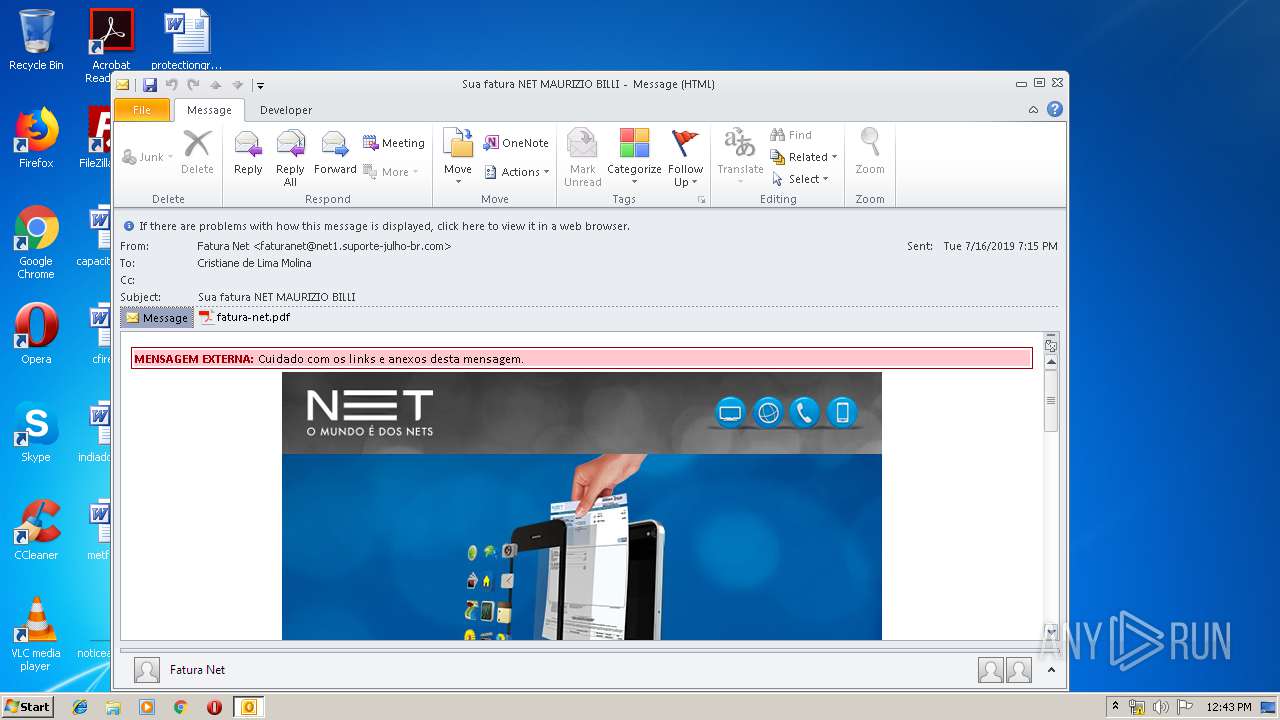
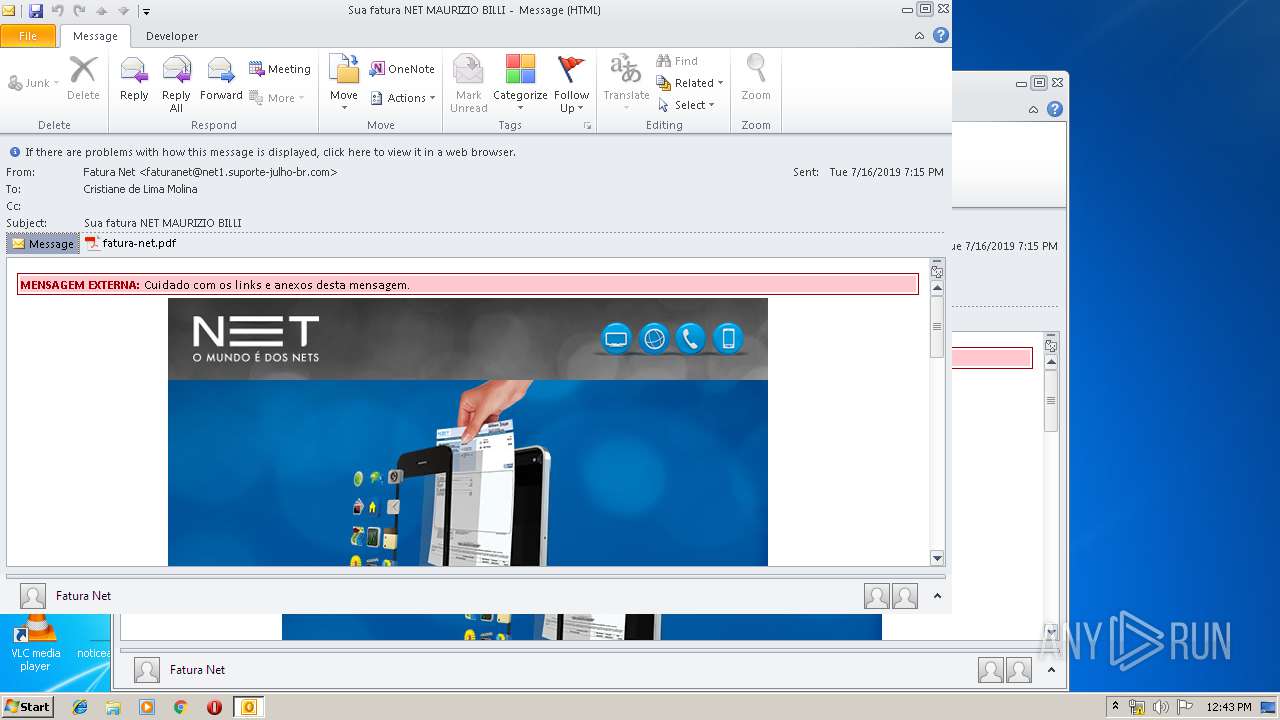
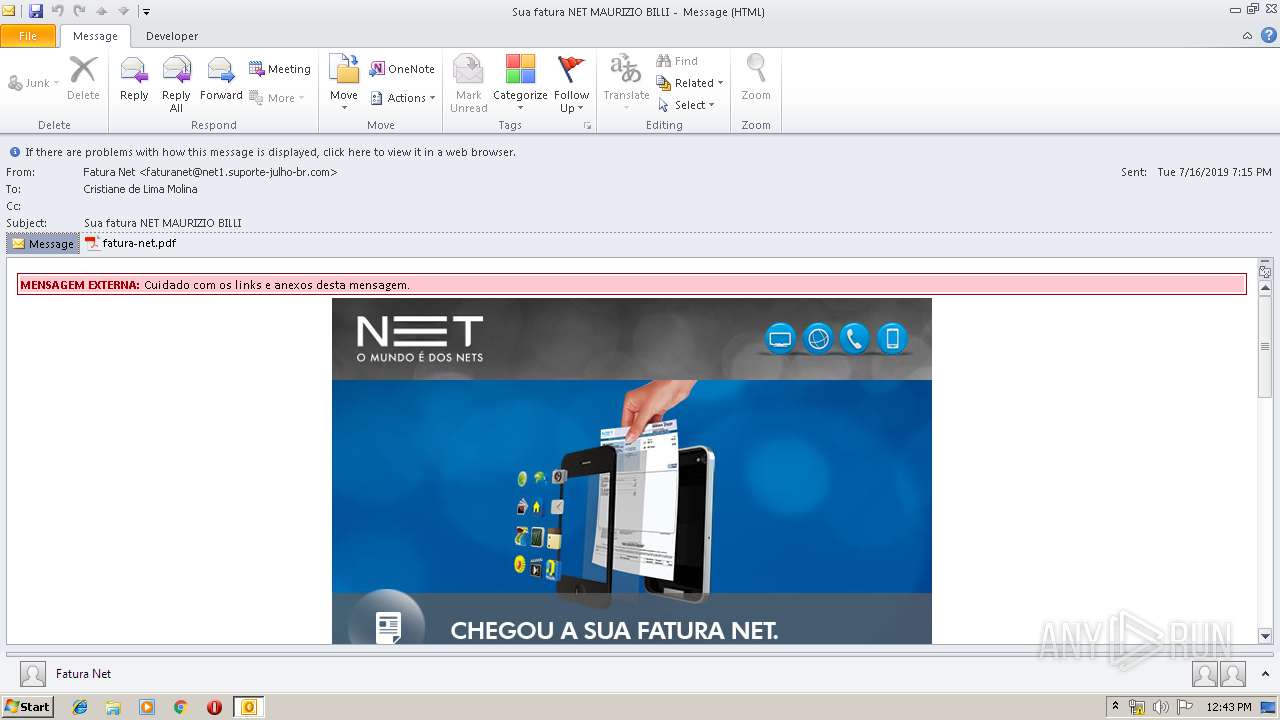
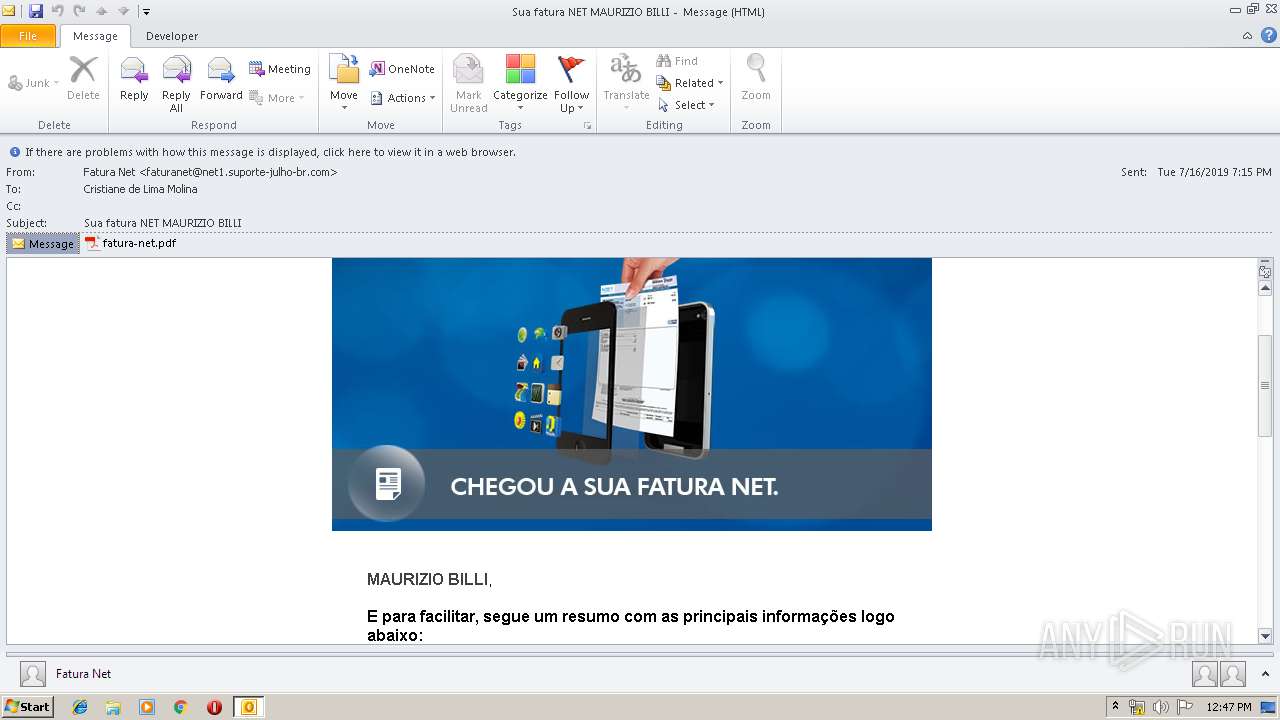
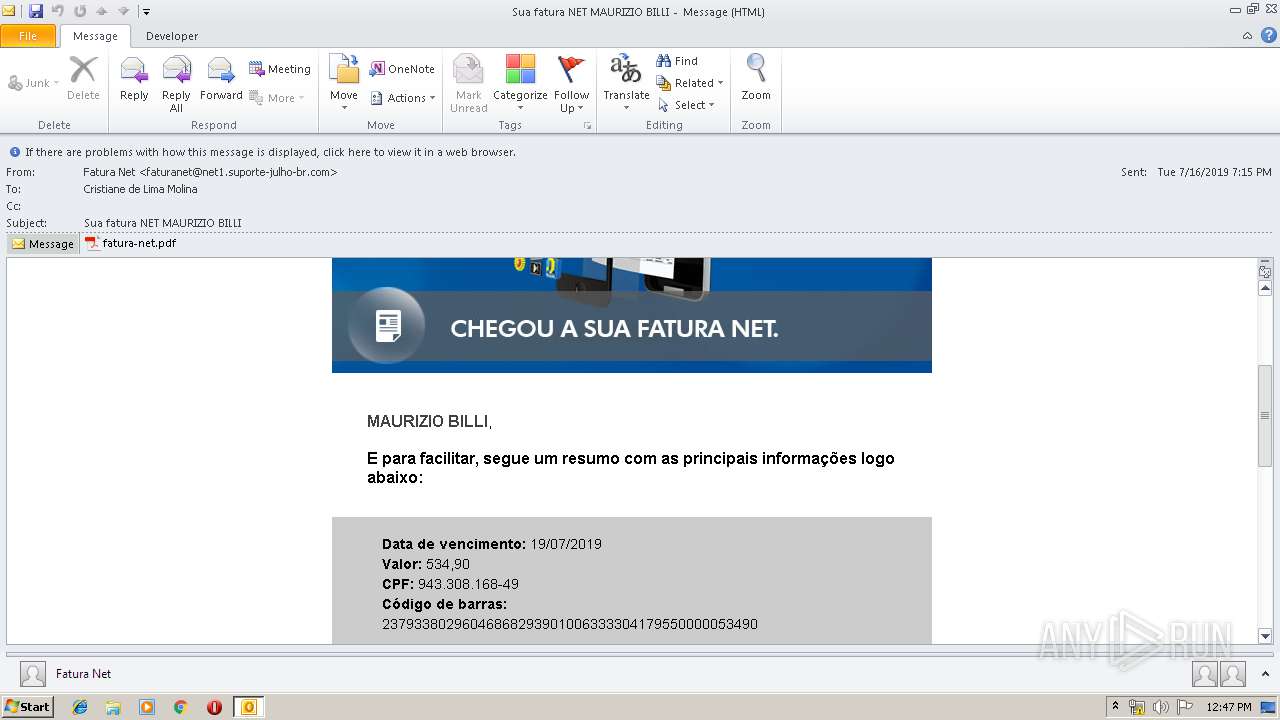
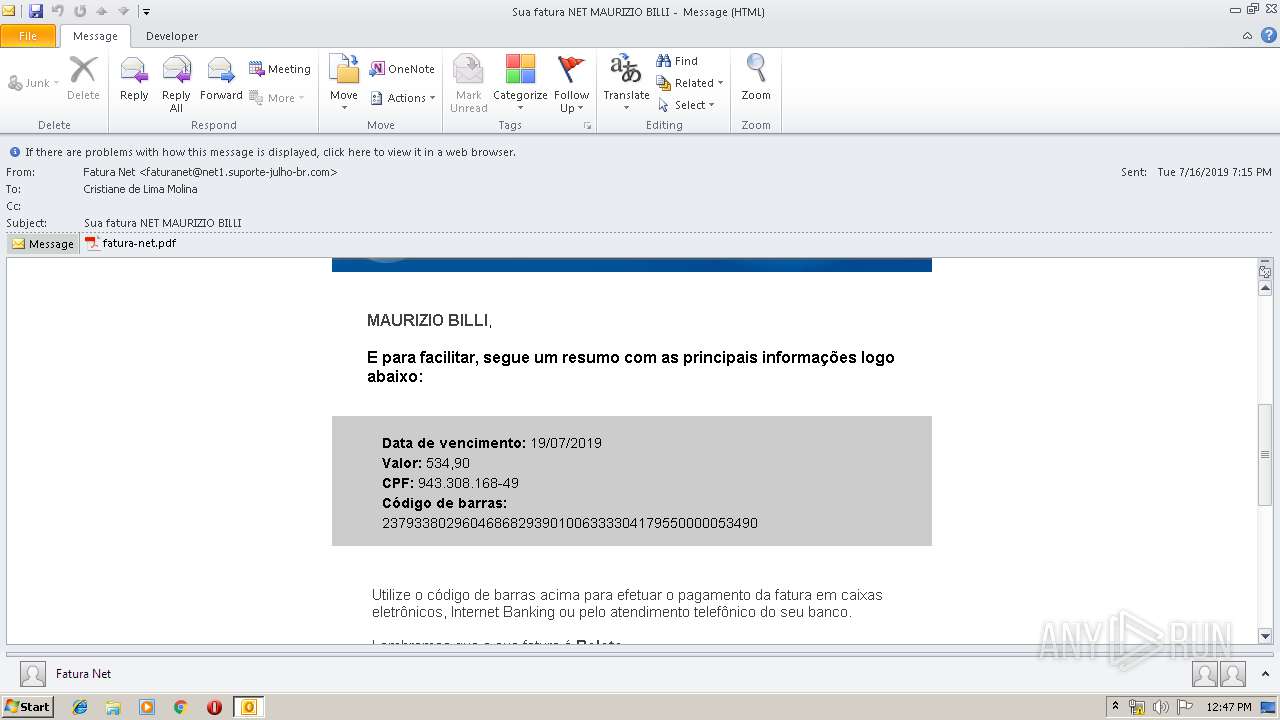
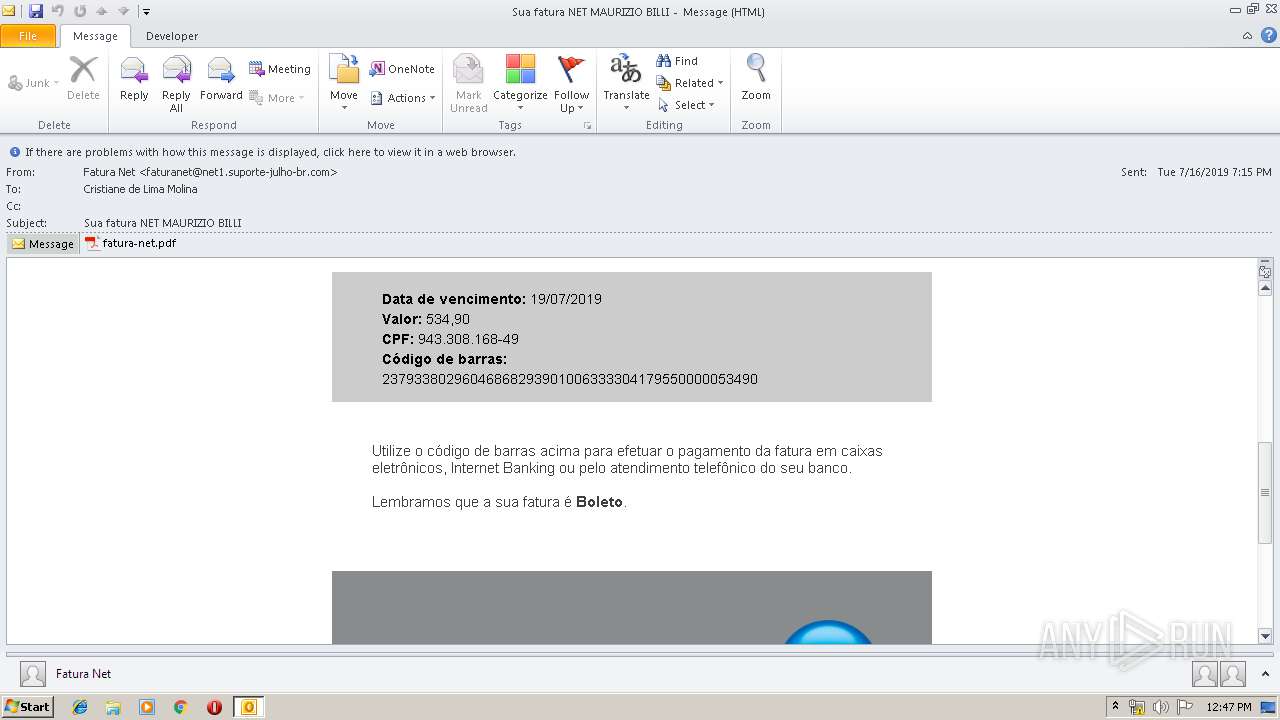
| File name: | Sua fatura NET MAURIZIO BILLI.msg |
| Full analysis: | https://app.any.run/tasks/70b8d0c4-982a-45ae-b792-544c0826fbc8 |
| Verdict: | Malicious activity |
| Analysis date: | July 17, 2019, 11:42:36 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | 5E35DBD9B2E58D0602E7B534D98BB351 |
| SHA1: | DEB43049691E8A5E15EA7B46DA6F208C3411541F |
| SHA256: | B1B41CCD4FF7741609091D4DFEBA10C96A2BC30A5FE6EABE0809BDA023B41857 |
| SSDEEP: | 1536:Y8UfDzKhhWkWQ9gtAuNtNBqOhbuzIw3IW7m:zUfDzKctNBhbWIw3IW7m |
MALICIOUS
Unusual execution from Microsoft Office
- OUTLOOK.EXE (PID: 3844)
SUSPICIOUS
Creates files in the user directory
- OUTLOOK.EXE (PID: 3844)
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 3844)
Starts Internet Explorer
- OUTLOOK.EXE (PID: 3844)
INFO
Application launched itself
- RdrCEF.exe (PID: 2528)
- iexplore.exe (PID: 3236)
Reads Internet Cache Settings
- iexplore.exe (PID: 2852)
Changes internet zones settings
- iexplore.exe (PID: 3236)
Reads internet explorer settings
- iexplore.exe (PID: 2852)
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 3844)
Creates files in the user directory
- iexplore.exe (PID: 2852)
- iexplore.exe (PID: 3236)
Reads settings of System Certificates
- iexplore.exe (PID: 3236)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msg | | | Outlook Message (58.9) |
|---|---|---|
| .oft | | | Outlook Form Template (34.4) |
Total processes
44
Monitored processes
8
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2528 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --backgroundcolor=16448250 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe RdrCEF Exit code: 3221225547 Version: 15.23.20053.211670 Modules
| |||||||||||||||
| 2852 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3236 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2952 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --disable-3d-apis --disable-databases --disable-direct-npapi-requests --disable-file-system --disable-notifications --disable-shared-workers --disable-direct-write --lang=en-US --lang=en-US --log-severity=disable --product-version="ReaderServices/15.23.20053 Chrome/45.0.2454.85" --device-scale-factor=1 --enable-delegated-renderer --num-raster-threads=2 --gpu-rasterization-msaa-sample-count=8 --content-image-texture-target=3553 --video-image-texture-target=3553 --disable-accelerated-video-decode --disable-webrtc-hw-encoding --disable-gpu-compositing --channel="2528.1.658466009\1966665134" --allow-no-sandbox-job /prefetch:673131151 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
| 3012 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --disable-3d-apis --disable-databases --disable-direct-npapi-requests --disable-file-system --disable-notifications --disable-shared-workers --disable-direct-write --lang=en-US --lang=en-US --log-severity=disable --product-version="ReaderServices/15.23.20053 Chrome/45.0.2454.85" --device-scale-factor=1 --enable-delegated-renderer --num-raster-threads=2 --gpu-rasterization-msaa-sample-count=8 --content-image-texture-target=3553 --video-image-texture-target=3553 --disable-accelerated-video-decode --disable-webrtc-hw-encoding --disable-gpu-compositing --channel="2528.0.90562465\2114048118" --allow-no-sandbox-job /prefetch:673131151 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
| 3104 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" --type=renderer "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\FUZ2A201\fatura-net.pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Reader DC Exit code: 1 Version: 15.23.20070.215641 Modules
| |||||||||||||||
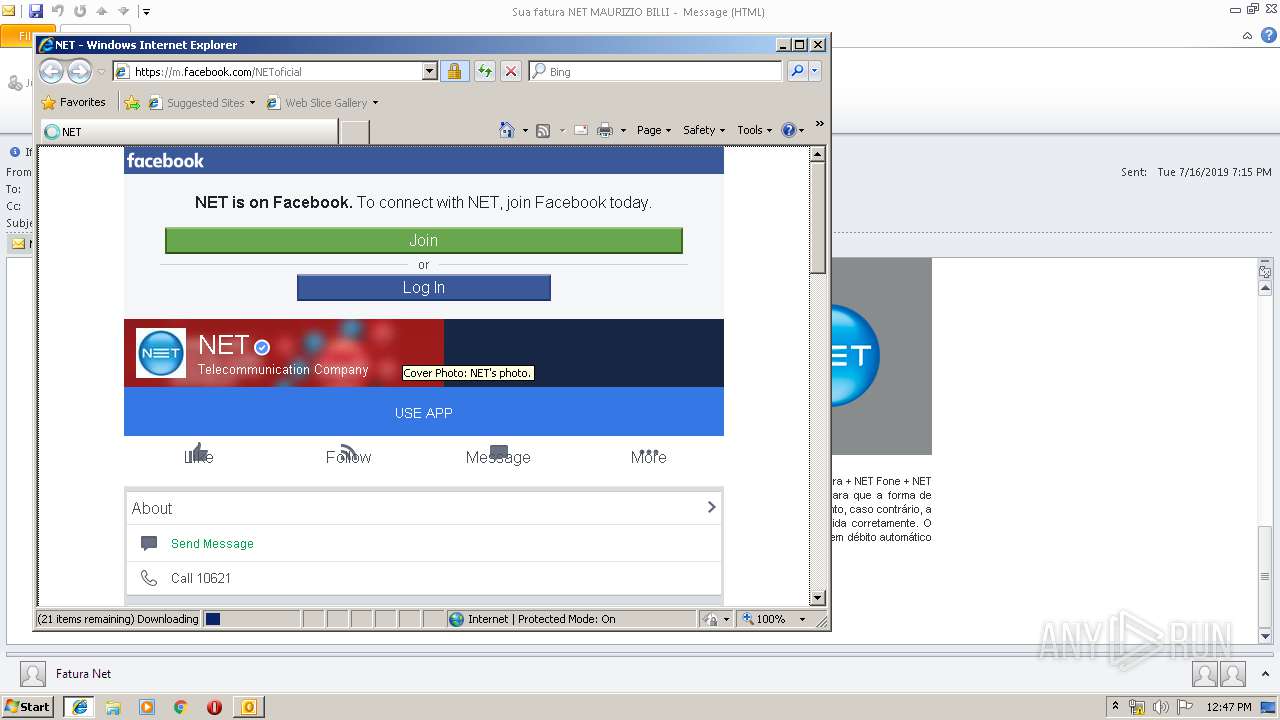
| 3236 | "C:\Program Files\Internet Explorer\iexplore.exe" https://www.facebook.com/NEToficial | C:\Program Files\Internet Explorer\iexplore.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3392 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\FUZ2A201\fatura-net.pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Reader DC Exit code: 1 Version: 15.23.20070.215641 Modules
| |||||||||||||||
| 3844 | "C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE" /f "C:\Users\admin\AppData\Local\Temp\Sua fatura NET MAURIZIO BILLI.msg" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
Total events
2 164
Read events
1 620
Write events
525
Delete events
19
Modification events
| (PID) Process: | (3844) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3844) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3844) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\Resiliency\StartupItems |
| Operation: | write | Name: | "#= |
Value: 22233D00040F0000010000000000000000000000 | |||
| (PID) Process: | (3844) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook |
| Operation: | write | Name: | MTTT |
Value: 040F0000705A31C5943CD50100000000 | |||
| (PID) Process: | (3844) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\SQM |
| Operation: | write | Name: | SQMSessionNumber |
Value: 0 | |||
| (PID) Process: | (3844) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\SQM |
| Operation: | write | Name: | SQMSessionDate |
Value: 220129920 | |||
| (PID) Process: | (3844) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\0a0d020000000000c000000000000046 |
| Operation: | write | Name: | 00030429 |
Value: 03000000 | |||
| (PID) Process: | (3844) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\9375CFF0413111d3B88A00104B2A6676 |
| Operation: | write | Name: | {ED475418-B0D6-11D2-8C3B-00104B2A6676} |
Value: | |||
| (PID) Process: | (3844) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\9375CFF0413111d3B88A00104B2A6676 |
| Operation: | write | Name: | LastChangeVer |
Value: 1200000000000000 | |||
| (PID) Process: | (3844) OUTLOOK.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109A10090400000000000F01FEC\Usage |
| Operation: | write | Name: | OutlookMAPI2Intl_1033 |
Value: 1324417045 | |||
Executable files
0
Suspicious files
5
Text files
60
Unknown types
20
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3844 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVRF722.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3844 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\JGRR2OYX\social-4[1].gif | image | |
MD5:— | SHA256:— | |||
| 3844 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\FUZ2A201\fatura-net (2).pdf\:Zone.Identifier:$DATA | — | |
MD5:— | SHA256:— | |||
| 3844 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\social-2[1].gif | image | |
MD5:— | SHA256:— | |||
| 3104 | AcroRd32.exe | C:\Users\admin\AppData\LocalLow\Adobe\Acrobat\DC\ReaderMessages-journal | — | |
MD5:— | SHA256:— | |||
| 3844 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3104 | AcroRd32.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\Cache\AdobeFnt16.lst.3104 | — | |
MD5:— | SHA256:— | |||
| 3844 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\JGRR2OYX\siga[1].gif | image | |
MD5:— | SHA256:— | |||
| 3104 | AcroRd32.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\AdobeFnt16.lst.3104 | — | |
MD5:— | SHA256:— | |||
| 3844 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\logo[1].jpg | image | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
15
TCP/UDP connections
35
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3844 | OUTLOOK.EXE | GET | 301 | 152.195.52.2:80 | http://www.netcombo.com.br/static/email/20161118120507/images/banner.jpg | US | — | — | whitelisted |
3844 | OUTLOOK.EXE | GET | 301 | 152.195.52.2:80 | http://www.netcombo.com.br/static/email/20161118120507/images/siga.gif | US | — | — | whitelisted |
3844 | OUTLOOK.EXE | GET | 301 | 152.195.52.2:80 | http://www.netcombo.com.br/static/email/20161118120507/images/social-2.gif | US | — | — | whitelisted |
3844 | OUTLOOK.EXE | GET | 301 | 152.195.52.2:80 | http://www.netcombo.com.br/static/email/20161118120507/images/social-1.gif | US | — | — | whitelisted |
3844 | OUTLOOK.EXE | GET | 301 | 152.195.52.2:80 | http://www.netcombo.com.br/static/email/20161118120507/images/social-4.gif | US | — | — | whitelisted |
3844 | OUTLOOK.EXE | GET | 301 | 152.195.52.2:80 | http://www.netcombo.com.br/static/email/20161118120507/images/social-3.gif | US | — | — | whitelisted |
3844 | OUTLOOK.EXE | GET | 301 | 152.195.52.2:80 | http://www.netcombo.com.br/static/email/20161118120507/images/social-5.gif | US | — | — | whitelisted |
3392 | AcroRd32.exe | GET | 304 | 2.16.186.33:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/280_15_23_20070.zip | unknown | — | — | whitelisted |
3392 | AcroRd32.exe | GET | 304 | 2.16.186.33:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/message.zip | unknown | — | — | whitelisted |
3392 | AcroRd32.exe | GET | 304 | 2.16.186.33:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/278_15_23_20070.zip | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3392 | AcroRd32.exe | 2.16.186.33:80 | acroipm2.adobe.com | Akamai International B.V. | — | whitelisted |
3392 | AcroRd32.exe | 2.18.233.74:443 | armmf.adobe.com | Akamai International B.V. | — | whitelisted |
2852 | iexplore.exe | 31.13.92.36:443 | www.facebook.com | Facebook, Inc. | IE | whitelisted |
3236 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
— | — | 31.13.92.36:443 | www.facebook.com | Facebook, Inc. | IE | whitelisted |
2852 | iexplore.exe | 31.13.64.21:443 | scontent-amt2-1.xx.fbcdn.net | Facebook, Inc. | IE | whitelisted |
2852 | iexplore.exe | 157.240.20.19:443 | static.xx.fbcdn.net | Facebook, Inc. | US | whitelisted |
3236 | iexplore.exe | 31.13.92.36:443 | www.facebook.com | Facebook, Inc. | IE | whitelisted |
3844 | OUTLOOK.EXE | 152.195.52.2:80 | www.netcombo.com.br | MCI Communications Services, Inc. d/b/a Verizon Business | US | unknown |
3844 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.netcombo.com.br |
| whitelisted |
config.messenger.msn.com |
| whitelisted |
acroipm2.adobe.com |
| whitelisted |
armmf.adobe.com |
| whitelisted |
www.facebook.com |
| whitelisted |
www.bing.com |
| whitelisted |
m.facebook.com |
| whitelisted |
static.xx.fbcdn.net |
| whitelisted |
scontent-amt2-1.xx.fbcdn.net |
| whitelisted |
facebook.com |
| whitelisted |