| File name: | g.exe |
| Full analysis: | https://app.any.run/tasks/a23e6181-50d4-43d4-889f-83aeef130bf2 |
| Verdict: | Malicious activity |
| Analysis date: | December 05, 2024, 17:25:52 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 6 sections |
| MD5: | 9C2AEB99843094262E5038FD152A7DB1 |
| SHA1: | 7596F6274F2AC19D4D1DF5A718A561ACFD730D3C |
| SHA256: | B1A74465A8C446D1B86D5984DEFDC18C9C06AD6107B7EB147F37DF9B78CDA104 |
| SSDEEP: | 98304:FOhQz1oKxRDaDLSPpegYgVbEwhTs0+VyVK:gz |
MALICIOUS
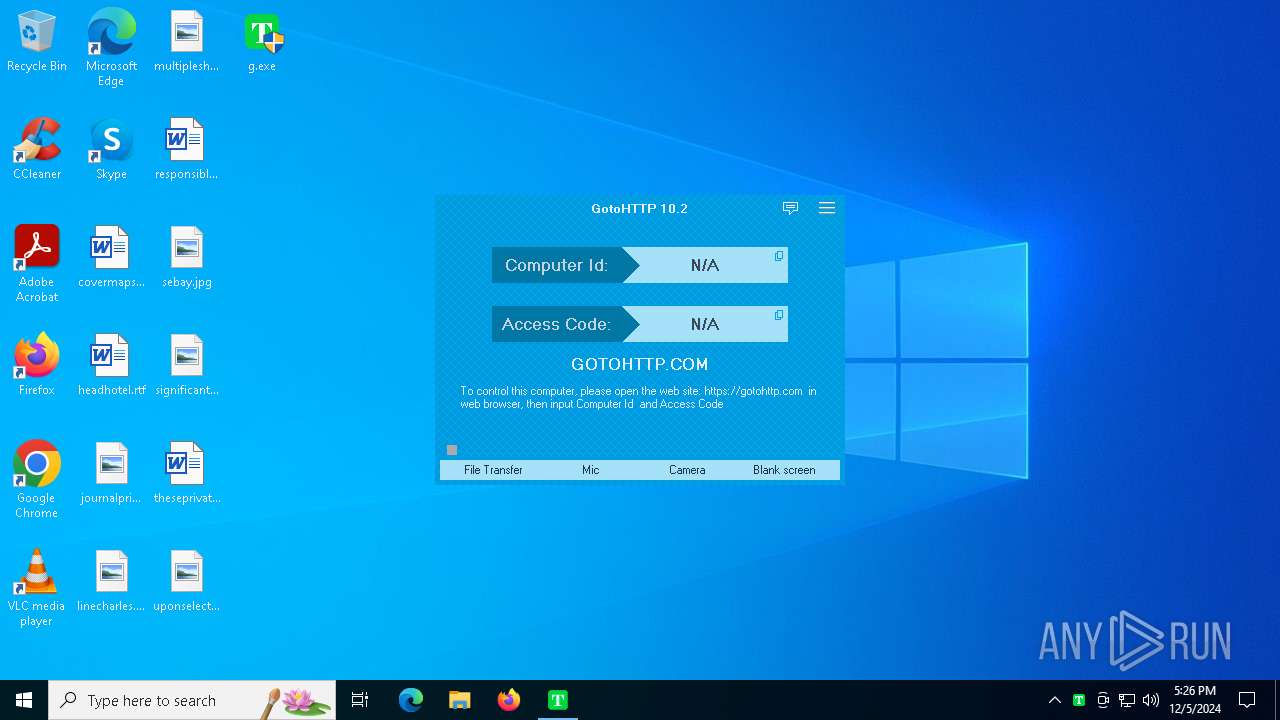
GOTOHTTP has been found
- g.exe (PID: 6624)
- g.exe (PID: 6648)
- g.exe (PID: 6676)
GOTOHTTP mutex has been found
- g.exe (PID: 6648)
- g.exe (PID: 6676)
SUSPICIOUS
Executes as Windows Service
- g.exe (PID: 6648)
Application launched itself
- g.exe (PID: 6648)
INFO
Reads the computer name
- g.exe (PID: 6648)
- g.exe (PID: 6624)
- g.exe (PID: 6676)
Checks supported languages
- g.exe (PID: 6648)
- g.exe (PID: 6676)
- g.exe (PID: 6624)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:05:11 01:53:45+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 9 |
| CodeSize: | 2151424 |
| InitializedDataSize: | 672768 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1c5cff |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 10.2.0.1925 |
| ProductVersionNumber: | 10.2.0.1925 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Dynamic link library |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Pingbo Inc |
| FileDescription: | GotoHTTP |
| FileVersion: | 10.2.0.1925 |
| InternalName: | GotoHTTP |
| LegalCopyright: | Copyright 2018-2024 Pingbo Inc |
| OriginalFileName: | GotoHTTP.exe |
| ProductName: | GotoHTTP |
| ProductVersion: | 10.2.0.1925 |
Total processes
121
Monitored processes
4
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 6492 | "C:\Users\admin\Desktop\g.exe" | C:\Users\admin\Desktop\g.exe | — | explorer.exe | |||||||||||
User: admin Company: Pingbo Inc Integrity Level: MEDIUM Description: GotoHTTP Exit code: 3221226540 Version: 10.2.0.1925 Modules
| |||||||||||||||
| 6624 | "C:\Users\admin\Desktop\g.exe" | C:\Users\admin\Desktop\g.exe | explorer.exe | ||||||||||||
User: admin Company: Pingbo Inc Integrity Level: HIGH Description: GotoHTTP Exit code: 0 Version: 10.2.0.1925 Modules
| |||||||||||||||
| 6648 | "C:\Users\admin\Desktop\g.exe" service | C:\Users\admin\Desktop\g.exe | services.exe | ||||||||||||
User: SYSTEM Company: Pingbo Inc Integrity Level: SYSTEM Description: GotoHTTP Version: 10.2.0.1925 Modules
| |||||||||||||||
| 6676 | "C:\Users\admin\Desktop\g.exe" Global\GotoHTTP_1 | C:\Users\admin\Desktop\g.exe | g.exe | ||||||||||||
User: SYSTEM Company: Pingbo Inc Integrity Level: SYSTEM Description: GotoHTTP Version: 10.2.0.1925 Modules
| |||||||||||||||
Total events
290
Read events
289
Write events
1
Delete events
0
Modification events
| (PID) Process: | (6624) g.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | SoftwareSASGeneration |
Value: 1 | |||
Executable files
0
Suspicious files
0
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6676 | g.exe | C:\Users\admin\Desktop\gotohttp.ini | text | |
MD5:D35E52D791DA98679F8AE07FCD931729 | SHA256:8D67FD59B92399F7CC34CA04B42D05537BCEF371517761733ECFD8BDB850BD58 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
56
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3568 | svchost.exe | GET | 200 | 23.216.77.14:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.14:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 43.130.10.102:443 | https://usw.gotohttp.com/gotover.12x?ver=102&lang=en | unknown | binary | 352 b | unknown |
— | — | GET | 200 | 43.130.10.102:443 | https://def.gotohttp.com/reg.12x?c=1&sn=r3AbXQcEHl8sPwsjMy4FcSgcXylbcihWcS9BEikBWCxgUSZUFFFoCTcnJSVBWVo2Ww8 | unknown | binary | 121 b | unknown |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.37.237.227:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3568 | svchost.exe | GET | 200 | 23.37.237.227:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 43.130.10.102:443 | https://usw.gotohttp.com/reg.12x?id=lYTrEkJRd1taBVVdZw&sn=lYTrXDQJNAQiZDA7ADcpJgwTVXZfKygEKCQBXDEaX34vWmFRVVNkUm18NydTV0IvWkQ&ver=GotoHTTP10.2 | unknown | binary | 10 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 2.16.204.160:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3568 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
6676 | g.exe | 43.130.10.102:443 | def.gotohttp.com | Tencent Building, Kejizhongyi Avenue | US | suspicious |
3568 | svchost.exe | 23.216.77.14:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.216.77.14:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.37.237.227:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
def.gotohttp.com |
| unknown |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
usw.gotohttp.com |
| unknown |
eu.gotohttp.com |
| unknown |
tk.gotohttp.com |
| unknown |
settings-win.data.microsoft.com |
| whitelisted |
hk.gotohttp.com |
| unknown |