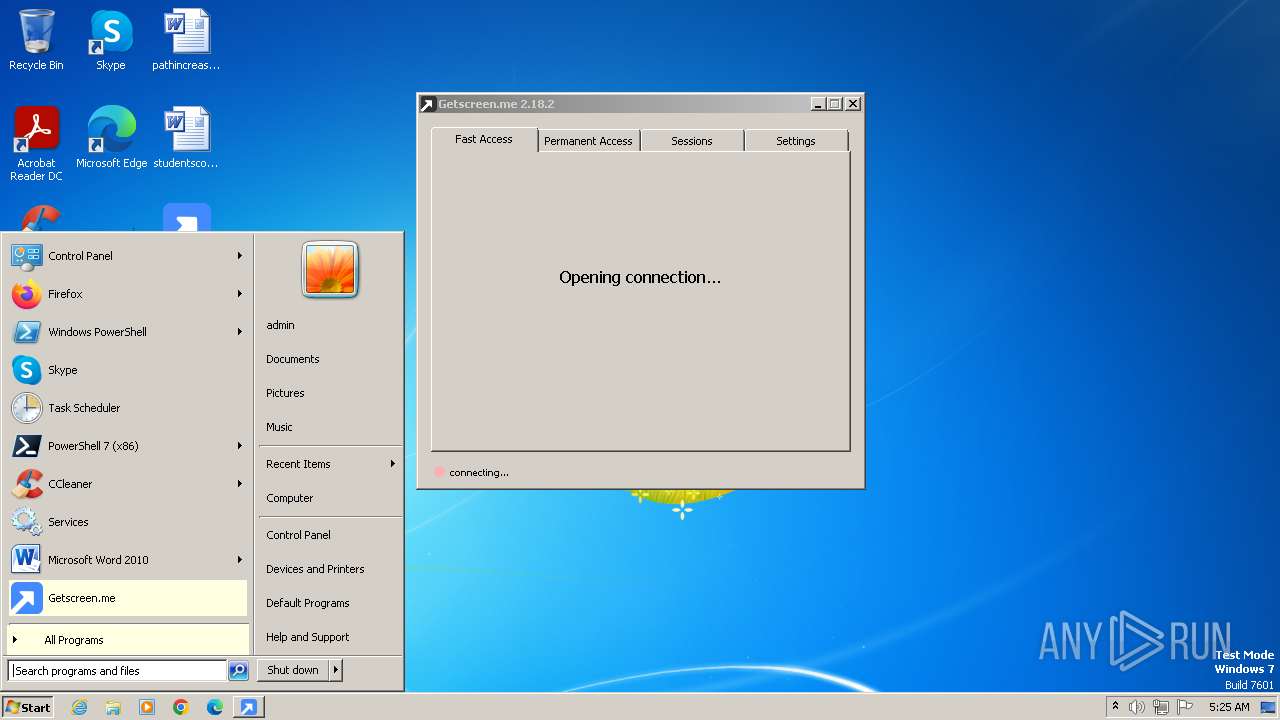
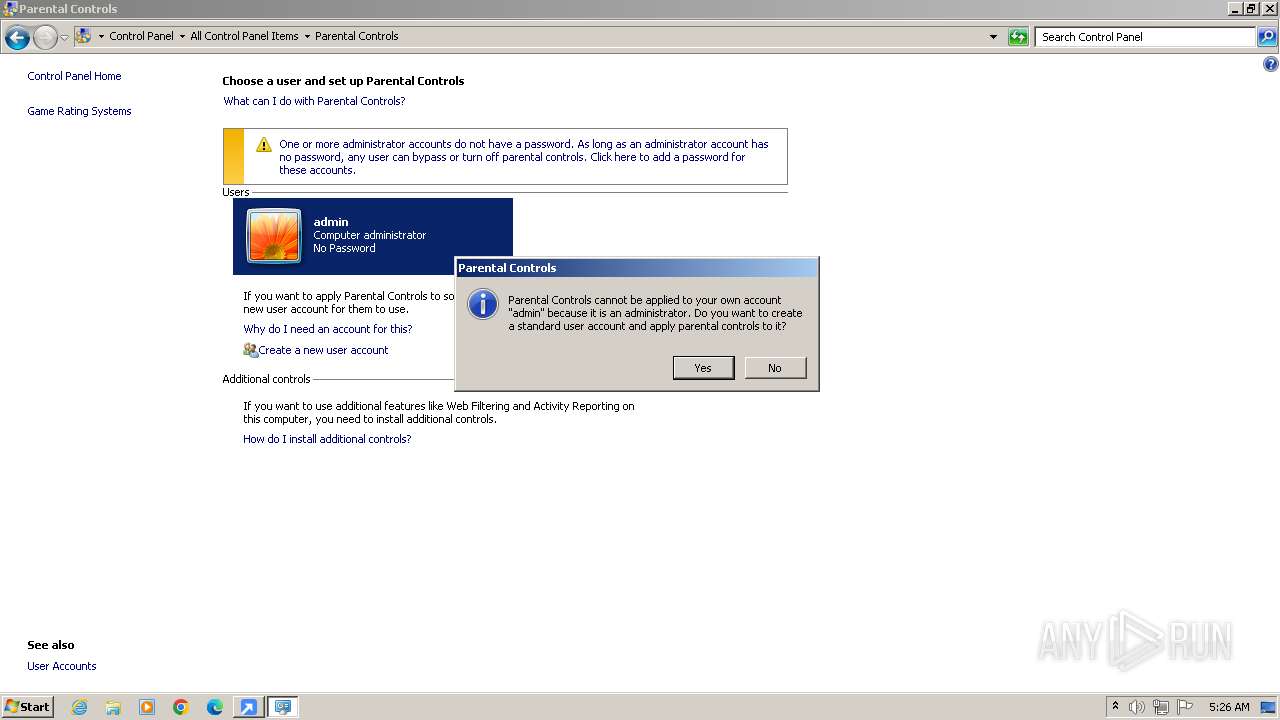
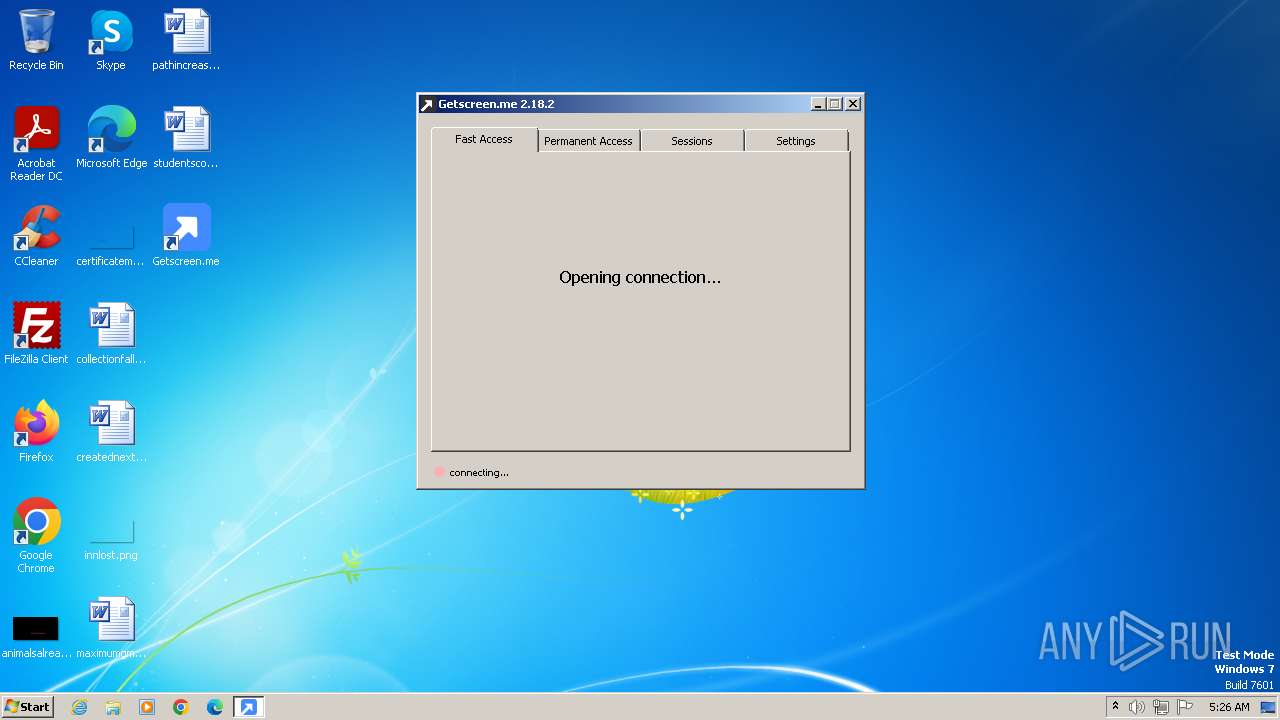
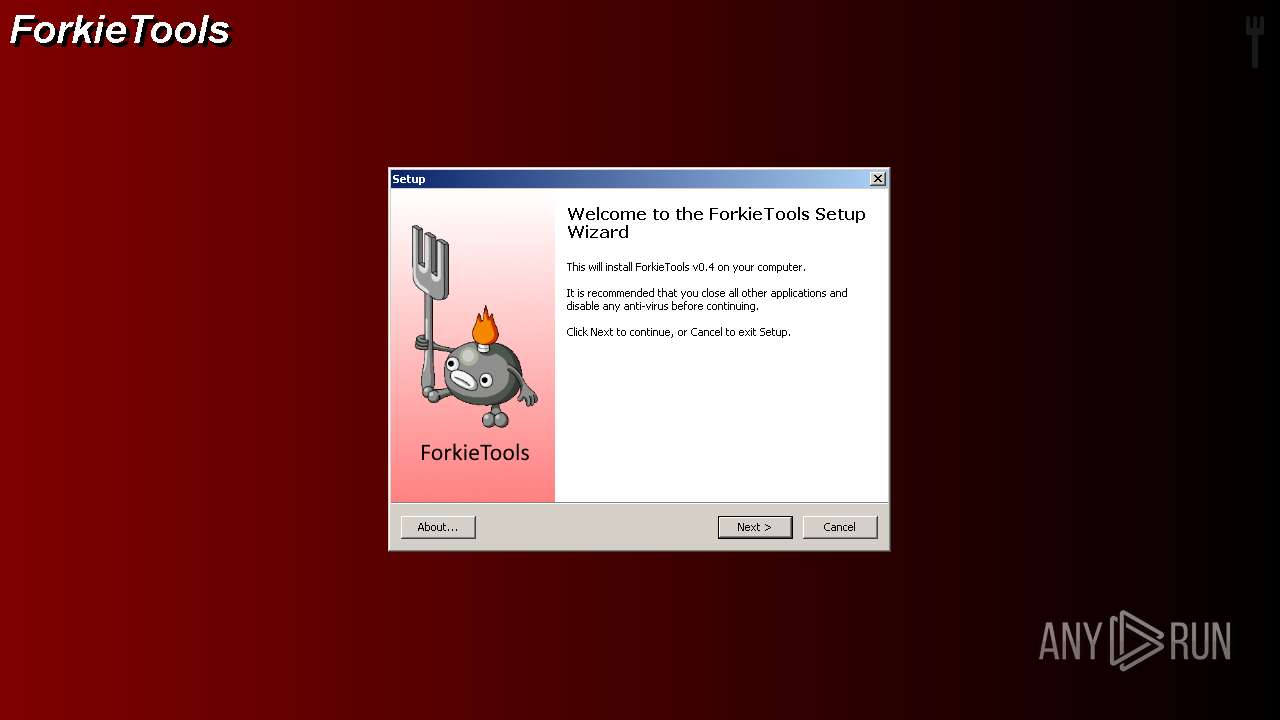
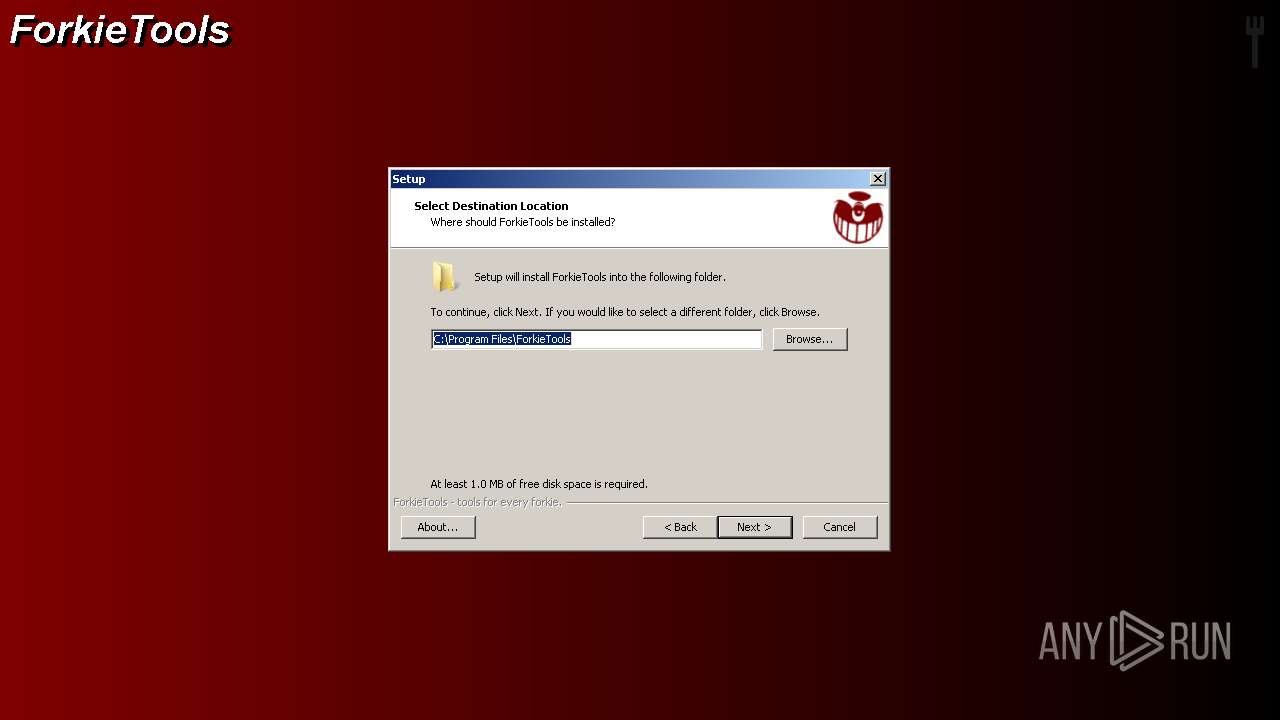
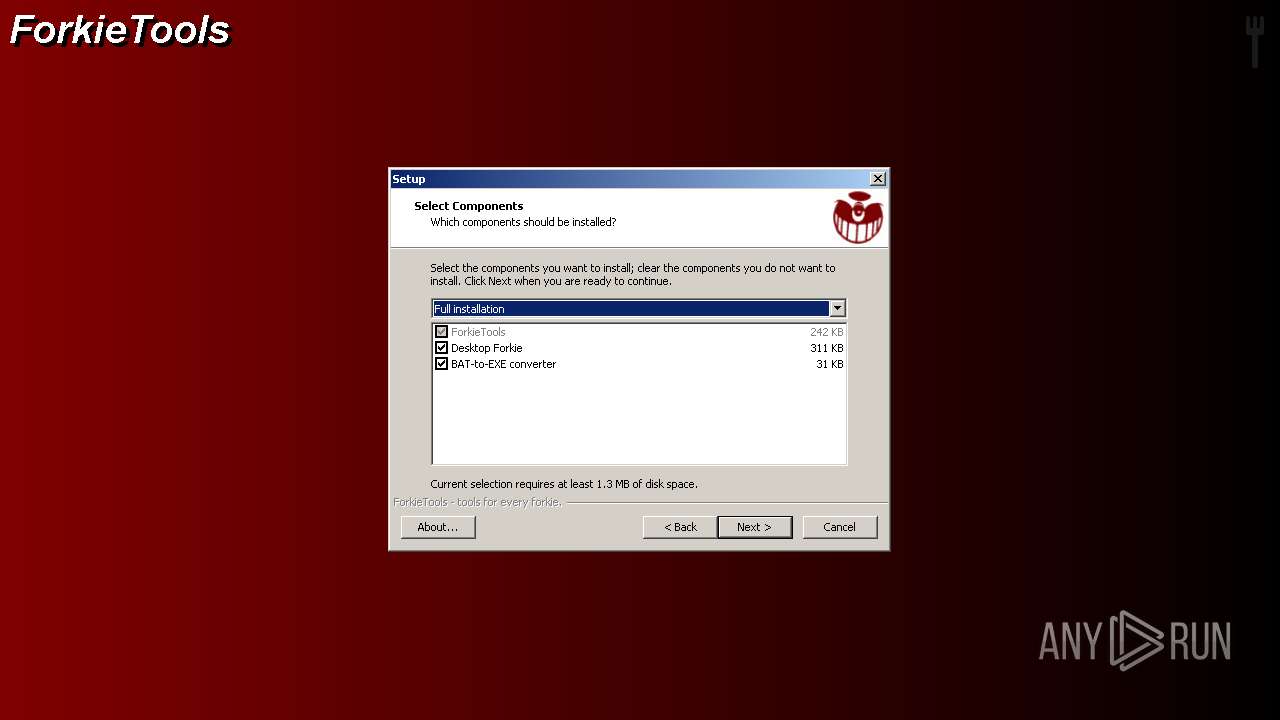
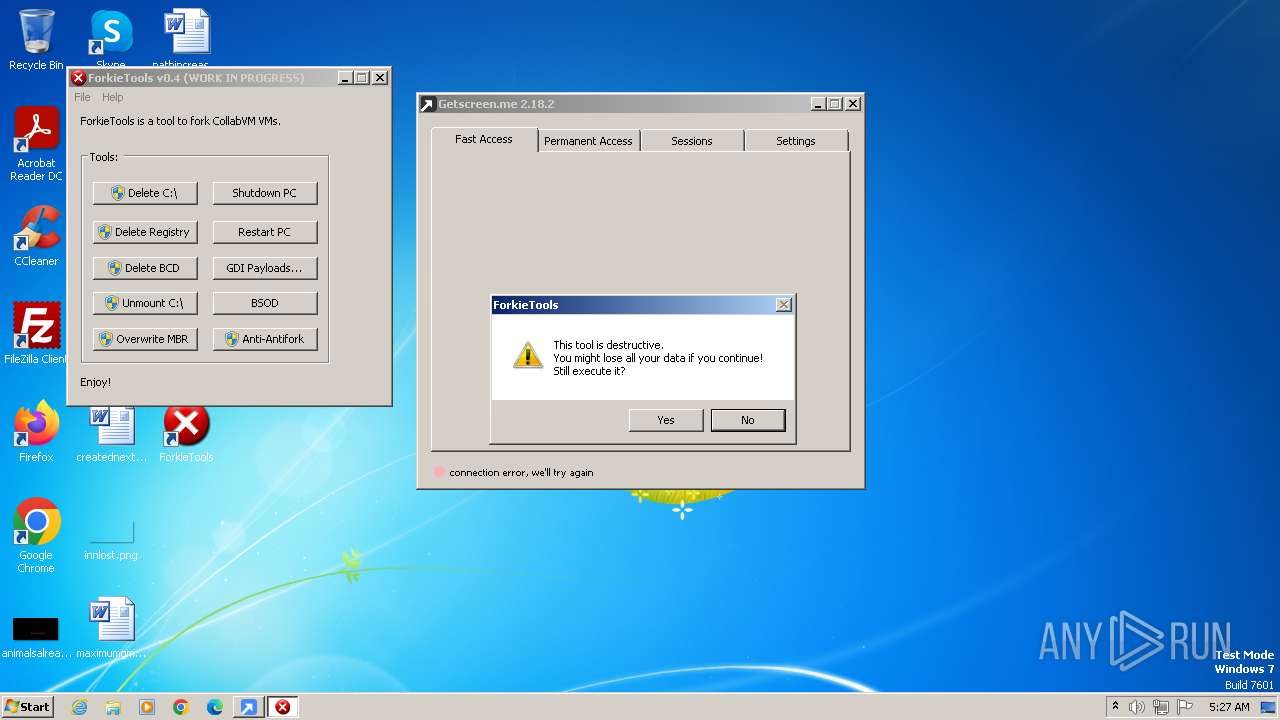
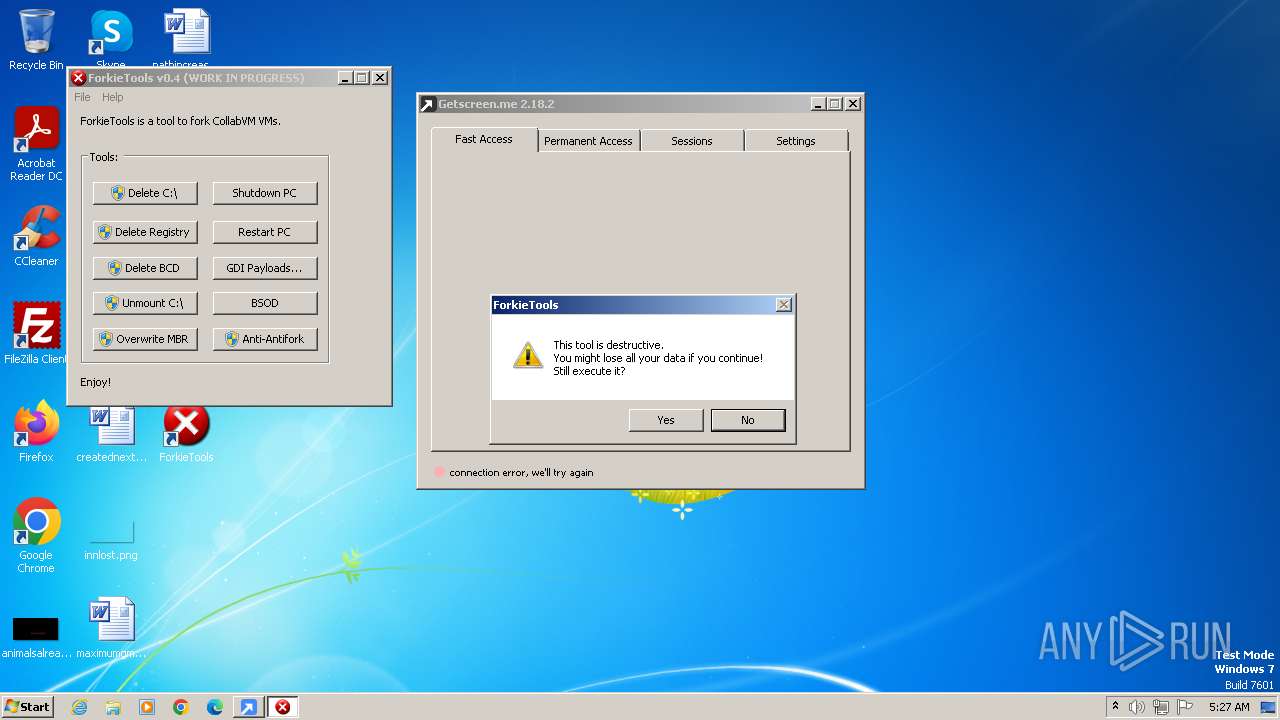
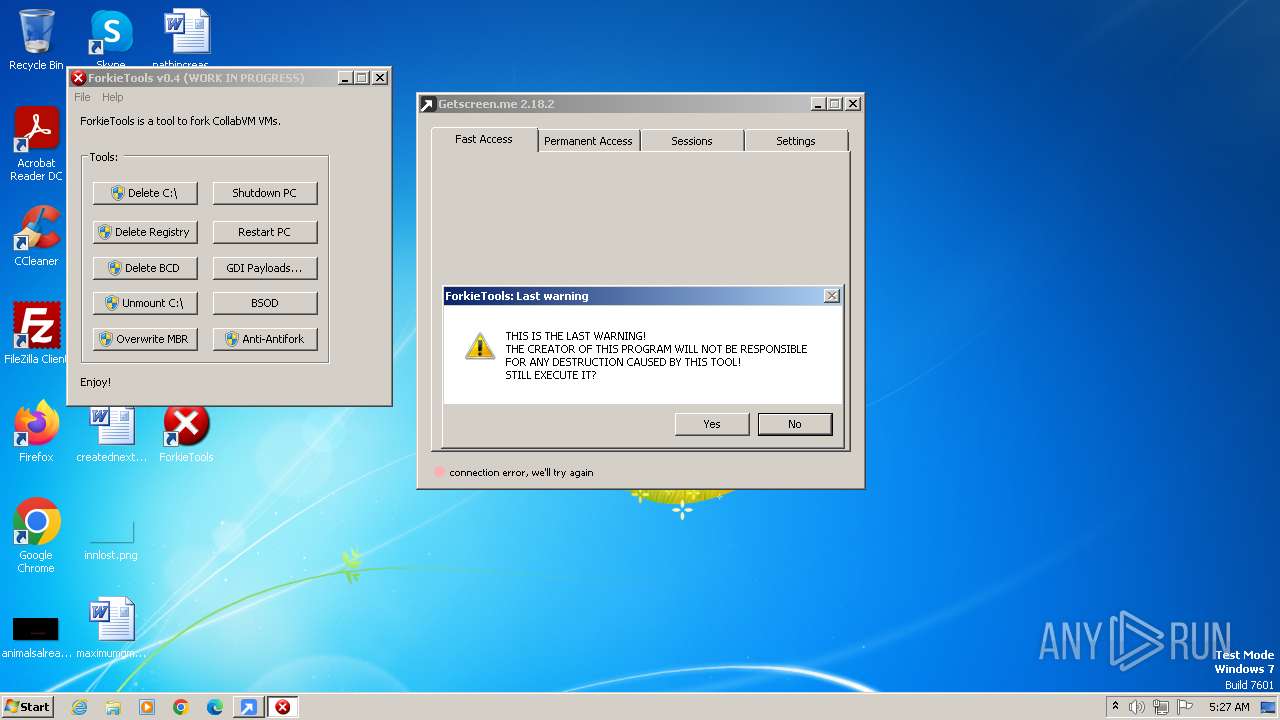
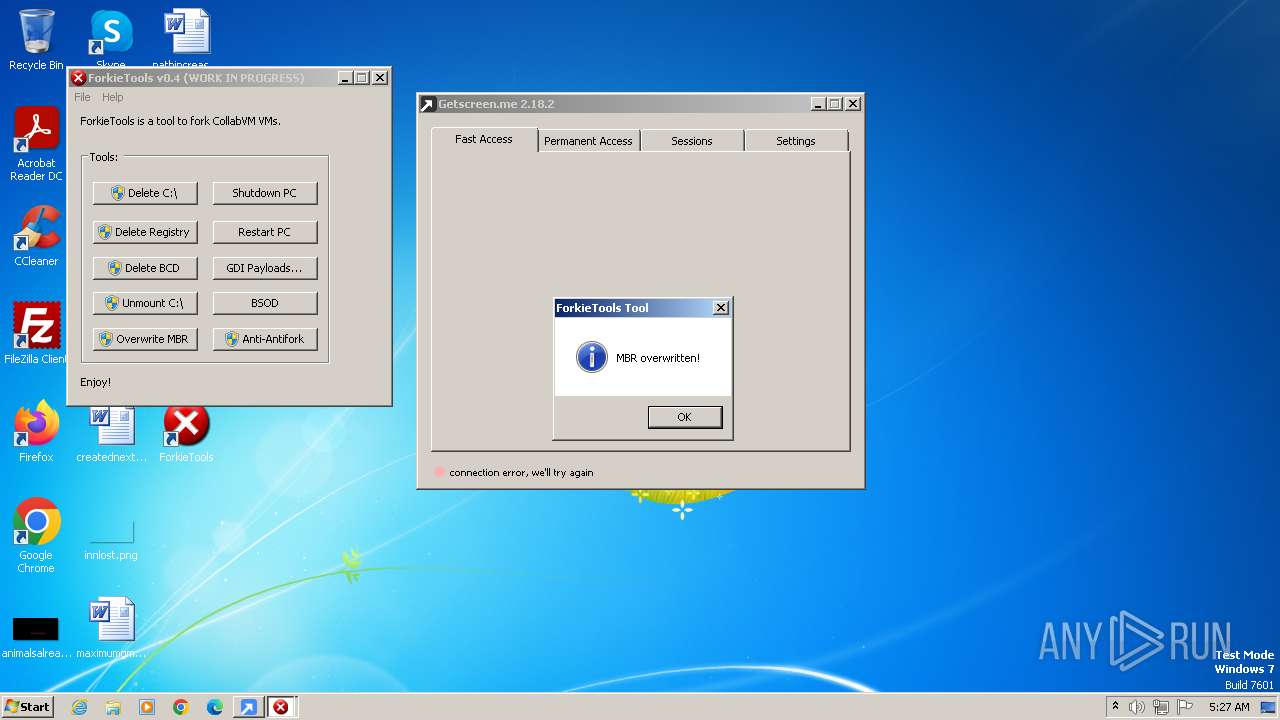
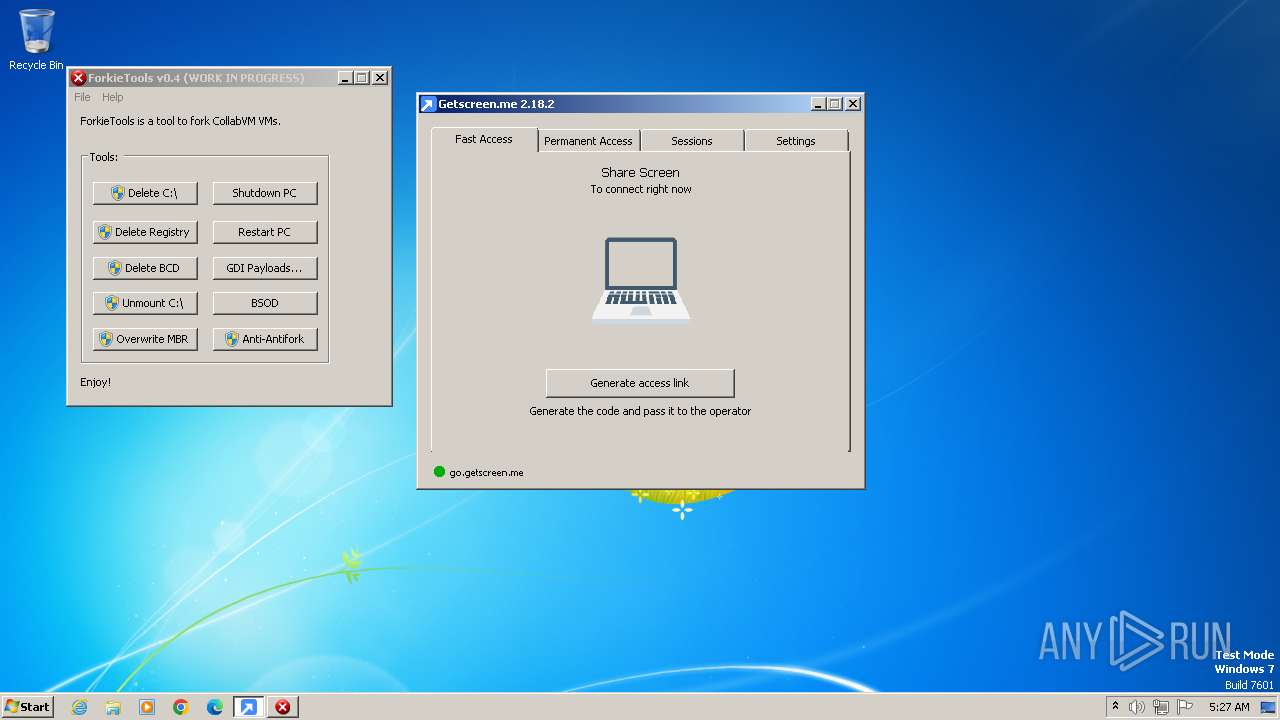
| File name: | getscreen-x86 (4).exe |
| Full analysis: | https://app.any.run/tasks/f52d5c73-76cf-441c-a7ef-778af3c2549a |
| Verdict: | Malicious activity |
| Analysis date: | March 21, 2024, 05:24:58 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed |
| MD5: | 4AD11A98ADB6E5B3877DCD2F8E57495A |
| SHA1: | 7978753DCABAE0ECEEA9EF5F45413B185C44426D |
| SHA256: | B1E54BE5FC56825041DB8AB7DC27D4EF4B45F37CD52B2AC0A2EFD692DA612073 |
| SSDEEP: | 98304:HqrJNNcxEpbA8Xv763d5M5ggRVA33Azr1gL/4k2u8iR/mrZZfjDv/wmM+pFo/LIY:5a+WO |
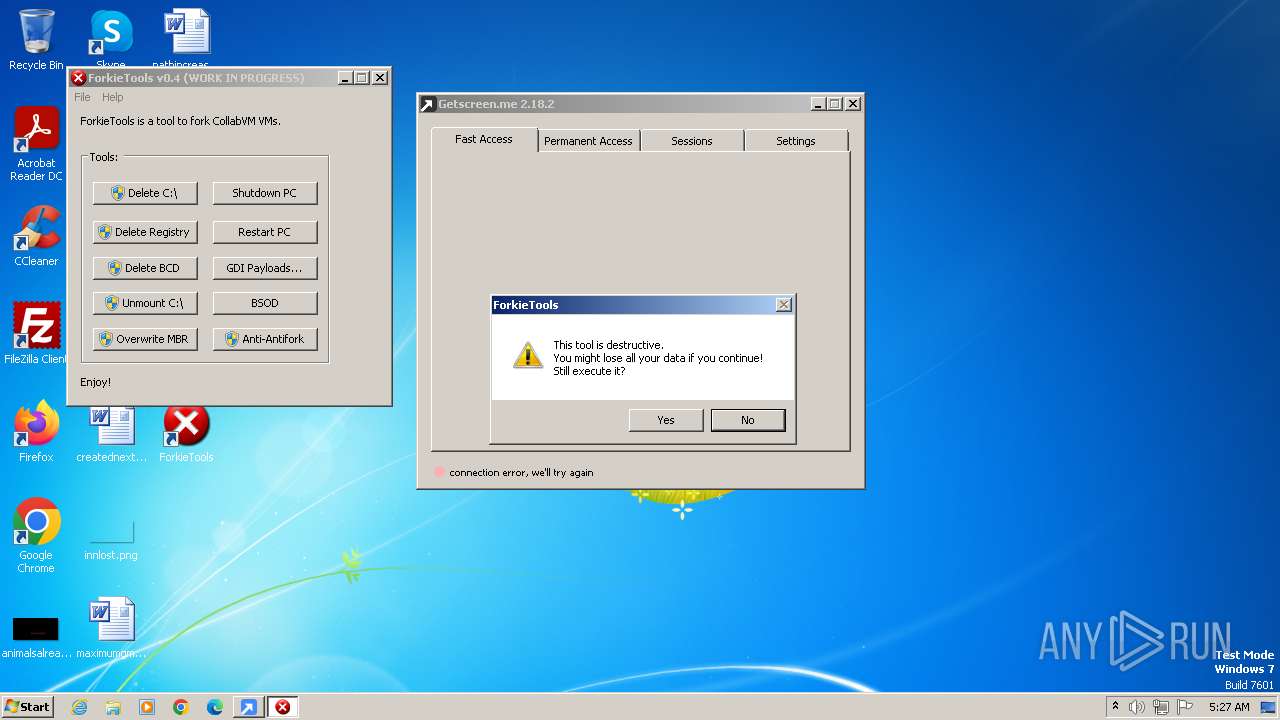
MALICIOUS
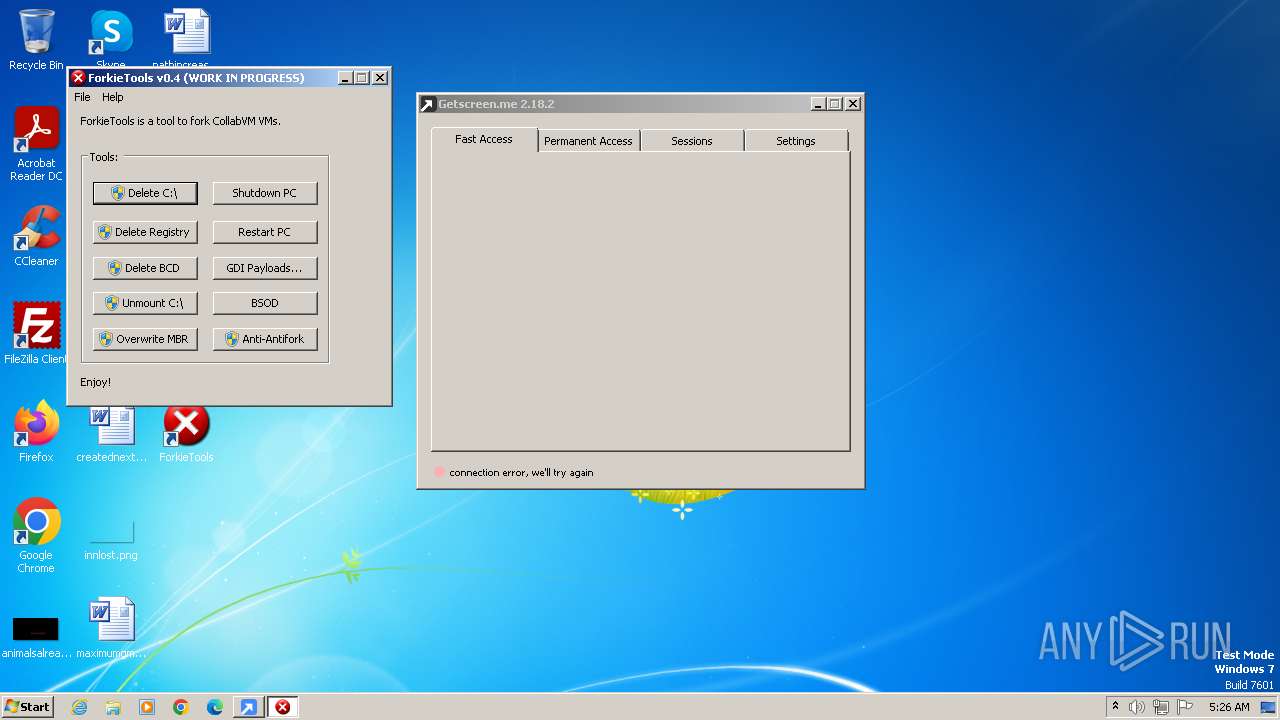
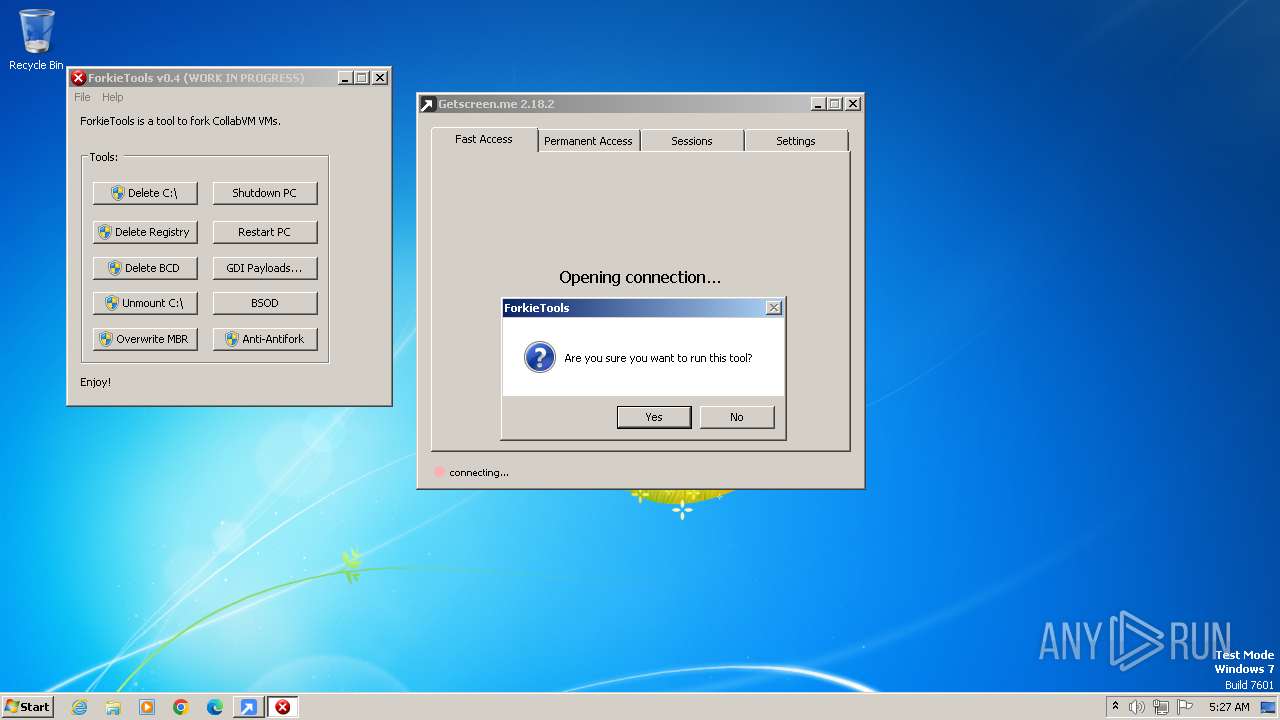
Drops the executable file immediately after the start
- getscreen-x86 (4).exe (PID: 4008)
- getscreen-x86 (4).exe (PID: 3488)
- getscreen-x86 (4).exe (PID: 2724)
- install.exe (PID: 3708)
- install.exe (PID: 3932)
- install.tmp (PID: 2332)
Changes the autorun value in the registry
- install.tmp (PID: 2332)
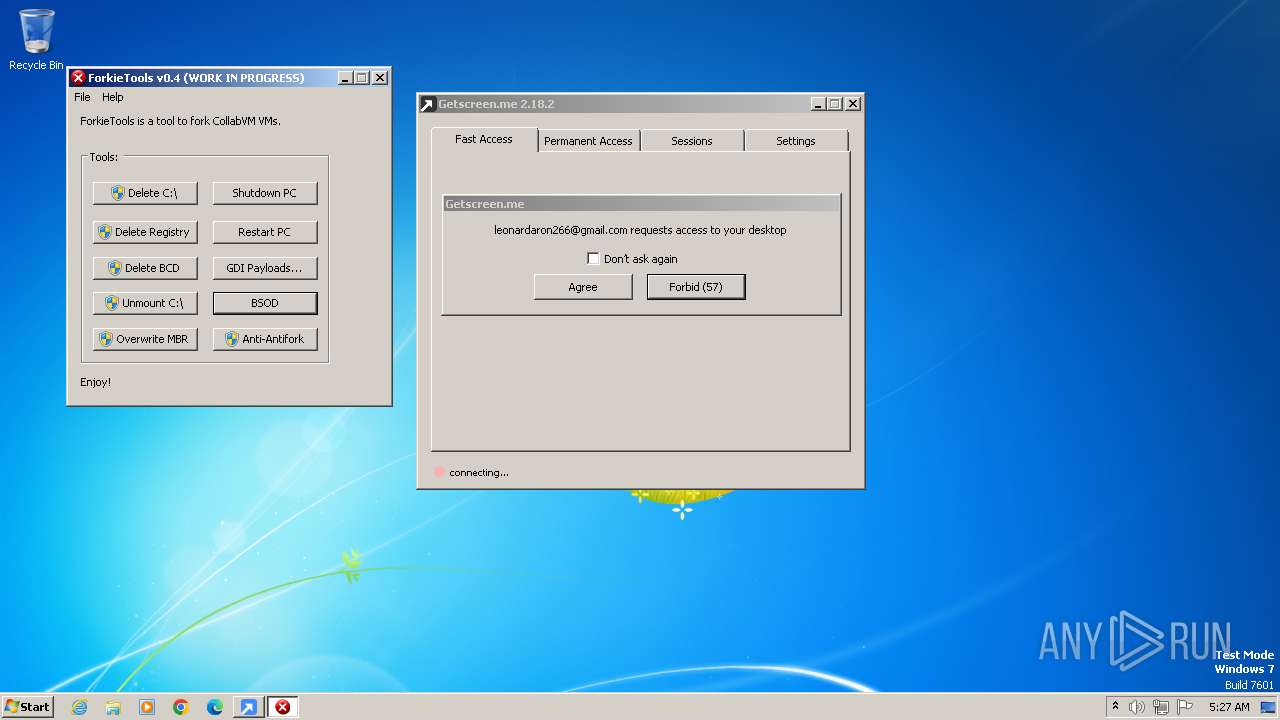
Steals credentials from Web Browsers
- VMForkGUI.exe (PID: 1768)
Creates a writable file in the system directory
- getscreen.exe (PID: 1340)
GETMESCREEN has been detected (SURICATA)
- getscreen.exe (PID: 1340)
Actions looks like stealing of personal data
- VMForkGUI.exe (PID: 1768)
SUSPICIOUS
Application launched itself
- getscreen-x86 (4).exe (PID: 4008)
- getscreen-x86 (4).exe (PID: 3488)
- getscreen.exe (PID: 1340)
- VMForkGUI.exe (PID: 3916)
Reads the Internet Settings
- getscreen-x86 (4).exe (PID: 4008)
- getscreen-x86 (4).exe (PID: 3488)
- VMForkGUI.exe (PID: 3916)
Reads security settings of Internet Explorer
- getscreen-x86 (4).exe (PID: 4008)
- VMForkGUI.exe (PID: 3916)
Executable content was dropped or overwritten
- getscreen-x86 (4).exe (PID: 3488)
- getscreen-x86 (4).exe (PID: 2724)
- install.exe (PID: 3932)
- install.exe (PID: 3708)
- install.tmp (PID: 2332)
Changes Internet Explorer settings (feature browser emulation)
- getscreen-x86 (4).exe (PID: 1824)
- getscreen.exe (PID: 2668)
Executes as Windows Service
- ktbryanfroonlnunfngritiotzkgvnr-elevate.exe (PID: 2960)
- getscreen.exe (PID: 1340)
Creates a software uninstall entry
- getscreen-x86 (4).exe (PID: 2724)
Reads the Windows owner or organization settings
- install.tmp (PID: 2332)
Non-standard symbols in registry
- install.tmp (PID: 2332)
Creates file in the systems drive root
- VMForkGUI.exe (PID: 1768)
Deletes system .NET executable
- VMForkGUI.exe (PID: 1768)
Connects to unusual port
- getscreen.exe (PID: 1340)
INFO
Reads the computer name
- getscreen-x86 (4).exe (PID: 4008)
- getscreen-x86 (4).exe (PID: 3488)
- getscreen-x86 (4).exe (PID: 1824)
- ktbryanfroonlnunfngritiotzkgvnr-elevate.exe (PID: 2960)
- getscreen-x86 (4).exe (PID: 2724)
- getscreen-x86 (4).exe (PID: 2904)
- getscreen.exe (PID: 2384)
- getscreen.exe (PID: 1340)
- install.tmp (PID: 2132)
- getscreen.exe (PID: 2668)
- getscreen.exe (PID: 1544)
- VMForkGUI.exe (PID: 3916)
- install.tmp (PID: 2332)
- getscreen.exe (PID: 1644)
- getscreen.exe (PID: 2024)
- getscreen.exe (PID: 2020)
- getscreen.exe (PID: 1604)
Checks supported languages
- getscreen-x86 (4).exe (PID: 4008)
- getscreen-x86 (4).exe (PID: 3488)
- getscreen-x86 (4).exe (PID: 1824)
- ktbryanfroonlnunfngritiotzkgvnr-elevate.exe (PID: 2960)
- getscreen-x86 (4).exe (PID: 2724)
- getscreen.exe (PID: 1340)
- getscreen.exe (PID: 2384)
- getscreen.exe (PID: 2668)
- getscreen-x86 (4).exe (PID: 2904)
- getscreen.exe (PID: 1544)
- install.exe (PID: 3708)
- install.tmp (PID: 2132)
- install.exe (PID: 3932)
- install.tmp (PID: 2332)
- VMForkGUI.exe (PID: 3916)
- VMForkGUI.exe (PID: 3964)
- VMForkGUI.exe (PID: 1768)
- getscreen.exe (PID: 2020)
- getscreen.exe (PID: 2024)
- getscreen.exe (PID: 1644)
- getscreen.exe (PID: 1604)
Creates files in the program directory
- getscreen-x86 (4).exe (PID: 4008)
- getscreen-x86 (4).exe (PID: 3488)
- getscreen-x86 (4).exe (PID: 2724)
- getscreen.exe (PID: 1340)
- install.tmp (PID: 2332)
Creates files or folders in the user directory
- getscreen-x86 (4).exe (PID: 3488)
Create files in a temporary directory
- dllhost.exe (PID: 920)
- install.exe (PID: 3932)
- install.exe (PID: 3708)
- install.tmp (PID: 2332)
Manual execution by a user
- install.exe (PID: 3708)
- getscreen.exe (PID: 1544)
Reads the machine GUID from the registry
- getscreen.exe (PID: 1340)
Reads mouse settings
- getscreen.exe (PID: 1604)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (76) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.6) |
| .exe | | | Generic Win/DOS Executable (5.6) |
| .exe | | | DOS Executable Generic (5.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:03:13 08:18:45+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.36 |
| CodeSize: | 3620864 |
| InitializedDataSize: | 20480 |
| UninitializedDataSize: | 20406272 |
| EntryPoint: | 0x16ea210 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.18.2.0 |
| ProductVersionNumber: | 2.18.2.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Unknown (0009) |
| CharacterSet: | Unicode |
| CompanyName: | Getscreen.me |
| InternalName: | Getscreen.me |
| OriginalFileName: | getscreen.exe |
| ProductName: | Getscreen.me |
| FileVersion: | 2.18.2 |
| LegalCopyright: | Copyright (C) 2023 |
| ProductVersion: | 2.18.2 |
Total processes
81
Monitored processes
23
Malicious processes
10
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 668 | C:\Windows\system32\DllHost.exe /Processid:{A2D8CFE7-7BA4-4BAD-B86B-851376B59134} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 920 | C:\Windows\system32\DllHost.exe /Processid:{86D5EB8A-859F-4C7B-A76B-2BD819B7A850} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1340 | "C:\Program Files\Getscreen.me\getscreen.exe" -service | C:\Program Files\Getscreen.me\getscreen.exe | services.exe | ||||||||||||
User: SYSTEM Company: Getscreen.me Integrity Level: SYSTEM Exit code: 0 Version: 2.18.2 Modules
| |||||||||||||||
| 1544 | "C:\Program Files\Getscreen.me\getscreen.exe" | C:\Program Files\Getscreen.me\getscreen.exe | — | explorer.exe | |||||||||||
User: admin Company: Getscreen.me Integrity Level: MEDIUM Exit code: 0 Version: 2.18.2 Modules
| |||||||||||||||
| 1604 | "C:\Program Files\Getscreen.me\getscreen.exe" -cpipe \\.\pipe\PCommand96Getscreen.me -child | C:\Program Files\Getscreen.me\getscreen.exe | — | getscreen.exe | |||||||||||
User: SYSTEM Company: Getscreen.me Integrity Level: SYSTEM Exit code: 0 Version: 2.18.2 Modules
| |||||||||||||||
| 1644 | "C:\Program Files\Getscreen.me\getscreen.exe" -cpipe \\.\pipe\PCommand96Getscreen.me -child | C:\Program Files\Getscreen.me\getscreen.exe | — | getscreen.exe | |||||||||||
User: SYSTEM Company: Getscreen.me Integrity Level: SYSTEM Exit code: 1 Version: 2.18.2 Modules
| |||||||||||||||
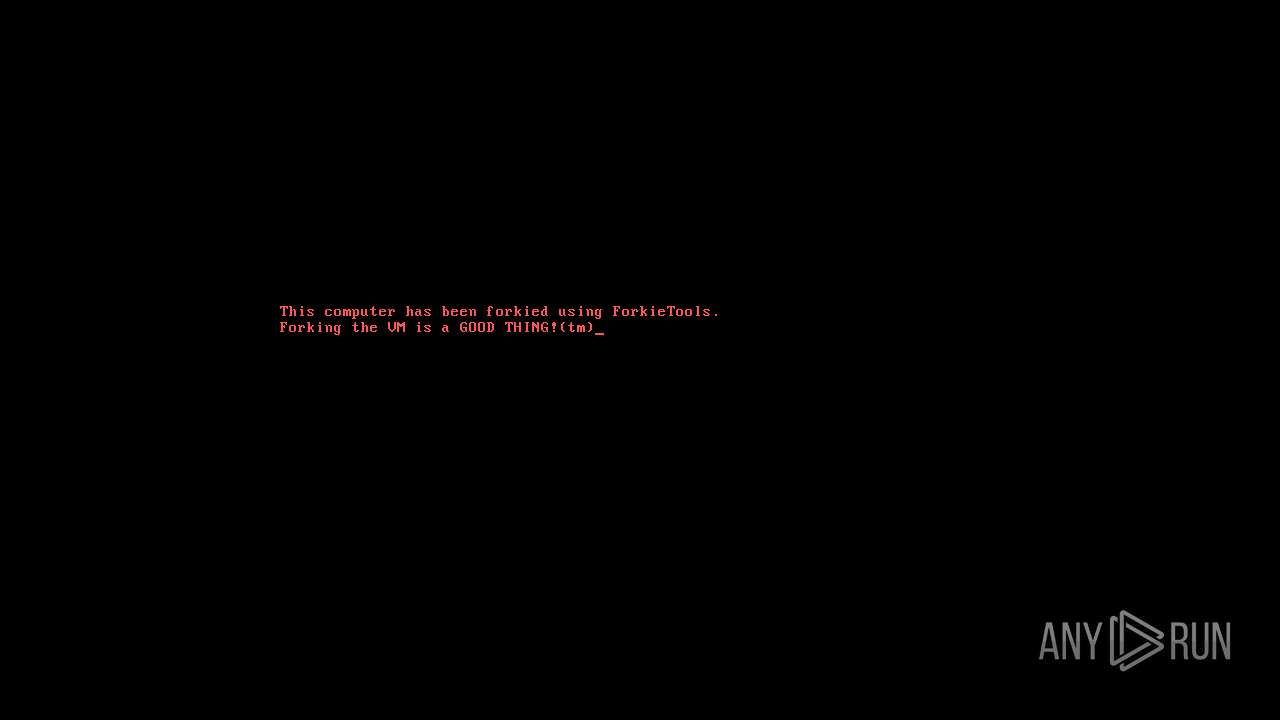
| 1768 | "C:\Program Files\ForkieTools\VMForkGUI.exe" VMForkRunTool1 | C:\Program Files\ForkieTools\VMForkGUI.exe | VMForkGUI.exe | ||||||||||||
User: admin Company: User123 Integrity Level: HIGH Description: ForkieTools GUI Exit code: 0 Version: v0.4 Modules
| |||||||||||||||
| 1824 | "C:\Users\admin\AppData\Local\Temp\getscreen-x86 (4).exe" -gpipe \\.\pipe\PCommand97Getscreen.me -gui | C:\Users\admin\AppData\Local\Temp\getscreen-x86 (4).exe | — | getscreen-x86 (4).exe | |||||||||||
User: admin Company: Getscreen.me Integrity Level: HIGH Exit code: 1 Version: 2.18.2 Modules
| |||||||||||||||
| 2020 | "C:\Program Files\Getscreen.me\getscreen.exe" -cpipe \\.\pipe\PCommand96Getscreen.me -child | C:\Program Files\Getscreen.me\getscreen.exe | — | getscreen.exe | |||||||||||
User: SYSTEM Company: Getscreen.me Integrity Level: SYSTEM Exit code: 1 Version: 2.18.2 Modules
| |||||||||||||||
| 2024 | "C:\Program Files\Getscreen.me\getscreen.exe" -epipe \\.\pipe\PCommand98phqghumeaylnlfd -environment | C:\Program Files\Getscreen.me\getscreen.exe | — | getscreen.exe | |||||||||||
User: admin Company: Getscreen.me Integrity Level: MEDIUM Exit code: 1 Version: 2.18.2 Modules
| |||||||||||||||
Total events
11 138
Read events
11 066
Write events
66
Delete events
6
Modification events
| (PID) Process: | (4008) getscreen-x86 (4).exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (4008) getscreen-x86 (4).exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (4008) getscreen-x86 (4).exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (4008) getscreen-x86 (4).exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1824) getscreen-x86 (4).exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main\FeatureControl\FEATURE_BROWSER_EMULATION |
| Operation: | write | Name: | getscreen-x86 (4).exe |
Value: 11001 | |||
| (PID) Process: | (1824) getscreen-x86 (4).exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\MAIN\FeatureControl\FEATURE_BROWSER_EMULATION |
| Operation: | write | Name: | getscreen-x86 (4).exe |
Value: 11001 | |||
| (PID) Process: | (1824) getscreen-x86 (4).exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\Domains\getscreen.me |
| Operation: | write | Name: | http |
Value: 2 | |||
| (PID) Process: | (1824) getscreen-x86 (4).exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\Domains\getscreen.me |
| Operation: | write | Name: | https |
Value: 2 | |||
| (PID) Process: | (1824) getscreen-x86 (4).exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\EscDomains\getscreen.me |
| Operation: | write | Name: | http |
Value: 2 | |||
| (PID) Process: | (1824) getscreen-x86 (4).exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\EscDomains\getscreen.me |
| Operation: | write | Name: | https |
Value: 2 | |||
Executable files
17
Suspicious files
9
Text files
4
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1340 | getscreen.exe | C:\ProgramData\Getscreen.me\memory\0000pipe0PCommand96Getscreen0me0 | — | |
MD5:— | SHA256:— | |||
| 3488 | getscreen-x86 (4).exe | C:\ProgramData\Getscreen.me\memory\111B6B764C7BDA01C8490D2A507BDA01A00D0000FFFFFFFF | — | |
MD5:— | SHA256:— | |||
| 2384 | getscreen.exe | C:\ProgramData\Getscreen.me\memory\0000pipe0PCommand96Getscreen0me0 | — | |
MD5:— | SHA256:— | |||
| 3488 | getscreen-x86 (4).exe | C:\ProgramData\Getscreen.me\settings.dat | binary | |
MD5:37953FA9D3A365F7564489E6A9D79BAA | SHA256:B7D9B16F65F4159E18FC5998A647A4692E2F19EA723A2BAE5DC2D6AE2D7D53A7 | |||
| 920 | dllhost.exe | C:\Users\admin\AppData\Local\Temp\Administrator.bmp | image | |
MD5:343FA15C150A516B20CC9F787CFD530E | SHA256:D632E9DBACDCD8F6B86BA011ED6B23F961D104869654CAA764216EA57A916524 | |||
| 2724 | getscreen-x86 (4).exe | C:\Users\admin\Desktop\Getscreen.me.lnk | binary | |
MD5:C55E9E6D14B70448A7BDCABC0F4A2B7C | SHA256:2232D0689B3BB248BA5B2DBAA949A95E5DA10FBE1A438453AE561267DBBED0E5 | |||
| 2384 | getscreen.exe | C:\Program Files\Getscreen.me\logs\20240321.log | text | |
MD5:20380D7AE6E58A2E32908E7F17B29FDF | SHA256:FA628391088081035F5C6E8D263B2F6C1BB7C589426509CC8E820363F1714BB7 | |||
| 2724 | getscreen-x86 (4).exe | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Getscreen.me.lnk | binary | |
MD5:5ED657750BA308DDA3090C5BDAB6AB16 | SHA256:9FCEE5ADEBD7090923A67644F3E5F649F1B49E6C81FB24D0197C2012A7E0C5FD | |||
| 2332 | install.tmp | C:\Program Files\ForkieTools\is-B0JES.tmp | executable | |
MD5:8059776AA7B83E8FE95BC14EFF4C86ED | SHA256:E16FC0ACFDFDA9F9B36E276AFFAC85010D8F23BF33E8260C0C55E00E4DF90E40 | |||
| 3708 | install.exe | C:\Users\admin\AppData\Local\Temp\is-QN06G.tmp\install.tmp | executable | |
MD5:6A6475DC9AE480A60A68FAA849C8AF90 | SHA256:856C7186CD2411906FC3544D2C2600E065BE5A5EB3CE1DEB8A314226A74C8DFD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
88
DNS requests
35
Threats
115
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3488 | getscreen-x86 (4).exe | 78.47.165.25:443 | getscreen.me | Hetzner Online GmbH | DE | unknown |
1340 | getscreen.exe | 78.47.165.25:443 | getscreen.me | Hetzner Online GmbH | DE | unknown |
1340 | getscreen.exe | 5.75.168.191:443 | getscreen.me | Hetzner Online GmbH | DE | unknown |
1340 | getscreen.exe | 103.43.75.192:443 | px-au1.getscreen.me | AS-CHOOPA | AU | unknown |
1340 | getscreen.exe | 5.188.225.23:443 | px-br1.getscreen.me | G-Core Labs S.A. | BR | unknown |
1340 | getscreen.exe | 45.65.9.108:443 | px-us1.getscreen.me | G-Core Labs S.A. | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
getscreen.me |
| unknown |
dns.msftncsi.com |
| shared |
px-au1.getscreen.me |
| unknown |
px-br1.getscreen.me |
| unknown |
px-us1.getscreen.me |
| unknown |
px-eu1.getscreen.me |
| unknown |
px-us2.getscreen.me |
| unknown |
px-in1.getscreen.me |
| unknown |
image.getscreen.me |
| unknown |
px-il1.getscreen.me |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1340 | getscreen.exe | Misc activity | REMOTE [ANY.RUN] GetMeScreen Remote Desktop Software |
1340 | getscreen.exe | Misc activity | REMOTE [ANY.RUN] GetMeScreen Remote Desktop Software |
1340 | getscreen.exe | Misc activity | REMOTE [ANY.RUN] GetMeScreen Remote Desktop Software |
1340 | getscreen.exe | Misc activity | REMOTE [ANY.RUN] GetMeScreen Remote Desktop Software |
1340 | getscreen.exe | Misc activity | REMOTE [ANY.RUN] GetMeScreen Remote Desktop Software |
1340 | getscreen.exe | Misc activity | REMOTE [ANY.RUN] GetMeScreen Remote Desktop Software |
1340 | getscreen.exe | Misc activity | REMOTE [ANY.RUN] GetMeScreen Remote Desktop Software |
1340 | getscreen.exe | Misc activity | ET INFO Session Traversal Utilities for NAT (STUN Binding Request) |
1340 | getscreen.exe | Misc activity | ET INFO Session Traversal Utilities for NAT (STUN Binding Request) |
1340 | getscreen.exe | Misc activity | ET INFO Session Traversal Utilities for NAT (STUN Binding Request) |