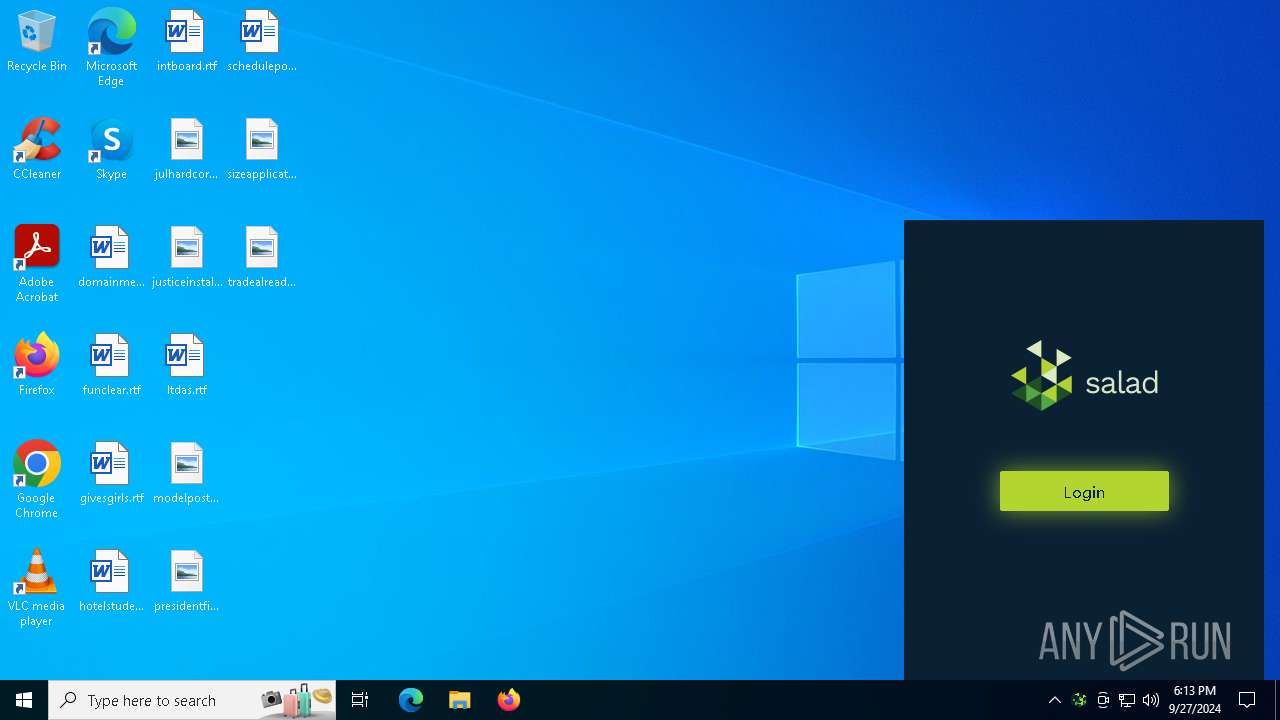
| URL: | https://salad.com/download?utm_source=yt&utm_medium=sponsor&utm_campaign=slashest24&utm_content=discord-nitro |
| Full analysis: | https://app.any.run/tasks/5d48c3cd-e03d-47e9-9918-a20dab33b22e |
| Verdict: | Malicious activity |
| Analysis date: | September 27, 2024, 18:08:38 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MD5: | B6EBB24F01D1BE5EFE2417E2773E03BD |
| SHA1: | A56638AFE083B34FF79666DB645ACB0E1641846B |
| SHA256: | B17F7BC3D259B9B8BE150BCFB0A2D83A0DE5FB493F88224BF663C5A80C3E3438 |
| SSDEEP: | 3:N8JK9GKIBb7WuDORIY5LFMMEomr9BQItKlAL+6BM1RXK:2k9GTBXWCsLF3mPQIXt |
MALICIOUS
Changes powershell execution policy (Unrestricted)
- system-information-workload.exe (PID: 6376)
SUSPICIOUS
Malware-specific behavior (creating "System.dll" in Temp)
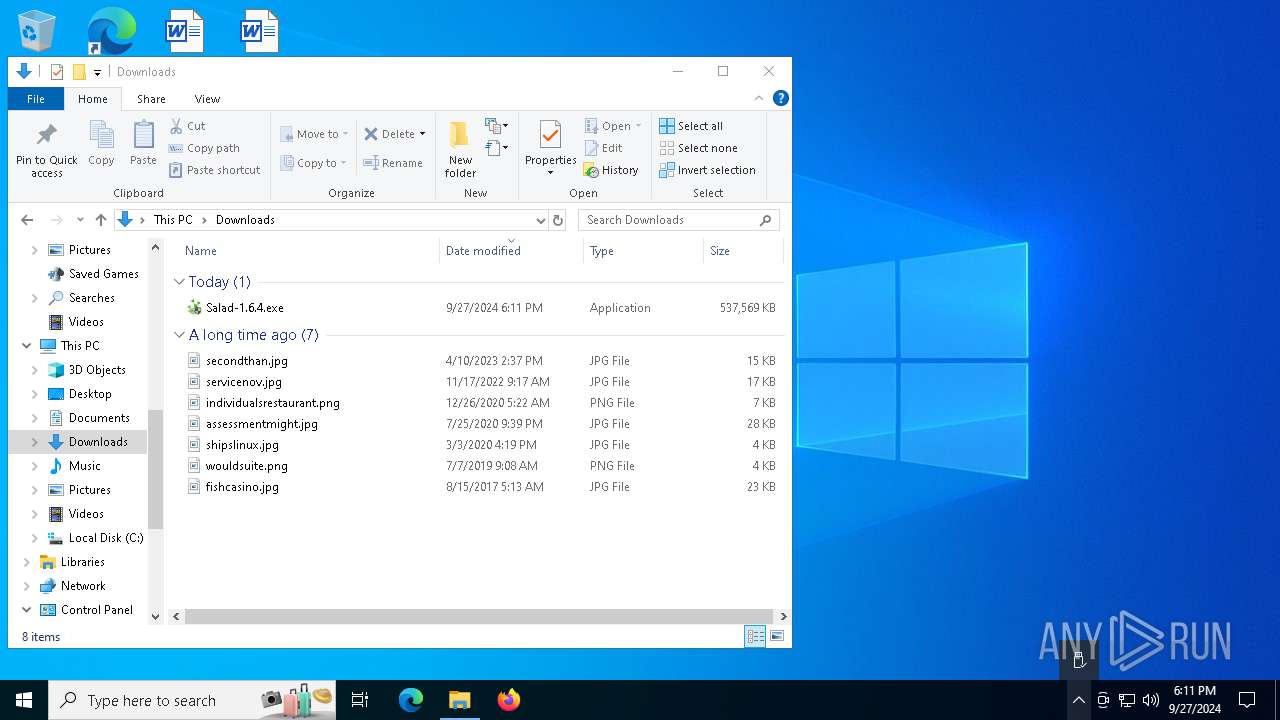
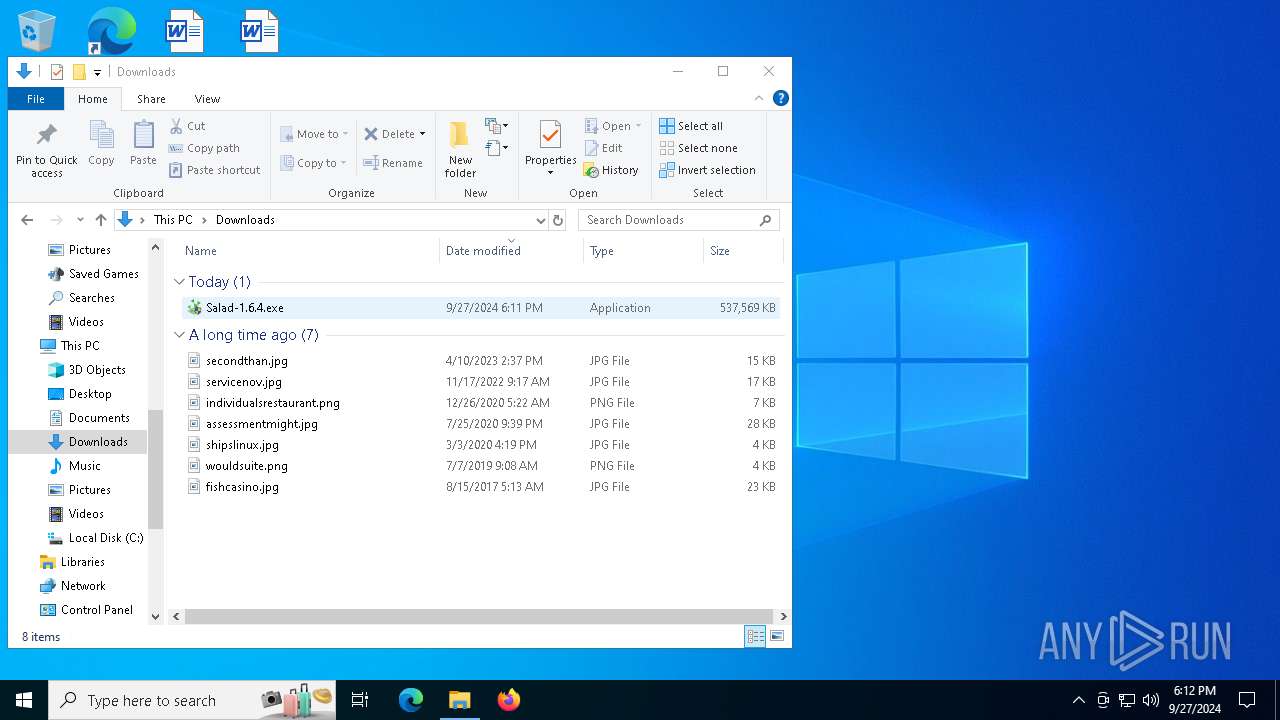
- Salad-1.6.4.exe (PID: 6872)
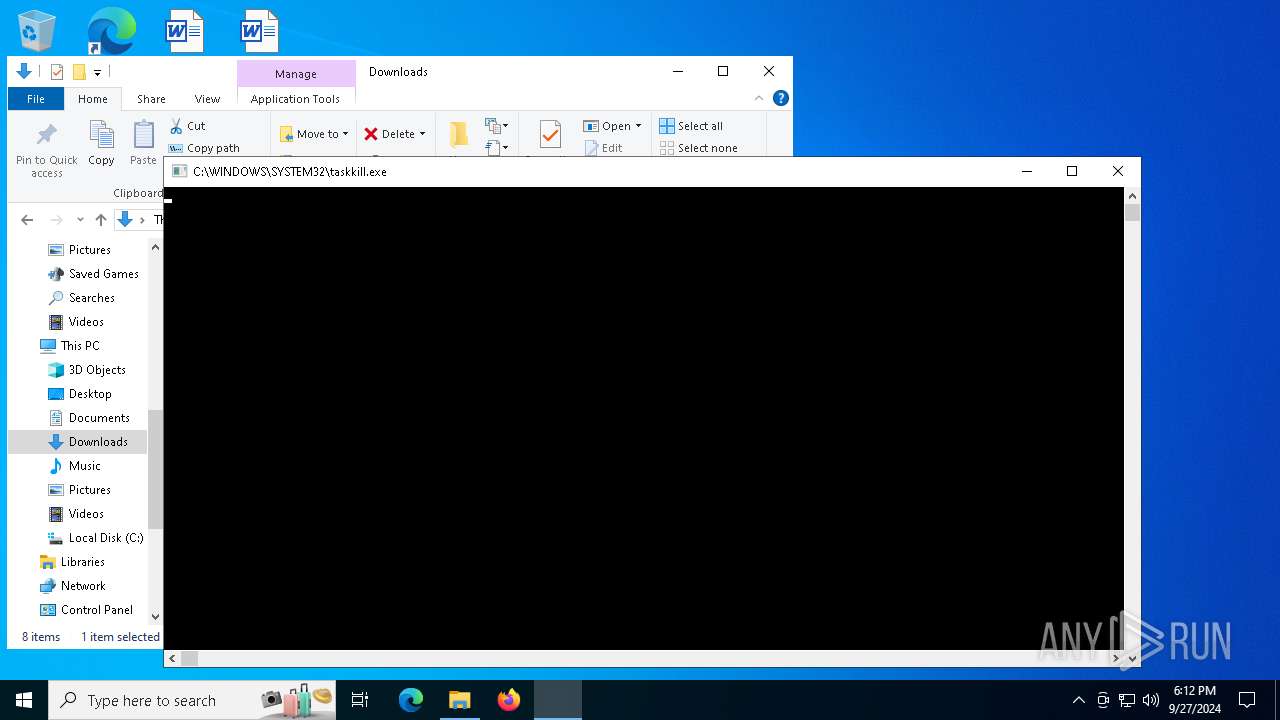
Uses TASKKILL.EXE to kill process
- Salad-1.6.4.exe (PID: 6872)
Process drops legitimate windows executable
- Salad-1.6.4.exe (PID: 6872)
Executable content was dropped or overwritten
- Salad-1.6.4.exe (PID: 6872)
- Test.exe (PID: 3784)
Drops 7-zip archiver for unpacking
- Salad-1.6.4.exe (PID: 6872)
The process drops C-runtime libraries
- Salad-1.6.4.exe (PID: 6872)
Executes as Windows Service
- Salad.Bootstrapper.exe (PID: 5388)
- WmiApSrv.exe (PID: 8044)
Application launched itself
- Salad.exe (PID: 608)
Starts CMD.EXE for commands execution
- Salad.exe (PID: 608)
- system-information-workload.exe (PID: 6376)
- NETSTAT.EXE (PID: 7576)
Starts POWERSHELL.EXE for commands execution
- Salad.exe (PID: 608)
- system-information-workload.exe (PID: 6376)
Drops a system driver (possible attempt to evade defenses)
- Test.exe (PID: 3784)
Executing commands from ".cmd" file
- system-information-workload.exe (PID: 6376)
Starts application with an unusual extension
- cmd.exe (PID: 5468)
