| File name: | asdasd.exe |
| Full analysis: | https://app.any.run/tasks/61238617-d1b3-49c3-a113-409704e9dc6b |
| Verdict: | Malicious activity |
| Analysis date: | November 27, 2023, 16:07:27 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 735C55A0BDD52F23A1F61761E81C13F9 |
| SHA1: | 97B09A73A02358A48149BBE98D94A0E9139EC228 |
| SHA256: | B1D8BD3173B7A7C759614BEFFB1CA3342957C71890BD2D504B873D10469B08A5 |
| SSDEEP: | 98304:m+cD4dn3EsXb8v/b9Sk0/46326xfsIkWnXFopLQ3iUrex4vkY7mZNmijVPiZQo:1+5WYi |
MALICIOUS
Drops the executable file immediately after the start
- asdasd.tmp (PID: 2308)
- asdasd.exe (PID: 888)
- asdasd.exe (PID: 2976)
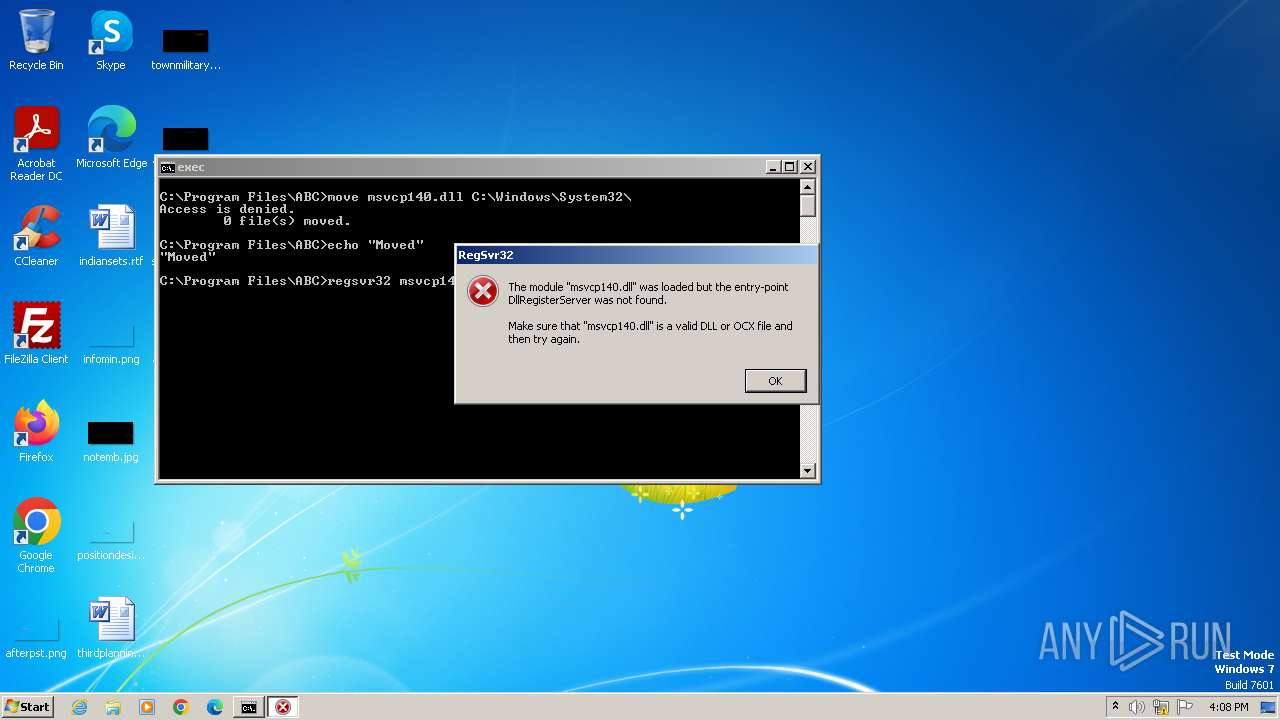
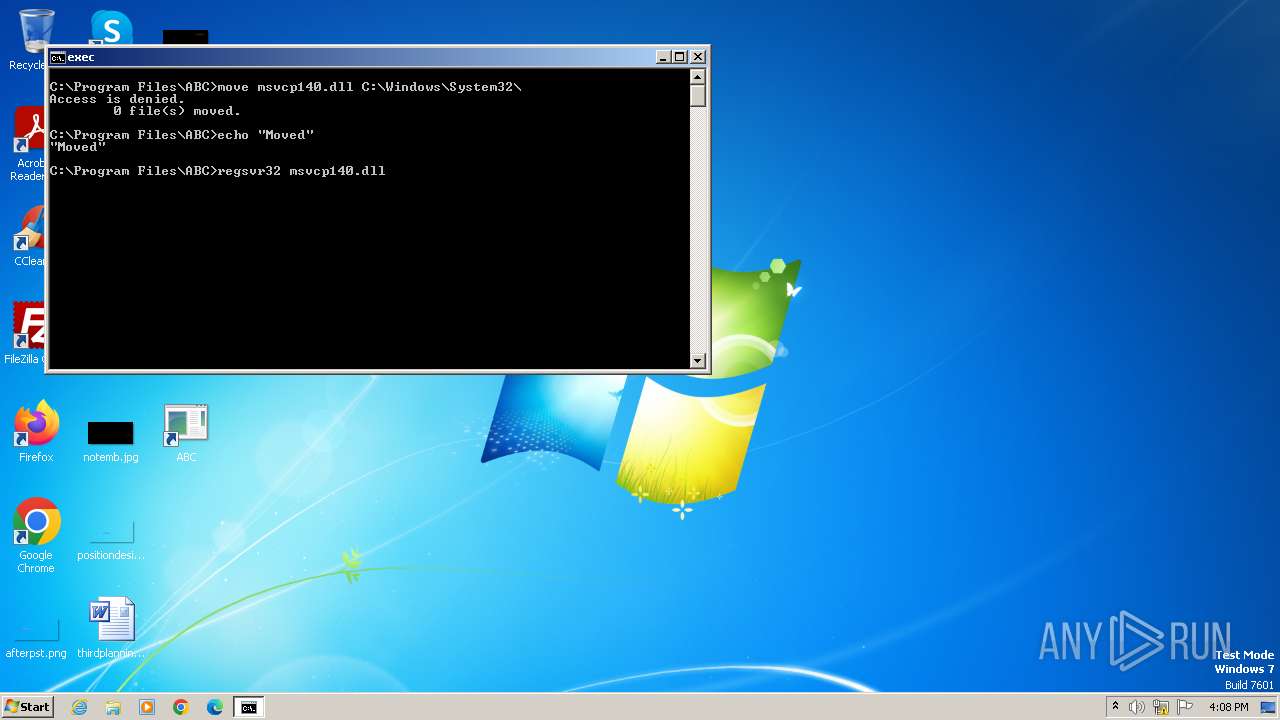
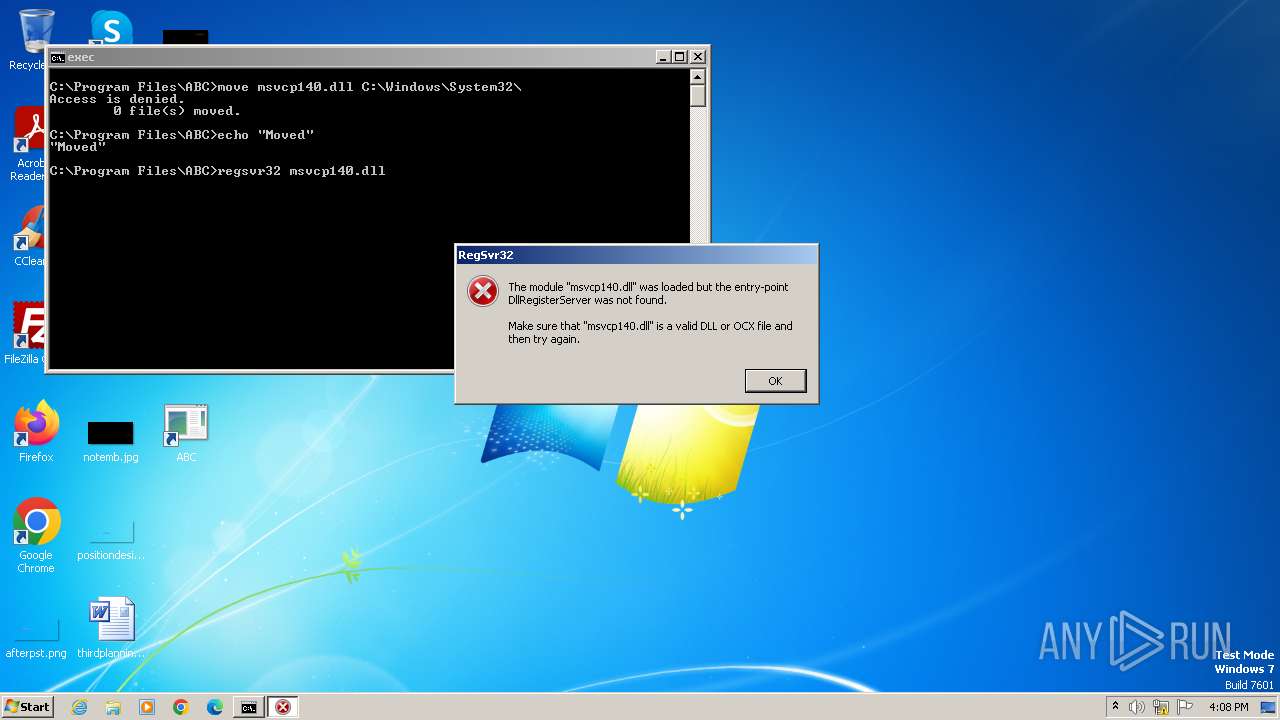
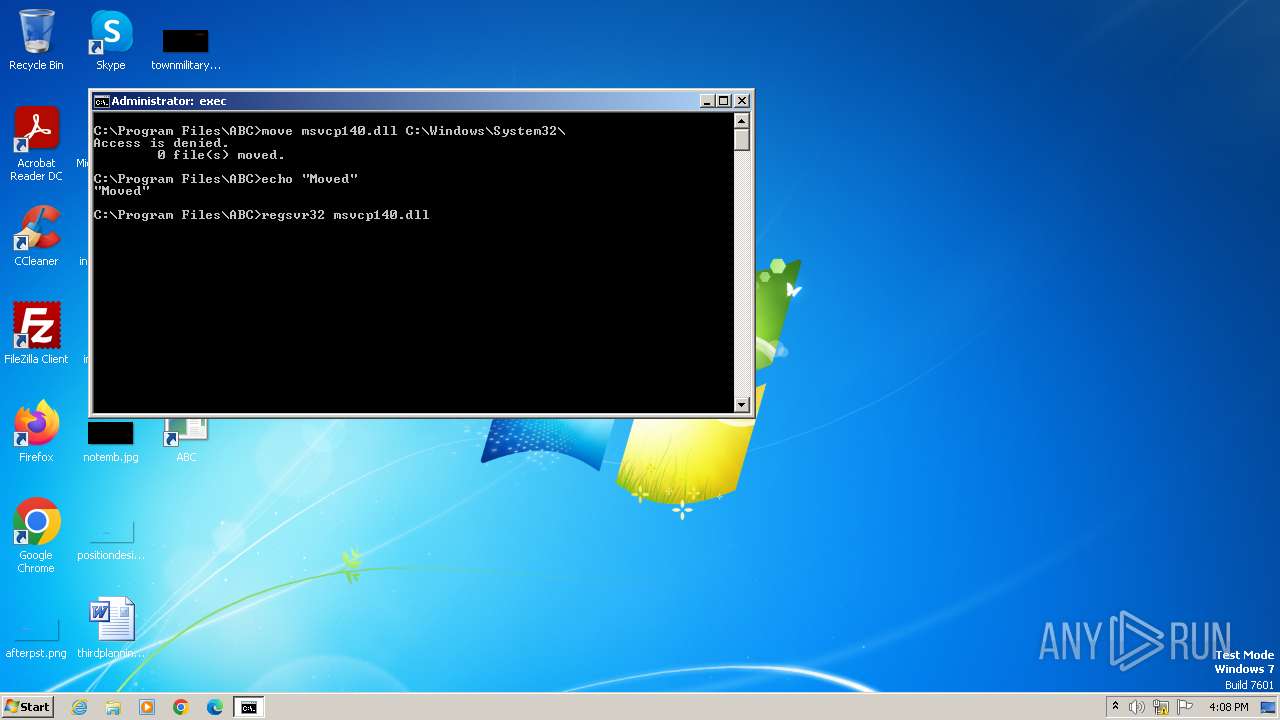
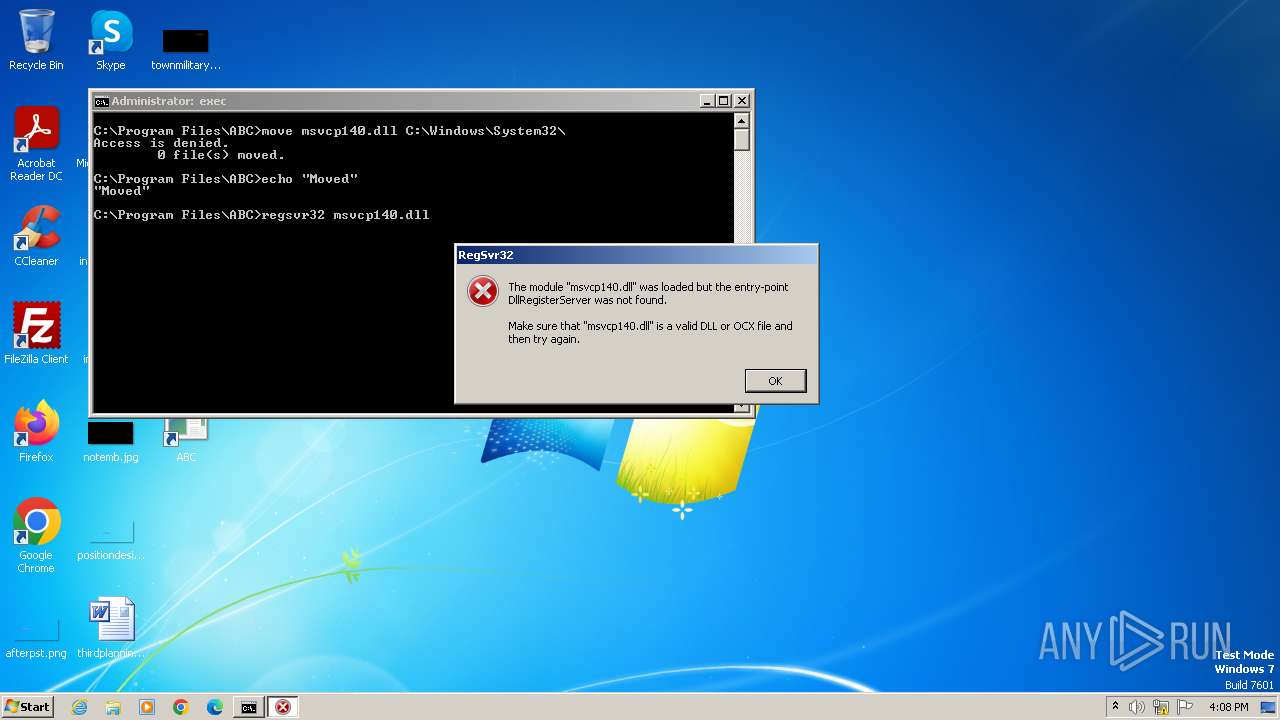
Registers / Runs the DLL via REGSVR32.EXE
- cmd.exe (PID: 2204)
- cmd.exe (PID: 1360)
- cmd.exe (PID: 3468)
SUSPICIOUS
Starts CMD.EXE for commands execution
- exec.exe (PID: 2416)
- exec.exe (PID: 3108)
- exec.exe (PID: 3216)
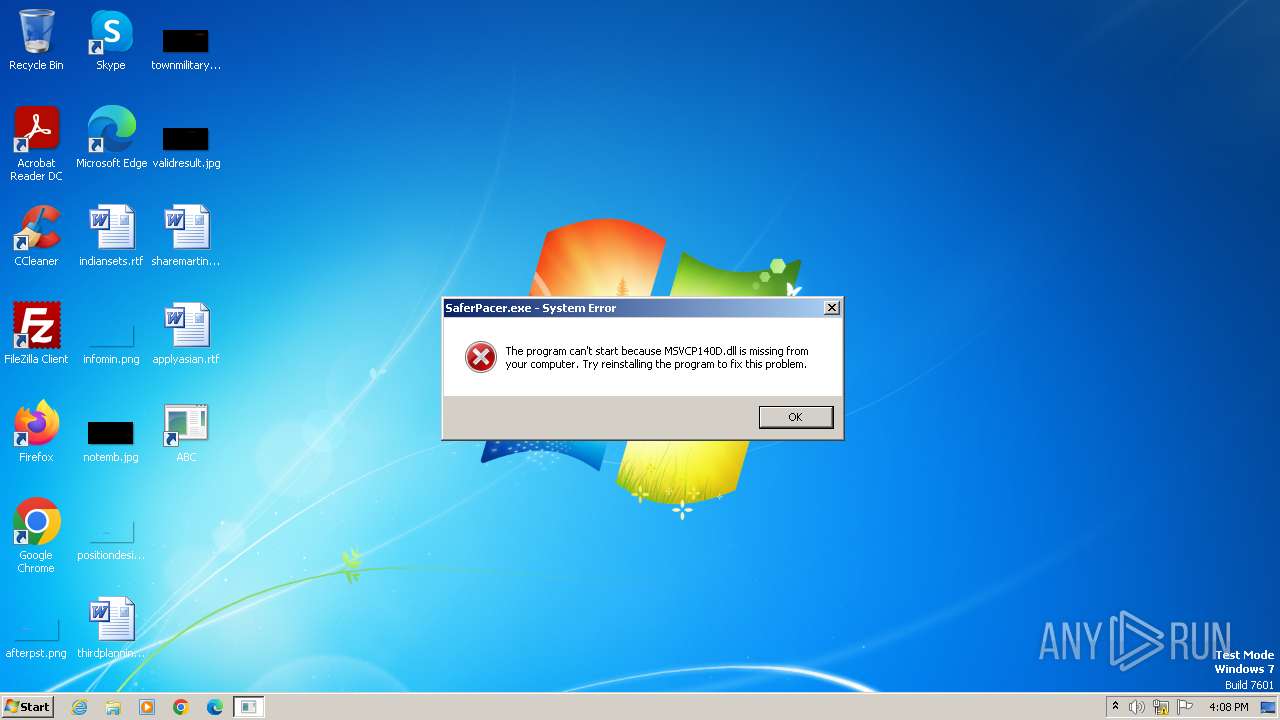
Process drops legitimate windows executable
- asdasd.tmp (PID: 2308)
Reads the Internet Settings
- exec.exe (PID: 2416)
- exec.exe (PID: 3216)
- exec.exe (PID: 3108)
Reads the Windows owner or organization settings
- asdasd.tmp (PID: 2308)
Executing commands from a ".bat" file
- exec.exe (PID: 2416)
- exec.exe (PID: 3108)
- exec.exe (PID: 3216)
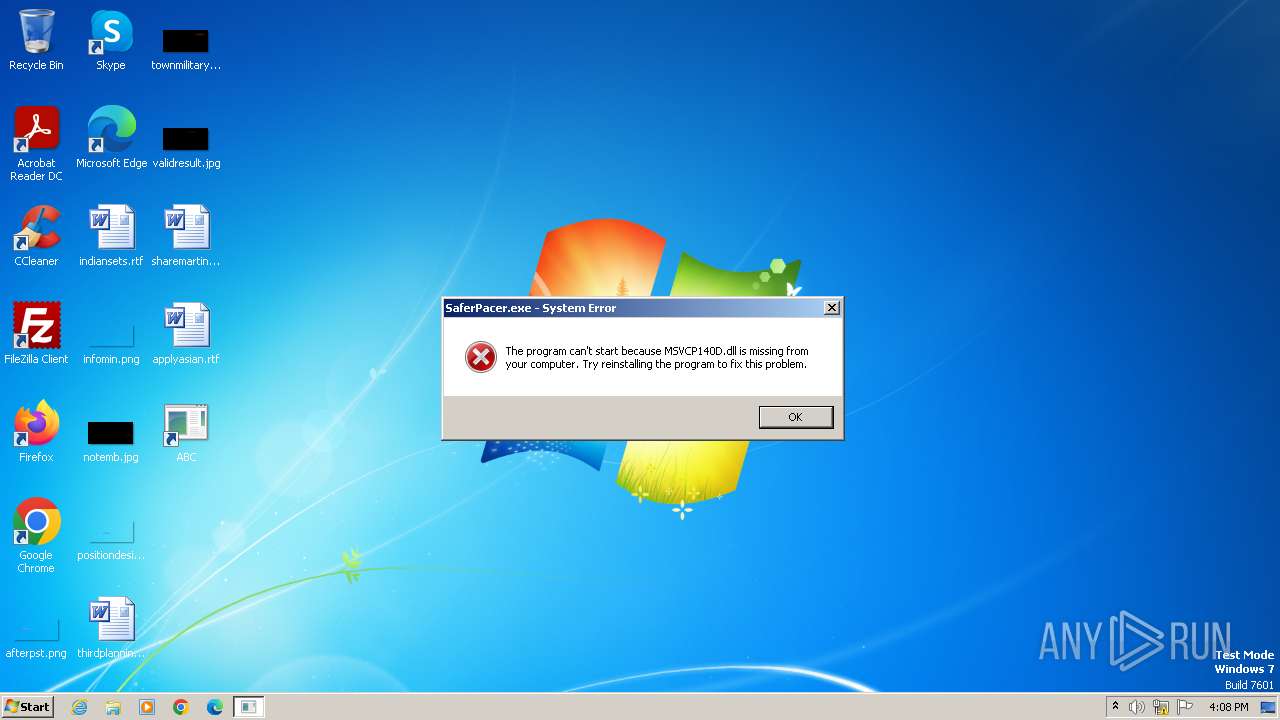
The process drops C-runtime libraries
- asdasd.tmp (PID: 2308)
INFO
Create files in a temporary directory
- asdasd.exe (PID: 2976)
- exec.exe (PID: 2416)
- asdasd.exe (PID: 888)
- exec.exe (PID: 3216)
- exec.exe (PID: 3108)
Checks supported languages
- asdasd.exe (PID: 2976)
- asdasd.tmp (PID: 844)
- asdasd.exe (PID: 888)
- asdasd.tmp (PID: 2308)
- exec.exe (PID: 2416)
- exec.exe (PID: 3216)
- exec.exe (PID: 3108)
Reads the computer name
- asdasd.tmp (PID: 2308)
- exec.exe (PID: 2416)
- asdasd.tmp (PID: 844)
- exec.exe (PID: 3108)
- exec.exe (PID: 3216)
Creates files in the program directory
- asdasd.tmp (PID: 2308)
Manual execution by a user
- exec.exe (PID: 3216)
- exec.exe (PID: 3108)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (53.5) |
|---|---|---|
| .exe | | | InstallShield setup (21) |
| .exe | | | Win32 EXE PECompact compressed (generic) (20.2) |
| .exe | | | Win32 Executable (generic) (2.1) |
| .exe | | | Win16/32 Executable Delphi generic (1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:02:15 15:54:16+01:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 741888 |
| InitializedDataSize: | 89600 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb5eec |
| OSVersion: | 6.1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
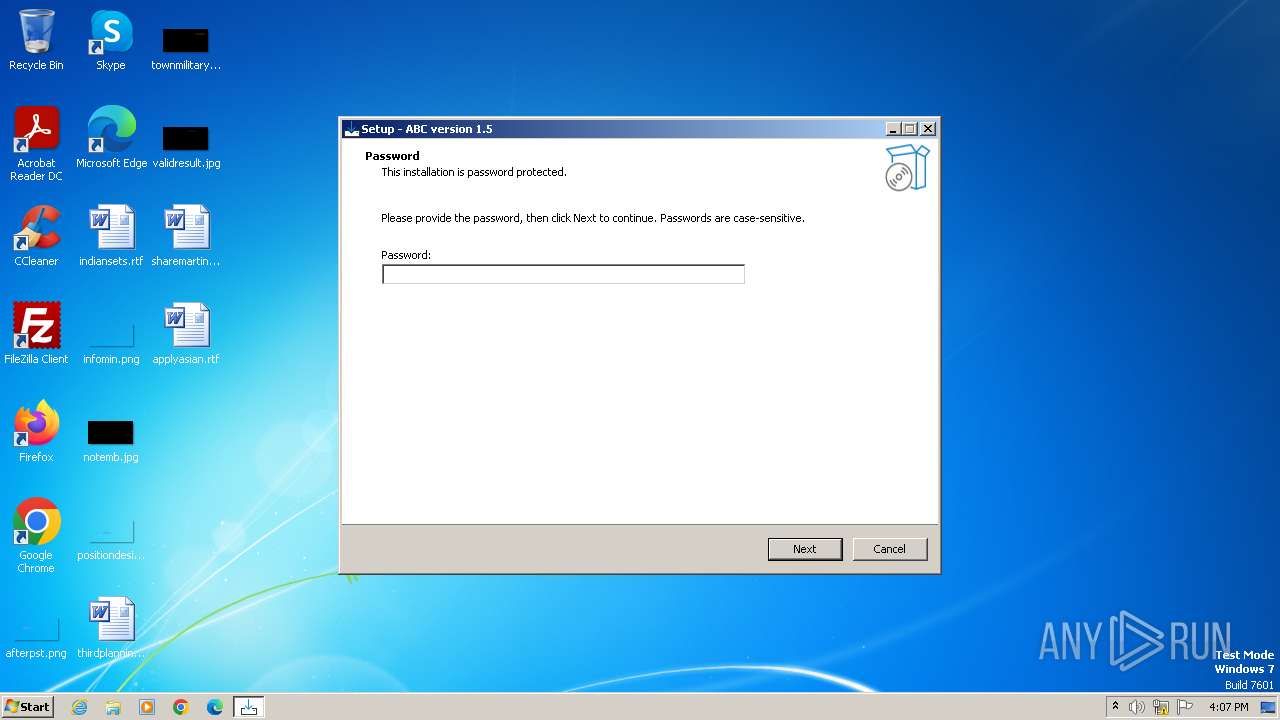
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | My Company, Inc. |
| FileDescription: | ABC Setup |
| FileVersion: | |
| LegalCopyright: | |
| OriginalFileName: | |
| ProductName: | ABC |
| ProductVersion: | 1.5 |
Total processes
64
Monitored processes
16
Malicious processes
4
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 664 | regsvr32 msvcp140.dll | C:\Windows\System32\regsvr32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft(C) Register Server Exit code: 4 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 844 | "C:\Users\admin\AppData\Local\Temp\is-KP8MI.tmp\asdasd.tmp" /SL5="$7019C,1336641,832512,C:\Users\admin\AppData\Local\Temp\asdasd.exe" | C:\Users\admin\AppData\Local\Temp\is-KP8MI.tmp\asdasd.tmp | — | asdasd.exe | |||||||||||
User: admin Company: My Company, Inc. Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 888 | "C:\Users\admin\AppData\Local\Temp\asdasd.exe" | C:\Users\admin\AppData\Local\Temp\asdasd.exe | — | explorer.exe | |||||||||||
User: admin Company: My Company, Inc. Integrity Level: MEDIUM Description: ABC Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 1360 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\6WXkRTJ0.bat" " | C:\Windows\System32\cmd.exe | — | exec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1784 | regsvr32 msvcp140.dll | C:\Windows\System32\regsvr32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft(C) Register Server Exit code: 4 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2204 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\kurxkrZp.bat" " | C:\Windows\System32\cmd.exe | — | exec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2308 | "C:\Users\admin\AppData\Local\Temp\is-MK4IK.tmp\asdasd.tmp" /SL5="$E0194,1336641,832512,C:\Users\admin\AppData\Local\Temp\asdasd.exe" /SPAWNWND=$C0182 /NOTIFYWND=$7019C | C:\Users\admin\AppData\Local\Temp\is-MK4IK.tmp\asdasd.tmp | — | asdasd.exe | |||||||||||
User: admin Company: My Company, Inc. Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 2416 | "C:\Program Files\ABC\exec.exe" | C:\Program Files\ABC\exec.exe | — | asdasd.tmp | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
| 2976 | "C:\Users\admin\AppData\Local\Temp\asdasd.exe" /SPAWNWND=$C0182 /NOTIFYWND=$7019C | C:\Users\admin\AppData\Local\Temp\asdasd.exe | asdasd.tmp | ||||||||||||
User: admin Company: My Company, Inc. Integrity Level: HIGH Description: ABC Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 3108 | "C:\Program Files\ABC\exec.exe" | C:\Program Files\ABC\exec.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
Total events
3 285
Read events
3 254
Write events
25
Delete events
6
Modification events
| (PID) Process: | (2308) asdasd.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 115 | |||
| (PID) Process: | (2308) asdasd.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | RegFilesHash |
Value: D450F7739F33D5ADC933F5AE55FC83737027BEF55C3F6210B069E0E6A1C01122 | |||
| (PID) Process: | (2308) asdasd.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | RegFiles0000 |
Value: C:\Program Files\ABC\exec.exe | |||
| (PID) Process: | (2308) asdasd.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (2308) asdasd.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | SessionHash |
Value: C809C5829014560D4EAFB17A8F0716F834A7F44BA37AC269E57E10ADB4E4771F | |||
| (PID) Process: | (2308) asdasd.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete value | Name: | Owner |
Value: 04090000B0198BDF4B21DA01 | |||
| (PID) Process: | (2308) asdasd.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2416) exec.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2416) exec.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2416) exec.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
Executable files
10
Suspicious files
3
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3468 | cmd.exe | — | ||
MD5:— | SHA256:— | |||
| 2308 | asdasd.tmp | C:\Program Files\ABC\exec.exe | executable | |
MD5:0B4BF6AD2A1954CA1A5B0EEEE9DF3CA5 | SHA256:8B93A9CE4965A612FF3CCC28F3349473AA89D630CBE3BC137D0857D4C8EB5FBA | |||
| 2308 | asdasd.tmp | C:\Program Files\ABC\unins000.dat | binary | |
MD5:C806415C14067B18937052B2D1D2BF53 | SHA256:26951A65EDEBDCB5EDC362740CA007FB4749F5A892A12915D02E9ACBF49D5968 | |||
| 2308 | asdasd.tmp | C:\Program Files\ABC\SaferPacer.exe | executable | |
MD5:58A4E799053C1589FB4FEEBCDC219DBF | SHA256:F804BDC45164D91D80D9CC7FE2E7F7134A99AFCB31C06ABDE7A6BCAC4E730056 | |||
| 2308 | asdasd.tmp | C:\Users\Public\Desktop\ABC.lnk | binary | |
MD5:E620E0A059DEC0FAF5646FF53EABF728 | SHA256:8C74D58ECF6556D3531138364E159B4FC3F30C293E6C720CDE36C8C9269199AE | |||
| 888 | asdasd.exe | C:\Users\admin\AppData\Local\Temp\is-KP8MI.tmp\asdasd.tmp | executable | |
MD5:E7F625813A3133E1124E693CD51F4A9D | SHA256:94DC10B62C04D0393DB46F6C57C9E7E59D1F26620688BB246F0619353CA63E77 | |||
| 2308 | asdasd.tmp | C:\Program Files\ABC\is-U7K05.tmp | executable | |
MD5:DD9E6E5809E98A1ECFCCF2980F46E2E0 | SHA256:2042A13D86E6D6F2EA90D0089526260ED16D3CC6DFE0D695C76DFB2995097FEF | |||
| 2308 | asdasd.tmp | C:\Program Files\ABC\is-M29H6.tmp | executable | |
MD5:58A4E799053C1589FB4FEEBCDC219DBF | SHA256:F804BDC45164D91D80D9CC7FE2E7F7134A99AFCB31C06ABDE7A6BCAC4E730056 | |||
| 2308 | asdasd.tmp | C:\Program Files\ABC\unins000.exe | executable | |
MD5:DD9E6E5809E98A1ECFCCF2980F46E2E0 | SHA256:2042A13D86E6D6F2EA90D0089526260ED16D3CC6DFE0D695C76DFB2995097FEF | |||
| 2308 | asdasd.tmp | C:\Program Files\ABC\is-SGG4E.tmp | executable | |
MD5:0B4BF6AD2A1954CA1A5B0EEEE9DF3CA5 | SHA256:8B93A9CE4965A612FF3CCC28F3349473AA89D630CBE3BC137D0857D4C8EB5FBA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |