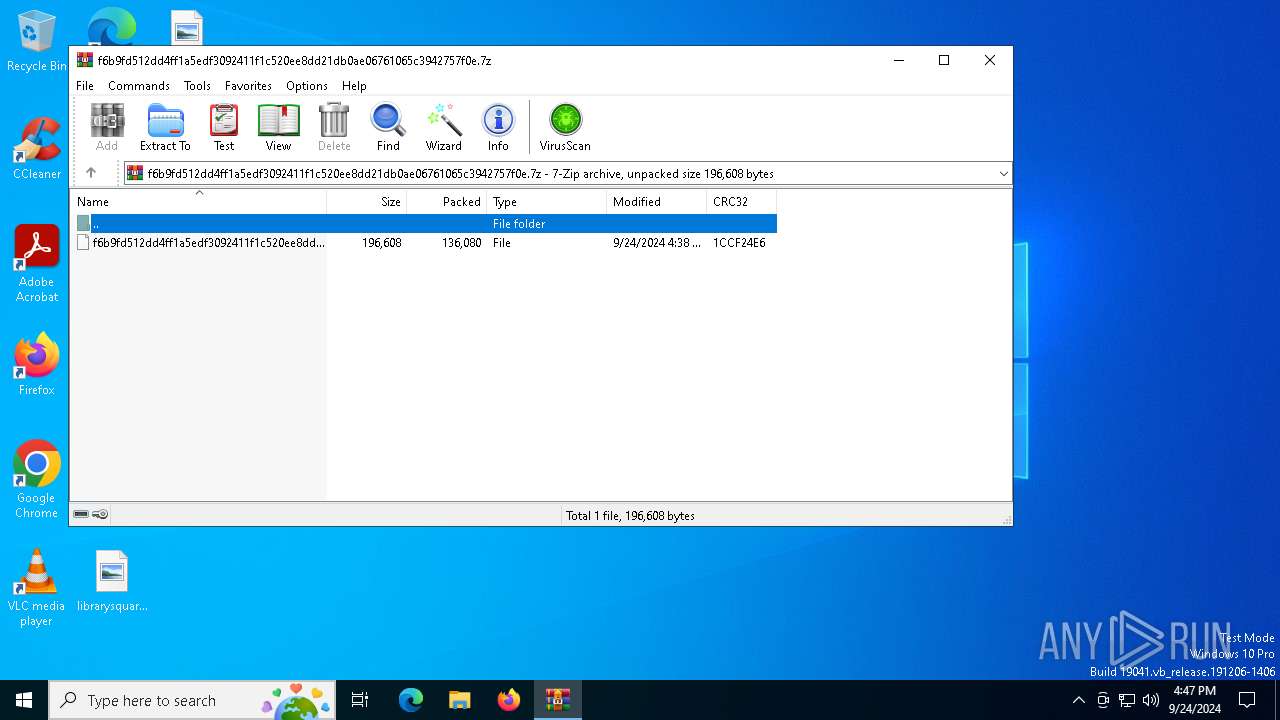
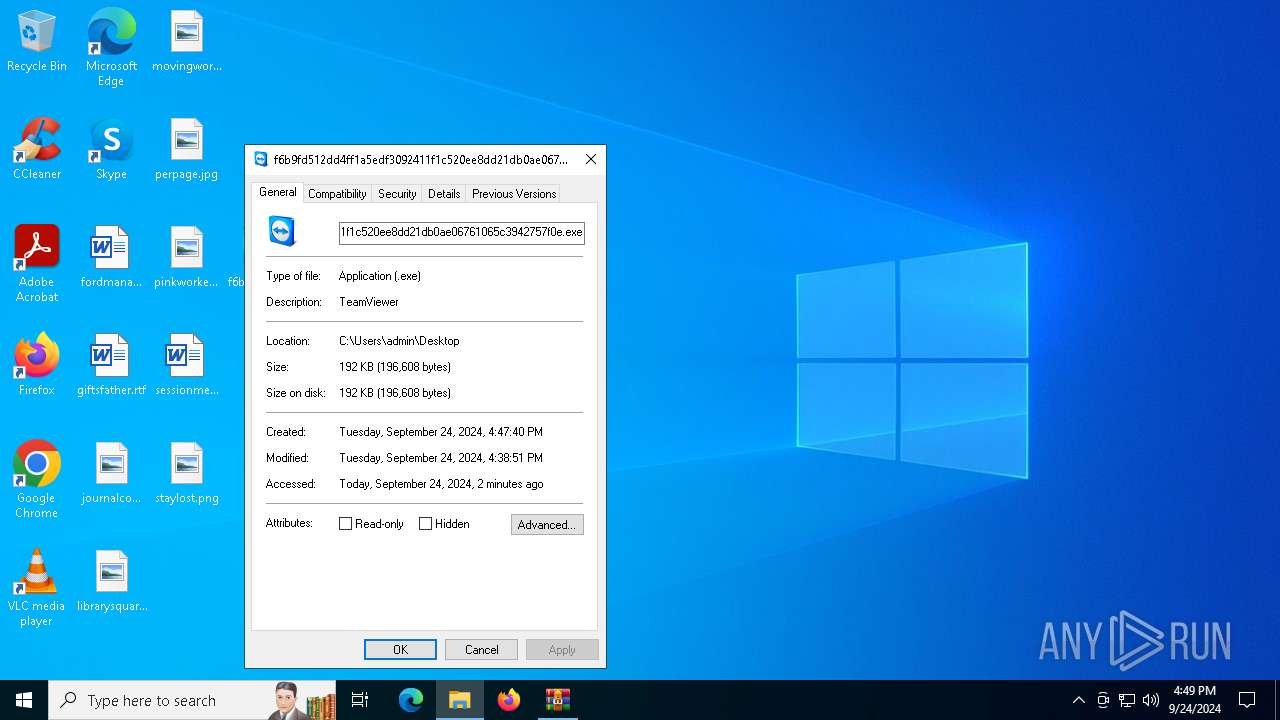
| File name: | f6b9fd512dd4ff1a5edf3092411f1c520ee8dd21db0ae06761065c3942757f0e.7z |
| Full analysis: | https://app.any.run/tasks/df573616-8577-4081-b50d-3109029f65f3 |
| Verdict: | Malicious activity |
| Analysis date: | September 24, 2024, 16:47:20 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 98AA528FC09B135BE032F3EFC5DA1873 |
| SHA1: | 9669272906198FF3824A4293A97088E033B1170F |
| SHA256: | B0FC99B39A1B3A2DD6DBF57C3D46056C372C4123231D4B8FF7733655D38BCA78 |
| SSDEEP: | 3072:EVYTB9Qhul+s5rd58f0l5sAy/CMeZmSBTnnj/KXOICX+boy7iwSszu051E9:MQB9QhulHr4kG2Zm4jBs7icuQ1i |
MALICIOUS
No malicious indicators.SUSPICIOUS
Application launched itself
- f6b9fd512dd4ff1a5edf3092411f1c520ee8dd21db0ae06761065c3942757f0e.exe (PID: 4152)
- lsass.exe (PID: 6108)
- f6b9fd512dd4ff1a5edf3092411f1c520ee8dd21db0ae06761065c3942757f0e.exe (PID: 1332)
- f6b9fd512dd4ff1a5edf3092411f1c520ee8dd21db0ae06761065c3942757f0e.exe (PID: 5212)
- f6b9fd512dd4ff1a5edf3092411f1c520ee8dd21db0ae06761065c3942757f0e.exe (PID: 2540)
- f6b9fd512dd4ff1a5edf3092411f1c520ee8dd21db0ae06761065c3942757f0e.exe (PID: 3164)
- lsass.exe (PID: 5364)
- f6b9fd512dd4ff1a5edf3092411f1c520ee8dd21db0ae06761065c3942757f0e.exe (PID: 5732)
- f6b9fd512dd4ff1a5edf3092411f1c520ee8dd21db0ae06761065c3942757f0e.exe (PID: 488)
- f6b9fd512dd4ff1a5edf3092411f1c520ee8dd21db0ae06761065c3942757f0e.exe (PID: 2852)
- f6b9fd512dd4ff1a5edf3092411f1c520ee8dd21db0ae06761065c3942757f0e.exe (PID: 6416)
- f6b9fd512dd4ff1a5edf3092411f1c520ee8dd21db0ae06761065c3942757f0e.exe (PID: 6708)
Starts itself from another location
- f6b9fd512dd4ff1a5edf3092411f1c520ee8dd21db0ae06761065c3942757f0e.exe (PID: 1236)
Executable content was dropped or overwritten
- f6b9fd512dd4ff1a5edf3092411f1c520ee8dd21db0ae06761065c3942757f0e.exe (PID: 1236)
The process executes via Task Scheduler
- default-browser-agent.exe (PID: 888)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7016)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 7136)
Manual execution by a user
- f6b9fd512dd4ff1a5edf3092411f1c520ee8dd21db0ae06761065c3942757f0e.exe (PID: 3164)
- f6b9fd512dd4ff1a5edf3092411f1c520ee8dd21db0ae06761065c3942757f0e.exe (PID: 5212)
- notepad++.exe (PID: 5900)
- f6b9fd512dd4ff1a5edf3092411f1c520ee8dd21db0ae06761065c3942757f0e.exe (PID: 6708)
- f6b9fd512dd4ff1a5edf3092411f1c520ee8dd21db0ae06761065c3942757f0e.exe (PID: 2540)
- f6b9fd512dd4ff1a5edf3092411f1c520ee8dd21db0ae06761065c3942757f0e.exe (PID: 6416)
The process uses the downloaded file
- WinRAR.exe (PID: 7016)
Application launched itself
- firefox.exe (PID: 5244)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
162
Monitored processes
28
Malicious processes
0
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 376 | "C:\Users\admin\AppData\Local\Temp\lsass.exe" | C:\Users\admin\AppData\Local\Temp\lsass.exe | — | lsass.exe | |||||||||||
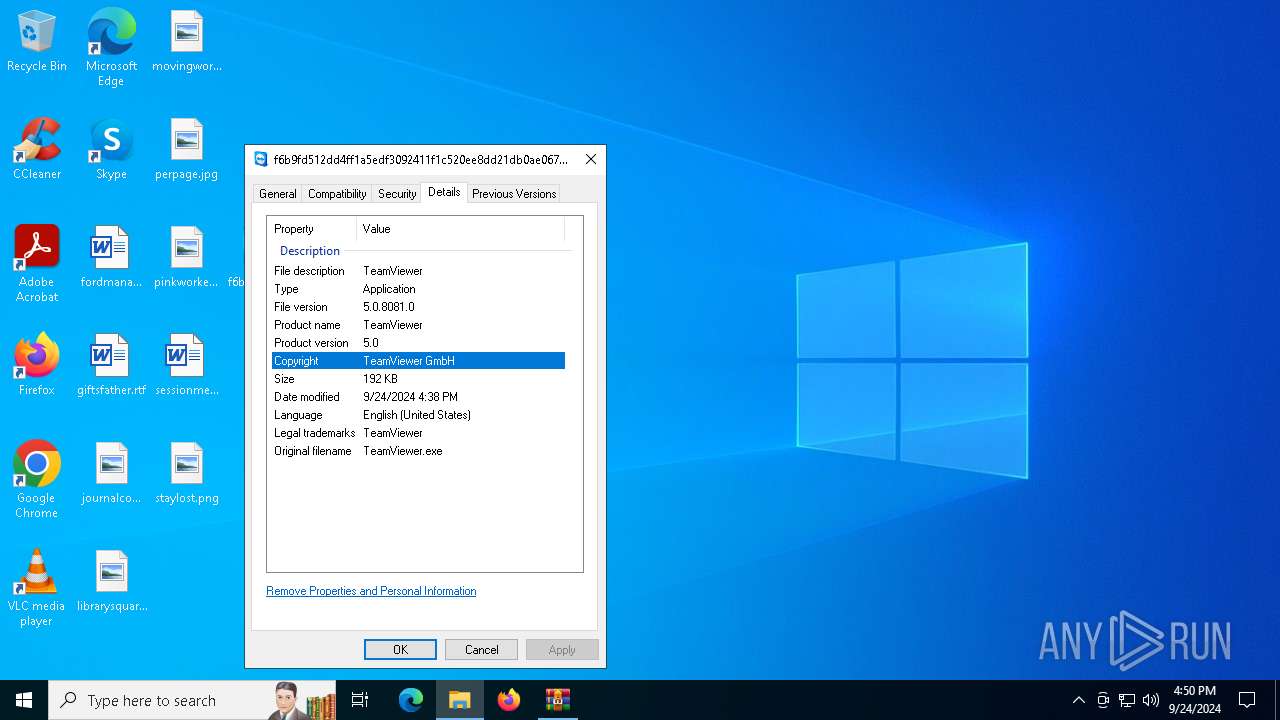
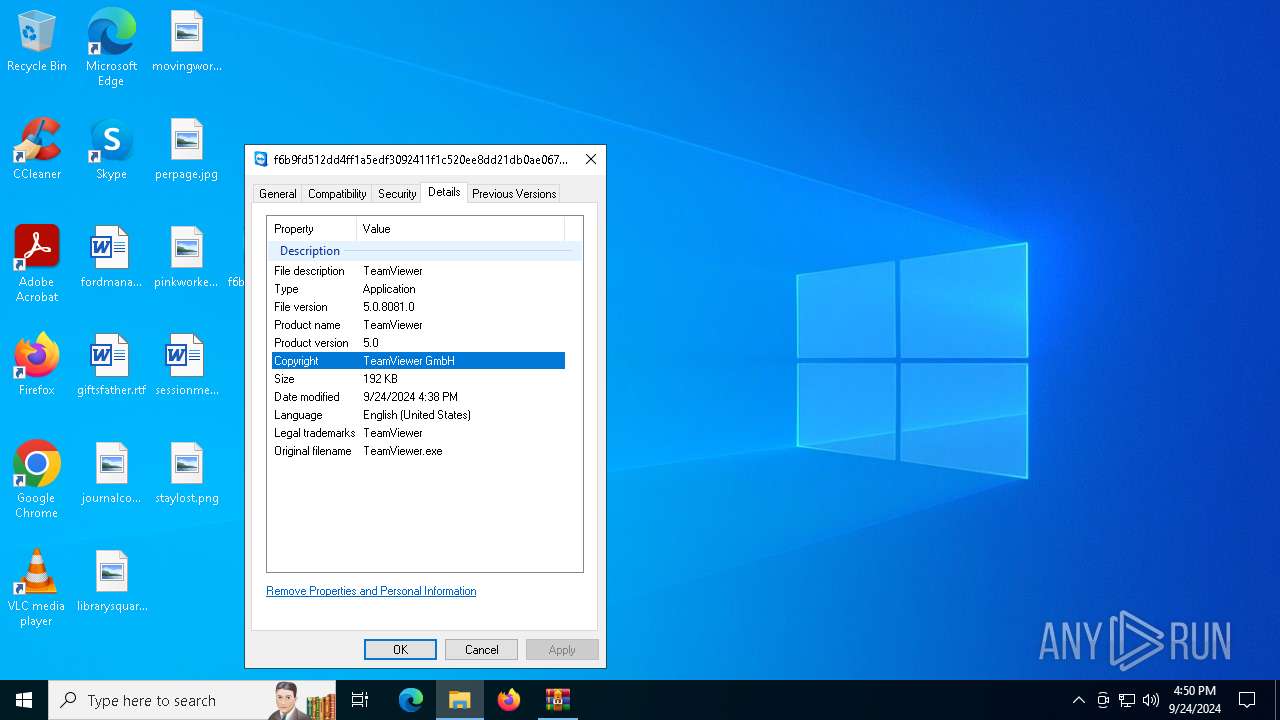
User: admin Company: TeamViewer GmbH Integrity Level: MEDIUM Description: TeamViewer Version: 5.0.8081.0 Modules
| |||||||||||||||
| 488 | "C:\Users\admin\Desktop\f6b9fd512dd4ff1a5edf3092411f1c520ee8dd21db0ae06761065c3942757f0e.exe" | C:\Users\admin\Desktop\f6b9fd512dd4ff1a5edf3092411f1c520ee8dd21db0ae06761065c3942757f0e.exe | — | f6b9fd512dd4ff1a5edf3092411f1c520ee8dd21db0ae06761065c3942757f0e.exe | |||||||||||
User: admin Company: TeamViewer GmbH Integrity Level: MEDIUM Description: TeamViewer Exit code: 0 Version: 5.0.8081.0 Modules
| |||||||||||||||
| 888 | "C:\Program Files\Mozilla Firefox\default-browser-agent.exe" do-task "308046B0AF4A39CB" | C:\Program Files\Mozilla Firefox\default-browser-agent.exe | — | svchost.exe | |||||||||||
User: admin Company: Mozilla Foundation Integrity Level: MEDIUM Exit code: 2147500037 Version: 123.0 Modules
| |||||||||||||||
| 1072 | "C:\Users\admin\Desktop\f6b9fd512dd4ff1a5edf3092411f1c520ee8dd21db0ae06761065c3942757f0e.exe" | C:\Users\admin\Desktop\f6b9fd512dd4ff1a5edf3092411f1c520ee8dd21db0ae06761065c3942757f0e.exe | — | f6b9fd512dd4ff1a5edf3092411f1c520ee8dd21db0ae06761065c3942757f0e.exe | |||||||||||
User: admin Company: TeamViewer GmbH Integrity Level: MEDIUM Description: TeamViewer Exit code: 0 Version: 5.0.8081.0 Modules
| |||||||||||||||
| 1236 | "C:\Users\admin\Desktop\f6b9fd512dd4ff1a5edf3092411f1c520ee8dd21db0ae06761065c3942757f0e.exe" | C:\Users\admin\Desktop\f6b9fd512dd4ff1a5edf3092411f1c520ee8dd21db0ae06761065c3942757f0e.exe | f6b9fd512dd4ff1a5edf3092411f1c520ee8dd21db0ae06761065c3942757f0e.exe | ||||||||||||
User: admin Company: TeamViewer GmbH Integrity Level: MEDIUM Description: TeamViewer Exit code: 0 Version: 5.0.8081.0 Modules
| |||||||||||||||
| 1332 | "C:\Users\admin\Desktop\f6b9fd512dd4ff1a5edf3092411f1c520ee8dd21db0ae06761065c3942757f0e.exe" | C:\Users\admin\Desktop\f6b9fd512dd4ff1a5edf3092411f1c520ee8dd21db0ae06761065c3942757f0e.exe | — | f6b9fd512dd4ff1a5edf3092411f1c520ee8dd21db0ae06761065c3942757f0e.exe | |||||||||||
User: admin Company: TeamViewer GmbH Integrity Level: MEDIUM Description: TeamViewer Exit code: 0 Version: 5.0.8081.0 Modules
| |||||||||||||||
| 1644 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2256 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2540 | "C:\Users\admin\Desktop\f6b9fd512dd4ff1a5edf3092411f1c520ee8dd21db0ae06761065c3942757f0e.exe" | C:\Users\admin\Desktop\f6b9fd512dd4ff1a5edf3092411f1c520ee8dd21db0ae06761065c3942757f0e.exe | — | explorer.exe | |||||||||||
User: admin Company: TeamViewer GmbH Integrity Level: MEDIUM Description: TeamViewer Exit code: 0 Version: 5.0.8081.0 Modules
| |||||||||||||||
| 2852 | "C:\Users\admin\Desktop\f6b9fd512dd4ff1a5edf3092411f1c520ee8dd21db0ae06761065c3942757f0e.exe" | C:\Users\admin\Desktop\f6b9fd512dd4ff1a5edf3092411f1c520ee8dd21db0ae06761065c3942757f0e.exe | — | f6b9fd512dd4ff1a5edf3092411f1c520ee8dd21db0ae06761065c3942757f0e.exe | |||||||||||
User: admin Company: TeamViewer GmbH Integrity Level: MEDIUM Description: TeamViewer Exit code: 0 Version: 5.0.8081.0 Modules
| |||||||||||||||
Total events
4 889
Read events
4 879
Write events
10
Delete events
0
Modification events
| (PID) Process: | (7016) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (7016) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\f6b9fd512dd4ff1a5edf3092411f1c520ee8dd21db0ae06761065c3942757f0e.7z | |||
| (PID) Process: | (7016) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7016) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7016) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7016) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
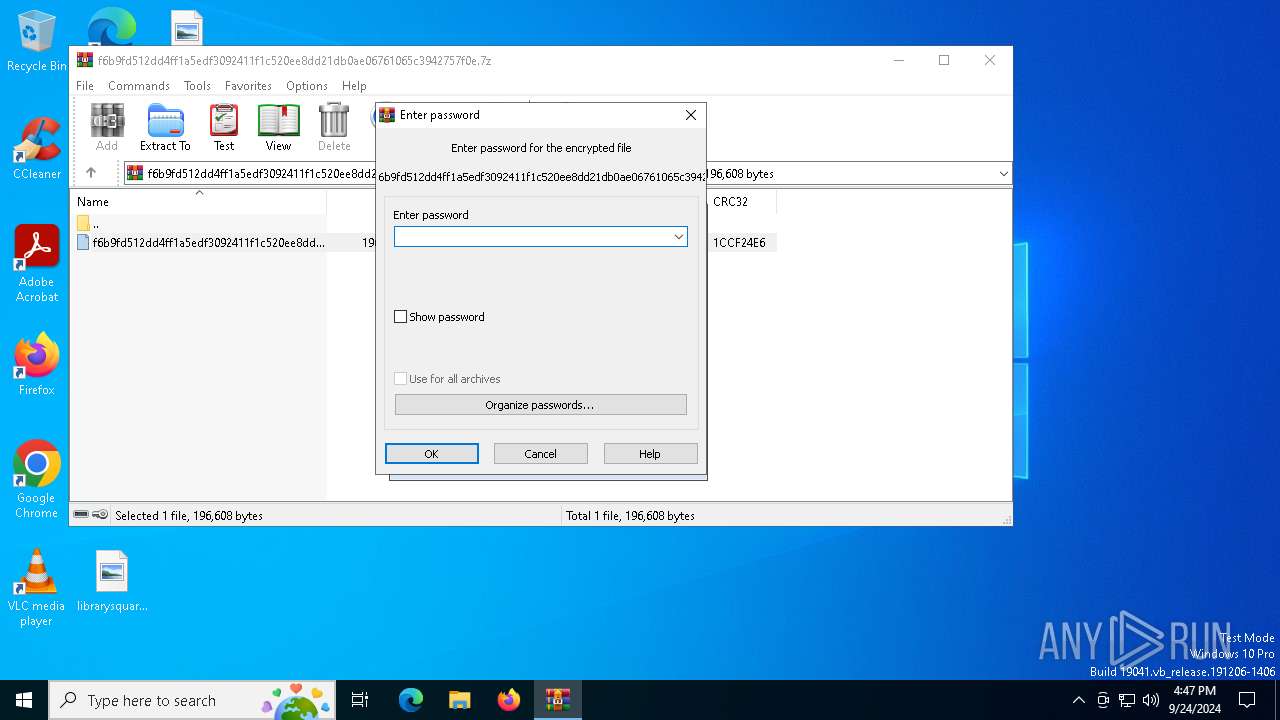
| (PID) Process: | (7016) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (1236) f6b9fd512dd4ff1a5edf3092411f1c520ee8dd21db0ae06761065c3942757f0e.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Windows Firewall |
Value: C:\Users\admin\AppData\Local\Temp\lsass.exe | |||
| (PID) Process: | (1236) f6b9fd512dd4ff1a5edf3092411f1c520ee8dd21db0ae06761065c3942757f0e.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Windows Firewall |
Value: C:\Users\admin\AppData\Local\Temp\lsass.exe | |||
| (PID) Process: | (5088) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
Executable files
2
Suspicious files
0
Text files
8
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7016 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb7016.26618\f6b9fd512dd4ff1a5edf3092411f1c520ee8dd21db0ae06761065c3942757f0e | executable | |
MD5:F314D09FB4A146E2C6FA6663554DDE16 | SHA256:F6B9FD512DD4FF1A5EDF3092411F1C520EE8DD21DB0AE06761065C3942757F0E | |||
| 5900 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\session.xml | text | |
MD5:0373799D50AC4F548CEBC0044D868E84 | SHA256:40CC96C544589DB72243BA931CCAD21567A85EA680AF06309837B3B60C45CEEC | |||
| 5900 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\stylers.xml | xml | |
MD5:312281C4126FA897EF21A7E8CCB8D495 | SHA256:53B4BE3ED1CFD712E53542B30CFE30C5DB35CC48BE7C57727DFEC26C9E882E90 | |||
| 5088 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Background Tasks Profiles\93u99co2.MozillaBackgroundTask-308046B0AF4A39CB-defaultagent\datareporting\glean\db\data.safe.bin | dbf | |
MD5:7D3D11283370585B060D50A12715851A | SHA256:86BFF840E1BEC67B7C91F97F4D37E3A638C5FDC7B56AAE210B01745F292347B9 | |||
| 5900 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\langs.xml | xml | |
MD5:FE22EC5755BC98988F9656F73B2E6FB8 | SHA256:F972C425CE176E960F6347F1CA2F64A8CE2B95A375C33A03E57538052BA0624D | |||
| 5088 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Background Tasks Profiles\93u99co2.MozillaBackgroundTask-308046B0AF4A39CB-defaultagent\prefs.js | text | |
MD5:05715CDC0C321FBC61AF9EF0E720C5A2 | SHA256:5194285A11DFDD8EEBB2815817478E34C7552EC79C8487F75DE8312A5DAB9C3B | |||
| 5088 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Background Tasks Profiles\93u99co2.MozillaBackgroundTask-308046B0AF4A39CB-defaultagent\datareporting\glean\db\data.safe.tmp | dbf | |
MD5:7D3D11283370585B060D50A12715851A | SHA256:86BFF840E1BEC67B7C91F97F4D37E3A638C5FDC7B56AAE210B01745F292347B9 | |||
| 1236 | f6b9fd512dd4ff1a5edf3092411f1c520ee8dd21db0ae06761065c3942757f0e.exe | C:\Users\admin\AppData\Local\Temp\lsass.exe | executable | |
MD5:F314D09FB4A146E2C6FA6663554DDE16 | SHA256:F6B9FD512DD4FF1A5EDF3092411F1C520EE8DD21DB0AE06761065C3942757F0E | |||
| 5900 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\shortcuts.xml | text | |
MD5:F11D96162BC521F5CF49FFE6B6841C9B | SHA256:BE9AEAEAB5A2E4899BA7E582274BA592C1B9BAF688B340A754B8EF32B23CFA9C | |||
| 5900 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\config.xml | xml | |
MD5:A2ED875AA42589077C4D08F4F8912018 | SHA256:77B0174D655F327C1FC9520B4F8831ECD82E98351B26BB9C2EDD98FF0CD63A2D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
56
DNS requests
60
Threats
74
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1952 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6196 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
1636 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1952 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1636 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6832 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1636 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1636 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6196 | svchost.exe | 40.126.32.76:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
phobiia.dyndns.info |
| unknown |
nexusrules.officeapps.live.com |
| whitelisted |
browser.pipe.aria.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.dyndns .info Domain |
2256 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.dyndns. Domain |
2256 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.dyndns .info Domain |
2256 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.dyndns. Domain |
2256 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.dyndns. Domain |
2256 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.dyndns .info Domain |
2256 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.dyndns .info Domain |
2256 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.dyndns. Domain |
2256 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.dyndns .info Domain |
2256 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.dyndns. Domain |
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: error while getting certificate informations
|