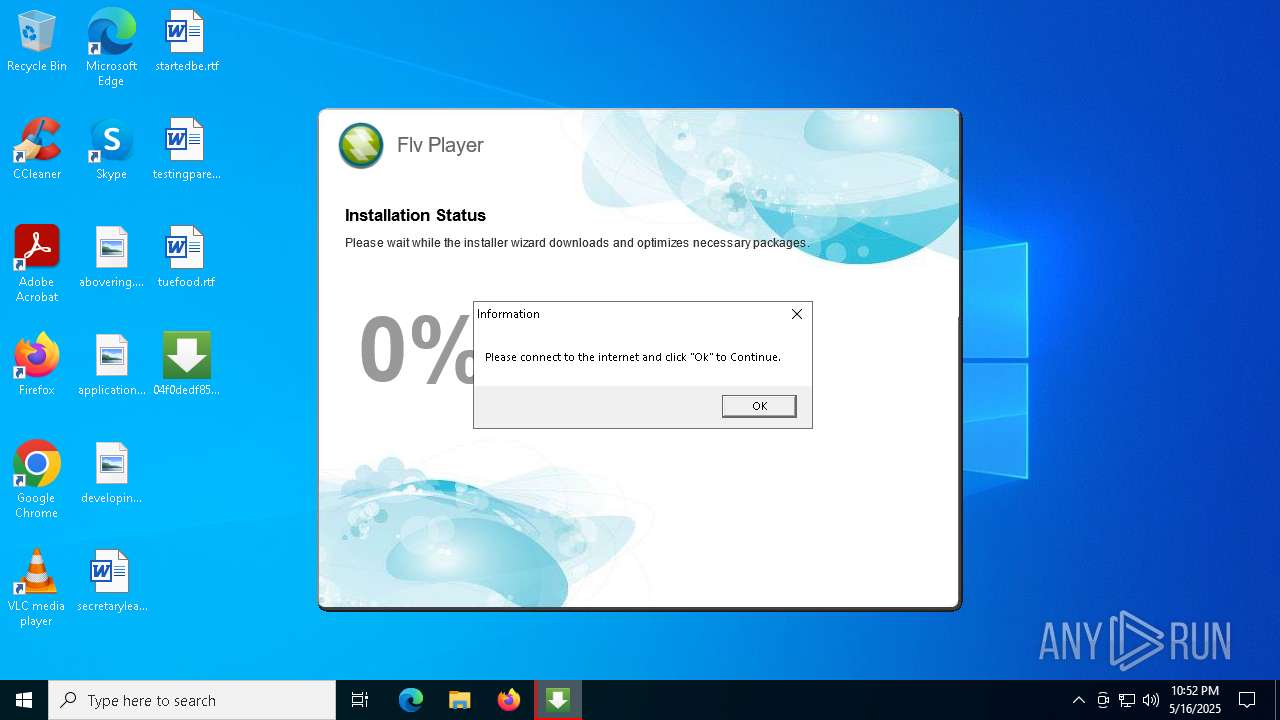
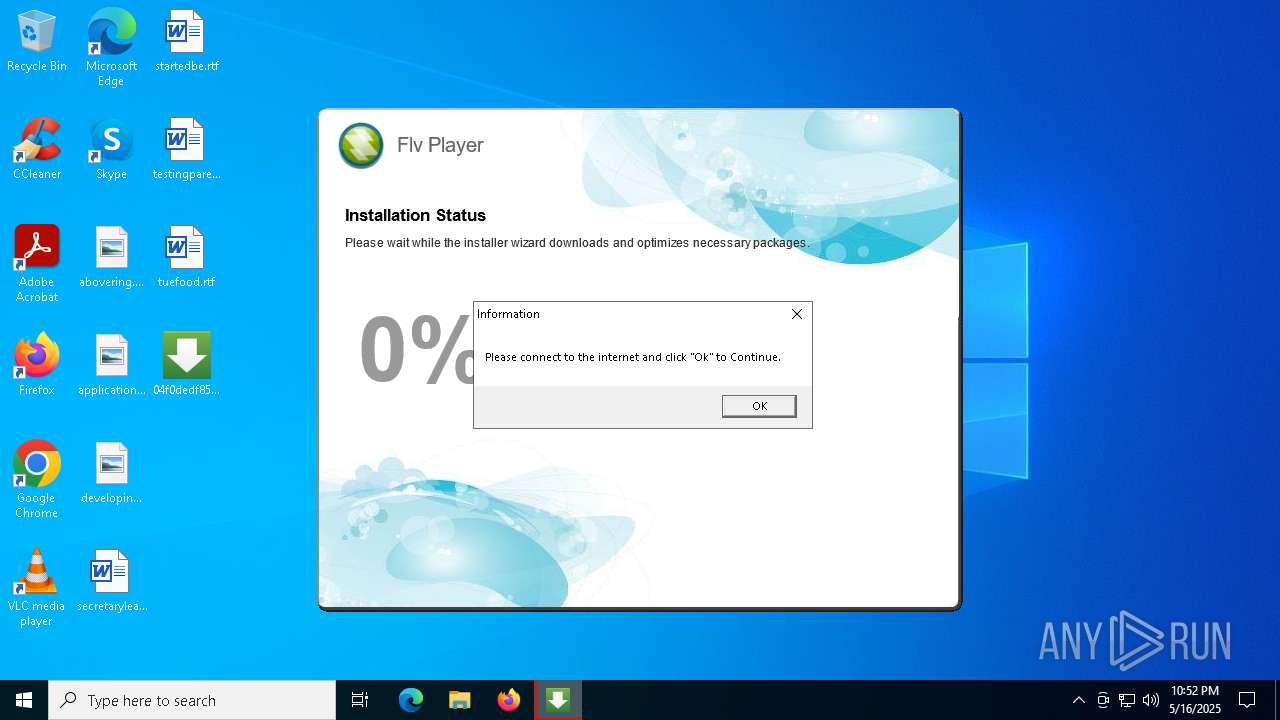
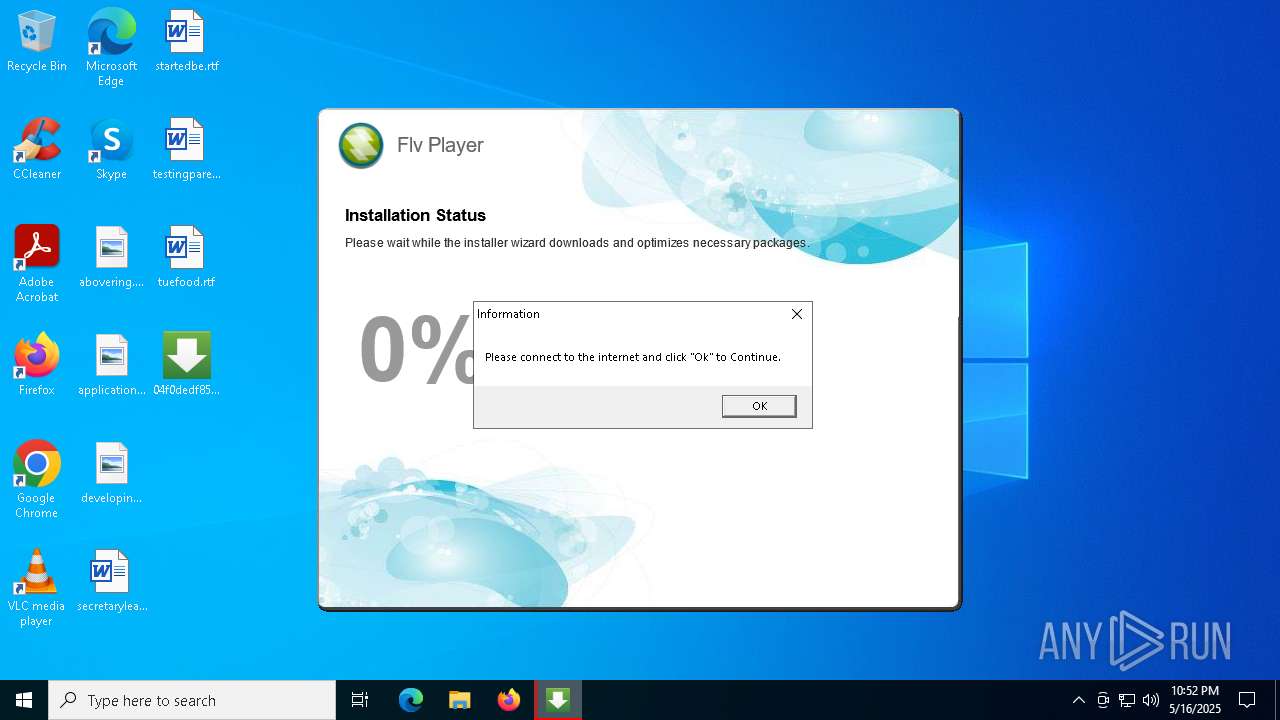
| File name: | 04f0dedf850ab68cdceda29c3625a2_04f0dedf_mare5ckq.exe |
| Full analysis: | https://app.any.run/tasks/1f529ea4-b552-4e6c-a6a8-58fa43854e48 |
| Verdict: | Malicious activity |
| Analysis date: | May 16, 2025, 22:49:47 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 8 sections |
| MD5: | 04F0DEDF850AB68CDCEDA29C3625A2C0 |
| SHA1: | F8AE2663B6CB9AFDF2FCB15D6AF534B82A2BDE88 |
| SHA256: | B18C1D96786AC6B92430D98246A4A418040982D9C1A38754AF2013EF68D070E2 |
| SSDEEP: | 24576:cdmnHSxccl6D5RvJaoDzH+HcECSzfm/JF+WaaoAHf7L7WB4Tn/4Odk/99Rty9EMM:cqHSyclQ5RvJawzH+HcECSzfm/JwWaa4 |
MALICIOUS
Executing a file with an untrusted certificate
- 04f0dedf850ab68cdceda29c3625a2_04f0dedf_mare5ckq.exe (PID: 744)
SUSPICIOUS
There is functionality for taking screenshot (YARA)
- 04f0dedf850ab68cdceda29c3625a2_04f0dedf_mare5ckq.exe (PID: 744)
Reads security settings of Internet Explorer
- 04f0dedf850ab68cdceda29c3625a2_04f0dedf_mare5ckq.exe (PID: 744)
Reads Internet Explorer settings
- 04f0dedf850ab68cdceda29c3625a2_04f0dedf_mare5ckq.exe (PID: 744)
Reads Microsoft Outlook installation path
- 04f0dedf850ab68cdceda29c3625a2_04f0dedf_mare5ckq.exe (PID: 744)
INFO
Create files in a temporary directory
- 04f0dedf850ab68cdceda29c3625a2_04f0dedf_mare5ckq.exe (PID: 744)
Process checks whether UAC notifications are on
- 04f0dedf850ab68cdceda29c3625a2_04f0dedf_mare5ckq.exe (PID: 744)
Checks supported languages
- 04f0dedf850ab68cdceda29c3625a2_04f0dedf_mare5ckq.exe (PID: 744)
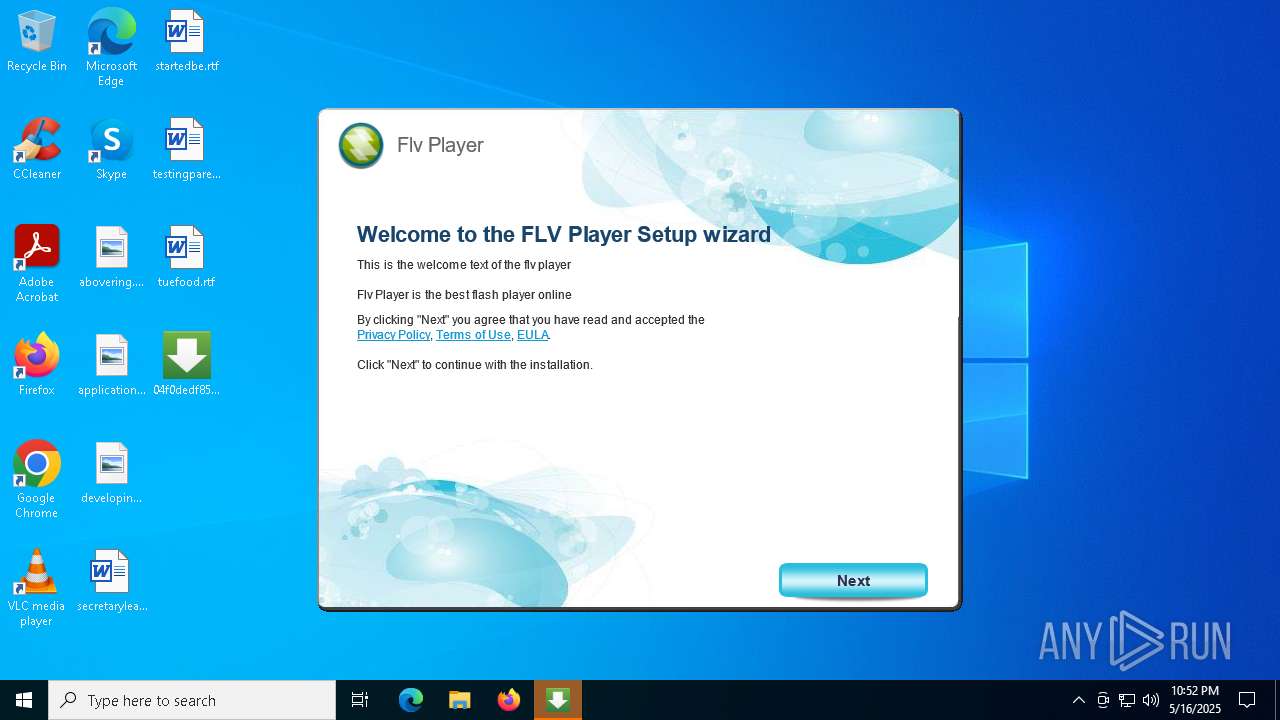
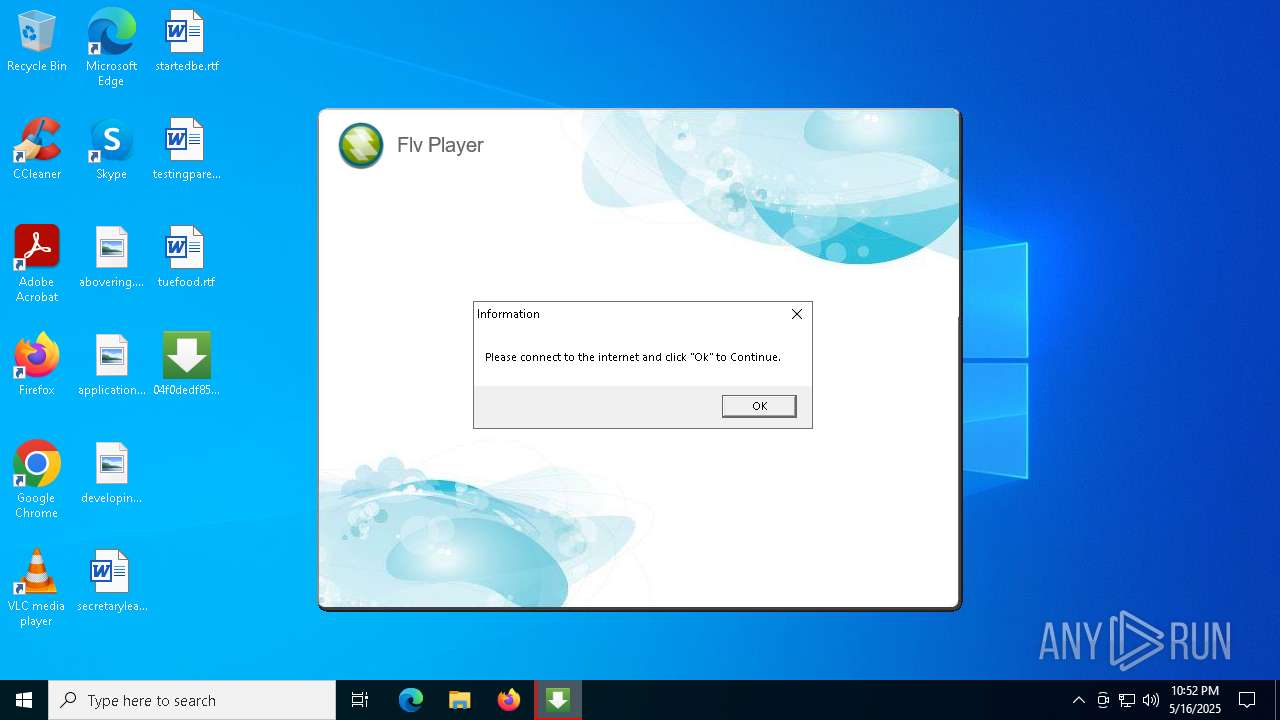
Detects InnoSetup installer (YARA)
- 04f0dedf850ab68cdceda29c3625a2_04f0dedf_mare5ckq.exe (PID: 744)
Compiled with Borland Delphi (YARA)
- 04f0dedf850ab68cdceda29c3625a2_04f0dedf_mare5ckq.exe (PID: 744)
Checks proxy server information
- slui.exe (PID: 5116)
- 04f0dedf850ab68cdceda29c3625a2_04f0dedf_mare5ckq.exe (PID: 744)
Reads the computer name
- 04f0dedf850ab68cdceda29c3625a2_04f0dedf_mare5ckq.exe (PID: 744)
UPX packer has been detected
- 04f0dedf850ab68cdceda29c3625a2_04f0dedf_mare5ckq.exe (PID: 744)
Process checks computer location settings
- 04f0dedf850ab68cdceda29c3625a2_04f0dedf_mare5ckq.exe (PID: 744)
Reads the software policy settings
- slui.exe (PID: 5116)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (77.7) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (10) |
| .dll | | | Win32 Dynamic Link Library (generic) (4.6) |
| .exe | | | Win32 Executable (generic) (3.1) |
| .exe | | | Win16/32 Executable Delphi generic (1.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 37888 |
| InitializedDataSize: | 40448 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x9c40 |
| OSVersion: | 1 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
126
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 744 | "C:\Users\admin\Desktop\04f0dedf850ab68cdceda29c3625a2_04f0dedf_mare5ckq.exe" | C:\Users\admin\Desktop\04f0dedf850ab68cdceda29c3625a2_04f0dedf_mare5ckq.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 5116 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
4 538
Read events
4 535
Write events
3
Delete events
0
Modification events
| (PID) Process: | (744) 04f0dedf850ab68cdceda29c3625a2_04f0dedf_mare5ckq.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (744) 04f0dedf850ab68cdceda29c3625a2_04f0dedf_mare5ckq.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (744) 04f0dedf850ab68cdceda29c3625a2_04f0dedf_mare5ckq.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
0
Suspicious files
3
Text files
35
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 744 | 04f0dedf850ab68cdceda29c3625a2_04f0dedf_mare5ckq.exe | C:\Users\admin\AppData\Local\Temp\0010C3CF.log | text | |
MD5:EE7FD5DA86A8C859FCAF2B6AA7BBE8B1 | SHA256:4B35A1ECE87DD7E29F69C9893BF17CA03BE02811DACA69A716A47228075DE103 | |||
| 744 | 04f0dedf850ab68cdceda29c3625a2_04f0dedf_mare5ckq.exe | C:\Users\admin\AppData\Local\Temp\ish1098718\css\sdk-ui\browse.css | text | |
MD5:6009D6E864F60AEA980A9DF94C1F7E1C | SHA256:5EF48A8C8C3771B4F233314D50DD3B5AFDCD99DD4B74A9745C8FE7B22207056D | |||
| 744 | 04f0dedf850ab68cdceda29c3625a2_04f0dedf_mare5ckq.exe | C:\Users\admin\AppData\Local\Temp\ish1098718\css\main.css | text | |
MD5:71C4B9EEE86D2B6DEE2759F9D4599891 | SHA256:4A0FB9191D25E0B38E33EA69D52DA7121322D2BAEA2F1071DA0C705FBF6C9AD6 | |||
| 744 | 04f0dedf850ab68cdceda29c3625a2_04f0dedf_mare5ckq.exe | C:\Users\admin\AppData\Local\Temp\ish1098718\css\sdk-ui\checkbox.css | text | |
MD5:64773C6B0E3413C81AEBC46CCE8C9318 | SHA256:B09504C1BF0486D3EC46500592B178A3A6C39284672AF8815C3687CC3D29560D | |||
| 744 | 04f0dedf850ab68cdceda29c3625a2_04f0dedf_mare5ckq.exe | C:\Users\admin\AppData\Local\Temp\ish1098718\css\ie6_main.css | text | |
MD5:B1F08F2E91E5873445192057D5B8925B | SHA256:87DDEB4F75EA86ED9943708C481767468F57E05EA16BFDD2E7E67413200302AE | |||
| 744 | 04f0dedf850ab68cdceda29c3625a2_04f0dedf_mare5ckq.exe | C:\Users\admin\AppData\Local\Temp\ish1098718\css\sdk-ui\button.css | text | |
MD5:37E1FF96E084EC201F0D95FEEF4D5E94 | SHA256:8E806F5B94FC294E918503C8053EF1284E4F4B1E02C7DA4F4635E33EC33E0534 | |||
| 744 | 04f0dedf850ab68cdceda29c3625a2_04f0dedf_mare5ckq.exe | C:\Users\admin\AppData\Local\Temp\ish1098718\css\sdk-ui\progress-bar.css | text | |
MD5:5335F1C12201B5F7CF5F8B4F5692E3D1 | SHA256:974CD89E64BDAA85BF36ED2A50AF266D245D781A8139F5B45D7C55A0B0841DDA | |||
| 744 | 04f0dedf850ab68cdceda29c3625a2_04f0dedf_mare5ckq.exe | C:\Users\admin\AppData\Local\Temp\ish1098718\css\sdk-ui\images\progress-bg.png | image | |
MD5:E9F12F92A9EEB8EBE911080721446687 | SHA256:C1CF449536BC2778E27348E45F0F53D04C284109199FB7A9AF7A61016B91F8BC | |||
| 744 | 04f0dedf850ab68cdceda29c3625a2_04f0dedf_mare5ckq.exe | C:\Users\admin\AppData\Local\Temp\ish1098718\csshover3.htc | binary | |
MD5:52FA0DA50BF4B27EE625C80D36C67941 | SHA256:E37E99DDFC73AC7BA774E23736B2EF429D9A0CB8C906453C75B14C029BDD5493 | |||
| 744 | 04f0dedf850ab68cdceda29c3625a2_04f0dedf_mare5ckq.exe | C:\Users\admin\AppData\Local\Temp\ish1098718\images\BG.jpg | image | |
MD5:F719B100453D490772A2EB9EAA3F807E | SHA256:A3357B1B14C5EFE4AFD0F218F45A3188F304C98D819952E2027037C1FE273488 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
49
DNS requests
22
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2104 | svchost.exe | GET | 200 | 23.48.23.194:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1300 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
1300 | SIHClient.exe | GET | 200 | 23.48.23.166:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
1300 | SIHClient.exe | GET | 200 | 23.48.23.166:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
1300 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1300 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
1300 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
1300 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
744 | 04f0dedf850ab68cdceda29c3625a2_04f0dedf_mare5ckq.exe | GET | — | 66.216.77.22:80 | http://d.adapd.com/widget/render/hash/5b6696d0970e9315472a9fc35565b682 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 23.48.23.194:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.32.134:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |