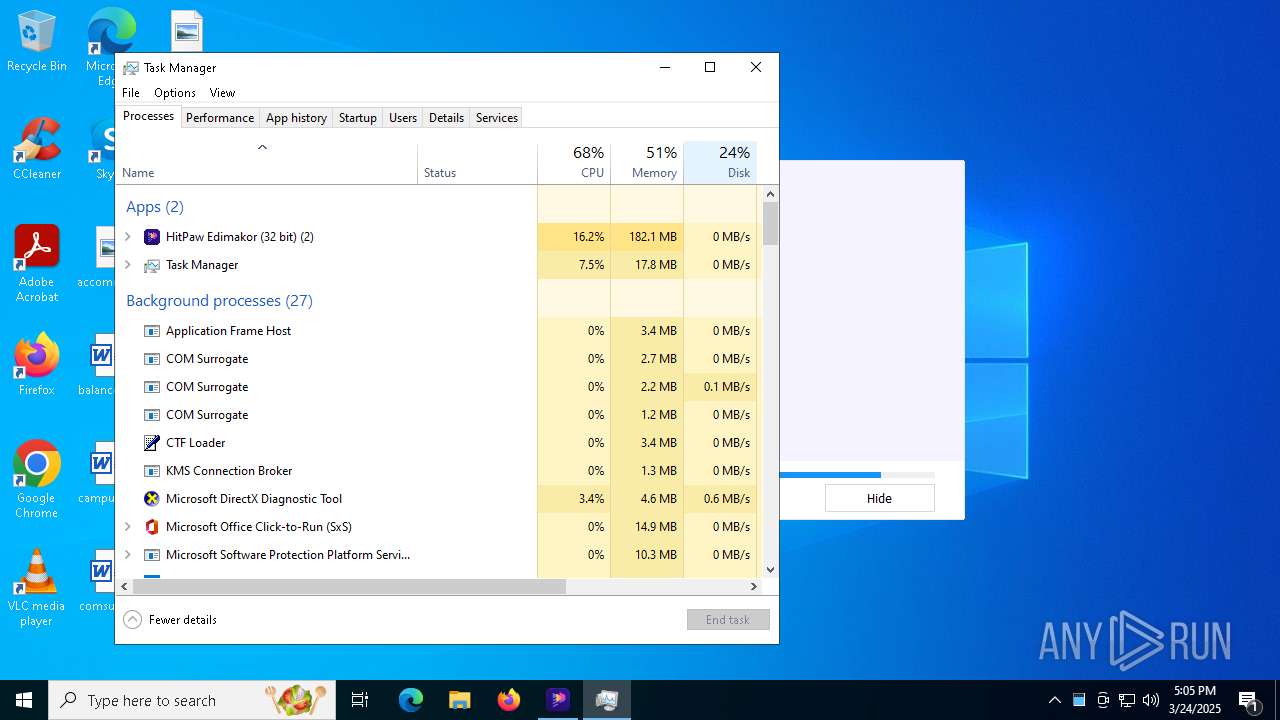
| File name: | hitpaw-edimakor-full_11742816193815166301.exe |
| Full analysis: | https://app.any.run/tasks/0d8f5900-c673-469c-bed7-853763e52696 |
| Verdict: | Malicious activity |
| Analysis date: | March 24, 2025, 17:03:13 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed, 3 sections |
| MD5: | 11C21DE37E98A41BFC615520C3B8093E |
| SHA1: | A8FBFC56D74AB77924B87BF2D0225BA29C245929 |
| SHA256: | B1FA18F25ED6F8137E8ADECF59F3052B9AB63A4E22E190D0611F9A5F1705B174 |
| SSDEEP: | 98304:bm2JbZKs1PyDsUPO0RHYxuyfpCd5iIQto65E0KqLvyInJl1Fg2tJ6X5TCyliloYY:hVFu |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
- hitpaw-edimakor-full_11742816193815166301.exe (PID: 7148)
- hitpawedimakor_hitpawem_3.6.1.tmp (PID: 7964)
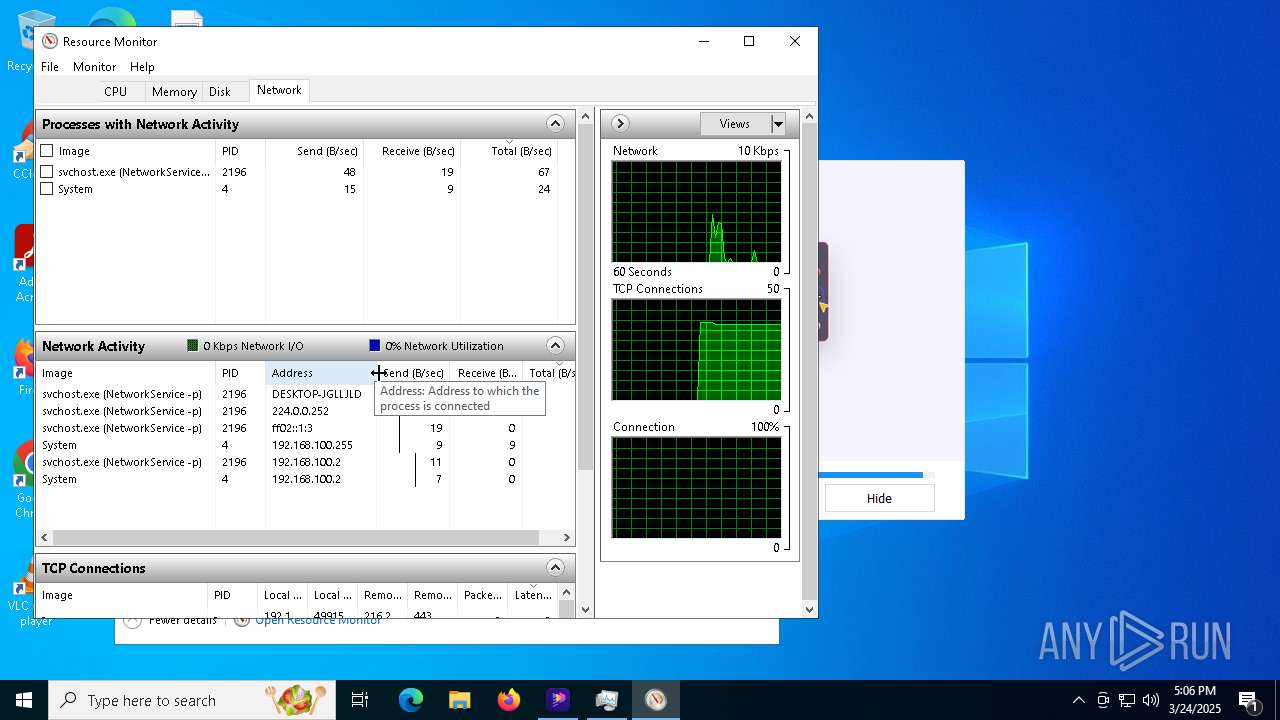
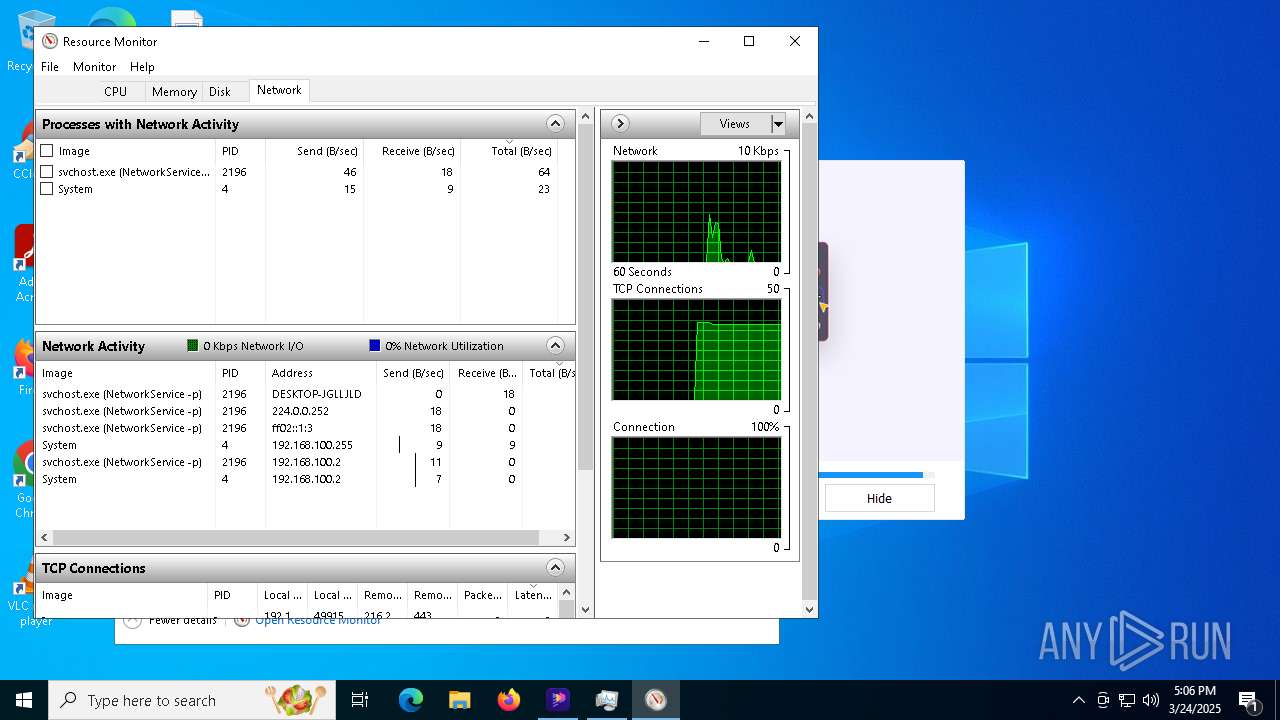
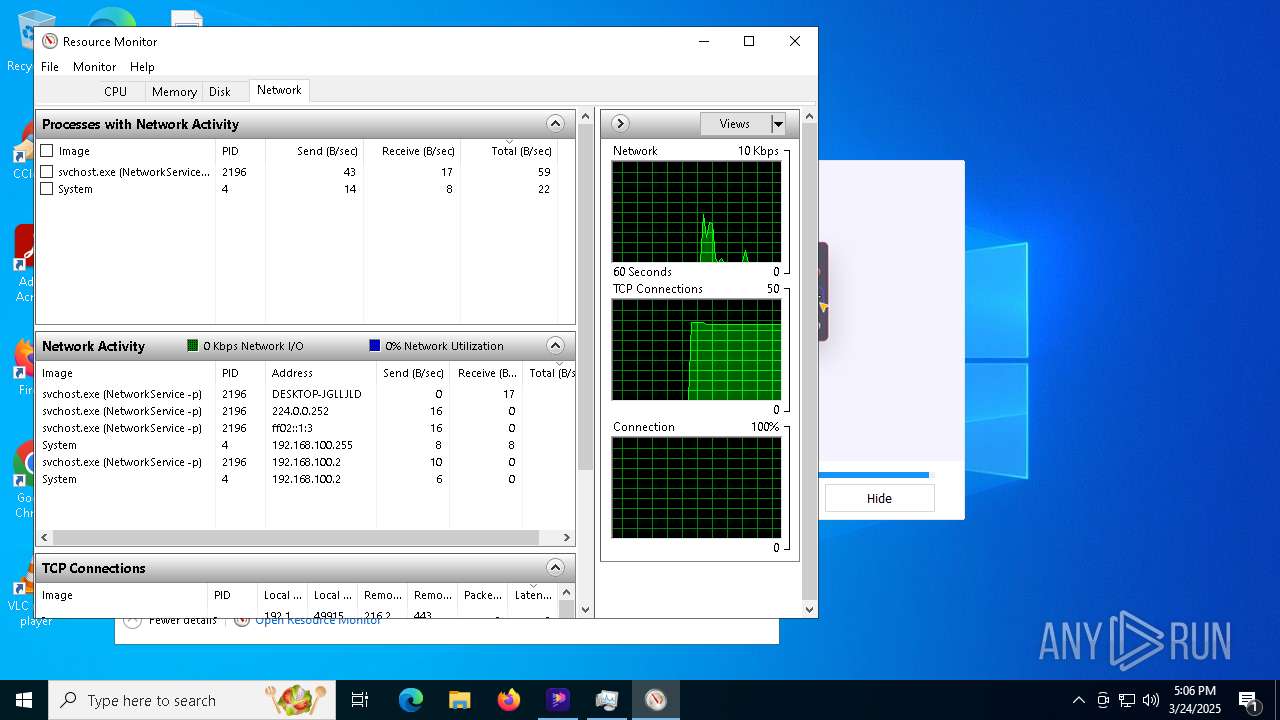
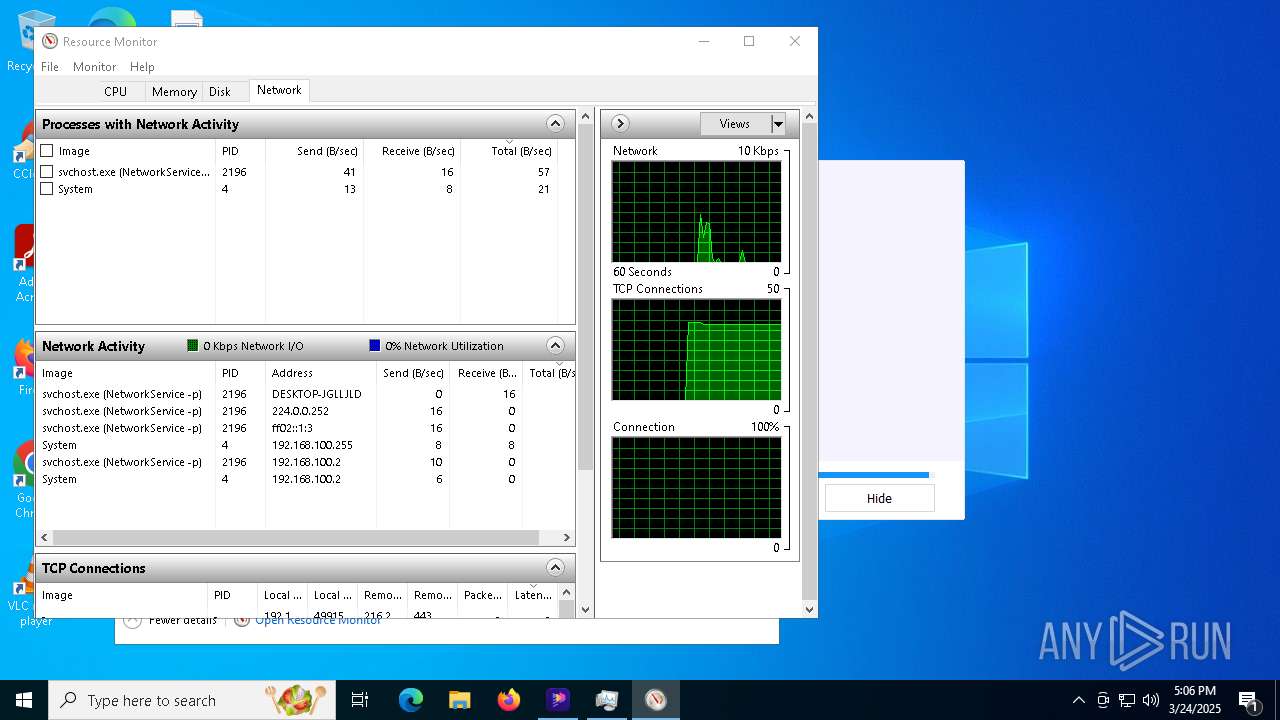
Checks for external IP
- hitpaw-edimakor-full_11742816193815166301.exe (PID: 7148)
- svchost.exe (PID: 2196)
Potential Corporate Privacy Violation
- hitpaw-edimakor-full_11742816193815166301.exe (PID: 7148)
Executable content was dropped or overwritten
- hitpawedimakor_hitpawem_3.6.1.exe (PID: 4428)
- hitpawedimakor_hitpawem_3.6.1.tmp (PID: 7964)
Uses TASKKILL.EXE to kill process
- hitpawedimakor_hitpawem_3.6.1.tmp (PID: 7964)
Get information on the list of running processes
- hitpawedimakor_hitpawem_3.6.1.tmp (PID: 7964)
- cmd.exe (PID: 4376)
- cmd.exe (PID: 3828)
Drops 7-zip archiver for unpacking
- hitpawedimakor_hitpawem_3.6.1.tmp (PID: 7964)
Starts CMD.EXE for commands execution
- hitpawedimakor_hitpawem_3.6.1.tmp (PID: 7964)
Process drops legitimate windows executable
- hitpawedimakor_hitpawem_3.6.1.tmp (PID: 7964)
The process drops C-runtime libraries
- hitpawedimakor_hitpawem_3.6.1.tmp (PID: 7964)
The process checks if it is being run in the virtual environment
- perfmon.exe (PID: 6972)
INFO
The sample compiled with english language support
- hitpaw-edimakor-full_11742816193815166301.exe (PID: 7148)
- hitpawedimakor_hitpawem_3.6.1.tmp (PID: 7964)
Reads the computer name
- hitpaw-edimakor-full_11742816193815166301.exe (PID: 7148)
- hitpawedimakor_hitpawem_3.6.1.tmp (PID: 7964)
- perfmon.exe (PID: 6972)
Reads the machine GUID from the registry
- hitpaw-edimakor-full_11742816193815166301.exe (PID: 7148)
Checks proxy server information
- hitpaw-edimakor-full_11742816193815166301.exe (PID: 7148)
- BackgroundTransferHost.exe (PID: 6800)
Checks supported languages
- hitpaw-edimakor-full_11742816193815166301.exe (PID: 7148)
- ShellExperienceHost.exe (PID: 8140)
- hitpawedimakor_hitpawem_3.6.1.exe (PID: 4428)
- hitpawedimakor_hitpawem_3.6.1.tmp (PID: 7964)
- perfmon.exe (PID: 6972)
Creates files or folders in the user directory
- hitpaw-edimakor-full_11742816193815166301.exe (PID: 7148)
- BackgroundTransferHost.exe (PID: 6800)
- dxdiag.exe (PID: 7896)
Reads the software policy settings
- hitpaw-edimakor-full_11742816193815166301.exe (PID: 7148)
- BackgroundTransferHost.exe (PID: 6800)
- slui.exe (PID: 7336)
- dxdiag.exe (PID: 7896)
- slui.exe (PID: 1764)
Creates files in the program directory
- hitpaw-edimakor-full_11742816193815166301.exe (PID: 7148)
- hitpawedimakor_hitpawem_3.6.1.tmp (PID: 7964)
Reads security settings of Internet Explorer
- BackgroundTransferHost.exe (PID: 8108)
- BackgroundTransferHost.exe (PID: 3888)
- BackgroundTransferHost.exe (PID: 6800)
- BackgroundTransferHost.exe (PID: 7680)
- BackgroundTransferHost.exe (PID: 1132)
- Taskmgr.exe (PID: 1228)
- dxdiag.exe (PID: 7896)
- resmon.exe (PID: 7568)
UPX packer has been detected
- hitpaw-edimakor-full_11742816193815166301.exe (PID: 7148)
Create files in a temporary directory
- hitpaw-edimakor-full_11742816193815166301.exe (PID: 7148)
- hitpawedimakor_hitpawem_3.6.1.exe (PID: 4428)
- hitpawedimakor_hitpawem_3.6.1.tmp (PID: 7964)
Manual execution by a user
- Taskmgr.exe (PID: 7672)
- Taskmgr.exe (PID: 1228)
The sample compiled with chinese language support
- hitpawedimakor_hitpawem_3.6.1.tmp (PID: 7964)
Process checks computer location settings
- hitpawedimakor_hitpawem_3.6.1.tmp (PID: 7964)
Reads the time zone
- perfmon.exe (PID: 6972)
Reads CPU info
- perfmon.exe (PID: 6972)
Compiled with Borland Delphi (YARA)
- hitpawedimakor_hitpawem_3.6.1.exe (PID: 4428)
- hitpawedimakor_hitpawem_3.6.1.tmp (PID: 7964)
Detects InnoSetup installer (YARA)
- hitpawedimakor_hitpawem_3.6.1.exe (PID: 4428)
- hitpawedimakor_hitpawem_3.6.1.tmp (PID: 7964)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (64.2) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.6) |
| .exe | | | Win32 Executable (generic) (10.6) |
| .exe | | | Generic Win/DOS Executable (4.7) |
| .exe | | | DOS Executable Generic (4.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:11:07 08:01:58+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 1601536 |
| InitializedDataSize: | 483328 |
| UninitializedDataSize: | 1449984 |
| EntryPoint: | 0x2e9cb0 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.7.20.1 |
| ProductVersionNumber: | 2.7.20.1 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | HitPaw |
| FileDescription: | HitPaw Edimakor |
| FileVersion: | 2.7.20.1 |
| LegalCopyright: | Copyright © 2021-2024 HITPAW CO.,LIMITED All Rights Reserved. |
| ProductName: | 20241107160128 |
| ProductVersion: | 2.7.20.1 |
Total processes
188
Monitored processes
47
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 788 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 924 | "C:\WINDOWS\system32\taskkill.exe" /F /IM HelpService.exe | C:\Windows\System32\taskkill.exe | — | hitpawedimakor_hitpawem_3.6.1.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1132 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1228 | "C:\WINDOWS\system32\taskmgr.exe" /7 | C:\Windows\System32\Taskmgr.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Manager Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1764 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2084 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | taskkill.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2104 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | taskkill.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2152 | find /c /i "StartUp.exe" | C:\Windows\SysWOW64\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2780 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | taskkill.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
24 772
Read events
24 611
Write events
139
Delete events
22
Modification events
| (PID) Process: | (7148) hitpaw-edimakor-full_11742816193815166301.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\GuidGuidold |
| Operation: | write | Name: | guid |
Value: B5DE0020-D6AC-433E-A738-77299B1F359A | |||
| (PID) Process: | (7148) hitpaw-edimakor-full_11742816193815166301.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\GuidGuidold |
| Operation: | write | Name: | user_id |
Value: 1001 | |||
| (PID) Process: | (7148) hitpaw-edimakor-full_11742816193815166301.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Tenorshare\Downloader2.5.0 |
| Operation: | write | Name: | GA_PC |
Value: 1 | |||
| (PID) Process: | (8108) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (8108) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (8108) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6800) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6800) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6800) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3888) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
Executable files
1 009
Suspicious files
69
Text files
1 559
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6800 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\eeb6feab-d4f4-4052-ac6b-09a22d4f2cff.down_data | — | |
MD5:— | SHA256:— | |||
| 7148 | hitpaw-edimakor-full_11742816193815166301.exe | C:\Users\admin\AppData\Local\Temp\hitpawedimakor_hitpawem\hitpawedimakor_hitpawem_3.6.1.exe | — | |
MD5:— | SHA256:— | |||
| 6800 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\9f876aad-1baf-40c1-834e-ca3df92c30d5.61e31bd0-2663-4442-b7ac-f2f1d8dc0b55.down_meta | binary | |
MD5:FE0D6908805C213E594074348CA56A6A | SHA256:F72162C104C52B19C47C577D3B05A72EFAD29A4D15855CE3597D2FCB7F2BB851 | |||
| 6800 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\9f876aad-1baf-40c1-834e-ca3df92c30d5.up_meta_secure | binary | |
MD5:D96CFE1F91930932F3013CB0ECAD8A8C | SHA256:59B67FA477A7CC411E50170F29D5D5370EF4294F085B21718079537722AD14DE | |||
| 7148 | hitpaw-edimakor-full_11742816193815166301.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\80237EE4964FC9C409AAF55BF996A292_FB287BEB63DB9E8D59A799779773B97C | binary | |
MD5:70F965BA8270A8D58F3A51A3EF1CFCCC | SHA256:1791021D3E08284042DCB6263F129C97052DDA10A7DA82CB639BAD192C9B2262 | |||
| 7148 | hitpaw-edimakor-full_11742816193815166301.exe | C:\Users\admin\AppData\Local\Temp\hitpawedimakor_hitpawem\galog.json | binary | |
MD5:E73529E18BBAF0605A77173EB56E2542 | SHA256:4F8D30B54DBC76EBFF34AA32EF73397EEEF56139075CF5C37FCA14B650B15366 | |||
| 1228 | Taskmgr.exe | C:\Users\admin\AppData\Local\D3DSCache\3534848bb9f4cb71\F4EB2D6C-ED2B-4BDD-AD9D-F913287E6768.lock | text | |
MD5:F49655F856ACB8884CC0ACE29216F511 | SHA256:7852FCE59C67DDF1D6B8B997EAA1ADFAC004A9F3A91C37295DE9223674011FBA | |||
| 7148 | hitpaw-edimakor-full_11742816193815166301.exe | C:\Users\admin\AppData\Local\Temp\hitpawedimakor_hitpawem\hitpawedimakor_hitpawem_3.6.1.exe.xml | text | |
MD5:940D39787ACF62A04721E821F615756E | SHA256:9B4382A07AE351F3C4382D26F36C817214500918CED7DD18FEE2EB25856BE0B1 | |||
| 7148 | hitpaw-edimakor-full_11742816193815166301.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\8EC9B1D0ABBD7F98B401D425828828CE_DADDBD2E616FBDBE0CD036EAFB5F1319 | binary | |
MD5:3A98C1EE5C90862C83F60BA5236E3095 | SHA256:BC6DB8C469613BAAD5E1E6668E995C5C492EDFA4E970CB004AC9A7A028AFEE91 | |||
| 6800 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\Content\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:4872BABAF39AA62B8D32695EBB7E9173 | SHA256:2EE85DF86EE29BBEB3DCA81AA29B6DE204F605A2769B84C728A329178A2D0999 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
97
DNS requests
41
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5360 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6800 | BackgroundTransferHost.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5360 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7148 | hitpaw-edimakor-full_11742816193815166301.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTjzY2p9Pa8oibmj%2BNSMWsz63kmWgQUuhbZbU2FL3MpdpovdYxqII%2BeyG8CEAuuZrxaun%2BVh8b56QTjMwQ%3D | unknown | — | — | whitelisted |
664 | backgroundTaskHost.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7148 | hitpaw-edimakor-full_11742816193815166301.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEA2Z%2Fk0pRoOk7pRvaISe4Lo%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
3216 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 20.190.160.3:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 23.54.109.203:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
7148 | hitpaw-edimakor-full_11742816193815166301.exe | 104.18.24.249:80 | www.tenorshare.com | CLOUDFLARENET | — | suspicious |
7148 | hitpaw-edimakor-full_11742816193815166301.exe | 104.18.24.249:443 | www.tenorshare.com | CLOUDFLARENET | — | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.tenorshare.com |
| whitelisted |
ip-api.com |
| whitelisted |
update.tenorshare.com |
| unknown |
www.google-analytics.com |
| whitelisted |
analytics.afirstsoft.cn |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7148 | hitpaw-edimakor-full_11742816193815166301.exe | Potential Corporate Privacy Violation | ET INFO Unsupported/Fake Windows NT Version 5.0 |
2196 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
2196 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
7148 | hitpaw-edimakor-full_11742816193815166301.exe | Potential Corporate Privacy Violation | ET INFO Unsupported/Fake Windows NT Version 5.0 |
7148 | hitpaw-edimakor-full_11742816193815166301.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |