| File name: | restart.exe |
| Full analysis: | https://app.any.run/tasks/28849c04-668b-4ffc-b740-3cf97c9d574c |
| Verdict: | Malicious activity |
| Analysis date: | April 14, 2020, 16:33:01 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 7CA14626517B01598DA5F1784F76A1EE |
| SHA1: | EFF311856C94A86D248E7D4A0FC9D22CC63326B8 |
| SHA256: | B22771D5BA48DC2B9AC1F92CBF6CA39AEE17FAF25F6C14CAE4C54718E0096DA6 |
| SSDEEP: | 6144:TpI0U0Tit+fe7xB74C8tJpZXDCPhWwiaYSojt:FZU0Otme7xF4tzr+PhJiaYSojt |
MALICIOUS
Loads the Task Scheduler COM API
- rundll32.exe (PID: 2444)
Changes internet zones settings
- ie4uinit.exe (PID: 2208)
SUSPICIOUS
Executed as Windows Service
- taskhost.exe (PID: 3016)
Uses RUNDLL32.EXE to load library
- ie4uinit.exe (PID: 2208)
- rundll32.exe (PID: 2444)
Application launched itself
- rundll32.exe (PID: 2444)
Creates files in the program directory
- ie4uinit.exe (PID: 2208)
- chrmstp.exe (PID: 852)
Reads Internet Cache Settings
- taskhost.exe (PID: 3016)
Writes to a desktop.ini file (may be used to cloak folders)
- ie4uinit.exe (PID: 2208)
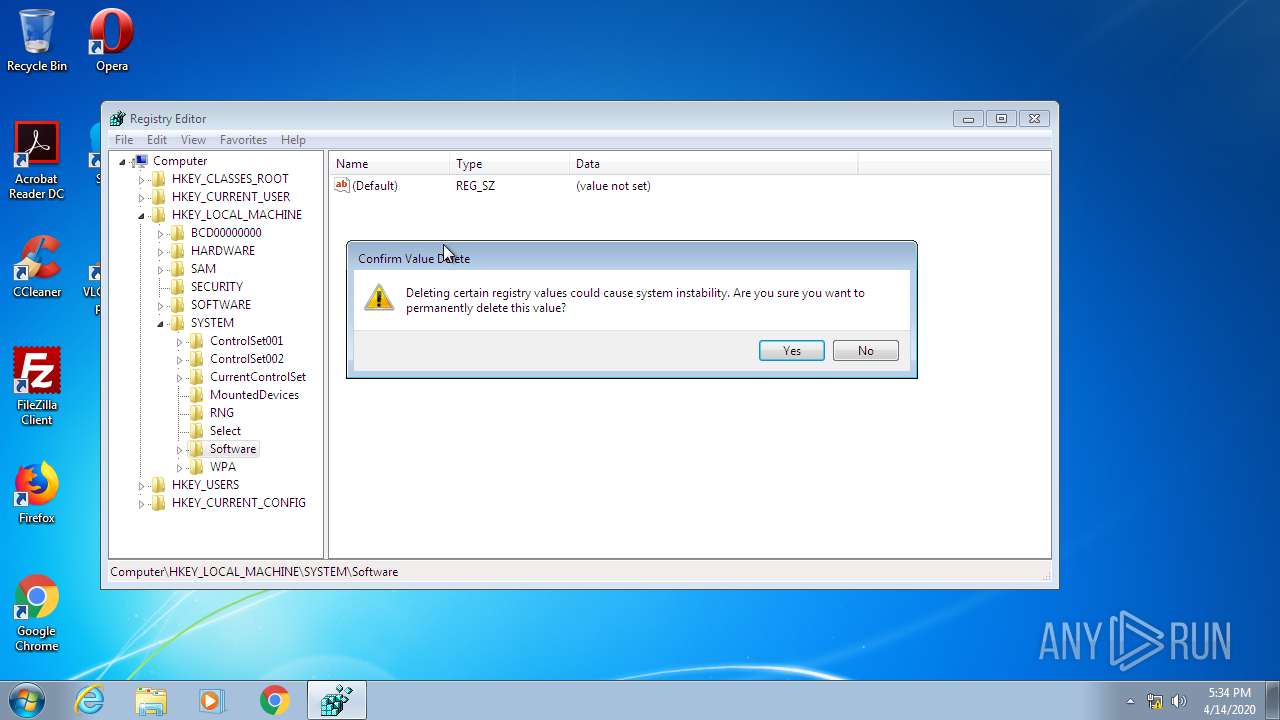
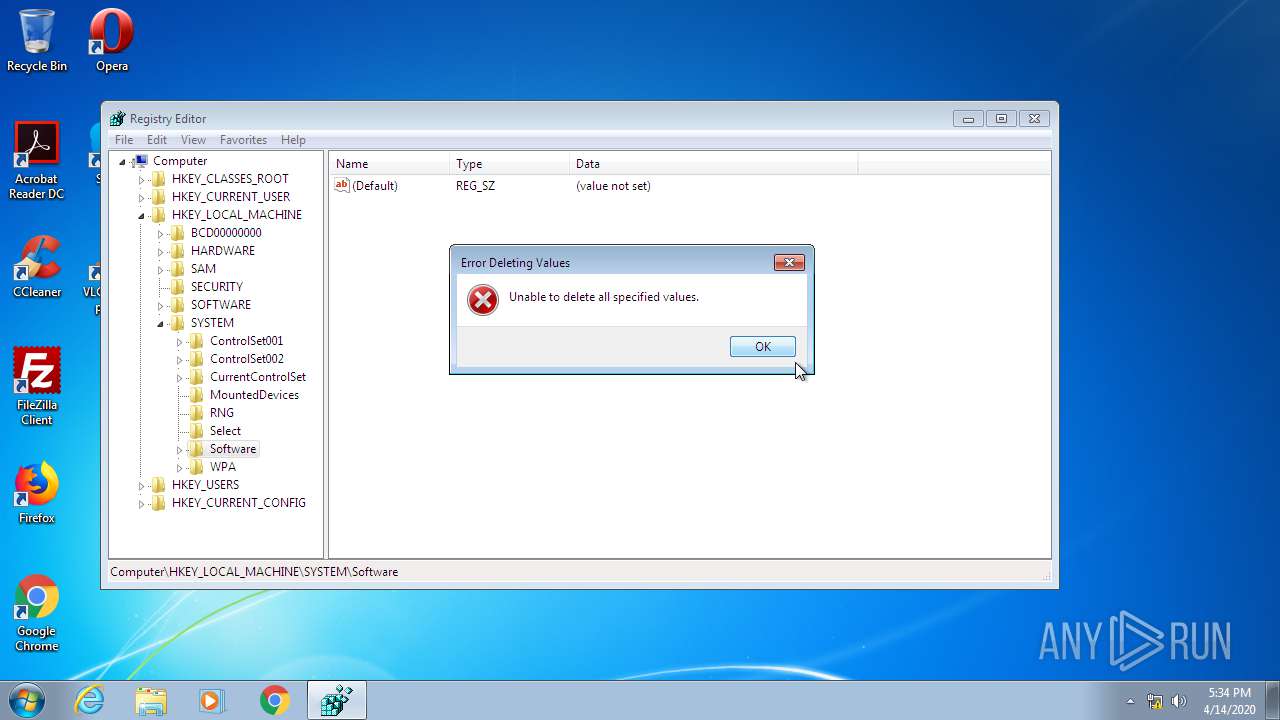
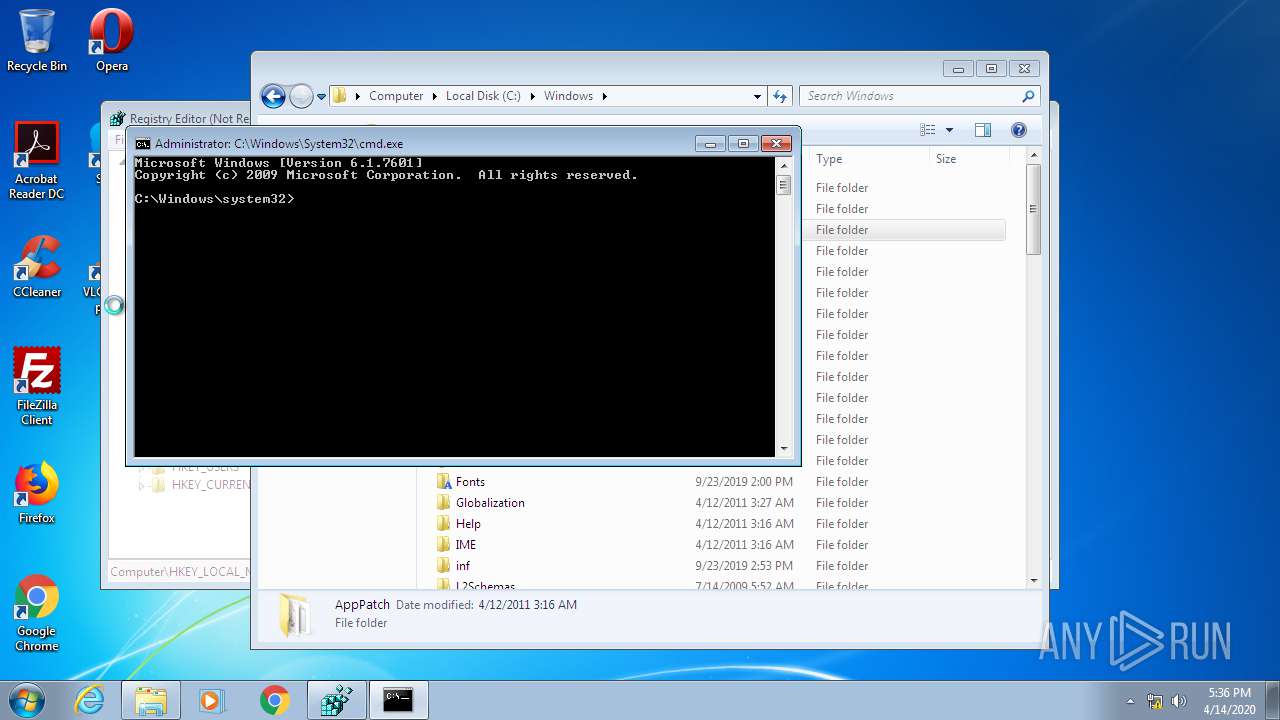
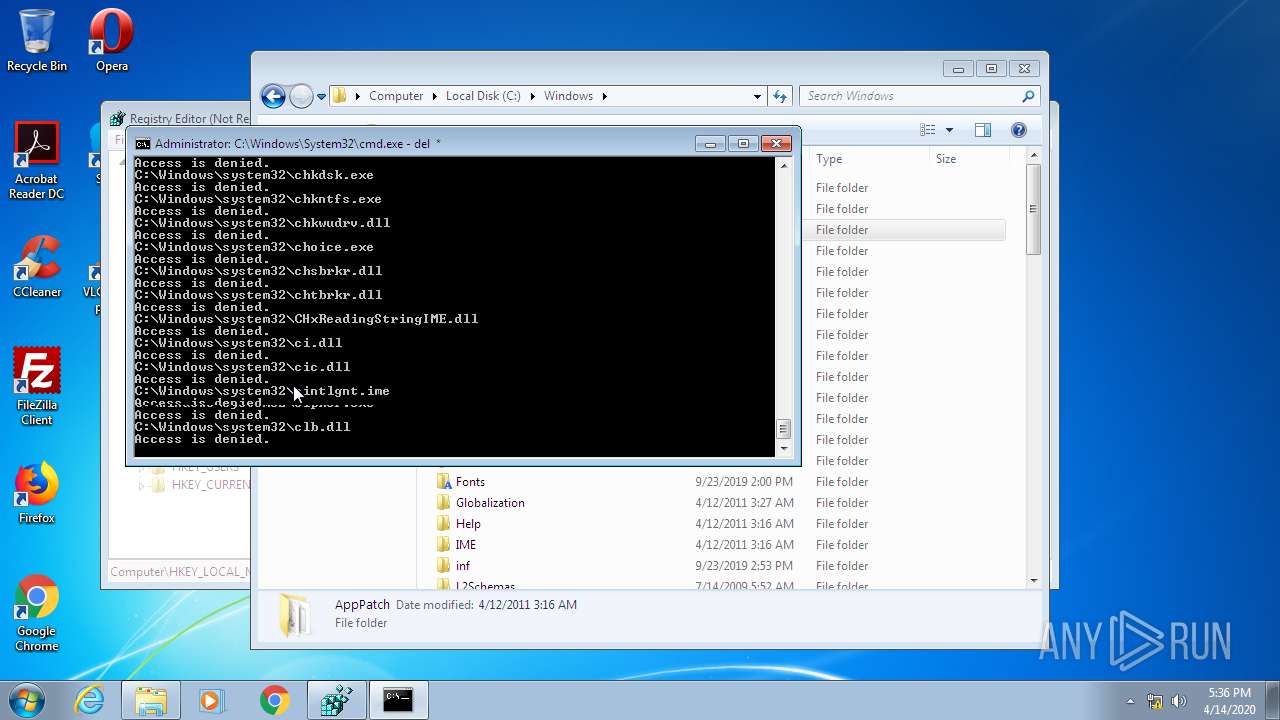
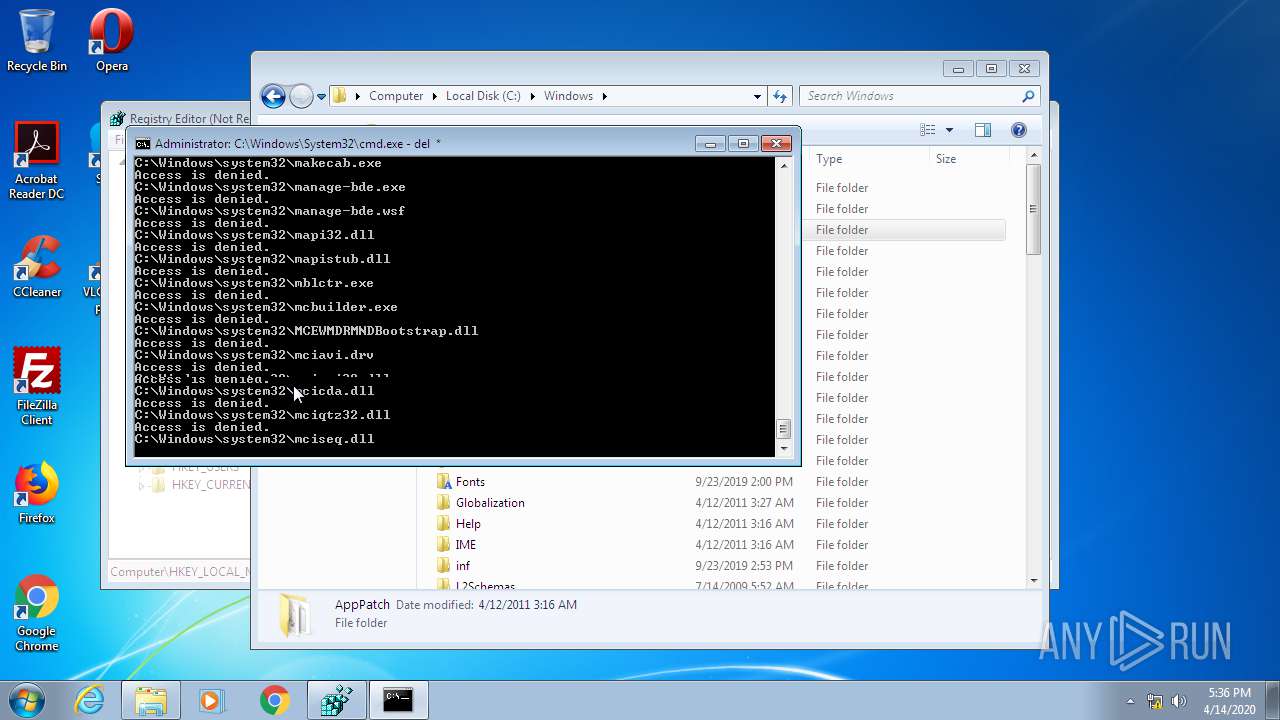
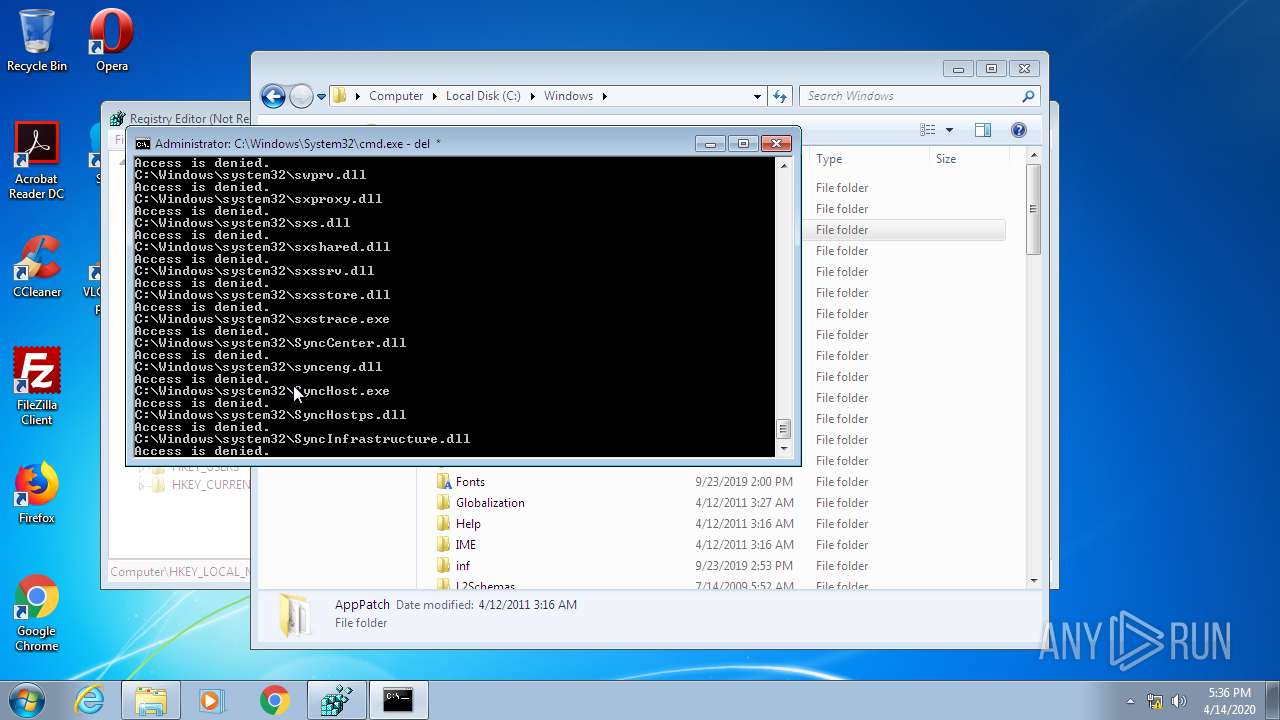
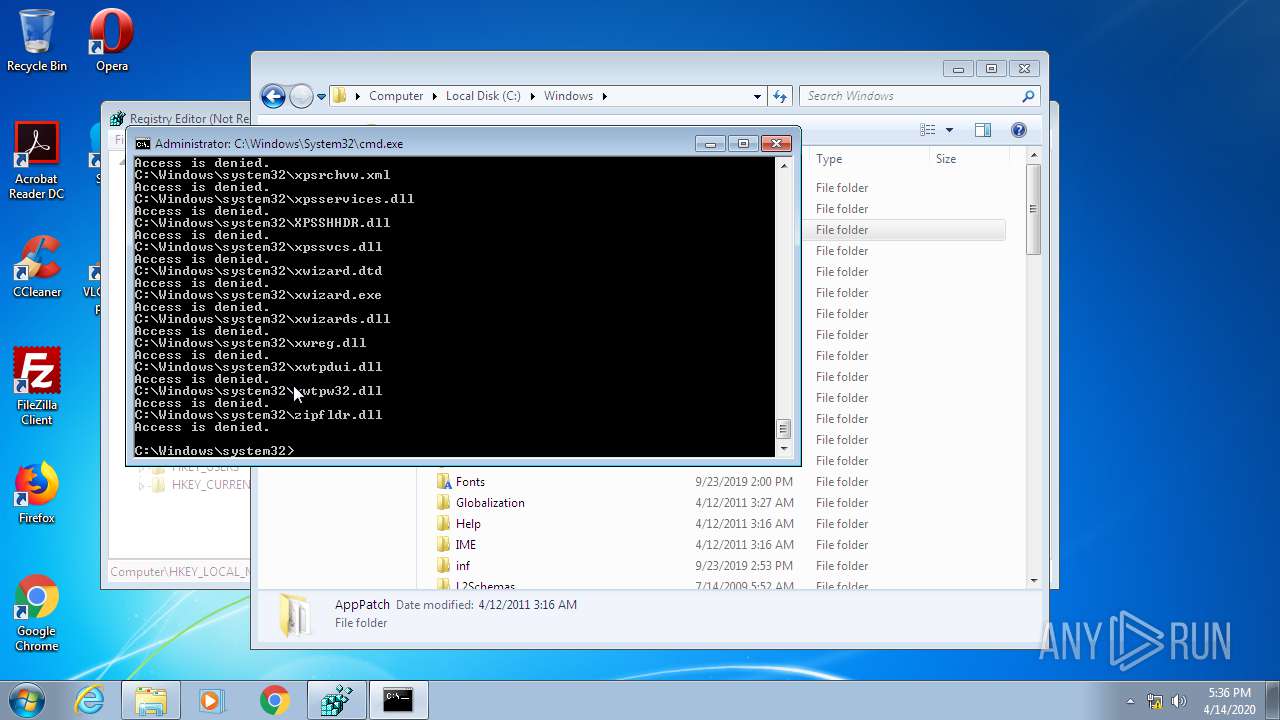
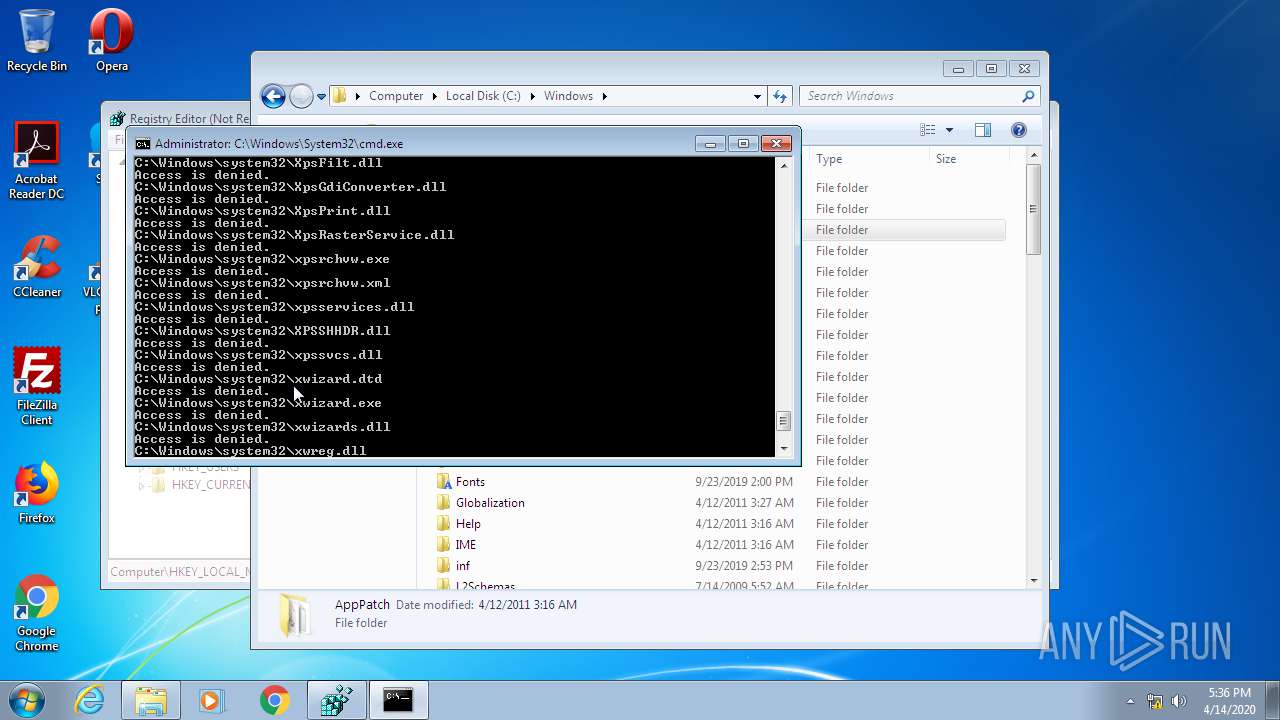
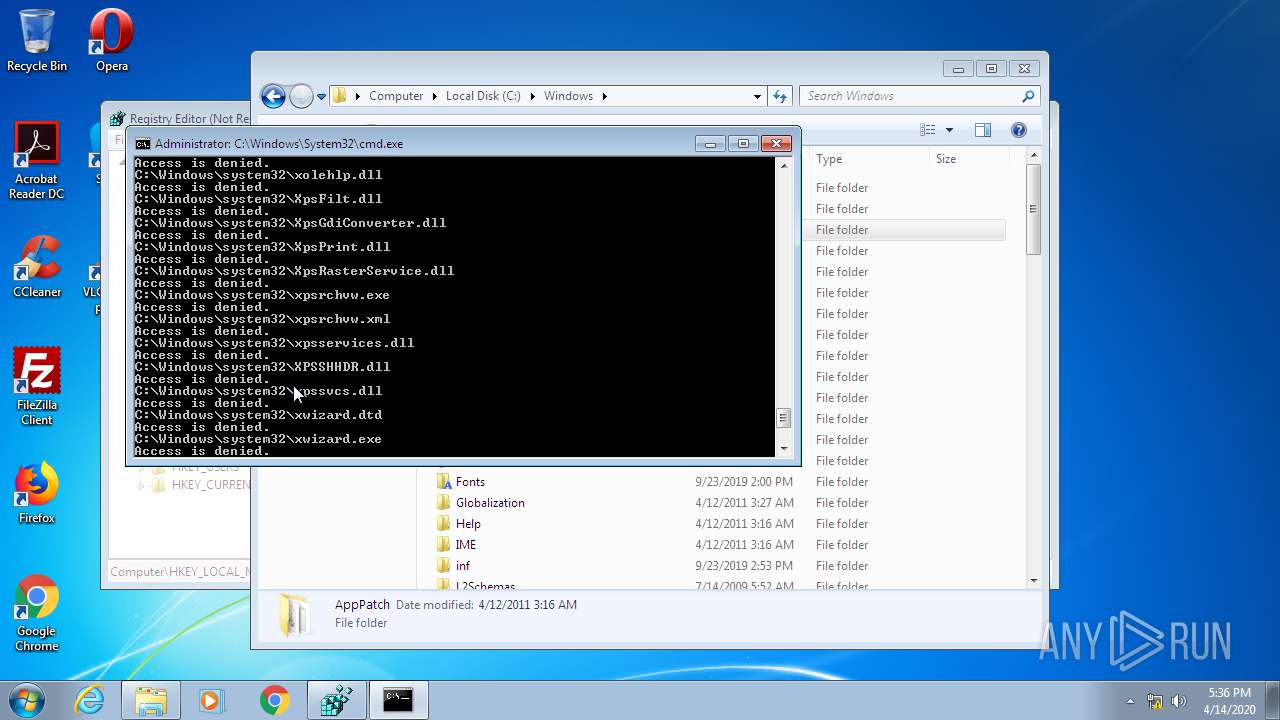
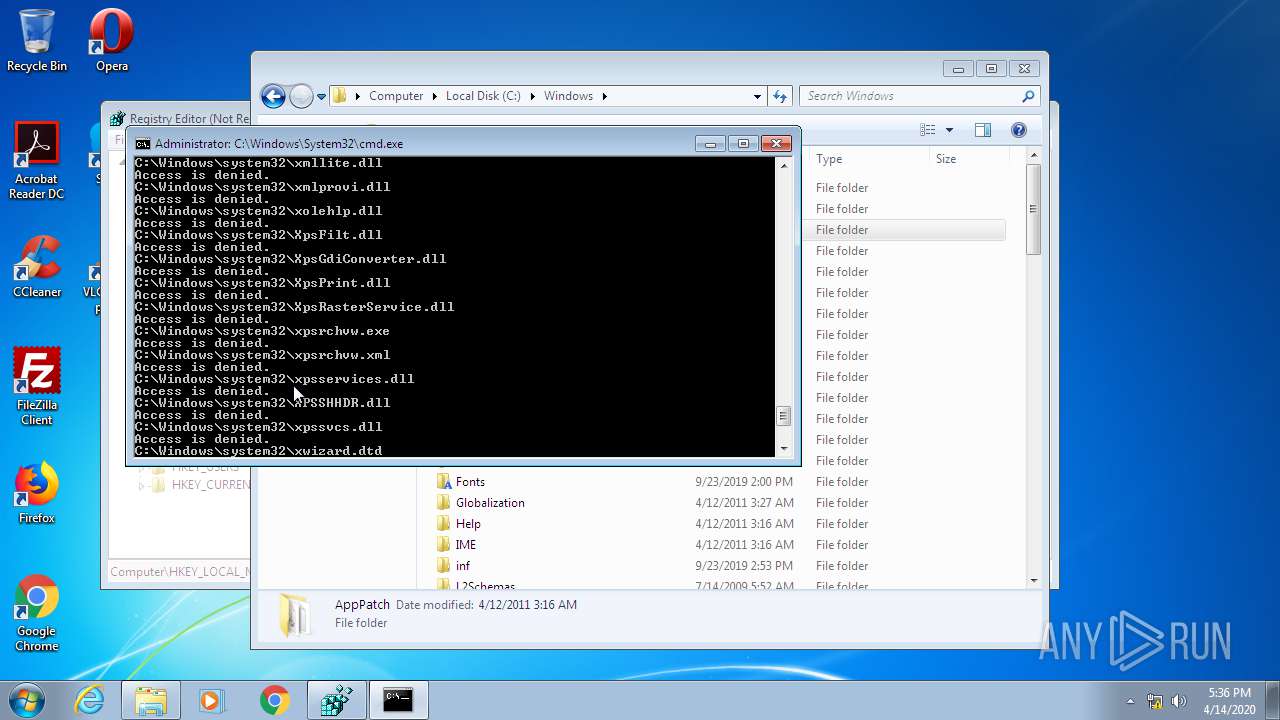
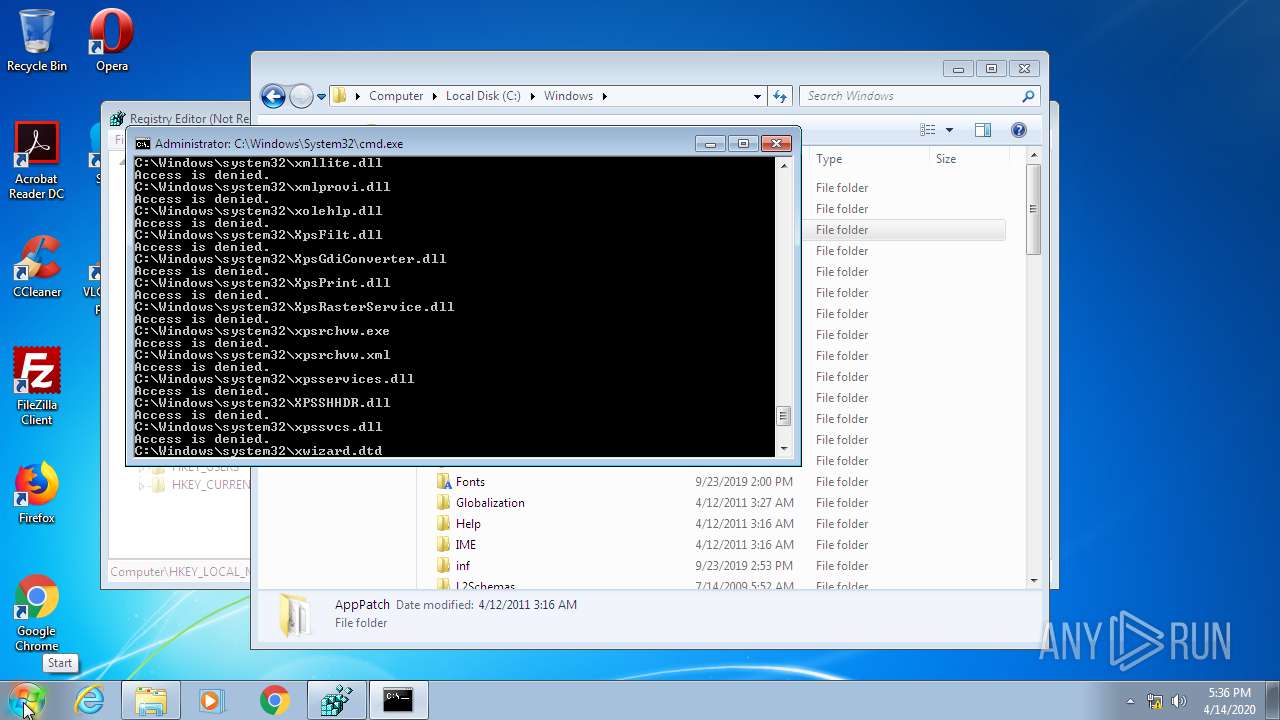
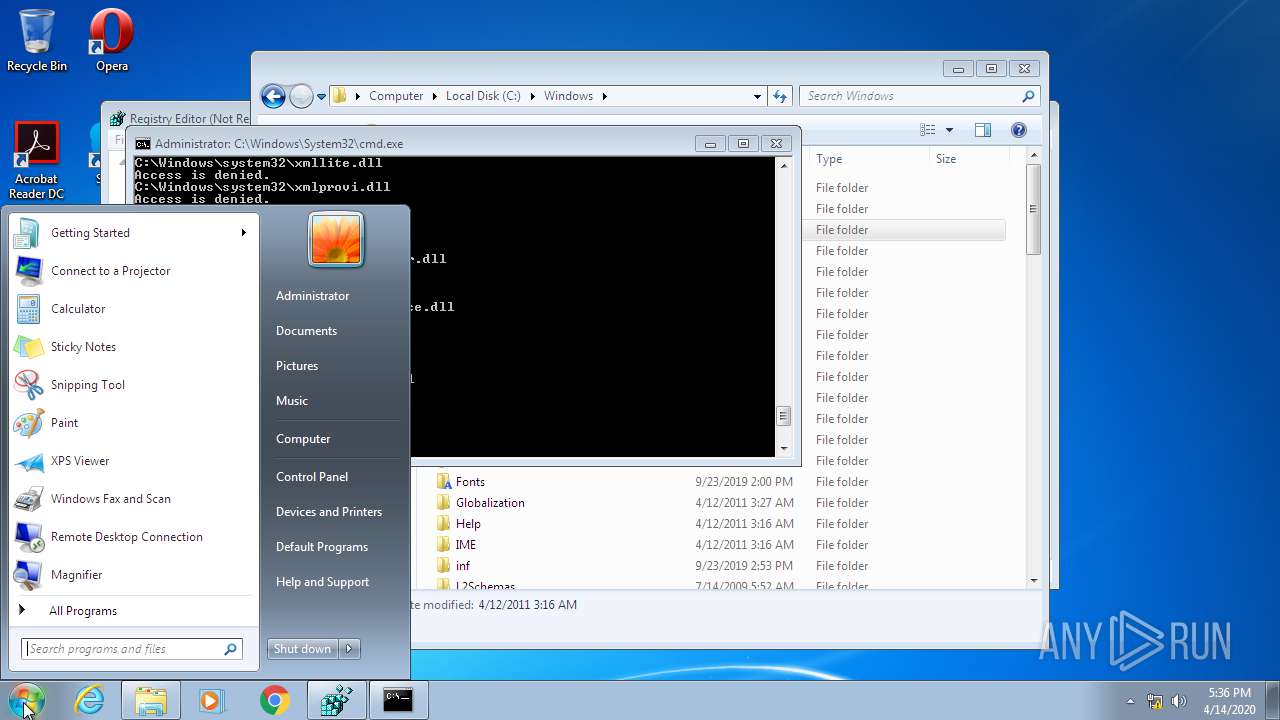
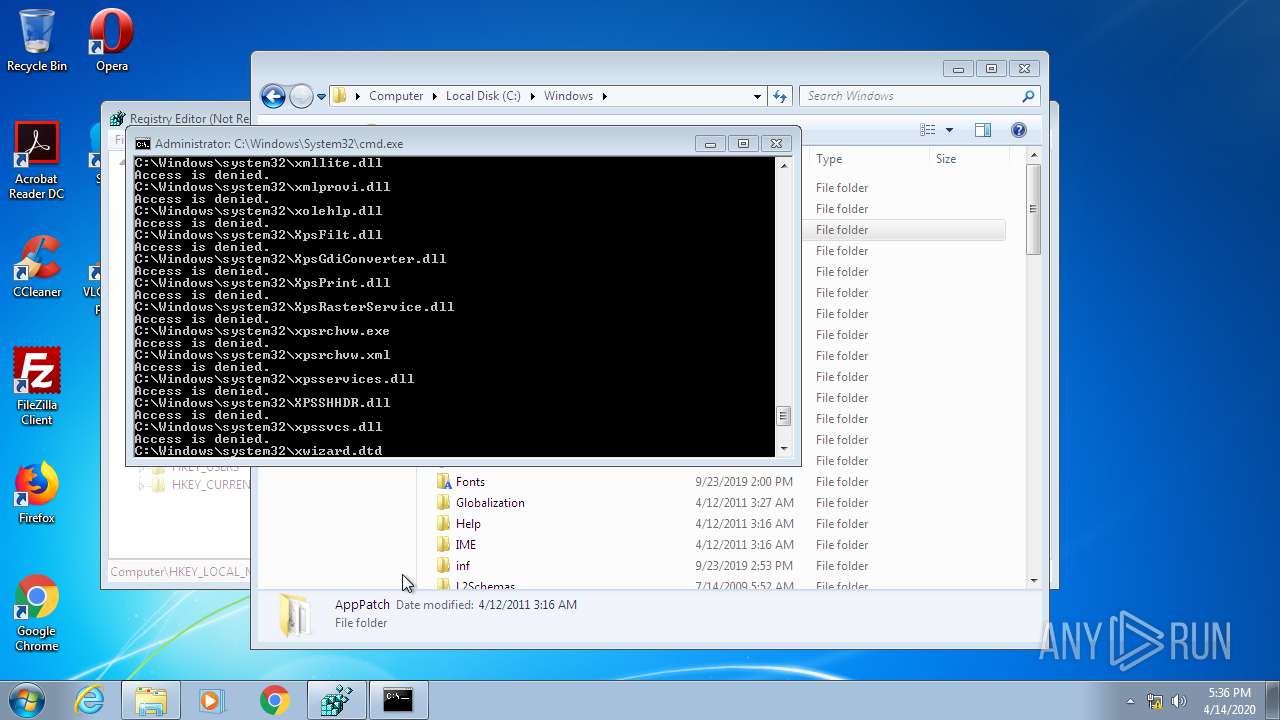
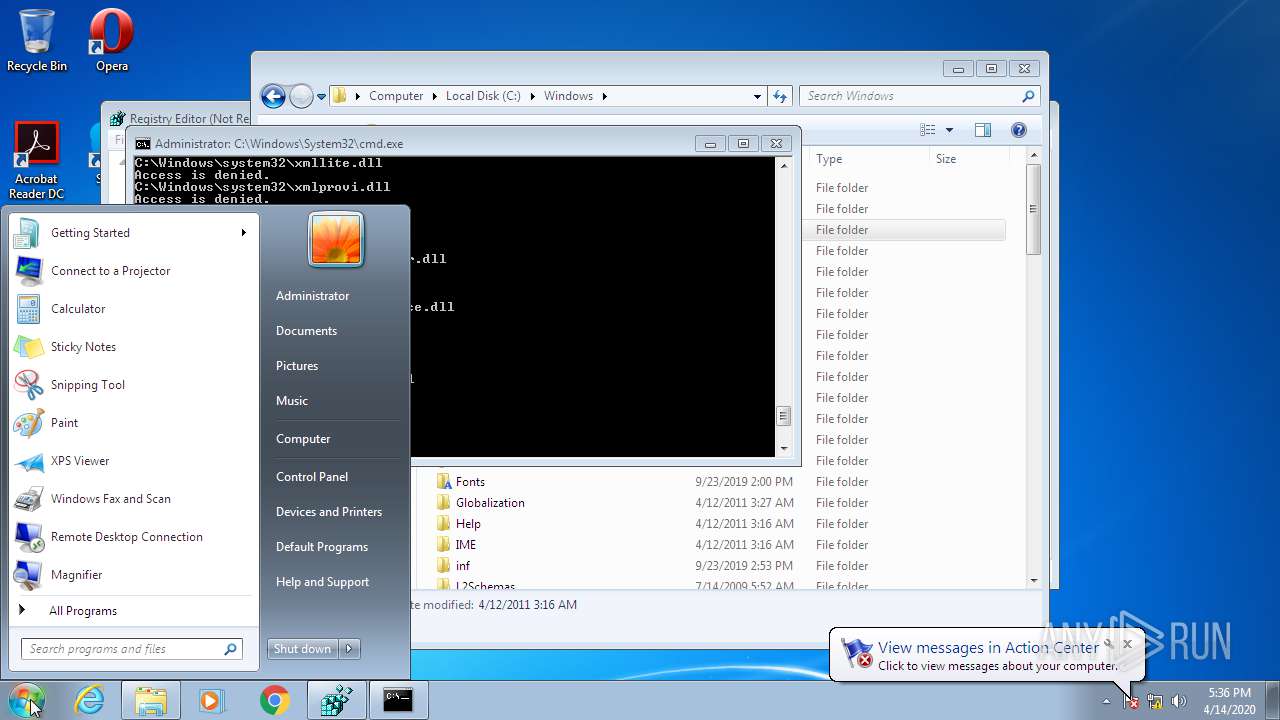
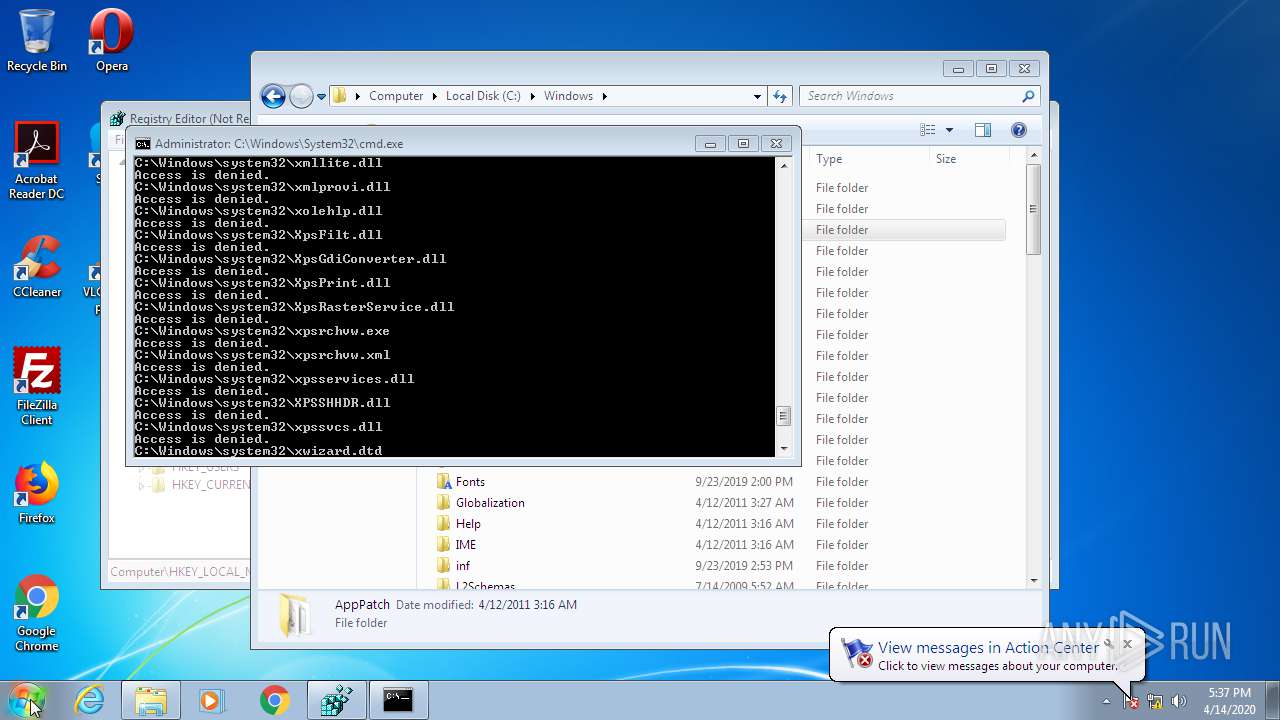
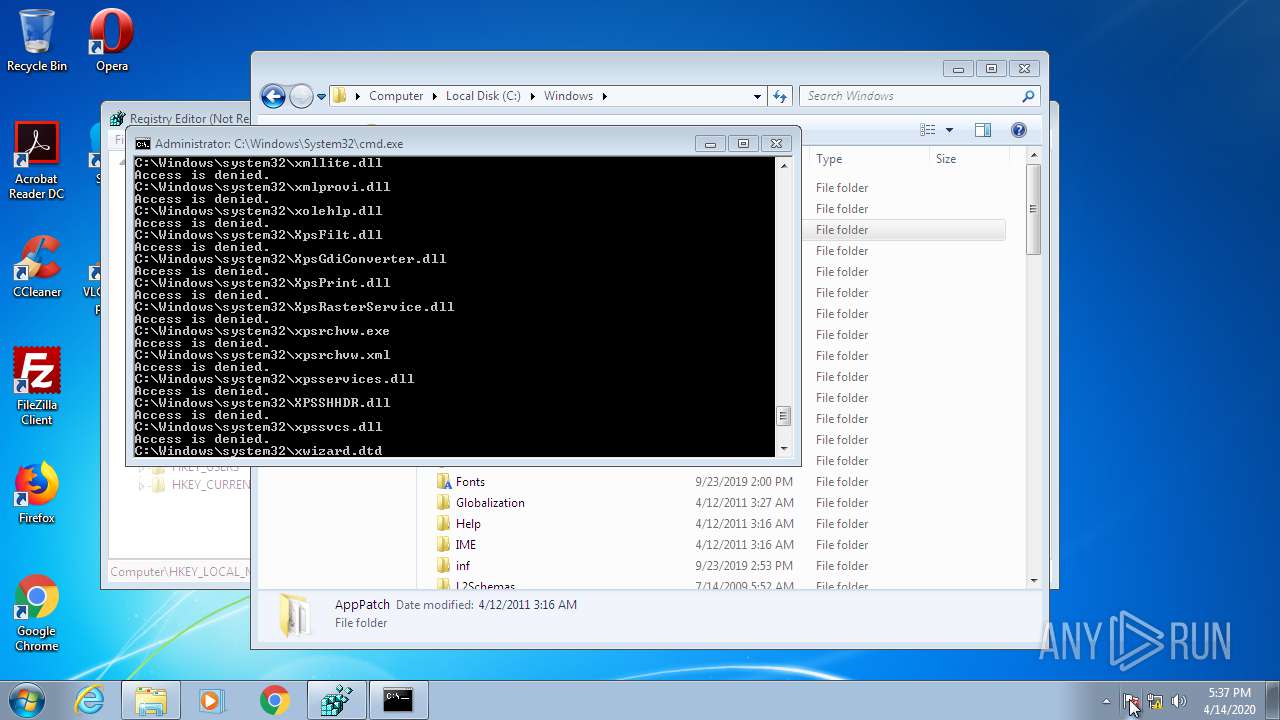
Removes files from Windows directory
- cmd.exe (PID: 944)
INFO
Manual execution by user
- ie4uinit.exe (PID: 2208)
- chrmstp.exe (PID: 852)
- ie4uinit.exe (PID: 3556)
- IMEKLMG.EXE (PID: 2976)
- IMEKLMG.EXE (PID: 3204)
- regedit.exe (PID: 2372)
- cmd.exe (PID: 944)
- verclsid.exe (PID: 2800)
- regedit.exe (PID: 2056)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | ASPack compressed Win32 Executable (generic) (92.6) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (3.1) |
| .exe | | | Win16/32 Executable Delphi generic (1.4) |
| .exe | | | Generic Win/DOS Executable (1.3) |
| .exe | | | DOS Executable Generic (1.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:20 00:22:17+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 374784 |
| InitializedDataSize: | 121344 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x7f001 |
| OSVersion: | 1 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
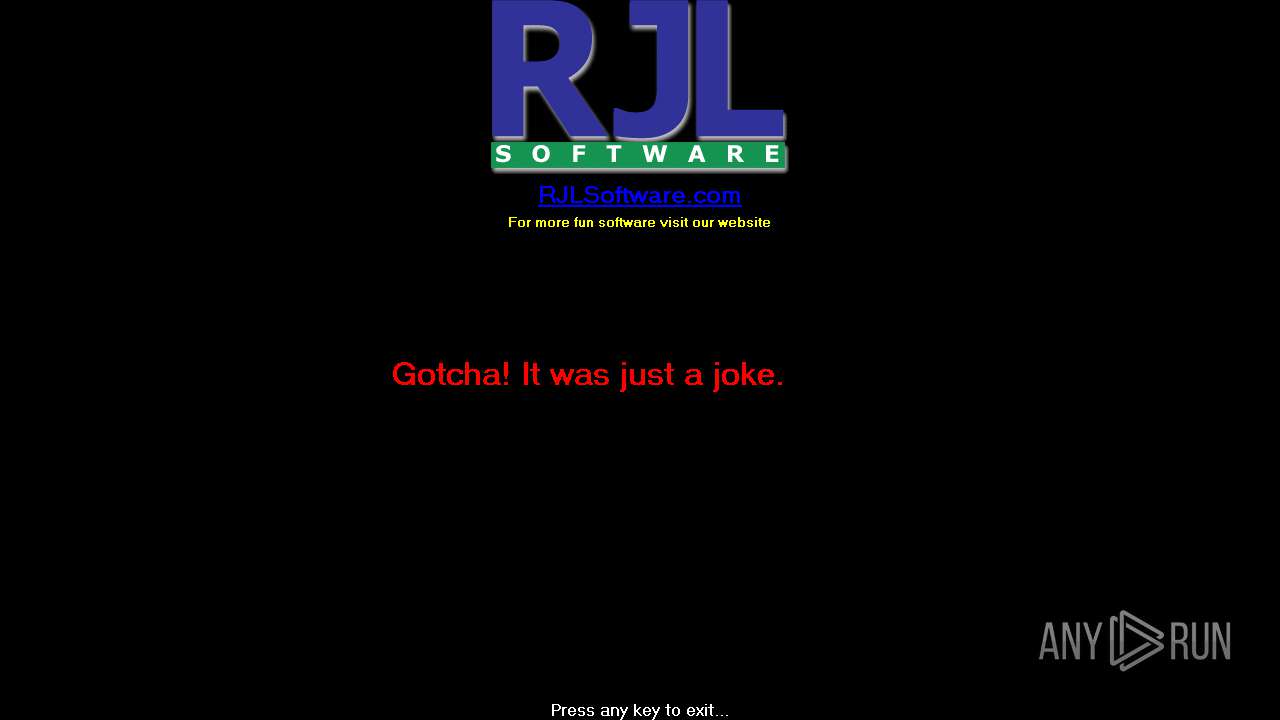
| CompanyName: | RJL Software, Inc. |
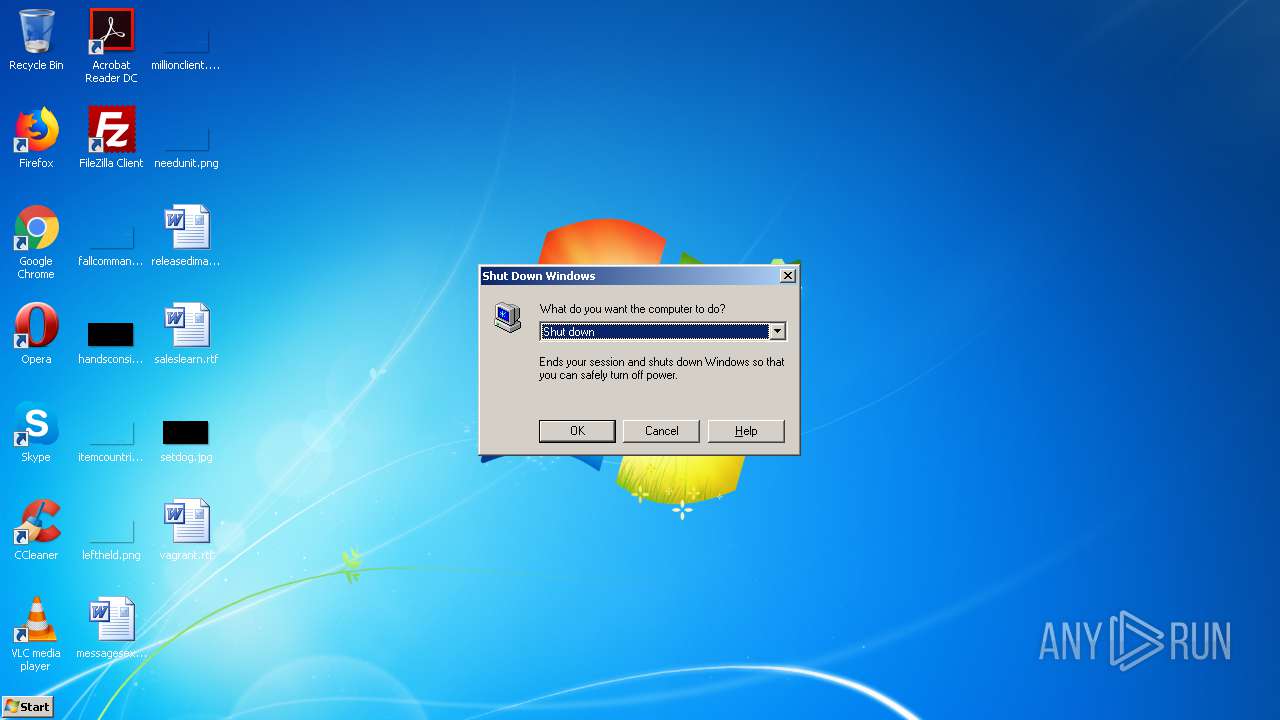
| FileDescription: | Simulates Windows shutdown |
| FileVersion: | 1.0.0.0 |
| InternalName: | Fake Shutdown |
| LegalCopyright: | Copyright 2001, RJL Software, Inc. |
| LegalTrademarks: | None. |
| OriginalFileName: | restart.exe |
| ProductName: | Fake Shutdown |
| ProductVersion: | 1.0.0.0 |
| Comments: | For more free fun software visit our website. |
| Website: | www.rjlsoftware.com |
| Email: | support@rjlsoftware.com |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 19-Jun-1992 22:22:17 |
| Detected languages: |
|
| CompanyName: | RJL Software, Inc. |
| FileDescription: | Simulates Windows shutdown |
| FileVersion: | 1.0.0.0 |
| InternalName: | Fake Shutdown |
| LegalCopyright: | Copyright 2001, RJL Software, Inc. |
| LegalTrademarks: | None. |
| OriginalFilename: | restart.exe |
| ProductName: | Fake Shutdown |
| ProductVersion: | 1.0.0.0 |
| Comments: | For more free fun software visit our website. |
| Website: | www.rjlsoftware.com |
| Email: | support@rjlsoftware.com |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0050 |
| Pages in file: | 0x0002 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x000F |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x001A |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000100 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 10 |
| Time date stamp: | 19-Jun-1992 22:22:17 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
CODE | 0x00001000 | 0x0005C000 | 0x00027A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.99895 |
DATA | 0x0005D000 | 0x00002000 | 0x00000A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.87984 |
BSS | 0x0005F000 | 0x00001000 | 0x00000000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.idata | 0x00060000 | 0x00002000 | 0x00000C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.76163 |
.tls | 0x00062000 | 0x00001000 | 0x00000000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rdata | 0x00063000 | 0x00001000 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0.20692 |
.reloc | 0x00064000 | 0x00006000 | 0x00000000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rsrc | 0x0006A000 | 0x00015000 | 0x00006400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.82563 |
.aspack | 0x0007F000 | 0x00002000 | 0x00001C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 6.09498 |
.data | 0x00081000 | 0x00001000 | 0x00000000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 3.36995 | 1080 | UNKNOWN | English - United States | RT_VERSION |
2 | 7.26277 | 308 | UNKNOWN | UNKNOWN | RT_CURSOR |
3 | 7.17121 | 308 | UNKNOWN | UNKNOWN | RT_CURSOR |
4 | 7.20236 | 308 | UNKNOWN | UNKNOWN | RT_CURSOR |
5 | 7.23119 | 308 | UNKNOWN | UNKNOWN | RT_CURSOR |
6 | 7.30823 | 308 | UNKNOWN | UNKNOWN | RT_CURSOR |
7 | 7.25935 | 308 | UNKNOWN | UNKNOWN | RT_CURSOR |
4085 | 7.51998 | 492 | UNKNOWN | UNKNOWN | RT_STRING |
4086 | 7.31172 | 408 | UNKNOWN | UNKNOWN | RT_STRING |
4087 | 7.00388 | 232 | UNKNOWN | UNKNOWN | RT_STRING |
Imports
advapi32.dll |
comctl32.dll |
gdi32.dll |
kernel32.dll |
ole32.dll |
oleaut32.dll |
shell32.dll |
user32.dll |
Total processes
99
Monitored processes
18
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 852 | "C:\Program Files\Google\Chrome\Application\75.0.3770.100\Installer\chrmstp.exe" --configure-user-settings --verbose-logging --system-level | C:\Program Files\Google\Chrome\Application\75.0.3770.100\Installer\chrmstp.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Google LLC Integrity Level: HIGH Description: Google Chrome Installer Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 944 | "C:\Windows\System32\cmd.exe" | C:\Windows\System32\cmd.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2052 | "C:\Program Files\Google\Chrome\Application\75.0.3770.100\Installer\chrmstp.exe" --type=crashpad-handler /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler --database=C:\Windows\TEMP\Crashpad --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=75.0.3770.100 --initial-client-data=0xd0,0xd8,0xdc,0xcc,0xe0,0xd42238,0xd42248,0xd42254 | C:\Program Files\Google\Chrome\Application\75.0.3770.100\Installer\chrmstp.exe | — | chrmstp.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: HIGH Description: Google Chrome Installer Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2056 | "C:\Windows\regedit.exe" | C:\Windows\regedit.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Editor Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2208 | "C:\Windows\System32\ie4uinit.exe" -UserConfig | C:\Windows\System32\ie4uinit.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: IE Per-User Initialization Utility Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2240 | "C:\Program Files\Common Files\Microsoft Shared\IME14\IMEKR\imkrmig.exe" | C:\Program Files\Common Files\Microsoft Shared\IME14\IMEKR\imkrmig.exe | — | IMEKLMG.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft IME 2010 Exit code: 0 Version: 14.0.4734.1000 Modules
| |||||||||||||||
| 2372 | "C:\Windows\regedit.exe" | C:\Windows\regedit.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Editor Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2444 | C:\Windows\System32\rundll32 C:\Windows\system32\migration\WininetPlugin.dll,MigrateCacheForUser /m | C:\Windows\System32\rundll32.exe | — | ie4uinit.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2800 | "C:\Windows\system32\verclsid.exe" /S /C {9E175B8B-F52A-11D8-B9A5-505054503030} /I {0C733A8A-2A1C-11CE-ADE5-00AA0044773D} /X 0x401 | C:\Windows\system32\verclsid.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Extension CLSID Verification Host Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2976 | "C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE" /SetPreload /JPN /Log | C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Office IME 2010 Exit code: 1 Version: 14.0.4734.1000 Modules
| |||||||||||||||
Total events
82 493
Read events
331
Write events
310
Delete events
81 852
Modification events
| (PID) Process: | (2208) ie4uinit.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Suggested Sites |
| Operation: | write | Name: | LogFileFolder |
Value: C:\Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low | |||
| (PID) Process: | (2208) ie4uinit.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\CLSID\{871C5380-42A0-1069-A2EA-08002B30309D}\ShellFolder |
| Operation: | write | Name: | Attributes |
Value: 0 | |||
| (PID) Process: | (2208) ie4uinit.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Active Setup\Installed Components\>{26923b43-4d38-484f-9b9e-de460746276c} |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (2208) ie4uinit.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\BrowserEmulation |
| Operation: | write | Name: | CVListTTL |
Value: 0 | |||
| (PID) Process: | (2208) ie4uinit.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\International\Scripts\3 |
| Operation: | write | Name: | IEPropFontName |
Value: Times New Roman | |||
| (PID) Process: | (2208) ie4uinit.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\International\Scripts\3 |
| Operation: | write | Name: | IEFixedFontName |
Value: Courier New | |||
| (PID) Process: | (2208) ie4uinit.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\International\Scripts\4 |
| Operation: | write | Name: | IEPropFontName |
Value: Times New Roman | |||
| (PID) Process: | (2208) ie4uinit.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\International\Scripts\4 |
| Operation: | write | Name: | IEFixedFontName |
Value: Courier New | |||
| (PID) Process: | (2208) ie4uinit.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\International\Scripts\5 |
| Operation: | write | Name: | IEPropFontName |
Value: Times New Roman | |||
| (PID) Process: | (2208) ie4uinit.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\International\Scripts\5 |
| Operation: | write | Name: | IEFixedFontName |
Value: Courier New | |||
Executable files
0
Suspicious files
6
Text files
62
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2208 | ie4uinit.exe | C:\Users\Administrator\AppData\Local\Temp\RGI5315.tmp | — | |
MD5:— | SHA256:— | |||
| 2208 | ie4uinit.exe | C:\Users\Administrator\AppData\Local\Temp\RGI5364.tmp | — | |
MD5:— | SHA256:— | |||
| 2208 | ie4uinit.exe | C:\Users\Administrator\AppData\Local\Temp\RGI5384.tmp | — | |
MD5:— | SHA256:— | |||
| 2208 | ie4uinit.exe | C:\Users\Administrator\AppData\Local\Temp\RGI548F.tmp | — | |
MD5:— | SHA256:— | |||
| 2208 | ie4uinit.exe | C:\Users\Administrator\AppData\Local\Temp\RGI54AF.tmp | — | |
MD5:— | SHA256:— | |||
| 2208 | ie4uinit.exe | C:\Users\Administrator\AppData\Local\Temp\RGI553D.tmp | — | |
MD5:— | SHA256:— | |||
| 3016 | taskhost.exe | C:\Users\Administrator\AppData\Local\Microsoft\Windows\WebCache\V01tmp.log | — | |
MD5:— | SHA256:— | |||
| 3016 | taskhost.exe | C:\Users\Administrator\AppData\Local\Microsoft\Windows\WebCache\V01.log | — | |
MD5:— | SHA256:— | |||
| 3016 | taskhost.exe | C:\Users\Administrator\AppData\Local\Microsoft\Windows\WebCache\WebCacheV01.dat | — | |
MD5:— | SHA256:— | |||
| 3636 | RunDll32.exe | C:\Users\Administrator\AppData\Local\Microsoft\Feeds Cache\X6UI5XYW\fwlink[1] | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report