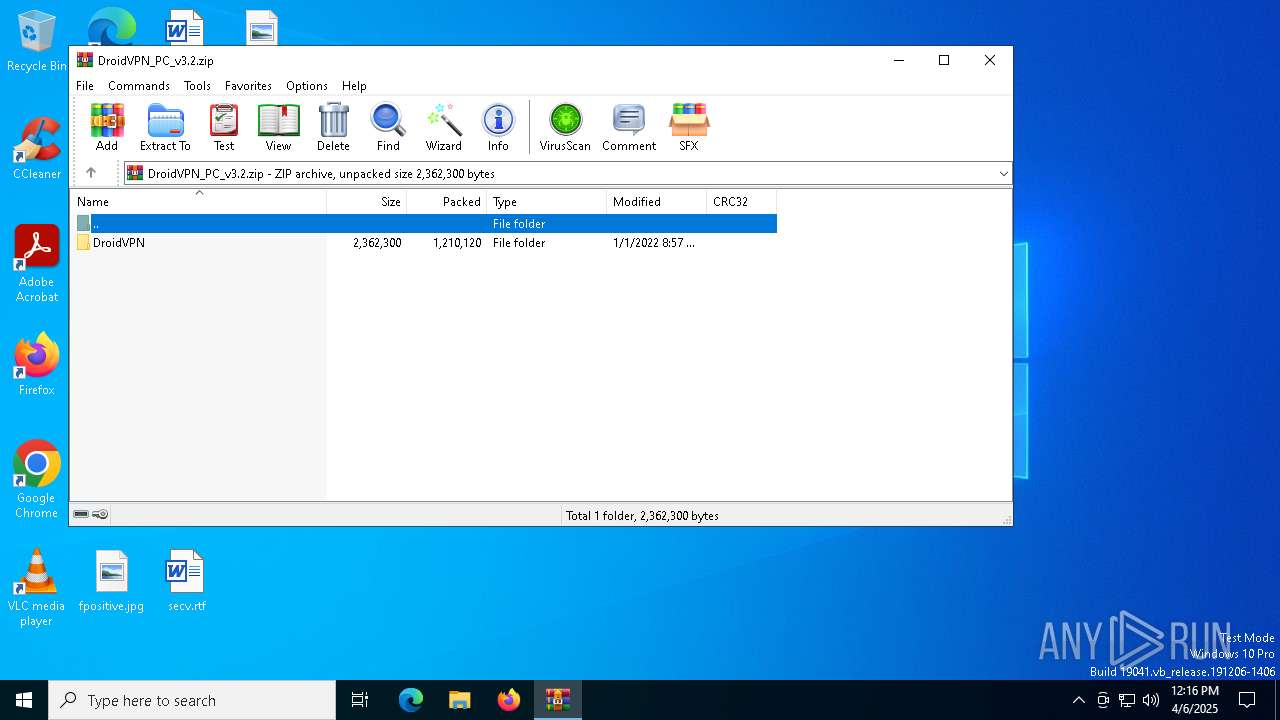
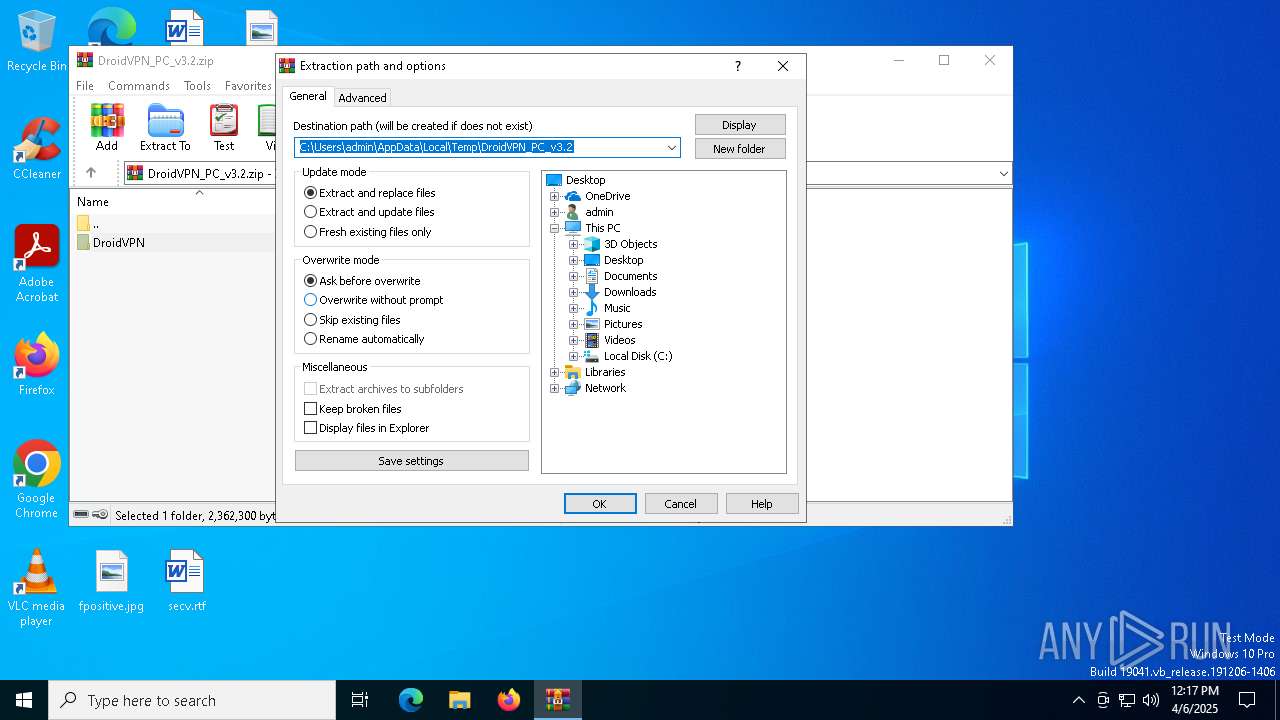
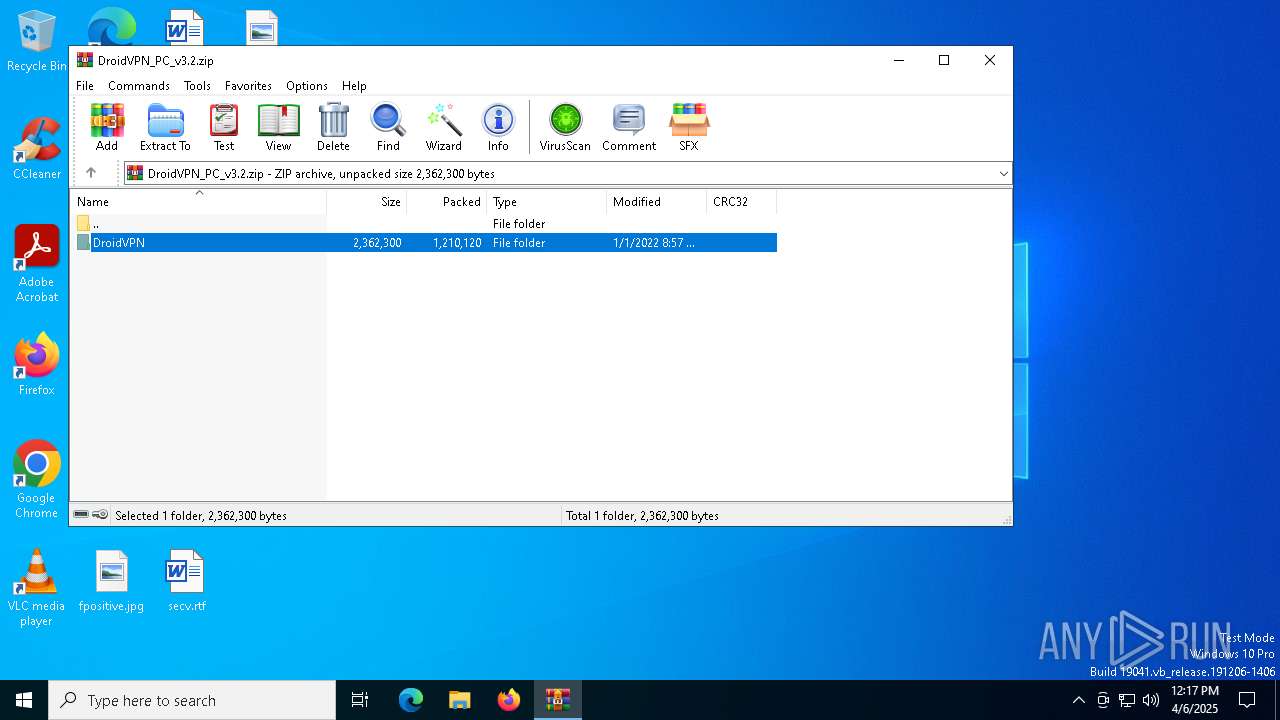
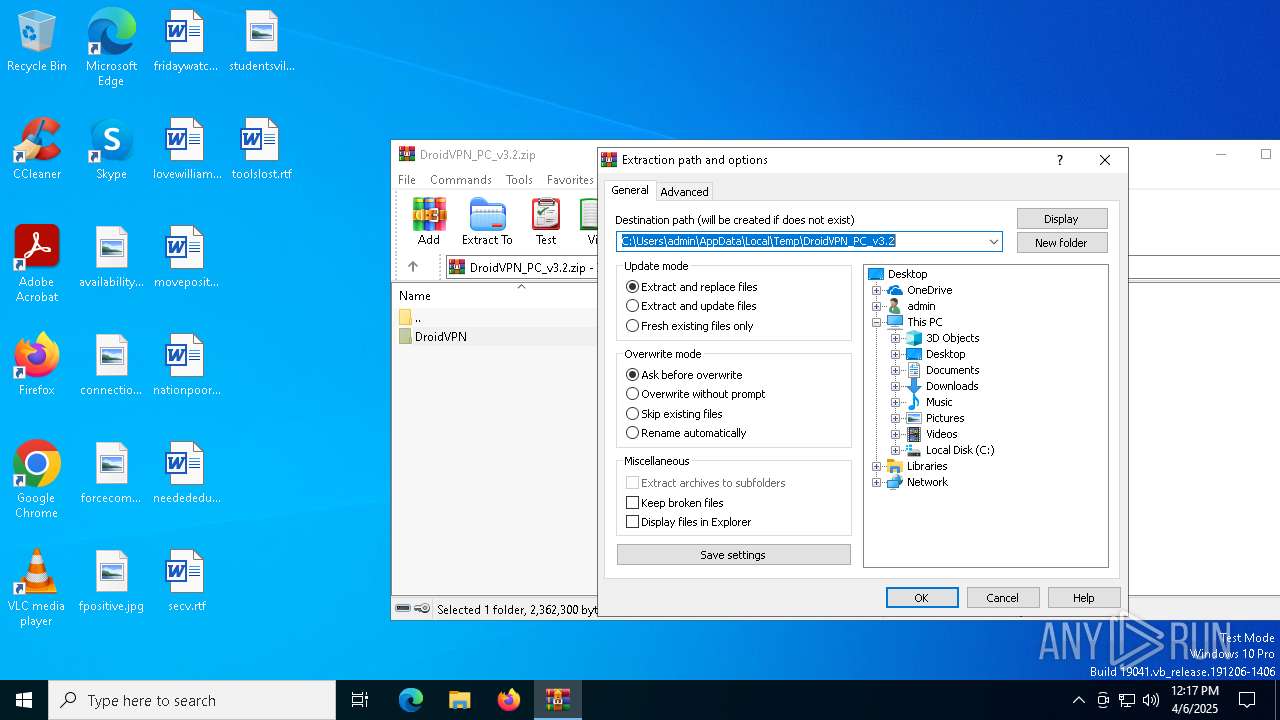
| download: | /DroidVPN-Official/DroidVPN/releases/download/3.0.5.3/DroidVPN_PC_v3.2.zip |
| Full analysis: | https://app.any.run/tasks/985411e7-7c48-4a90-b6e3-7e47a503a551 |
| Verdict: | Malicious activity |
| Analysis date: | April 06, 2025, 12:16:32 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 2B39B731FFEF0527F021D23557DFF770 |
| SHA1: | 0CEA5A54C600F48DBCB2999CD57294BDB5F88167 |
| SHA256: | B240475F1B3498D812293C241FFF35438474688385C228A3DF28655AA8B57F14 |
| SSDEEP: | 49152:Oz8JTlZ8iLSxGng7Z5GPKr3vMNCT7RNtV9z9DYIVrlCDYIyocJ4UoSC5jDYID5Dw:cuX8iLSN5GKvdTVNt/Nnrly4iUoSC538 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Creates file in the systems drive root
- WinRAR.exe (PID: 4300)
Drops a system driver (possible attempt to evade defenses)
- WinRAR.exe (PID: 4300)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 4300)
Process drops legitimate windows executable
- WinRAR.exe (PID: 4300)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 4300)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4300)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xpi | | | Mozilla Firefox browser extension (66.6) |
|---|---|---|
| .zip | | | ZIP compressed archive (33.3) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2022:01:01 16:57:10 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | DroidVPN/ |
Total processes
130
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4300 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\DroidVPN_PC_v3.2.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 7236 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7268 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 231
Read events
3 207
Write events
11
Delete events
13
Modification events
| (PID) Process: | (4300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\DroidVPN_PC_v3.2.zip | |||
| (PID) Process: | (4300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
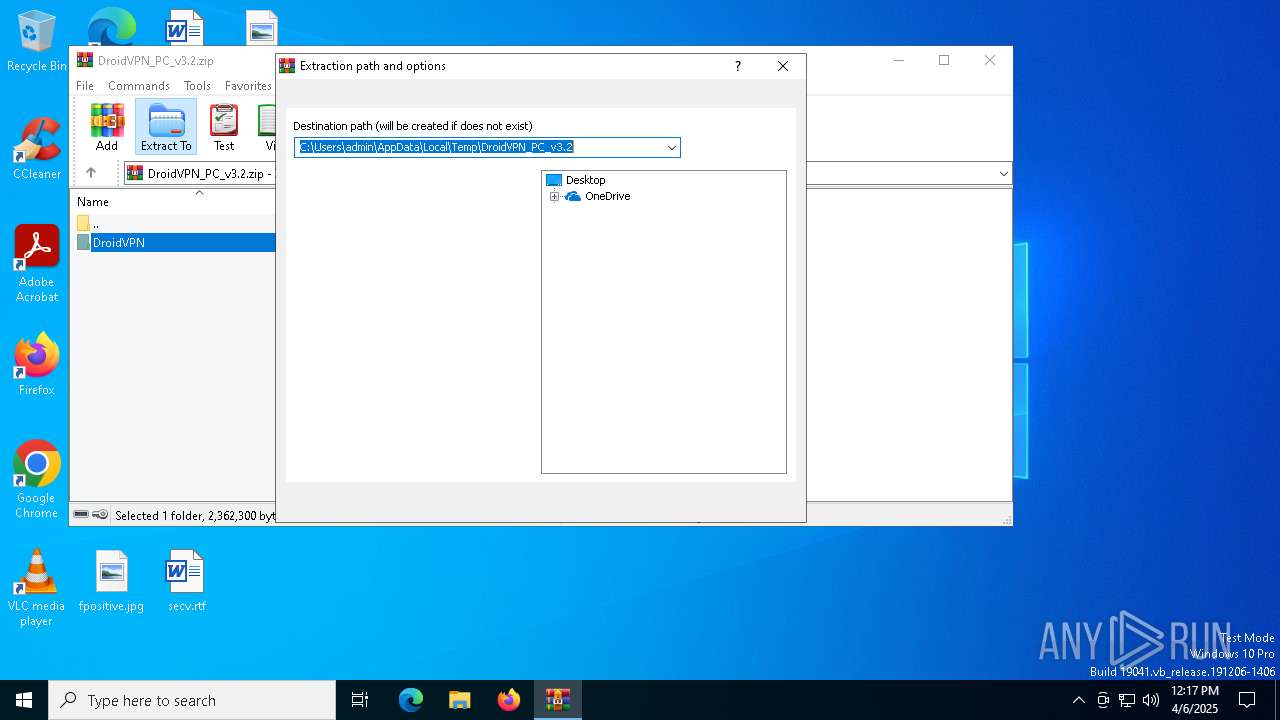
| (PID) Process: | (4300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (4300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
Executable files
18
Suspicious files
10
Text files
12
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4300 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\DroidVPN_PC_v3.2\DroidVPN\driver\x86\tap0901.sys | executable | |
MD5:11D34FC869F5BDA29949FE3858380894 | SHA256:07147942CEE61570653D617B42C90ABCABF55C690A162E2B3C89EF6BD4C32E89 | |||
| 4300 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\DroidVPN_PC_v3.2\DroidVPN\driver\x86\tap0901.cat | binary | |
MD5:CBC64A0DB899A217546CAD0B7AAE63E7 | SHA256:F74EE1DB54D3AF3FE6495AAAFED42D2A0CF77E1B3993B00BF301A51D6943A2FC | |||
| 4300 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\DroidVPN_PC_v3.2\DroidVPN\driver\x86\tapinstall.exe | executable | |
MD5:D1B6303856C0BD48190CB0B4B1FA7F5F | SHA256:AFBBC11B086CCD0B23FA4B9B60718690B99544AF94931E5AFB05A8266190C6F1 | |||
| 4300 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\DroidVPN_PC_v3.2\DroidVPN\droidvpn.conf | text | |
MD5:18D9214DE7342F3B256CC8465AACBB60 | SHA256:681B9FD164EAFF083ECE59BBFA413203D7F607246CB79AC71FD2D1007483E9AE | |||
| 4300 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\DroidVPN_PC_v3.2\DroidVPN\DroidVPN.exe | executable | |
MD5:FDCB0F507F402053A86150DB123B0FFD | SHA256:A89178129E5FDEF2BC5E6900FCAA8A47C6311C7201B26B59DB4A0374564760BA | |||
| 4300 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\DroidVPN_PC_v3.2\DroidVPN\droidvpn.dll | executable | |
MD5:4166324B5EA73036FF6B40353B7CBEC9 | SHA256:F5EAA8A3472CDC786A43C11C890B854EAEBD59C9F39A174A4DF773C8A171BDC9 | |||
| 4300 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\DroidVPN_PC_v3.2\DroidVPN\driver\x64\install.bat | text | |
MD5:4131D543638D19687A5F31E34F74FA06 | SHA256:1DEABE641D930028AF7293B1A348E14A6ADDDA6081B609A5425429E1F78AD102 | |||
| 4300 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\DroidVPN_PC_v3.2\DroidVPN\driver\x64\tap0901.sys | executable | |
MD5:B6E9DF4829CD9FCBB8C69B8DA4C5108F | SHA256:E6E3583C7A14ACE94738B14A69D978F29AE68FFB67730DE45C09C7BA276E7D1F | |||
| 4300 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\DroidVPN_PC_v3.2\DroidVPN\droidvpn32.exe | executable | |
MD5:DD51EBF38117B506AD9E5F574835650A | SHA256:66BAEF36B07E22622266896ADEFA3F247FE3880B1737FB1BACF36B5D51DEB33B | |||
| 4300 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\DroidVPN_PC_v3.2\DroidVPN\DroidVPNLauncher.exe | executable | |
MD5:F5F5C47EB00F2D55228500A744D33CA2 | SHA256:30251FDD7DB959A319D3FBCDA79EB773A0AEE9FD0E7FCEE6A79E6218EDF39F50 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
18
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7804 | SIHClient.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7804 | SIHClient.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 20.7.1.246:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6544 | svchost.exe | 40.126.32.133:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |