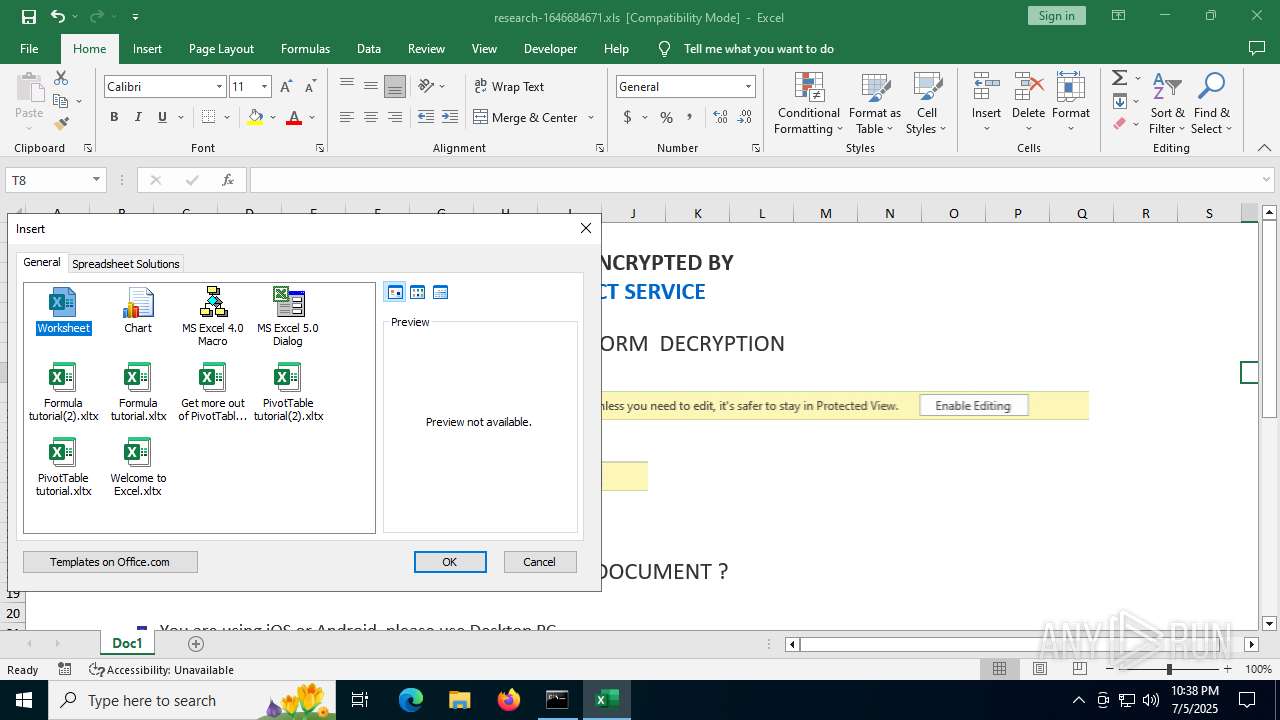
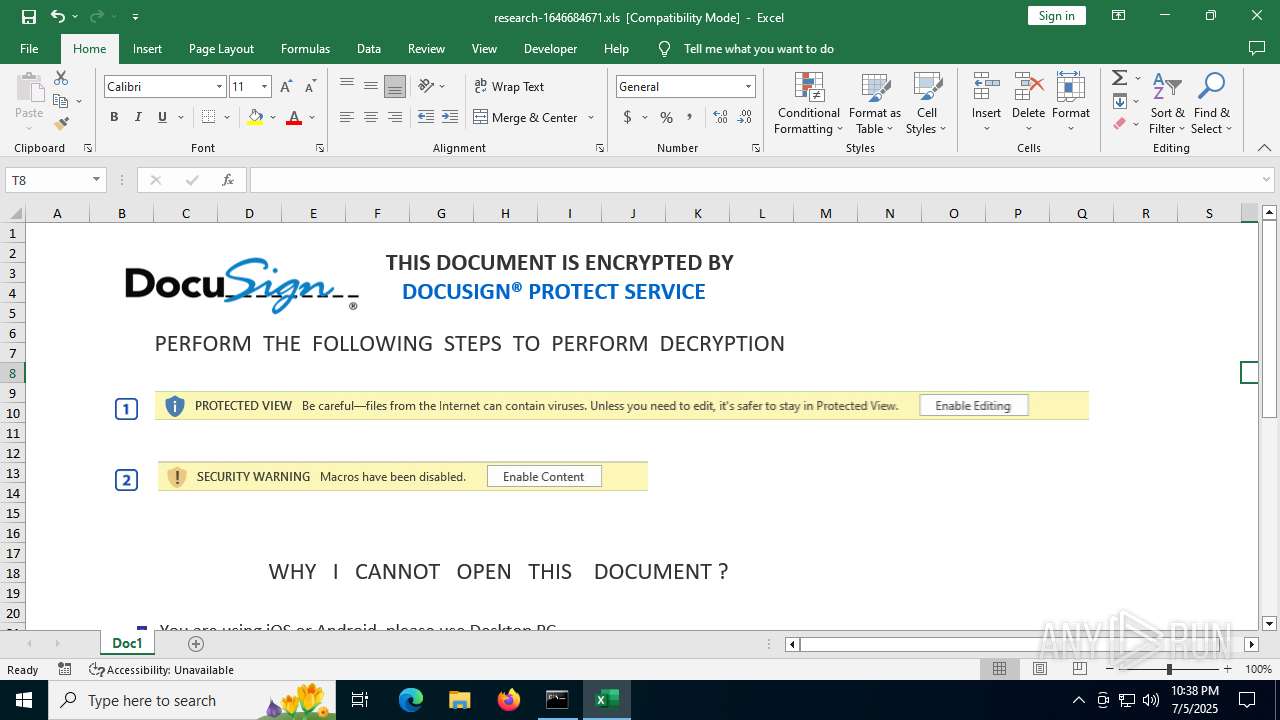
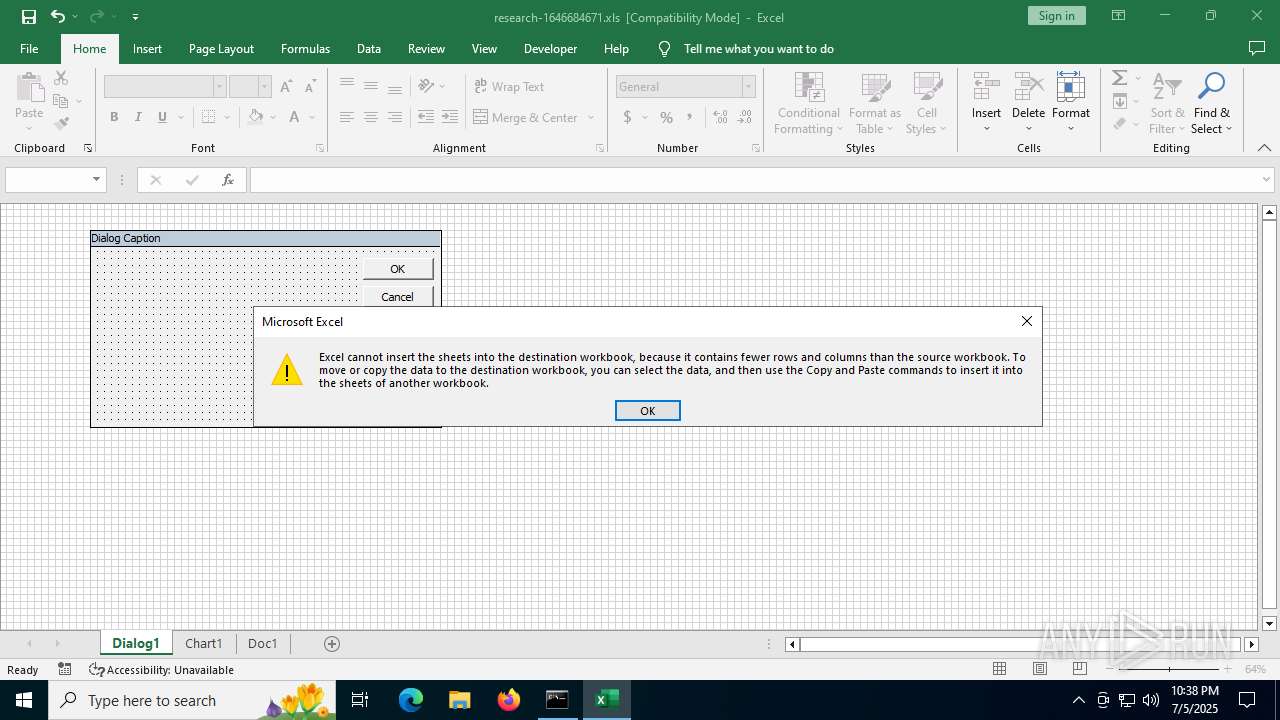
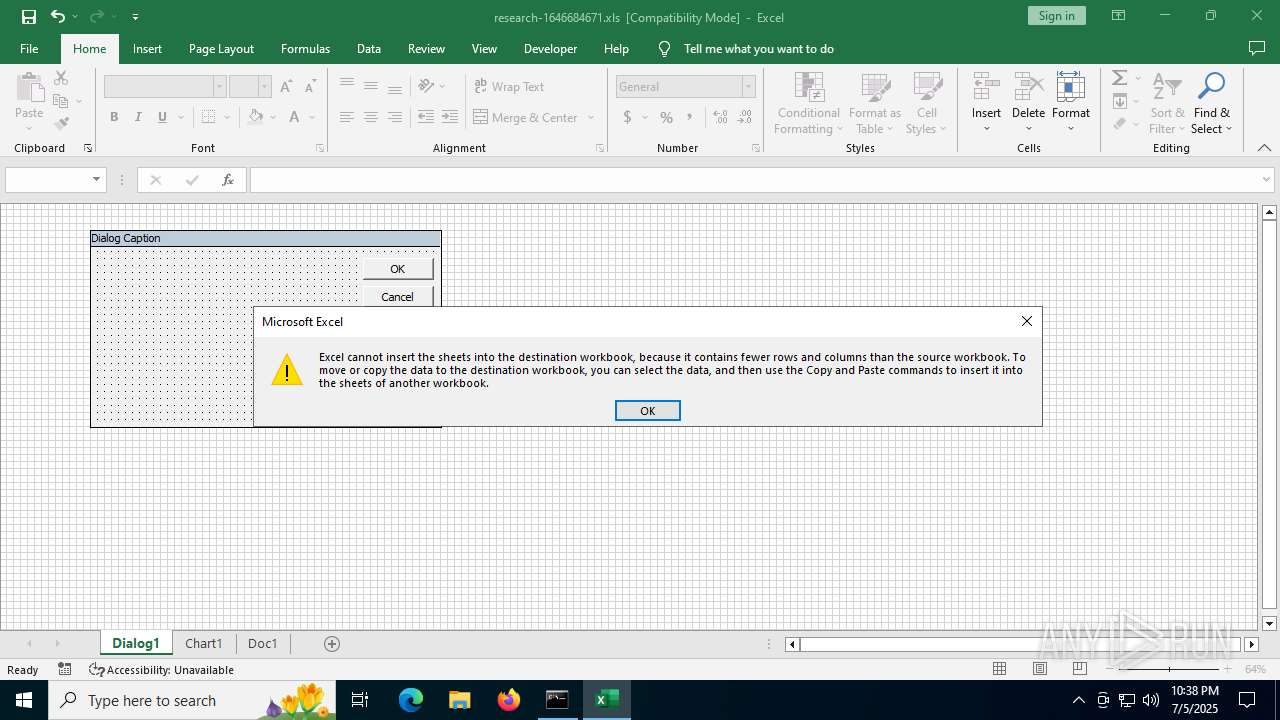
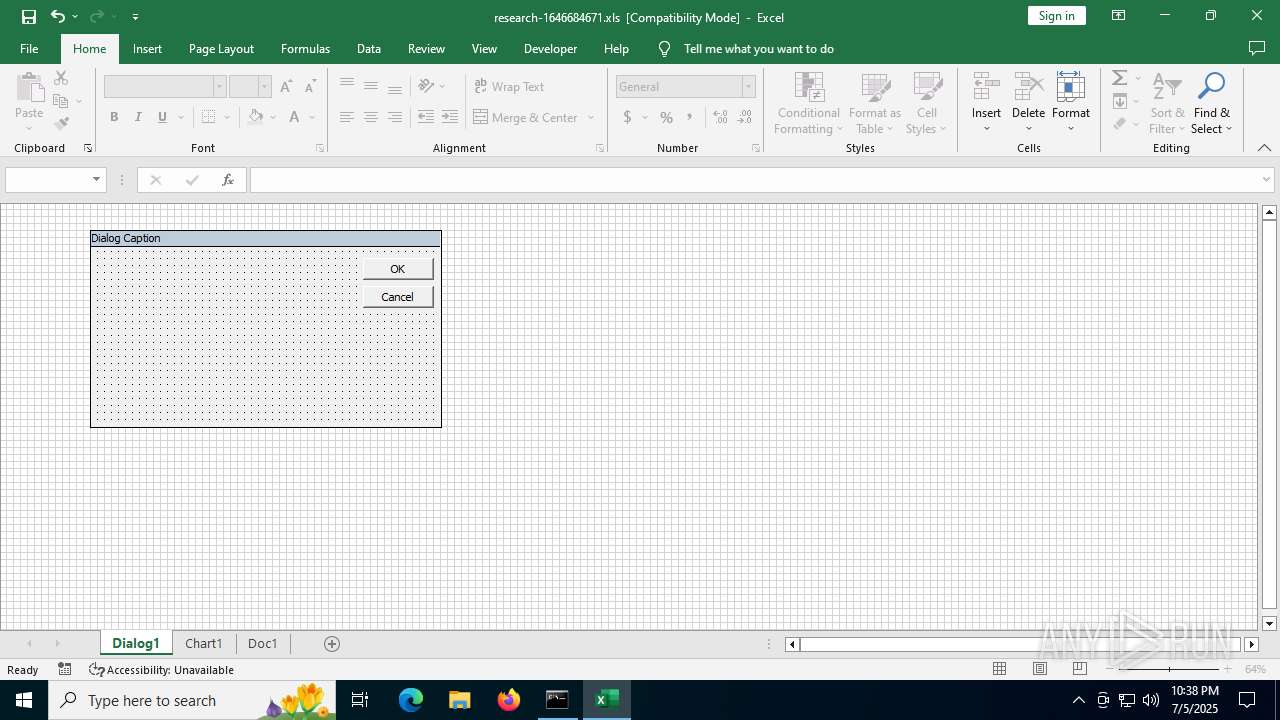
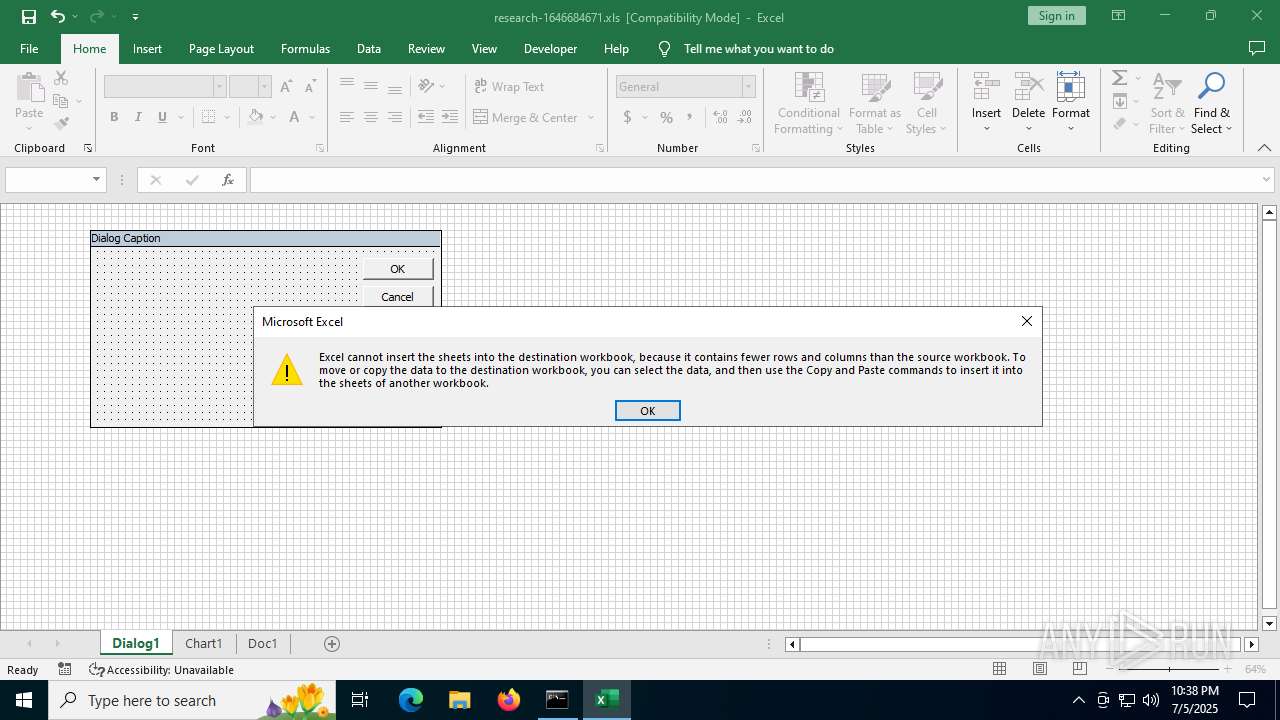
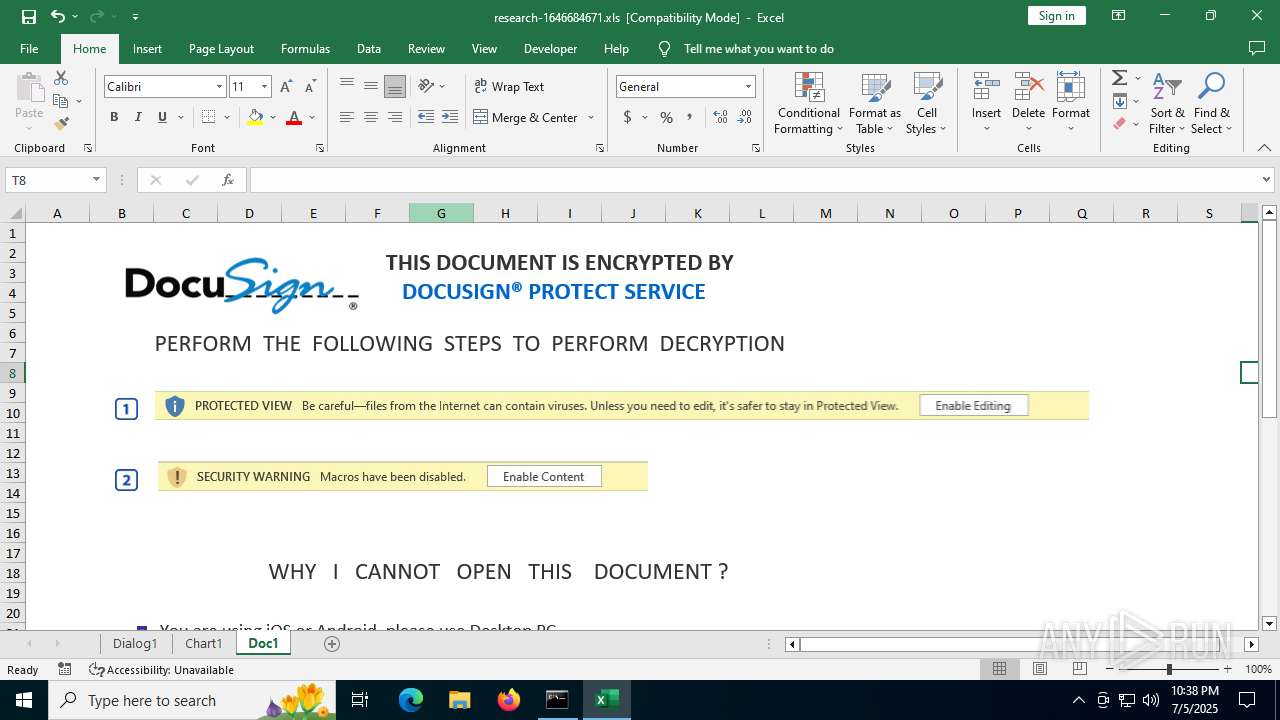
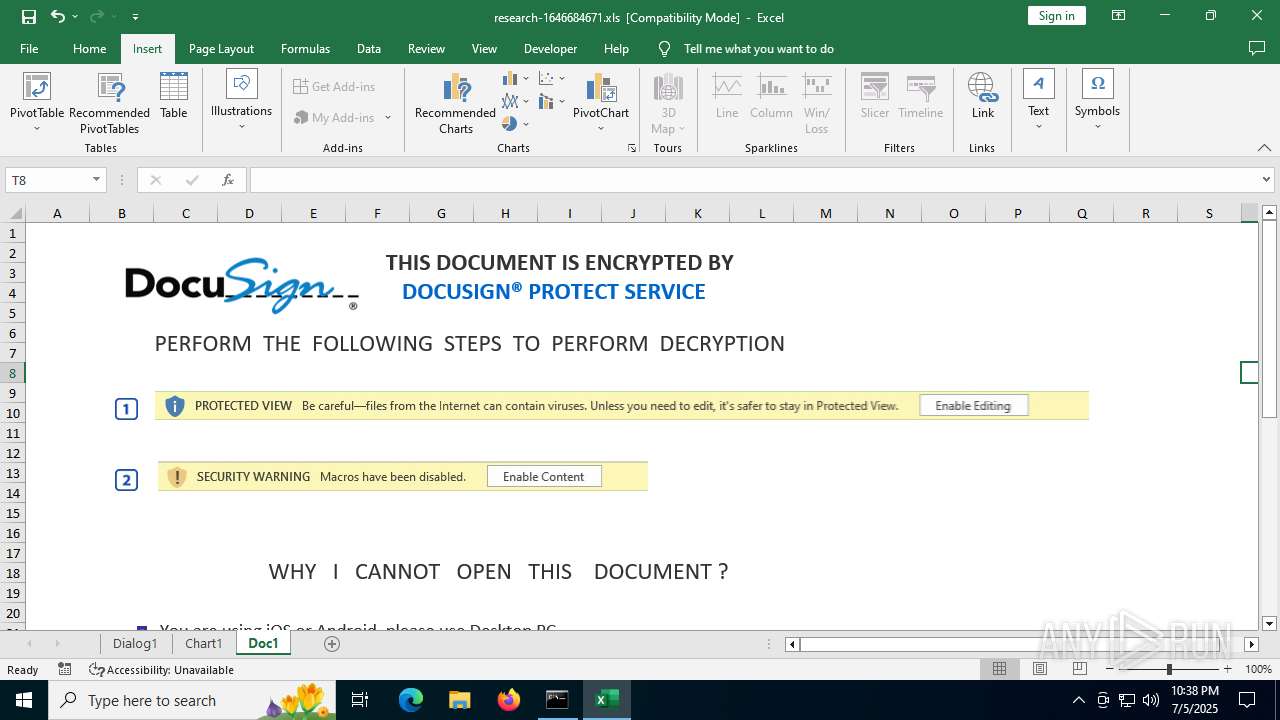
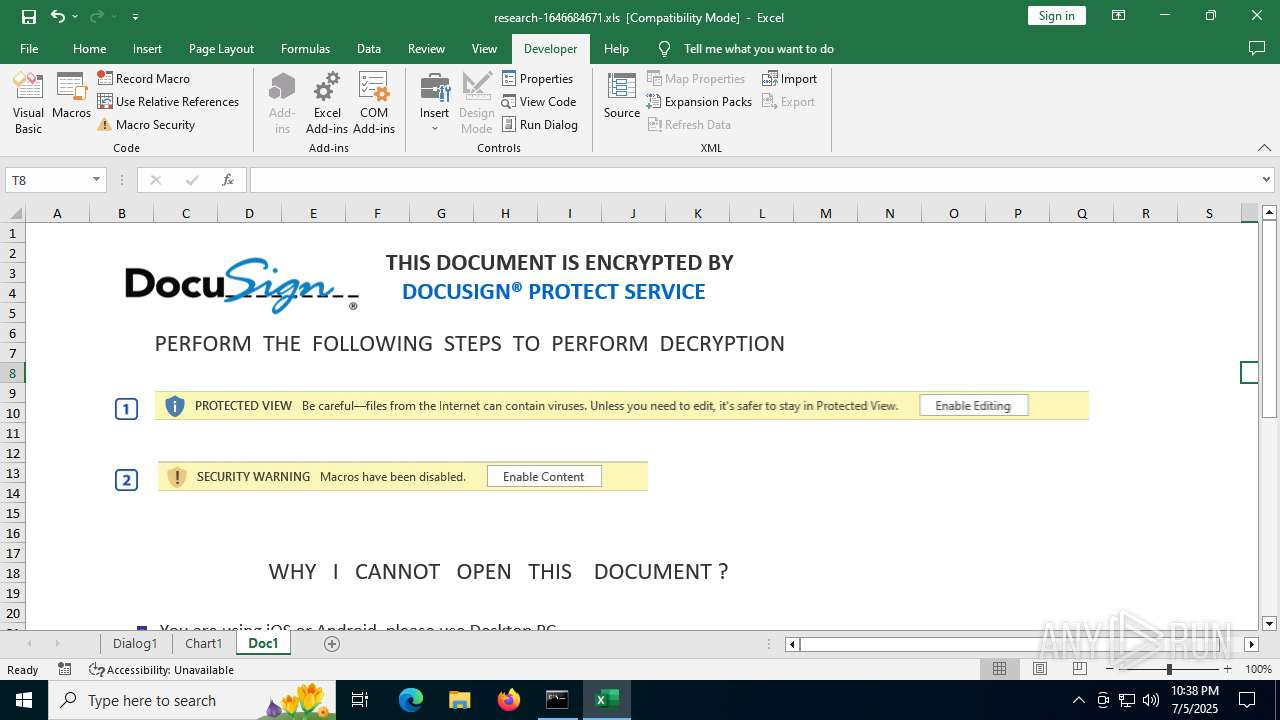
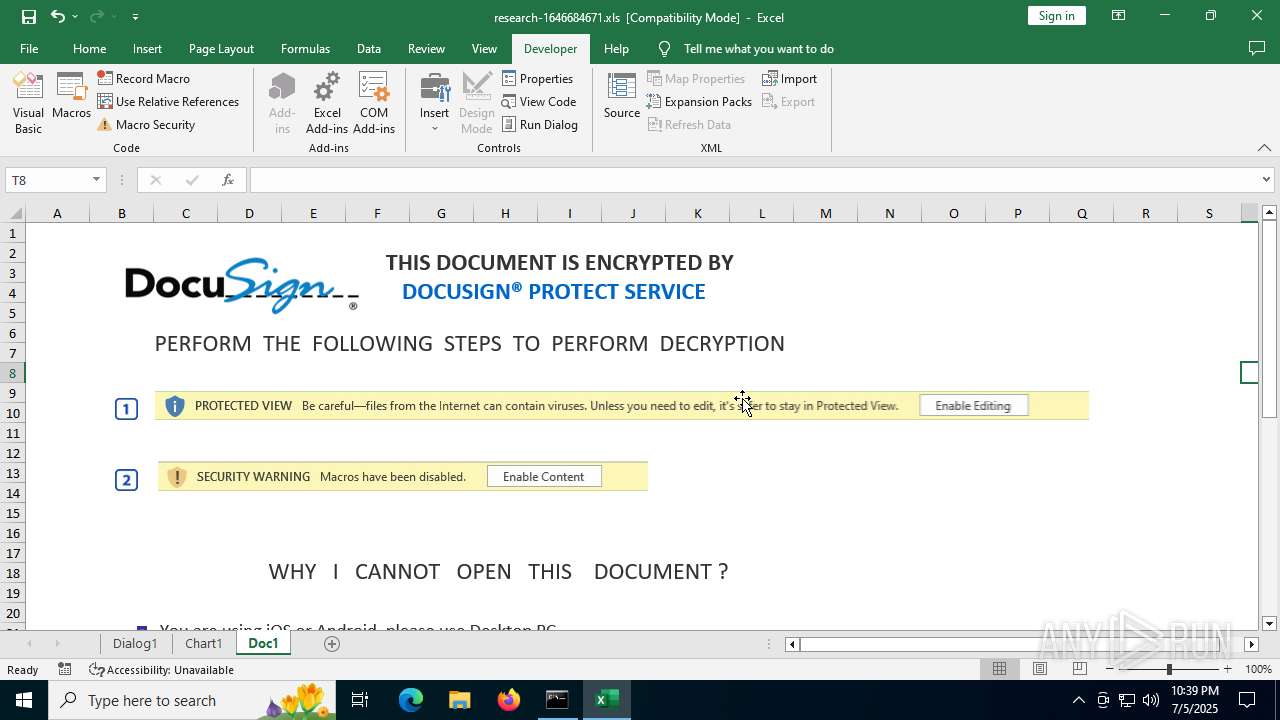
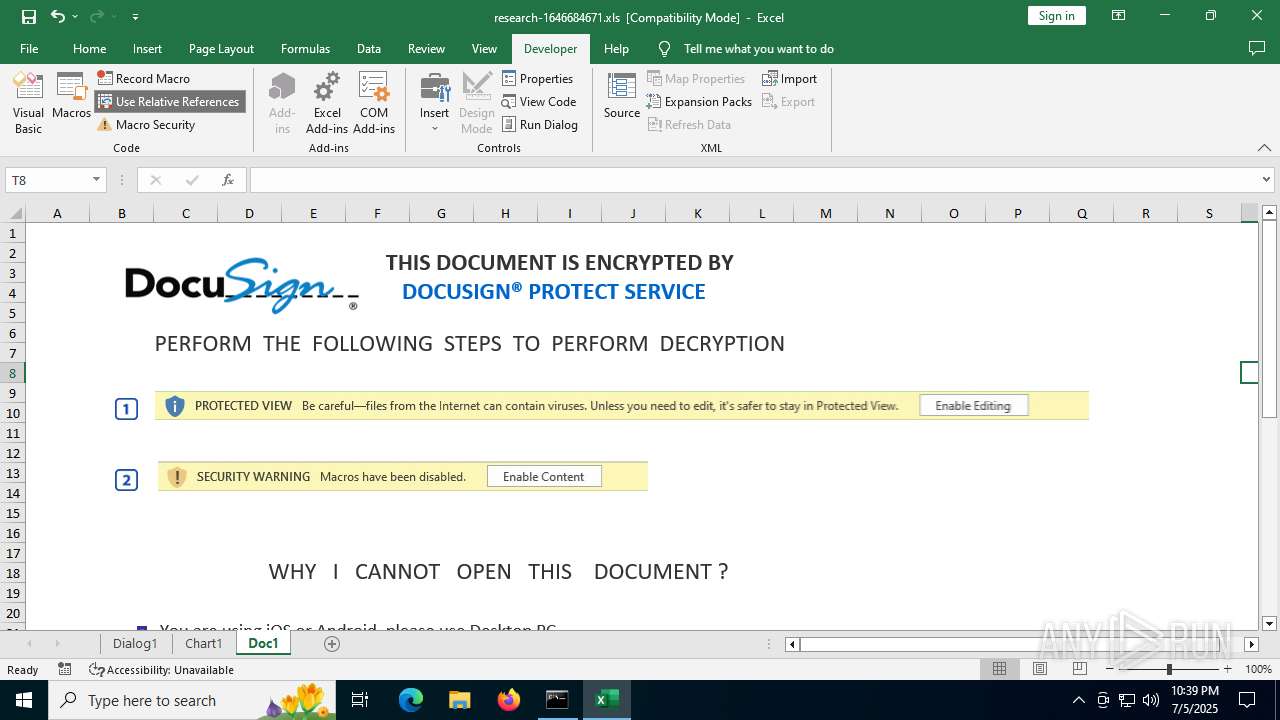
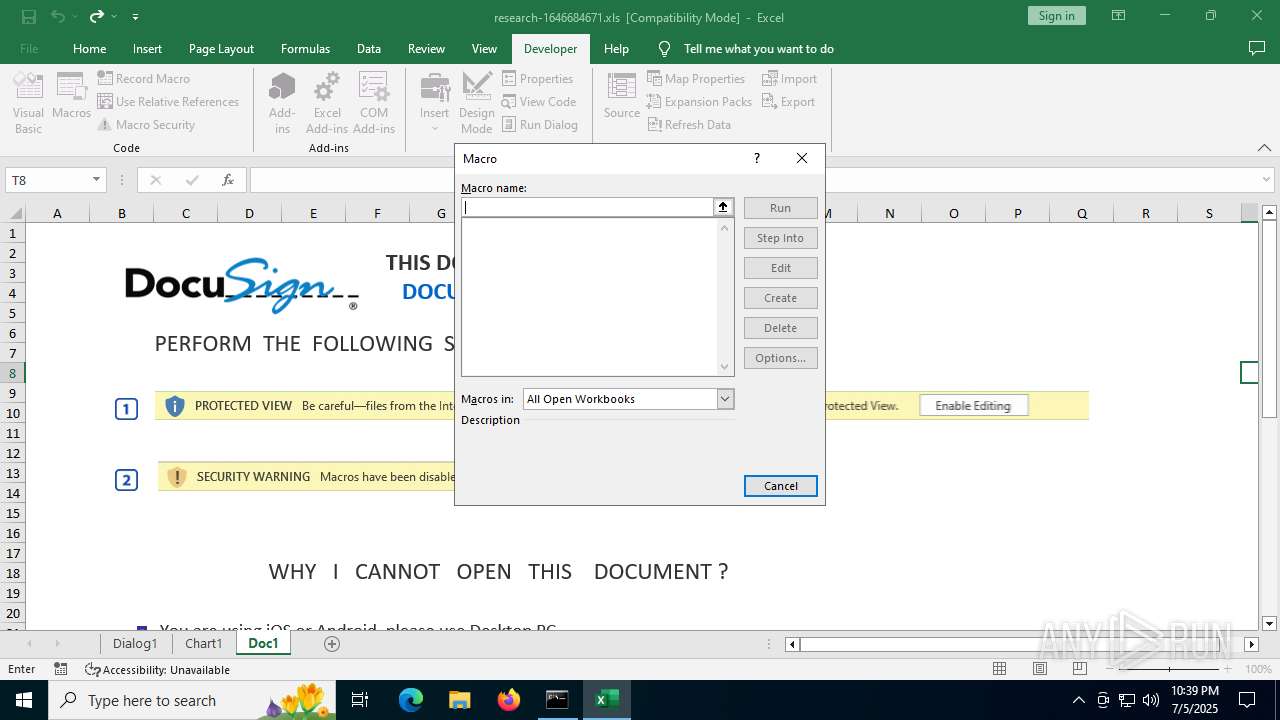
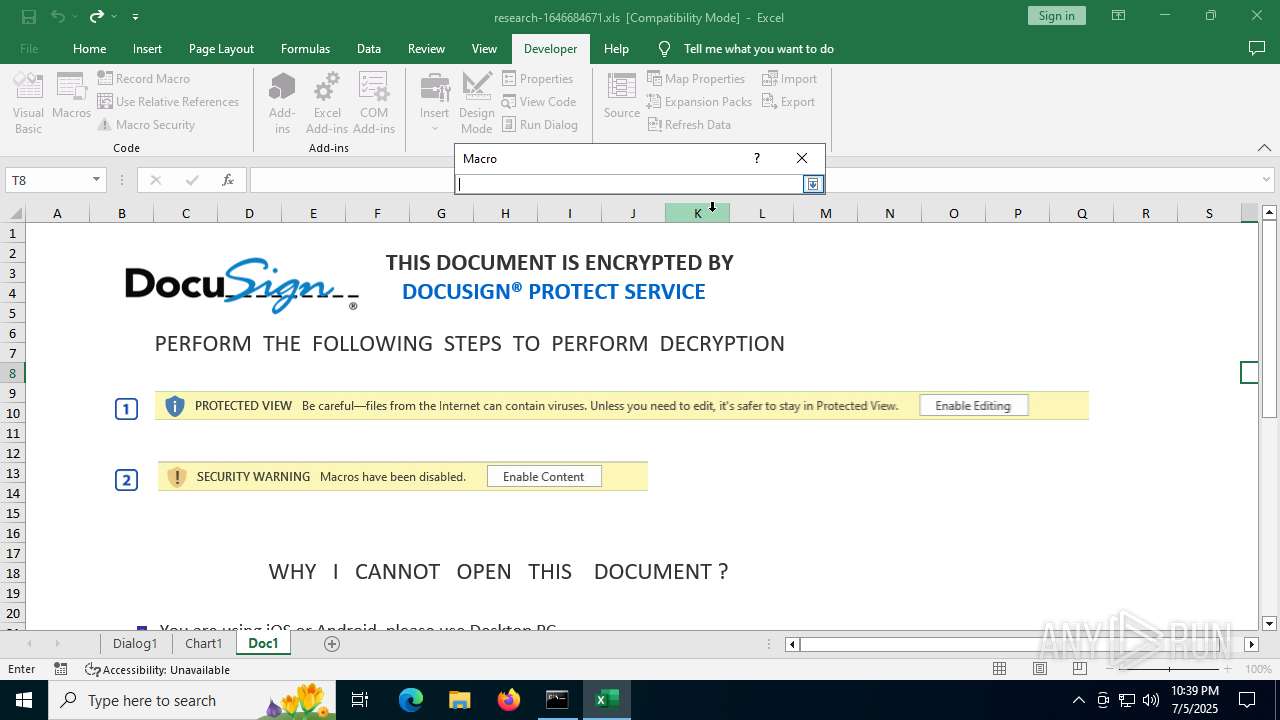
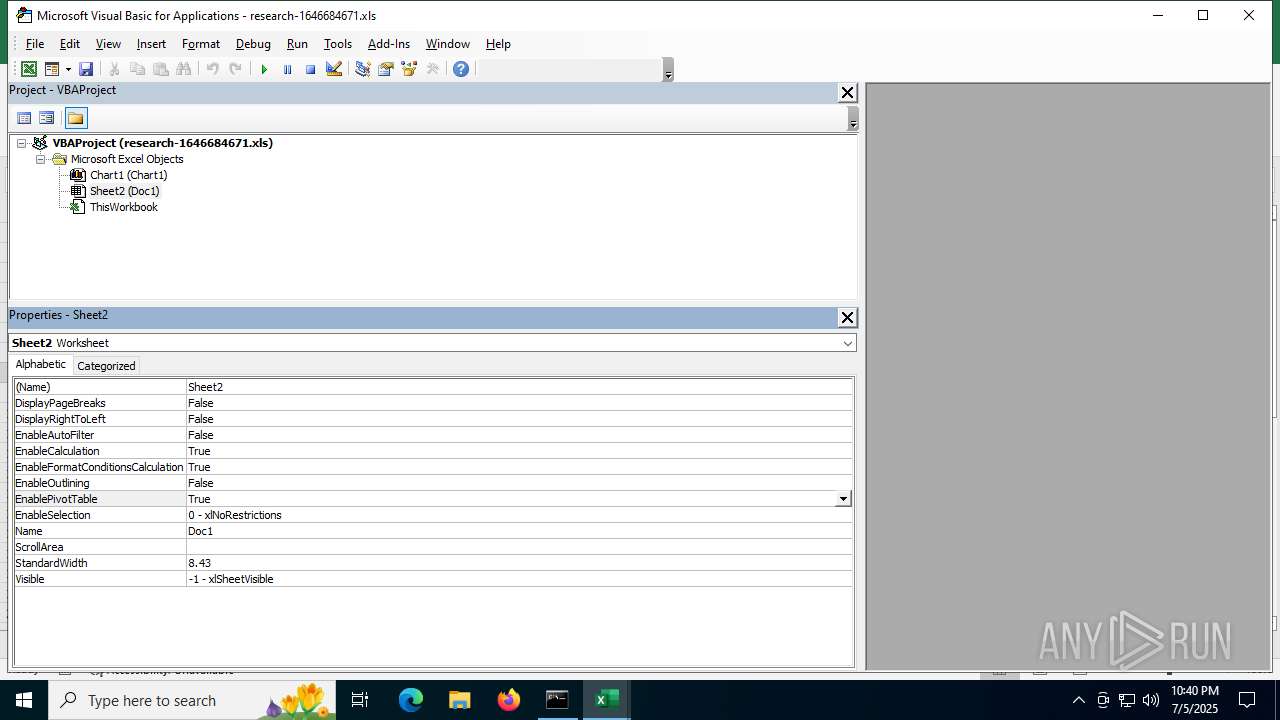
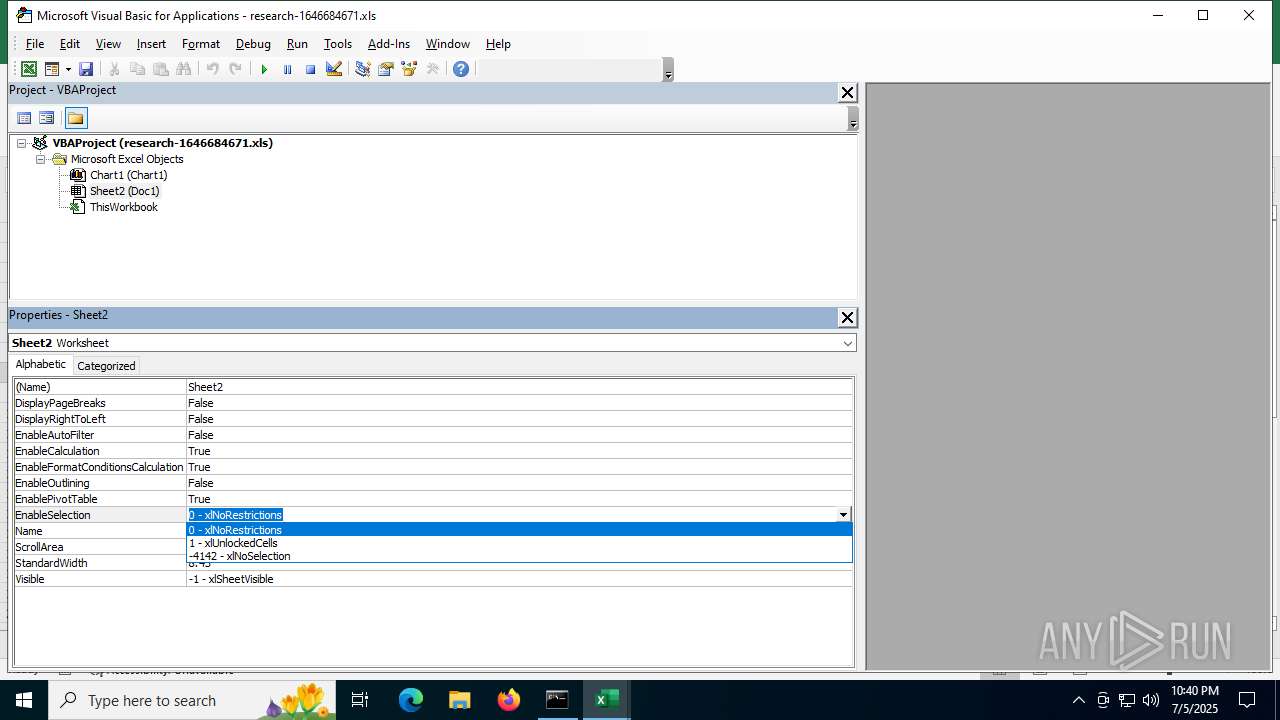
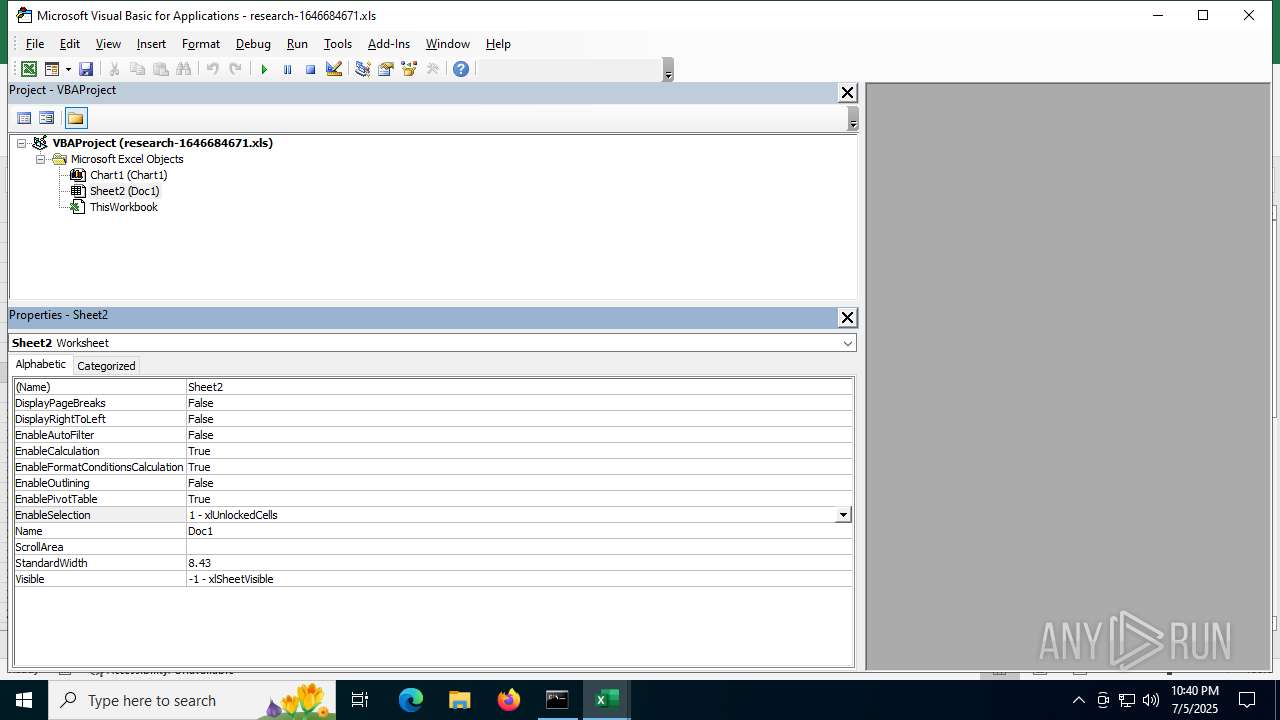
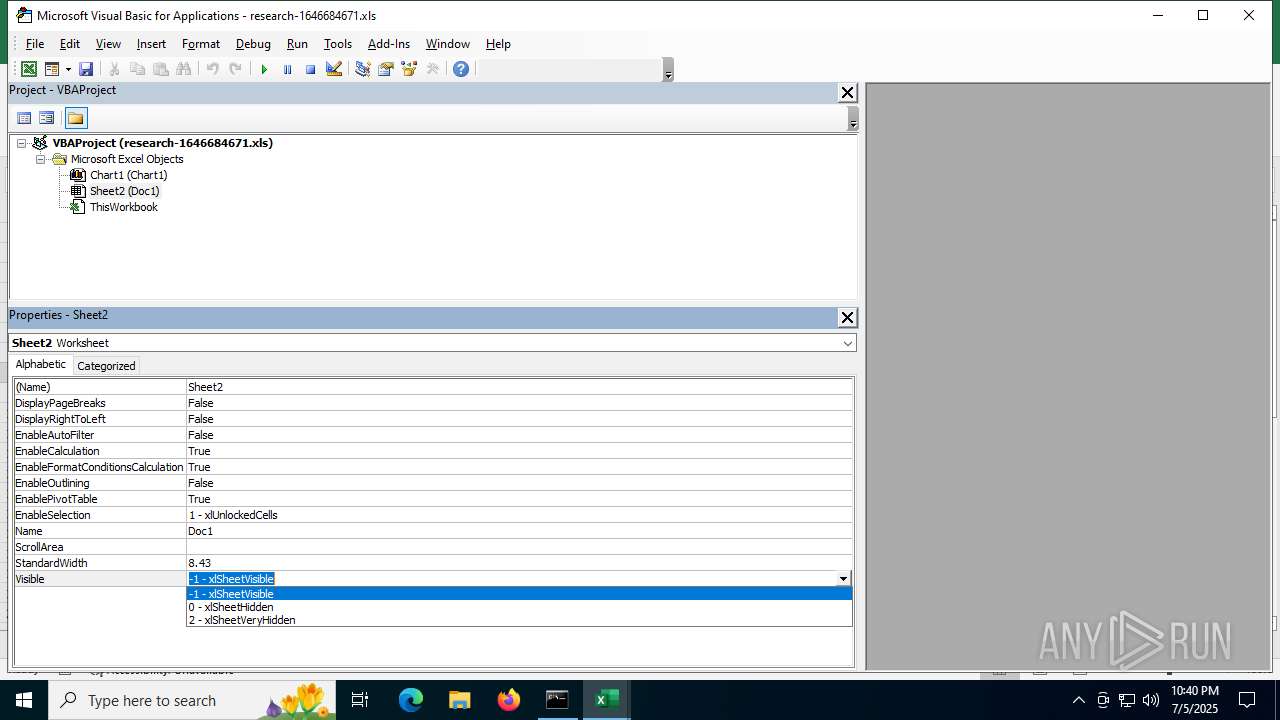
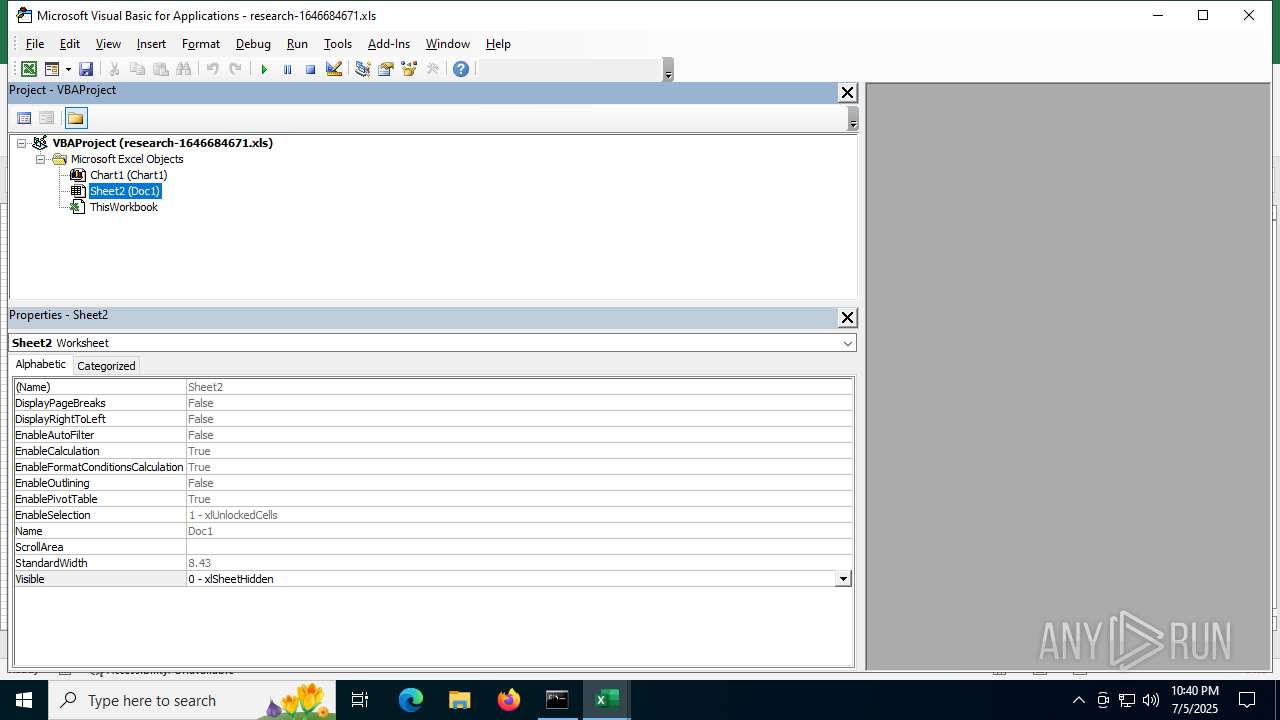
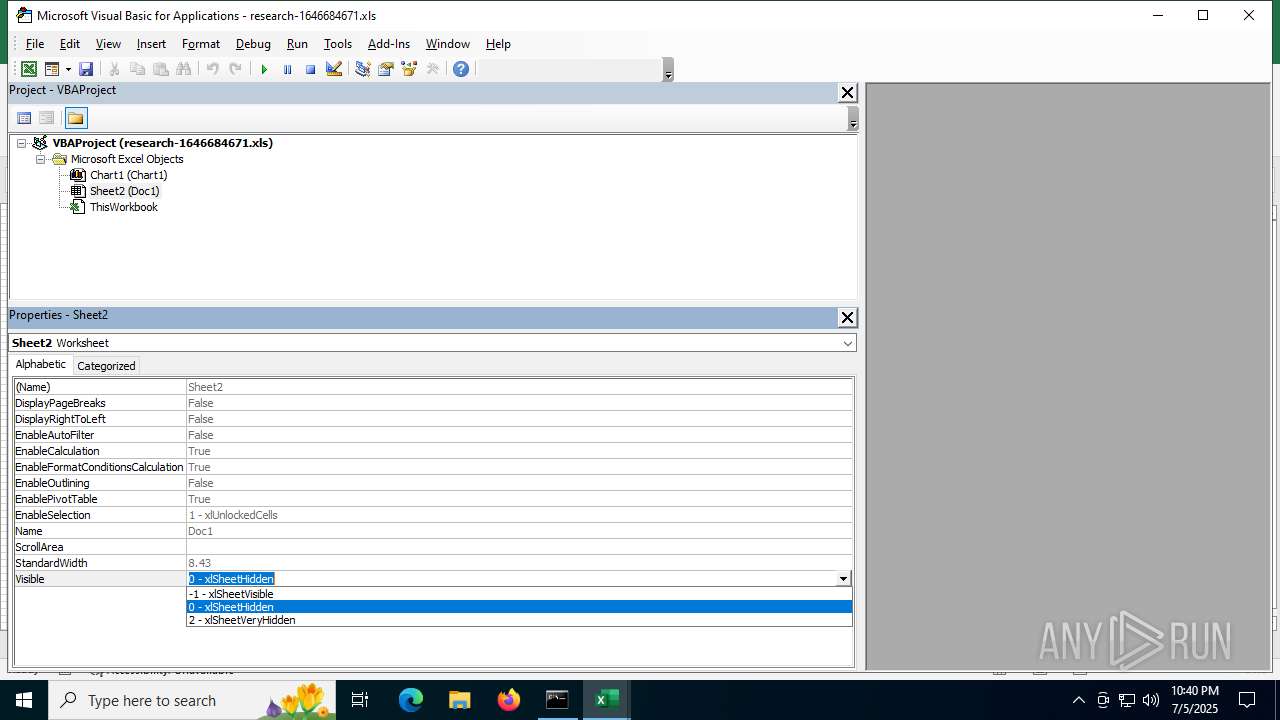
| File name: | research-1646684671.xls |
| Full analysis: | https://app.any.run/tasks/b4e4e5c2-c292-4ea3-be43-09c908c562f4 |
| Verdict: | Malicious activity |
| Analysis date: | July 05, 2025, 22:36:34 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-excel |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, Code page: 1252, Last Saved By: Amanda, Name of Creating Application: Microsoft Excel, Create Time/Date: Fri Jun 5 18:17:20 2015, Last Saved Time/Date: Sun Jun 13 09:24:55 2021, Security: 0 |
| MD5: | 927005139A0BE61EFE849C715D875DD2 |
| SHA1: | 0F6A91916941D85B69E5320873A5D1C45055BC4E |
| SHA256: | B23491EDE17F9A5B7D6AD27D3051A2224C214A5AFA2139E5147BD26319577F85 |
| SSDEEP: | 6144:Hknl9oBdySAx76F6XeyTVtW/9Ny9ABnl5/PBgxOHjuM9Mq:jl5/WxIjL |
MALICIOUS
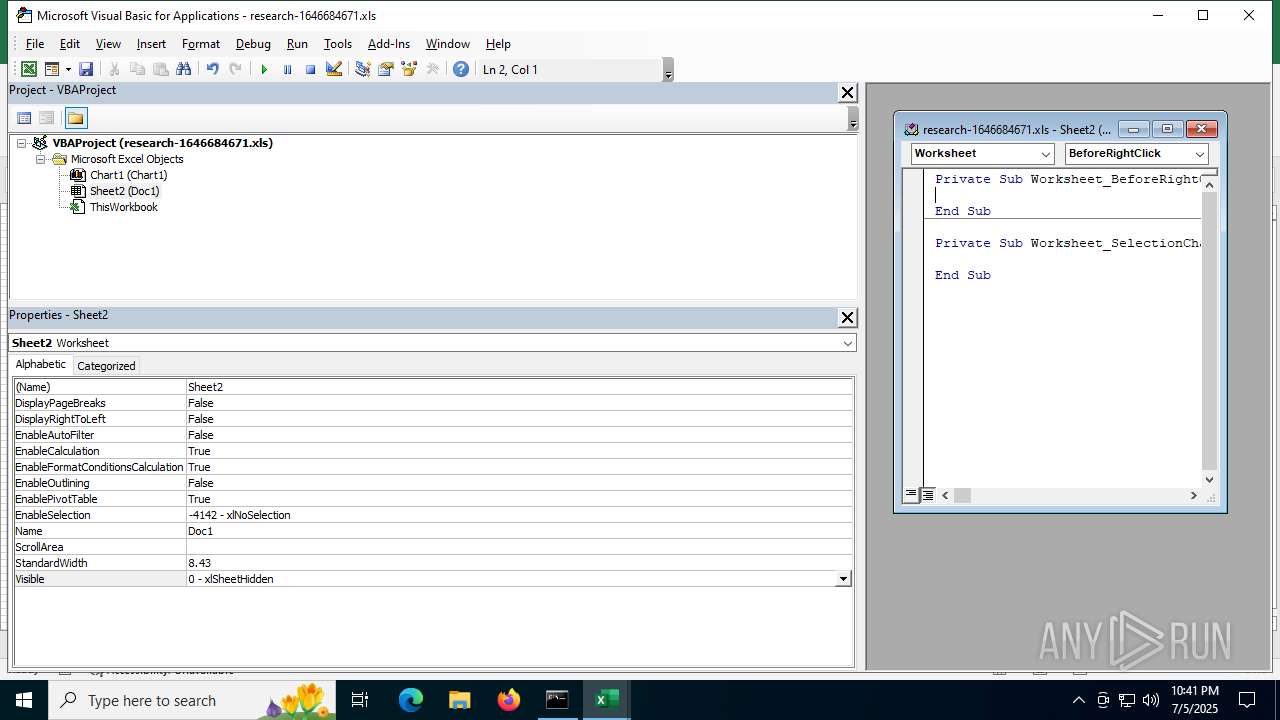
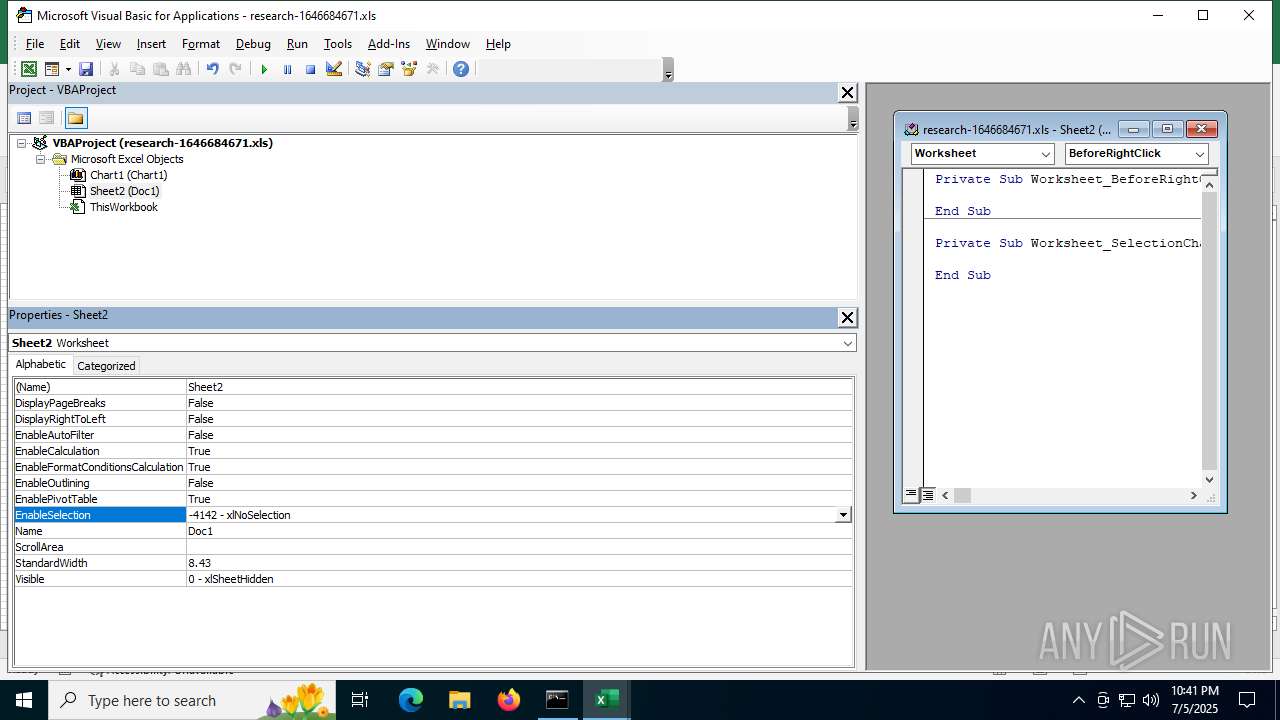
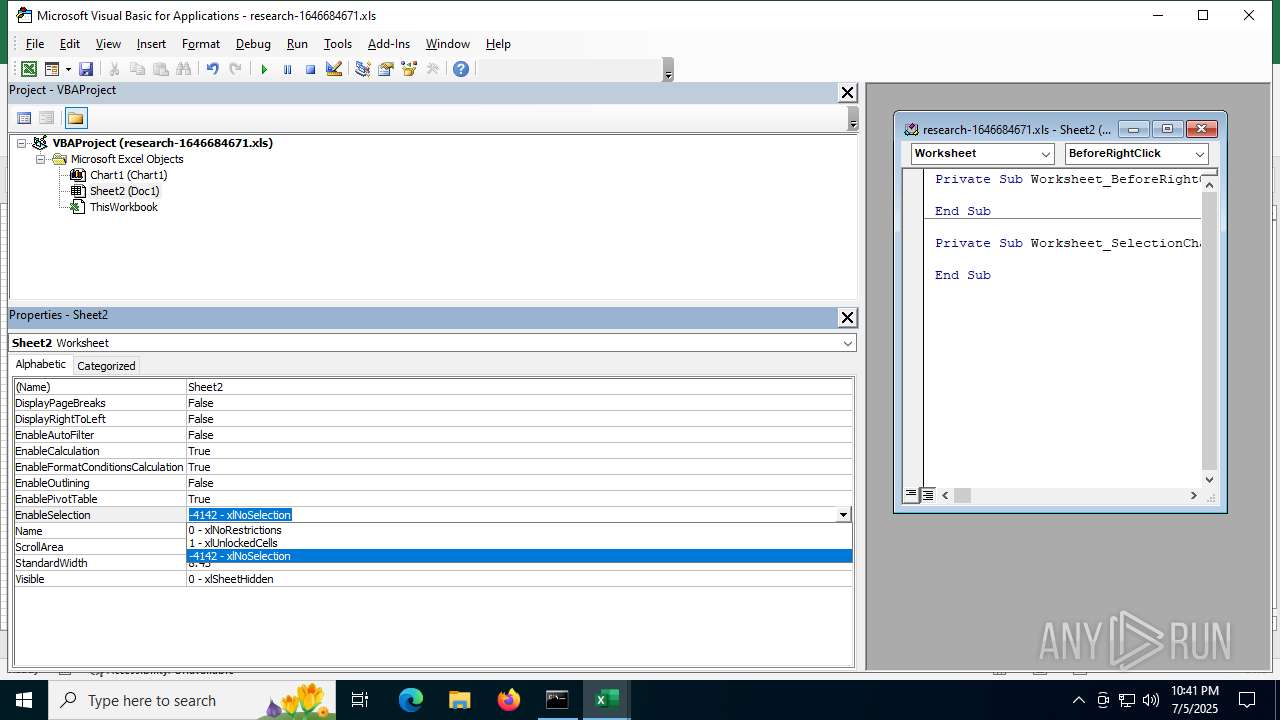
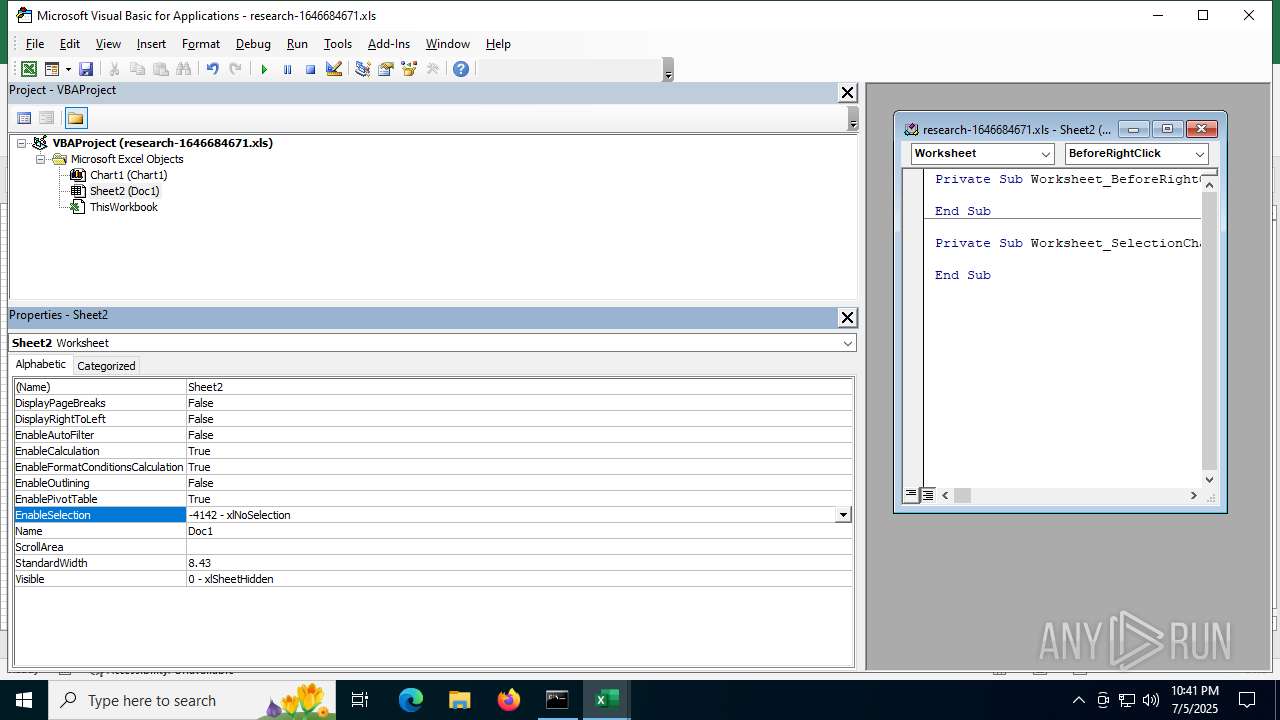
Calls Win API functions (MACROS)
- EXCEL.EXE (PID: 7156)
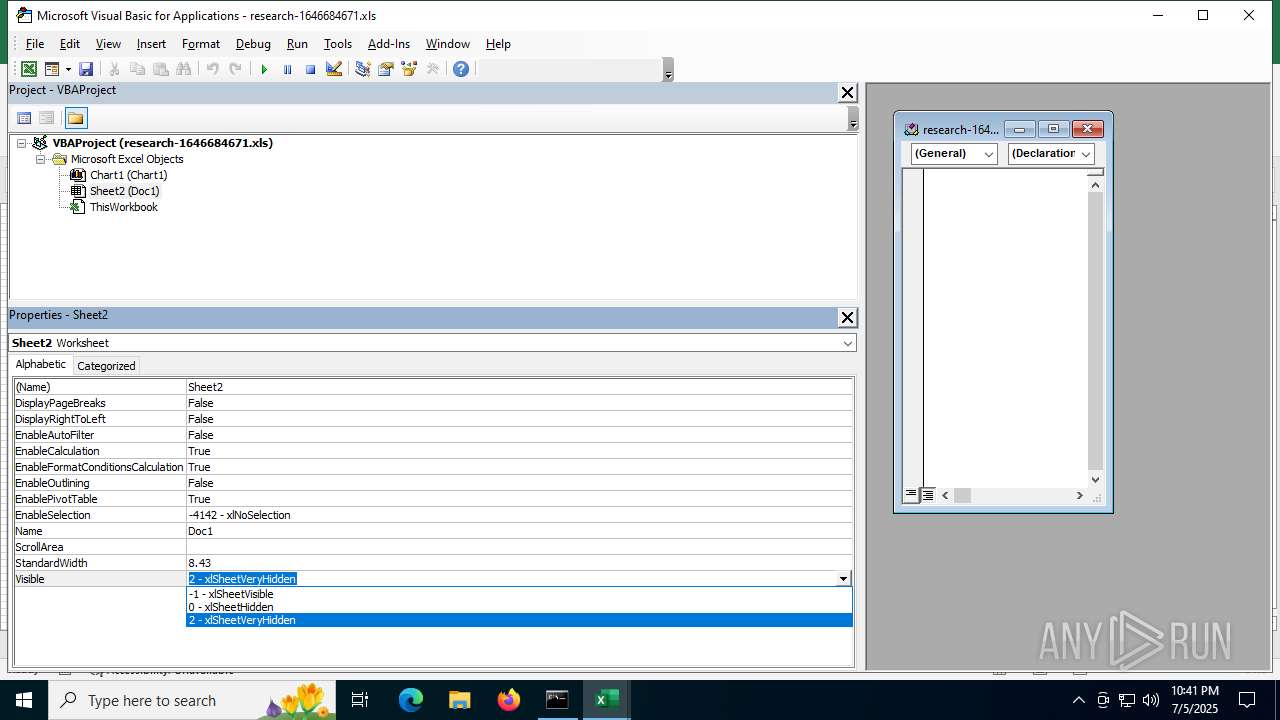
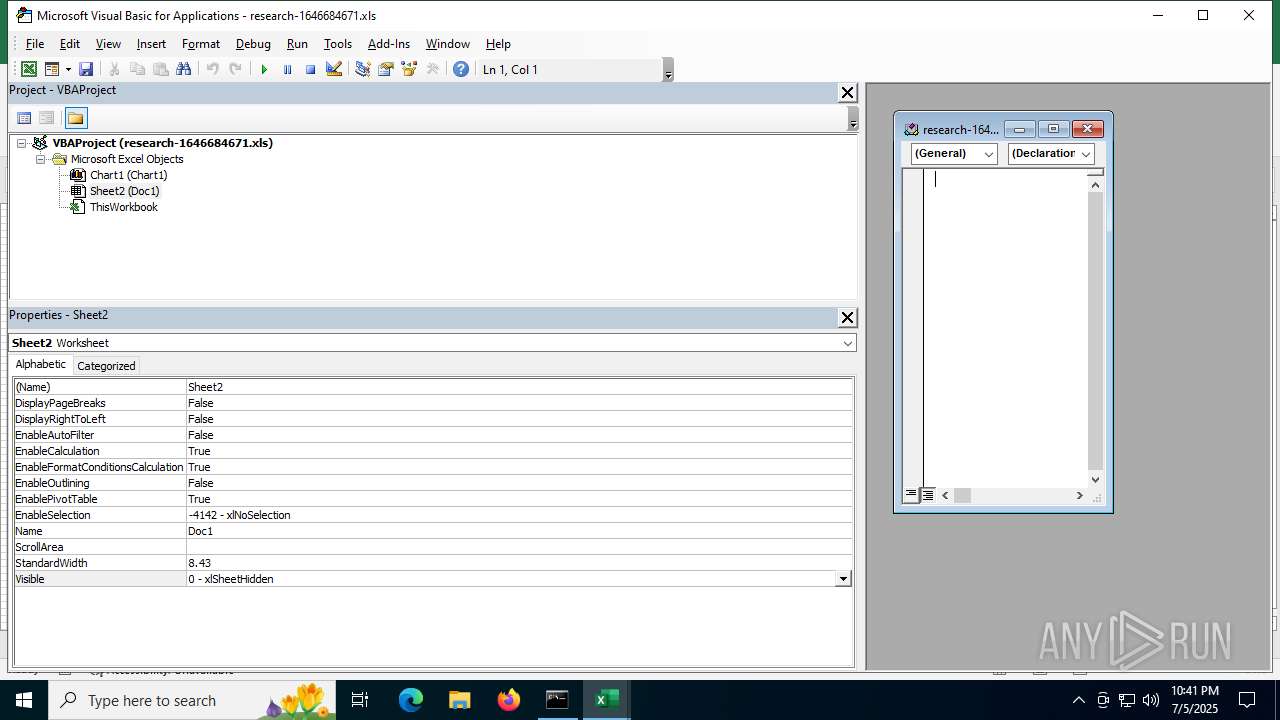
Registers / Runs the DLL via REGSVR32.EXE
- EXCEL.EXE (PID: 7156)
Unusual execution from MS Office
- EXCEL.EXE (PID: 7156)
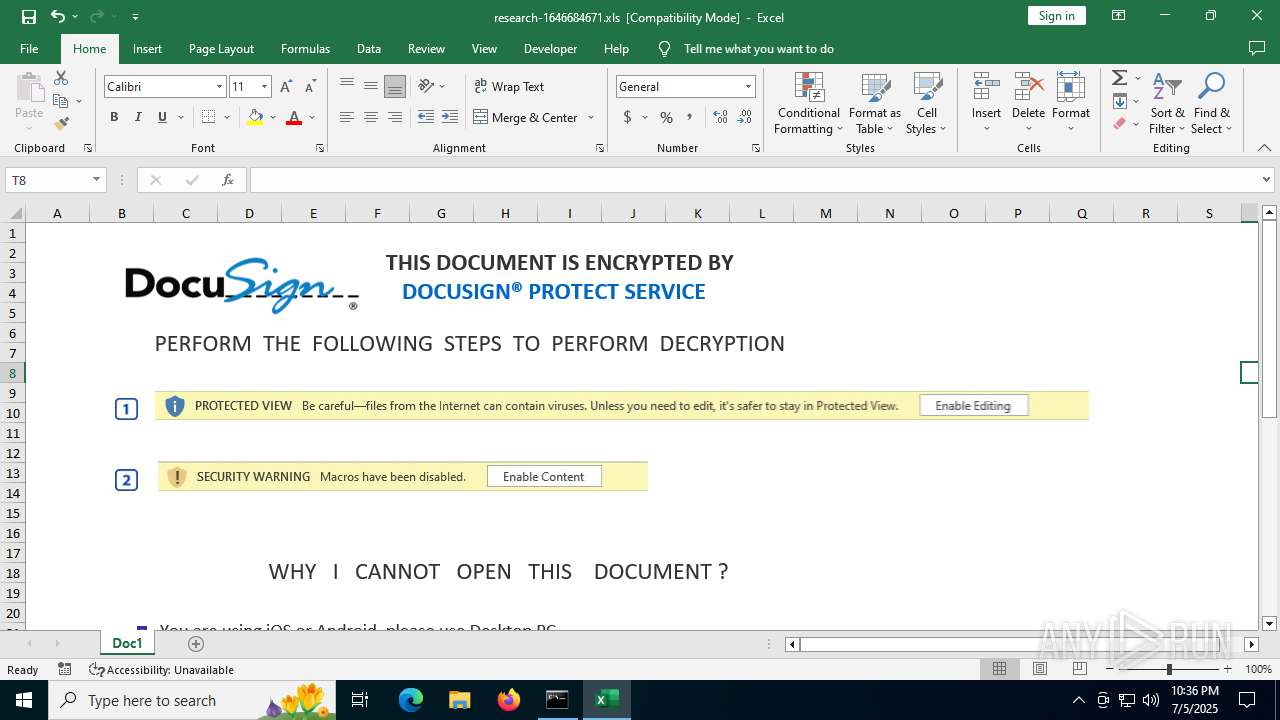
Drops known malicious image
- EXCEL.EXE (PID: 7156)
SUSPICIOUS
Sets XML DOM element text (SCRIPT)
- splwow64.exe (PID: 4916)
INFO
Reads security settings of Internet Explorer
- splwow64.exe (PID: 4916)
Reads the software policy settings
- slui.exe (PID: 6164)
Checks proxy server information
- slui.exe (PID: 6164)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xls | | | Microsoft Excel sheet (78.9) |
|---|
EXIF
FlashPix
| Author: | - |
|---|---|
| LastModifiedBy: | Amanda |
| Software: | Microsoft Excel |
| CreateDate: | 2015:06:05 18:17:20 |
| ModifyDate: | 2021:06:13 09:24:55 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | - |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| TitleOfParts: |
|
| HeadingPairs: |
|
Total processes
155
Monitored processes
7
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2532 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4572 | regsvr32 -s ..\iroto1.dll | C:\Windows\System32\regsvr32.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft(C) Register Server Exit code: 3 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4916 | C:\WINDOWS\splwow64.exe 8192 | C:\Windows\splwow64.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Print driver host for applications Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5564 | regsvr32 -s ..\iroto.dll | C:\Windows\System32\regsvr32.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft(C) Register Server Exit code: 3 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6164 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7052 | "C:\Windows\System32\cmd.exe" /k C:\Users\admin\AppData\Local\Temp\research-1646684671.xls | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7156 | "C:\Program Files\Microsoft Office\Root\Office16\EXCEL.EXE" "C:\Users\admin\AppData\Local\Temp\research-1646684671.xls" | C:\Program Files\Microsoft Office\root\Office16\EXCEL.EXE | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Version: 16.0.16026.20146 Modules
| |||||||||||||||
Total events
51 209
Read events
41 134
Write events
10 040
Delete events
35
Modification events
| (PID) Process: | (7052) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.xls\OpenWithProgids |
| Operation: | write | Name: | Excel.Sheet.8 |
Value: | |||
| (PID) Process: | (7052) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {97E467B4-98C6-4F19-9588-161B7773D6F6} {886D8EEB-8CF2-4446-8D02-CDBA1DBDCF99} 0xFFFF |
Value: 010000000000000007D54346FDEDDB01 | |||
| (PID) Process: | (7156) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 1 |
Value: 01D014000000001000B24E9A3E02000000000000000600000000000000 | |||
| (PID) Process: | (7156) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (7156) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 2 | |||
| (PID) Process: | (7156) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 2 | |||
| (PID) Process: | (7156) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 2 | |||
| (PID) Process: | (7156) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 2 | |||
| (PID) Process: | (7156) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ja-jp |
Value: 2 | |||
| (PID) Process: | (7156) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ko-kr |
Value: 2 | |||
Executable files
18
Suspicious files
108
Text files
146
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7156 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:04E74F1D63CDC39FDA95250E0286D75F | SHA256:0E869DAE454B27F864873255B2C0BF8D04CE537BD93BBEE5BD284EBADAB5CAD8 | |||
| 7156 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\UsageMetricsStore\FileActivityStoreV3\Excel\ASkwMDAwMDAwMC0wMDAwLTAwMDAtMDAwMC0wMDAwMDAwMDAwMDBfTnVsbAA.S | binary | |
MD5:2D033F9A60BD62A34BEBA7CA8BFCA781 | SHA256:7BCAF38951E1B440B09DAF2FCC3659A78DF421C4E0296F4A702B0AFE754C8207 | |||
| 7156 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:102FF1B56BF3D9BD757F1D4AB9A43BD0 | SHA256:92D4CAD216D618838B851523032474F60E1CD43AAE3308AB6C76E2504E78F5D9 | |||
| 7156 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\936F10BC72DB0BC0181957BCF75D6817 | binary | |
MD5:14640B9690173B85D33DBE9CC2E1085E | SHA256:3552B49E3CF2C4757B43D569F4259C4BDC271012CC5DC99BD10465EA68A84E11 | |||
| 7156 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:27DE676559879654F7EC53F60085D945 | SHA256:25A1FD9DE227967686B4D03BFF9F47E7FDEDEB3FA587BEBAD400DE97555F1288 | |||
| 7156 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_363582827213C09529A76F35FB615187 | binary | |
MD5:1EB7064D7DFF9B7279672E6EE740BFB4 | SHA256:9F0B6CED178C48202494E9709F8773E6B3A73C2EFC56FE314C1EE2A02D31A7EE | |||
| 7156 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\BEINCR40ZQIUICG8E9IJ.temp | binary | |
MD5:4FCB2A3EE025E4A10D21E1B154873FE2 | SHA256:90BF6BAA6F968A285F88620FBF91E1F5AA3E66E2BAD50FD16F37913280AD8228 | |||
| 7156 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\b8ab77100df80ab2.customDestinations-ms | binary | |
MD5:4FCB2A3EE025E4A10D21E1B154873FE2 | SHA256:90BF6BAA6F968A285F88620FBF91E1F5AA3E66E2BAD50FD16F37913280AD8228 | |||
| 7156 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.MSO\25691017.png | image | |
MD5:5D8695378E81D6A97DE3342F7B7199BA | SHA256:2E979F39FDBE795B2CEDEC7279760D72FE5CE024464C0CDA370CD6FED43C8F18 | |||
| 7156 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.MSO\54FDFB2C.png | image | |
MD5:9C3D035A70E26A96B44539BFBBCCFAE1 | SHA256:D7769A198EE0F62601D0571F4E378696696978465861812A119F8E3073439DD7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
17
TCP/UDP connections
71
DNS requests
41
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7156 | EXCEL.EXE | GET | 200 | 104.18.21.213:80 | http://r11.c.lencr.org/29.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7076 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7156 | EXCEL.EXE | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5416 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5416 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 2.23.197.184:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
7156 | EXCEL.EXE | GET | — | 95.100.181.23:80 | http://crl.microsoft.com/pki/crl/products/MicCodSigPCA_08-31-2010.crl | unknown | — | — | whitelisted |
7156 | EXCEL.EXE | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEA8fFXWCzc0zc0vcX82UGjM%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3720 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7156 | EXCEL.EXE | 52.109.28.46:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
7156 | EXCEL.EXE | 52.123.128.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7156 | EXCEL.EXE | 188.209.214.83:443 | nws.visionconsulting.ro | ROMARG SRL | RO | unknown |
7156 | EXCEL.EXE | 104.18.21.213:80 | r11.c.lencr.org | CLOUDFLARENET | — | whitelisted |
7156 | EXCEL.EXE | 52.111.231.8:443 | messaging.lifecycle.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
nws.visionconsulting.ro |
| unknown |
r11.c.lencr.org |
| whitelisted |
royalpalm.sparkblue.lk |
| unknown |
messaging.lifecycle.office.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |