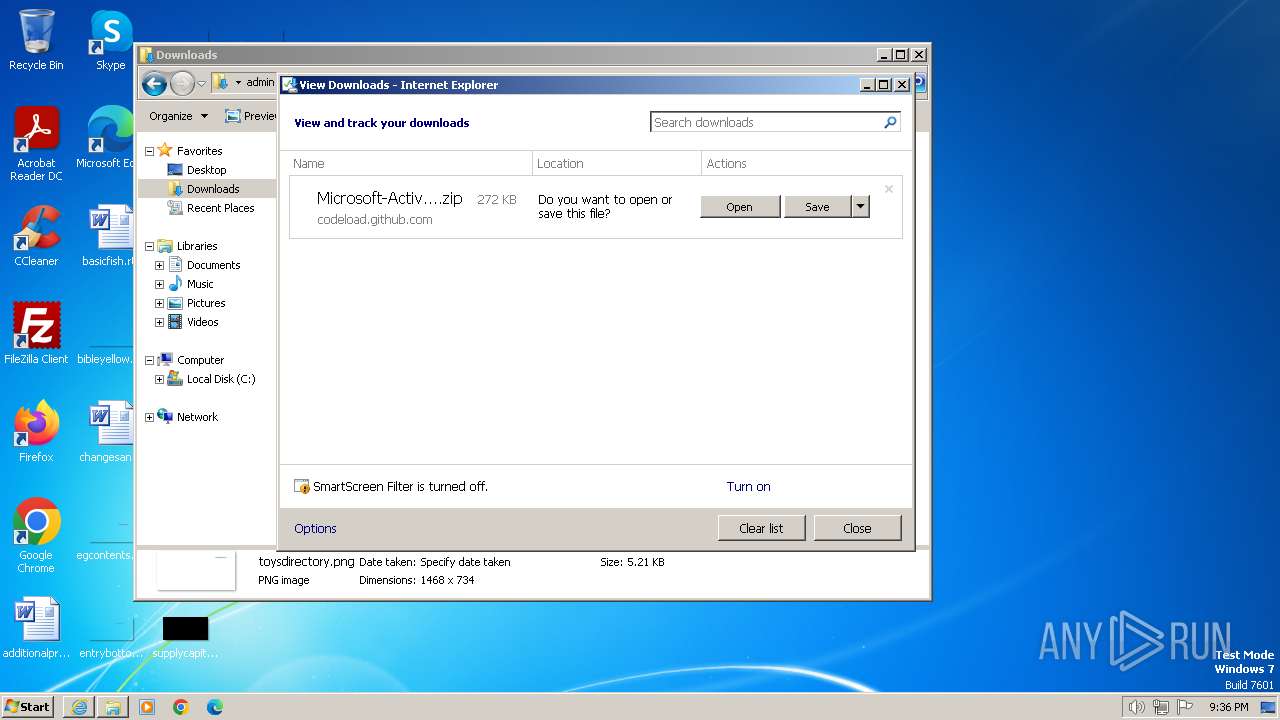
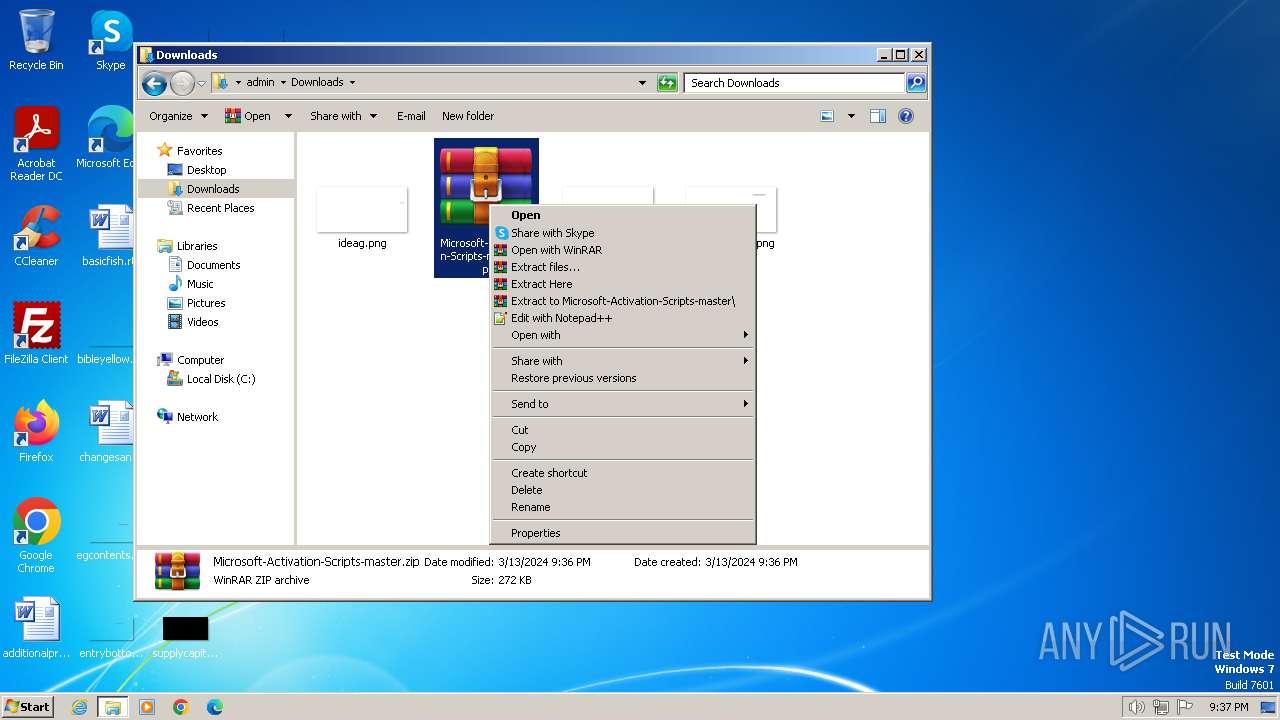
| URL: | https://github.com/massgravel/Microsoft-Activation-Scripts/archive/refs/heads/master.zip |
| Full analysis: | https://app.any.run/tasks/a18a7ded-5c62-4b7f-9367-1058b25bebd6 |
| Verdict: | Malicious activity |
| Analysis date: | March 13, 2024, 21:36:09 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 3FF8839C672B82FB74C4974355D26F22 |
| SHA1: | 82A186FD7EFEB846290087079B3AE447D3D0B3A1 |
| SHA256: | B1CC61EF885E3C1FC8E9B89903A4B2AD12FFA23A639CB29EC841064752756E88 |
| SSDEEP: | 3:N8tEd4PKoHXuukGR3RLLLGXUBNMT4RSL6o:2uuPKzukGv/LGXU7S4UL6o |
MALICIOUS
No malicious indicators.SUSPICIOUS
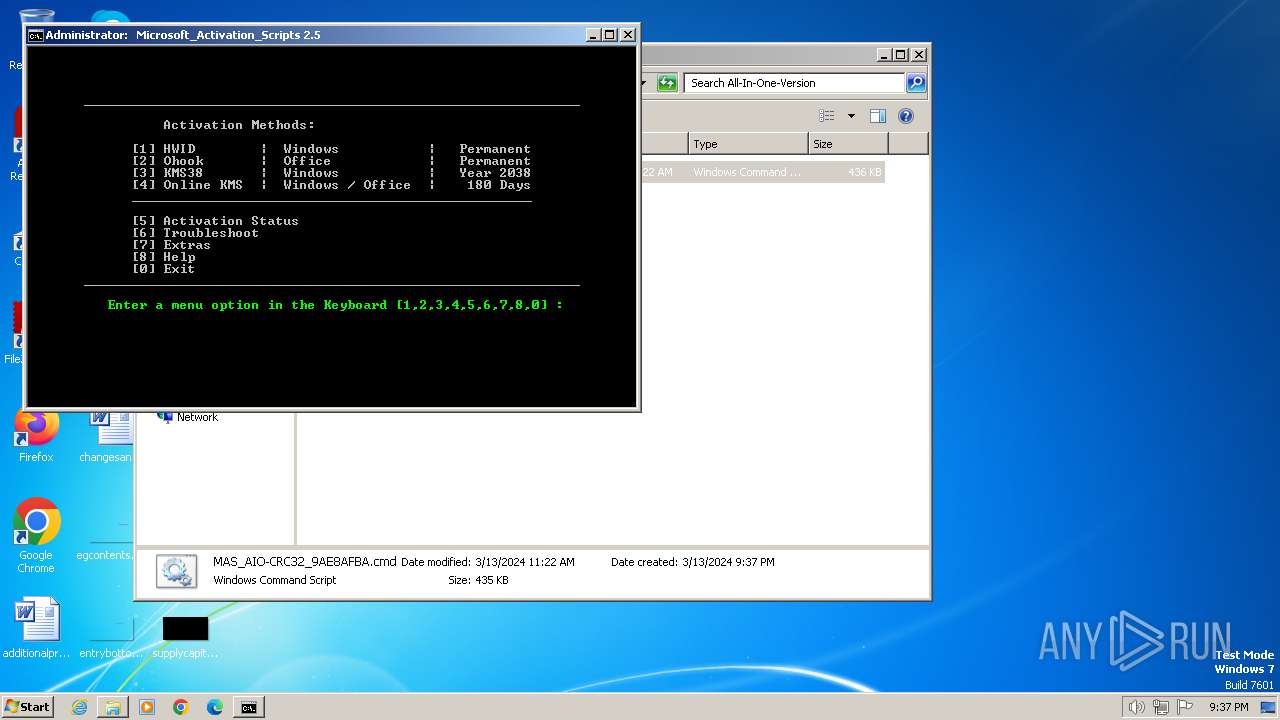
Executing commands from ".cmd" file
- cmd.exe (PID: 1540)
- powershell.exe (PID: 2588)
- cmd.exe (PID: 3140)
Application launched itself
- cmd.exe (PID: 1540)
- cmd.exe (PID: 3140)
Starts SC.EXE for service management
- cmd.exe (PID: 1540)
- cmd.exe (PID: 3140)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 1540)
- cmd.exe (PID: 3140)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 1540)
- powershell.exe (PID: 2588)
- cmd.exe (PID: 3140)
Reads the Internet Settings
- powershell.exe (PID: 2588)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 1540)
- cmd.exe (PID: 3140)
INFO
The process uses the downloaded file
- iexplore.exe (PID: 3700)
- WinRAR.exe (PID: 1112)
Modifies the phishing filter of IE
- iexplore.exe (PID: 3700)
Manual execution by a user
- explorer.exe (PID: 2692)
- WinRAR.exe (PID: 1112)
- cmd.exe (PID: 1540)
Application launched itself
- iexplore.exe (PID: 3700)
Checks operating system version
- cmd.exe (PID: 1540)
- cmd.exe (PID: 3140)
Checks supported languages
- mode.com (PID: 3048)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
90
Monitored processes
46
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 128 | C:\Windows\system32\cmd.exe /c "prompt $H&for %B in (1) do rem" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 296 | C:\Windows\system32\cmd.exe /c ver | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 392 | C:\Windows\system32\cmd.exe /S /D /c" echo "-el" " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 480 | sc query Null | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: A tool to aid in developing services for WindowsNT Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 668 | find "127.69.2.5" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 992 | find /i "C:\Users\admin\AppData\Local\Temp" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (grep) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1112 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Downloads\Microsoft-Activation-Scripts-master.zip" C:\Users\admin\Downloads\Microsoft-Activation-Scripts-master\ | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1172 | reg query HKCU\Console /v QuickEdit | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1192 | choice /C:123456780 /N | C:\Windows\System32\choice.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Offers the user a choice Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1264 | C:\Windows\system32\cmd.exe /c ver | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
20 689
Read events
20 535
Write events
114
Delete events
40
Modification events
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31094158 | |||
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31094158 | |||
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3700) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
25
Text files
22
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3952 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\A66A8DB907BADC9D16AD67B2FBFFDD5C | binary | |
MD5:CA04C6A6054267B35639885F16C443C1 | SHA256:961CA7B9F33D3D9D05D3C774723333B9C699BA2491AC3C7CA1FB2E78A86D2F38 | |||
| 3952 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\D0E1C4B6144E7ECAB3F020E4A19EFC29_B5F77004C894173A10E3A199871D2D90 | binary | |
MD5:A6A3FB7FFA6BC5F57ABA3930765C166B | SHA256:05C69EED738EAF5EDFBEBEE4C65FAF3F0EFAD7F576808F269E4869DAFB4E66B5 | |||
| 3700 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\EAF8AA29A62AB29E614331747385D816_F9E4DC0B9D5C777357D7DB8DEF51118A | der | |
MD5:B4847C3050E5E738F309421F13E030C7 | SHA256:1C1F40EC09590EE2F93B770706675A1657DC2556E9670D89E2288841A3CD812D | |||
| 3700 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\favicon[1].ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 3700 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 3952 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B2FAF7692FD9FFBD64EDE317E42334BA_89854CA6A0F0936A4D2ECA78845CEA25 | binary | |
MD5:46282C389AE14962BC5A561DB8A35CB9 | SHA256:FE4316A1D246ADCC8205813E5F965ECC538FC066C7FC66F33331AC400DD26E40 | |||
| 3952 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\D0E1C4B6144E7ECAB3F020E4A19EFC29_B5F77004C894173A10E3A199871D2D90 | binary | |
MD5:861594F08CF5D8C310D252F9A9640EA4 | SHA256:80A24034896314D432C5326BE56805EB63F0879F1A481BB9CFFDC3F13A4EC593 | |||
| 3952 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B2FAF7692FD9FFBD64EDE317E42334BA_89854CA6A0F0936A4D2ECA78845CEA25 | der | |
MD5:D6D6DC1B5FA907601ED19ED2D0BBA6E7 | SHA256:2CFCE700B5A56DF3A8CB456E149F5AF4E84735259AAAC19E593A37E1F0DDD7BB | |||
| 3952 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\A66A8DB907BADC9D16AD67B2FBFFDD5C | binary | |
MD5:F54ECF45773AF8D5DE70203C59DB1731 | SHA256:2CA0238B63AE2940E451B464178699D8447E1FDCBA15CF96BE4F9770F60C0DA2 | |||
| 3700 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\urlblockindex[1].bin | binary | |
MD5:FA518E3DFAE8CA3A0E495460FD60C791 | SHA256:775853600060162C4B4E5F883F9FD5A278E61C471B3EE1826396B6D129499AA7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
23
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3700 | iexplore.exe | GET | 304 | 23.53.41.250:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?74c153e8c4875ce9 | unknown | — | — | unknown |
3700 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | binary | 313 b | unknown |
3952 | iexplore.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.usertrust.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBSr83eyJy3njhjVpn5bEpfc6MXawQQUOuEJhtTPGcKWdnRJdtzgNcZjY5oCEQDzZE5rbgBQI34JRr174fUd | unknown | binary | 978 b | unknown |
3952 | iexplore.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEFZnHQTqT5lMbxCBR1nSdZQ%3D | unknown | binary | 1.42 Kb | unknown |
3700 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
3952 | iexplore.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTPlNxcMEqnlIVyH5VuZ4lawhZX3QQU9oUKOxGG4QR9DqoLLNLuzGR7e64CEE4o94a2bBo7lCzSxA63QqU%3D | unknown | binary | 281 b | unknown |
3952 | iexplore.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTPlNxcMEqnlIVyH5VuZ4lawhZX3QQU9oUKOxGG4QR9DqoLLNLuzGR7e64CEQCL3A%2F%2FVHcvqtFzJz8jNiqv | unknown | binary | 281 b | unknown |
1080 | svchost.exe | GET | 304 | 184.24.77.173:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?c14a917a25499794 | unknown | compressed | 67.5 Kb | unknown |
1080 | svchost.exe | GET | 200 | 184.24.77.173:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?4f071b604691de88 | unknown | compressed | 67.5 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3952 | iexplore.exe | 140.82.121.4:443 | github.com | GITHUB | US | unknown |
3700 | iexplore.exe | 104.126.37.184:443 | www.bing.com | Akamai International B.V. | DE | unknown |
3700 | iexplore.exe | 23.53.41.250:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
3700 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3700 | iexplore.exe | 104.126.37.130:443 | www.bing.com | Akamai International B.V. | DE | unknown |
3952 | iexplore.exe | 104.18.38.233:80 | ocsp.comodoca.com | CLOUDFLARENET | — | shared |
3952 | iexplore.exe | 172.64.149.23:80 | ocsp.comodoca.com | CLOUDFLARENET | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
github.com |
| shared |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
ocsp.sectigo.com |
| whitelisted |
codeload.github.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |