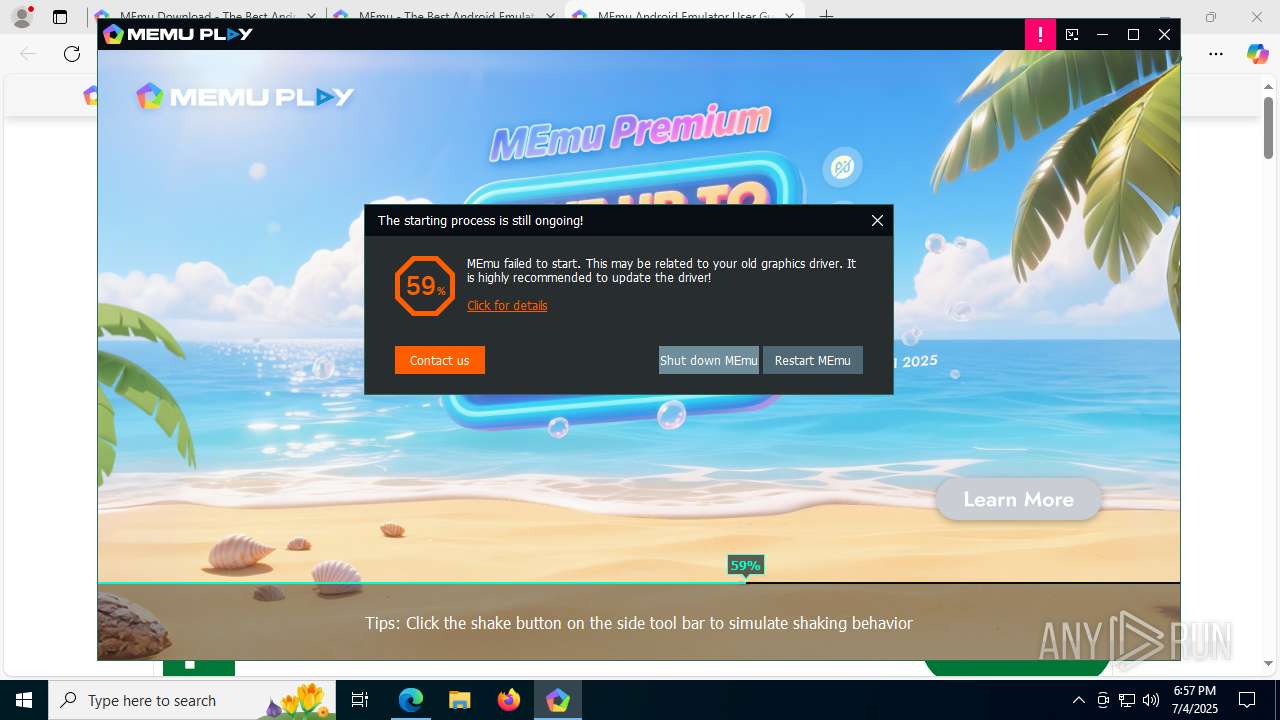
| URL: | https://www.memuplay.com/download-memu-on-pc.html |
| Full analysis: | https://app.any.run/tasks/2ead2246-3ee8-4663-aec9-4fb4979431a3 |
| Verdict: | Malicious activity |
| Analysis date: | July 04, 2025, 18:52:28 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 2081FBA0BCE7F3B3E8B07675CA3A4146 |
| SHA1: | A676FC12EDABB10D72F1C595B4FD396B039FF7CF |
| SHA256: | B0DCC2AC1CB43535C24589211C0637FB917CDC41111EC06E946AB181F7CC1E61 |
| SSDEEP: | 3:N8DSLdZ38JIeEcNGn:2OLdZMGzcQ |
MALICIOUS
Executing a file with an untrusted certificate
- MEmuDrvInst.exe (PID: 7460)
- MemuService.exe (PID: 1868)
- 7za.exe (PID: 4808)
Registers / Runs the DLL via REGSVR32.EXE
- Setup.exe (PID: 5168)
SUSPICIOUS
There is functionality for taking screenshot (YARA)
- MEmu-setup-abroad-07ea07f6.exe (PID: 684)
- Setup.exe (PID: 5168)
- MEmu.exe (PID: 3972)
Potential Corporate Privacy Violation
- MEmu-setup-abroad-07ea07f6.exe (PID: 684)
Creates file in the systems drive root
- MEmu-setup-abroad-07ea07f6.exe (PID: 684)
Drops 7-zip archiver for unpacking
- Setup.exe (PID: 5168)
- 7za.exe (PID: 3672)
Process drops legitimate windows executable
- Setup.exe (PID: 5168)
- 7za.exe (PID: 3672)
- 7za.exe (PID: 724)
- 7za.exe (PID: 1868)
Windows service management via SC.EXE
- sc.exe (PID: 7300)
- sc.exe (PID: 7540)
- sc.exe (PID: 4048)
- sc.exe (PID: 6460)
- sc.exe (PID: 2880)
- sc.exe (PID: 4984)
- sc.exe (PID: 7120)
- sc.exe (PID: 2296)
- sc.exe (PID: 5908)
- sc.exe (PID: 5988)
- sc.exe (PID: 7636)
- sc.exe (PID: 5080)
- sc.exe (PID: 1932)
- sc.exe (PID: 4960)
- sc.exe (PID: 1964)
- sc.exe (PID: 620)
- sc.exe (PID: 1132)
- sc.exe (PID: 8012)
- sc.exe (PID: 7440)
- sc.exe (PID: 5460)
- sc.exe (PID: 3788)
- sc.exe (PID: 1612)
- sc.exe (PID: 4380)
- sc.exe (PID: 7132)
- sc.exe (PID: 6860)
- sc.exe (PID: 3388)
Executable content was dropped or overwritten
- Setup.exe (PID: 5168)
- 7za.exe (PID: 3672)
- 7za.exe (PID: 724)
- 7za.exe (PID: 1868)
- MEmuDrvInst.exe (PID: 7460)
The process creates files with name similar to system file names
- 7za.exe (PID: 724)
The process drops C-runtime libraries
- 7za.exe (PID: 3672)
- 7za.exe (PID: 724)
- 7za.exe (PID: 1868)
Drops a system driver (possible attempt to evade defenses)
- 7za.exe (PID: 724)
- MEmuDrvInst.exe (PID: 7460)
Reads security settings of Internet Explorer
- MEmuDrvInst.exe (PID: 7460)
Creates files in the driver directory
- MEmuDrvInst.exe (PID: 7460)
Creates/Modifies COM task schedule object
- MEmuManage.exe (PID: 4648)
- regsvr32.exe (PID: 2992)
- regsvr32.exe (PID: 8132)
Executes as Windows Service
- MemuService.exe (PID: 1868)
Creates a software uninstall entry
- Setup.exe (PID: 5168)
Searches for installed software
- MEmuConsole.exe (PID: 3840)
- MEmu.exe (PID: 3972)
Starts CMD.EXE for commands execution
- MEmu.exe (PID: 3972)
Starts application with an unusual extension
- cmd.exe (PID: 7372)
Process uses IPCONFIG to clear DNS cache
- cmd.exe (PID: 3576)
There is functionality for VM detection antiVM strings (YARA)
- MEmu.exe (PID: 3972)
Application launched itself
- adb.exe (PID: 7480)
INFO
Executable content was dropped or overwritten
- msedge.exe (PID: 5808)
Application launched itself
- msedge.exe (PID: 5808)
Checks supported languages
- identity_helper.exe (PID: 7524)
- MEmu-setup-abroad-07ea07f6.exe (PID: 684)
- Setup.exe (PID: 5168)
- 7za.exe (PID: 3672)
- 7za.exe (PID: 724)
- 7za.exe (PID: 1868)
- MEmuDrvInst.exe (PID: 7460)
- MEmuManage.exe (PID: 4648)
- MEmuSVC.exe (PID: 7944)
- MEmuSVC.exe (PID: 4104)
- MEmuSVC.exe (PID: 7960)
- MEmuSVC.exe (PID: 6200)
- MemuService.exe (PID: 1868)
- MEmuRepair.exe (PID: 4768)
- MEmuManage.exe (PID: 7456)
- MEmuSVC.exe (PID: 6508)
- MEmuManage.exe (PID: 4552)
- MEmuManage.exe (PID: 4880)
- memuc.exe (PID: 516)
- MEmuSVC.exe (PID: 6128)
- MEmuConsole.exe (PID: 3840)
- MEmuSVC.exe (PID: 4692)
- MEmu.exe (PID: 320)
- MEmuSVC.exe (PID: 7072)
- screenrecord.exe (PID: 7860)
- MEmuRepair.exe (PID: 6760)
- MEmu.exe (PID: 2432)
- MEmuManage.exe (PID: 8124)
- MEmuManage.exe (PID: 6528)
- MEmuManage.exe (PID: 5432)
- MEmuSVC.exe (PID: 7468)
- screenrecord.exe (PID: 7520)
- MEmu.exe (PID: 3972)
- MEmuHeadless.exe (PID: 7500)
- MEmuSVC.exe (PID: 5232)
- MEmuManage.exe (PID: 7432)
- chcp.com (PID: 4724)
- 7za.exe (PID: 4808)
- adb.exe (PID: 7480)
- adb.exe (PID: 8004)
Reads the computer name
- identity_helper.exe (PID: 7524)
- MEmu-setup-abroad-07ea07f6.exe (PID: 684)
- Setup.exe (PID: 5168)
- 7za.exe (PID: 3672)
- 7za.exe (PID: 724)
- 7za.exe (PID: 1868)
- MEmuDrvInst.exe (PID: 7460)
- MEmuSVC.exe (PID: 6200)
- MemuService.exe (PID: 1868)
- MEmuManage.exe (PID: 4648)
- MEmuSVC.exe (PID: 7944)
- MEmuRepair.exe (PID: 4768)
- MEmuManage.exe (PID: 7456)
- MEmuSVC.exe (PID: 6508)
- MEmuManage.exe (PID: 4552)
- MEmuManage.exe (PID: 4880)
- MEmu.exe (PID: 320)
- MEmuSVC.exe (PID: 6128)
- MEmuConsole.exe (PID: 3840)
- MEmuSVC.exe (PID: 4692)
- MEmuSVC.exe (PID: 7072)
- MEmu.exe (PID: 2432)
- MEmuRepair.exe (PID: 6760)
- MEmuManage.exe (PID: 8124)
- MEmuManage.exe (PID: 6528)
- MEmuManage.exe (PID: 5432)
- MEmuManage.exe (PID: 7432)
- MEmu.exe (PID: 3972)
- MEmuSVC.exe (PID: 7468)
- MEmuHeadless.exe (PID: 7500)
- MEmuSVC.exe (PID: 5232)
- adb.exe (PID: 8004)
Reads Environment values
- identity_helper.exe (PID: 7524)
Creates files or folders in the user directory
- MEmu-setup-abroad-07ea07f6.exe (PID: 684)
- Setup.exe (PID: 5168)
- MEmu.exe (PID: 3972)
Reads CPU info
- MEmu-setup-abroad-07ea07f6.exe (PID: 684)
- Setup.exe (PID: 5168)
- MEmuRepair.exe (PID: 4768)
- MEmuConsole.exe (PID: 3840)
- MEmu.exe (PID: 2432)
- MEmuRepair.exe (PID: 6760)
- MEmu.exe (PID: 3972)
Creates files in the program directory
- MEmu-setup-abroad-07ea07f6.exe (PID: 684)
- Setup.exe (PID: 5168)
- 7za.exe (PID: 3672)
- 7za.exe (PID: 724)
- 7za.exe (PID: 1868)
- MemuService.exe (PID: 1868)
- MEmuSVC.exe (PID: 4692)
- MEmuSVC.exe (PID: 6128)
- MEmuConsole.exe (PID: 3840)
- MEmu.exe (PID: 3972)
- MEmuHeadless.exe (PID: 7500)
- MEmuSVC.exe (PID: 7468)
- 7za.exe (PID: 4808)
Checks proxy server information
- slui.exe (PID: 4456)
- MEmuConsole.exe (PID: 3840)
- MEmu.exe (PID: 3972)
Reads the software policy settings
- slui.exe (PID: 4456)
- MEmuDrvInst.exe (PID: 7460)
The sample compiled with english language support
- Setup.exe (PID: 5168)
- 7za.exe (PID: 3672)
- 7za.exe (PID: 724)
- MEmuDrvInst.exe (PID: 7460)
- 7za.exe (PID: 1868)
Reads the machine GUID from the registry
- MEmuDrvInst.exe (PID: 7460)
- MEmuConsole.exe (PID: 3840)
- MEmu.exe (PID: 3972)
Reads security settings of Internet Explorer
- explorer.exe (PID: 7300)
- explorer.exe (PID: 5848)
Create files in a temporary directory
- MEmu.exe (PID: 3972)
- adb.exe (PID: 8004)
Changes the display of characters in the console
- cmd.exe (PID: 7372)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
336
Monitored processes
179
Malicious processes
8
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 320 | "C:\Program Files\Microvirt\MEmu\MEmu.exe" adjustconfig MEmu | C:\Program Files\Microvirt\MEmu\MEmu.exe | — | Setup.exe | |||||||||||
User: admin Company: Microvirt Software Technology Co. Ltd. Integrity Level: HIGH Description: MEmu App Player Exit code: 0 Version: 9.2.3.0 Modules
| |||||||||||||||
| 516 | "C:\Program Files\Microvirt\MEmu\MEmuc.exe" create 96 | C:\Program Files\Microvirt\MEmu\memuc.exe | — | Setup.exe | |||||||||||
User: admin Company: Microvirt Software Technology Co. Ltd. Integrity Level: HIGH Description: memuc Exit code: 0 Version: 9.2.3.0 Modules
| |||||||||||||||
| 620 | "C:\WINDOWS\system32\sc" query MEmuNetLwf | C:\Windows\SysWOW64\sc.exe | — | Setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 1060 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
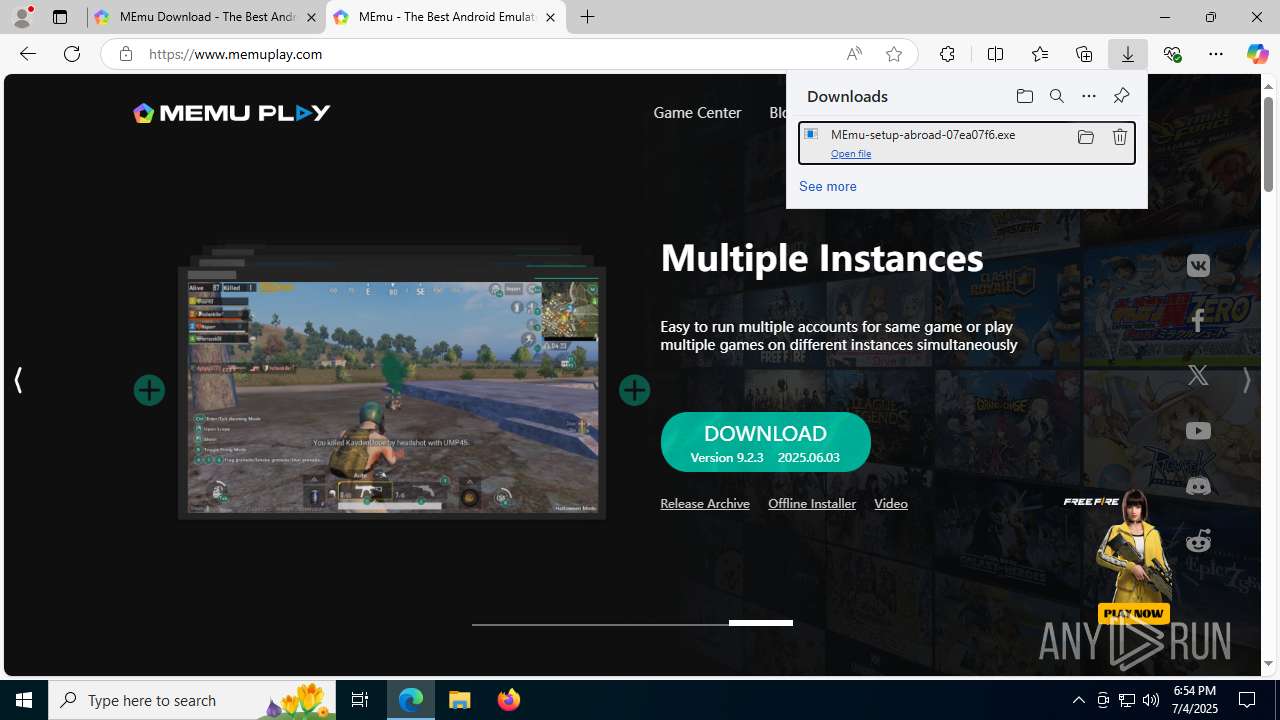
| 684 | "C:\Users\admin\Downloads\MEmu-setup-abroad-07ea07f6.exe" | C:\Users\admin\Downloads\MEmu-setup-abroad-07ea07f6.exe | msedge.exe | ||||||||||||
User: admin Company: Microvirt Software Technology Co. Ltd. Integrity Level: HIGH Description: MEmu Installer Exit code: 0 Version: 9.0.0.0 Modules
| |||||||||||||||
| 724 | "C:\Program Files\Microvirt\tempDir\7za.exe" x -y -aoa "C:\Program Files\Microvirt\MEmuHyperv64.7z" "-oC:\Program Files\Microvirt\MEmuHyperv" | C:\Program Files\Microvirt\tempDir\7za.exe | Setup.exe | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: HIGH Description: 7-Zip Console Exit code: 0 Version: 23.01 Modules
| |||||||||||||||
| 1132 | "C:\WINDOWS\system32\sc" query MEmuNetAdp | C:\Windows\SysWOW64\sc.exe | — | Setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 1060 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1156 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_search_indexer.mojom.SearchIndexerInterfaceBroker --lang=en-US --service-sandbox-type=search_indexer --disable-quic --message-loop-type-ui --string-annotations --always-read-main-dll --field-trial-handle=7804,i,10364066384516008841,11856015515002953602,262144 --variations-seed-version --mojo-platform-channel-handle=6284 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1300 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | adb.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1520 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=41 --always-read-main-dll --field-trial-handle=5528,i,10364066384516008841,11856015515002953602,262144 --variations-seed-version --mojo-platform-channel-handle=5768 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1612 | C:\WINDOWS\System32\sc query MEmuSVC | C:\Windows\SysWOW64\sc.exe | — | Setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
27 420
Read events
26 176
Write events
409
Delete events
835
Modification events
| (PID) Process: | (5808) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (5808) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (5808) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (5808) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (5808) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 6894DB47B5972F00 | |||
| (PID) Process: | (5808) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328416 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {13A7C770-7220-4760-A59E-21C08A5FFEBF} | |||
| (PID) Process: | (5808) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328416 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {E4937261-6685-423E-BB4F-A6BA9A072A18} | |||
| (PID) Process: | (5808) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328416 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {38D4377E-503A-4A55-B69E-020A98FE4B0A} | |||
| (PID) Process: | (5808) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328416 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {1EB9F1FA-75A2-44E1-8DF6-880B91B7B29A} | |||
| (PID) Process: | (5808) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328416 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {AEF032A0-A2B2-4FBF-84E1-ECFC27030980} | |||
Executable files
237
Suspicious files
993
Text files
868
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5808 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old~RF175890.TMP | — | |
MD5:— | SHA256:— | |||
| 5808 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5808 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF1758af.TMP | — | |
MD5:— | SHA256:— | |||
| 5808 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF1758af.TMP | — | |
MD5:— | SHA256:— | |||
| 5808 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5808 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5808 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF1758af.TMP | — | |
MD5:— | SHA256:— | |||
| 5808 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5808 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF1758ed.TMP | — | |
MD5:— | SHA256:— | |||
| 5808 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF1758ed.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
60
TCP/UDP connections
270
DNS requests
264
Threats
38
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2132 | msedge.exe | GET | 200 | 150.171.28.11:80 | http://edge.microsoft.com/browsernetworktime/time/1/current?cup2key=2:QVD4pHkHC7W0raKkC7VutLPGbaANoWOPzQd7-GuWblM&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
8160 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2132 | msedge.exe | GET | 200 | 18.66.122.8:80 | http://www.memuplay.com/blog/wp-content/uploads/2016/03/getstarted-2-small.jpg | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.48.23.194:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2512 | svchost.exe | HEAD | 200 | 23.50.131.72:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1751966473&P2=404&P3=2&P4=GJu0rDS4HFq0vY%2b%2bQVlsKowbEi2o3jtNdki8SShqyTZ8xY%2fKTD3zgAHuW28zZf12IGaloTvMATmuY%2bX7JAKdvw%3d%3d | unknown | — | — | whitelisted |
8160 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2668 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2512 | svchost.exe | GET | 206 | 23.50.131.72:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1751966473&P2=404&P3=2&P4=GJu0rDS4HFq0vY%2b%2bQVlsKowbEi2o3jtNdki8SShqyTZ8xY%2fKTD3zgAHuW28zZf12IGaloTvMATmuY%2bX7JAKdvw%3d%3d | unknown | — | — | whitelisted |
2512 | svchost.exe | GET | 206 | 23.50.131.72:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1751966473&P2=404&P3=2&P4=GJu0rDS4HFq0vY%2b%2bQVlsKowbEi2o3jtNdki8SShqyTZ8xY%2fKTD3zgAHuW28zZf12IGaloTvMATmuY%2bX7JAKdvw%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3964 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2132 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2132 | msedge.exe | 150.171.28.11:80 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2132 | msedge.exe | 150.171.28.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2132 | msedge.exe | 92.123.104.45:443 | copilot.microsoft.com | Akamai International B.V. | DE | whitelisted |
2132 | msedge.exe | 18.66.122.58:443 | www.memuplay.com | AMAZON-02 | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
www.memuplay.com |
| whitelisted |
copilot.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
dl.memuplay.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
securepubads.g.doubleclick.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2132 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2132 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2132 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2132 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2132 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
2132 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
684 | MEmu-setup-abroad-07ea07f6.exe | Misc activity | INFO [ANY.RUN] USER_AGENTS Suspicious User-Agent (Mozilla/5.0) |
684 | MEmu-setup-abroad-07ea07f6.exe | Misc activity | INFO [ANY.RUN] USER_AGENTS Suspicious User-Agent (Mozilla/5.0) |
684 | MEmu-setup-abroad-07ea07f6.exe | Misc activity | INFO [ANY.RUN] USER_AGENTS Suspicious User-Agent (Mozilla/5.0) |
684 | MEmu-setup-abroad-07ea07f6.exe | Misc activity | INFO [ANY.RUN] USER_AGENTS Suspicious User-Agent (Mozilla/5.0) |
Process | Message |
|---|---|
MEmu-setup-abroad-07ea07f6.exe | Qt: Untested Windows version 10.0 detected!
|
MEmu-setup-abroad-07ea07f6.exe | QWindowsWindow::setGeometryDp: Unable to set geometry 21x14+320+100 on QWidgetWindow/'QCheckBoxClassWindow'. Resulting geometry: 120x14+320+100 (frame: 8, 31, 8, 8, custom margin: 0, 0, 0, 0, minimum size: 0x0, maximum size: 16777215x16777215).
|
MEmu-setup-abroad-07ea07f6.exe | QWindowsWindow::setGeometryDp: Unable to set geometry 55x14+320+100 on QWidgetWindow/'QLabelClassWindow'. Resulting geometry: 120x14+320+100 (frame: 8, 31, 8, 8, custom margin: 0, 0, 0, 0, minimum size: 0x0, maximum size: 16777215x16777215).
|
MEmu-setup-abroad-07ea07f6.exe | MainWindowDialog::downFinished : exe wait condition wake all
|
MEmu-setup-abroad-07ea07f6.exe | QThread: Destroyed while thread is still running
|
Setup.exe | Qt: Untested Windows version 10.0 detected!
|
Setup.exe | QWindowsWindow::setGeometryDp: Unable to set geometry 21x14+320+100 on QWidgetWindow/'QCheckBoxClassWindow'. Resulting geometry: 120x14+320+100 (frame: 8, 31, 8, 8, custom margin: 0, 0, 0, 0, minimum size: 0x0, maximum size: 16777215x16777215).
|
Setup.exe | QWindowsWindow::setGeometryDp: Unable to set geometry 55x14+320+100 on QWidgetWindow/'QLabelClassWindow'. Resulting geometry: 120x14+320+100 (frame: 8, 31, 8, 8, custom margin: 0, 0, 0, 0, minimum size: 0x0, maximum size: 16777215x16777215).
|