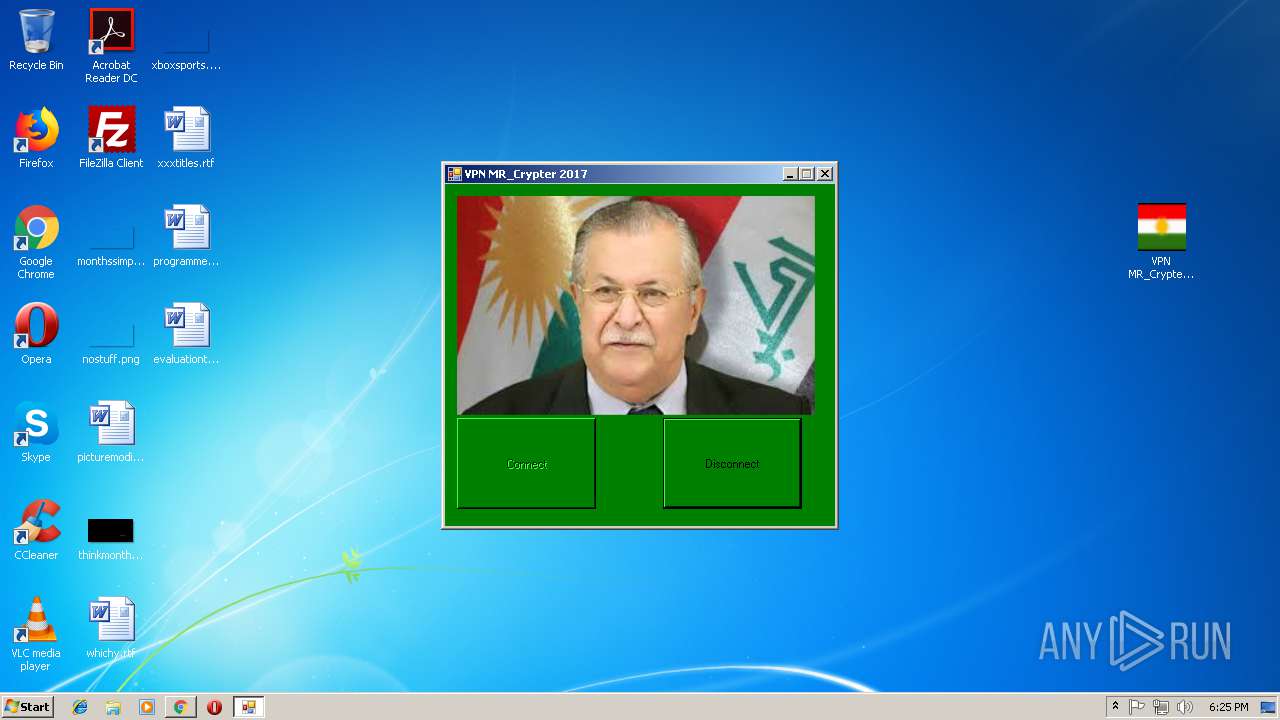
| download: | VPN+MR_Crypter.rar |
| Full analysis: | https://app.any.run/tasks/31c465d8-ba59-4488-9823-971c836acb6b |
| Verdict: | Malicious activity |
| Analysis date: | December 03, 2018, 18:22:33 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | D6CC1E15CCA34EB6F55E031F6873600C |
| SHA1: | E5E07D7A14AA9557152F08BA09B1EF69B1739C20 |
| SHA256: | B16FE32276144F1D085852375D2F7641E50943873C67DCFB07BCC60516245D79 |
| SSDEEP: | 24576:U2u/Zec/UfRIpMw7Gp/u5SUdoY39h1hkxmT4:U33/9MkK/17Yth1hoc4 |
MALICIOUS
Application was dropped or rewritten from another process
- EXPLORER.EXE (PID: 4080)
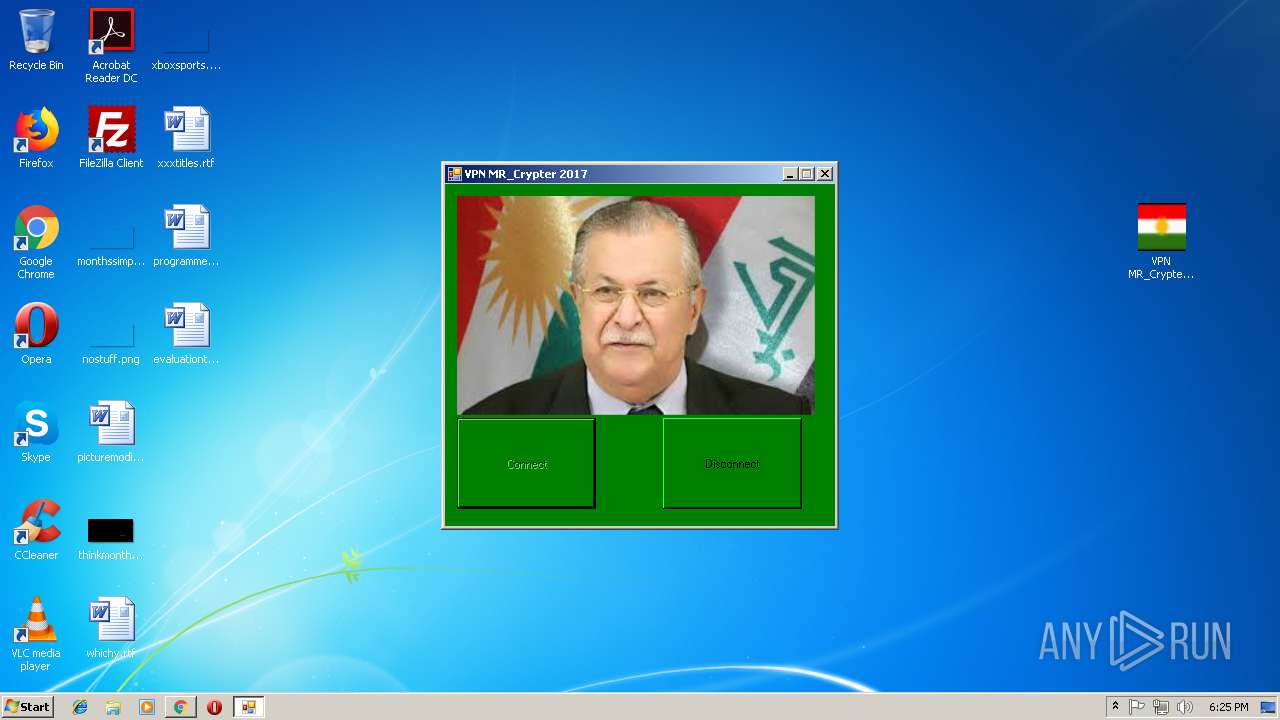
- VPN MR_Crypter.exe (PID: 2940)
- VPN MR_CRYPTER.EXE (PID: 2616)
Loads dropped or rewritten executable
- EXPLORER.EXE (PID: 4080)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2996)
- VPN MR_Crypter.exe (PID: 2940)
- EXPLORER.EXE (PID: 4080)
Creates executable files which already exist in Windows
- VPN MR_Crypter.exe (PID: 2940)
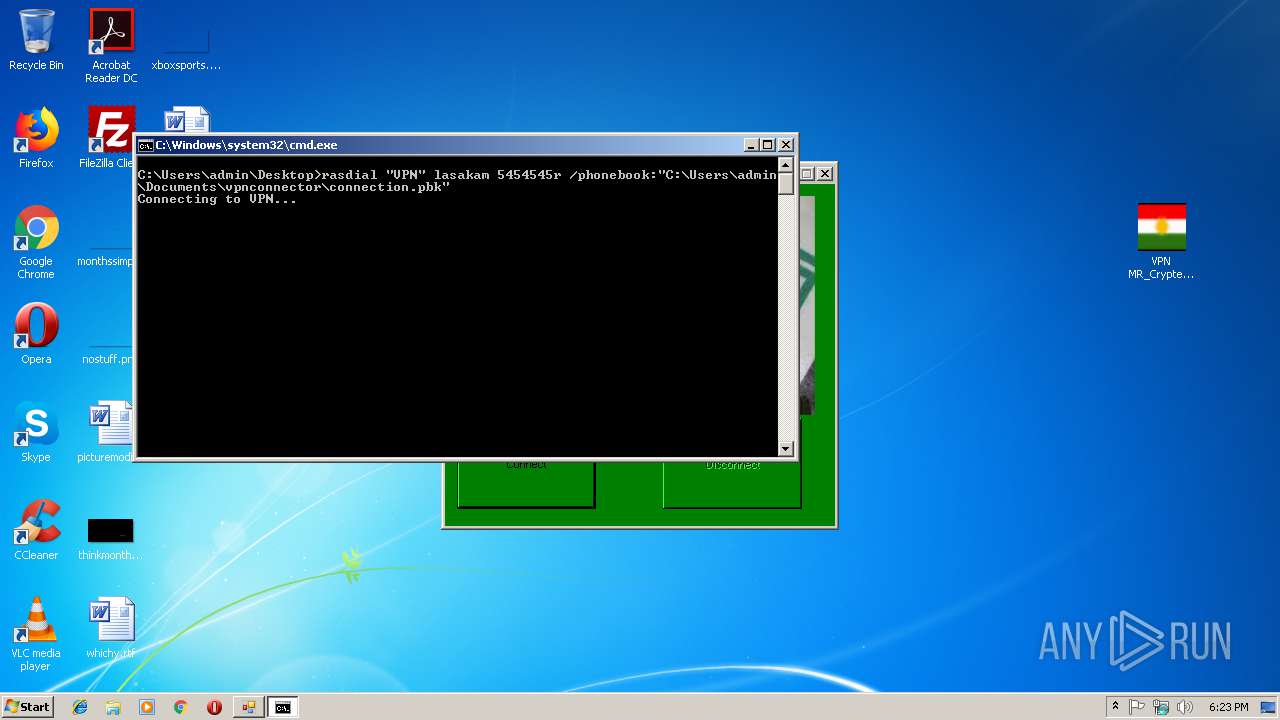
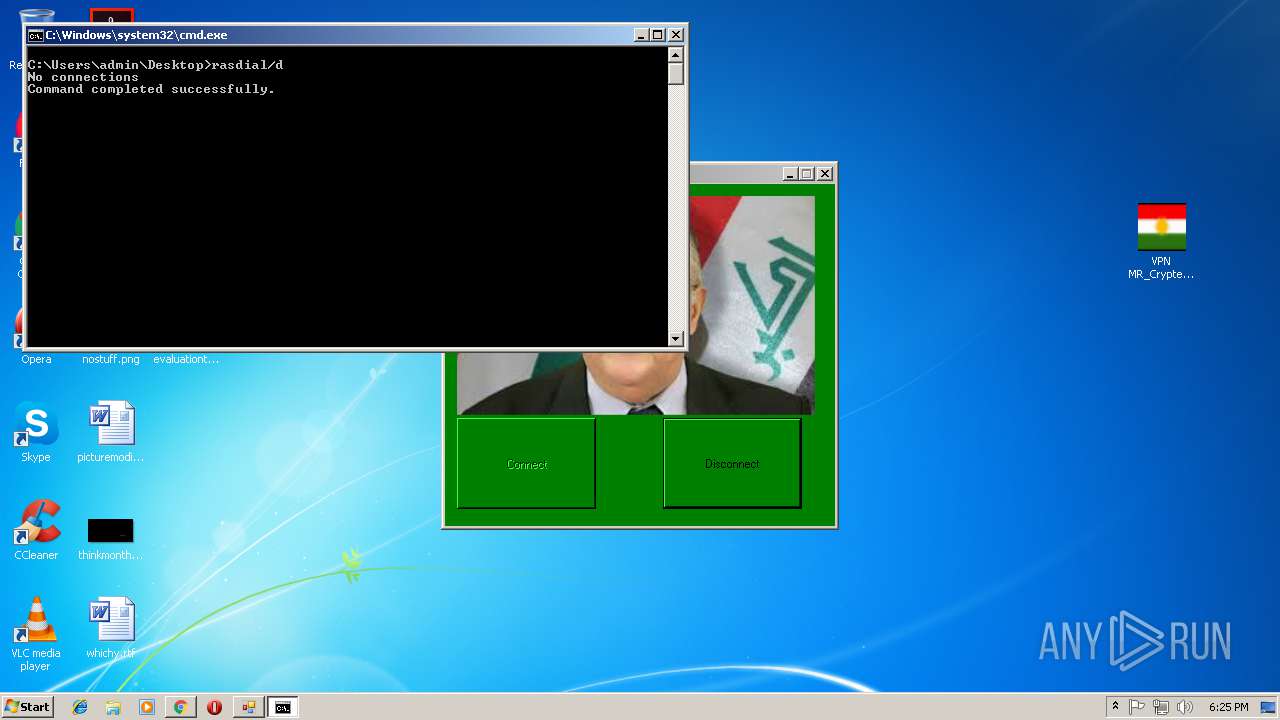
Starts CMD.EXE for commands execution
- VPN MR_CRYPTER.EXE (PID: 2616)
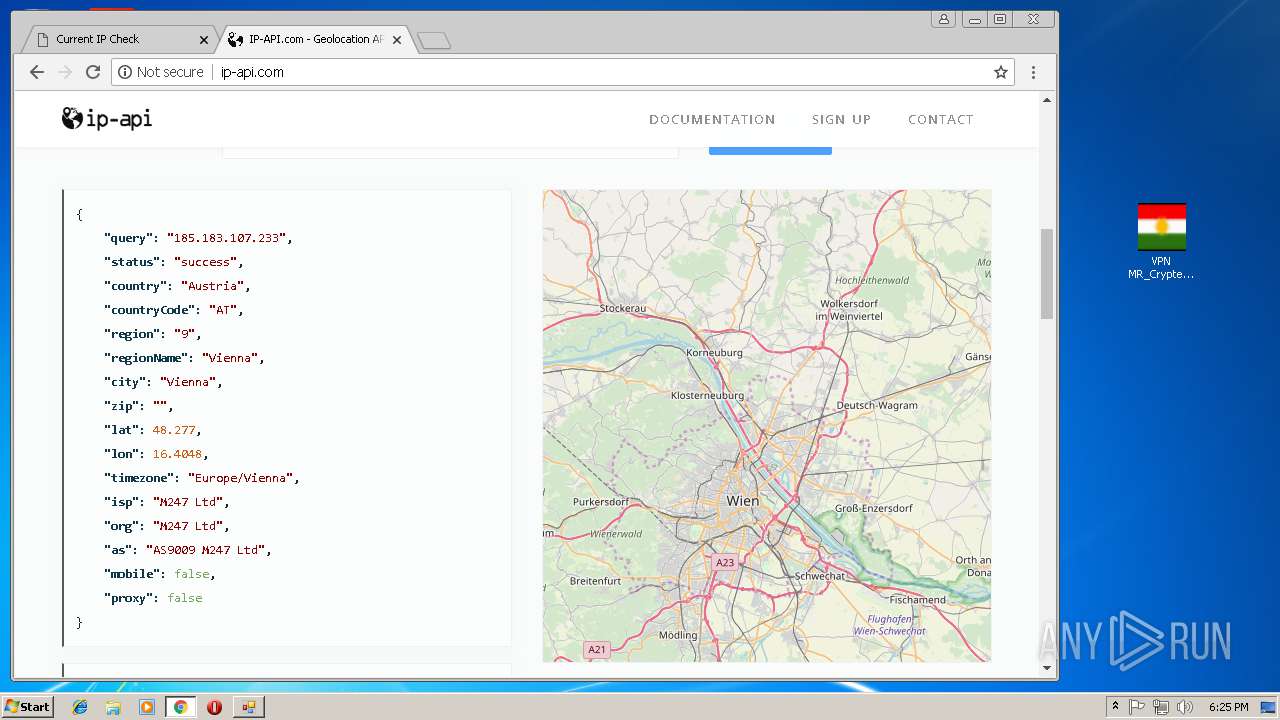
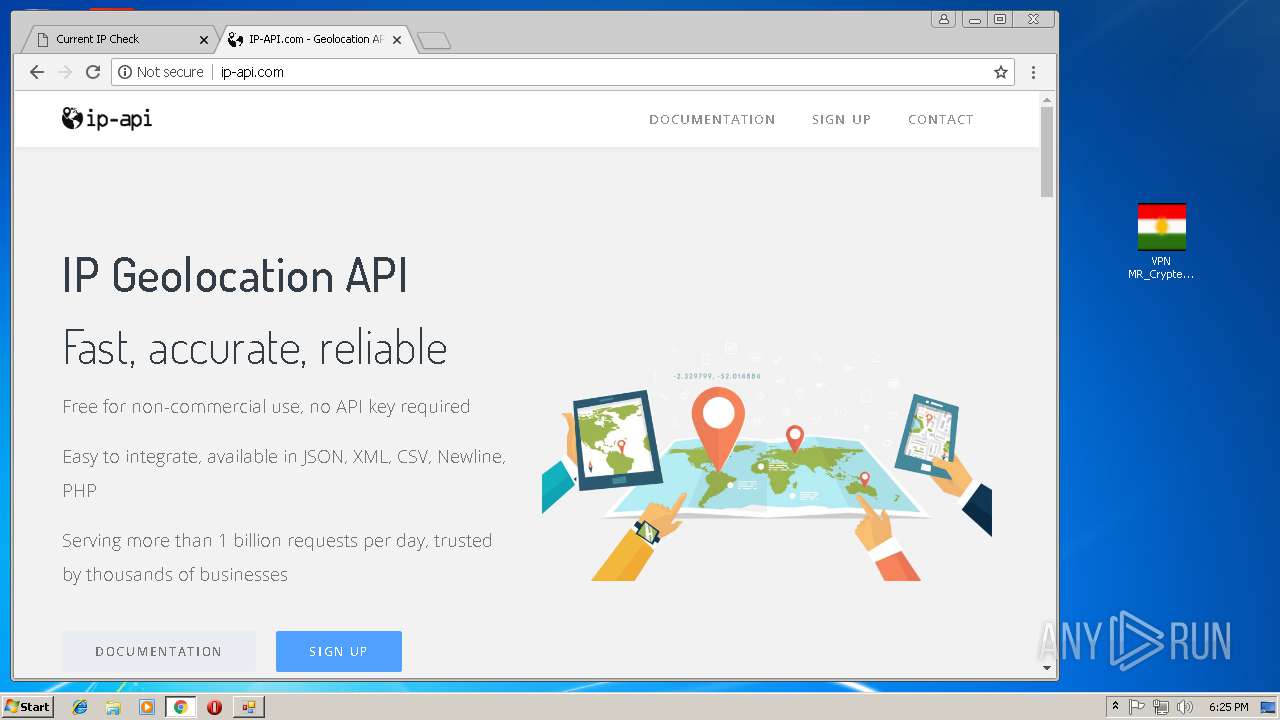
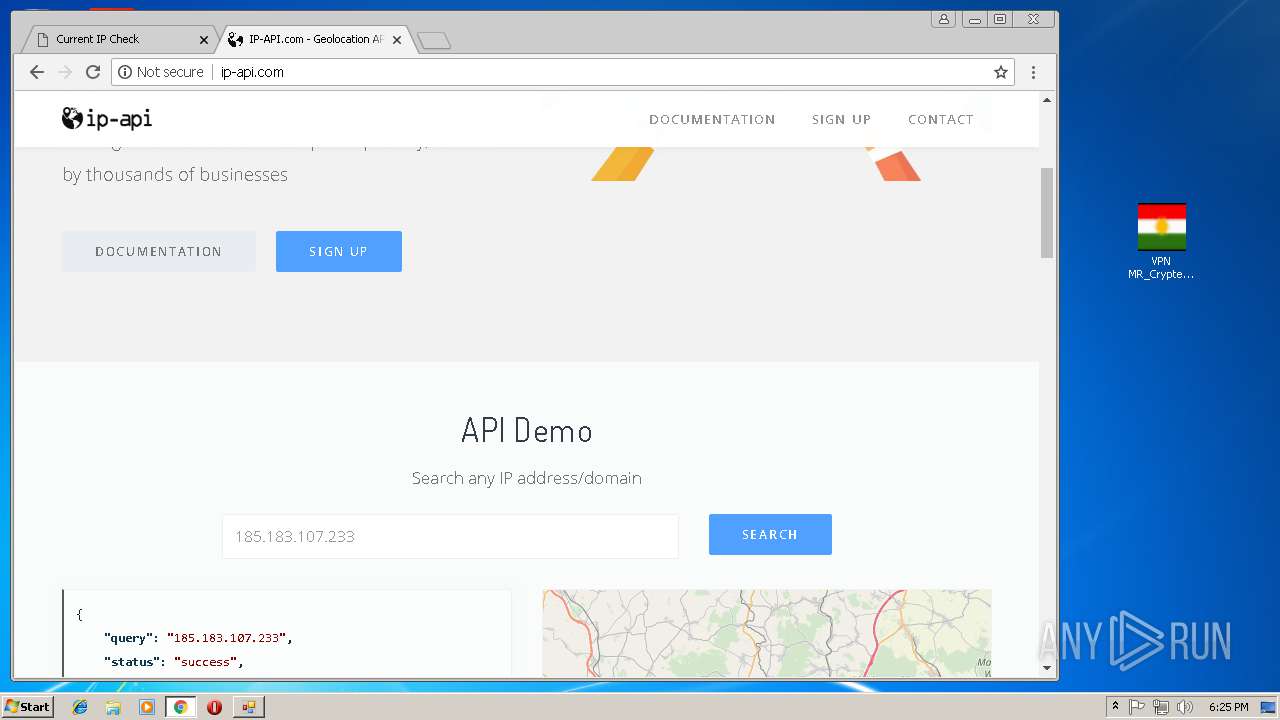
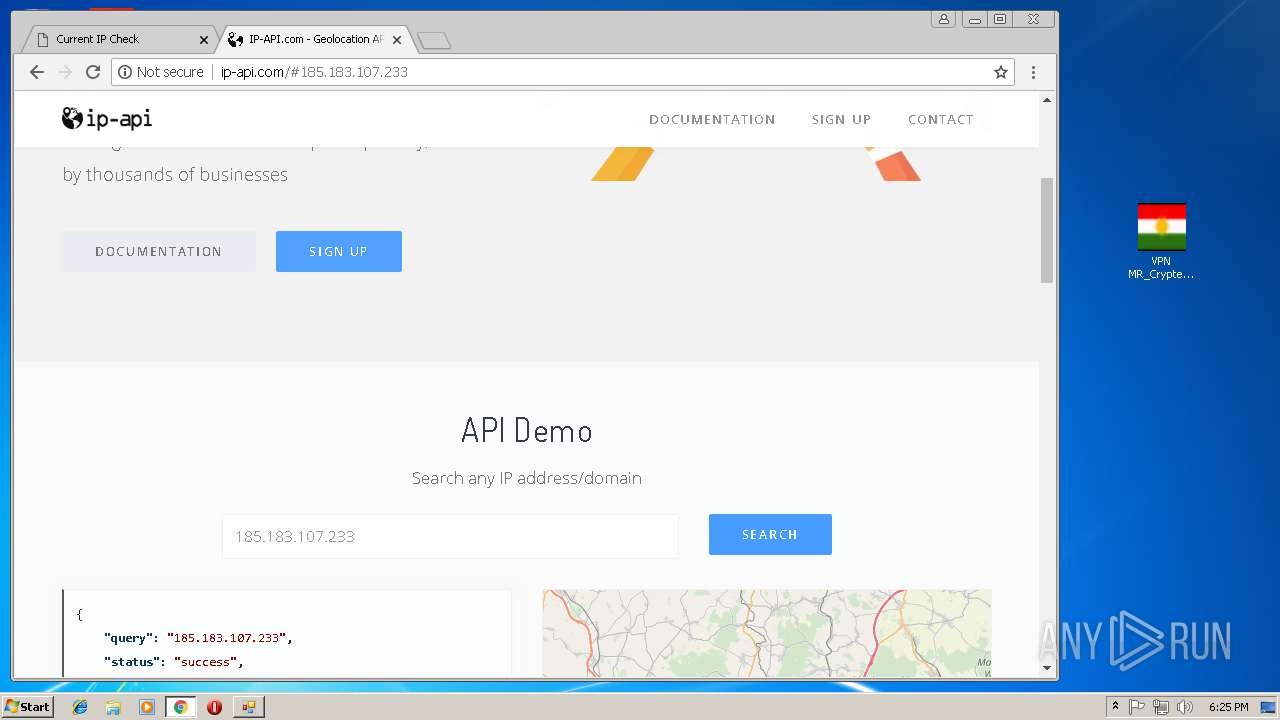
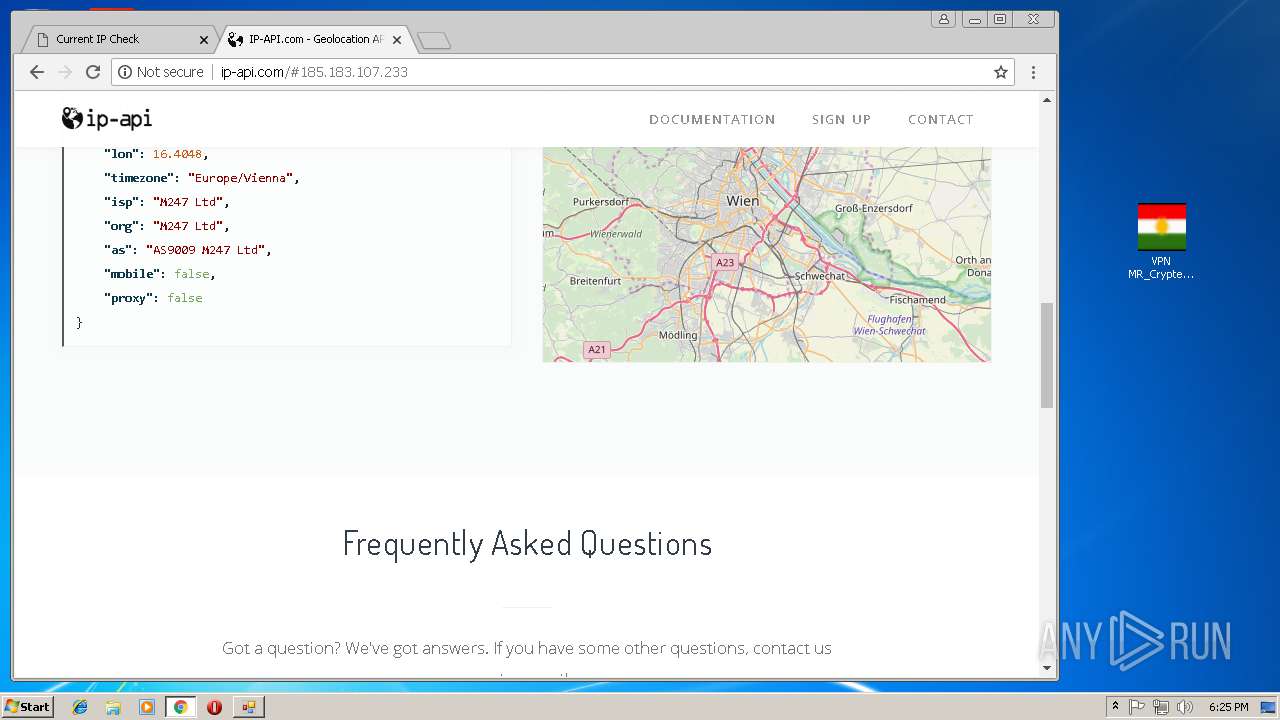
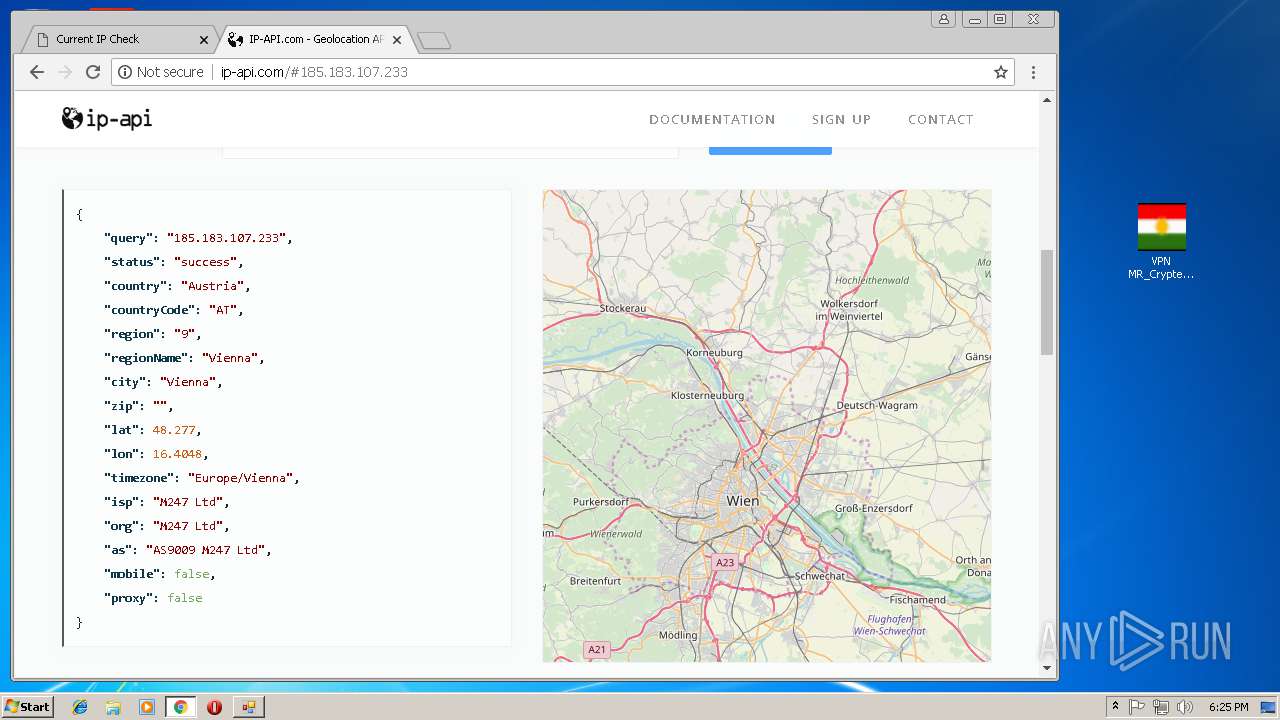
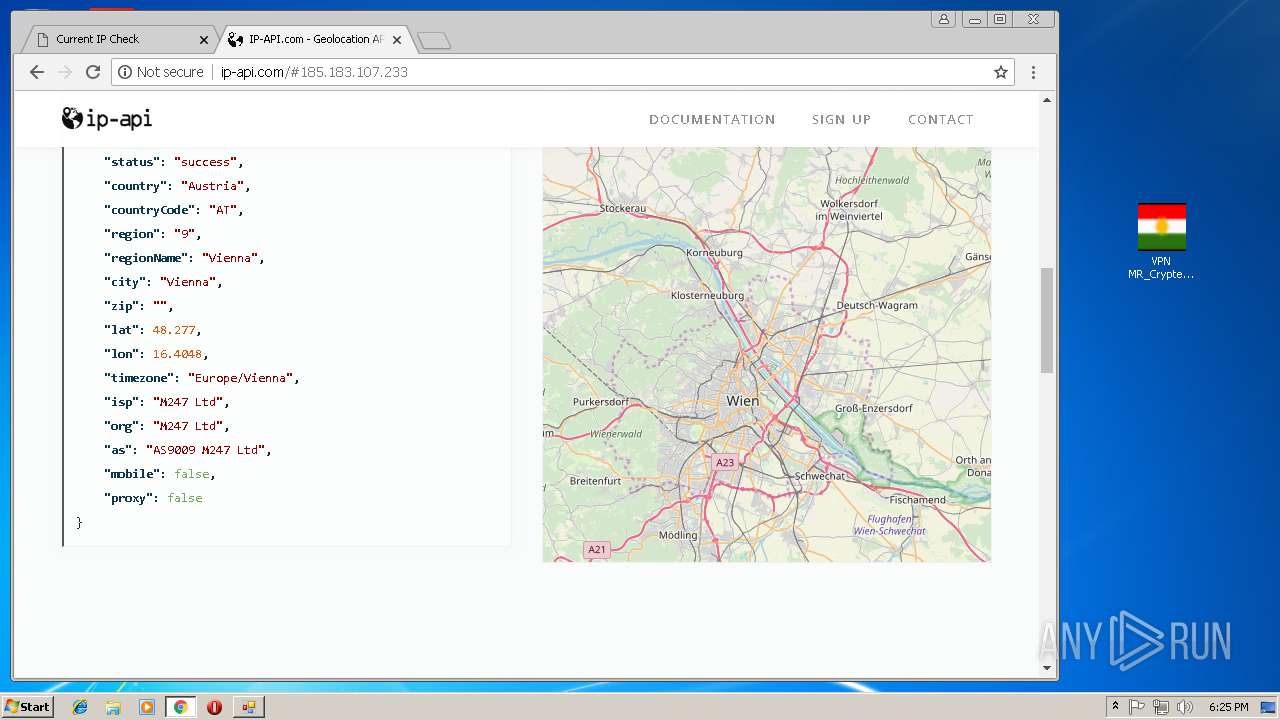
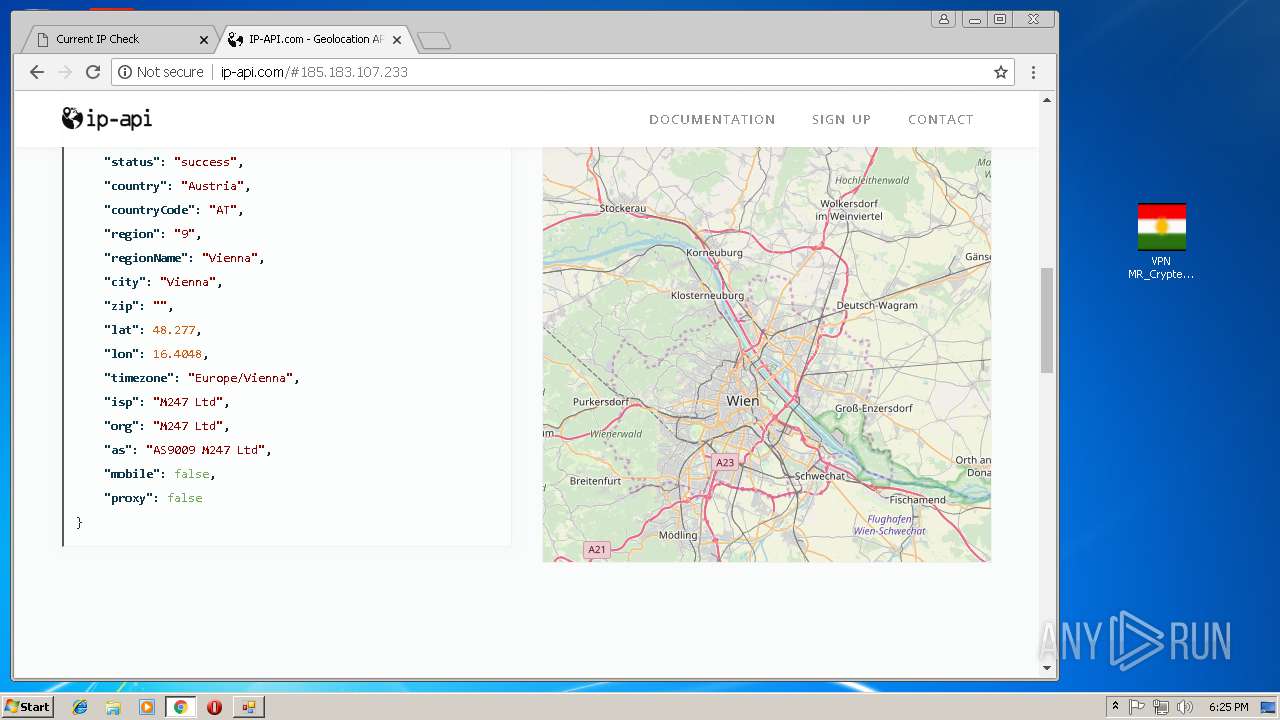
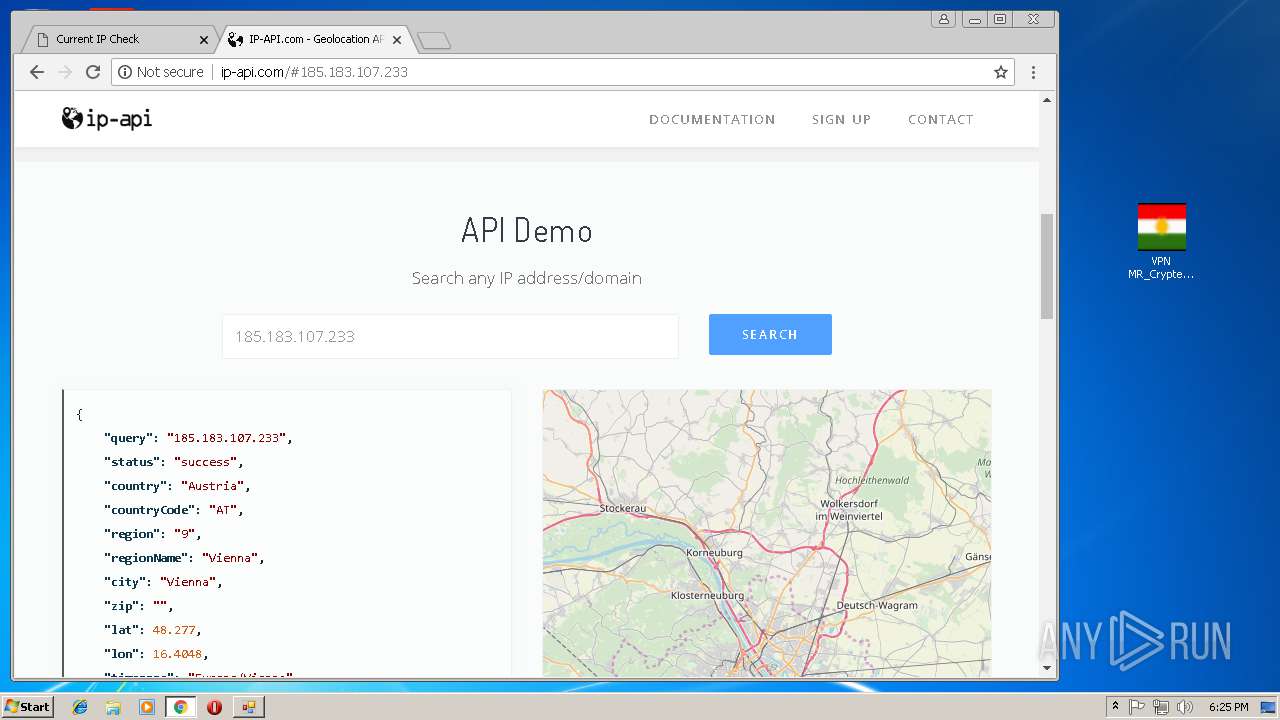
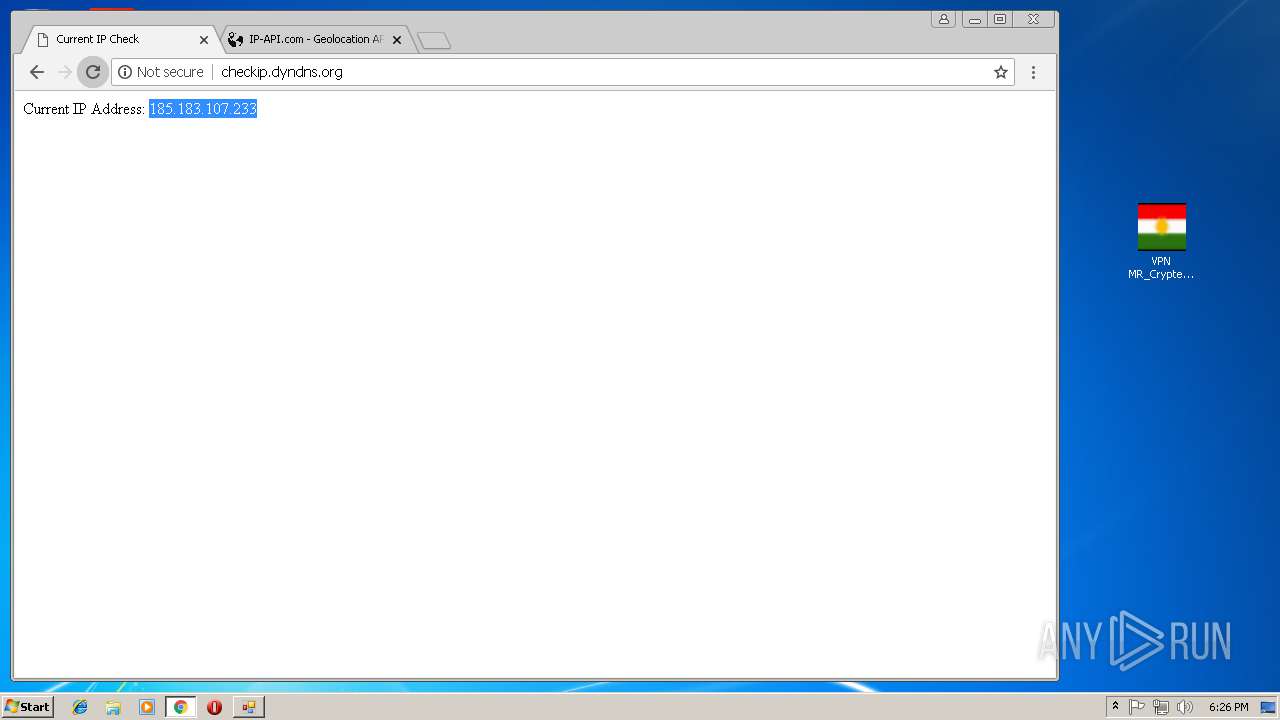
Checks for external IP
- chrome.exe (PID: 992)
INFO
Application launched itself
- chrome.exe (PID: 992)
Reads settings of System Certificates
- chrome.exe (PID: 992)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
106
Monitored processes
56
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 340 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=980,3072166494604207468,9107733461470253665,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=F5693C2168CA23C3CDDFA392FA945261 --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=F5693C2168CA23C3CDDFA392FA945261 --renderer-client-id=6 --mojo-platform-channel-handle=3564 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 792 | rasdial /d | C:\Windows\system32\rasdial.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Remote Access Command Line Dial UI Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 992 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 1252 | cmd /c ""C:\Users\admin\Documents\vpnconnector\disconnect.bat" " | C:\Windows\system32\cmd.exe | — | VPN MR_CRYPTER.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1420 | rasdial /d | C:\Windows\system32\rasdial.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Remote Access Command Line Dial UI Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1428 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=2716 --on-initialized-event-handle=304 --parent-handle=308 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 1440 | cmd /c ""C:\Users\admin\Documents\vpnconnector\disconnect.bat" " | C:\Windows\system32\cmd.exe | — | VPN MR_CRYPTER.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1820 | rasdial /d | C:\Windows\system32\rasdial.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Remote Access Command Line Dial UI Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1832 | rasdial /d | C:\Windows\system32\rasdial.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Remote Access Command Line Dial UI Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2156 | cmd /c ""C:\Users\admin\Documents\vpnconnector\disconnect.bat" " | C:\Windows\system32\cmd.exe | — | VPN MR_CRYPTER.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
1 810
Read events
1 691
Write events
116
Delete events
3
Modification events
| (PID) Process: | (2996) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2996) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2996) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2996) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\VPN+MR_Crypter.rar | |||
| (PID) Process: | (2996) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2996) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2996) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2996) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2996) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (2996) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\AppData\Local\Temp | |||
Executable files
4
Suspicious files
77
Text files
107
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4080 | EXPLORER.EXE | C:\Users\admin\AppData\Local\Temp\autC6A2.tmp | — | |
MD5:— | SHA256:— | |||
| 4080 | EXPLORER.EXE | C:\Users\admin\AppData\Local\Temp\buggokg | — | |
MD5:— | SHA256:— | |||
| 4080 | EXPLORER.EXE | C:\Users\admin\AppData\Local\Temp\autC6F1.tmp | — | |
MD5:— | SHA256:— | |||
| 992 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Download Service\EntryDB\LOG.old | — | |
MD5:— | SHA256:— | |||
| 992 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | — | |
MD5:— | SHA256:— | |||
| 992 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\c161fa03-9cf9-4bf9-9c39-703006d786bc.tmp | — | |
MD5:— | SHA256:— | |||
| 992 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Download Service\EntryDB\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 992 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2996 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2996.39172\VPN MR_Crypter.exe | executable | |
MD5:— | SHA256:— | |||
| 2940 | VPN MR_Crypter.exe | C:\Users\admin\AppData\Local\Temp\VPN MR_CRYPTER.EXE | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
22
TCP/UDP connections
61
DNS requests
32
Threats
31
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
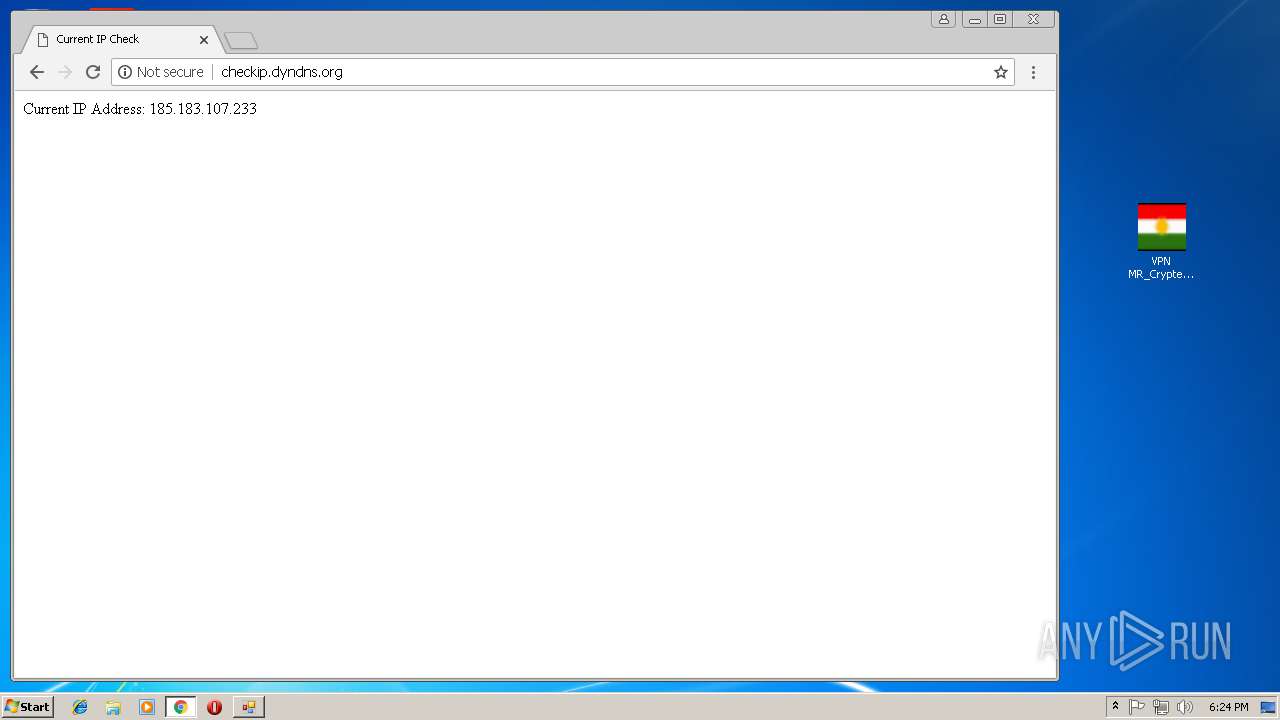
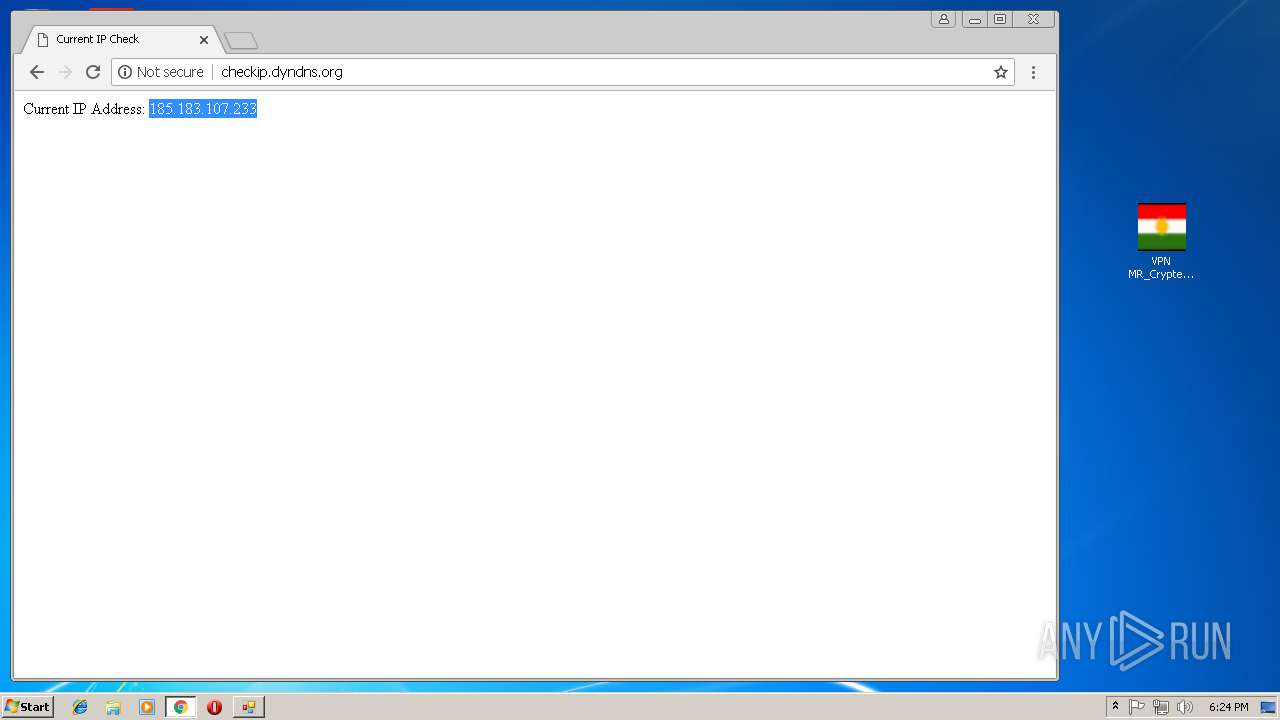
992 | chrome.exe | GET | 200 | 131.186.113.70:80 | http://checkip.dyndns.org/ | US | html | 107 b | shared |
976 | svchost.exe | GET | 200 | 13.107.4.50:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 55.2 Kb | whitelisted |
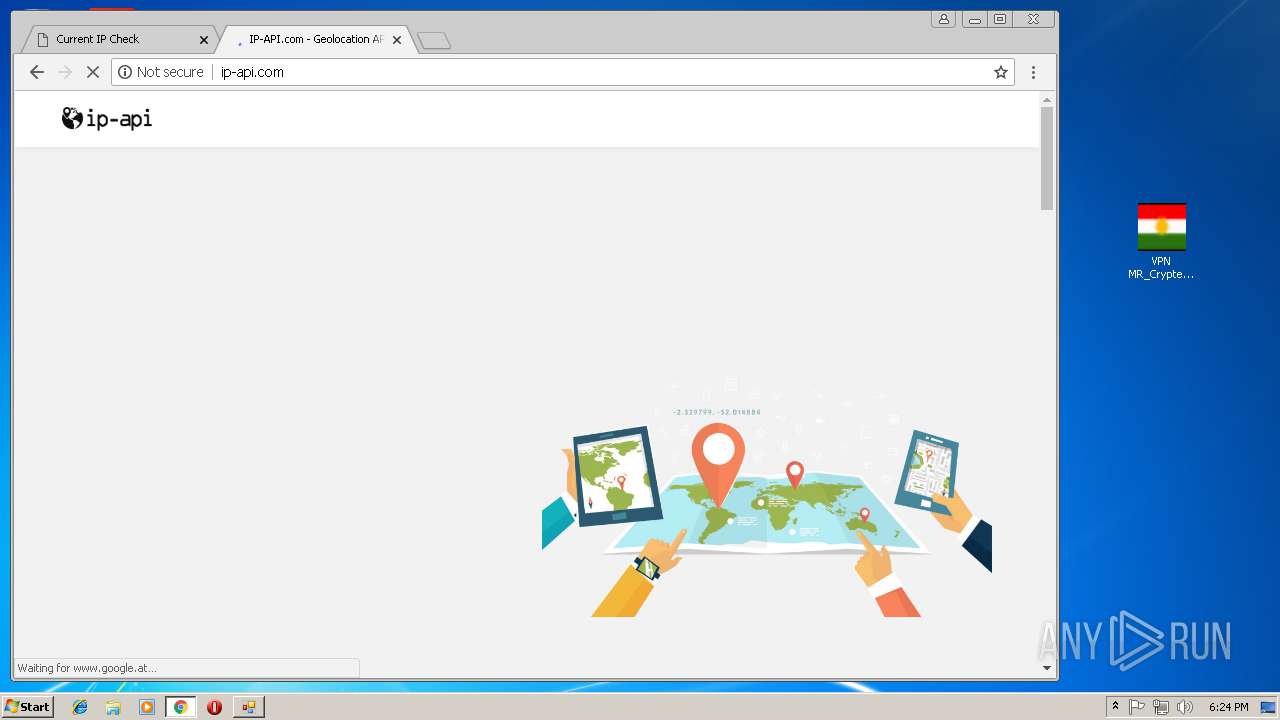
992 | chrome.exe | GET | 200 | 185.194.141.58:80 | http://ip-api.com/docs/static/bg.jpg | DE | image | 47.3 Kb | malicious |
992 | chrome.exe | GET | 200 | 185.194.141.58:80 | http://ip-api.com/ | DE | html | 9.64 Kb | malicious |
992 | chrome.exe | GET | 200 | 185.194.141.58:80 | http://ip-api.com/json/?fields=258047&lang=en | DE | text | 285 b | malicious |
992 | chrome.exe | GET | 200 | 131.186.113.70:80 | http://checkip.dyndns.org/favicon.ico | US | html | 107 b | shared |
992 | chrome.exe | GET | 200 | 185.194.141.58:80 | http://ip-api.com/docs/static/page.css | DE | text | 18.0 Kb | malicious |
992 | chrome.exe | GET | 200 | 81.4.120.220:80 | http://qwttz5ber2gswhi2n3y0q8opjlphwi83.edns.ip-api.com/json?lang=en | NL | text | 184 b | suspicious |
992 | chrome.exe | GET | 200 | 31.220.4.108:80 | http://fp.ip-api.com/json | NL | text | 550 b | shared |
992 | chrome.exe | GET | 200 | 185.194.141.58:80 | http://ip-api.com/json/?fields=258047&lang=en | DE | text | 285 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
992 | chrome.exe | 31.220.4.108:80 | fp.ip-api.com | HostHatch, Inc | NL | suspicious |
— | — | 178.73.195.104:500 | se.frootvpn.com | Portlane AB | SE | unknown |
— | — | 178.73.195.104:4500 | se.frootvpn.com | Portlane AB | SE | unknown |
976 | svchost.exe | 178.73.195.104:443 | se.frootvpn.com | Portlane AB | SE | unknown |
4 | System | 178.73.195.101:1723 | se.frootvpn.com | Portlane AB | SE | suspicious |
976 | svchost.exe | 13.107.4.50:80 | www.download.windowsupdate.com | Microsoft Corporation | US | whitelisted |
992 | chrome.exe | 216.58.215.227:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
992 | chrome.exe | 216.58.215.234:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
992 | chrome.exe | 172.217.168.3:443 | www.google.de | Google Inc. | US | whitelisted |
992 | chrome.exe | 172.217.168.45:443 | accounts.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
se.frootvpn.com |
| suspicious |
www.download.windowsupdate.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
www.google.de |
| whitelisted |
www.gstatic.com |
| whitelisted |
safebrowsing.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
ssl.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
www.google.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4 | System | Potential Corporate Privacy Violation | POLICY [PTsecurity] PPTP tunnel based VPN (Start connection request) |
4 | System | Potential Corporate Privacy Violation | POLICY [PTsecurity] PPTP VPN Protocol |
4 | System | Potential Corporate Privacy Violation | POLICY [PTsecurity] PPTP tunnel based VPN (Start connection request) |
1056 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.dyndns. Domain |
992 | chrome.exe | Potential Corporate Privacy Violation | ET POLICY External IP Lookup - checkip.dyndns.org |
992 | chrome.exe | Potentially Bad Traffic | ET POLICY DynDNS CheckIp External IP Address Server Response |
992 | chrome.exe | Potential Corporate Privacy Violation | ET POLICY External IP Lookup - checkip.dyndns.org |
992 | chrome.exe | Potentially Bad Traffic | ET POLICY DynDNS CheckIp External IP Address Server Response |
992 | chrome.exe | Potential Corporate Privacy Violation | ET POLICY External IP Lookup ip-api.com |
992 | chrome.exe | Potential Corporate Privacy Violation | ET POLICY External IP Lookup ip-api.com |
Process | Message |
|---|---|
VPN MR_Crypter.exe | C:\Users\admin\AppData\Local\Temp\EXPLORER.EXE |
VPN MR_Crypter.exe | C:\Users\admin\AppData\Local\Temp\VPN MR_CRYPTER.EXE |