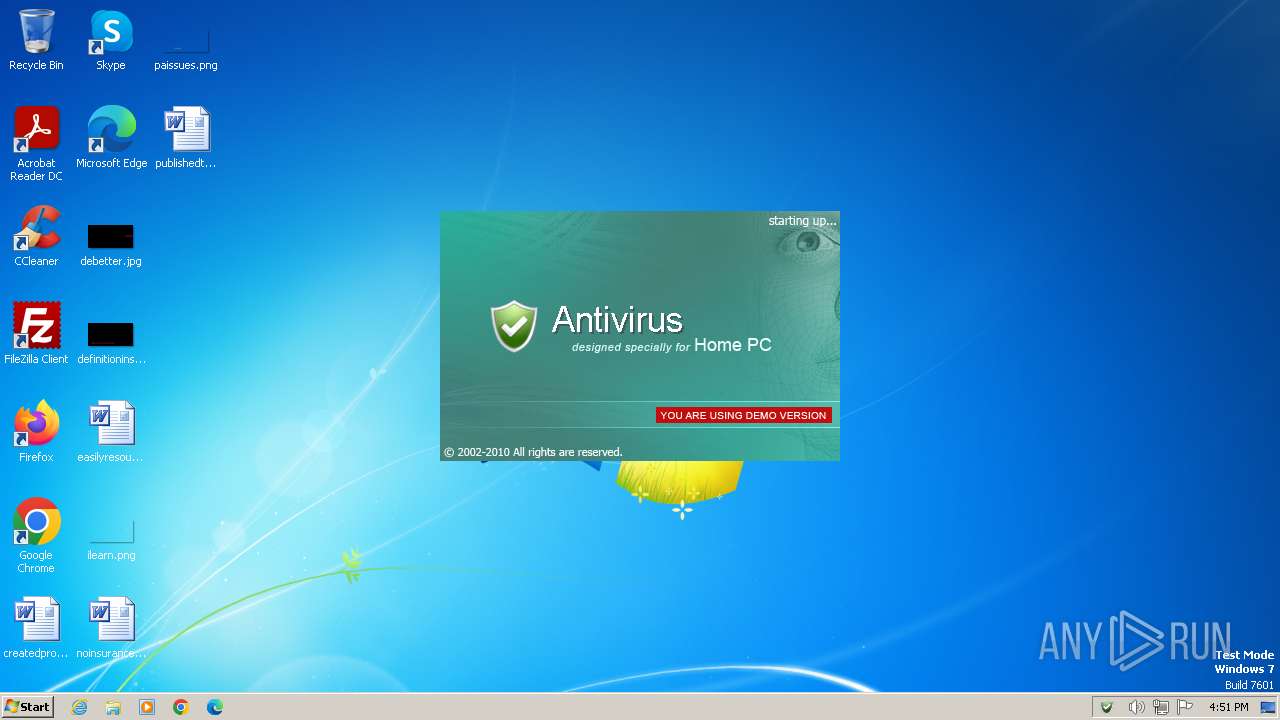
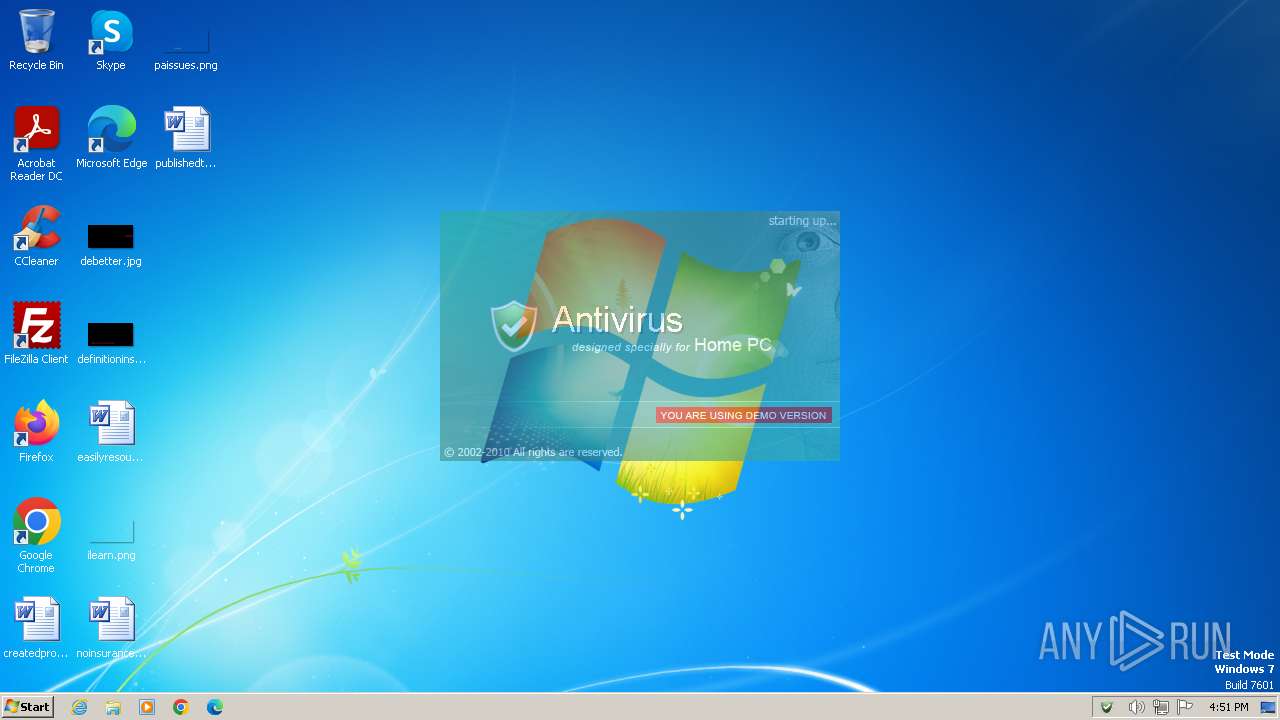
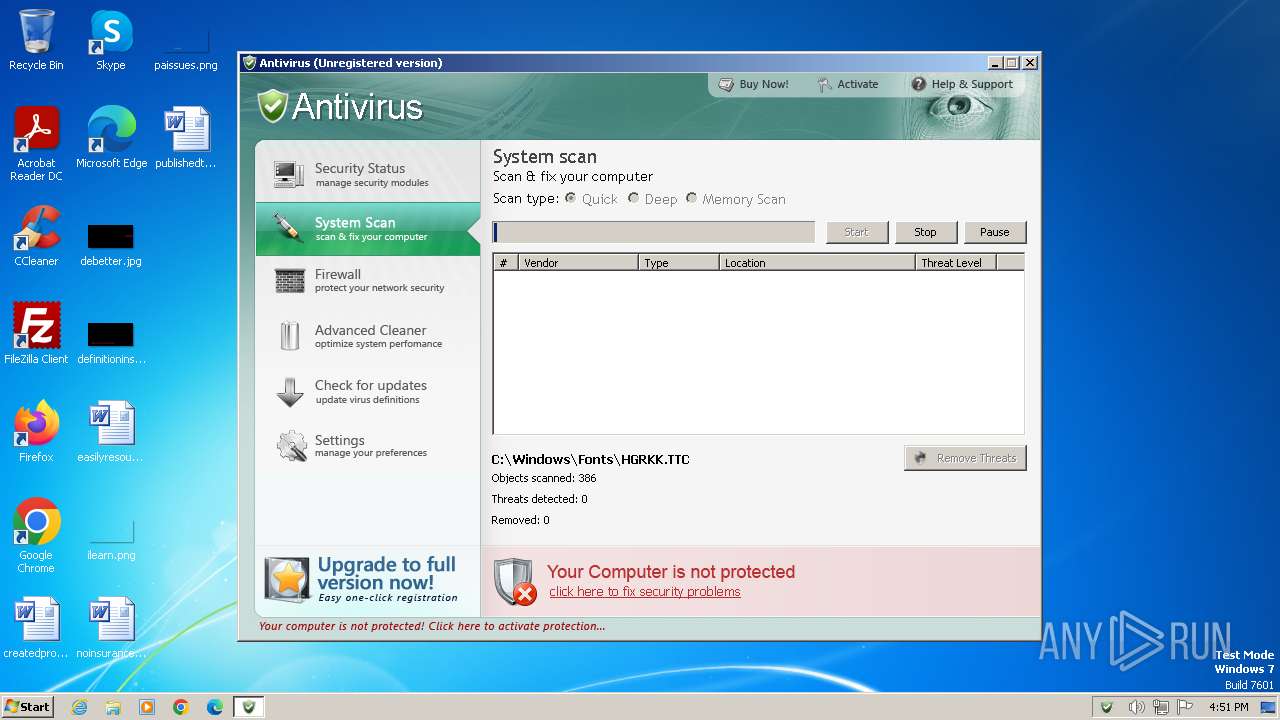
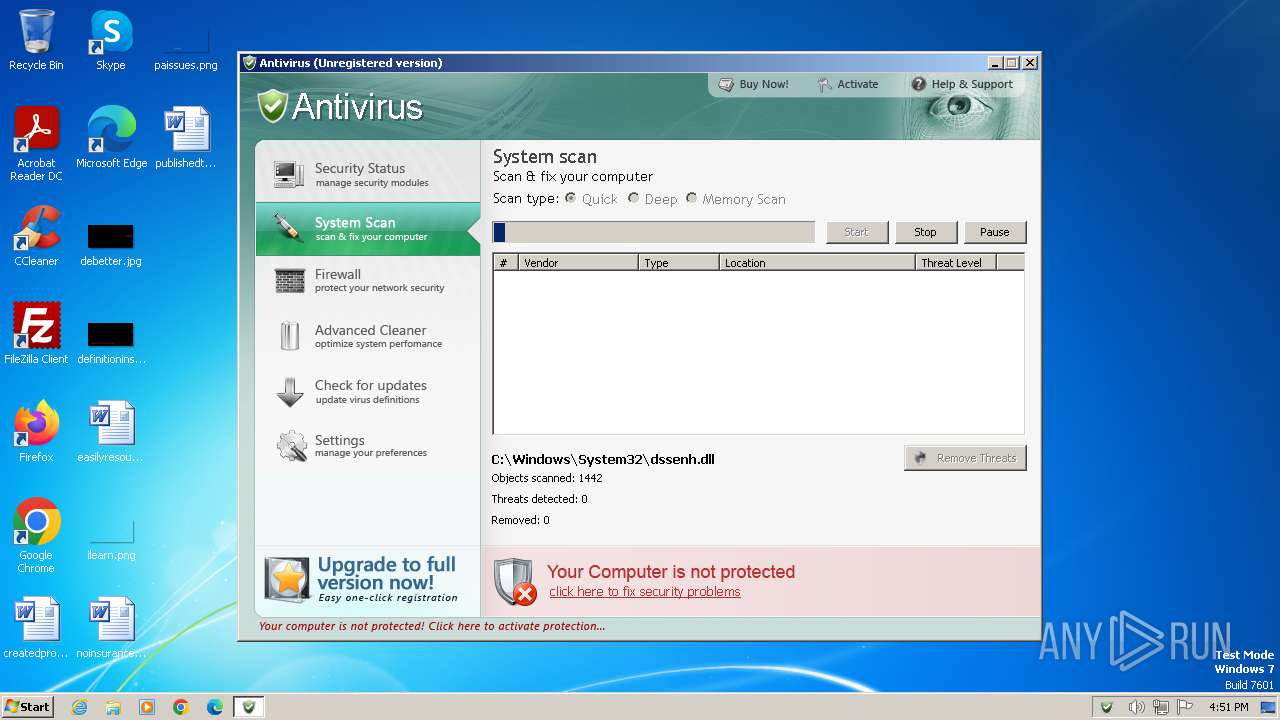
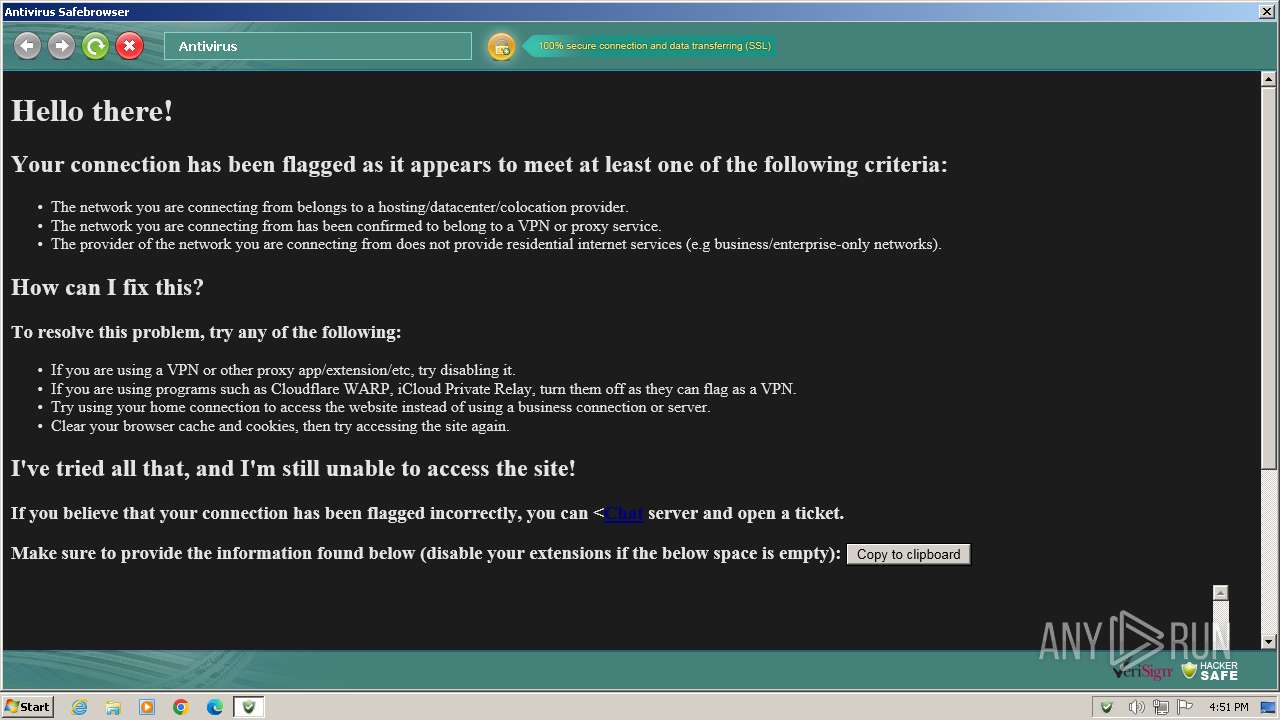
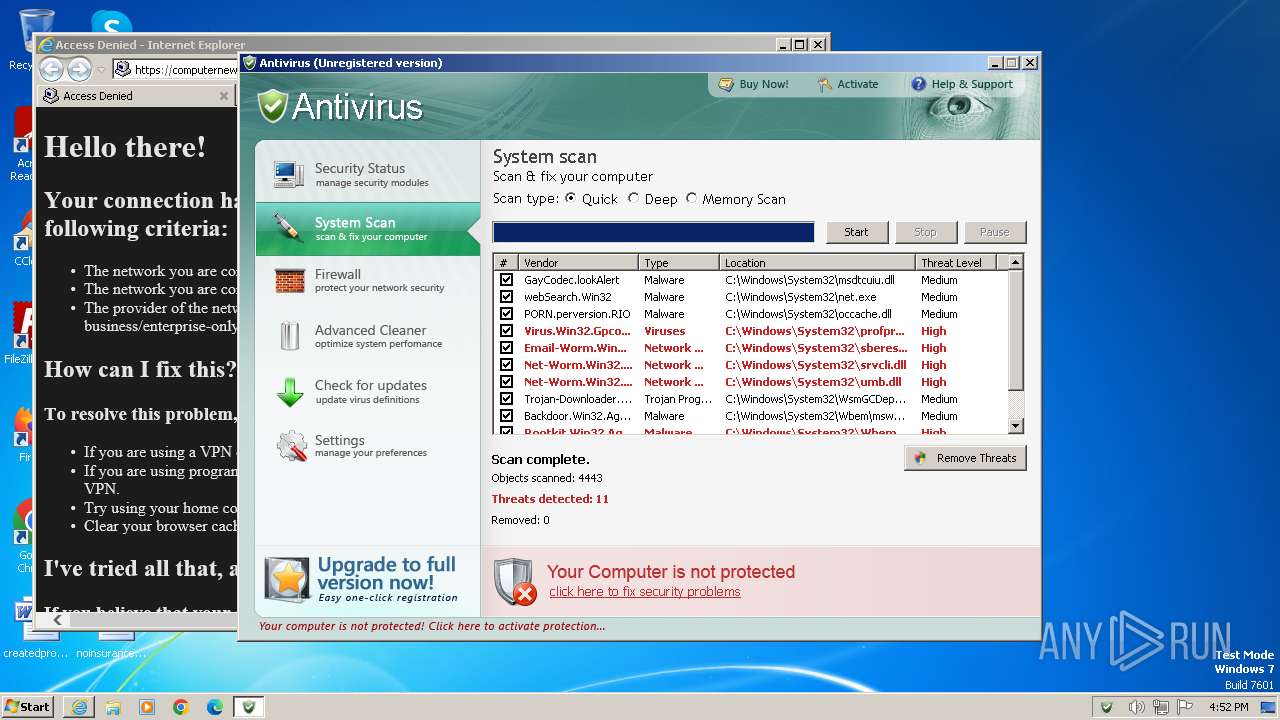
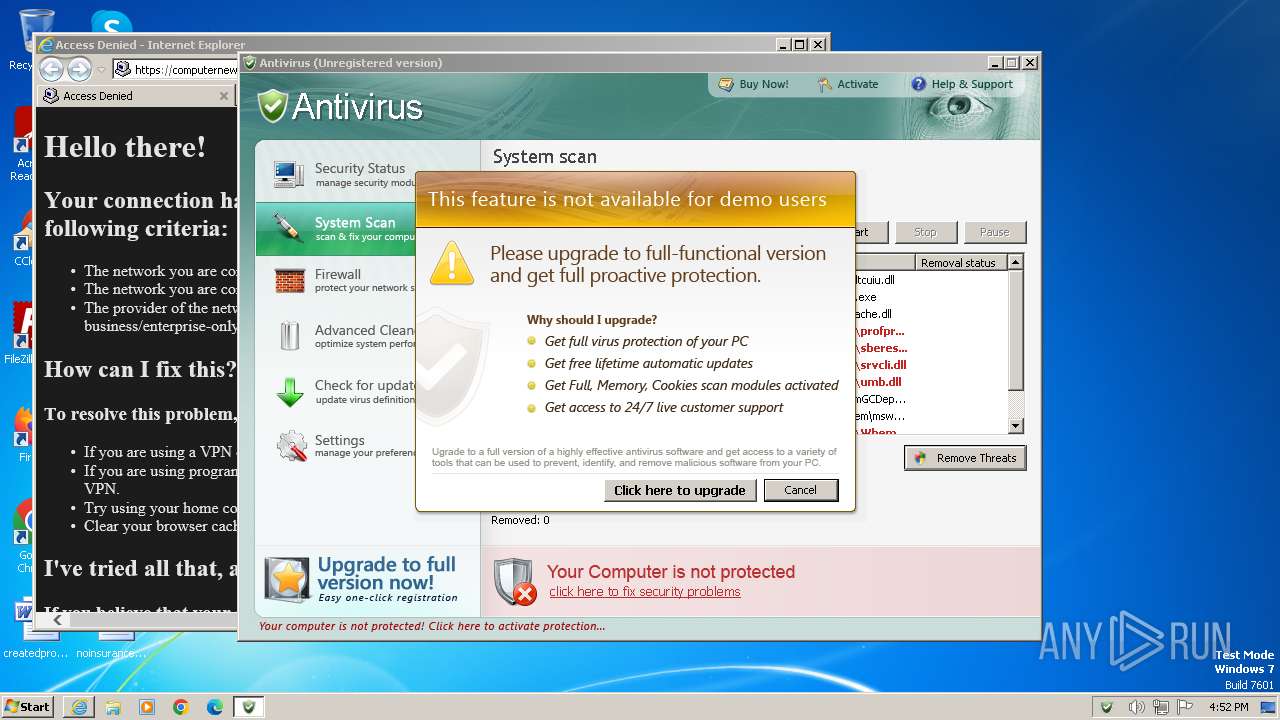
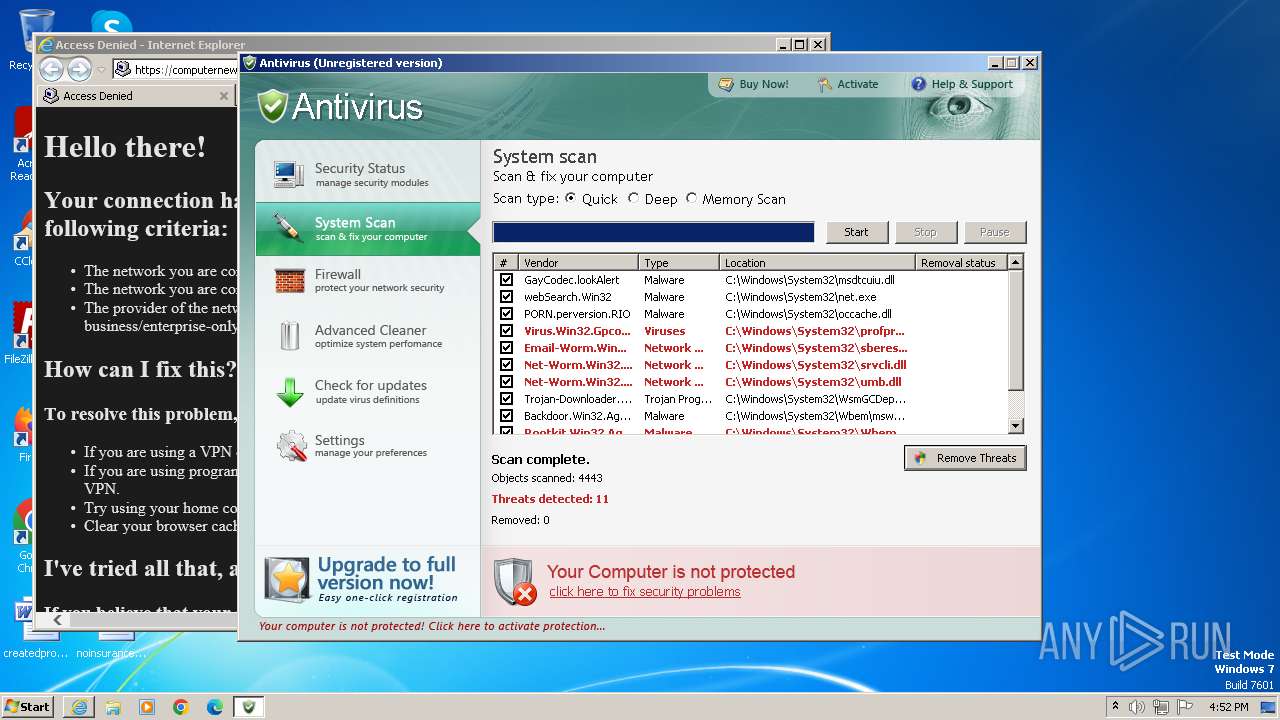
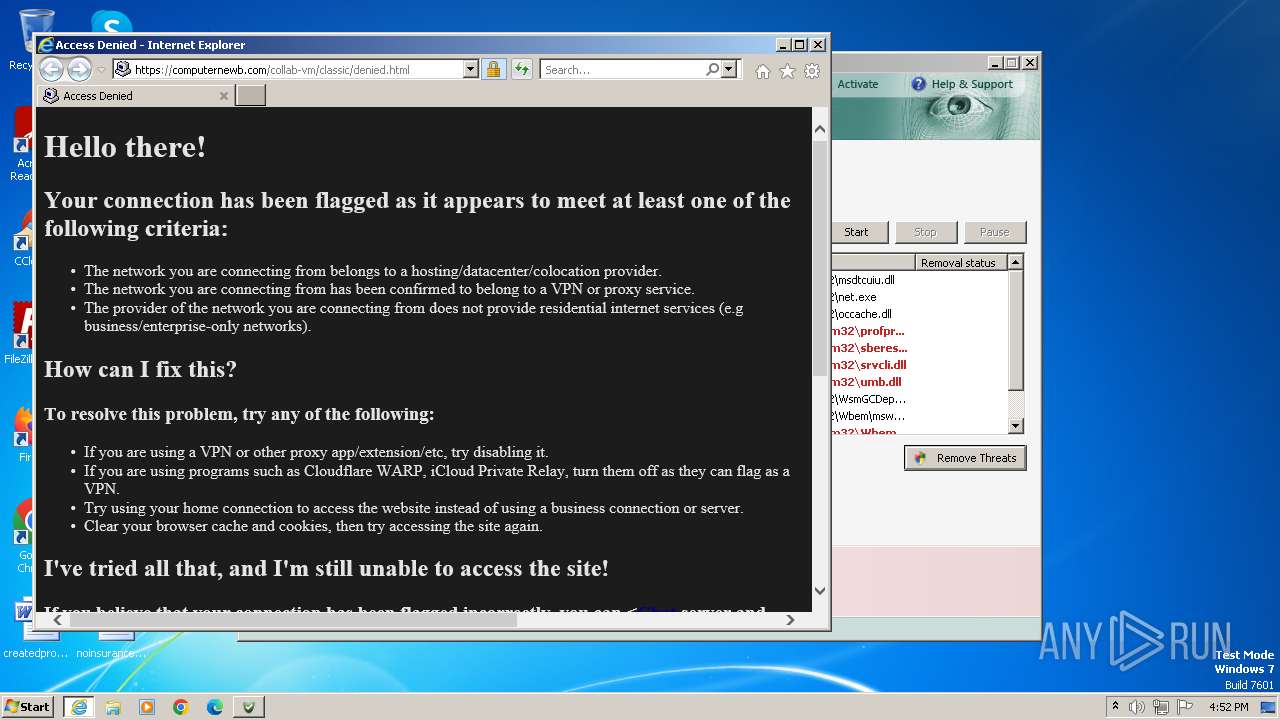
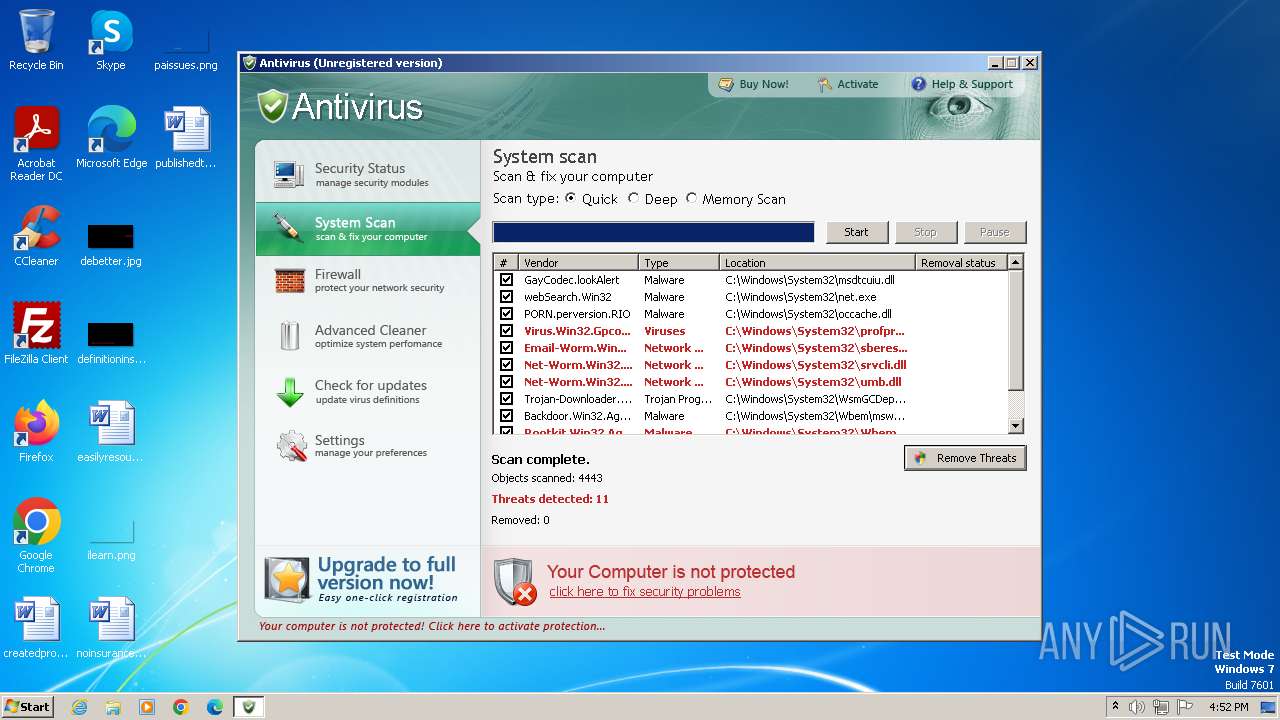
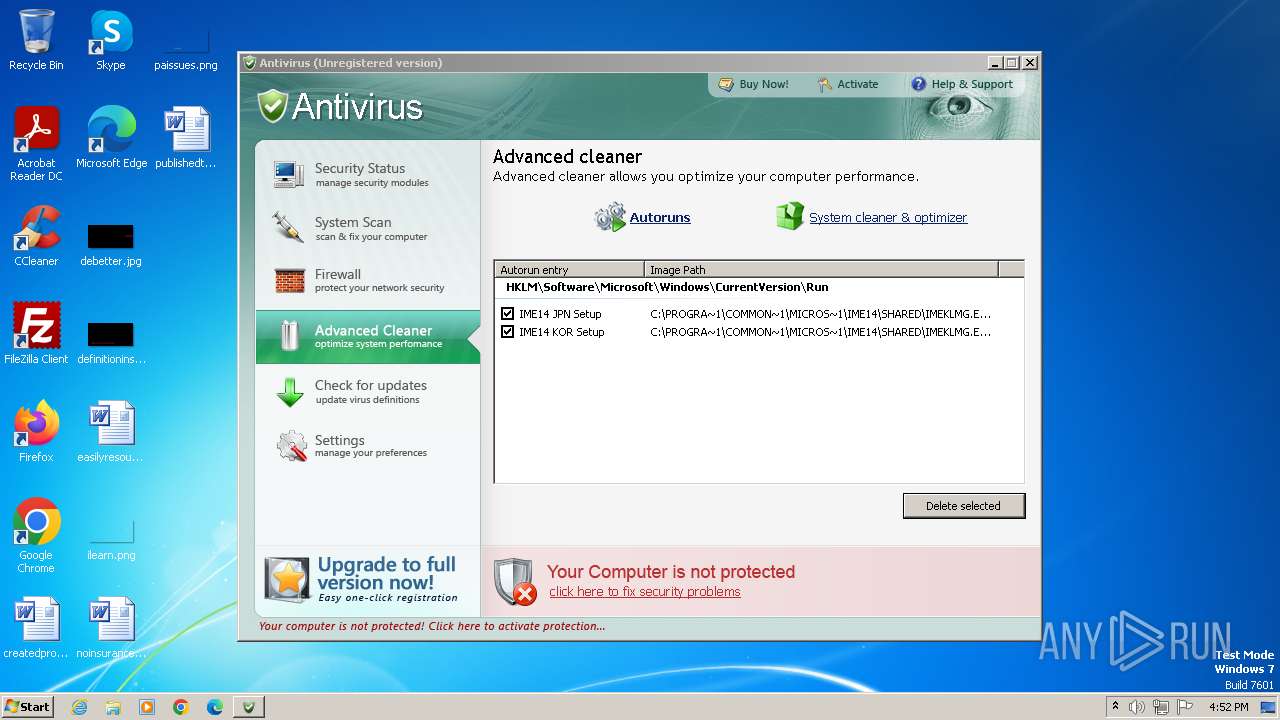
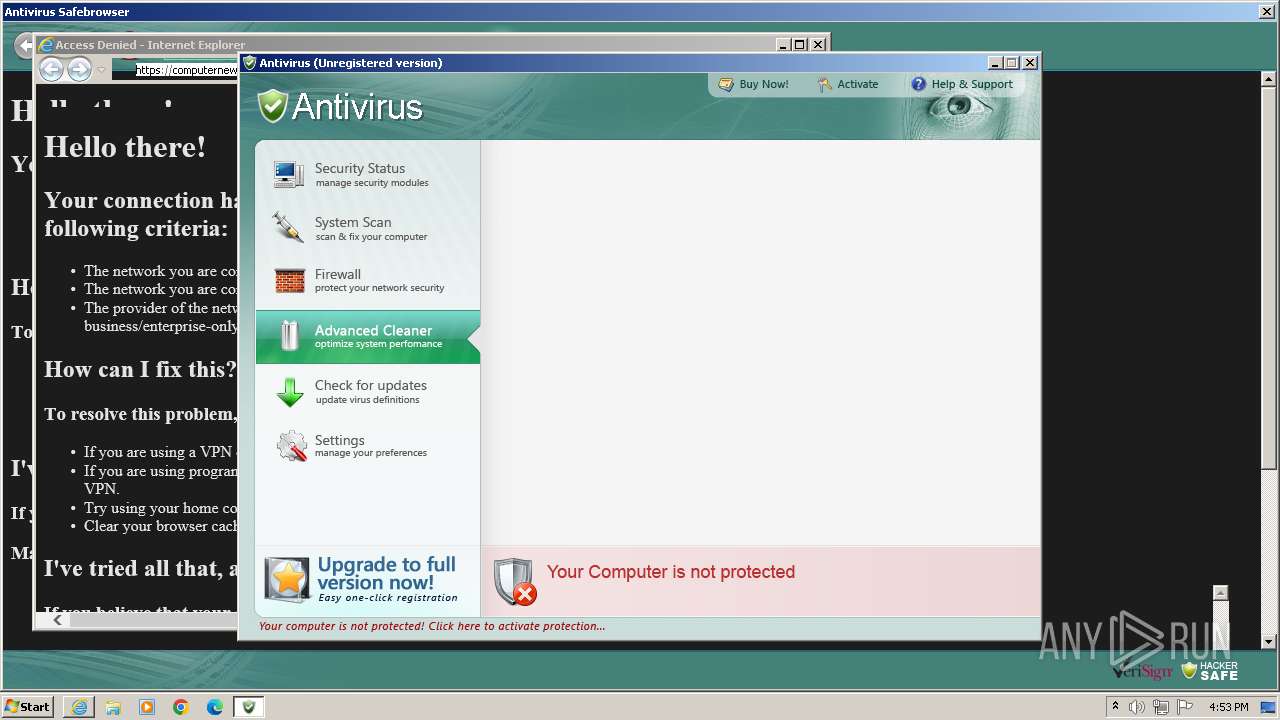
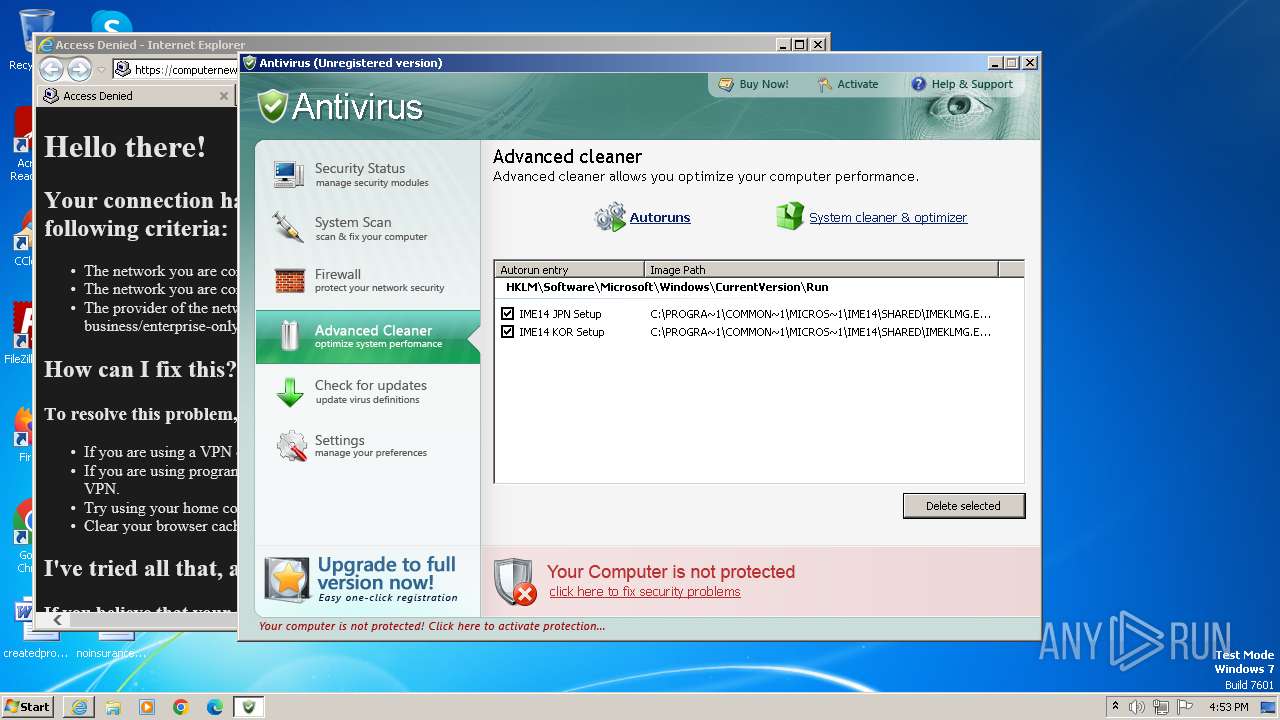
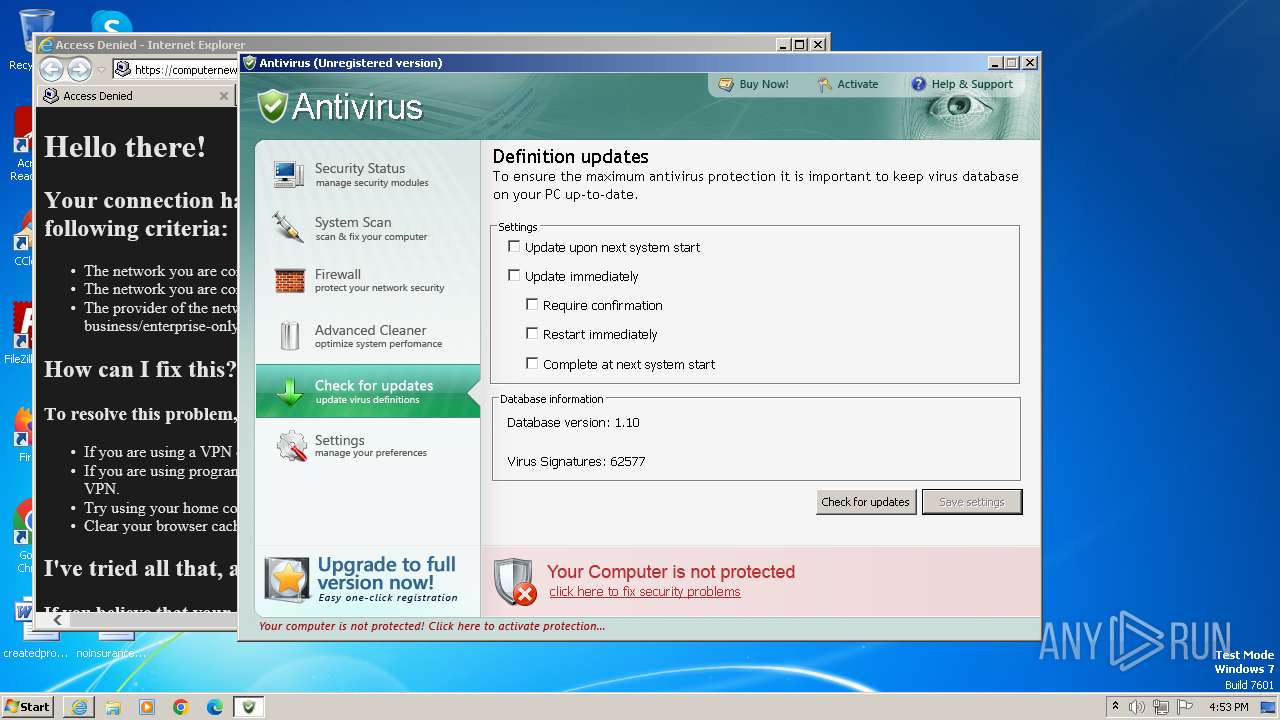
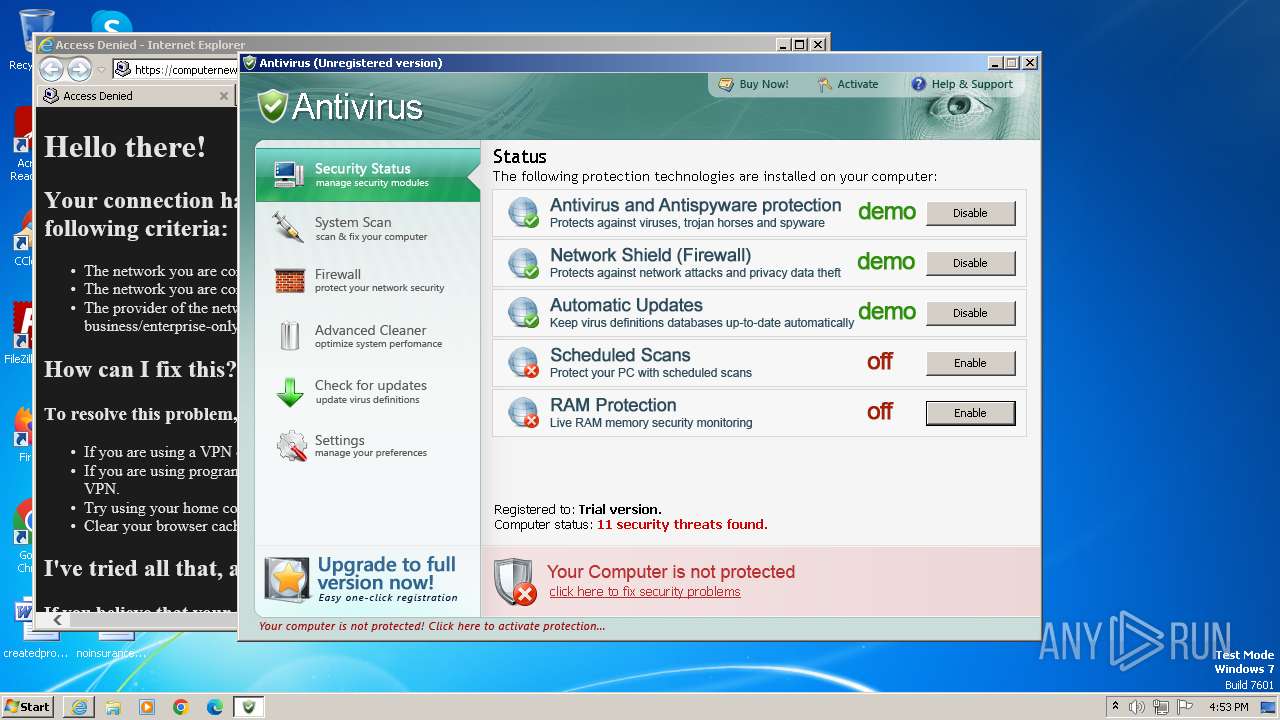
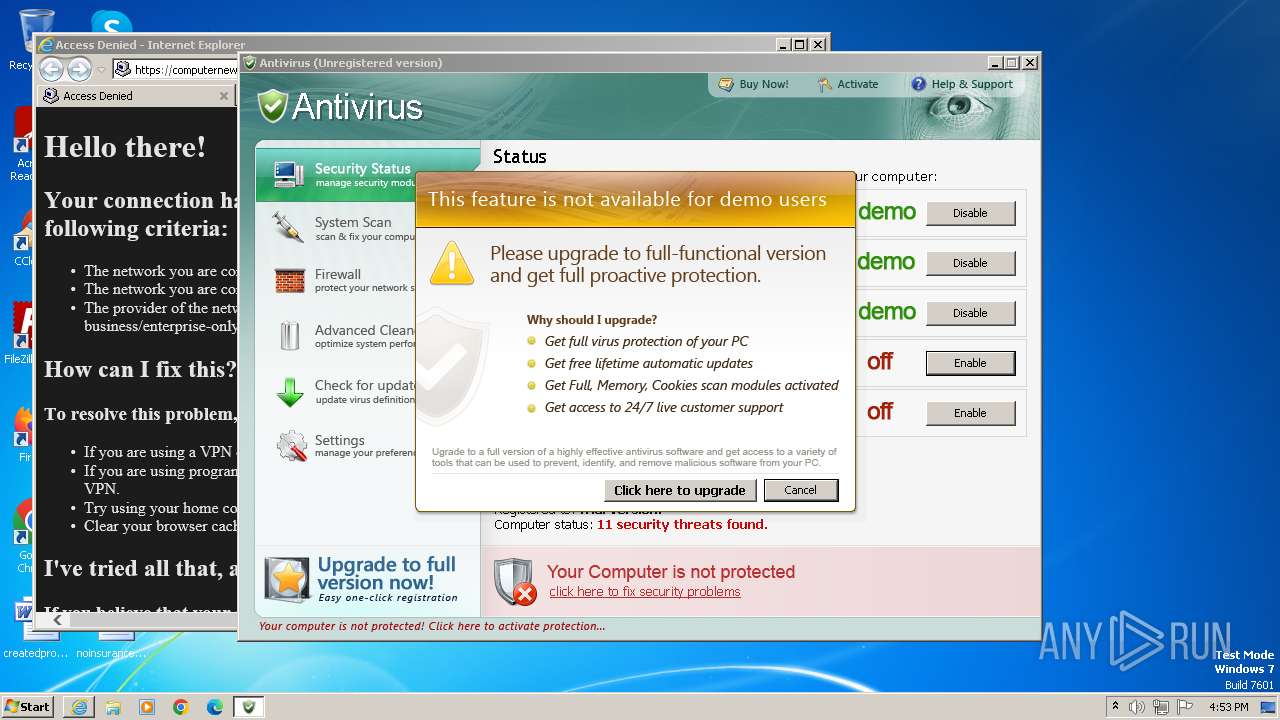
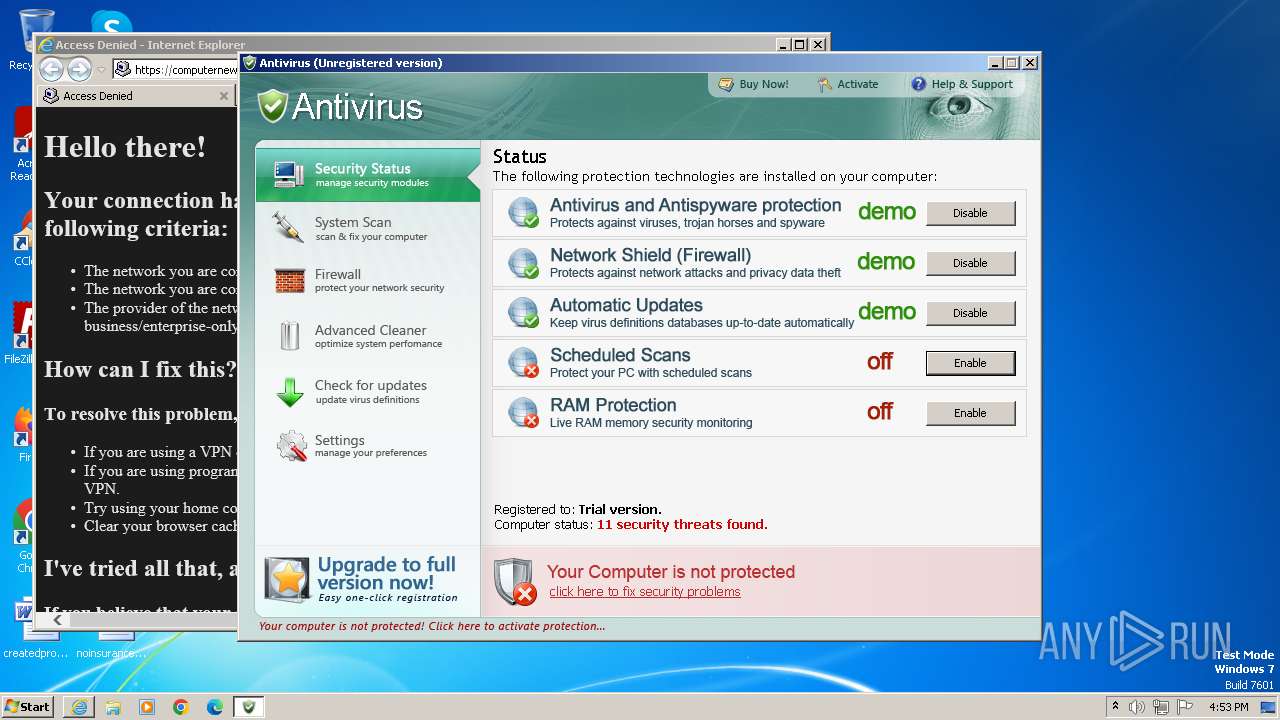
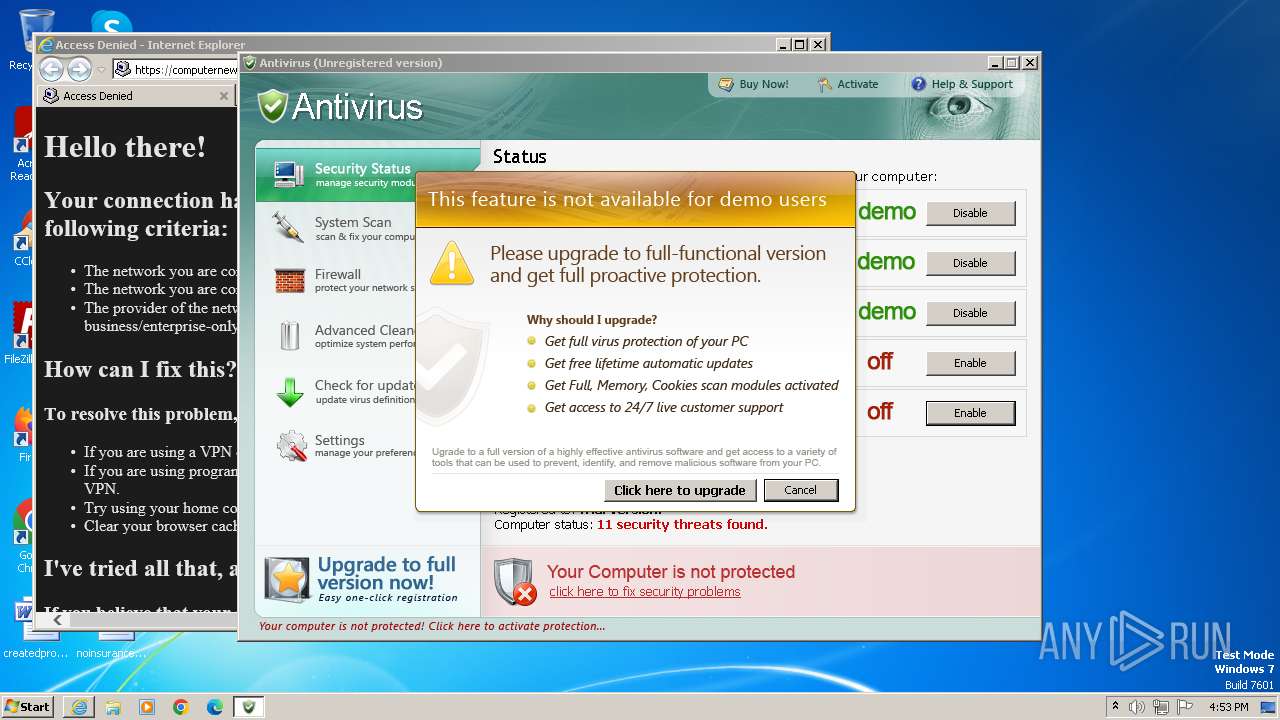
| File name: | Antivirus.exe |
| Full analysis: | https://app.any.run/tasks/b19a4c56-19b0-4f01-b377-4bfed7812ad2 |
| Verdict: | Malicious activity |
| Analysis date: | February 10, 2024, 16:51:21 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | C7E9746B1B039B8BD1106BCA3038C38F |
| SHA1: | CB93AC887876BAFE39C5F9AA64970D5E747FB191 |
| SHA256: | B1369BD254D96F7966047AD4BE06103830136629590182D49E5CB8680529EBD4 |
| SSDEEP: | 49152:FH/1Fdq0wneDrEoYxWFjmYMcKabLVp3diY7kp:FH/1Fdq0nIo2YAcl/NisA |
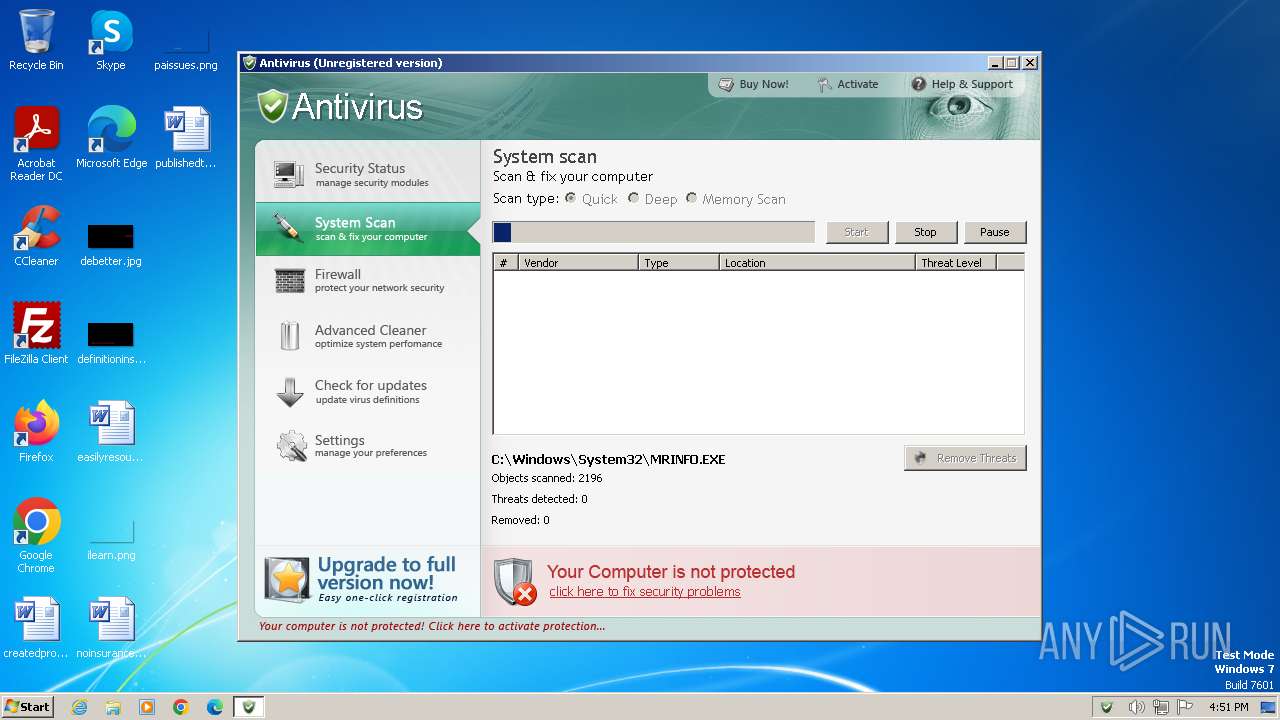
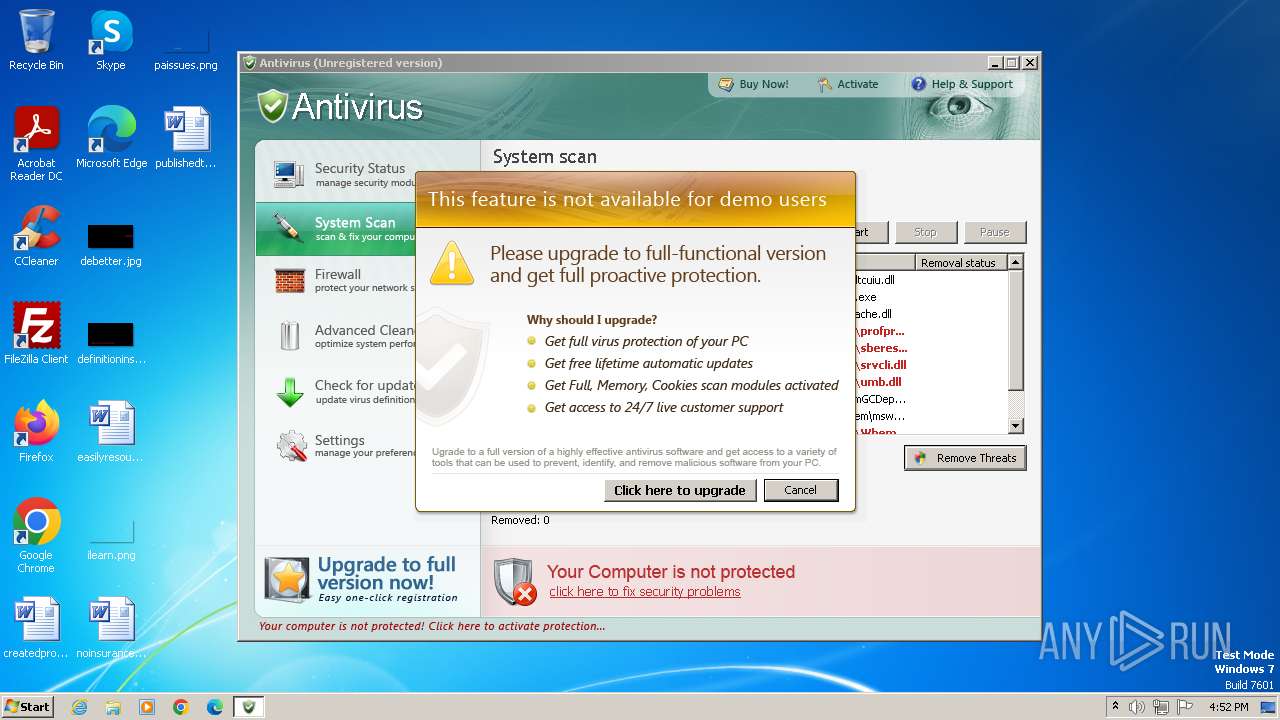
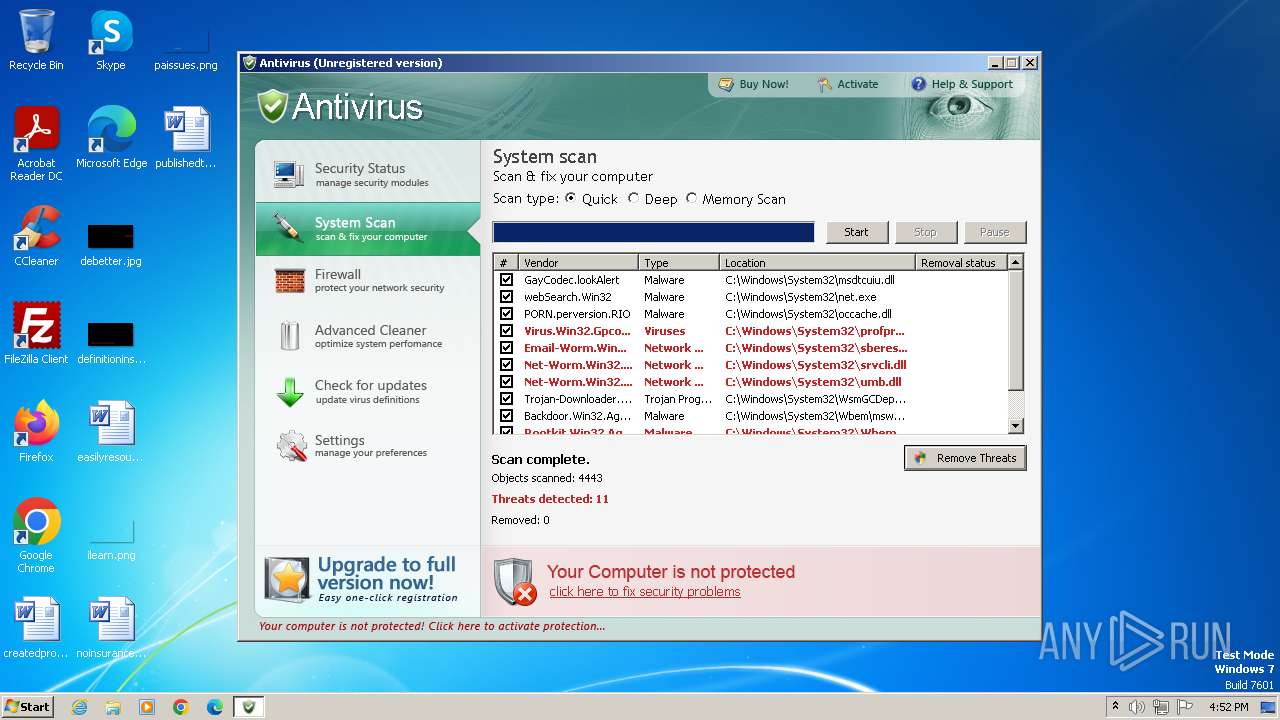
MALICIOUS
Drops the executable file immediately after the start
- Antivirus.exe (PID: 3668)
Uses NET.EXE to stop Windows Security Center service
- Antivirus.exe (PID: 3668)
- net.exe (PID: 3944)
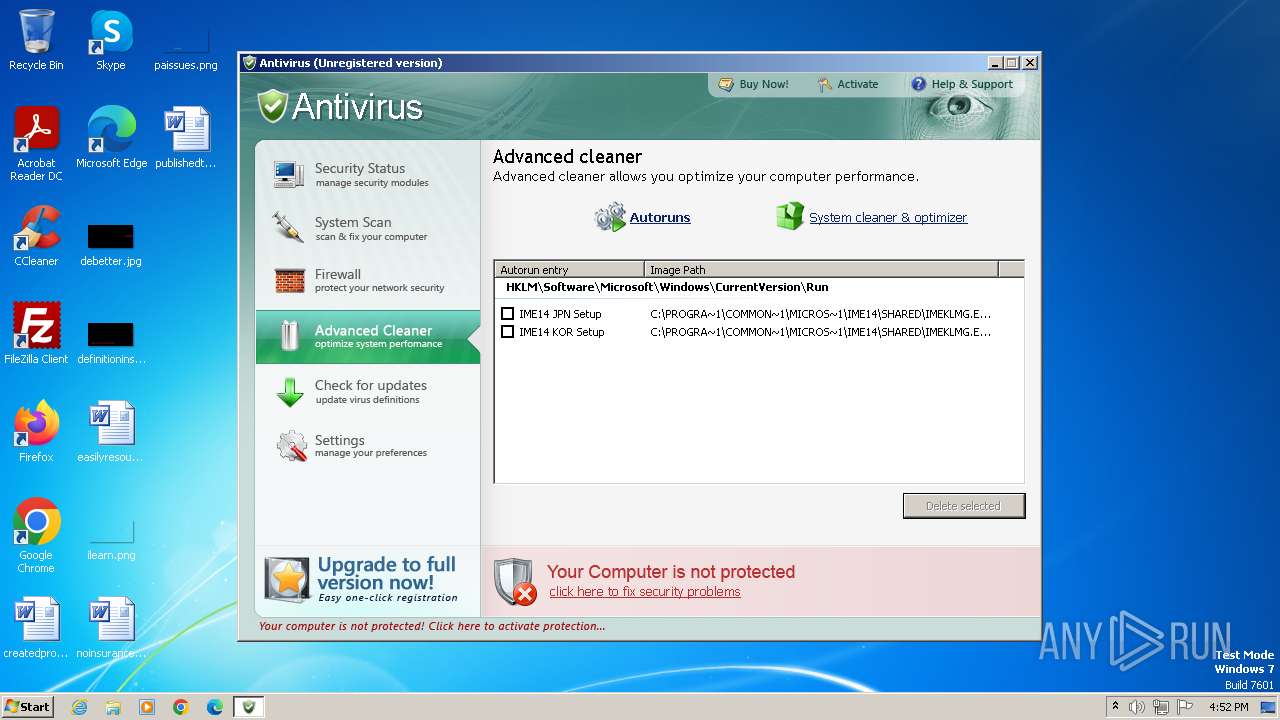
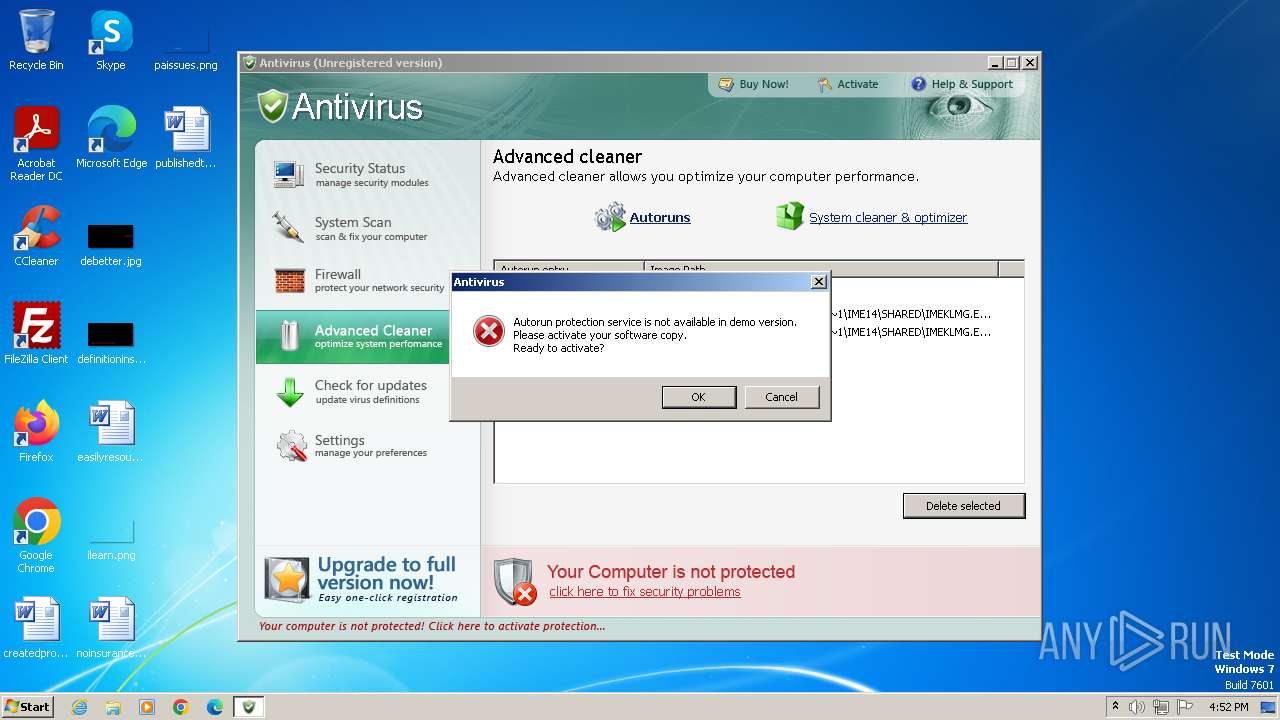
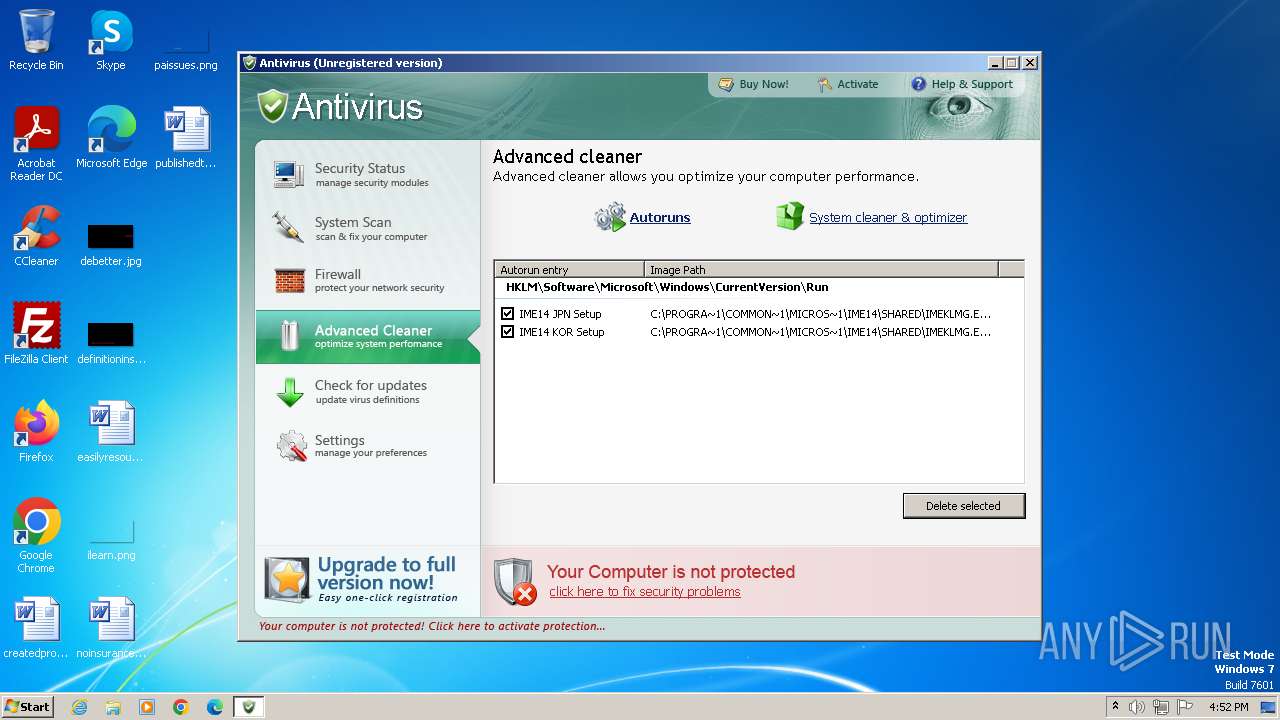
Changes the autorun value in the registry
- Antivirus.exe (PID: 3668)
Starts NET.EXE for service management
- Antivirus.exe (PID: 3668)
- net.exe (PID: 3228)
- net.exe (PID: 3944)
- net.exe (PID: 2332)
- net.exe (PID: 1876)
SUSPICIOUS
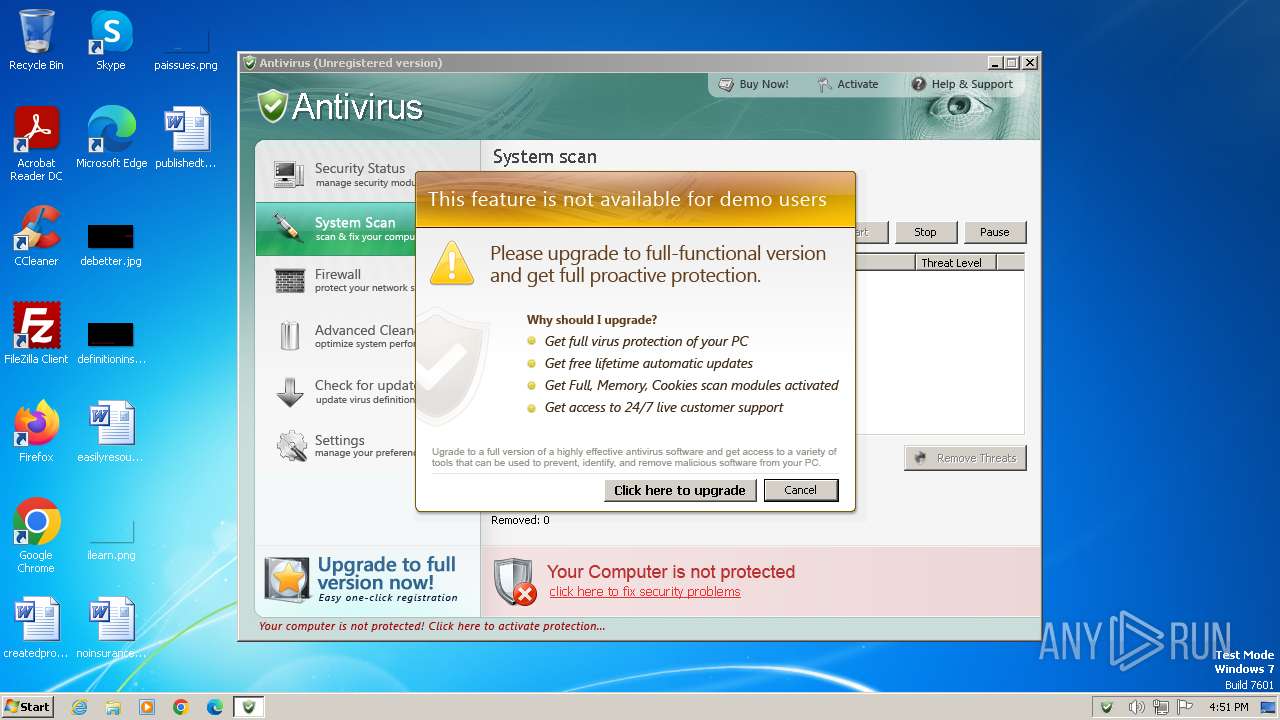
Changes internet zones settings
- Antivirus.exe (PID: 3668)
Reads the Internet Settings
- Antivirus.exe (PID: 3668)
Reads security settings of Internet Explorer
- Antivirus.exe (PID: 3668)
Reads Internet Explorer settings
- Antivirus.exe (PID: 3668)
Reads settings of System Certificates
- Antivirus.exe (PID: 3668)
Checks Windows Trust Settings
- Antivirus.exe (PID: 3668)
Reads Microsoft Outlook installation path
- Antivirus.exe (PID: 3668)
INFO
Checks supported languages
- Antivirus.exe (PID: 3668)
Reads the computer name
- Antivirus.exe (PID: 3668)
Checks proxy server information
- Antivirus.exe (PID: 3668)
Reads the machine GUID from the registry
- Antivirus.exe (PID: 3668)
Create files in a temporary directory
- Antivirus.exe (PID: 3668)
- mofcomp.exe (PID: 2444)
Reads Environment values
- Antivirus.exe (PID: 3668)
Reads the software policy settings
- Antivirus.exe (PID: 3668)
Creates files or folders in the user directory
- Antivirus.exe (PID: 3668)
Process checks whether UAC notifications are on
- Antivirus.exe (PID: 3668)
Application launched itself
- iexplore.exe (PID: 2728)
- iexplore.exe (PID: 3636)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2010:07:21 07:55:24+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 8 |
| CodeSize: | 708608 |
| InitializedDataSize: | 1357312 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3f9df |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
59
Monitored processes
14
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1692 | C:\Windows\system32\net1 stop wscsvc | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1836 | C:\Windows\system32\net1 stop winmgmt /y | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1876 | net start winmgmt | C:\Windows\System32\net.exe | — | Antivirus.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2232 | C:\Windows\system32\net1 start wscsvc | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2244 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2728 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2332 | net start wscsvc | C:\Windows\System32\net.exe | — | Antivirus.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2444 | mofcomp C:\Users\admin\AppData\Local\Temp\4otjesjty.mof | C:\Windows\System32\wbem\mofcomp.exe | — | Antivirus.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: The Managed Object Format (MOF) Compiler Exit code: 3 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2648 | C:\Windows\system32\net1 start winmgmt | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2728 | "C:\Program Files\Internet Explorer\iexplore.exe" -Embedding | C:\Program Files\Internet Explorer\iexplore.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3228 | net stop winmgmt /y | C:\Windows\System32\net.exe | — | Antivirus.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
43 360
Read events
42 968
Write events
306
Delete events
86
Modification events
| (PID) Process: | (3668) Antivirus.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\AnVi |
| Operation: | write | Name: | Settings_0 |
Value: 1 | |||
| (PID) Process: | (3668) Antivirus.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | Use FormSuggest |
Value: Yes | |||
| (PID) Process: | (3668) Antivirus.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\3 |
| Operation: | write | Name: | 1601 |
Value: 0 | |||
| (PID) Process: | (3668) Antivirus.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | WarnOnZoneCrossing |
Value: 0 | |||
| (PID) Process: | (3668) Antivirus.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\AnVi |
| Operation: | write | Name: | SecStatus_3 |
Value: 1 | |||
| (PID) Process: | (3668) Antivirus.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\AnVi |
| Operation: | write | Name: | SecStatus_4 |
Value: 1 | |||
| (PID) Process: | (3668) Antivirus.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\AnVi |
| Operation: | write | Name: | SecStatus_5 |
Value: 1 | |||
| (PID) Process: | (3668) Antivirus.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\AnVi |
| Operation: | write | Name: | FD |
Value: 0 | |||
| (PID) Process: | (3668) Antivirus.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\AnVi |
| Operation: | write | Name: | GUID |
Value: 425360974253608542536082 | |||
| (PID) Process: | (3668) Antivirus.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\AnVi |
| Operation: | write | Name: | Data |
Value: :2238:2411:2584:2757:2930:3103:3276:3622:3795:3968:4314:4487: | |||
Executable files
0
Suspicious files
12
Text files
15
Unknown types
15
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3668 | Antivirus.exe | C:\Users\admin\AppData\Local\Temp\4otjesjty.mof | text | |
MD5:7FAD92AFDA308DCA8ACFC6FF45C80C24 | SHA256:76E19416EB826A27BDCF626C3877CF7812BBE9B62CC2CCC5C2F65461D644246F | |||
| 3668 | Antivirus.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:8D00D1D53331A5D8C3215B635CBF0C4D | SHA256:8CDCA3E5F4B5D978B94A06EA2EB7EED7BEC4BCAE220156B36B2A29943F15C166 | |||
| 3668 | Antivirus.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_F2DAF19C1F776537105D08FC8D978464 | der | |
MD5:8202A1CD02E7D69597995CABBE881A12 | SHA256:58F381C3A0A0ACE6321DA22E40BD44A597BD98B9C9390AB9258426B5CF75A7A5 | |||
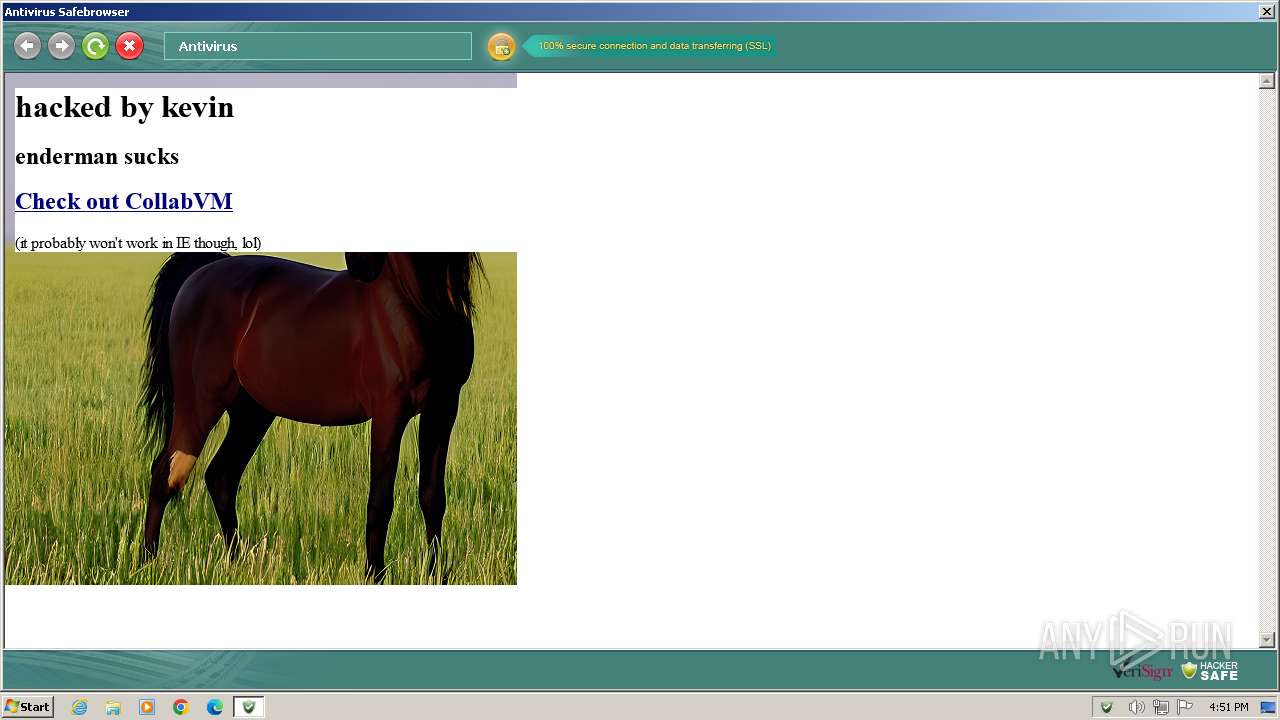
| 3668 | Antivirus.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\kevin[1].bmp | image | |
MD5:17B80ACE3086B464254C4D05BF85E488 | SHA256:2290DED38494032284D49E7D53744B78CE836EC6354F4856878769C5D6FD2716 | |||
| 3668 | Antivirus.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\buy[1].htm | html | |
MD5:69D2D338A7178B991A67134E1E72EAA6 | SHA256:921BEAA969E6A74EF33305DEAF7B5925ACD1D2FF5091266F693BFBAA15CAD5DA | |||
| 3668 | Antivirus.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:46517D43D1D09C99E74E0492BC38D8A6 | SHA256:779294754FBE6247424E486D10D2978E76251902FD2F0F1CFD5900D13B2B9AB4 | |||
| 3668 | Antivirus.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\denied[1].htm | html | |
MD5:5D547EF9172CEB87DC6934FA11FF9253 | SHA256:D8E32585F3821E94A203F8BDCDA73DCF73FDAD45BE5A51AD20C9A06210780561 | |||
| 2244 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\v84a3a4012de94ce1a686ba8c167c359c1696973893317[1].js | text | |
MD5:DD1D068FDB5FE90B6C05A5B3940E088C | SHA256:6153D13804862B0FC1C016CF1129F34CB7C6185F2CF4BF1A3A862EECDAB50101 | |||
| 2728 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\imagestore\f7ruq93\imagestore.dat | binary | |
MD5:052E4F8A8904E16F641D06D358F4853B | SHA256:9B4CFC062347091DDC251F0E25756F91E9756760121325EEF8B89E857E645036 | |||
| 2728 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\EAF8AA29A62AB29E614331747385D816_F9E4DC0B9D5C777357D7DB8DEF51118A | der | |
MD5:AC18AD50EB0F947D10138013E66192E6 | SHA256:090DAFF0E114748D5C6229A12B0FD5D92FA6761F9B0CE5E988B1FD79C611CB14 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
28
TCP/UDP connections
32
DNS requests
20
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3668 | Antivirus.exe | GET | 404 | 54.39.157.64:80 | http://searchdusty.com/avt/avt_db | unknown | html | 153 b | unknown |
3668 | Antivirus.exe | GET | 404 | 54.39.157.64:80 | http://searchdusty.com/avt/avt.dat | unknown | html | 153 b | unknown |
3668 | Antivirus.exe | GET | 404 | 54.39.157.64:80 | http://searchdusty.com/avt/avtr.dat | unknown | html | 153 b | unknown |
3668 | Antivirus.exe | GET | 200 | 54.39.157.64:80 | http://searchdusty.com/customers/buy.php?pid=AVT_BASIC&id=139&subid=1 | unknown | html | 985 b | unknown |
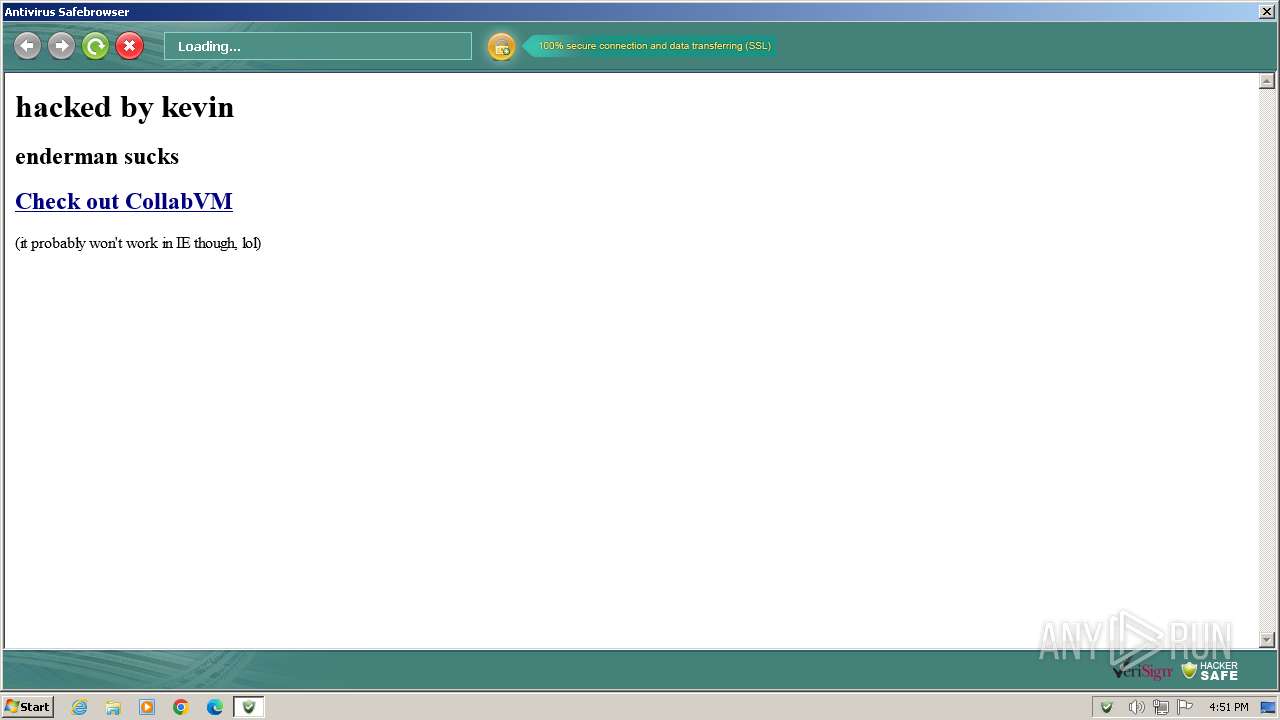
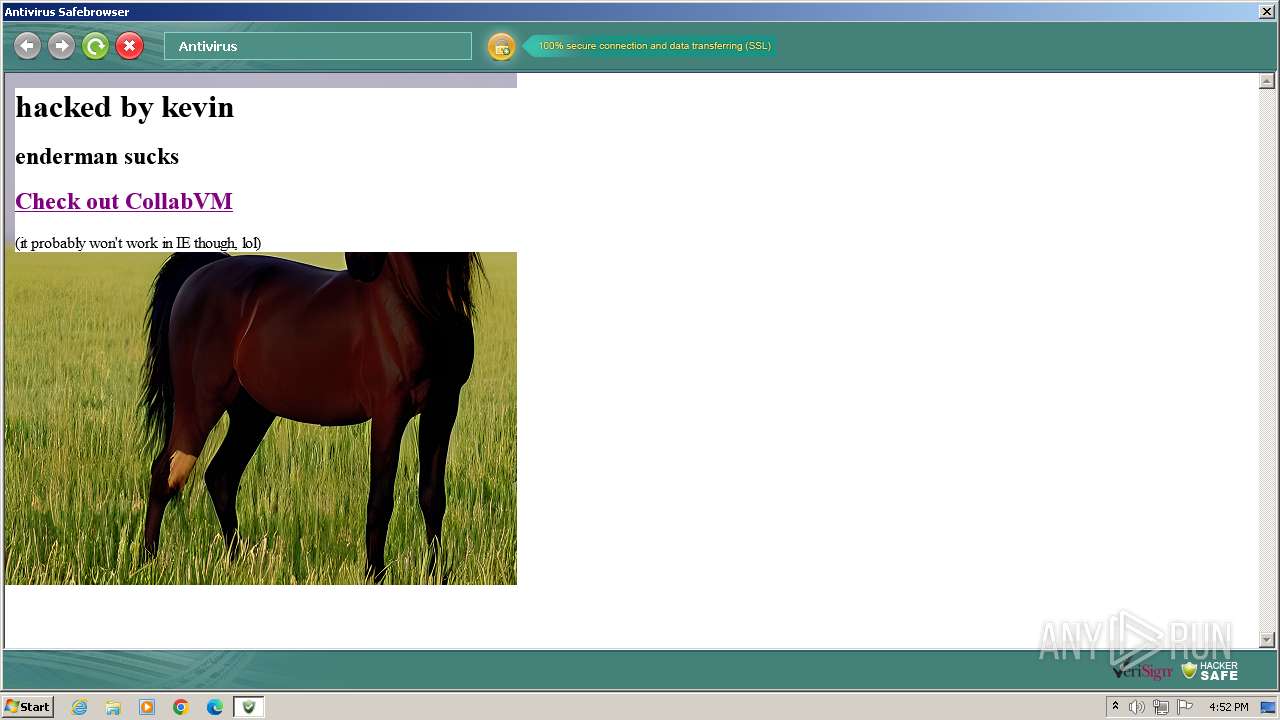
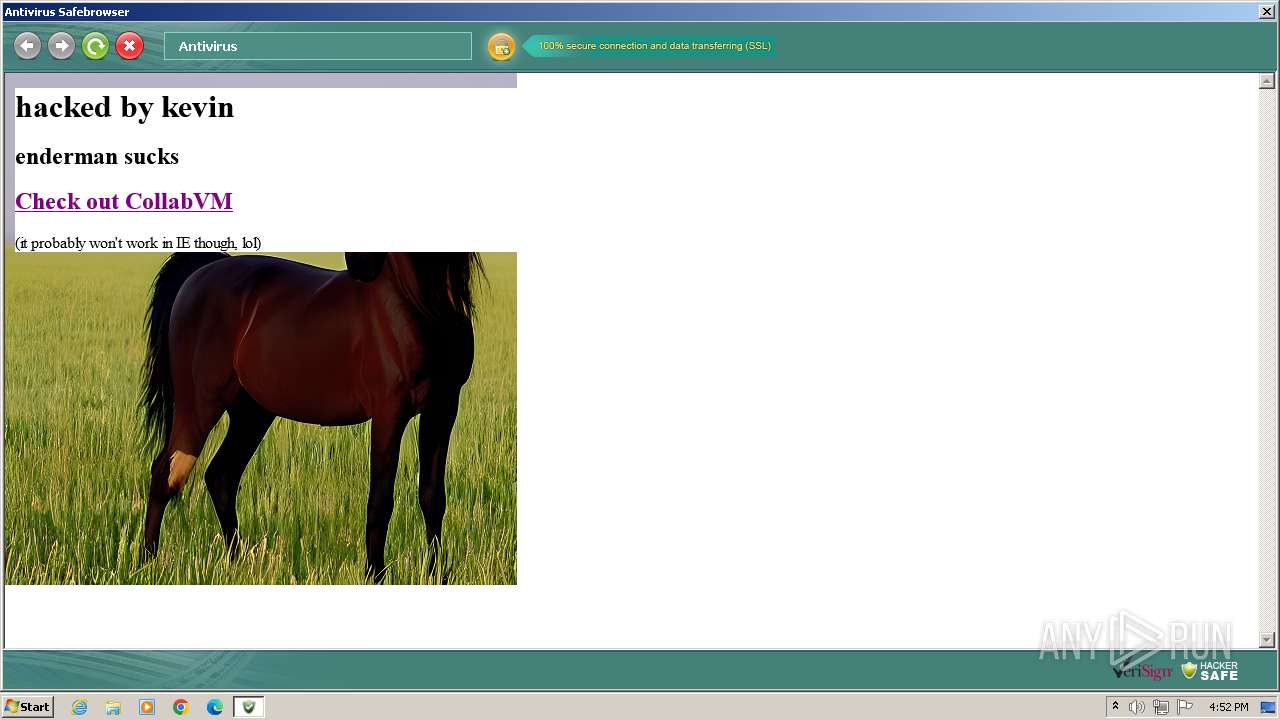
3668 | Antivirus.exe | GET | 200 | 54.39.157.64:80 | http://searchdusty.com/kevin.bmp | unknown | image | 768 Kb | unknown |
3668 | Antivirus.exe | GET | — | 54.39.157.64:80 | http://searchdusty.com/kevin.mp3 | unknown | — | — | unknown |
— | — | GET | 304 | 23.32.238.88:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?6d795d1723487b52 | unknown | — | — | unknown |
— | — | GET | 200 | 142.250.185.131:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
— | — | GET | 200 | 142.250.185.131:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFCjJ1PwkYAi7fE%3D | unknown | binary | 724 b | unknown |
3668 | Antivirus.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | unknown | binary | 1.47 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3668 | Antivirus.exe | 54.39.157.64:80 | searchdusty.com | OVH SAS | CA | unknown |
3668 | Antivirus.exe | 188.114.97.3:443 | computernewb.com | CLOUDFLARENET | NL | unknown |
3668 | Antivirus.exe | 23.32.238.88:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | whitelisted |
3668 | Antivirus.exe | 142.250.185.131:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
3668 | Antivirus.exe | 104.16.57.101:443 | static.cloudflareinsights.com | CLOUDFLARENET | — | unknown |
3668 | Antivirus.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
2244 | iexplore.exe | 188.114.97.3:443 | computernewb.com | CLOUDFLARENET | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
fastsofgeld.com |
| unknown |
searchdusty.com |
| whitelisted |
frequentwin.com |
| unknown |
highway-traffic.com |
| unknown |
computernewb.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
static.cloudflareinsights.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
api.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3668 | Antivirus.exe | Potentially Bad Traffic | ET USER_AGENTS User-Agent (Internet Explorer) |
3668 | Antivirus.exe | Potentially Bad Traffic | ET USER_AGENTS User-Agent (Internet Explorer) |
3668 | Antivirus.exe | Potentially Bad Traffic | ET USER_AGENTS User-Agent (Internet Explorer) |
3668 | Antivirus.exe | Potentially Bad Traffic | ET USER_AGENTS User-Agent (Internet Explorer) |
3668 | Antivirus.exe | Potentially Bad Traffic | ET USER_AGENTS User-Agent (Internet Explorer) |
3668 | Antivirus.exe | Potentially Bad Traffic | ET USER_AGENTS User-Agent (Internet Explorer) |
3668 | Antivirus.exe | Potentially Bad Traffic | ET USER_AGENTS User-Agent (Internet Explorer) |
3668 | Antivirus.exe | Potentially Bad Traffic | ET USER_AGENTS User-Agent (Internet Explorer) |
3668 | Antivirus.exe | Potentially Bad Traffic | ET USER_AGENTS User-Agent (Internet Explorer) |