Uses ROUTE.EXE to obtain the routing table information
- cmd.exe (PID: 7972)
The process hides Powershell's copyright startup banner
- system-information-workload.exe (PID: 6376)
The process bypasses the loading of PowerShell profile settings
- system-information-workload.exe (PID: 6376)
INFO
Executable content was dropped or overwritten
- msedge.exe (PID: 1280)
- msedge.exe (PID: 7184)
Checks supported languages
- identity_helper.exe (PID: 7780)
Reads the computer name
- identity_helper.exe (PID: 7780)
Manual execution by a user
- Salad-1.6.4.exe (PID: 7528)
- Salad-1.6.4.exe (PID: 6872)
- Salad.exe (PID: 608)
Application launched itself
- msedge.exe (PID: 3520)
- msedge.exe (PID: 1280)
Changes the display of characters in the console
- cmd.exe (PID: 5468)
Reads Environment values
- identity_helper.exe (PID: 7780)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
375
Monitored processes
231
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 240 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7420 --field-trial-handle=2708,i,8333336837163799751,14513866260742211146,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 304 | C:\WINDOWS\system32\icacls.exe C:\ProgramData\Oracle\Java\.oracle_jre_usage /grant "everyone":(OI)(CI)M | C:\Windows\System32\icacls.exe | — | java.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 400 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7360 --field-trial-handle=2708,i,8333336837163799751,14513866260742211146,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 512 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=4952 --field-trial-handle=2180,i,2761575640408224254,17237036811935803344,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 512 | C:\WINDOWS\system32\cmd.exe /d /s /c "gulp.cmd --version" | C:\Windows\System32\cmd.exe | — | system-information-workload.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 608 | "C:\Program Files\Salad\Salad.exe" | C:\Program Files\Salad\Salad.exe | explorer.exe | ||||||||||||
User: admin Company: Salad Technologies Integrity Level: MEDIUM Description: Salad Version: 1.6.4.20240830.2 Modules
| |||||||||||||||
| 652 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 780 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7268 --field-trial-handle=2708,i,8333336837163799751,14513866260742211146,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 940 | powershell.exe -NoProfile -NoLogo -InputFormat Text -NoExit -ExecutionPolicy Unrestricted -Command - | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | system-information-workload.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 992 | C:\WINDOWS\system32\cmd.exe /d /s /c "nginx -v 2>&1" | C:\Windows\System32\cmd.exe | — | system-information-workload.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
195 714
Read events
195 625
Write events
58
Delete events
31
Modification events
| (PID) Process: | (1280) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\1770460 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {E865DAE3-7C06-481A-8AAF-203944098089} | |||
| (PID) Process: | (1280) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\1770460 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {C8E2A652-0582-43BC-AA07-0D5E5D721C9E} | |||
| (PID) Process: | (1280) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 3EC1D607B4812F00 | |||
| (PID) Process: | (1280) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | MicrosoftEdgeAutoLaunch_29EBC4579851B72EE312C449CF839B1A |
Value: "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --no-startup-window --win-session-start | |||
| (PID) Process: | (1280) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate\Clients\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\Commands\on-logon-autolaunch |
| Operation: | write | Name: | Enabled |
Value: 0 | |||
| (PID) Process: | (1280) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\Profiles |
| Operation: | write | Name: | EnhancedLinkOpeningDefault |
Value: Default | |||
| (PID) Process: | (1280) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\1770460 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {E24D2DC6-838D-4558-88BD-2E5D7D8D37BF} | |||
| (PID) Process: | (1280) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\1770460 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {3F7992C3-F3DC-4A83-9B8C-F58BA22B6D4E} | |||
| (PID) Process: | (1280) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\1770460 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {22EE342B-0E0D-497C-B182-EB375D24556B} | |||
| (PID) Process: | (1280) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\1770460 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {3652578C-7D4A-4DCA-BE46-E759F6D685A9} | |||
Executable files
283
Suspicious files
577
Text files
335
Unknown types
19
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1280 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF3f5a91.TMP | — | |
MD5:— | SHA256:— | |||
| 1280 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1280 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF3f5b6b.TMP | — | |
MD5:— | SHA256:— | |||
| 1280 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1280 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF3f5baa.TMP | — | |
MD5:— | SHA256:— | |||
| 1280 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1280 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF3f5b9a.TMP | — | |
MD5:— | SHA256:— | |||
| 1280 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1280 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF3f5bba.TMP | — | |
MD5:— | SHA256:— | |||
| 1280 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
119
TCP/UDP connections
228
DNS requests
239
Threats
16
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4516 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7868 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1840 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | HEAD | 200 | 184.24.77.30:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/a1310cb6-94be-46c6-b8dc-986450234260?P1=1728041586&P2=404&P3=2&P4=ZTiwteZS0oKmnS6B4O2GPI%2bUiWFBR18zYG4cnMMjBbg1PNC%2f1xfwC5Y5lSg1ljofvmPtBegxGeROgeG8djG24g%3d%3d | unknown | — | — | whitelisted |
1840 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6128 | svchost.exe | GET | 206 | 184.24.77.30:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/a1310cb6-94be-46c6-b8dc-986450234260?P1=1728041586&P2=404&P3=2&P4=ZTiwteZS0oKmnS6B4O2GPI%2bUiWFBR18zYG4cnMMjBbg1PNC%2f1xfwC5Y5lSg1ljofvmPtBegxGeROgeG8djG24g%3d%3d | unknown | — | — | whitelisted |
6128 | svchost.exe | GET | 206 | 184.24.77.30:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/a1310cb6-94be-46c6-b8dc-986450234260?P1=1728041586&P2=404&P3=2&P4=ZTiwteZS0oKmnS6B4O2GPI%2bUiWFBR18zYG4cnMMjBbg1PNC%2f1xfwC5Y5lSg1ljofvmPtBegxGeROgeG8djG24g%3d%3d | unknown | — | — | whitelisted |
6128 | svchost.exe | GET | 206 | 184.24.77.30:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/a1310cb6-94be-46c6-b8dc-986450234260?P1=1728041586&P2=404&P3=2&P4=ZTiwteZS0oKmnS6B4O2GPI%2bUiWFBR18zYG4cnMMjBbg1PNC%2f1xfwC5Y5lSg1ljofvmPtBegxGeROgeG8djG24g%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 239.255.255.250:1900 | — | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 142.250.185.106:443 | fonts.googleapis.com | — | — | whitelisted |
— | — | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
— | — | 104.26.0.249:443 | salad.com | — | — | unknown |
— | — | 162.159.138.60:443 | player.vimeo.com | CLOUDFLARENET | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
salad.com |
| unknown |
edge.microsoft.com |
| whitelisted |
business.bing.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
bzib.nelreports.net |
| whitelisted |
www.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |
1712 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
1712 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |