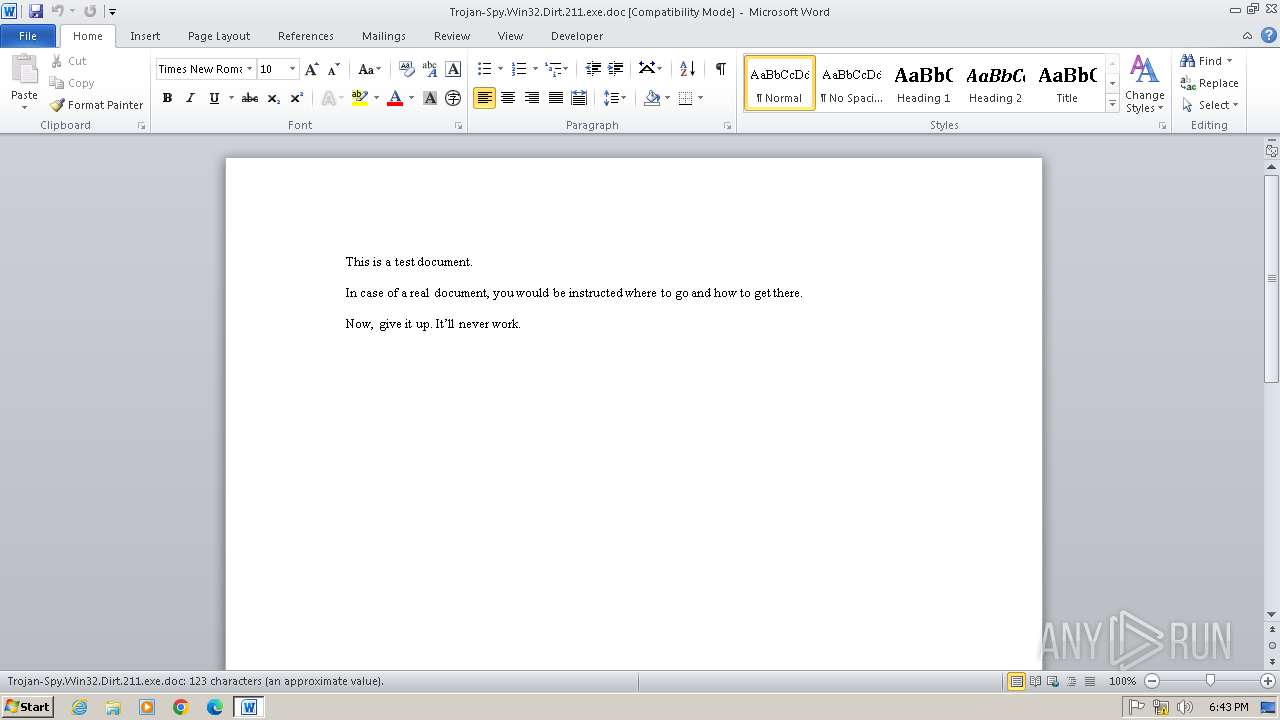
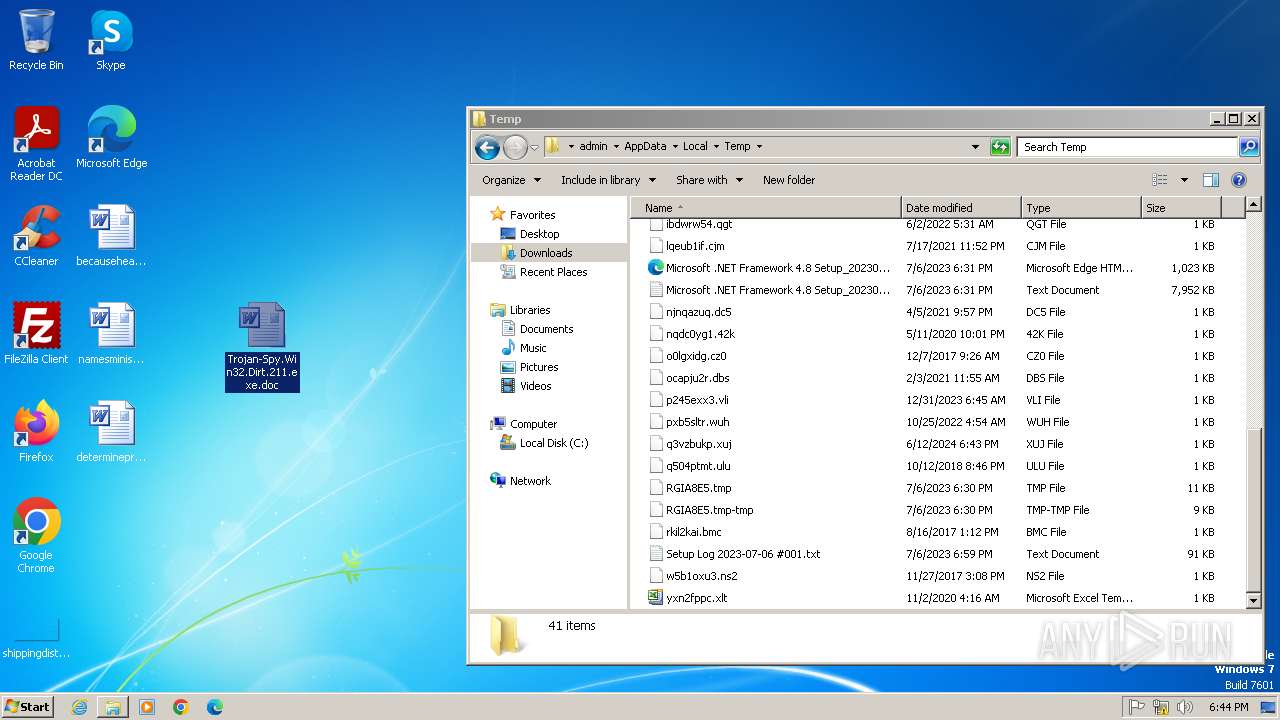
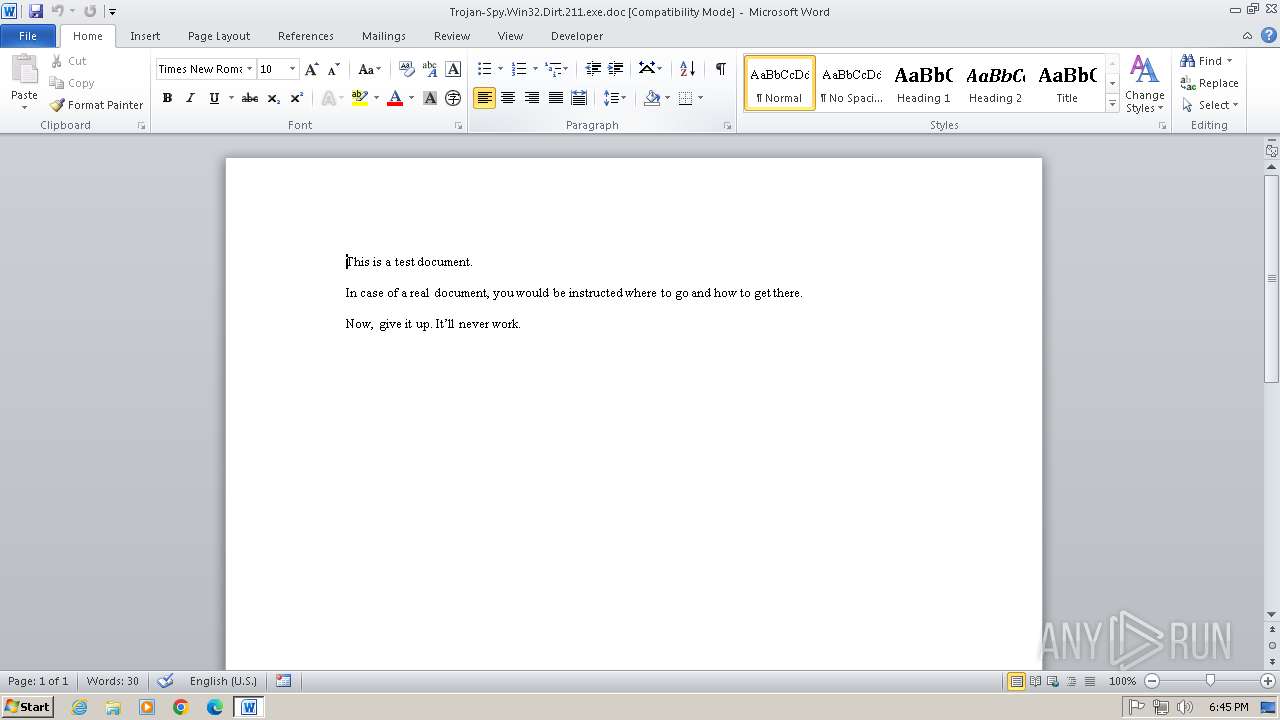
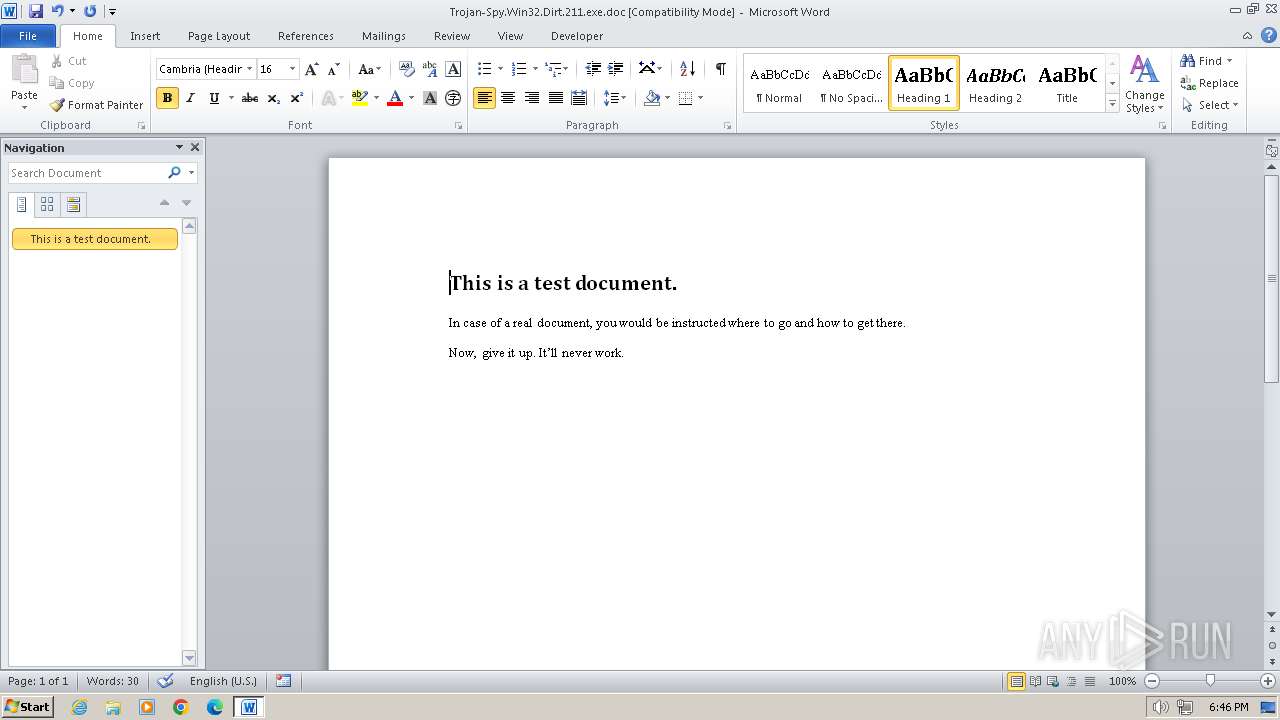
| File name: | Trojan-Spy.Win32.Dirt.211.exe |
| Full analysis: | https://app.any.run/tasks/596db051-1dc5-4100-ace8-26c62d9e1887 |
| Verdict: | Malicious activity |
| Analysis date: | April 27, 2025, 17:43:12 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
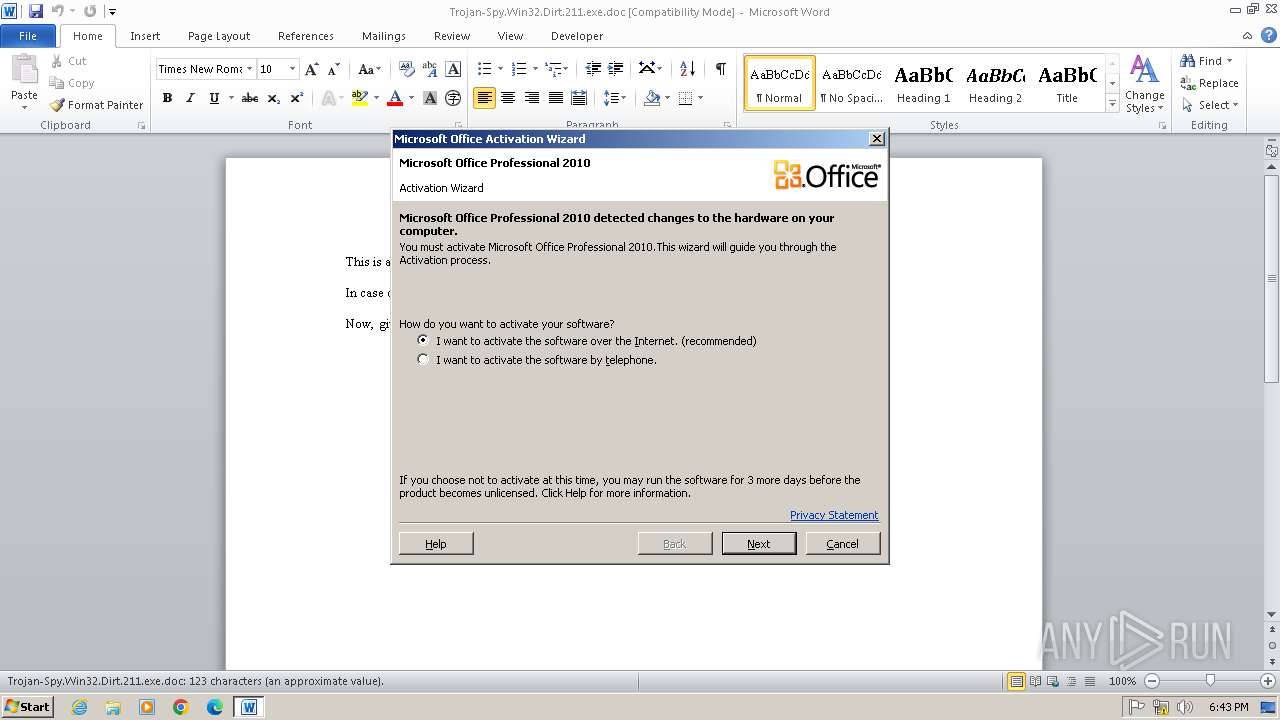
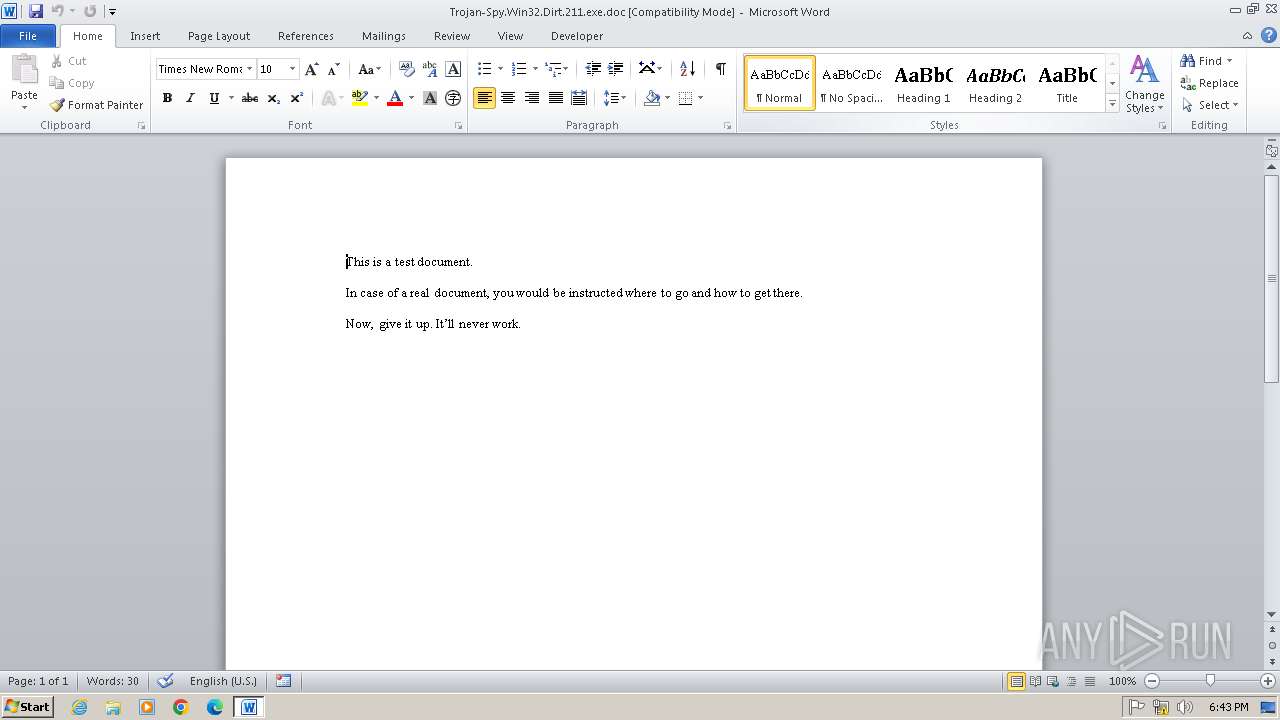
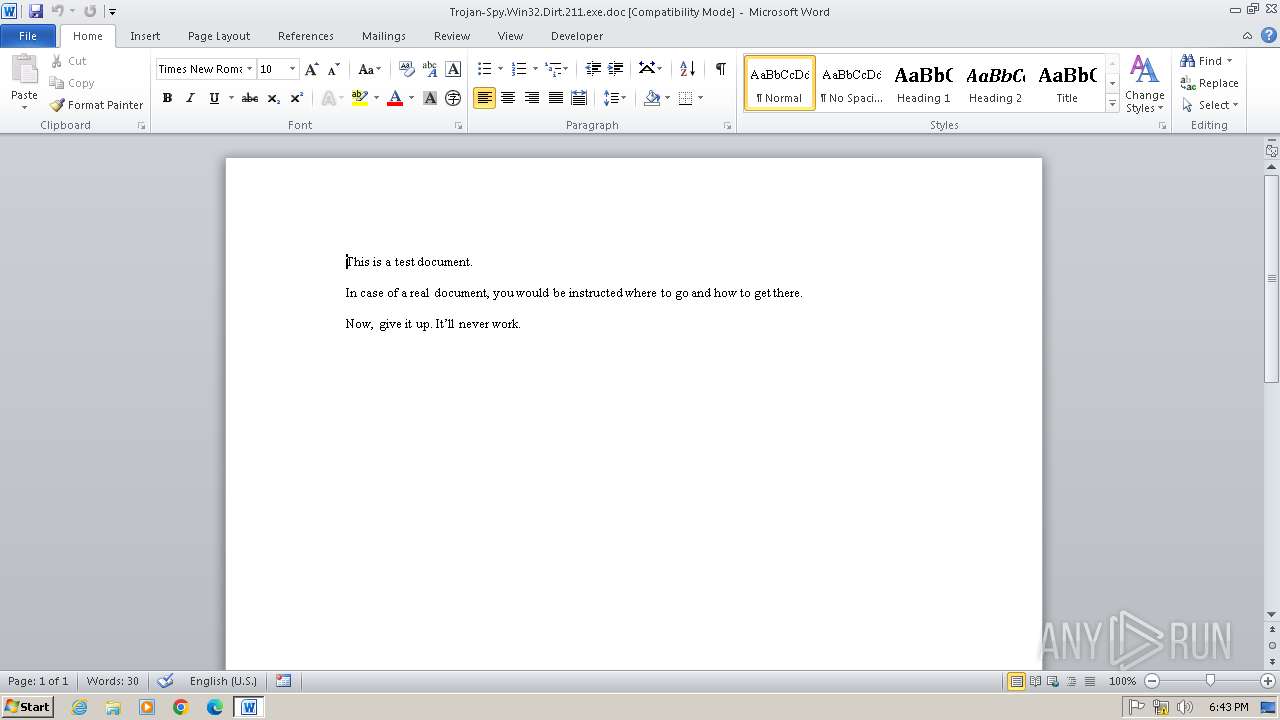
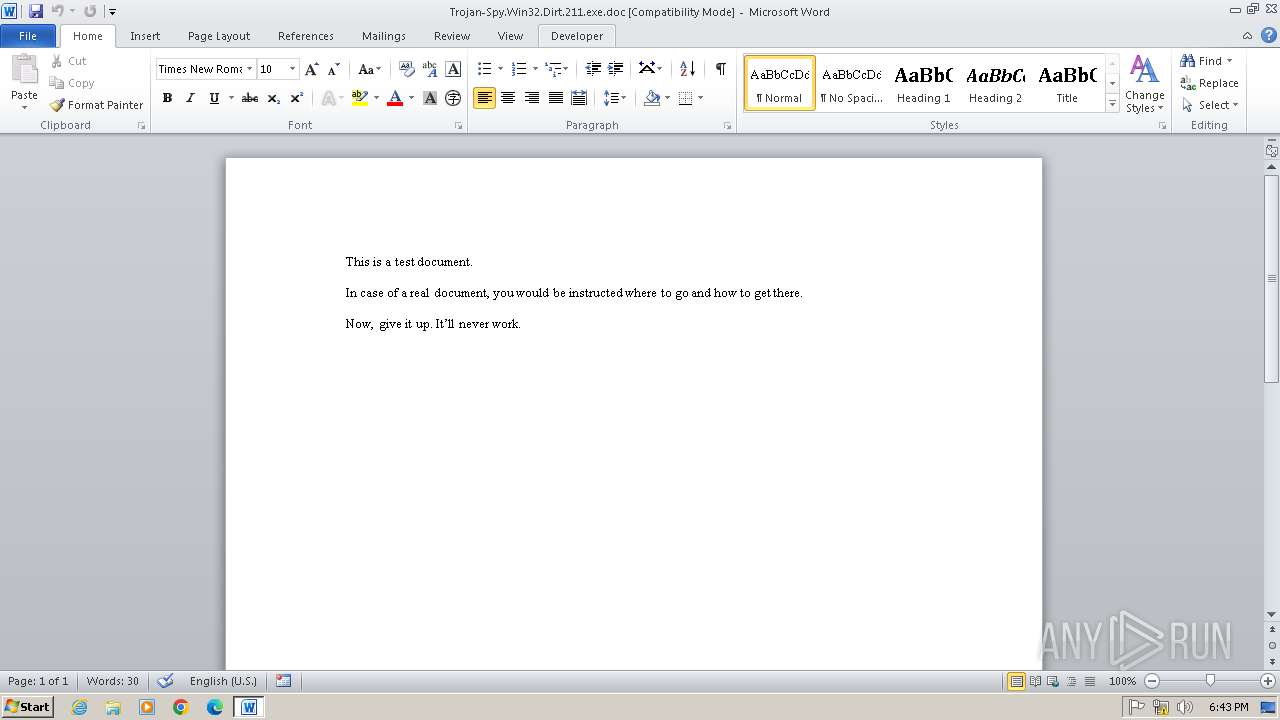
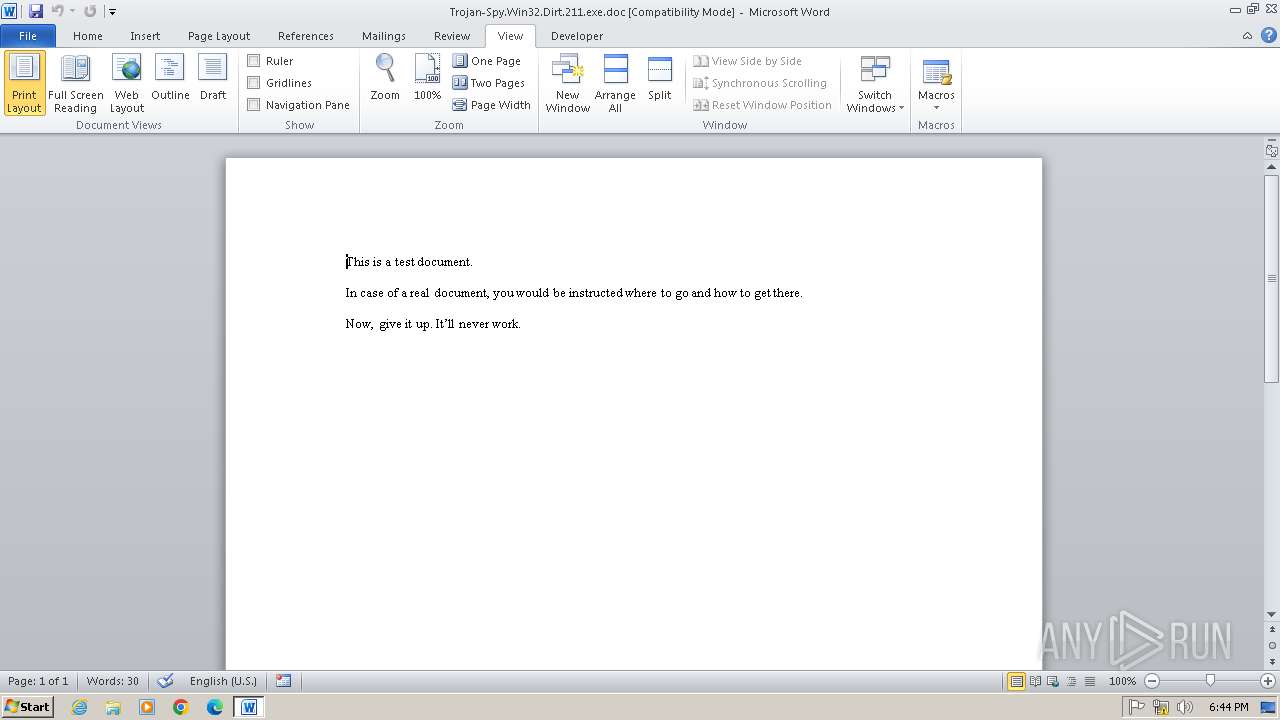
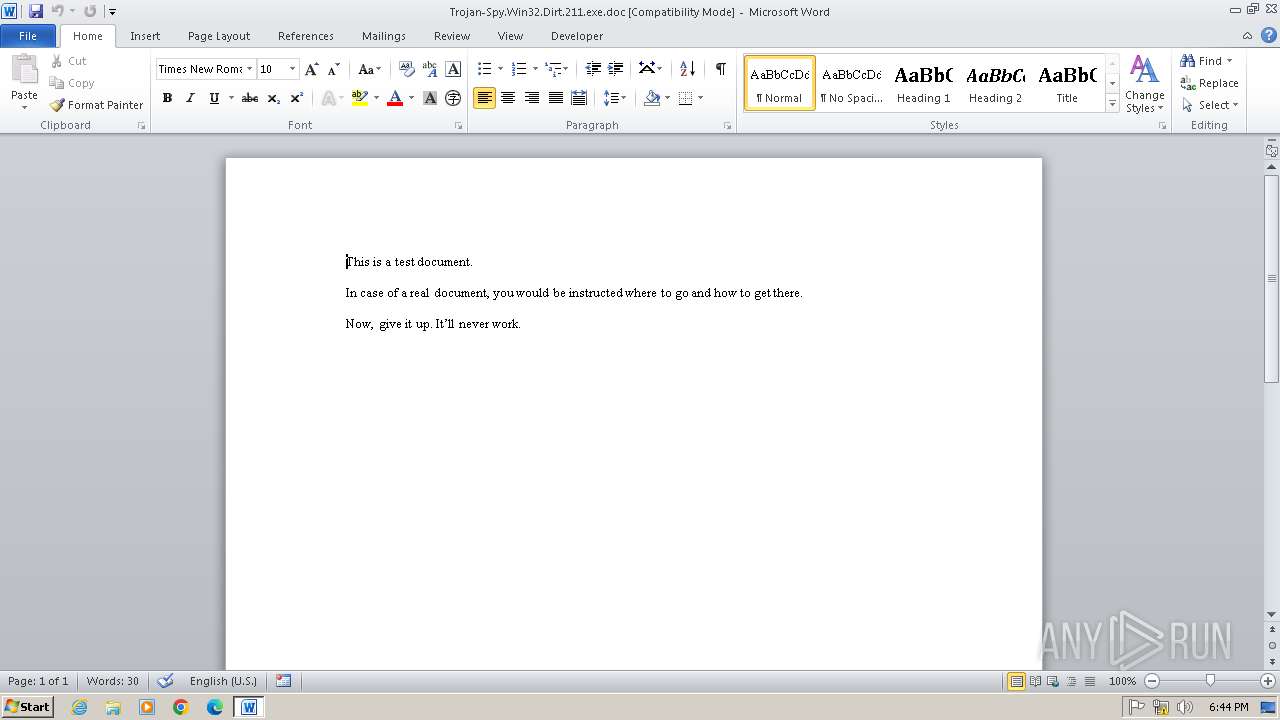
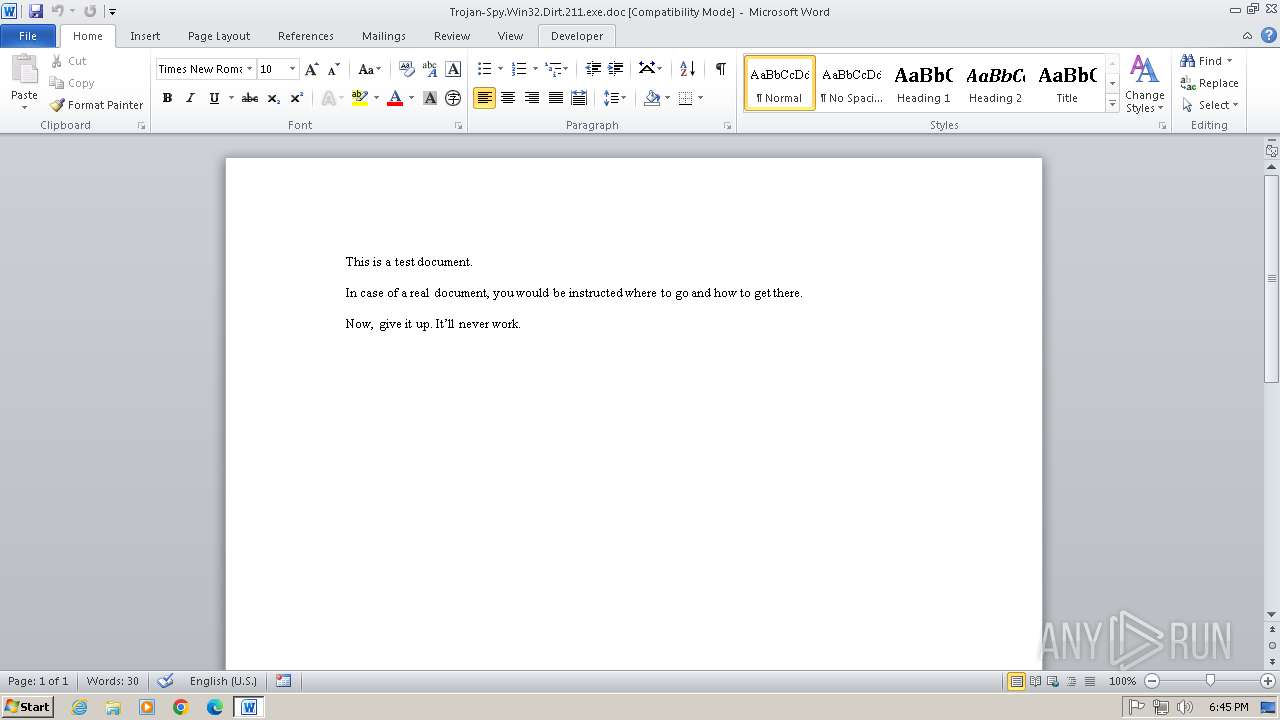
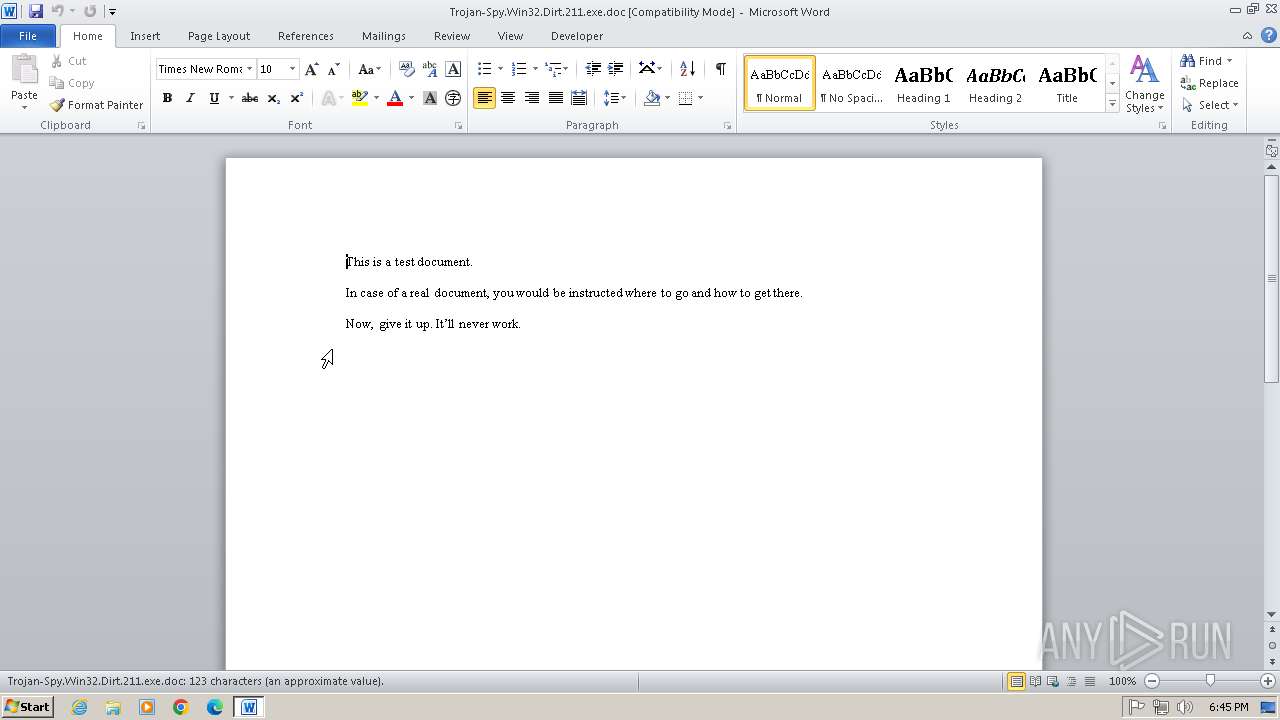
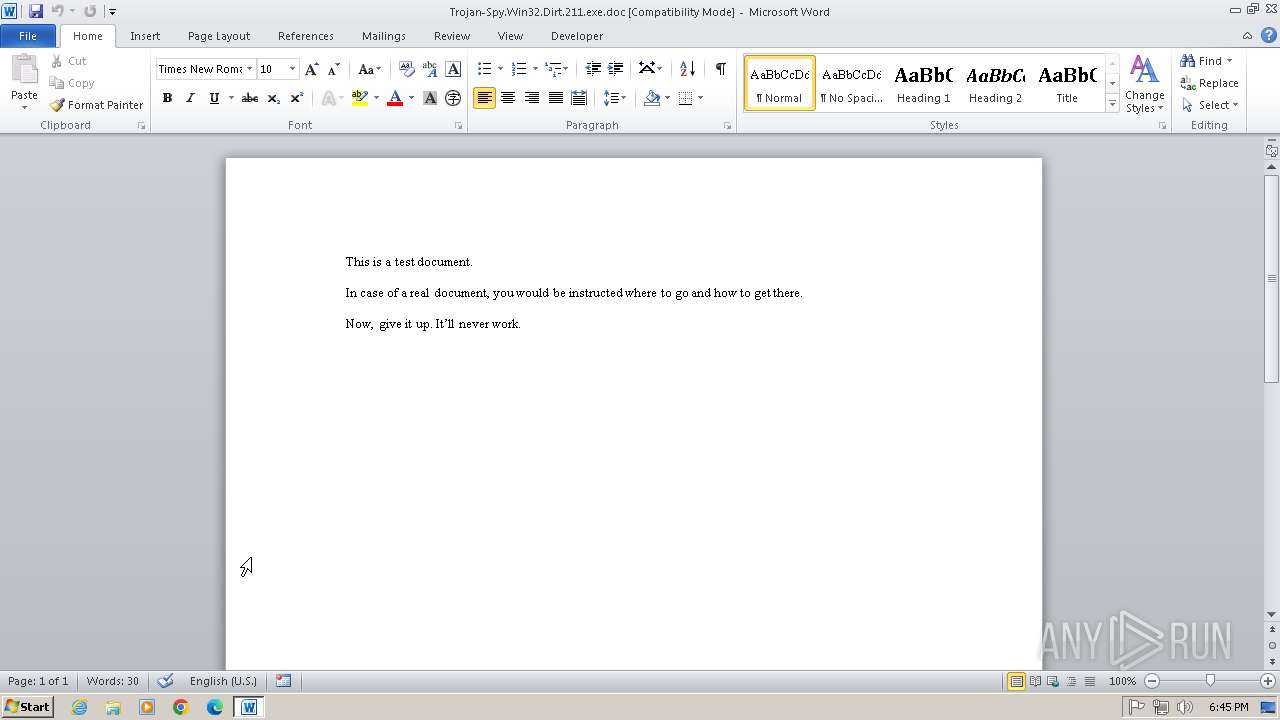
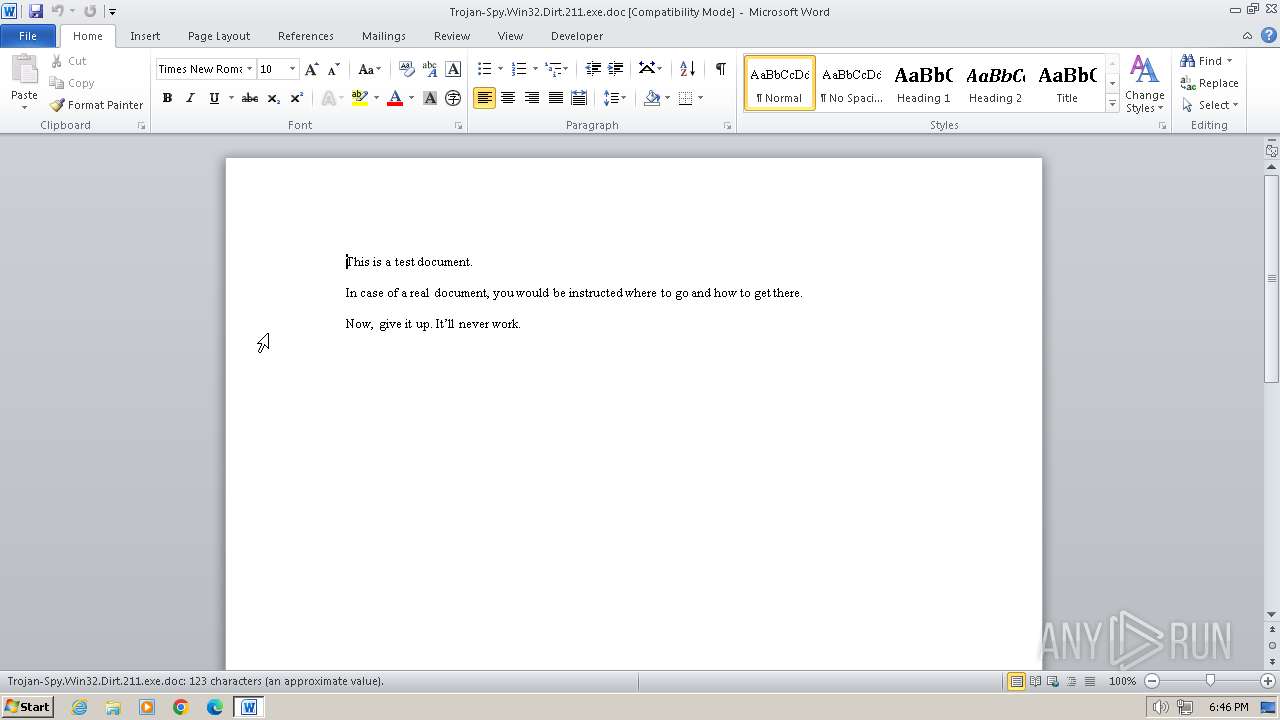
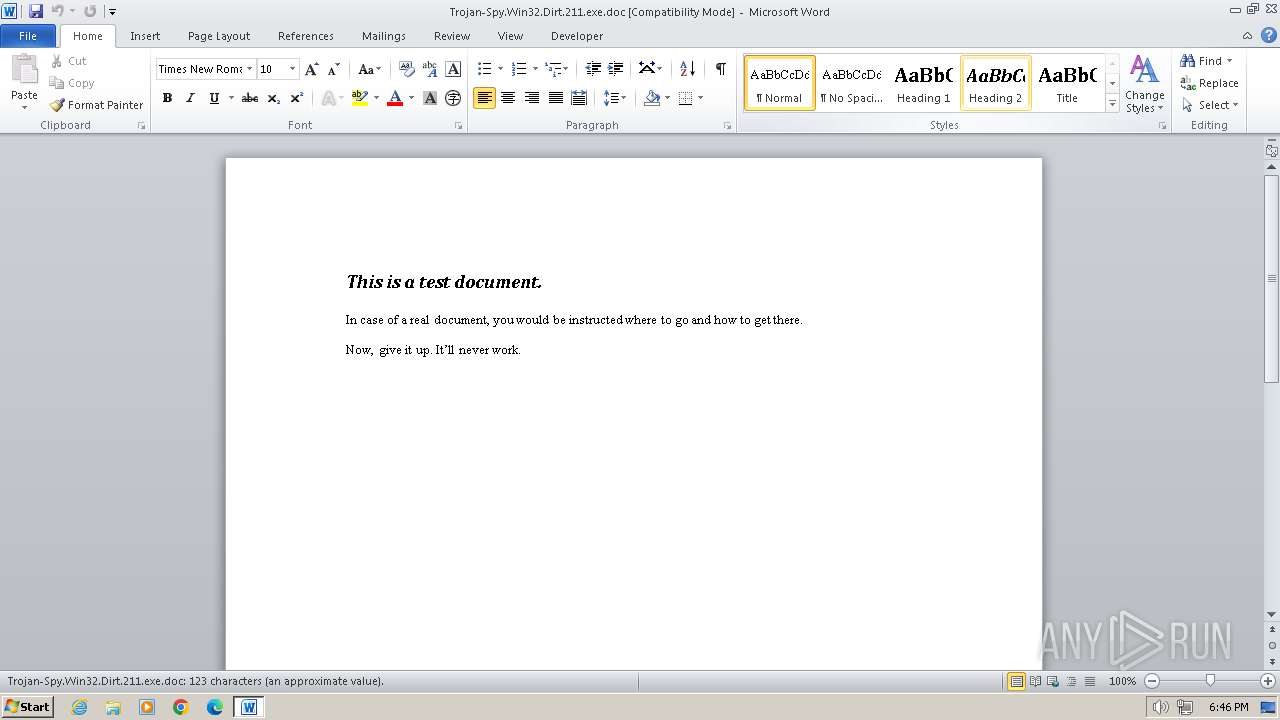
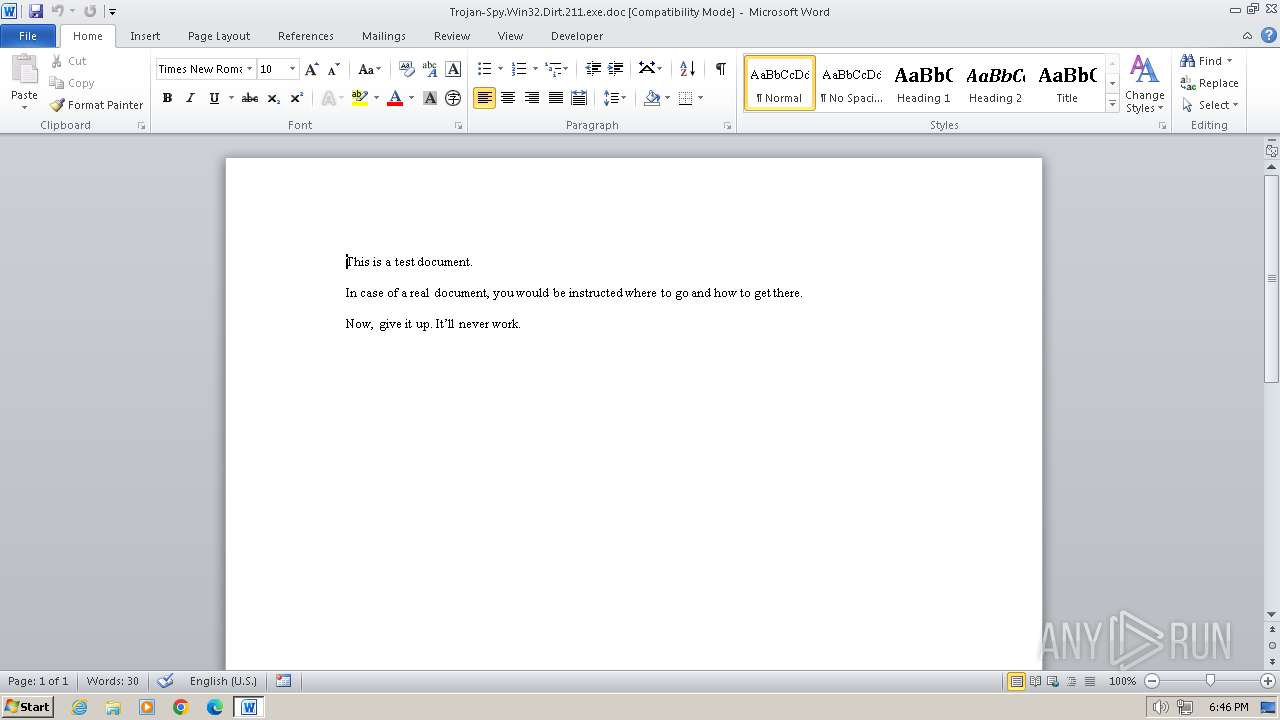
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 4.10, Code page: 1252, Title: This is a test document, Author: ., Template: Normal.dot, Last Saved By: Customer , Revision Number: 2, Name of Creating Application: Microsoft Word 9.0, Create Time/Date: Sun Dec 12 10:32:00 1999, Last Saved Time/Date: Sun Dec 12 10:32:00 1999, Number of Pages: 1, Number of Words: 21, Number of Characters: 123, Security: 0 |
| MD5: | 05B04255C90AE48BD66014C0155FE2A6 |
| SHA1: | B4691BFC7211D649EE1F74FF5B20466B30133424 |
| SHA256: | B12AEF4EF587EF760D0CB7393B7A7B6202943A8579089F821CA158D229C0250C |
| SSDEEP: | 384:79oa/BAK5D8wznVjFY4HxHz6js3ip6g6:exK5EAxHz6jW8 |
MALICIOUS
No malicious indicators.SUSPICIOUS
The process executes via Task Scheduler
- sipnotify.exe (PID: 1444)
- ctfmon.exe (PID: 1692)
Reads the Internet Settings
- sipnotify.exe (PID: 1444)
INFO
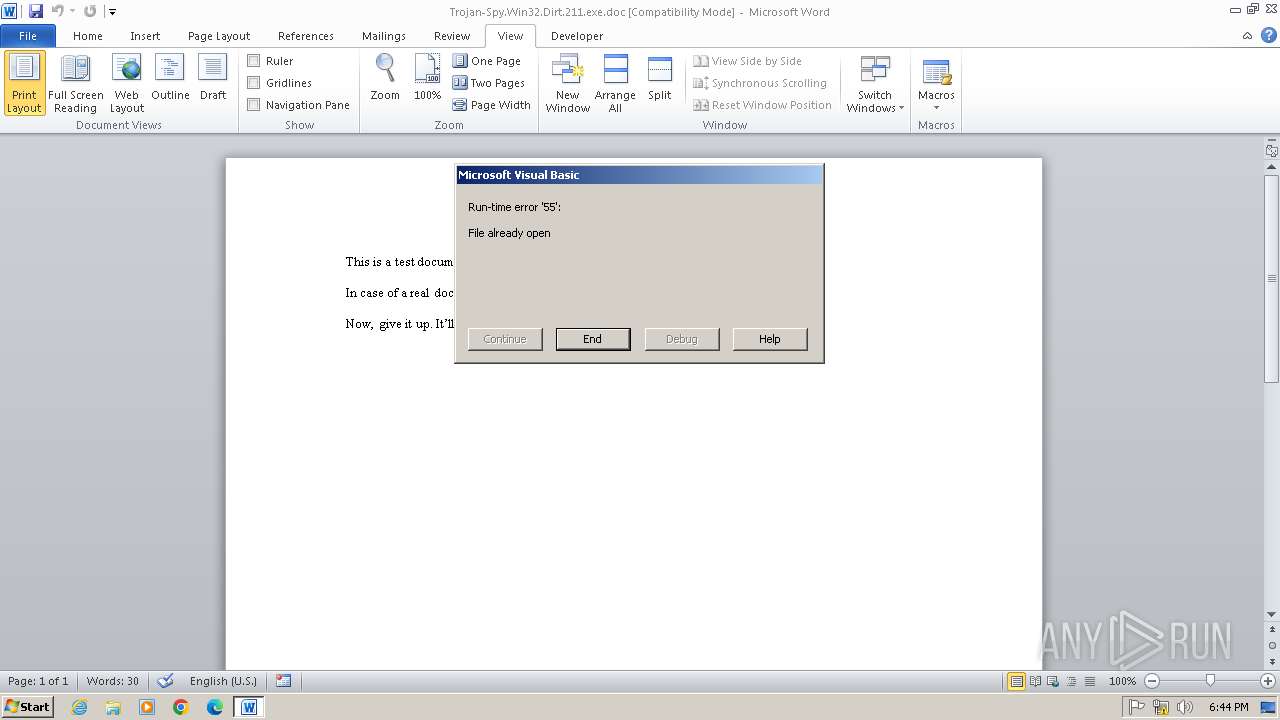
Disables trace logs
- WINWORD.EXE (PID: 2936)
Manual execution by a user
- explorer.exe (PID: 2588)
- WINWORD.EXE (PID: 2936)
- WINWORD.EXE (PID: 3196)
- IMEKLMG.EXE (PID: 2096)
- WINWORD.EXE (PID: 2528)
- explorer.exe (PID: 2756)
- IMEKLMG.EXE (PID: 2088)
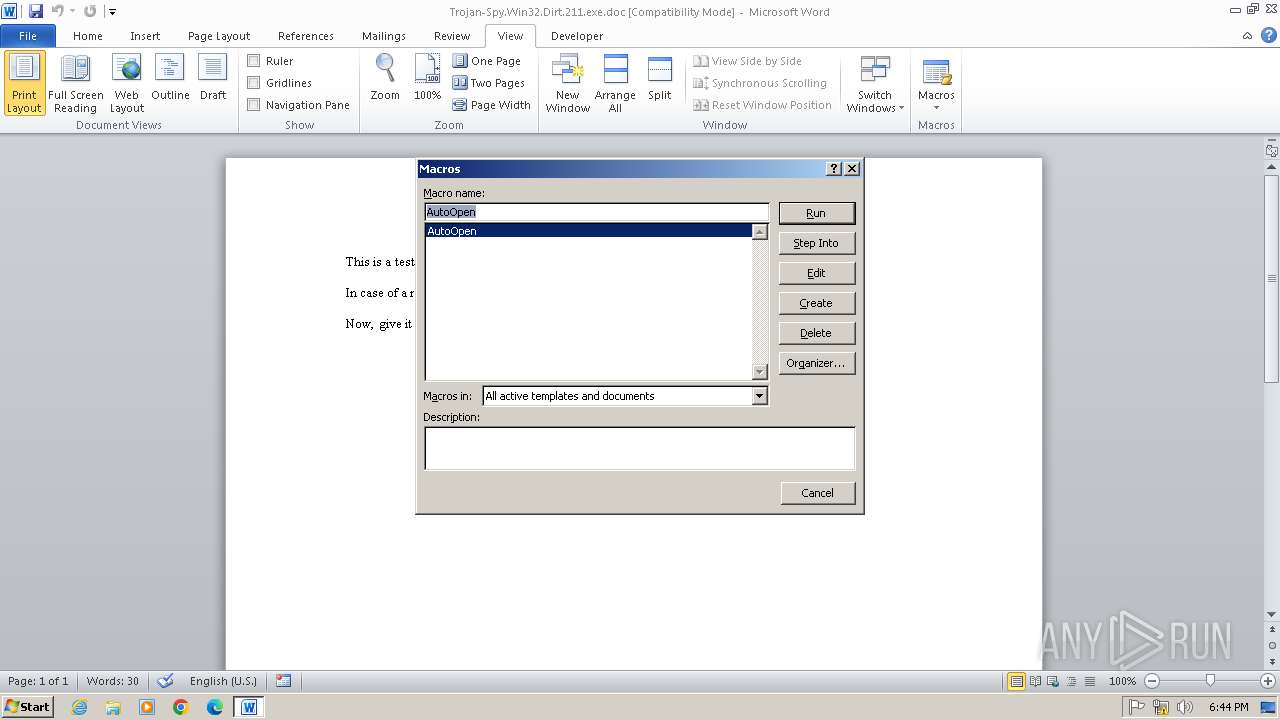
An automatically generated document
- WINWORD.EXE (PID: 2472)
Reads the computer name
- IMEKLMG.EXE (PID: 2088)
- IMEKLMG.EXE (PID: 2096)
Checks supported languages
- IMEKLMG.EXE (PID: 2088)
- IMEKLMG.EXE (PID: 2096)
Process checks whether UAC notifications are on
- IMEKLMG.EXE (PID: 2096)
- IMEKLMG.EXE (PID: 2088)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Identification: | Word 8.0 |
|---|---|
| LanguageCode: | English (US) |
| DocFlags: | 1Table, ExtChar |
| System: | Windows |
| Word97: | No |
| Title: | This is a test document |
| Subject: | - |
| Author: | . |
| Keywords: | - |
| Template: | Normal.dot |
| LastModifiedBy: | Customer |
| Software: | Microsoft Word 9.0 |
| CreateDate: | 1999:12:12 10:32:00 |
| ModifyDate: | 1999:12:12 10:32:00 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | . |
| CharCountWithSpaces: | 151 |
| AppVersion: | 9.272 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | This is a test document |
| HeadingPairs: |
|
| CompObjUserTypeLen: | 24 |
| CompObjUserType: | Microsoft Word Document |
| LastPrinted: | 0000:00:00 00:00:00 |
| RevisionNumber: | 2 |
| TotalEditTime: | - |
| Words: | 21 |
| Characters: | 123 |
| Pages: | 1 |
| Paragraphs: | 1 |
| Lines: | 1 |
| LastSavedBy: | Customer (C:\Source\cds\cdsmacros\source.doc) |
Total processes
97
Monitored processes
10
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1444 | C:\Windows\system32\sipnotify.exe -LogonOrUnlock | C:\Windows\System32\sipnotify.exe | taskeng.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: sipnotify Exit code: 0 Version: 6.1.7602.20480 (win7sp1_ldr_escrow.191010-1716) Modules
| |||||||||||||||
| 1692 | C:\Windows\System32\ctfmon.exe | C:\Windows\System32\ctfmon.exe | — | taskeng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CTF Loader Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2088 | "C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE" /SetPreload /JPN /Log | C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office IME 2010 Exit code: 1 Version: 14.0.4734.1000 Modules
| |||||||||||||||
| 2096 | "C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE" /SetPreload /KOR /Log | C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office IME 2010 Exit code: 1 Version: 14.0.4734.1000 Modules
| |||||||||||||||
| 2472 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n C:\Users\admin\AppData\Local\Temp\Trojan-Spy.Win32.Dirt.211.exe.doc | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2528 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\Trojan-Spy.Win32.Dirt.211.exe.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2588 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2756 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2936 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /vu "C:\Users\admin\Desktop\Trojan-Spy.Win32.Dirt.211.exe.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3196 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\Trojan-Spy.Win32.Dirt.211.exe.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
48 667
Read events
36 730
Write events
10 457
Delete events
1 480
Modification events
| (PID) Process: | (2472) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | */# |
Value: 2A2F2300A8090000010000000000000000000000 | |||
| (PID) Process: | (2472) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2472) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2472) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2472) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2472) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2472) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2472) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2472) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2472) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
1
Suspicious files
36
Text files
7
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2472 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR177B.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2936 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR8795.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3196 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRF10D.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2472 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\VBE\MSForms.exd | binary | |
MD5:A534C6937CC7C3DAF9782A2B799DD044 | SHA256:5B63CFF38C7F7F5D0DE665A4AE793C5D92B1EB8F125903A087BA6CAFE7EF92DF | |||
| 2936 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | ini | |
MD5:9670CAB7E80288B910AFEC76B17CCAE1 | SHA256:9382A284B316DB583A14BE9AA66CEB44E4826E9BB28E987CF45EE4D7D95D0E96 | |||
| 2472 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRF{BC394AC5-5615-46FA-976B-721E4C29EFEA}.tmp | binary | |
MD5:A7AF0E9BEF84057CB9179EBC52C82D4D | SHA256:A5CD46C216B2E4937A948016FB6FE51EADCBE3AF5A09B4F448674F3F41900EC3 | |||
| 2472 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\Word14.customUI | compressed | |
MD5:2708920706D645A7A9C0F8584C97289A | SHA256:15B3426F48393612BF91D1A04981D37CA41A4727BED15DBC2FD0C1715F40C9EC | |||
| 2472 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DFD1922221683A1A8A.TMP | binary | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
| 2472 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{D2D581FE-E1E4-46DF-A4DD-977DA9D0A93E}.tmp | binary | |
MD5:5D4D94EE7E06BBB0AF9584119797B23A | SHA256:4826C0D860AF884D3343CA6460B0006A7A2CE7DBCCC4D743208585D997CC5FD1 | |||
| 2936 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{A5C6479F-2157-4D70-BB05-51495A96CC12}.tmp | binary | |
MD5:5D4D94EE7E06BBB0AF9584119797B23A | SHA256:4826C0D860AF884D3343CA6460B0006A7A2CE7DBCCC4D743208585D997CC5FD1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
14
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2936 | WINWORD.EXE | POST | 302 | 23.213.166.81:80 | http://go.microsoft.com/fwlink/?LinkID=120750 | unknown | — | — | whitelisted |
2936 | WINWORD.EXE | POST | 302 | 23.213.166.81:80 | http://go.microsoft.com/fwlink/?LinkID=120751 | unknown | — | — | whitelisted |
2936 | WINWORD.EXE | POST | 302 | 23.213.166.81:80 | http://go.microsoft.com/fwlink/?LinkID=120752 | unknown | — | — | whitelisted |
1444 | sipnotify.exe | HEAD | 503 | 23.67.143.243:80 | http://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE2JgkA?v=133902531648900000 | unknown | — | — | whitelisted |
2936 | WINWORD.EXE | GET | 200 | 52.109.32.97:80 | http://office14client.microsoft.com/config14?UILCID=1033&CLCID=1033&ILCID=1033&HelpLCID=1033&App={019C826E-445A-4649-A5B0-0BF08FCC4EEE}&build=14.0.6023 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2936 | WINWORD.EXE | 23.213.166.81:80 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
2936 | WINWORD.EXE | 40.91.76.224:443 | activation.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2936 | WINWORD.EXE | 52.109.32.97:80 | office14client.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
1120 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
1444 | sipnotify.exe | 23.67.143.243:80 | query.prod.cms.rt.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
activation.sls.microsoft.com |
| whitelisted |
office14client.microsoft.com |
| whitelisted |
query.prod.cms.rt.microsoft.com |
| whitelisted |