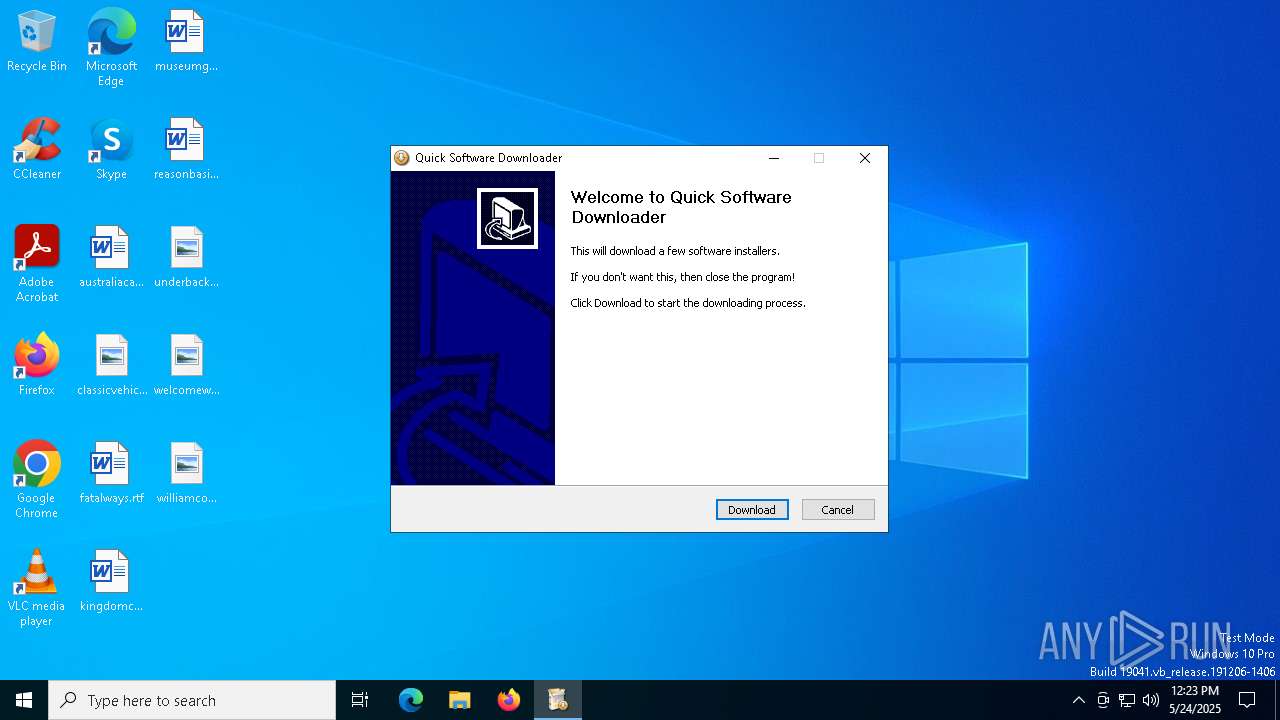
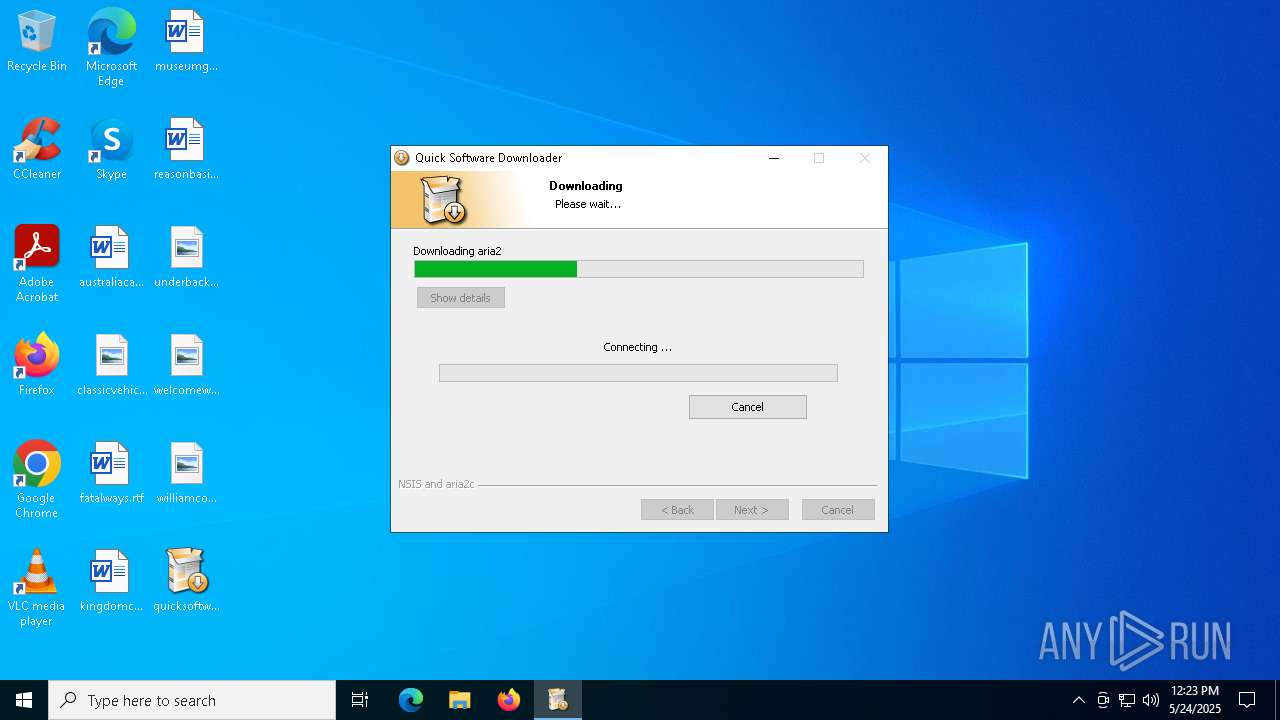
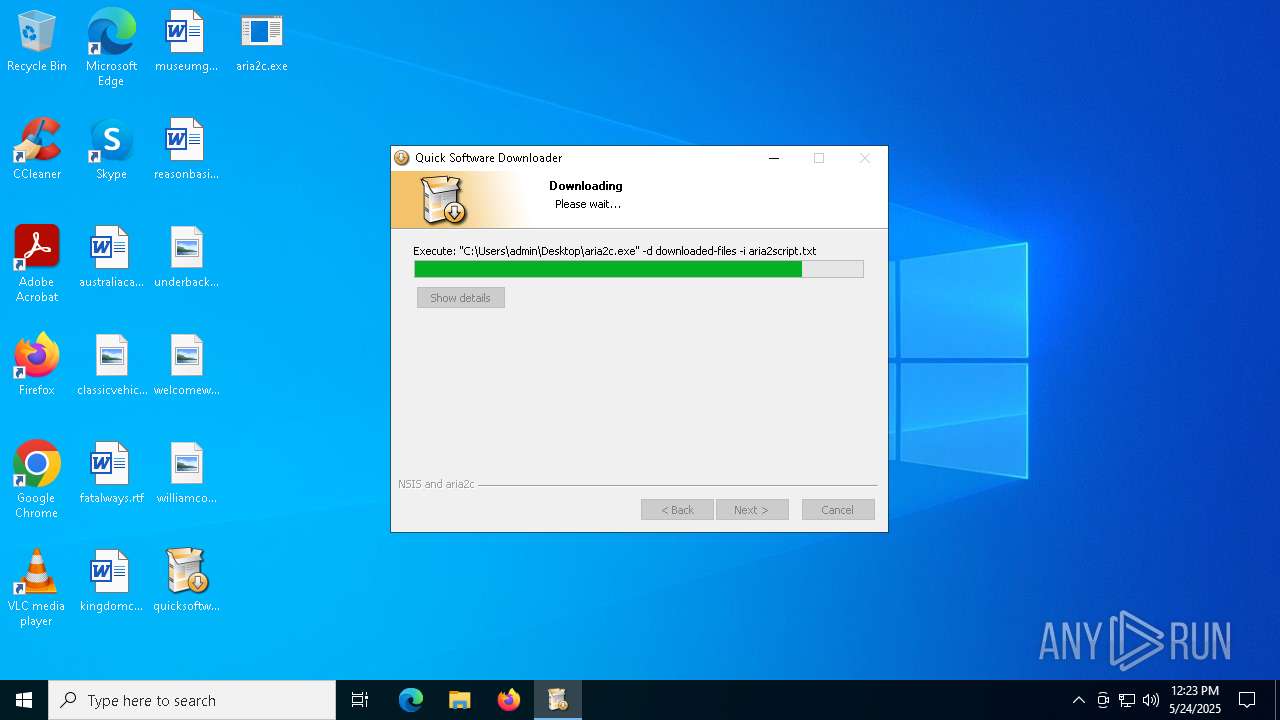
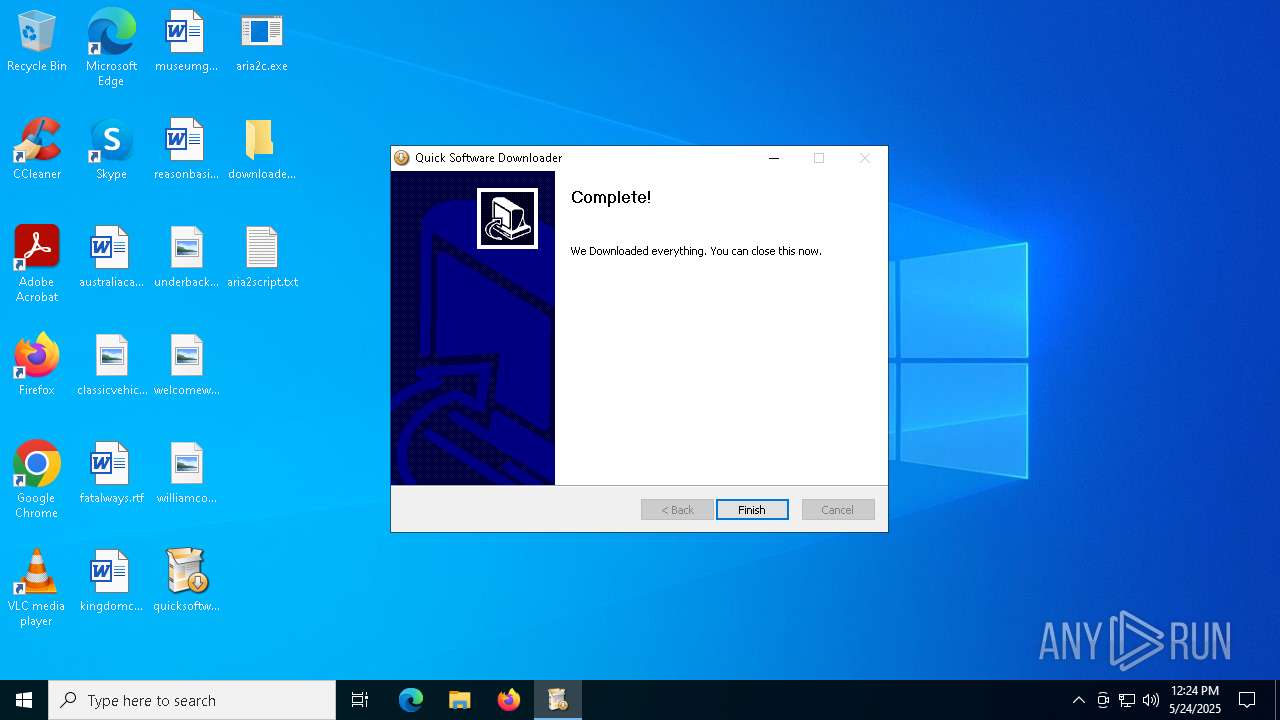
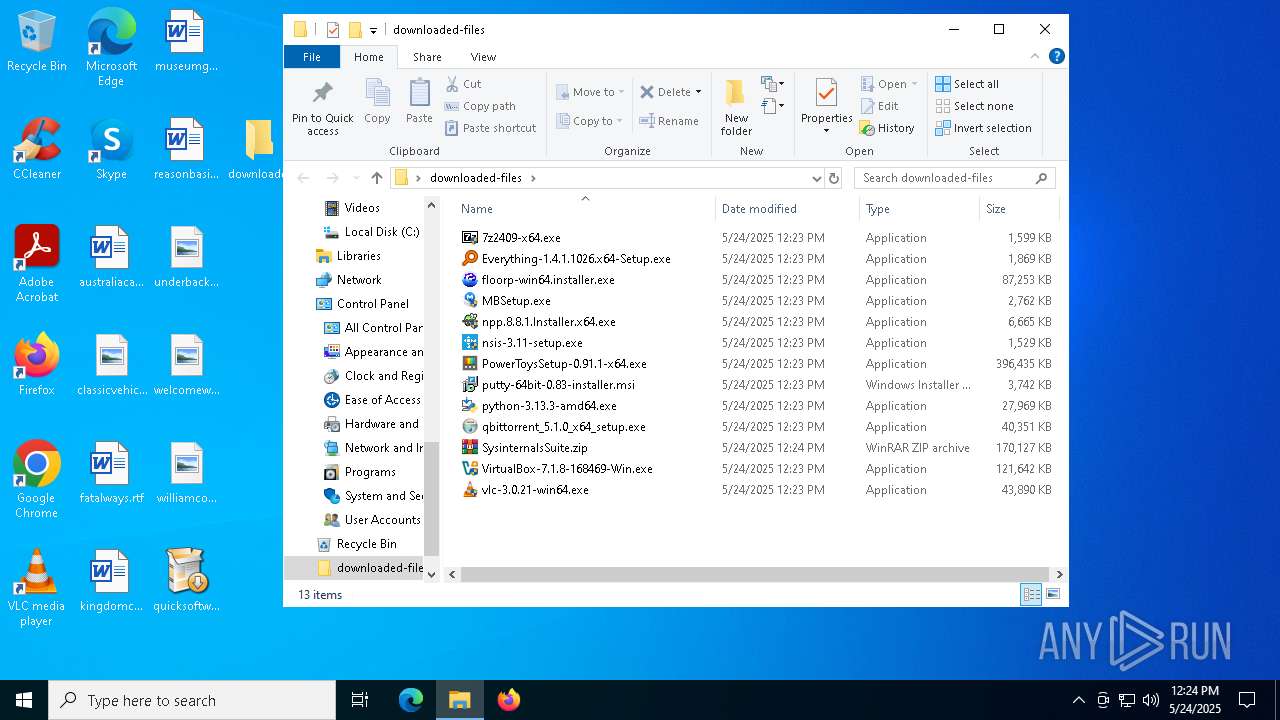
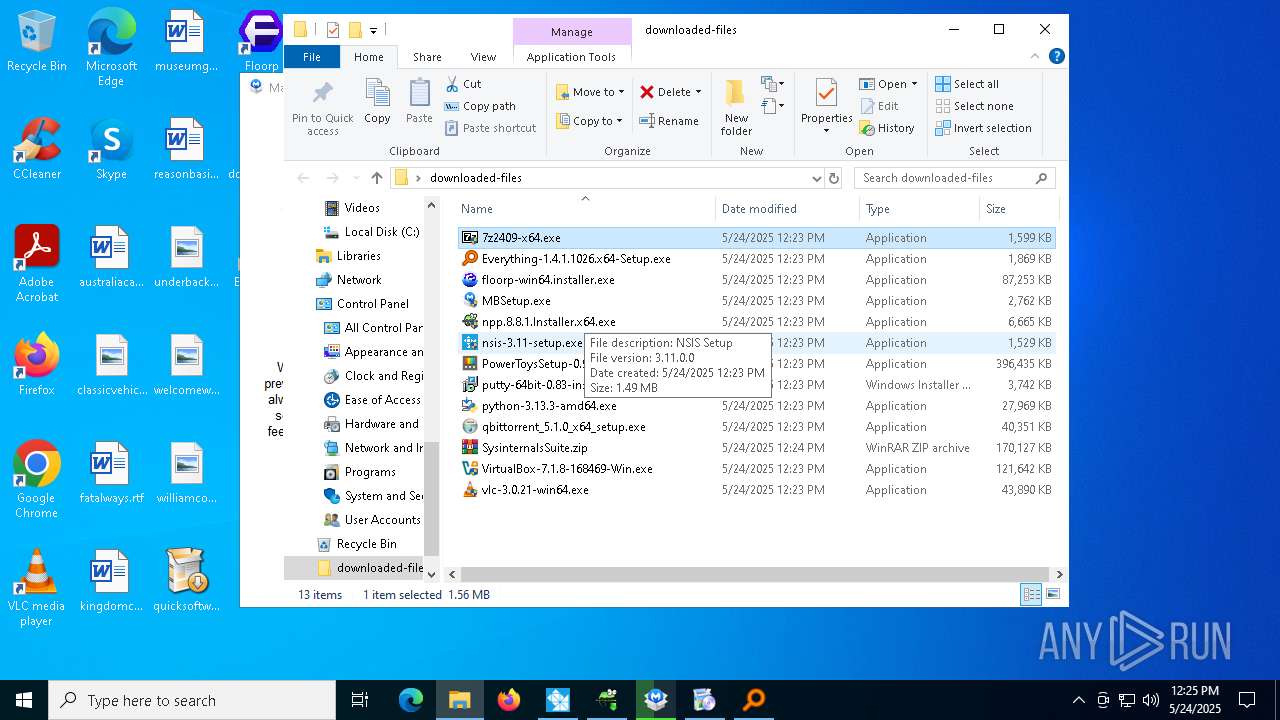
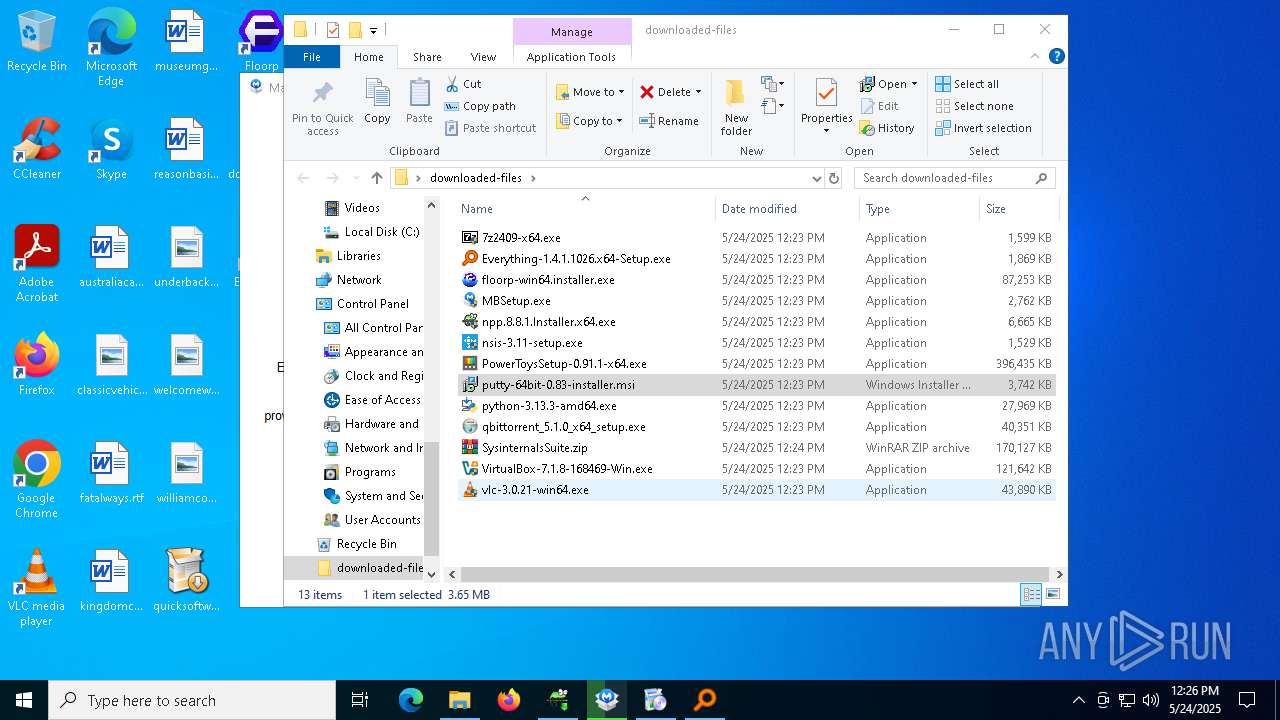
| File name: | quicksoftware-dl.exe |
| Full analysis: | https://app.any.run/tasks/de30250f-b0f7-414f-98b2-74216d8a97dc |
| Verdict: | Malicious activity |
| Analysis date: | May 24, 2025, 12:23:01 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | ADD26F07028D142EDB4EC2B018C9D62A |
| SHA1: | 76D903040626DB9DB94552A0FE880E3FA75E863E |
| SHA256: | B12DE74429CCE391832B921C1E60D797C9E629BE3949A7BF24DBF871AC60B1D7 |
| SSDEEP: | 3072:ylZMtTwu1DZN9VVF1VlVrabVFXzaVS4TgIz4O9m5DtXU:y/MtJN9VVF1VlVSTXzaVS4TgIz4iqDm |
MALICIOUS
Registers / Runs the DLL via REGSVR32.EXE
- npp.8.8.1.Installer.x64.exe (PID: 2692)
- setup.exe (PID: 2904)
SUSPICIOUS
Malware-specific behavior (creating "System.dll" in Temp)
- quicksoftware-dl.exe (PID: 4628)
- nsis-3.11-setup.exe (PID: 1300)
- npp.8.8.1.Installer.x64.exe (PID: 2692)
- setup.exe (PID: 2552)
- setup.exe (PID: 2904)
- Everything-1.4.1.1026.x64-Setup.exe (PID: 3868)
- nsis-3.11-setup.exe (PID: 3968)
- NSIS.exe (PID: 7152)
Reads security settings of Internet Explorer
- quicksoftware-dl.exe (PID: 4628)
- setup.exe (PID: 2552)
- setup.exe (PID: 2904)
The process creates files with name similar to system file names
- quicksoftware-dl.exe (PID: 4628)
- npp.8.8.1.Installer.x64.exe (PID: 2692)
- nsis-3.11-setup.exe (PID: 1300)
- setup.exe (PID: 2552)
- setup.exe (PID: 2904)
- MBAMInstallerService.exe (PID: 3036)
Executable content was dropped or overwritten
- quicksoftware-dl.exe (PID: 4628)
- aria2c.exe (PID: 1696)
- nsis-3.11-setup.exe (PID: 1300)
- npp.8.8.1.Installer.x64.exe (PID: 2692)
- MBSetup.exe (PID: 4448)
- floorp-win64.installer.exe (PID: 6344)
- MBAMInstallerService.exe (PID: 3036)
- setup.exe (PID: 2552)
- setup.exe (PID: 2904)
- Everything-1.4.1.1026.x64-Setup.exe (PID: 3868)
- everything.exe (PID: 5508)
- 7z2409-x64.exe (PID: 5172)
- nsis-3.11-setup.exe (PID: 3968)
- NSIS.exe (PID: 7152)
- PowerToysSetup-0.91.1-x64.exe (PID: 5176)
- PowerToysSetup-0.91.1-x64.exe (PID: 4180)
- PowerToysSetup-0.91.1-x64.exe (PID: 1228)
- MicrosoftEdgeWebview2Setup.exe (PID: 3272)
- VirtualBox-7.1.8-168469-Win.exe (PID: 208)
- MBVpnTunnelService.exe (PID: 6880)
- drvinst.exe (PID: 7020)
- MBAMService.exe (PID: 6708)
- drvinst.exe (PID: 8396)
- drvinst.exe (PID: 7628)
- MBAMService.exe (PID: 6816)
- drvinst.exe (PID: 7344)
- drvinst.exe (PID: 8336)
- drvinst.exe (PID: 8608)
- drvinst.exe (PID: 7372)
- drvinst.exe (PID: 7428)
There is functionality for taking screenshot (YARA)
- quicksoftware-dl.exe (PID: 4628)
- nsis-3.11-setup.exe (PID: 1300)
- npp.8.8.1.Installer.x64.exe (PID: 2692)
- setup.exe (PID: 2552)
- Everything-1.4.1.1026.x64-Setup.exe (PID: 3868)
- setup.exe (PID: 2904)
- Everything.exe (PID: 4700)
Starts CMD.EXE for commands execution
- quicksoftware-dl.exe (PID: 4628)
- PowerToysSetup-0.91.1-x64.exe (PID: 1228)
Drops 7-zip archiver for unpacking
- aria2c.exe (PID: 1696)
- MBAMInstallerService.exe (PID: 3036)
- 7z2409-x64.exe (PID: 5172)
Searches for installed software
- npp.8.8.1.Installer.x64.exe (PID: 2692)
- MBSetup.exe (PID: 4448)
- MBAMInstallerService.exe (PID: 3036)
Creates a software uninstall entry
- npp.8.8.1.Installer.x64.exe (PID: 2692)
- nsis-3.11-setup.exe (PID: 1300)
Creates/Modifies COM task schedule object
- regsvr32.exe (PID: 5736)
Reads the BIOS version
- MBSetup.exe (PID: 4448)
Creates files in the driver directory
- MBSetup.exe (PID: 4448)
The process verifies whether the antivirus software is installed
- MBSetup.exe (PID: 4448)
- MBAMInstallerService.exe (PID: 3036)
The process drops C-runtime libraries
- floorp-win64.installer.exe (PID: 6344)
- setup.exe (PID: 2904)
- MBAMInstallerService.exe (PID: 3036)
- MBAMService.exe (PID: 6708)
Process drops legitimate windows executable
- floorp-win64.installer.exe (PID: 6344)
- setup.exe (PID: 2904)
- MBAMInstallerService.exe (PID: 3036)
- PowerToysSetup-0.91.1-x64.exe (PID: 4180)
- PowerToysSetup-0.91.1-x64.exe (PID: 5176)
- PowerToysSetup-0.91.1-x64.exe (PID: 1228)
- MicrosoftEdgeWebview2Setup.exe (PID: 3272)
- MicrosoftEdgeUpdate.exe (PID: 7100)
- MBAMService.exe (PID: 6708)
Drops a system driver (possible attempt to evade defenses)
- MBAMInstallerService.exe (PID: 3036)
- MBVpnTunnelService.exe (PID: 6880)
- drvinst.exe (PID: 7020)
- MBAMService.exe (PID: 6816)
- msiexec.exe (PID: 684)
- MBAMService.exe (PID: 6708)
- drvinst.exe (PID: 8396)
- drvinst.exe (PID: 7628)
- drvinst.exe (PID: 7344)
- drvinst.exe (PID: 8336)
- msiexec.exe (PID: 6372)
- drvinst.exe (PID: 7428)
- drvinst.exe (PID: 8608)
- drvinst.exe (PID: 7372)
Application launched itself
- setup.exe (PID: 2552)
- floorp.exe (PID: 6148)
- floorp.exe (PID: 3760)
- everything.exe (PID: 4376)
- msiexec.exe (PID: 684)
- floorp.exe (PID: 2892)
- floorp.exe (PID: 512)
Executes as Windows Service
- Everything.exe (PID: 4700)
- MBAMInstallerService.exe (PID: 3036)
- VSSVC.exe (PID: 1812)
- MBAMService.exe (PID: 6708)
Starts itself from another location
- everything.exe (PID: 5508)
- PowerToysSetup-0.91.1-x64.exe (PID: 4180)
Starts a Microsoft application from unusual location
- PowerToysSetup-0.91.1-x64.exe (PID: 5176)
- PowerToysSetup-0.91.1-x64.exe (PID: 4180)
- PowerToysSetup-0.91.1-x64.exe (PID: 1228)
- MicrosoftEdgeUpdate.exe (PID: 7100)
Executing commands from ".cmd" file
- PowerToysSetup-0.91.1-x64.exe (PID: 1228)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 6592)
INFO
Checks supported languages
- quicksoftware-dl.exe (PID: 4628)
- aria2c.exe (PID: 1696)
- nsis-3.11-setup.exe (PID: 1300)
- npp.8.8.1.Installer.x64.exe (PID: 2692)
- MBSetup.exe (PID: 4448)
- MBAMInstallerService.exe (PID: 3036)
- floorp-win64.installer.exe (PID: 6344)
- setup.exe (PID: 2552)
- setup.exe (PID: 2904)
The sample compiled with english language support
- quicksoftware-dl.exe (PID: 4628)
- aria2c.exe (PID: 1696)
- nsis-3.11-setup.exe (PID: 1300)
- npp.8.8.1.Installer.x64.exe (PID: 2692)
- MBSetup.exe (PID: 4448)
- floorp-win64.installer.exe (PID: 6344)
- MBAMInstallerService.exe (PID: 3036)
- setup.exe (PID: 2904)
- everything.exe (PID: 5508)
- Everything-1.4.1.1026.x64-Setup.exe (PID: 3868)
- hh.exe (PID: 1568)
- PowerToysSetup-0.91.1-x64.exe (PID: 5176)
- PowerToysSetup-0.91.1-x64.exe (PID: 4180)
- PowerToysSetup-0.91.1-x64.exe (PID: 1228)
- MicrosoftEdgeWebview2Setup.exe (PID: 3272)
- MicrosoftEdgeUpdate.exe (PID: 7100)
- msiexec.exe (PID: 684)
- VirtualBox-7.1.8-168469-Win.exe (PID: 208)
- MBVpnTunnelService.exe (PID: 6880)
- drvinst.exe (PID: 7020)
- MBAMService.exe (PID: 6816)
- MBAMService.exe (PID: 6708)
- msiexec.exe (PID: 6372)
- drvinst.exe (PID: 8396)
- drvinst.exe (PID: 7628)
- drvinst.exe (PID: 7344)
- drvinst.exe (PID: 8336)
- drvinst.exe (PID: 8608)
- drvinst.exe (PID: 7372)
- 7z2409-x64.exe (PID: 5172)
- drvinst.exe (PID: 7428)
Reads the computer name
- quicksoftware-dl.exe (PID: 4628)
- aria2c.exe (PID: 1696)
- nsis-3.11-setup.exe (PID: 1300)
- npp.8.8.1.Installer.x64.exe (PID: 2692)
- MBSetup.exe (PID: 4448)
- MBAMInstallerService.exe (PID: 3036)
- floorp-win64.installer.exe (PID: 6344)
- setup.exe (PID: 2552)
- setup.exe (PID: 2904)
Checks proxy server information
- quicksoftware-dl.exe (PID: 4628)
- MBSetup.exe (PID: 4448)
Reads the machine GUID from the registry
- quicksoftware-dl.exe (PID: 4628)
- aria2c.exe (PID: 1696)
- MBSetup.exe (PID: 4448)
Creates files or folders in the user directory
- quicksoftware-dl.exe (PID: 4628)
- nsis-3.11-setup.exe (PID: 1300)
- npp.8.8.1.Installer.x64.exe (PID: 2692)
Create files in a temporary directory
- quicksoftware-dl.exe (PID: 4628)
- nsis-3.11-setup.exe (PID: 1300)
- MBSetup.exe (PID: 4448)
- npp.8.8.1.Installer.x64.exe (PID: 2692)
- setup.exe (PID: 2552)
- floorp-win64.installer.exe (PID: 6344)
- setup.exe (PID: 2904)
Reads the software policy settings
- quicksoftware-dl.exe (PID: 4628)
- slui.exe (PID: 5116)
- MBSetup.exe (PID: 4448)
- MBAMInstallerService.exe (PID: 3036)
Creates a new folder
- cmd.exe (PID: 4844)
Manual execution by a user
- nsis-3.11-setup.exe (PID: 5972)
- nsis-3.11-setup.exe (PID: 1300)
- npp.8.8.1.Installer.x64.exe (PID: 5504)
- npp.8.8.1.Installer.x64.exe (PID: 2692)
- MBSetup.exe (PID: 4376)
- MBSetup.exe (PID: 4448)
- floorp-win64.installer.exe (PID: 6344)
- Everything-1.4.1.1026.x64-Setup.exe (PID: 3868)
- 7z2409-x64.exe (PID: 1560)
- 7z2409-x64.exe (PID: 5172)
- nsis-3.11-setup.exe (PID: 3968)
- nsis-3.11-setup.exe (PID: 3012)
- PowerToysSetup-0.91.1-x64.exe (PID: 5176)
- msiexec.exe (PID: 6708)
- VirtualBox-7.1.8-168469-Win.exe (PID: 2560)
- VirtualBox-7.1.8-168469-Win.exe (PID: 208)
Creates files in the program directory
- nsis-3.11-setup.exe (PID: 1300)
- npp.8.8.1.Installer.x64.exe (PID: 2692)
- MBSetup.exe (PID: 4448)
- MBAMInstallerService.exe (PID: 3036)
- setup.exe (PID: 2904)
Process checks whether UAC notifications are on
- setup.exe (PID: 2552)
Process checks computer location settings
- setup.exe (PID: 2552)
The sample compiled with spanish language support
- MBAMInstallerService.exe (PID: 3036)
Manages system restore points
- SrTasks.exe (PID: 540)
- SrTasks.exe (PID: 840)
- SrTasks.exe (PID: 8160)
Executable content was dropped or overwritten
- msiexec.exe (PID: 6708)
- msiexec.exe (PID: 684)
- msiexec.exe (PID: 6372)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:03:08 23:05:20+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 27136 |
| InitializedDataSize: | 184832 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x358d |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
282
Monitored processes
130
Malicious processes
14
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 208 | "C:\Users\admin\Desktop\downloaded-files\VirtualBox-7.1.8-168469-Win.exe" | C:\Users\admin\Desktop\downloaded-files\VirtualBox-7.1.8-168469-Win.exe | explorer.exe | |
User: admin Company: Oracle and/or its affiliates Integrity Level: HIGH Description: VirtualBox Installer Version: 7.1.8.168469 | ||||
| 512 | "C:\Program Files\Ablaze Floorp\floorp.exe" -first-startup | C:\Program Files\Ablaze Floorp\floorp.exe | floorp.exe | |
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Floorp Exit code: 0 Version: 128.11.0 | ||||
| 540 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | dllhost.exe |
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft® Windows System Protection background tasks. Exit code: 2147942487 Version: 10.0.19041.1 (WinBuild.160101.0800) | ||||
| 684 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | |
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) | ||||
| 776 | C:\Windows\syswow64\MsiExec.exe -Embedding F1BE0055C721514935BA20BC896F5F98 M Global\MSI0000 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe |
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) | ||||
| 840 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:12 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe |
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | ||||
| 1184 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | ||||
| 1228 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | aria2c.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | ||||
| 1228 | "C:\Program Files\Everything\Everything.exe" -disable-update-notification -uninstall-quick-launch-shortcut -no-choose-volumes -language 1033 | C:\Program Files\Everything\Everything.exe | — | Everything-1.4.1.1026.x64-Setup.exe |
User: admin Company: voidtools Integrity Level: MEDIUM Description: Everything Exit code: 0 Version: 1.4.1.1026 | ||||
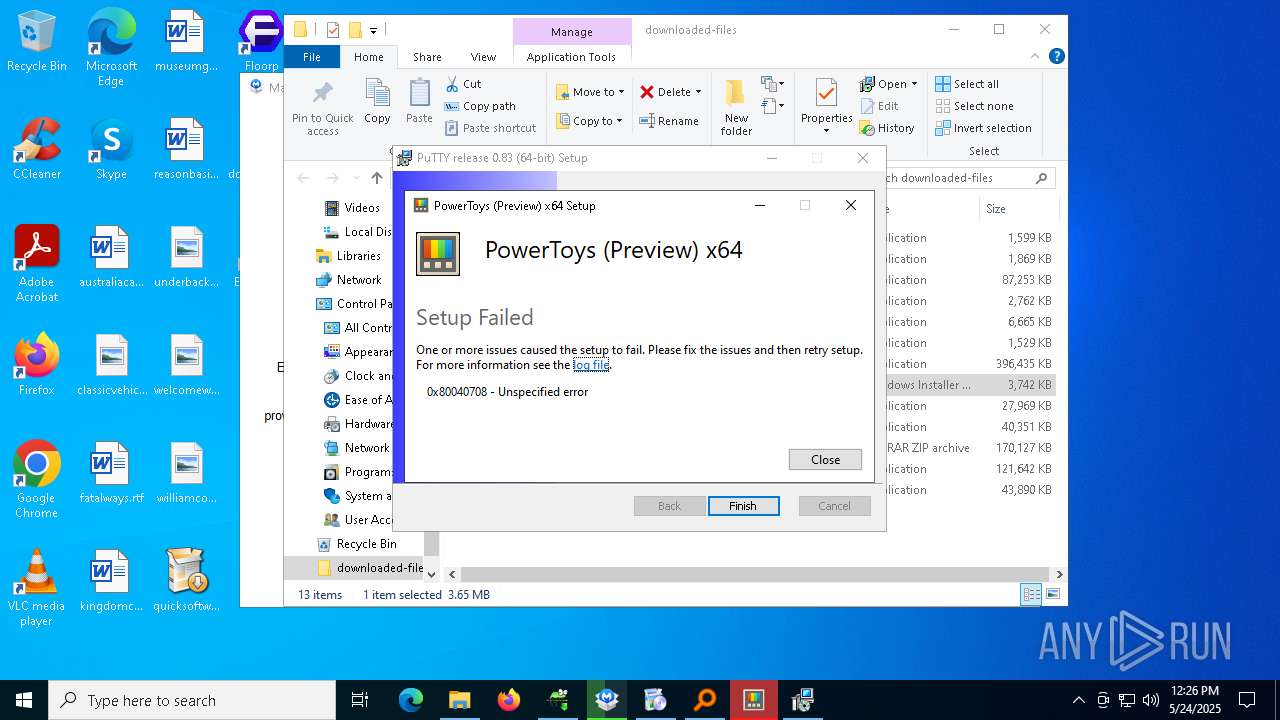
| 1228 | "C:\Users\admin\AppData\Local\Temp\{29E6096F-97DB-4959-BD69-E279302ACA62}\.be\PowerToysSetup-0.91.1-x64.exe" -q -burn.elevated BurnPipe.{542B1980-416A-499E-943F-48FEA839D396} {60148399-FB13-41A0-B376-2ACC09AF8AA0} 4180 | C:\Users\admin\AppData\Local\Temp\{29E6096F-97DB-4959-BD69-E279302ACA62}\.be\PowerToysSetup-0.91.1-x64.exe | PowerToysSetup-0.91.1-x64.exe | |
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: PowerToys (Preview) x64 Exit code: 1800 Version: 0.91.1 | ||||
Total events
0
Read events
0
Write events
0
Delete events
0
Modification events
Executable files
1 829
Suspicious files
881
Text files
933
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4628 | quicksoftware-dl.exe | C:\Users\admin\AppData\Local\Temp\nsoA655.tmp\modern-wizard.bmp | image | |
MD5:CBE40FD2B1EC96DAEDC65DA172D90022 | SHA256:3AD2DC318056D0A2024AF1804EA741146CFC18CC404649A44610CBF8B2056CF2 | |||
| 4628 | quicksoftware-dl.exe | C:\Users\admin\AppData\Local\Temp\nsoA655.tmp\INetC.dll | executable | |
MD5:40D7ECA32B2F4D29DB98715DD45BFAC5 | SHA256:85E03805F90F72257DD41BFDAA186237218BBB0EC410AD3B6576A88EA11DCCB9 | |||
| 4628 | quicksoftware-dl.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CE7B026C819922EDB9B7ED78605E20A3_731147EC87359F0E7CBB8FC748CE2C9A | binary | |
MD5:8843F1AE49584247BE4128757E5E5500 | SHA256:903F16DAFC8BCDA73B59E9328A3C2FFE4DD350543D847ED50E2EE4B8BF6526CE | |||
| 4628 | quicksoftware-dl.exe | C:\Users\admin\AppData\Local\Temp\nsoA655.tmp\modern-header.bmp | image | |
MD5:583C38FB0F5AF5FE584D9A9B01D6A3E7 | SHA256:4C9E804CE1A391F8E603B7B9C732A6529C1E81BE4D12F125C8562EA9D49095C2 | |||
| 4628 | quicksoftware-dl.exe | C:\Users\admin\AppData\Local\Temp\nsoA655.tmp\System.dll | executable | |
MD5:9B38A1B07A0EBC5C7E59E63346ECC2DB | SHA256:C881253DAFCF1322A771139B1A429EC1E78C507CA81A218A20DC1A4B25ABBFE7 | |||
| 4628 | quicksoftware-dl.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CE7B026C819922EDB9B7ED78605E20A3_731147EC87359F0E7CBB8FC748CE2C9A | binary | |
MD5:C1EE51398687C0DFF82034211587B60A | SHA256:F59CE236F8A5010BB66F4791B768B55D28C1644AE3EEF778E864103E77ACAC38 | |||
| 4628 | quicksoftware-dl.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\KCV3KQBA\urllist[1].txt | text | |
MD5:F71E3833F698C3C62409469692A5446B | SHA256:CFC2233ED169E5BEA2B1D9F04538F24B602B8ECC9016896300A6D5D5C59C7627 | |||
| 4628 | quicksoftware-dl.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\54C62B182F5BF07FA8427C07B0A3AAF8_786EA6C36BF7ABFF201B638497282D19 | binary | |
MD5:2EAA0859782ED877B89881411A4D2CA1 | SHA256:A2F3DFD9E9644901A5807E03AF713A1FCE517D79B2170CA1C4048302E15A3326 | |||
| 4628 | quicksoftware-dl.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\54C62B182F5BF07FA8427C07B0A3AAF8_786EA6C36BF7ABFF201B638497282D19 | binary | |
MD5:2C4D15B99429A495319CDEF89BB38A1D | SHA256:FD2ED1BD4303C246D3514830353F38D24E450F865CB0C41647F7BE80702CEB1E | |||
| 1696 | aria2c.exe | C:\Users\admin\Desktop\downloaded-files\qbittorrent_5.1.0_x64_setup.exe.aria2__temp | binary | |
MD5:D0C2C66F63A39745F3F0E0EADA9B65EC | SHA256:A87902653E08AAF32FABC4FB8EDF073329337A20C7D89814E7C95F1034842255 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
73
TCP/UDP connections
196
DNS requests
226
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
756 | lsass.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTPlNxcMEqnlIVyH5VuZ4lawhZX3QQU9oUKOxGG4QR9DqoLLNLuzGR7e64CEQCrZoa1YnvoBZaCEzAShkn1 | unknown | — | — | whitelisted |
756 | lsass.exe | GET | 200 | 18.66.147.114:80 | http://e6.c.lencr.org/46.crl | unknown | — | — | whitelisted |
756 | lsass.exe | GET | 200 | 2.23.197.184:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
756 | lsass.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | unknown | — | — | whitelisted |
756 | lsass.exe | GET | 200 | 204.79.197.203:80 | http://oneocsp.microsoft.com/ocsp/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSzT%2FzqwcqNvhP9i4c4sCPz2JbzrAQU%2FglxQFUFEETYpIF1uJ4a6UoGiMgCEzMCGJMA9BYEJXFQUDQAAAIYkwA%3D | unknown | — | — | whitelisted |
756 | lsass.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | unknown | — | — | whitelisted |
756 | lsass.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5796 | svchost.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
864 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
5796 | svchost.exe | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
5796 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4628 | quicksoftware-dl.exe | 139.84.173.225:443 | files.webdevtest.ftp.sh | AS-CHOOPA | US | unknown |
4628 | quicksoftware-dl.exe | 18.173.205.113:80 | ocsps.ssl.com | — | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
files.webdevtest.ftp.sh |
| unknown |
ocsps.ssl.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
7-zip.org |
| unknown |
github.com |
| whitelisted |
netcologne.dl.sourceforge.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a *.ftp .sh Domain |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |