasks.exe (PID: 4892)
- schtasks.exe (PID: 6828)
- schtasks.exe (PID: 2516)
- schtasks.exe (PID: 14328)
- schtasks.exe (PID: 13492)
- schtasks.exe (PID: 14116)
- schtasks.exe (PID: 684)
- schtasks.exe (PID: 3332)
- schtasks.exe (PID: 4892)
- schtasks.exe (PID: 7228)
- schtasks.exe (PID: 7644)
- schtasks.exe (PID: 7308)
- schtasks.exe (PID: 7528)
- schtasks.exe (PID: 8108)
- schtasks.exe (PID: 5036)
- schtasks.exe (PID: 8280)
- schtasks.exe (PID: 7356)
- schtasks.exe (PID: 7900)
- schtasks.exe (PID: 8452)
- schtasks.exe (PID: 7884)
- schtasks.exe (PID: 8296)
- schtasks.exe (PID: 8752)
- schtasks.exe (PID: 4244)
Executable content was dropped or overwritten
- alma.exe (PID: 856)
INFO
Checks proxy server information
- alma.exe (PID: 680)
- alma.exe (PID: 3008)
- alma.exe (PID: 856)
- alma.exe (PID: 4944)
The sample compiled with chinese language support
- WinRAR.exe (PID: 5256)
- alma.exe (PID: 856)
Manual execution by a user
- alma.exe (PID: 680)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5256)
Checks supported languages
- alma.exe (PID: 680)
- alma.exe (PID: 856)
- alma.exe (PID: 3008)
- alma.exe (PID: 4944)
Reads the computer name
- alma.exe (PID: 680)
- alma.exe (PID: 3008)
- alma.exe (PID: 856)
- alma.exe (PID: 4944)
Reads the machine GUID from the registry
- alma.exe (PID: 680)
- alma.exe (PID: 3008)
- alma.exe (PID: 856)
- alma.exe (PID: 4944)
Creates files or folders in the user directory
- alma.exe (PID: 680)
- alma.exe (PID: 3008)
- alma.exe (PID: 856)
- alma.exe (PID: 4944)
Reads the software policy settings
- alma.exe (PID: 680)
- alma.exe (PID: 856)
- alma.exe (PID: 3008)
- alma.exe (PID: 4944)
- slui.exe (PID: 5244)
Process checks computer location settings
- alma.exe (PID: 680)
- alma.exe (PID: 3008)
Creates a new folder
- cmd.exe (PID: 2320)
- cmd.exe (PID: 5596)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 5640)
- powershell.exe (PID: 5936)
- powershell.exe (PID: 5260)
- powershell.exe (PID: 6300)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 5640)
- powershell.exe (PID: 5936)
- powershell.exe (PID: 6300)
- powershell.exe (PID: 5260)
Creates files in the program directory
- alma.exe (PID: 4944)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
xor-url
(PID) Process(856) alma.exe
Decrypted-URLs (16)http://crl.microsoft.com/pki/crl/products/MicrosoftCodeVerifRoot.crl0
http://crl.verisign.com/pca3-g5.crl04
http://csc3-2010-aia.verisign.com/CSC3-2010.cer0
http://csc3-2010-crl.verisign.com/CSC3-2010.crl0D
http://logo.verisign.com/vslogo.gif04
http://ocsp.verisign.com0
http://ptlogin2.qun.qq.com
http://qun.qq.com
https://fs-im-kefu.7moor-fs1.com/ly/4d2c3f00-7d4c-11e5-af15-41bf63ae4ea0/1728896464326/4.txt
https://fs-im-kefu.7moor-fs1.com/ly/4d2c3f00-7d4c-11e5-af15-41bf63ae4ea0/1741001373486/7.txt
https://fs-im-kefu.7moor-fs1.com/ly/4d2c3f00-7d4c-11e5-af15-41bf63ae4ea0/1744359904544/3.txt
https://ssl.ptlogin2.qq.com
https://www.verisign.com/cps0*
https://www.verisign.com/rpa
https://www.verisign.com/rpa0
https://xui.ptlogin2.qq.com/cgi-bin/xlogin?appid=715030901&daid=73&hide_close_icon=1&pt_no_auth=1&s_url=http%3A%2F%2Fqun.qq.com%2Fmember.html%23
(PID) Process(4944) alma.exe
Decrypted-URLs (1)http://schemas.microsoft.com/SMI/2005/WindowsSettings
Decrypted-URLs (16)http://crl.microsoft.com/pki/crl/products/MicrosoftCodeVerifRoot.crl0
http://crl.verisign.com/pca3-g5.crl04
http://csc3-2010-aia.verisign.com/CSC3-2010.cer0
http://csc3-2010-crl.verisign.com/CSC3-2010.crl0D
http://logo.verisign.com/vslogo.gif04
http://ocsp.verisign.com0
http://ptlogin2.qun.qq.com
http://qun.qq.com
https://fs-im-kefu.7moor-fs1.com/ly/4d2c3f00-7d4c-11e5-af15-41bf63ae4ea0/1728896464326/4.txt
https://fs-im-kefu.7moor-fs1.com/ly/4d2c3f00-7d4c-11e5-af15-41bf63ae4ea0/1741001373486/7.txt
https://fs-im-kefu.7moor-fs1.com/ly/4d2c3f00-7d4c-11e5-af15-41bf63ae4ea0/1744359904544/3.txt
https://ssl.ptlogin2.qq.com
https://www.verisign.com/cps0*
https://www.verisign.com/rpa
https://www.verisign.com/rpa0
https://xui.ptlogin2.qq.com/cgi-bin/xlogin?appid=715030901&daid=73&hide_close_icon=1&pt_no_auth=1&s_url=http%3A%2F%2Fqun.qq.com%2Fmember.html%23
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0003 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2025:04:11 15:09:00 |
| ZipCRC: | 0xc69d6d21 |
| ZipCompressedSize: | 2176305 |
| ZipUncompressedSize: | 6440448 |
| ZipFileName: | 4fdb4c07ff2ef4f768629bb9df11221a44273a677138f526fbbe3dab3f08ebba.exe |
Total processes
423
Monitored processes
293
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 472 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 472 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | schtasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | schtasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 664 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | schtasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 680 | "C:\Users\admin\Desktop\alma.exe" | C:\Users\admin\Desktop\alma.exe | explorer.exe | ||||||||||||
User: admin Company: TODO: <公司名> Integrity Level: MEDIUM Description: ZZZZ Exit code: 0 Version: 1.0.0.1 Modules
| |||||||||||||||
| 684 | schtasks /Query /TN MM | C:\Windows\SysWOW64\schtasks.exe | — | alma.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 856 | "C:\Users\admin\Desktop\alma.exe" | C:\Users\admin\Desktop\alma.exe | alma.exe | ||||||||||||
User: admin Company: TODO: <公司名> Integrity Level: HIGH Description: ZZZZ Version: 1.0.0.1 Modules
xor-url(PID) Process(856) alma.exe Decrypted-URLs (16)http://crl.microsoft.com/pki/crl/products/MicrosoftCodeVerifRoot.crl0 http://crl.verisign.com/pca3-g5.crl04 http://csc3-2010-aia.verisign.com/CSC3-2010.cer0 http://csc3-2010-crl.verisign.com/CSC3-2010.crl0D http://logo.verisign.com/vslogo.gif04 http://ocsp.verisign.com0 http://ptlogin2.qun.qq.com http://qun.qq.com https://fs-im-kefu.7moor-fs1.com/ly/4d2c3f00-7d4c-11e5-af15-41bf63ae4ea0/1728896464326/4.txt https://fs-im-kefu.7moor-fs1.com/ly/4d2c3f00-7d4c-11e5-af15-41bf63ae4ea0/1741001373486/7.txt https://fs-im-kefu.7moor-fs1.com/ly/4d2c3f00-7d4c-11e5-af15-41bf63ae4ea0/1744359904544/3.txt https://ssl.ptlogin2.qq.com https://www.verisign.com/cps0* https://www.verisign.com/rpa https://www.verisign.com/rpa0 https://xui.ptlogin2.qq.com/cgi-bin/xlogin?appid=715030901&daid=73&hide_close_icon=1&pt_no_auth=1&s_url=http%3A%2F%2Fqun.qq.com%2Fmember.html%23 | |||||||||||||||
| 1132 | schtasks /Query /TN MM | C:\Windows\SysWOW64\schtasks.exe | — | alma.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1240 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1272 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | schtasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
29 805
Read events
29 773
Write events
32
Delete events
0
Modification events
| (PID) Process: | (5256) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5256) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5256) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5256) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\dd.zip | |||
| (PID) Process: | (5256) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5256) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5256) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5256) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5256) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (5256) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
Executable files
3
Suspicious files
19
Text files
16
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5256 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb5256.566\4fdb4c07ff2ef4f768629bb9df11221a44273a677138f526fbbe3dab3f08ebba.exe | executable | |
MD5:C5CD3F4F064C0E9729CDED6A3037EBF3 | SHA256:4FDB4C07FF2EF4F768629BB9DF11221A44273A677138F526FBBE3DAB3F08EBBA | |||
| 680 | alma.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\07CEF2F654E3ED6050FFC9B6EB844250_F2E1DEACCFEC1F5F7BA6427BFFFD4385 | binary | |
MD5:C87B17DCF59AD732DC88CA2C3741BF9B | SHA256:02CB46881EDB245310F2EA0C357C3818D242C69A9663762C1E0F9C316E7B0765 | |||
| 680 | alma.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B2FAF7692FD9FFBD64EDE317E42334BA_D7393C8F62BDE4D4CB606228BC7A711E | binary | |
MD5:6FAE12D47B9EA133082099784E433E30 | SHA256:A78F5357DC3DAF7AC367081EC9A01C1737D00C199541CDF83F90C72138CF8437 | |||
| 680 | alma.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\2B12220AECB8D51406052488C95A6C3C_1AA83278792580608C828A90FFEB9420 | binary | |
MD5:9F04E345396DEEB6EA18930701AEDAEB | SHA256:650C57587C9A266E871AEE16F8BF77DB07F74265FC2843715C8EDD59B36BB8D1 | |||
| 5640 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_23f3pbq2.ua0.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5936 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_vpth5lue.l4v.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5936 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_o2vyflii.v2q.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5640 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_z2kxqroe.ezi.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 680 | alma.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B2FAF7692FD9FFBD64EDE317E42334BA_D7393C8F62BDE4D4CB606228BC7A711E | binary | |
MD5:6EC34697B5E535625F4287F4AB99F0BC | SHA256:E8E0345E65F69786EA3D8A11A1AF4A8F02AF567A0B6953CFAE578636764C1081 | |||
| 680 | alma.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\2B12220AECB8D51406052488C95A6C3C_1AA83278792580608C828A90FFEB9420 | binary | |
MD5:74A54C6EE7FFAE21BF5BEBF8A748F1CE | SHA256:FD8CCA25BA45BA45D6413E2508F6B33A1F25EBEAE87D43E516122813BB898DE9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
31
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.216.77.18:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.18:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
680 | alma.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | unknown | — | — | whitelisted |
680 | alma.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.trust-provider.cn/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQIzuhSh8YGNy3SuMUAiCzbrW1YlAQUQDAii40qMin4ECENAGNeRdMs4CUCEHjR9DRRVqEwZIfnrWPIx%2Bw%3D | unknown | — | — | malicious |
1132 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1132 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
680 | alma.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.usertrust.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEQCZ8KttybEufwX%2F1yKE0dH%2F | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.216.77.18:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.18:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.159.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
2112 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
fs-im-kefu.7moor-fs1.com |
| unknown |
ocsp.comodoca.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
ocsp.trust-provider.cn |
| malicious |