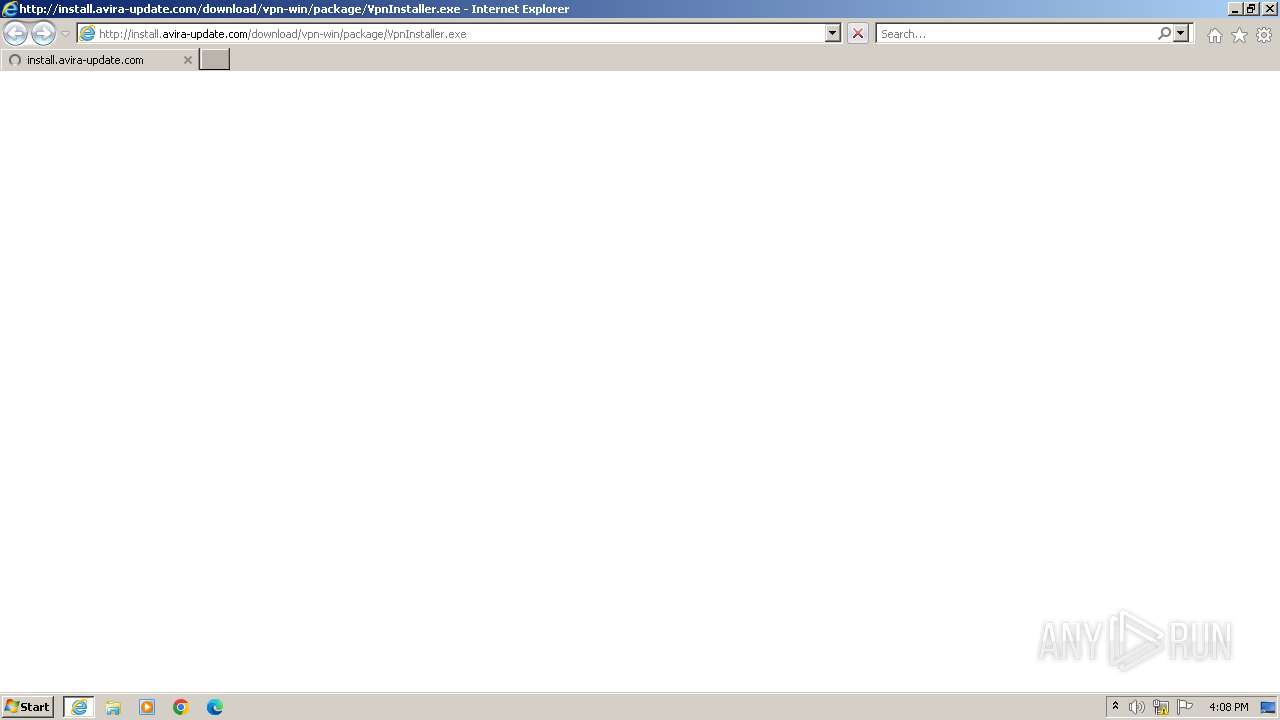
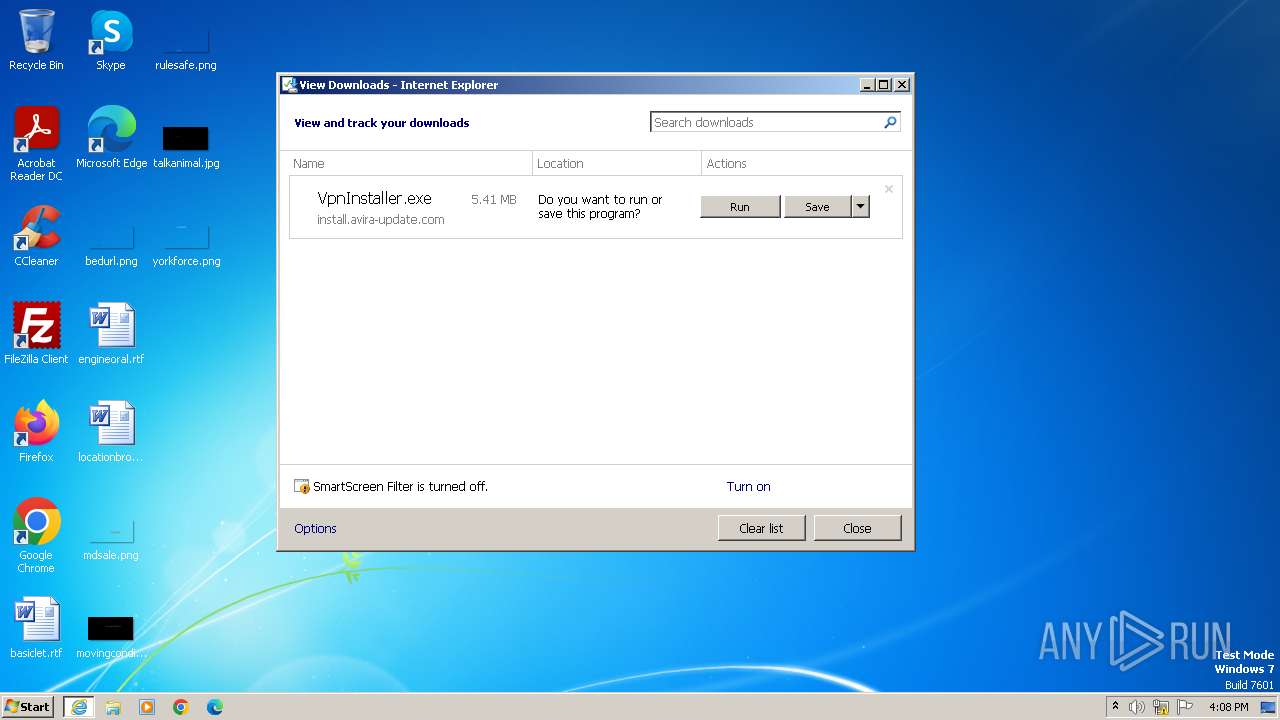
| URL: | install.avira-update.com/download/vpn-win/package/VpnInstaller.exe |
| Full analysis: | https://app.any.run/tasks/81563d66-34d6-47e0-be55-38e24858f85e |
| Verdict: | Malicious activity |
| Threats: | A loader is malicious software that infiltrates devices to deliver malicious payloads. This malware is capable of infecting victims’ computers, analyzing their system information, and installing other types of threats, such as trojans or stealers. Criminals usually deliver loaders through phishing emails and links by relying on social engineering to trick users into downloading and running their executables. Loaders employ advanced evasion and persistence tactics to avoid detection. |
| Analysis date: | April 29, 2024, 15:07:57 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | E0ABB956A7FD4EE1E4C2BEED3FD69A37 |
| SHA1: | 2EEE0BCBCC224BC4B001F322ED69B74636147E24 |
| SHA256: | B21BDDE2154119E82FE39A2924EB71F72AFCE172B09F13A7393BDB5E7676E4B2 |
| SSDEEP: | 3:KWirRDExKL1wFREJOXLNn:KWiJRJOXLN |
MALICIOUS
Drops the executable file immediately after the start
- VpnInstaller.exe (PID: 1368)
Actions looks like stealing of personal data
- Avira.VpnService.exe (PID: 2244)
SUSPICIOUS
Potential Corporate Privacy Violation
- iexplore.exe (PID: 4040)
Executable content was dropped or overwritten
- VpnInstaller.exe (PID: 1368)
Reads the Internet Settings
- VpnInstaller.exe (PID: 1368)
- Avira.WebAppHost.exe (PID: 568)
Reads security settings of Internet Explorer
- VpnInstaller.exe (PID: 1368)
- Avira.VpnService.exe (PID: 2244)
- Avira.WebAppHost.exe (PID: 568)
Reads settings of System Certificates
- VpnInstaller.exe (PID: 1368)
Checks Windows Trust Settings
- VpnInstaller.exe (PID: 1368)
Drops a system driver (possible attempt to evade defenses)
- VpnInstaller.exe (PID: 1368)
The process verifies whether the antivirus software is installed
- ns8419.tmp (PID: 1132)
- ns910B.tmp (PID: 1792)
- sc.exe (PID: 1788)
- Avira.VpnService.exe (PID: 2244)
- Avira.WebAppHost.exe (PID: 568)
- Avira.NetworkBlocker.exe (PID: 2624)
- VpnInstaller.exe (PID: 1368)
Creates or modifies Windows services
- VpnInstaller.exe (PID: 1368)
Process drops legitimate windows executable
- VpnInstaller.exe (PID: 1368)
Starts application with an unusual extension
- VpnInstaller.exe (PID: 1368)
Creates a software uninstall entry
- VpnInstaller.exe (PID: 1368)
Executes as Windows Service
- Avira.VpnService.exe (PID: 2244)
Starts SC.EXE for service management
- ns910B.tmp (PID: 1792)
The process creates files with name similar to system file names
- VpnInstaller.exe (PID: 1368)
Adds/modifies Windows certificates
- Avira.VpnService.exe (PID: 2244)
Searches for installed software
- Avira.VpnService.exe (PID: 2244)
Reads the Windows owner or organization settings
- Avira.VpnService.exe (PID: 2244)
INFO
Application launched itself
- iexplore.exe (PID: 3984)
Executable content was dropped or overwritten
- iexplore.exe (PID: 4040)
- iexplore.exe (PID: 3984)
Modifies the phishing filter of IE
- iexplore.exe (PID: 3984)
Drops the executable file immediately after the start
- iexplore.exe (PID: 4040)
- iexplore.exe (PID: 3984)
Checks supported languages
- wmpnscfg.exe (PID: 1872)
- ns8419.tmp (PID: 1132)
- ns910B.tmp (PID: 1792)
- Avira.VpnService.exe (PID: 2244)
- Avira.WebAppHost.exe (PID: 568)
- VpnInstaller.exe (PID: 1368)
- Avira.NetworkBlocker.exe (PID: 2624)
Reads the computer name
- wmpnscfg.exe (PID: 1872)
- Avira.VpnService.exe (PID: 2244)
- VpnInstaller.exe (PID: 1368)
- Avira.WebAppHost.exe (PID: 568)
- Avira.NetworkBlocker.exe (PID: 2624)
The process uses the downloaded file
- iexplore.exe (PID: 3984)
Manual execution by a user
- wmpnscfg.exe (PID: 1872)
- Avira.WebAppHost.exe (PID: 568)
Reads Environment values
- VpnInstaller.exe (PID: 1368)
- Avira.VpnService.exe (PID: 2244)
Checks proxy server information
- VpnInstaller.exe (PID: 1368)
Creates files or folders in the user directory
- VpnInstaller.exe (PID: 1368)
Reads the software policy settings
- VpnInstaller.exe (PID: 1368)
- Avira.VpnService.exe (PID: 2244)
Reads the machine GUID from the registry
- VpnInstaller.exe (PID: 1368)
- Avira.VpnService.exe (PID: 2244)
- Avira.WebAppHost.exe (PID: 568)
Creates files in the program directory
- VpnInstaller.exe (PID: 1368)
- Avira.VpnService.exe (PID: 2244)
Reads CPU info
- Avira.VpnService.exe (PID: 2244)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
51
Monitored processes
11
Malicious processes
5
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 568 | "C:\Program Files\Avira\VPN\Avira.WebAppHost.exe" /migrateSettings | C:\Program Files\Avira\VPN\Avira.WebAppHost.exe | — | explorer.exe | |||||||||||
User: admin Company: Avira Operations GmbH & Co. KG Integrity Level: MEDIUM Description: Avira Phantom VPN Exit code: 0 Version: 2.44.1.19926 Modules
| |||||||||||||||
| 1132 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\nsistemp\nso8129.tmp\ns8419.tmp" "C:\Program Files\Avira\VPN\OpenVpn\TAP\i386\tapinstall.exe" tap_remove "tap0901" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\nsistemp\nso8129.tmp\ns8419.tmp | — | VpnInstaller.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 3221225501 Modules
| |||||||||||||||
| 1368 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\VpnInstaller.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\VpnInstaller.exe | iexplore.exe | ||||||||||||
User: admin Company: Avira Operations GmbH & Co. KG Integrity Level: HIGH Description: Avira Phantom VPN Installer Exit code: 0 Version: 2.44.1.19908 Modules
| |||||||||||||||
| 1432 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\VpnInstaller.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\VpnInstaller.exe | — | iexplore.exe | |||||||||||
User: admin Company: Avira Operations GmbH & Co. KG Integrity Level: MEDIUM Description: Avira Phantom VPN Installer Exit code: 3221226540 Version: 2.44.1.19908 Modules
| |||||||||||||||
| 1788 | "C:\Windows\system32\sc.exe" failure AviraPhantomVPN reset= 86400 actions= restart/5000/restart/10000//1000 | C:\Windows\System32\sc.exe | — | ns910B.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1792 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\nsistemp\nso8129.tmp\ns910B.tmp" "C:\Windows\system32\sc.exe" failure AviraPhantomVPN reset= 86400 actions= restart/5000/restart/10000//1000 | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\nsistemp\nso8129.tmp\ns910B.tmp | — | VpnInstaller.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1872 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2244 | "C:\Program Files\Avira\VPN\Avira.VpnService.exe" | C:\Program Files\Avira\VPN\Avira.VpnService.exe | services.exe | ||||||||||||
User: SYSTEM Company: Avira Operations GmbH & Co. KG Integrity Level: SYSTEM Description: VpnService Version: 2.44.1.19908 Modules
| |||||||||||||||
| 2624 | "C:\Program Files\Avira\VPN\Avira.NetworkBlocker.exe" delete | C:\Program Files\Avira\VPN\Avira.NetworkBlocker.exe | — | Avira.VpnService.exe | |||||||||||
User: SYSTEM Integrity Level: SYSTEM Exit code: 0 Modules
| |||||||||||||||
| 3984 | "C:\Program Files\Internet Explorer\iexplore.exe" "install.avira-update.com/download/vpn-win/package/VpnInstaller.exe" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
26 398
Read events
26 154
Write events
194
Delete events
50
Modification events
| (PID) Process: | (3984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: 149843536 | |||
| (PID) Process: | (3984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31103559 | |||
| (PID) Process: | (3984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 450319786 | |||
| (PID) Process: | (3984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31103559 | |||
| (PID) Process: | (3984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
65
Suspicious files
33
Text files
367
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4040 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\VpnInstaller.exe.mkxrjhq.partial | executable | |
MD5:9B41201BB6D9B439103B7A2FB1D41038 | SHA256:F6D4A140924AF35DFBC63729736310737C6356052094B19FDDCB6E88D7E210ED | |||
| 1368 | VpnInstaller.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\064D75DF60A1456F63CEF9F347BAA00B_56E55841A2CD721637450FF62327CD0F | binary | |
MD5:593918EFD3BC73CFF5C8B9373485F5DE | SHA256:FA935FCEC87A808FB9A41C5F63C2C5C24E8F132A71A4DEAA889E3115CC17CD8A | |||
| 1368 | VpnInstaller.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\nsistemp\nso8129.tmp\base64.dll | executable | |
MD5:AC6FB776262B63562C00374392FE1C55 | SHA256:7E10EF2723A50B7346449F8BB39EFAB8A99E2815D33D311ECB8112734F91519D | |||
| 1368 | VpnInstaller.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\064D75DF60A1456F63CEF9F347BAA00B_56E55841A2CD721637450FF62327CD0F | der | |
MD5:530303F2D8B012042D4322AD6714607E | SHA256:61CF6FF378CEE621E5D55C5E99B9168267DCDCF3836DBF8D20F3FA00430CFF71 | |||
| 1368 | VpnInstaller.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_430EA0912164D1B129D6E1DC07C63959 | binary | |
MD5:199952F878179E34CFBEF7203E80C755 | SHA256:82EE9833621904E8F803F234ADDE39B29F1C611AA816DB80A179998A7DEC4BA9 | |||
| 1368 | VpnInstaller.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\nsistemp\nso8129.tmp\System.dll | executable | |
MD5:0063D48AFE5A0CDC02833145667B6641 | SHA256:AC9DFE3B35EA4B8932536ED7406C29A432976B685CC5322F94EF93DF920FEDE7 | |||
| 3984 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF4C2AE11D8CEBD426.TMP | gmc | |
MD5:D99634AE19F764BD328E9925EC95010F | SHA256:03FBD0639E1752F4B2BBA0DF732B0C1C2D839163B33C97D01C6F19B32B9F50A5 | |||
| 1368 | VpnInstaller.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\nsistemp\nso8129.tmp\FindProcDLL.dll | executable | |
MD5:75E7351A0F836B8659E6F315683C29F7 | SHA256:7FFC549E7F679A08C77FA230654B77CDFFB3444296BB7C6B8B5769DB374B61EE | |||
| 1368 | VpnInstaller.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:73EEFB684C6B5861795AF4AF30BEB445 | SHA256:99CC097E19EDB3461EB9ECADC00CFFE87BD5110785F13120A590E6A2BA608CF1 | |||
| 1368 | VpnInstaller.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\nsistemp\nst8149.tmp | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
19
DNS requests
11
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4040 | iexplore.exe | GET | 200 | 23.199.214.7:80 | http://install.avira-update.com/download/vpn-win/package/VpnInstaller.exe | unknown | — | — | unknown |
1368 | VpnInstaller.exe | GET | 304 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?b59702af0c46080c | unknown | — | — | unknown |
1368 | VpnInstaller.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA0HeCoTP8b5pXKW4TH%2F0Xk%3D | unknown | — | — | unknown |
3984 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
1368 | VpnInstaller.exe | GET | 200 | 192.229.221.95:80 | http://status.geotrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS6FKmrgWTGr7Q8nSk4Oub50ler6QQUlE%2FUXYvkpOKmgP792PkA76O%2BAlcCEAgCQr2BWQcpQeKtOv5EuBE%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4040 | iexplore.exe | 23.199.214.7:80 | install.avira-update.com | AKAMAI-AS | DE | unknown |
1368 | VpnInstaller.exe | 35.190.25.25:443 | api.mixpanel.com | GOOGLE | US | whitelisted |
1368 | VpnInstaller.exe | 199.232.210.172:80 | ctldl.windowsupdate.com | FASTLY | US | unknown |
1368 | VpnInstaller.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
2244 | Avira.VpnService.exe | 18.194.64.246:443 | api.phantom.avira-vpn.com | AMAZON-02 | DE | unknown |
2244 | Avira.VpnService.exe | 3.122.47.82:443 | api.phantom.avira-vpn.com | AMAZON-02 | DE | unknown |
2244 | Avira.VpnService.exe | 35.190.25.25:443 | api.mixpanel.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
install.avira-update.com |
| unknown |
api.mixpanel.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
status.geotrust.com |
| whitelisted |
api.phantom.avira-vpn.com |
| unknown |
r20swj13mr.microsoft.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
dispatch.avira-update.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4040 | iexplore.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |