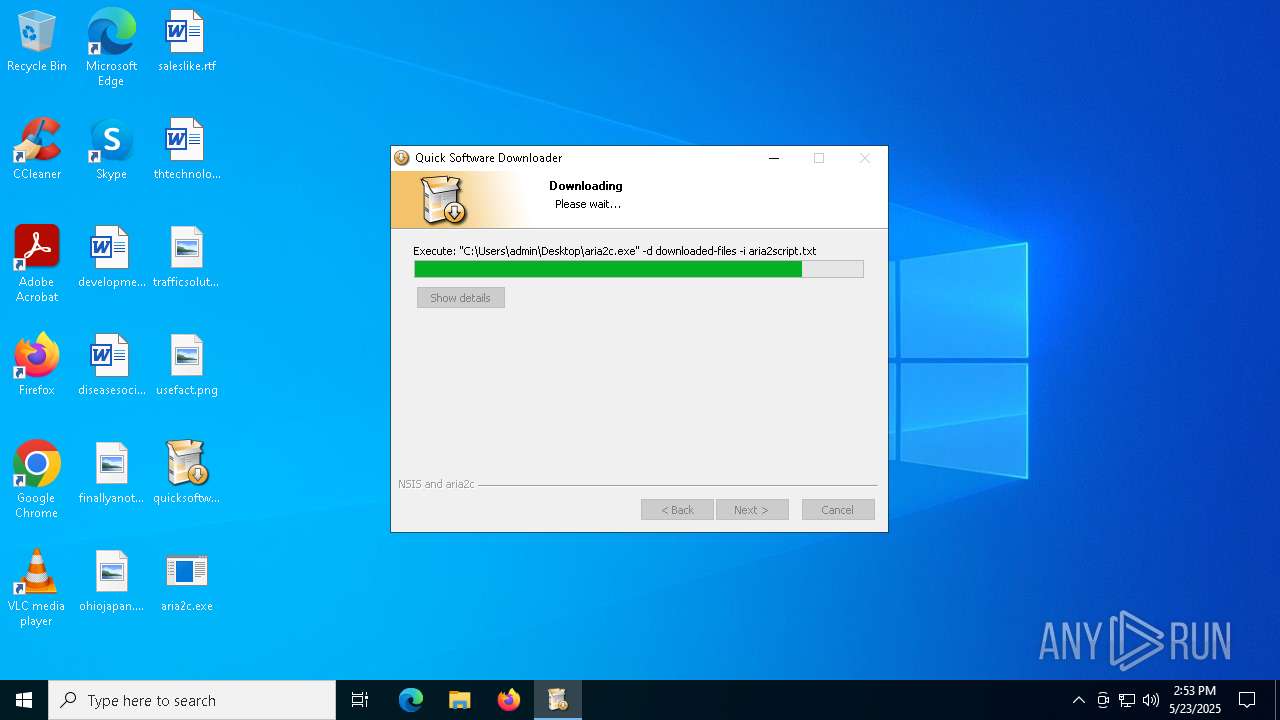
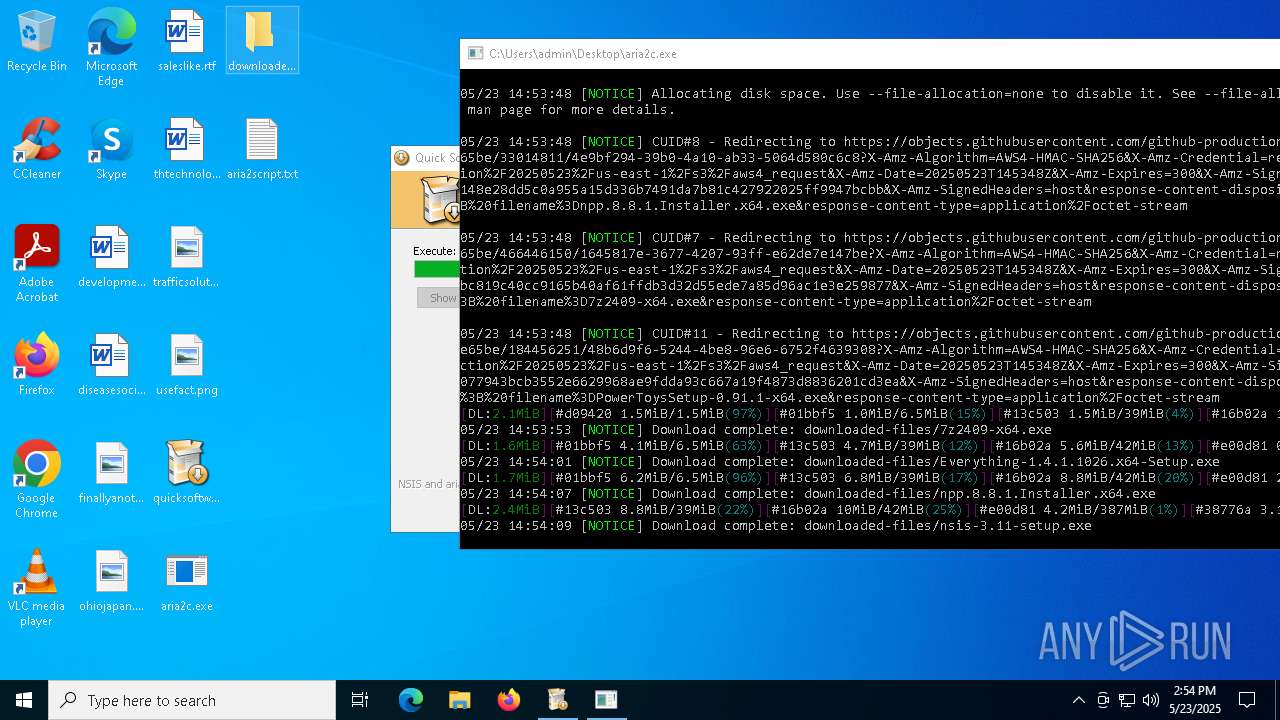
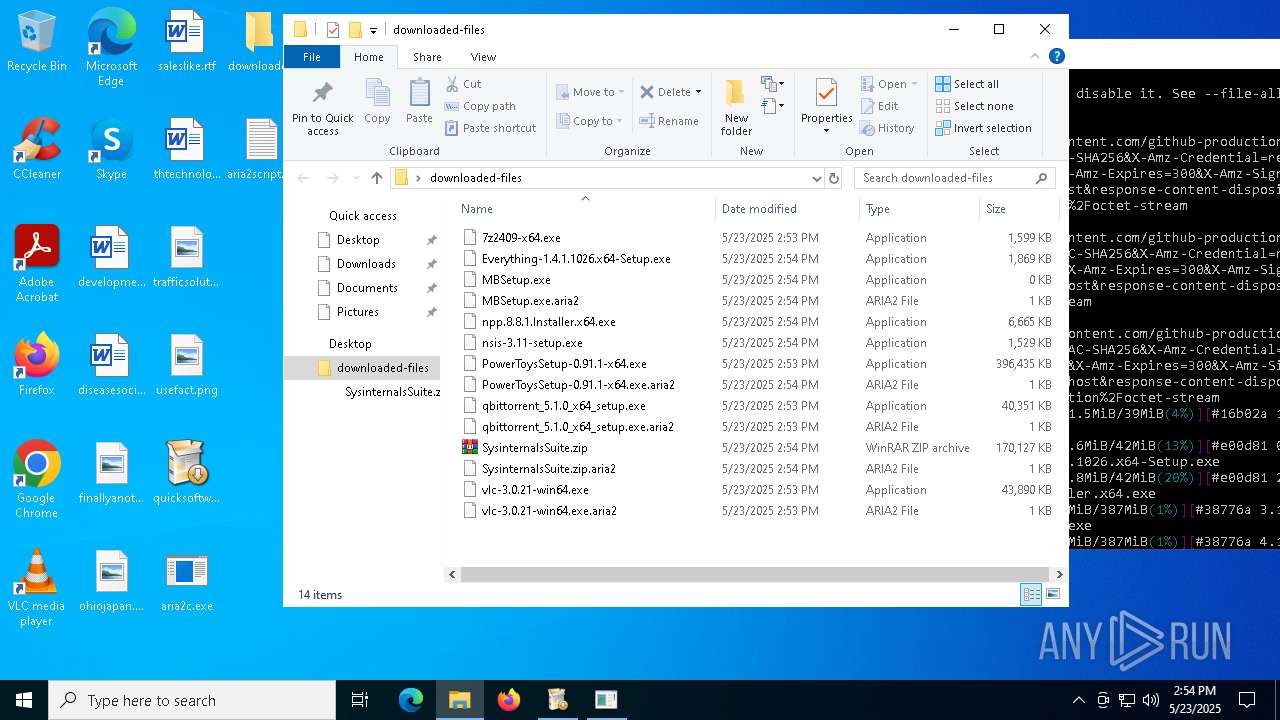
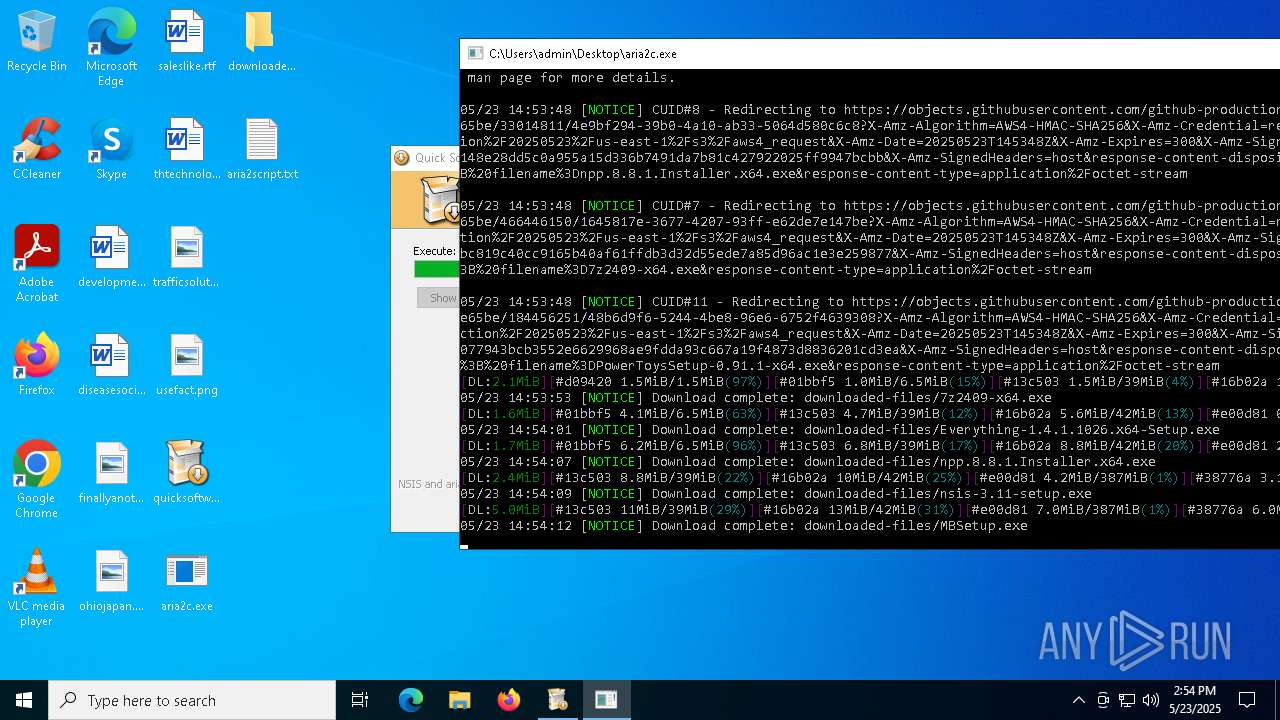
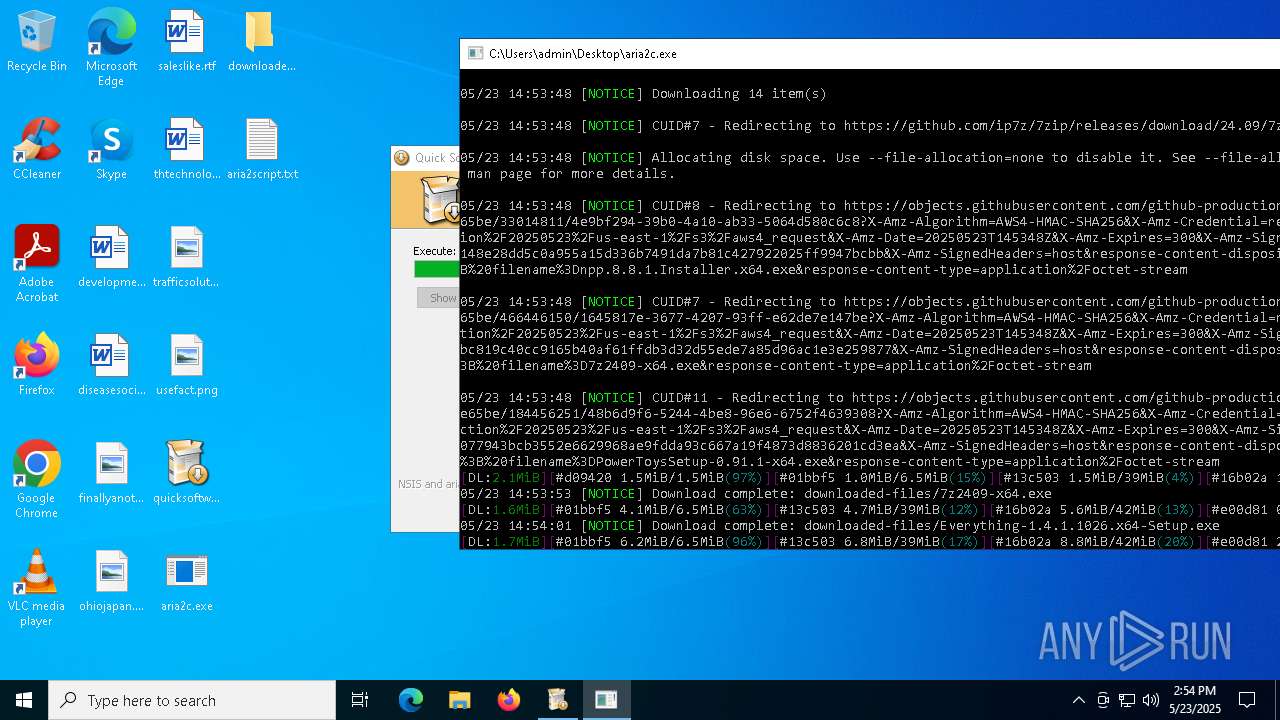
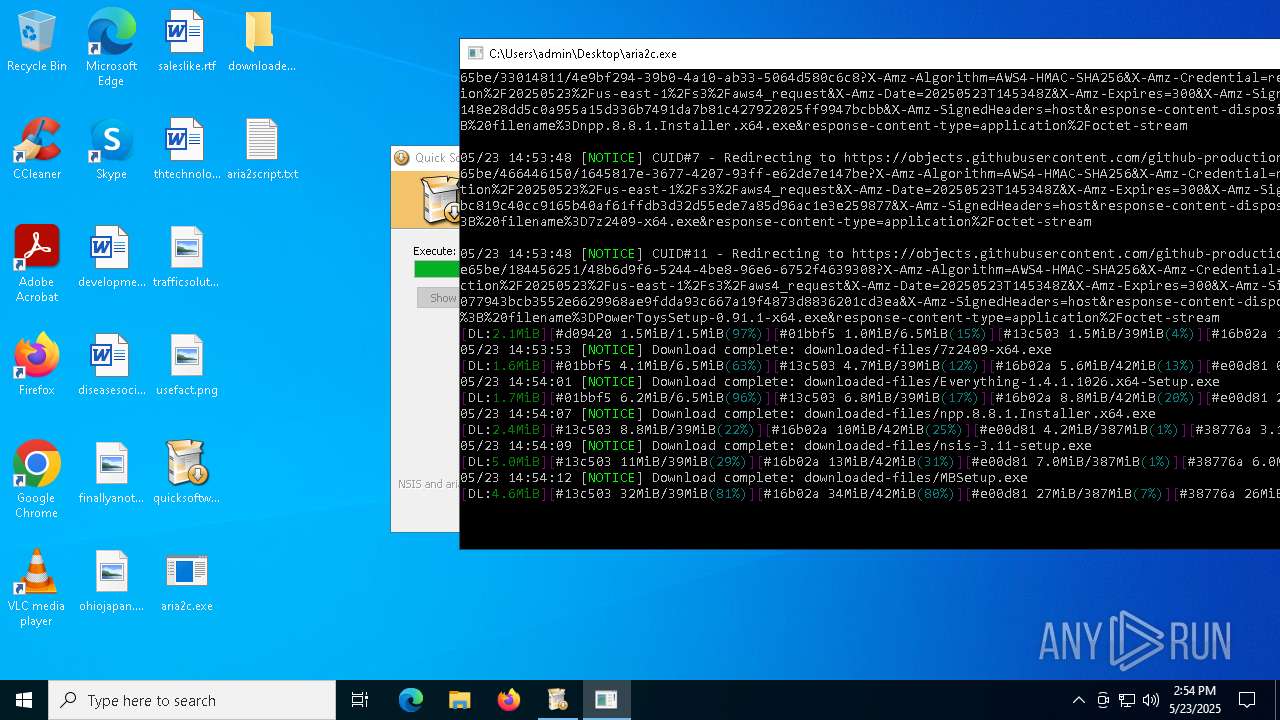
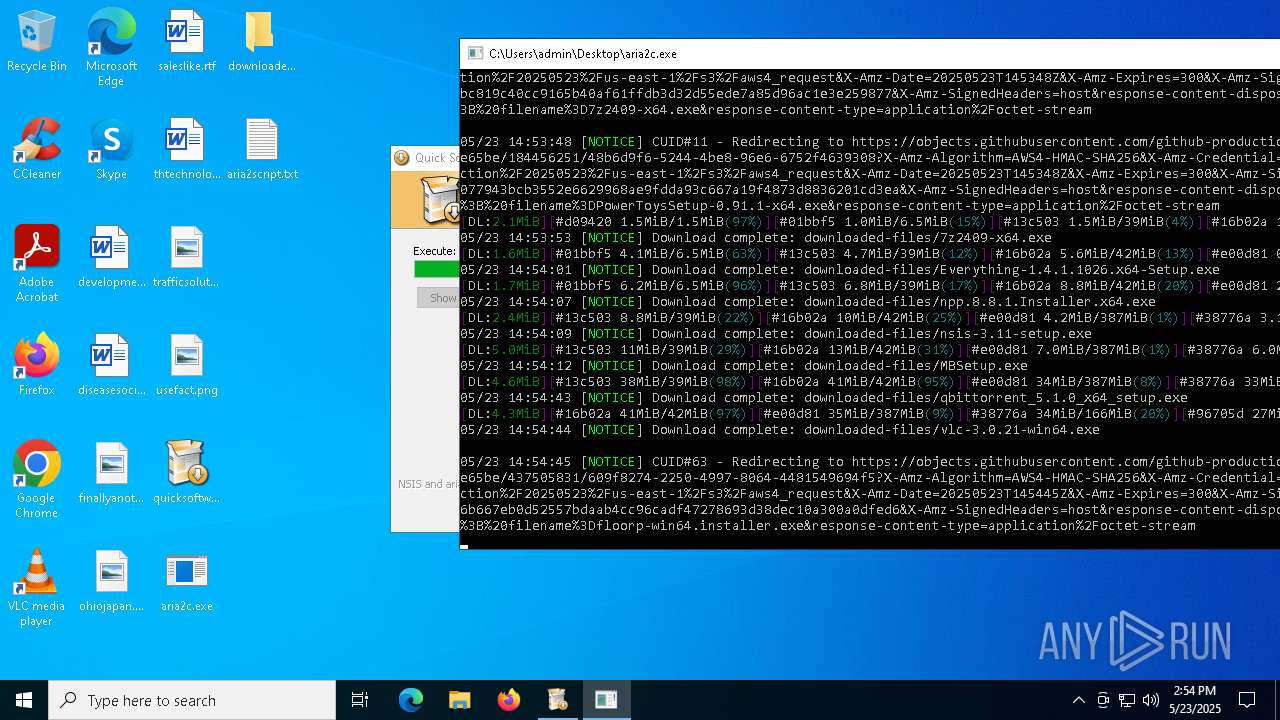
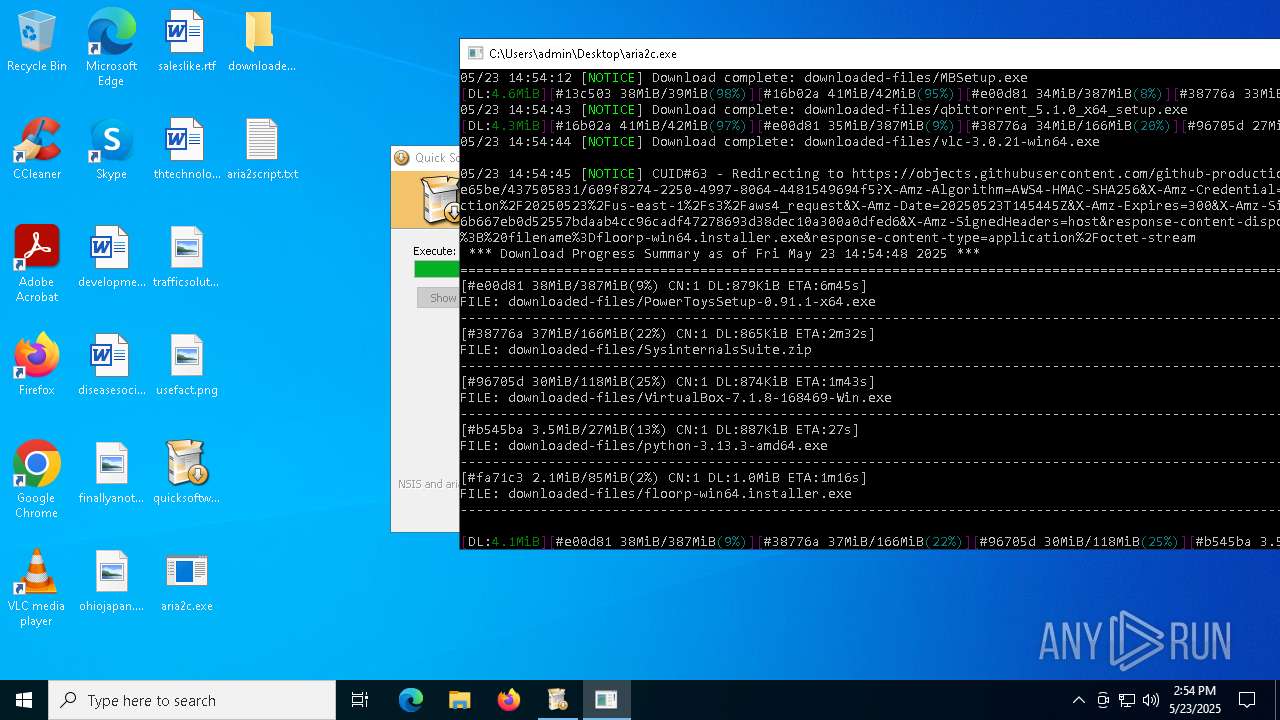
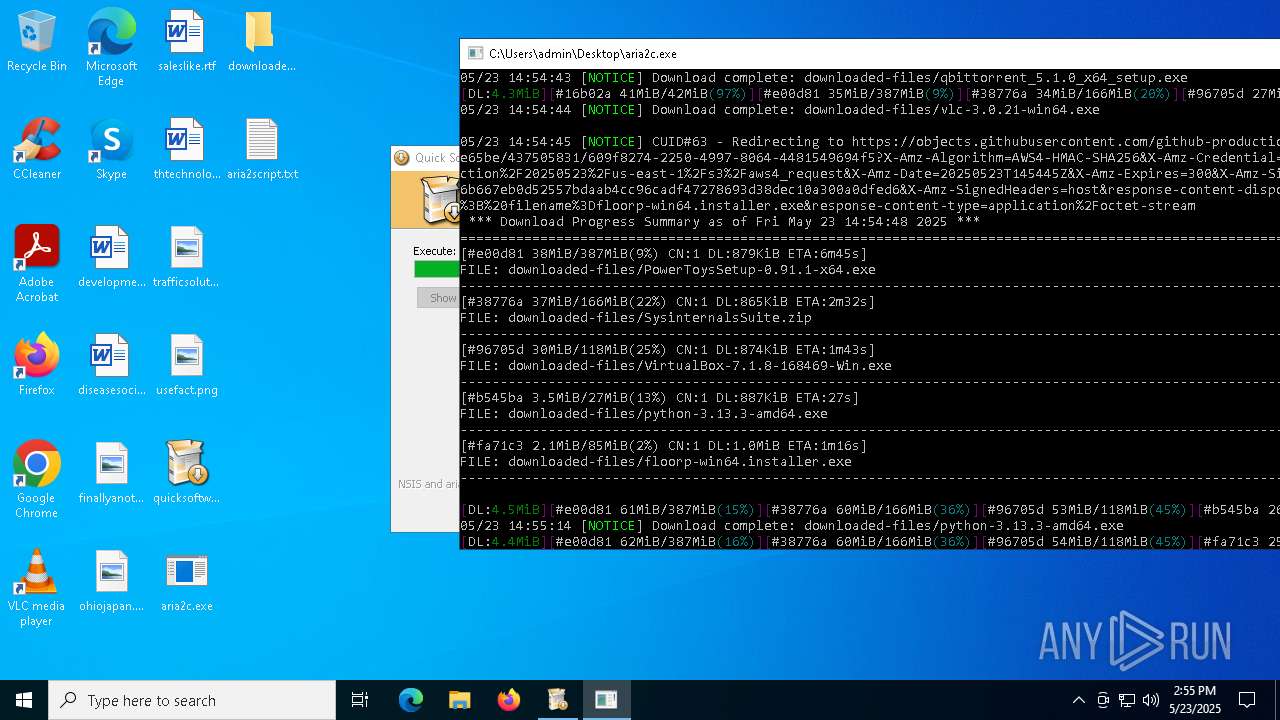
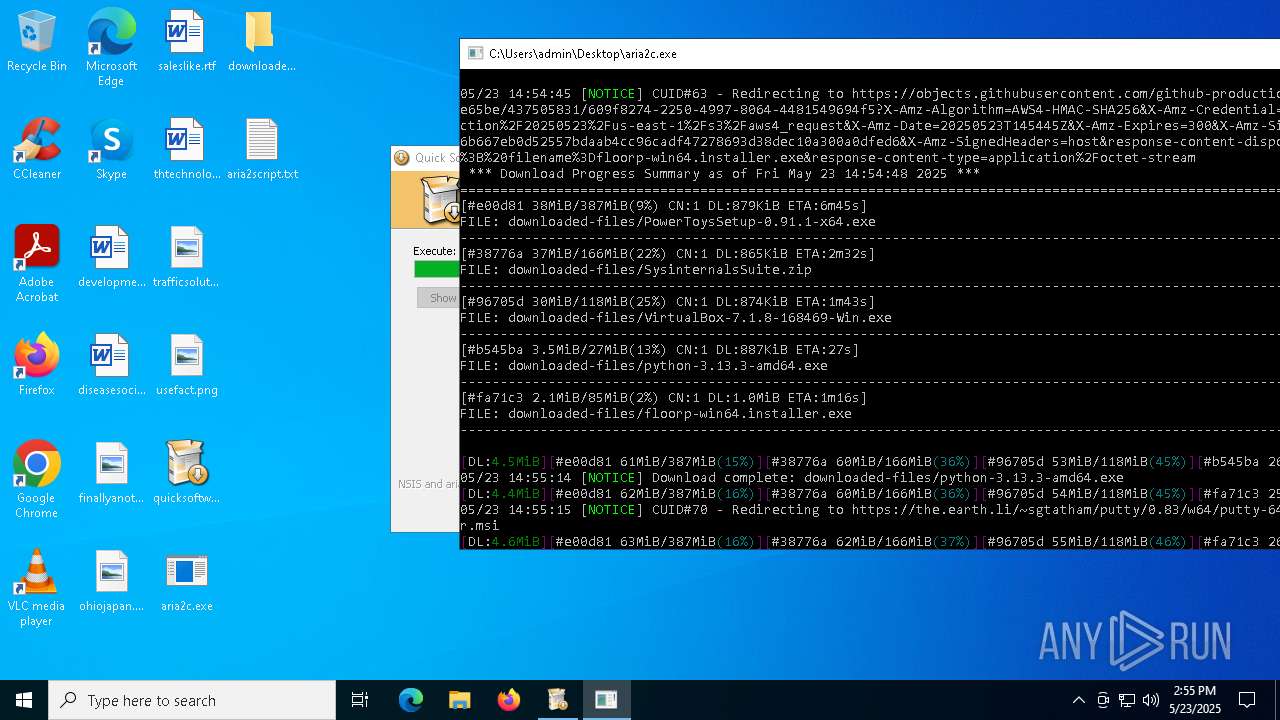
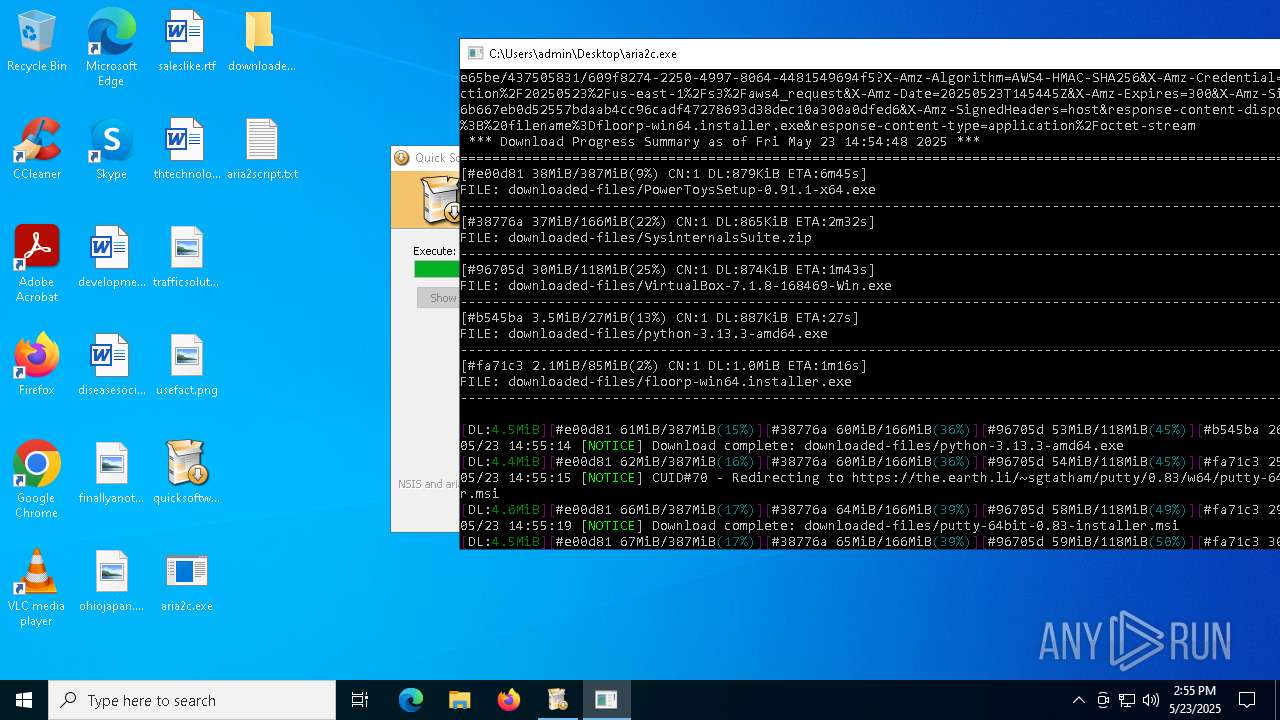
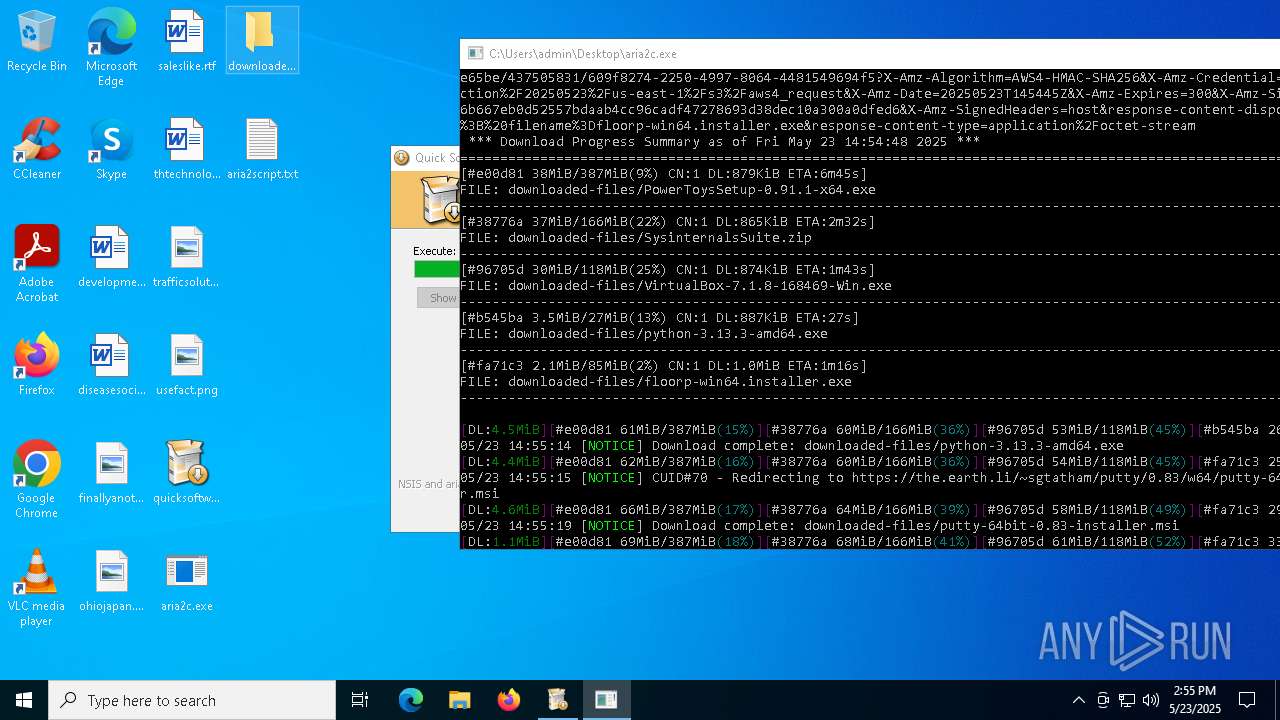
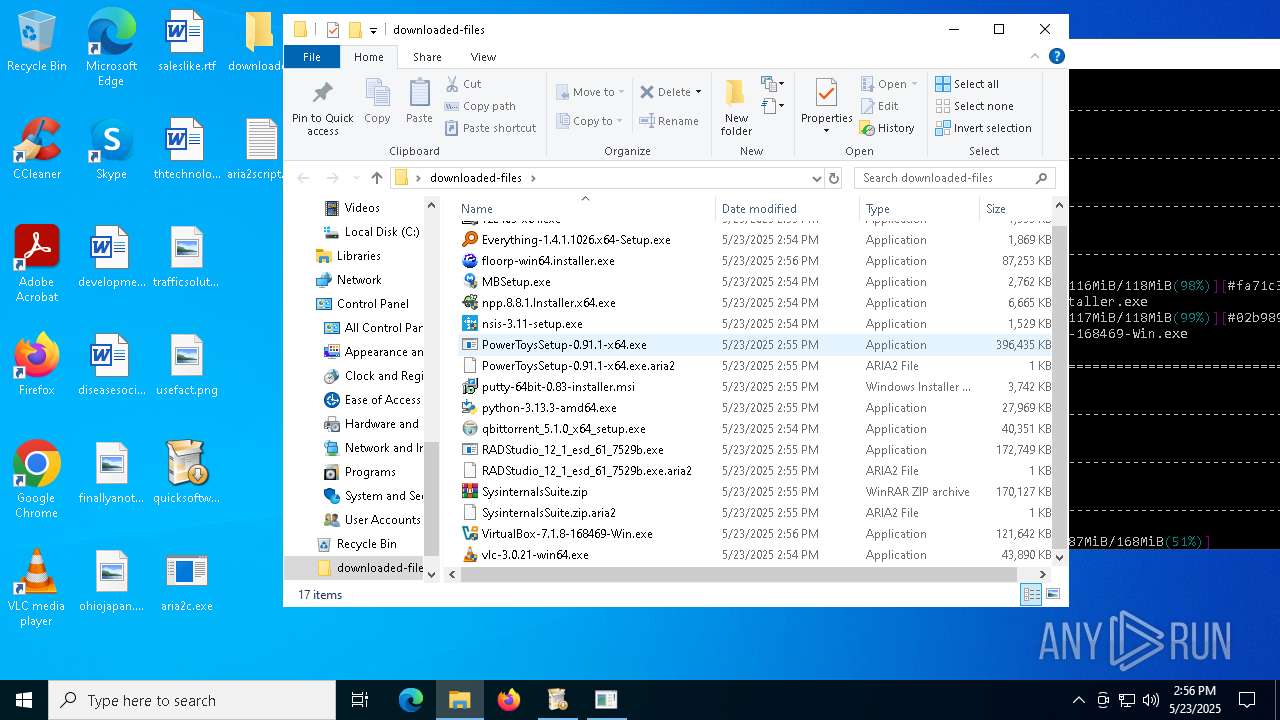
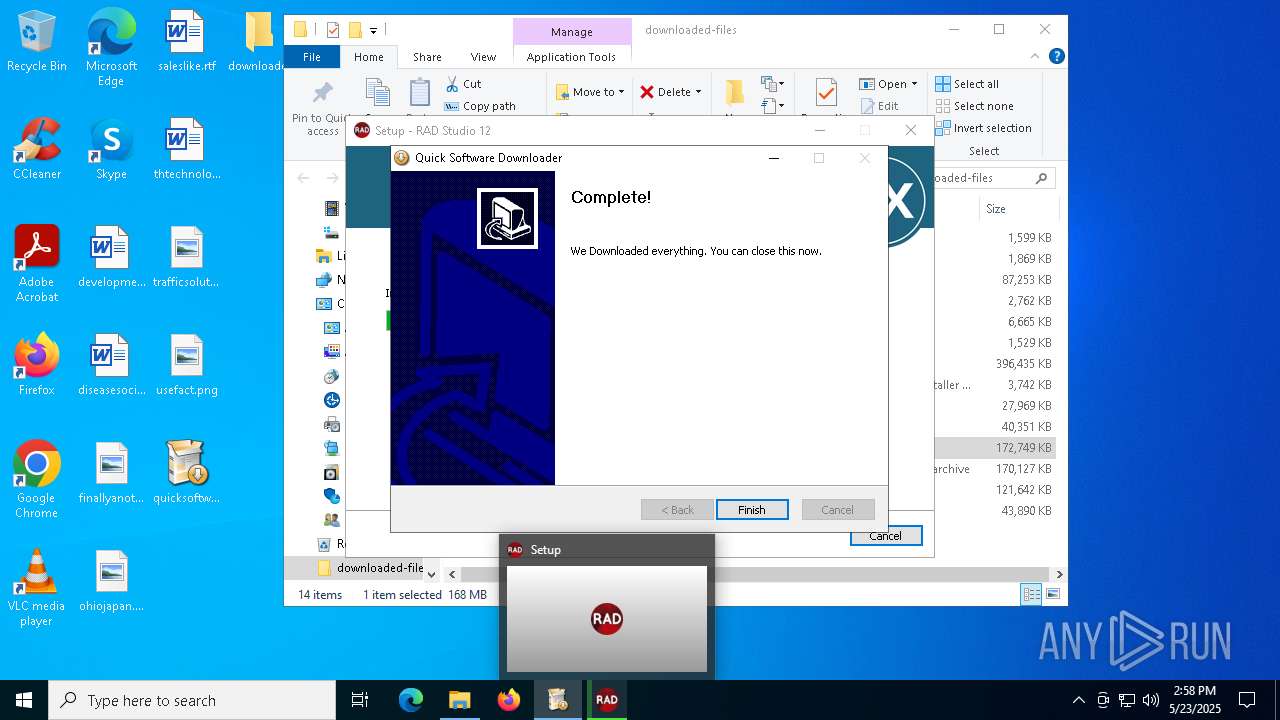
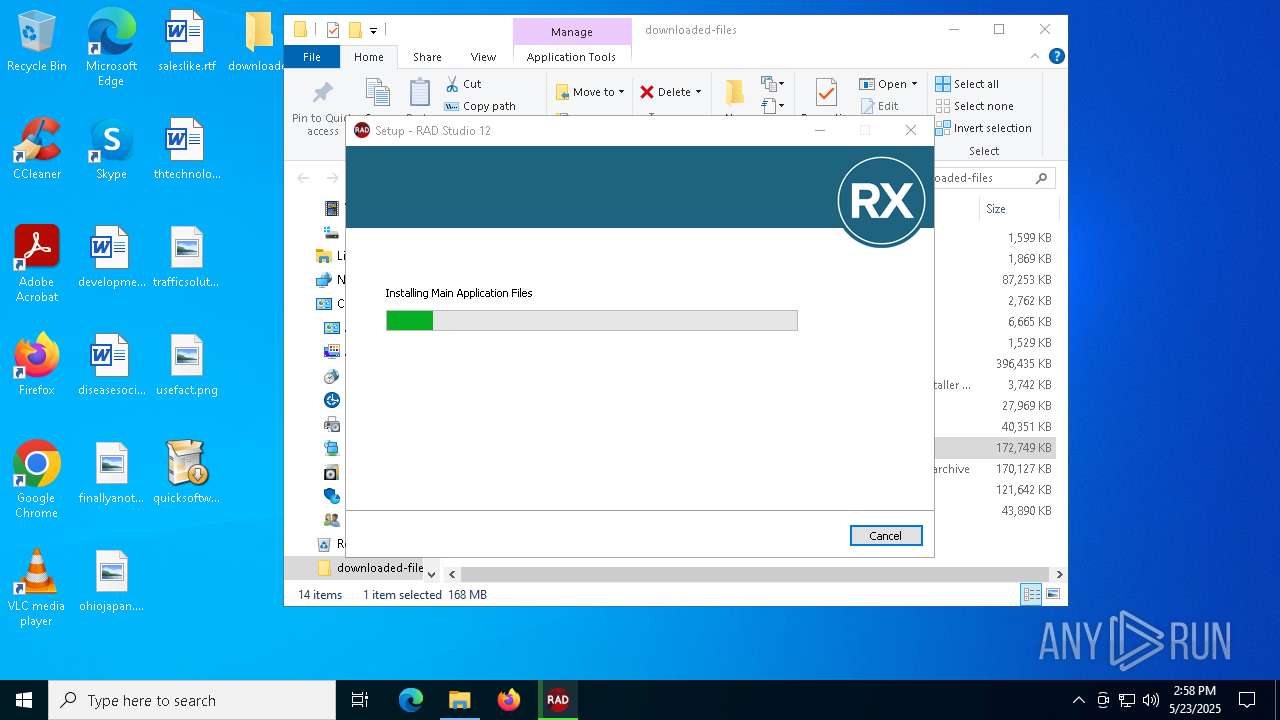
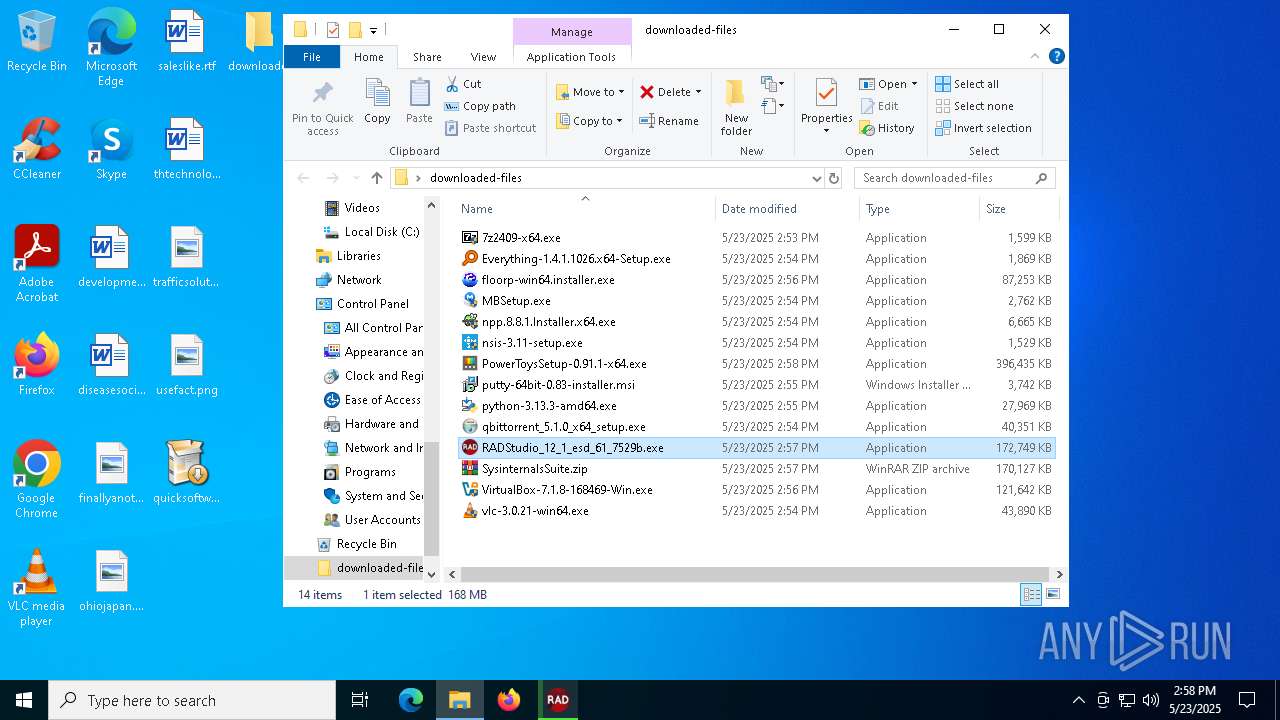
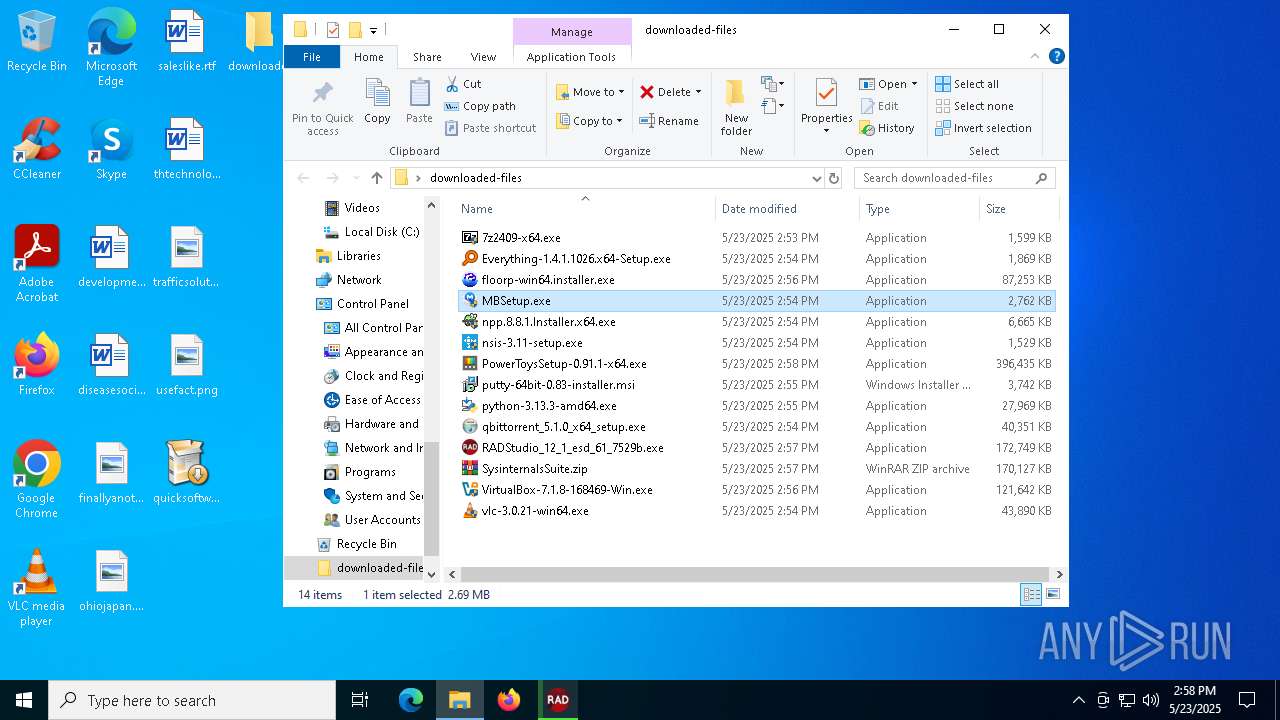
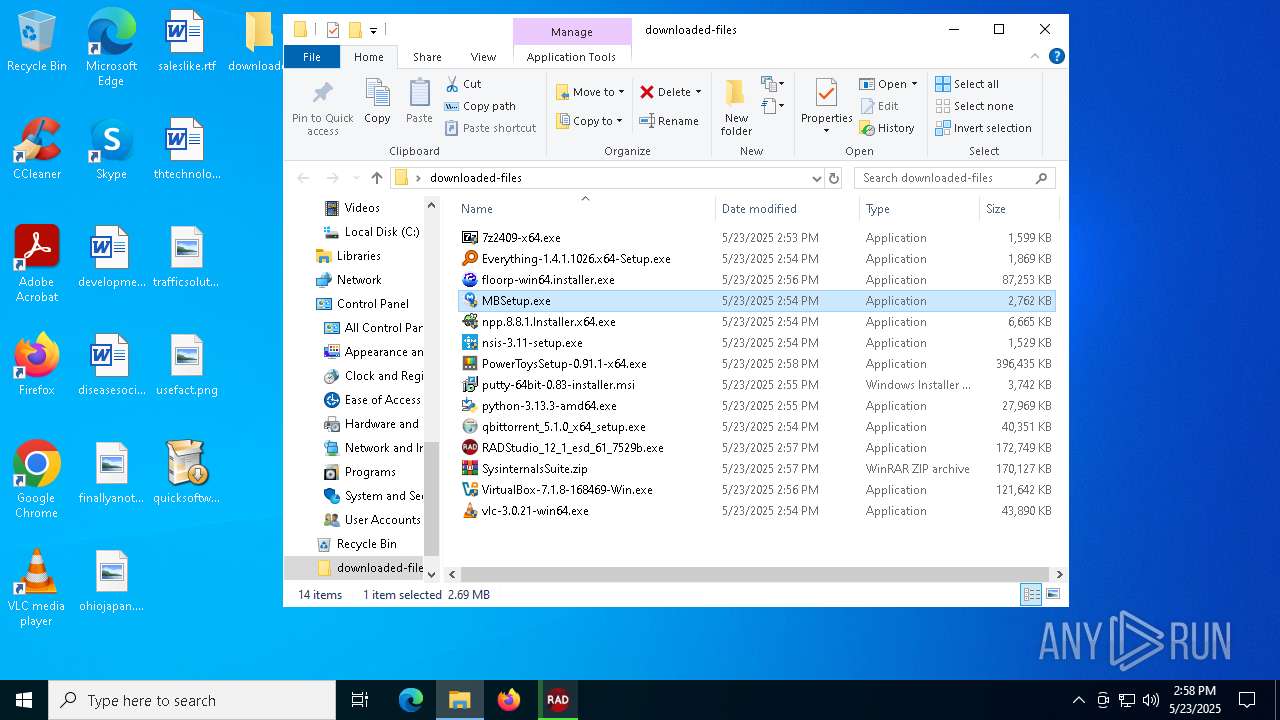
| File name: | quicksoftware-dl.exe |
| Full analysis: | https://app.any.run/tasks/3adb0cca-dc10-4faa-8ade-16943080de24 |
| Verdict: | Malicious activity |
| Analysis date: | May 23, 2025, 14:53:26 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | ADD26F07028D142EDB4EC2B018C9D62A |
| SHA1: | 76D903040626DB9DB94552A0FE880E3FA75E863E |
| SHA256: | B12DE74429CCE391832B921C1E60D797C9E629BE3949A7BF24DBF871AC60B1D7 |
| SSDEEP: | 3072:ylZMtTwu1DZN9VVF1VlVrabVFXzaVS4TgIz4O9m5DtXU:y/MtJN9VVF1VlVSTXzaVS4TgIz4iqDm |
MALICIOUS
Executing a file with an untrusted certificate
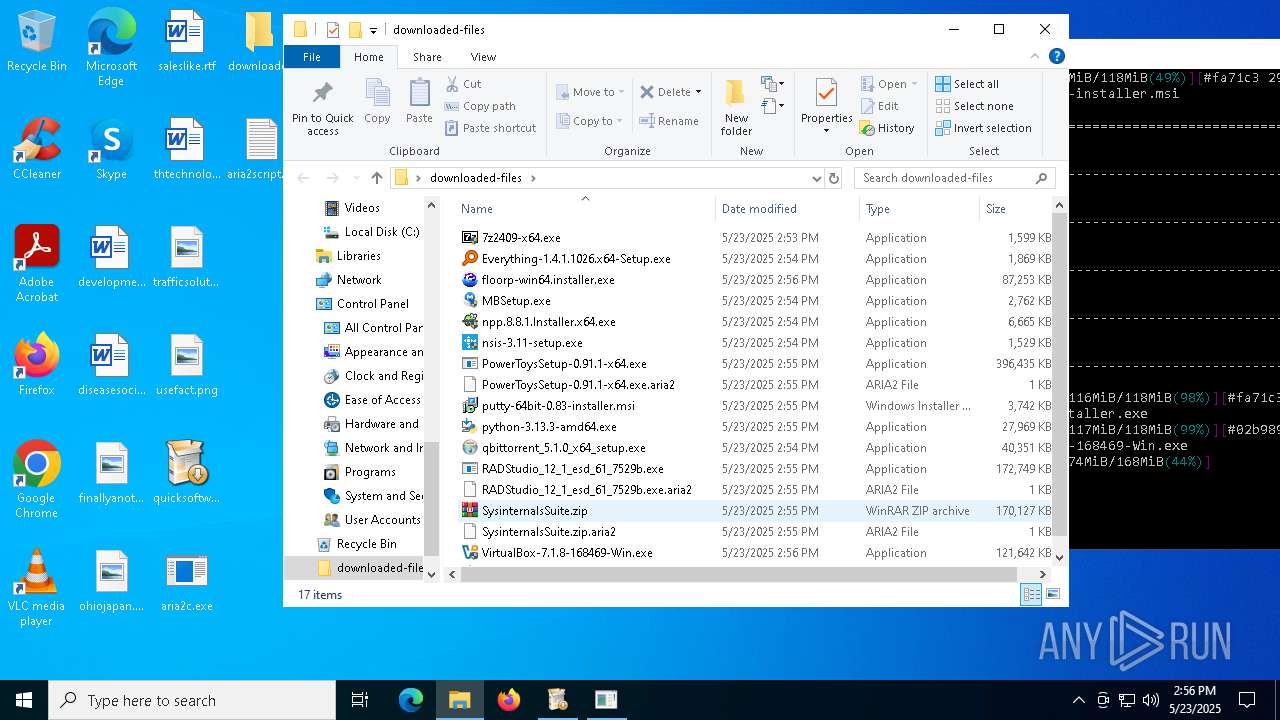
- RADStudio_12_1_esd_61_7529b.exe (PID: 1748)
- RADStudio_12_1_esd_61_7529b.exe (PID: 6620)
- LicenseManager.exe (PID: 6728)
SUSPICIOUS
Malware-specific behavior (creating "System.dll" in Temp)
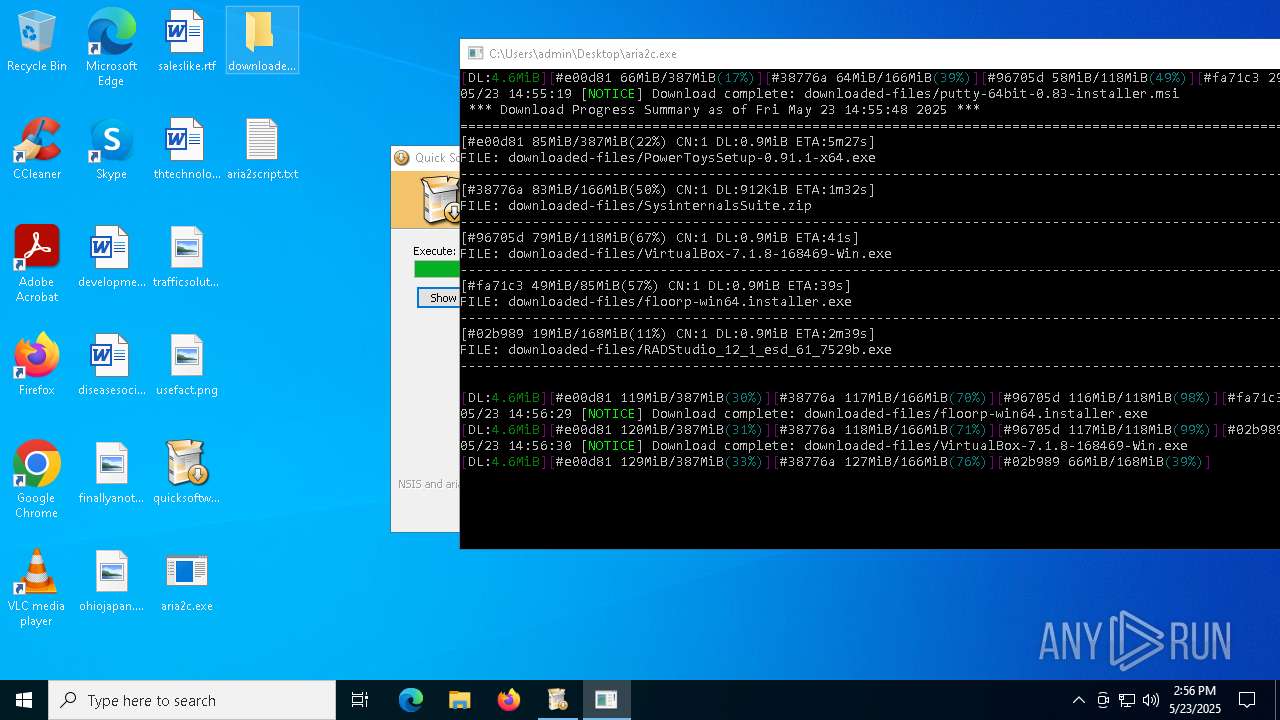
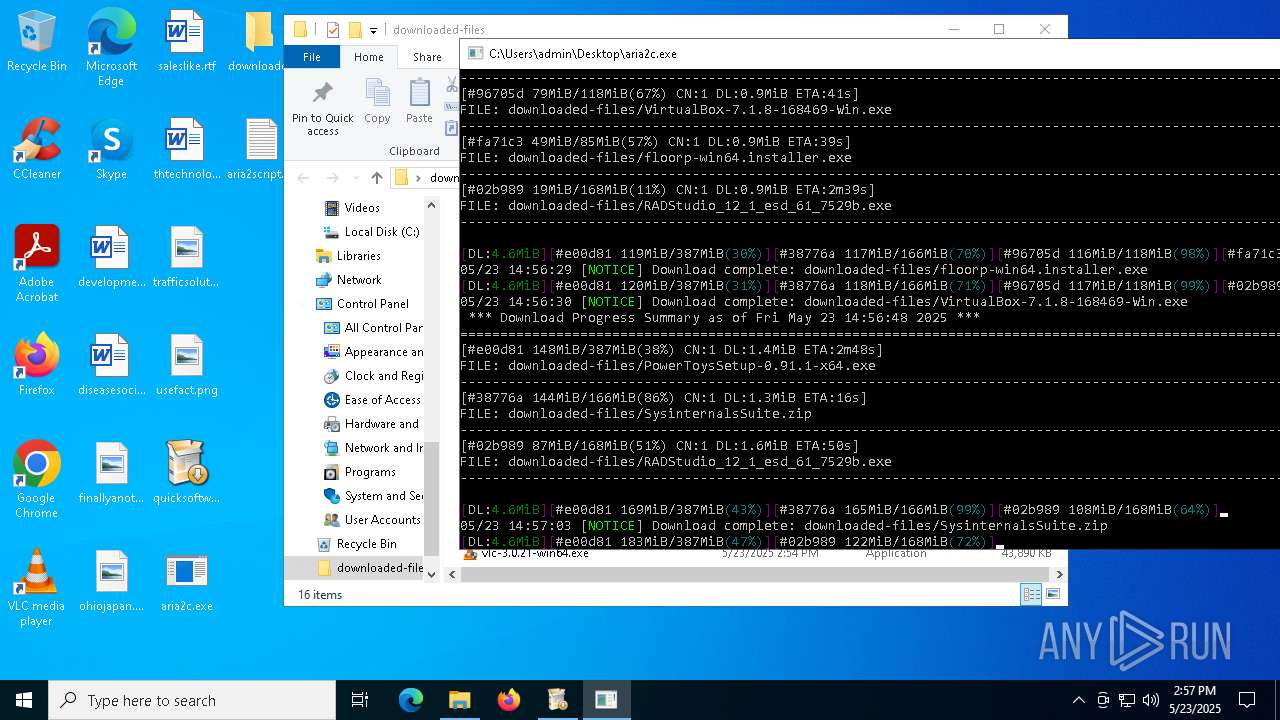
- quicksoftware-dl.exe (PID: 4244)
The process creates files with name similar to system file names
- quicksoftware-dl.exe (PID: 4244)
Executable content was dropped or overwritten
- quicksoftware-dl.exe (PID: 4244)
- aria2c.exe (PID: 3180)
- RADStudio_12_1_esd_61_7529b.tmp (PID: 2800)
- RADStudio_12_1_esd_61_7529b.exe (PID: 6620)
- RADStudio_12_1_esd_61_7529b.exe (PID: 1748)
- MBSetup.exe (PID: 3800)
Drops 7-zip archiver for unpacking
- aria2c.exe (PID: 3180)
Reads security settings of Internet Explorer
- quicksoftware-dl.exe (PID: 4244)
- RADStudio_12_1_esd_61_7529b.tmp (PID: 2332)
- RADStudio_12_1_esd_61_7529b.tmp (PID: 2800)
There is functionality for taking screenshot (YARA)
- quicksoftware-dl.exe (PID: 4244)
Starts CMD.EXE for commands execution
- quicksoftware-dl.exe (PID: 4244)
Reads the Windows owner or organization settings
- RADStudio_12_1_esd_61_7529b.tmp (PID: 2800)
Reads the BIOS version
- MBSetup.exe (PID: 3800)
Searches for installed software
- MBSetup.exe (PID: 3800)
- MBAMInstallerService.exe (PID: 6744)
Creates files in the driver directory
- MBSetup.exe (PID: 3800)
Executes as Windows Service
- MBAMInstallerService.exe (PID: 6744)
The process verifies whether the antivirus software is installed
- MBSetup.exe (PID: 3800)
- MBAMInstallerService.exe (PID: 6744)
INFO
Checks proxy server information
- quicksoftware-dl.exe (PID: 4244)
- slui.exe (PID: 1012)
- LicenseManager.exe (PID: 6728)
- MBSetup.exe (PID: 3800)
The sample compiled with english language support
- quicksoftware-dl.exe (PID: 4244)
- aria2c.exe (PID: 3180)
- RADStudio_12_1_esd_61_7529b.tmp (PID: 2800)
- MBSetup.exe (PID: 3800)
Reads the computer name
- quicksoftware-dl.exe (PID: 4244)
- aria2c.exe (PID: 3180)
- RADStudio_12_1_esd_61_7529b.tmp (PID: 2332)
- RADStudio_12_1_esd_61_7529b.tmp (PID: 2800)
- LicenseManager.exe (PID: 6728)
- MBSetup.exe (PID: 3800)
- MBAMInstallerService.exe (PID: 6744)
Create files in a temporary directory
- quicksoftware-dl.exe (PID: 4244)
- RADStudio_12_1_esd_61_7529b.exe (PID: 1748)
- RADStudio_12_1_esd_61_7529b.exe (PID: 6620)
- RADStudio_12_1_esd_61_7529b.tmp (PID: 2800)
- MBSetup.exe (PID: 3800)
Checks supported languages
- quicksoftware-dl.exe (PID: 4244)
- aria2c.exe (PID: 3180)
- RADStudio_12_1_esd_61_7529b.exe (PID: 1748)
- RADStudio_12_1_esd_61_7529b.tmp (PID: 2332)
- RADStudio_12_1_esd_61_7529b.tmp (PID: 2800)
- RADStudio_12_1_esd_61_7529b.exe (PID: 6620)
- LicenseManager.exe (PID: 6728)
- MBSetup.exe (PID: 3800)
- MBAMInstallerService.exe (PID: 6744)
Reads the software policy settings
- slui.exe (PID: 3192)
- quicksoftware-dl.exe (PID: 4244)
- slui.exe (PID: 1012)
- LicenseManager.exe (PID: 6728)
- MBSetup.exe (PID: 3800)
- MBAMInstallerService.exe (PID: 6744)
Manual execution by a user
- notepad.exe (PID: 5728)
- RADStudio_12_1_esd_61_7529b.exe (PID: 1748)
- MBSetup.exe (PID: 1276)
- MBSetup.exe (PID: 3800)
Reads security settings of Internet Explorer
- notepad.exe (PID: 5728)
Creates files or folders in the user directory
- quicksoftware-dl.exe (PID: 4244)
- LicenseManager.exe (PID: 6728)
Reads the machine GUID from the registry
- quicksoftware-dl.exe (PID: 4244)
- aria2c.exe (PID: 3180)
- MBSetup.exe (PID: 3800)
Creates a new folder
- cmd.exe (PID: 4724)
Process checks computer location settings
- RADStudio_12_1_esd_61_7529b.tmp (PID: 2332)
- RADStudio_12_1_esd_61_7529b.tmp (PID: 2800)
Creates files in the program directory
- RADStudio_12_1_esd_61_7529b.tmp (PID: 2800)
- LicenseManager.exe (PID: 6728)
- MBSetup.exe (PID: 3800)
- MBAMInstallerService.exe (PID: 6744)
Compiled with Borland Delphi (YARA)
- RADStudio_12_1_esd_61_7529b.exe (PID: 1748)
- RADStudio_12_1_esd_61_7529b.tmp (PID: 2332)
- RADStudio_12_1_esd_61_7529b.exe (PID: 6620)
- RADStudio_12_1_esd_61_7529b.tmp (PID: 2800)
Detects InnoSetup installer (YARA)
- RADStudio_12_1_esd_61_7529b.tmp (PID: 2332)
- RADStudio_12_1_esd_61_7529b.exe (PID: 1748)
- RADStudio_12_1_esd_61_7529b.exe (PID: 6620)
- RADStudio_12_1_esd_61_7529b.tmp (PID: 2800)
The sample compiled with french language support
- RADStudio_12_1_esd_61_7529b.tmp (PID: 2800)
The sample compiled with german language support
- RADStudio_12_1_esd_61_7529b.tmp (PID: 2800)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:03:08 23:05:20+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 27136 |
| InitializedDataSize: | 184832 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x358d |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
152
Monitored processes
19
Malicious processes
5
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1012 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
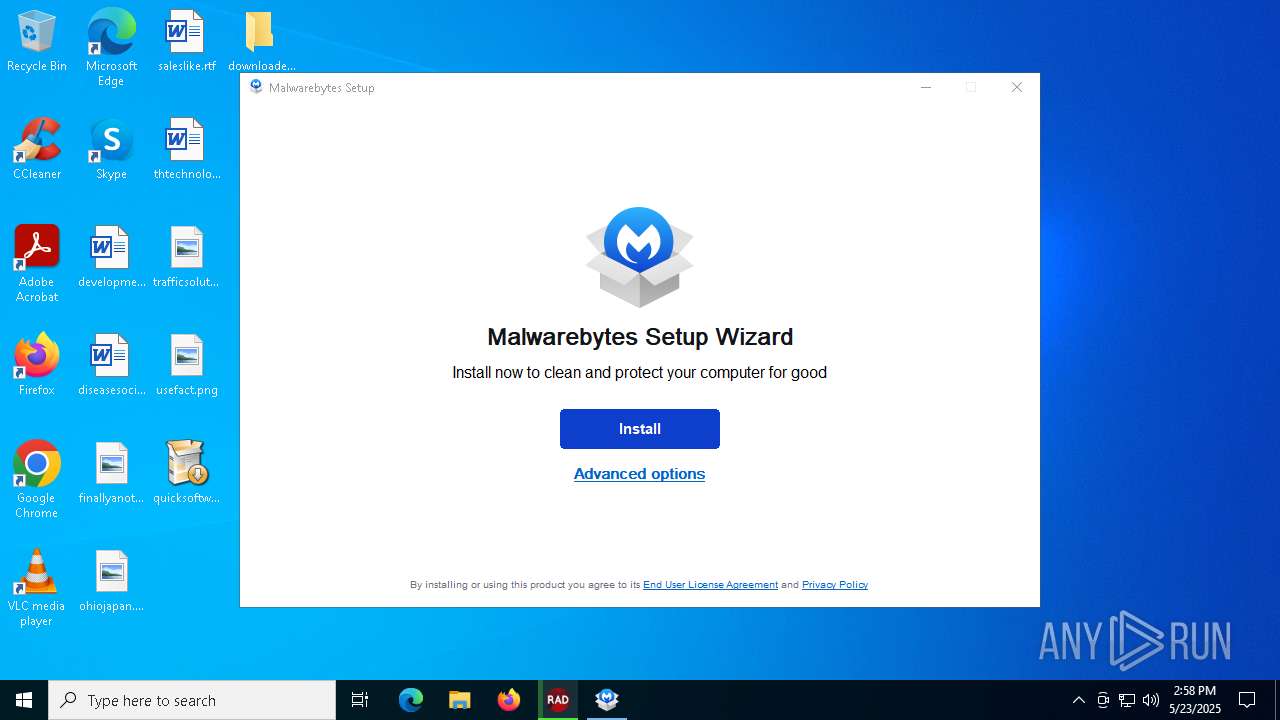
| 1276 | "C:\Users\admin\Desktop\downloaded-files\MBSetup.exe" | C:\Users\admin\Desktop\downloaded-files\MBSetup.exe | — | explorer.exe | |||||||||||
User: admin Company: Malwarebytes Integrity Level: MEDIUM Description: Malwarebytes Setup Exit code: 3221226540 Version: 5.3.1.129 Modules
| |||||||||||||||
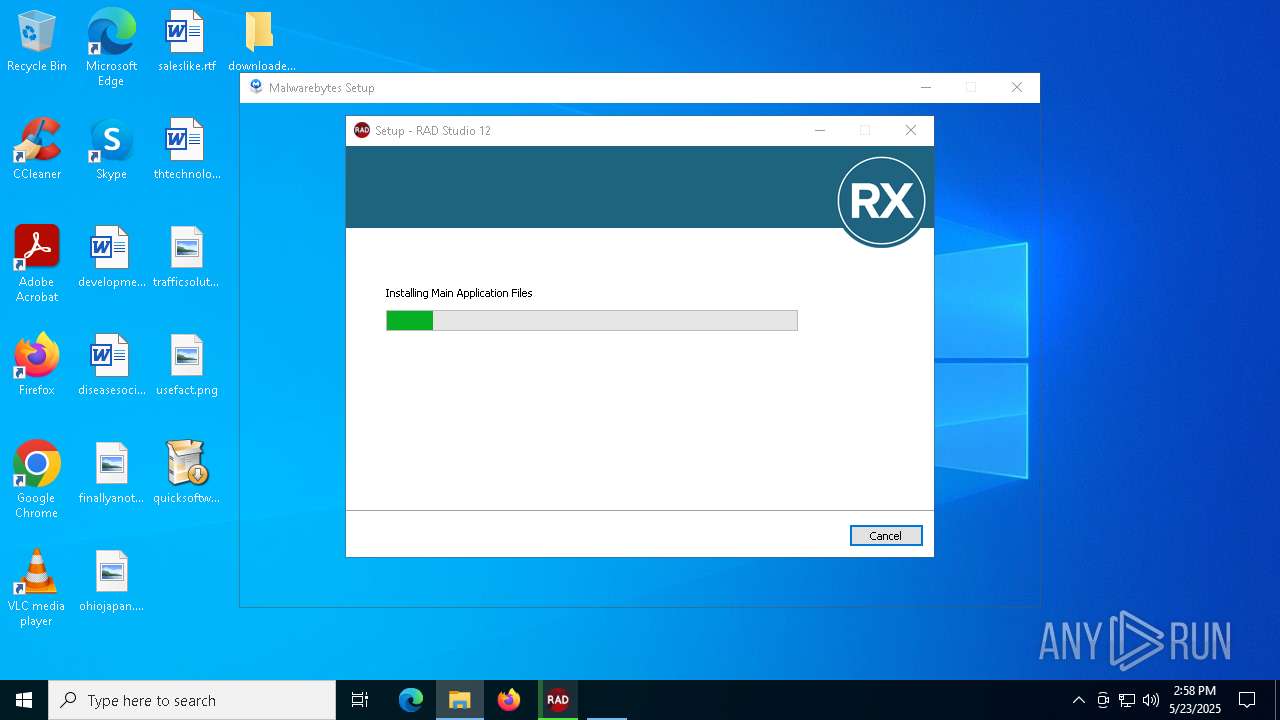
| 1748 | "C:\Users\admin\Desktop\downloaded-files\RADStudio_12_1_esd_61_7529b.exe" | C:\Users\admin\Desktop\downloaded-files\RADStudio_12_1_esd_61_7529b.exe | explorer.exe | ||||||||||||
User: admin Company: Embarcadero Technologies, Inc. Integrity Level: MEDIUM Description: RAD Studio 12 Setup Version: Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2332 | "C:\Users\admin\AppData\Local\Temp\is-MAUH1.tmp\RADStudio_12_1_esd_61_7529b.tmp" /SL5="$2033E,175867963,868352,C:\Users\admin\Desktop\downloaded-files\RADStudio_12_1_esd_61_7529b.exe" | C:\Users\admin\AppData\Local\Temp\is-MAUH1.tmp\RADStudio_12_1_esd_61_7529b.tmp | — | RADStudio_12_1_esd_61_7529b.exe | |||||||||||
User: admin Company: Embarcadero Technologies, Inc. Integrity Level: MEDIUM Description: Setup/Uninstall Version: 51.1052.0.0 Modules
| |||||||||||||||
| 2800 | "C:\Users\admin\AppData\Local\Temp\is-CAN9U.tmp\RADStudio_12_1_esd_61_7529b.tmp" /SL5="$3032A,175867963,868352,C:\Users\admin\Desktop\downloaded-files\RADStudio_12_1_esd_61_7529b.exe" /SPAWNWND=$B0292 /NOTIFYWND=$2033E | C:\Users\admin\AppData\Local\Temp\is-CAN9U.tmp\RADStudio_12_1_esd_61_7529b.tmp | RADStudio_12_1_esd_61_7529b.exe | ||||||||||||
User: admin Company: Embarcadero Technologies, Inc. Integrity Level: HIGH Description: Setup/Uninstall Version: 51.1052.0.0 Modules
| |||||||||||||||
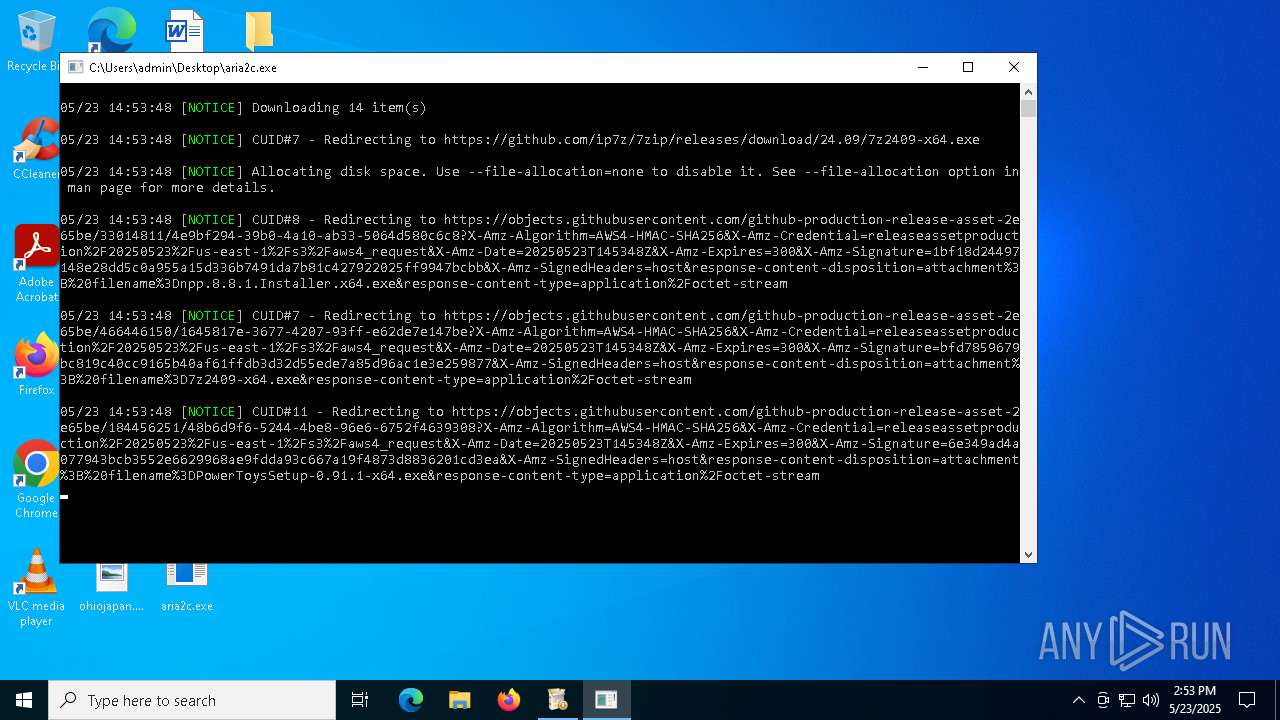
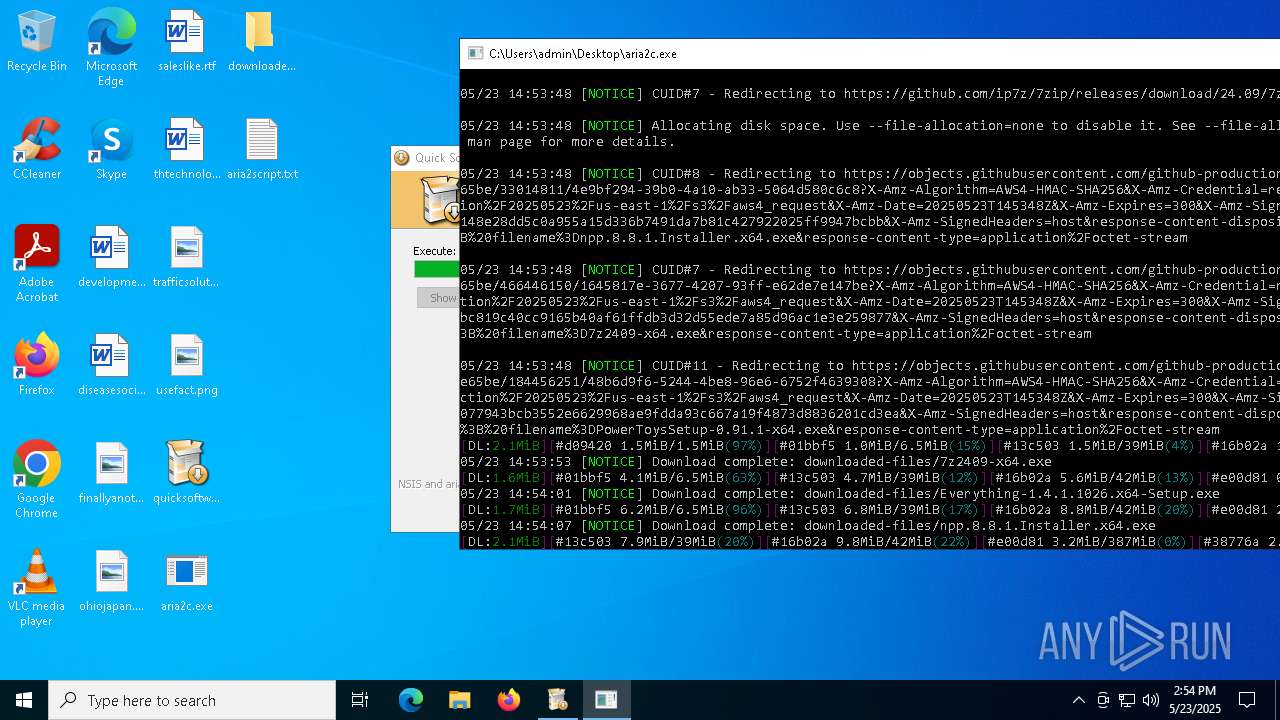
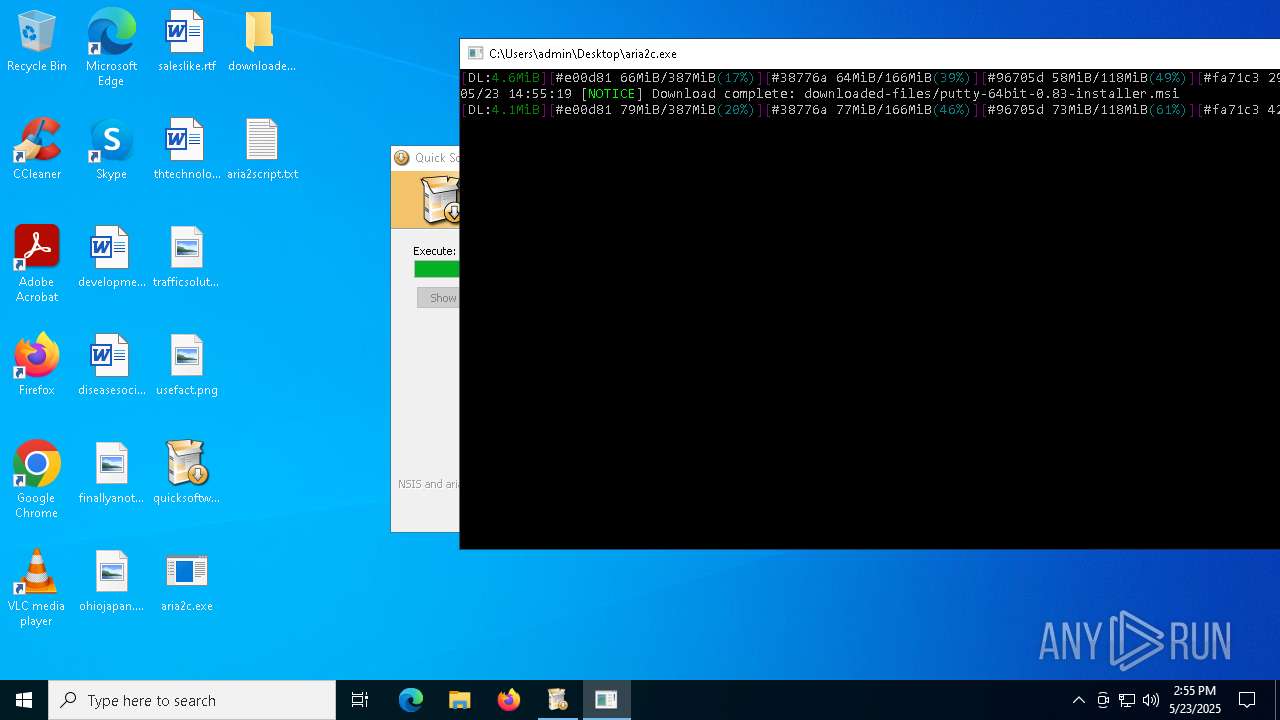
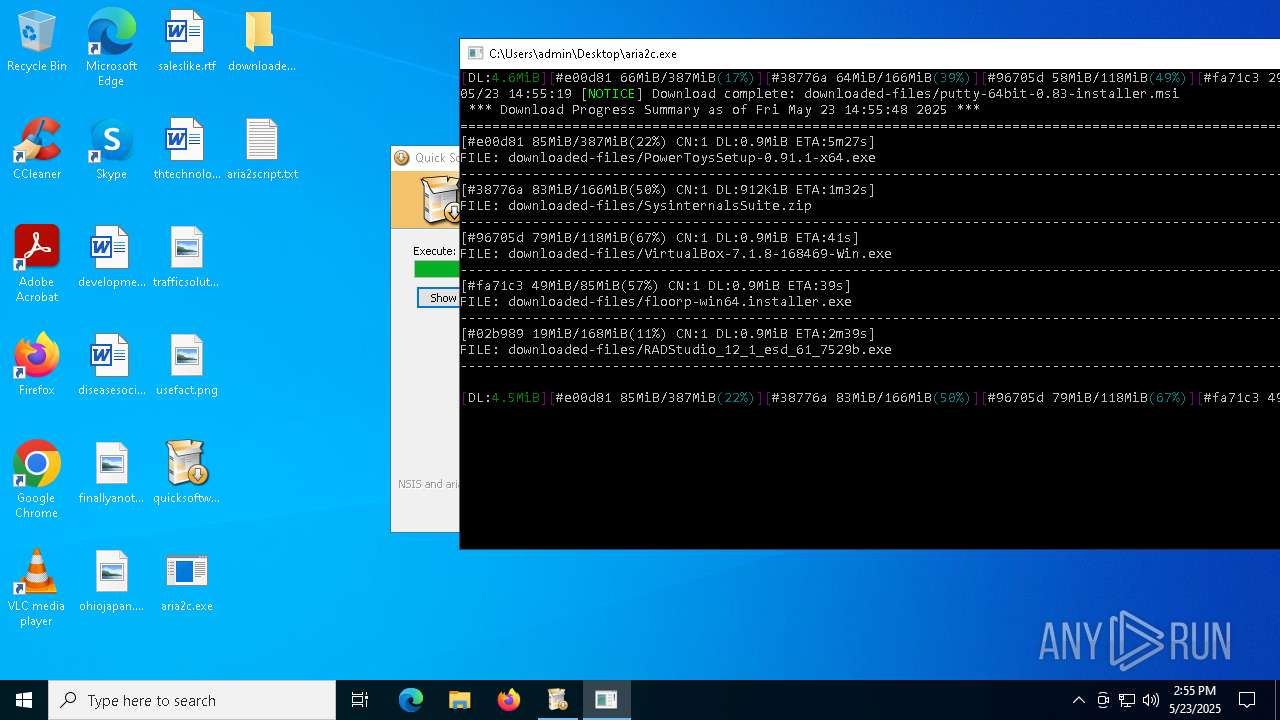
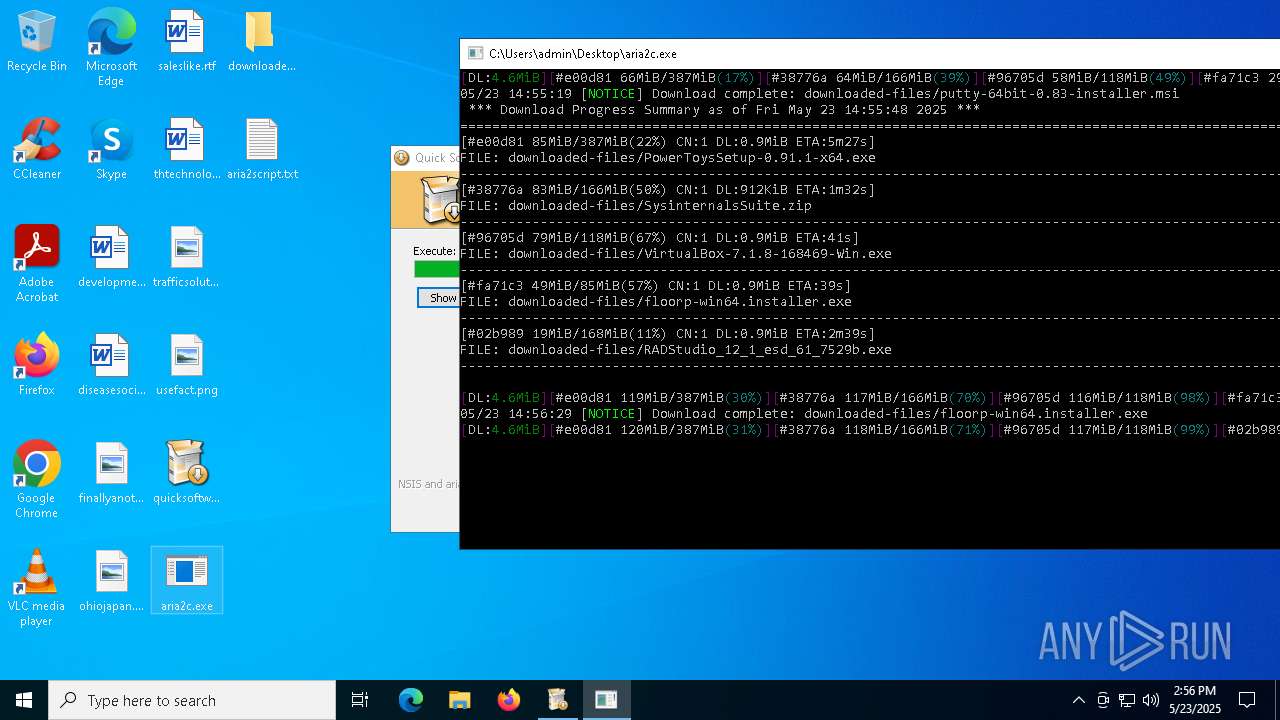
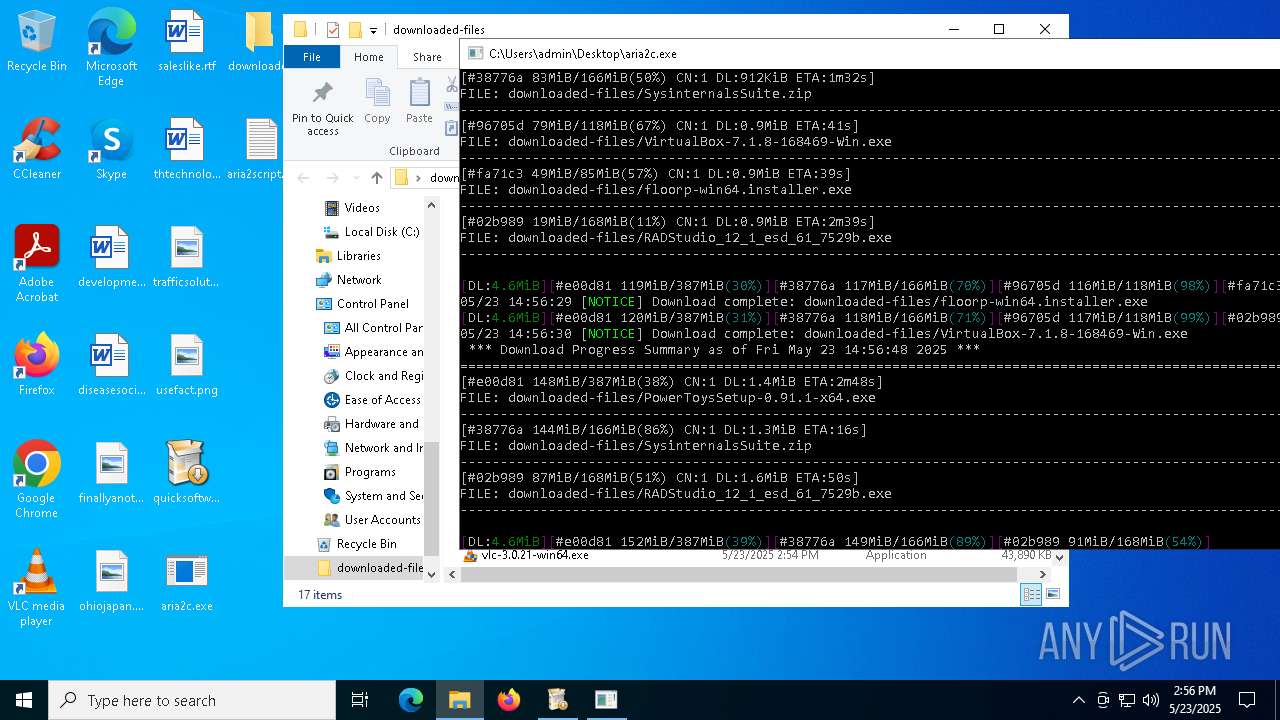
| 3180 | "C:\Users\admin\Desktop\aria2c.exe" -d downloaded-files -i aria2script.txt | C:\Users\admin\Desktop\aria2c.exe | quicksoftware-dl.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3192 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3800 | "C:\Users\admin\Desktop\downloaded-files\MBSetup.exe" | C:\Users\admin\Desktop\downloaded-files\MBSetup.exe | explorer.exe | ||||||||||||
User: admin Company: Malwarebytes Integrity Level: HIGH Description: Malwarebytes Setup Version: 5.3.1.129 Modules
| |||||||||||||||
| 4024 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
5 562
Read events
5 521
Write events
40
Delete events
1
Modification events
| (PID) Process: | (4244) quicksoftware-dl.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (4244) quicksoftware-dl.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (4244) quicksoftware-dl.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2800) RADStudio_12_1_esd_61_7529b.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Embarcadero\BDS\23.0\Globals |
| Operation: | write | Name: | Personalities |
Value: 3 | |||
| (PID) Process: | (3800) MBSetup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Malwarebytes |
| Operation: | write | Name: | id |
Value: 99d0fe45135d43dcad62ec09df36e1cc | |||
| (PID) Process: | (3800) MBSetup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Malwarebytes |
| Operation: | write | Name: | id |
Value: 99d0fe45135d43dcad62ec09df36e1cc | |||
| (PID) Process: | (3800) MBSetup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\mbamtestkey |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3800) MBSetup.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\MBAMInstallerService\Parameters |
| Operation: | write | Name: | UserName |
Value: admin | |||
| (PID) Process: | (3800) MBSetup.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\MBAMInstallerService\Parameters |
| Operation: | write | Name: | ProductCode |
Value: MBAM-C | |||
| (PID) Process: | (3800) MBSetup.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\MBAMInstallerService\Parameters |
| Operation: | write | Name: | ProductBuild |
Value: consumer | |||
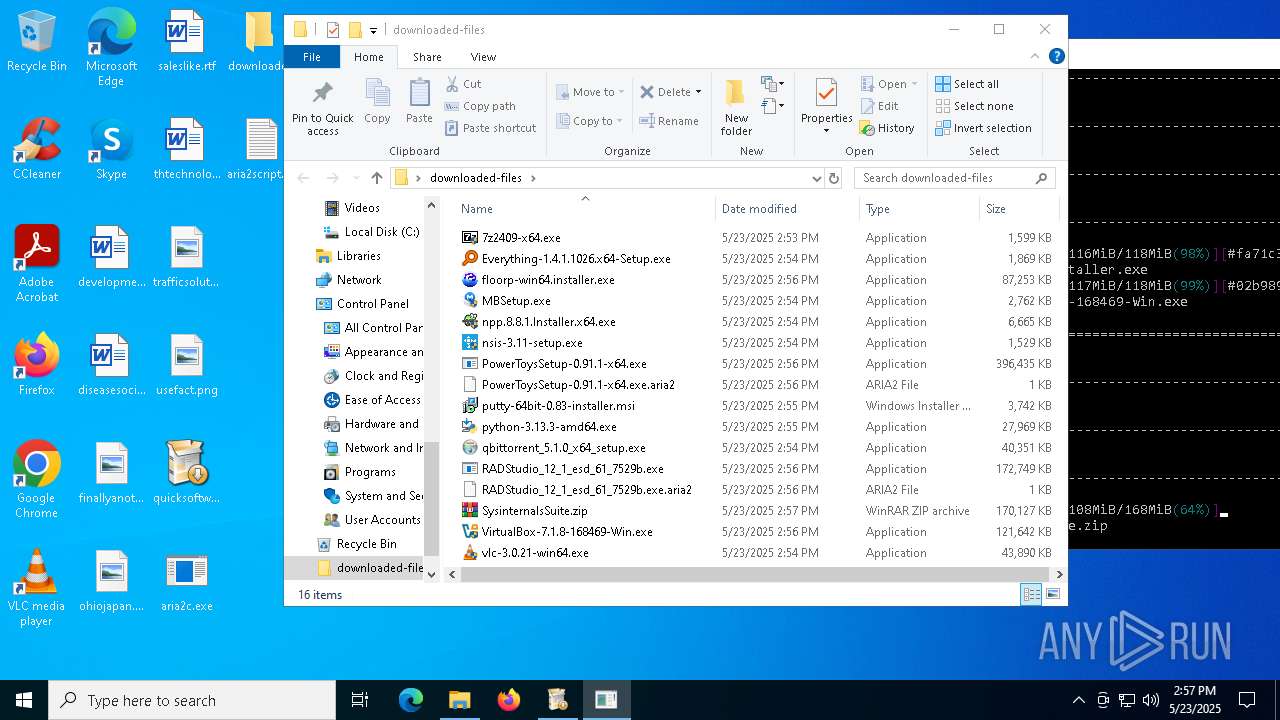
Executable files
474
Suspicious files
157
Text files
343
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4244 | quicksoftware-dl.exe | C:\Users\admin\AppData\Local\Temp\nsrC844.tmp\System.dll | executable | |
MD5:9B38A1B07A0EBC5C7E59E63346ECC2DB | SHA256:C881253DAFCF1322A771139B1A429EC1E78C507CA81A218A20DC1A4B25ABBFE7 | |||
| 4244 | quicksoftware-dl.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\aria2c[1].exe | executable | |
MD5:6C5EA5A82D756BCA4A9610C8D2260D2F | SHA256:B9CD71B275AF11B63C33457B0F43F2F2675937070C563E195F223EFD7FA4C74B | |||
| 4244 | quicksoftware-dl.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:E192462F281446B5D1500D474FBACC4B | SHA256:F1BA9F1B63C447682EBF9DE956D0DA2A027B1B779ABEF9522D347D3479139A60 | |||
| 4244 | quicksoftware-dl.exe | C:\Users\admin\AppData\Local\Temp\nsrC844.tmp\modern-wizard.bmp | image | |
MD5:CBE40FD2B1EC96DAEDC65DA172D90022 | SHA256:3AD2DC318056D0A2024AF1804EA741146CFC18CC404649A44610CBF8B2056CF2 | |||
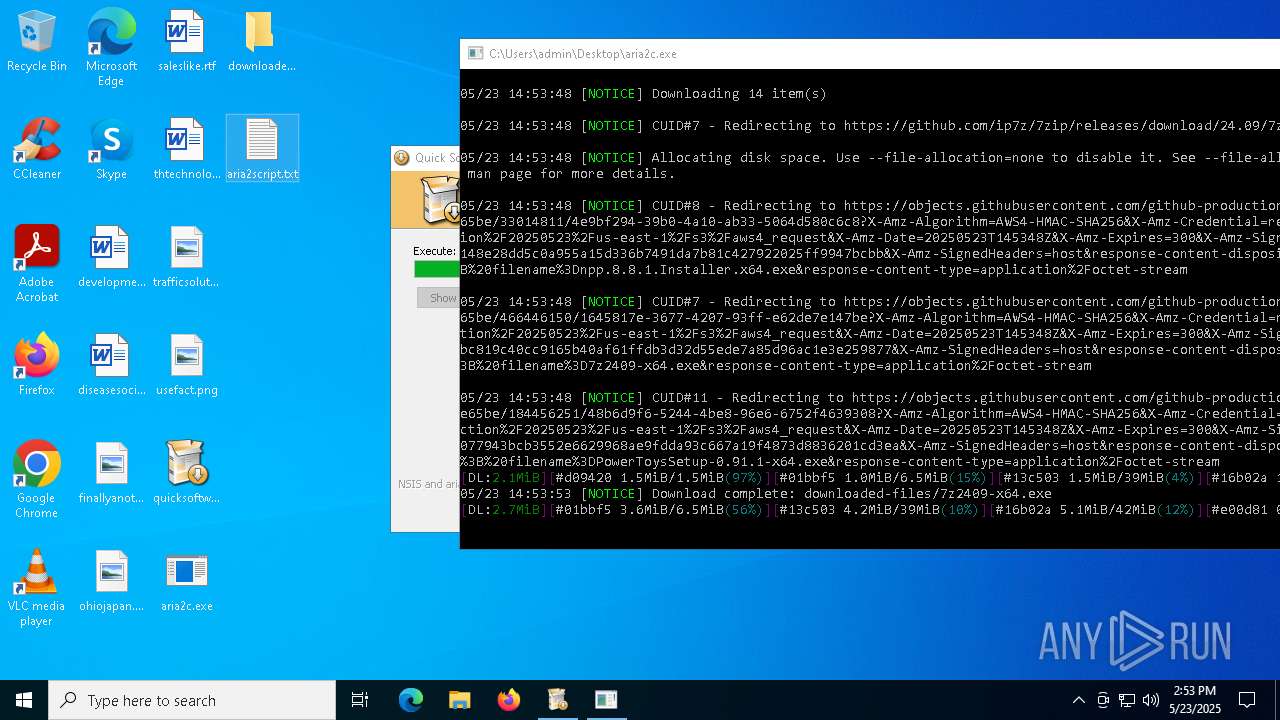
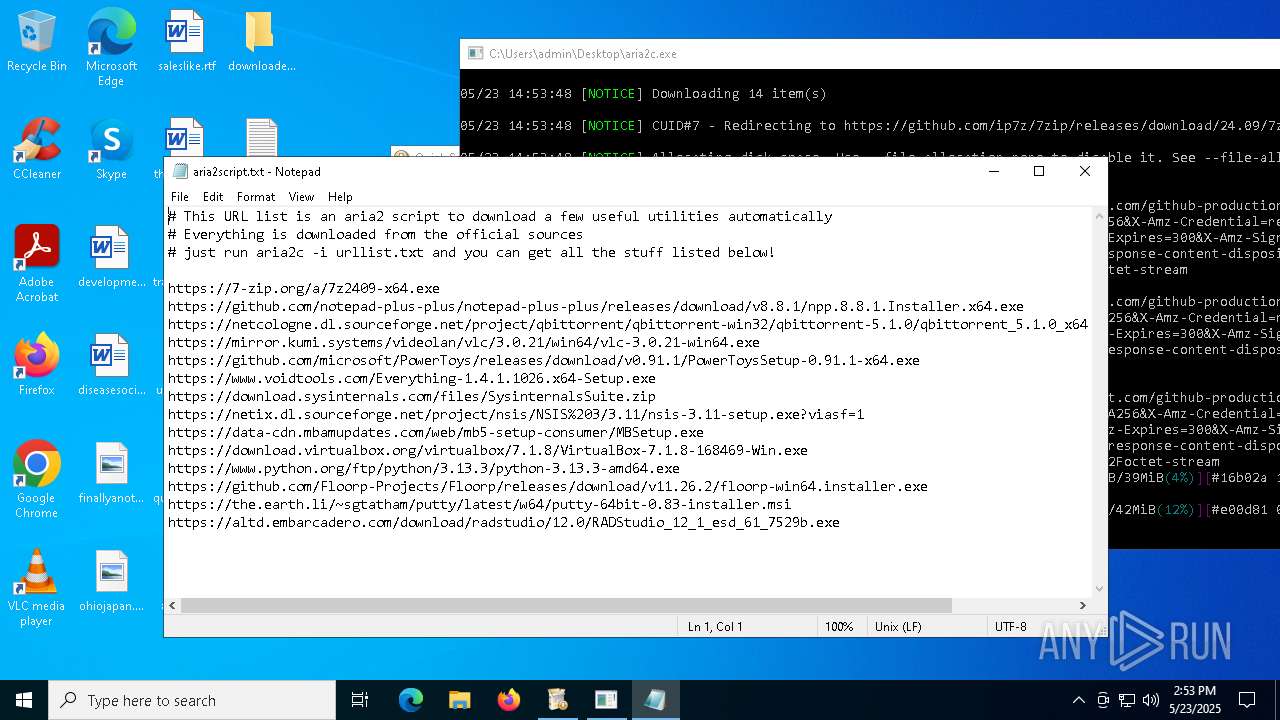
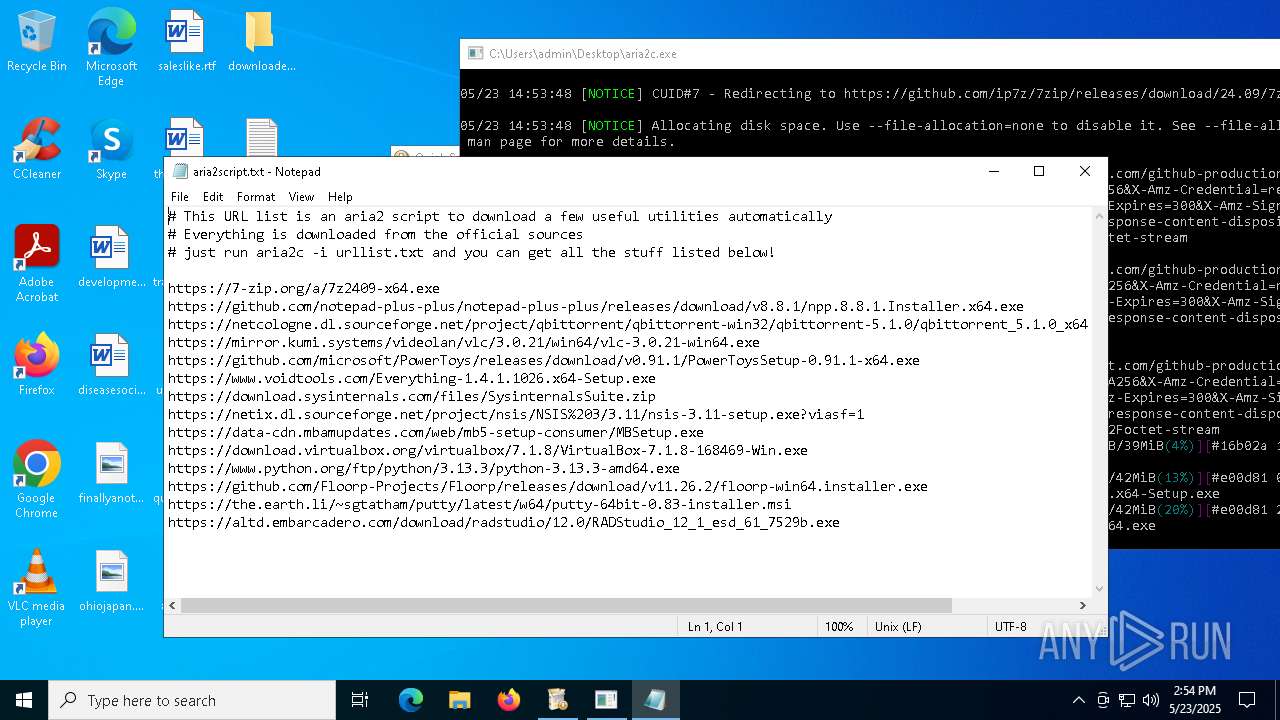
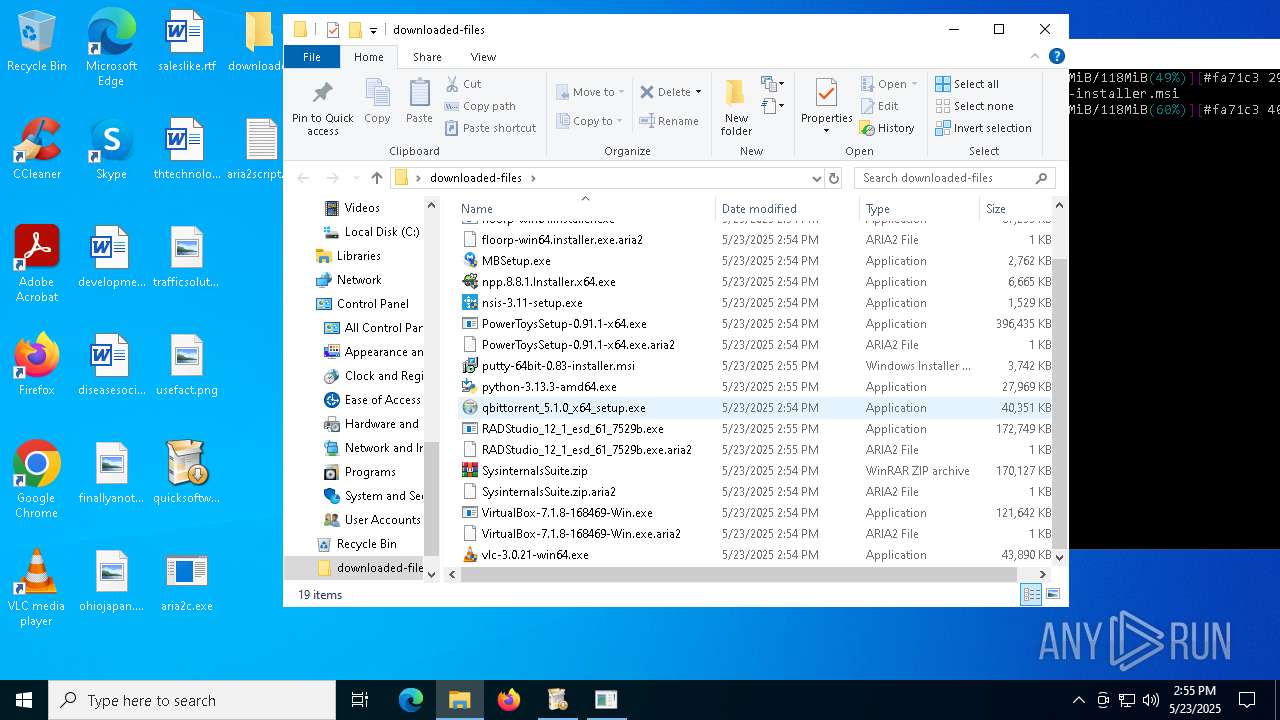
| 4244 | quicksoftware-dl.exe | C:\Users\admin\Desktop\aria2script.txt | text | |
MD5:F71E3833F698C3C62409469692A5446B | SHA256:CFC2233ED169E5BEA2B1D9F04538F24B602B8ECC9016896300A6D5D5C59C7627 | |||
| 4244 | quicksoftware-dl.exe | C:\Users\admin\AppData\Local\Temp\nsrC844.tmp\nsDialogs.dll | executable | |
MD5:8F0E7415F33843431DF308BB8E06AF81 | SHA256:BB49F15FA83452370047A7801E39FC7F64E70C7545B8999BB85AA4749EAA048B | |||
| 4244 | quicksoftware-dl.exe | C:\Users\admin\AppData\Local\Temp\nsrC844.tmp\INetC.dll | executable | |
MD5:40D7ECA32B2F4D29DB98715DD45BFAC5 | SHA256:85E03805F90F72257DD41BFDAA186237218BBB0EC410AD3B6576A88EA11DCCB9 | |||
| 4244 | quicksoftware-dl.exe | C:\Users\admin\AppData\Local\Temp\nsrC844.tmp\modern-header.bmp | image | |
MD5:583C38FB0F5AF5FE584D9A9B01D6A3E7 | SHA256:4C9E804CE1A391F8E603B7B9C732A6529C1E81BE4D12F125C8562EA9D49095C2 | |||
| 4244 | quicksoftware-dl.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:5B49561CCE1EC633EEF03FC6ADDC8E1B | SHA256:C88EEF78C8432430AD0A3571BCF736D19975CBC496887A37F6BA4B71A75FB645 | |||
| 4244 | quicksoftware-dl.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\KCV3KQBA\urllist[1].txt | text | |
MD5:F71E3833F698C3C62409469692A5446B | SHA256:CFC2233ED169E5BEA2B1D9F04538F24B602B8ECC9016896300A6D5D5C59C7627 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
21
TCP/UDP connections
59
DNS requests
43
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
756 | lsass.exe | GET | 200 | 18.66.147.67:80 | http://e6.c.lencr.org/46.crl | unknown | — | — | whitelisted |
756 | lsass.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | unknown | — | — | whitelisted |
5392 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
756 | lsass.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | unknown | — | — | whitelisted |
5392 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
756 | lsass.exe | GET | 200 | 131.253.33.203:80 | http://oneocsp.microsoft.com/ocsp/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSzT%2FzqwcqNvhP9i4c4sCPz2JbzrAQU%2FglxQFUFEETYpIF1uJ4a6UoGiMgCEzMCGJMA9BYEJXFQUDQAAAIYkwA%3D | unknown | — | — | whitelisted |
756 | lsass.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
4244 | quicksoftware-dl.exe | GET | 200 | 23.209.209.135:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
4244 | quicksoftware-dl.exe | GET | 200 | 3.167.227.5:80 | http://r11.c.lencr.org/84.crl | unknown | — | — | whitelisted |
756 | lsass.exe | GET | 200 | 3.167.227.86:80 | http://r11.c.lencr.org/93.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
4244 | quicksoftware-dl.exe | 139.84.173.225:443 | files.webdevtest.ftp.sh | AS-CHOOPA | US | unknown |
4244 | quicksoftware-dl.exe | 23.209.209.135:80 | x1.c.lencr.org | PT. Telekomunikasi Selular | ID | whitelisted |
4244 | quicksoftware-dl.exe | 3.167.227.5:80 | r11.c.lencr.org | — | US | whitelisted |
6544 | svchost.exe | 20.190.159.64:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2112 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
client.wns.windows.com |
| whitelisted |
files.webdevtest.ftp.sh |
| unknown |
x1.c.lencr.org |
| whitelisted |
r11.c.lencr.org |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
7-zip.org |
| unknown |
github.com |
| whitelisted |
netcologne.dl.sourceforge.net |
| whitelisted |
mirror.kumi.systems |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a *.ftp .sh Domain |