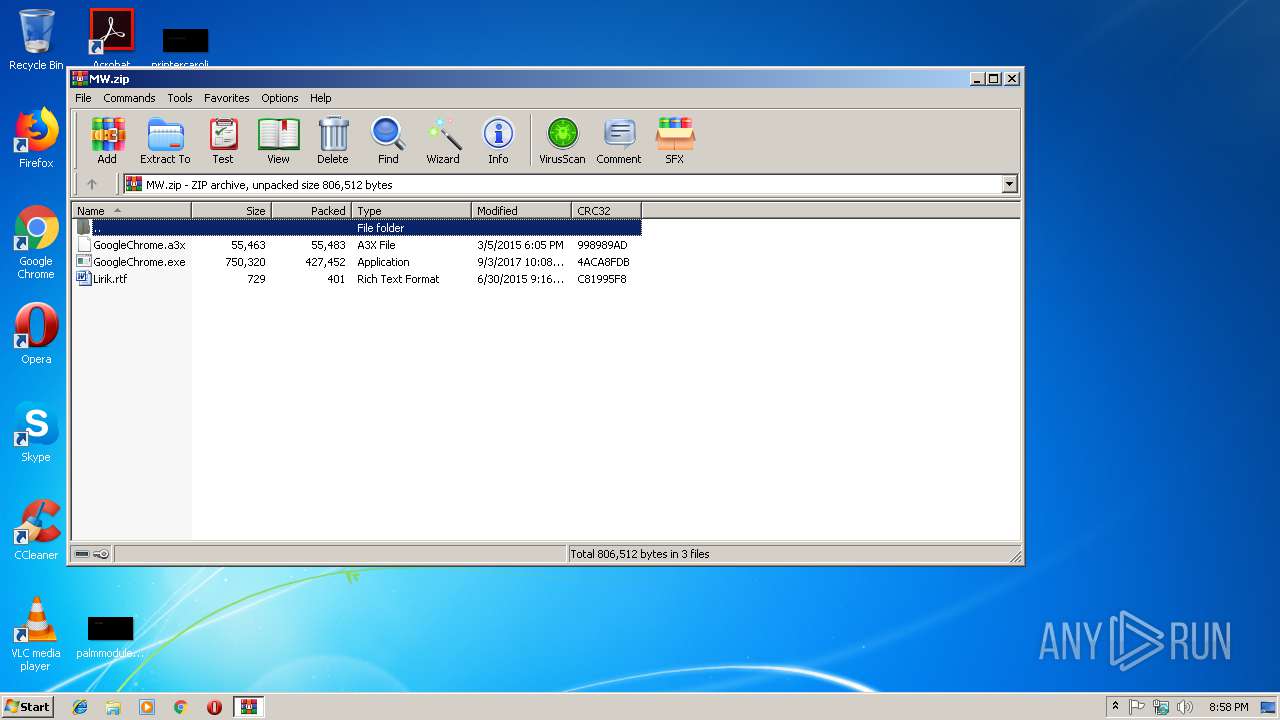
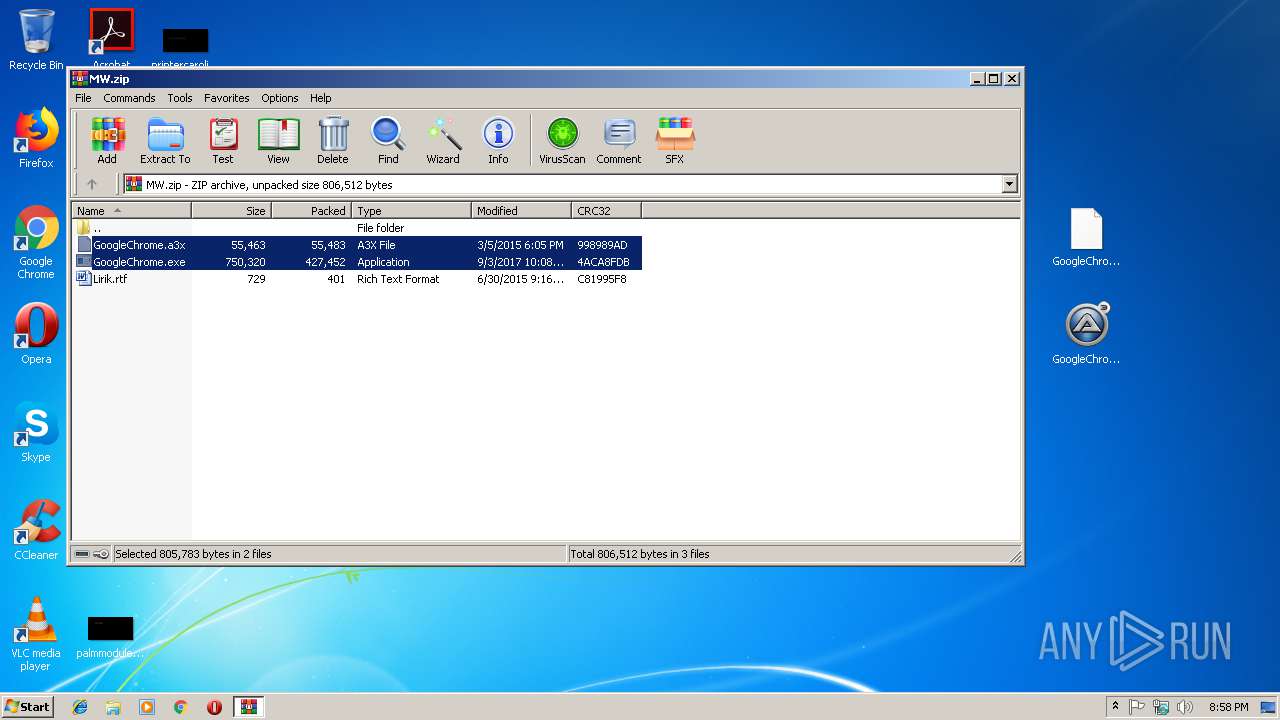
| File name: | MW.zip |
| Full analysis: | https://app.any.run/tasks/dbe2bae7-b026-414f-bc15-39e8d69cdeff |
| Verdict: | Malicious activity |
| Analysis date: | March 14, 2019, 20:57:44 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | B62D33BE0CEB7E65267333941A19710F |
| SHA1: | 292CC051FE0205CD00738E4D4EAA06AD4B33E89C |
| SHA256: | B160A40F9B2EE0D821D1F3423EAE452A096EBE6D755CDBDB6E388CE323DAFB72 |
| SSDEEP: | 12288:7yQo3SB2r/hlonASybLEsus8G+KetJlhiFD1cG:lkSYrWKIs8TuD17 |
MALICIOUS
Application was dropped or rewritten from another process
- GoogleChrome.exe (PID: 3092)
- GoogleChrome.exe (PID: 2348)
- GoogleChrome.exe (PID: 2120)
Changes the autorun value in the registry
- GoogleChrome.exe (PID: 2348)
- GoogleChrome.exe (PID: 2120)
SUSPICIOUS
Writes to a desktop.ini file (may be used to cloak folders)
- GoogleChrome.exe (PID: 3092)
- GoogleChrome.exe (PID: 2348)
- GoogleChrome.exe (PID: 2120)
Executable content was dropped or overwritten
- GoogleChrome.exe (PID: 3092)
- GoogleChrome.exe (PID: 2348)
- GoogleChrome.exe (PID: 2120)
Starts itself from another location
- GoogleChrome.exe (PID: 3092)
Uses NETSH.EXE for network configuration
- GoogleChrome.exe (PID: 2348)
- GoogleChrome.exe (PID: 2120)
Drop AutoIt3 executable file
- GoogleChrome.exe (PID: 3092)
- GoogleChrome.exe (PID: 2120)
- GoogleChrome.exe (PID: 2348)
Starts CMD.EXE for commands execution
- GoogleChrome.exe (PID: 3092)
Connects to unusual port
- GoogleChrome.exe (PID: 2348)
Creates files in the program directory
- GoogleChrome.exe (PID: 2348)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2015:03:05 18:05:28 |
| ZipCRC: | 0x998989ad |
| ZipCompressedSize: | 55483 |
| ZipUncompressedSize: | 55463 |
| ZipFileName: | GoogleChrome.a3x |
Total processes
40
Monitored processes
7
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
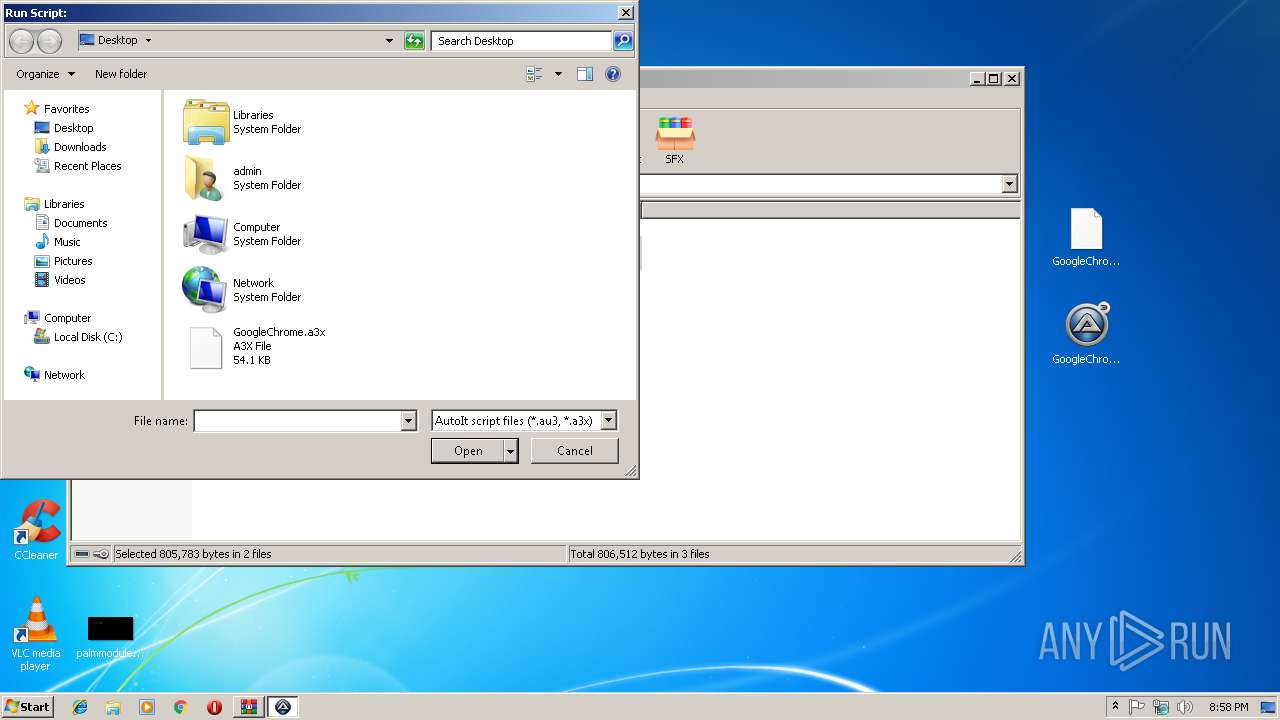
| 2120 | C:\GoogleChrome/GoogleChrome.exe C:\GoogleChrome/GoogleChrome.a3x | C:\GoogleChrome\GoogleChrome.exe | cmd.exe | ||||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Script Exit code: 0 Version: 3, 3, 8, 1 Modules
| |||||||||||||||
| 2332 | "C:\Windows\System32\netsh.exe" firewall add allowedprogram "C:\GoogleChrome\GoogleChrome.exe" "GoogleChrome.exe" ENABLE | C:\Windows\System32\netsh.exe | — | GoogleChrome.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2348 | "C:\GoogleChrome\GoogleChrome.exe" /AutoIt3ExecuteScript C:\GoogleChrome\GoogleChrome.a3x | C:\GoogleChrome\GoogleChrome.exe | GoogleChrome.exe | ||||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Script Exit code: 0 Version: 3, 3, 8, 1 Modules
| |||||||||||||||
| 2688 | "C:\Windows\System32\cmd.exe" /c start C:\GoogleChrome/GoogleChrome.exe C:\GoogleChrome/GoogleChrome.a3x | C:\Windows\System32\cmd.exe | — | GoogleChrome.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2984 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\MW.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3092 | "C:\Users\admin\Desktop\GoogleChrome.exe" | C:\Users\admin\Desktop\GoogleChrome.exe | explorer.exe | ||||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Script Exit code: 0 Version: 3, 3, 8, 1 Modules
| |||||||||||||||
| 3180 | "C:\Windows\System32\netsh.exe" firewall add allowedprogram "C:\GoogleChrome\GoogleChrome.exe" "GoogleChrome.exe" ENABLE | C:\Windows\System32\netsh.exe | — | GoogleChrome.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 603
Read events
1 365
Write events
237
Delete events
1
Modification events
| (PID) Process: | (2984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2984) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\MW.zip | |||
| (PID) Process: | (2984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3092) GoogleChrome.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 02020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (3092) GoogleChrome.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 0000000001000000020000000700000006000000030000000500000004000000FFFFFFFF | |||
Executable files
3
Suspicious files
0
Text files
30
Unknown types
21
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2984 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2984.9163\GoogleChrome.a3x | — | |
MD5:— | SHA256:— | |||
| 2984 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2984.9163\GoogleChrome.exe | — | |
MD5:— | SHA256:— | |||
| 3092 | GoogleChrome.exe | C:\GoogleChrome\collectionplaying.rtf | text | |
MD5:— | SHA256:— | |||
| 3092 | GoogleChrome.exe | C:\GoogleChrome\iibelieve.rtf | text | |
MD5:— | SHA256:— | |||
| 2348 | GoogleChrome.exe | C:\GoogleChrome\GoogleUpdate.lnk | lnk | |
MD5:— | SHA256:— | |||
| 3092 | GoogleChrome.exe | C:\GoogleChrome\menbuilt.rtf | text | |
MD5:— | SHA256:— | |||
| 2348 | GoogleChrome.exe | C:\MozillaFirefox\clearasia.png | image | |
MD5:— | SHA256:— | |||
| 3092 | GoogleChrome.exe | C:\GoogleChrome\printercarolina.jpg | image | |
MD5:— | SHA256:— | |||
| 3092 | GoogleChrome.exe | C:\GoogleChrome\palmmodule.jpg | image | |
MD5:— | SHA256:— | |||
| 2348 | GoogleChrome.exe | C:\GoogleChrome\WindowsUpdate.lnk | lnk | |
MD5:AB787A9AA4630CCE04A25689D4E05641 | SHA256:47CE7C41BE5911A6B64E80FE334091C6E6B9DF37926C88795A0D3A19C6AF37F9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
9
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2348 | GoogleChrome.exe | 195.22.4.21:1212 | dmad.info | Claranet Ltd | PT | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
dmad.info |
| malicious |