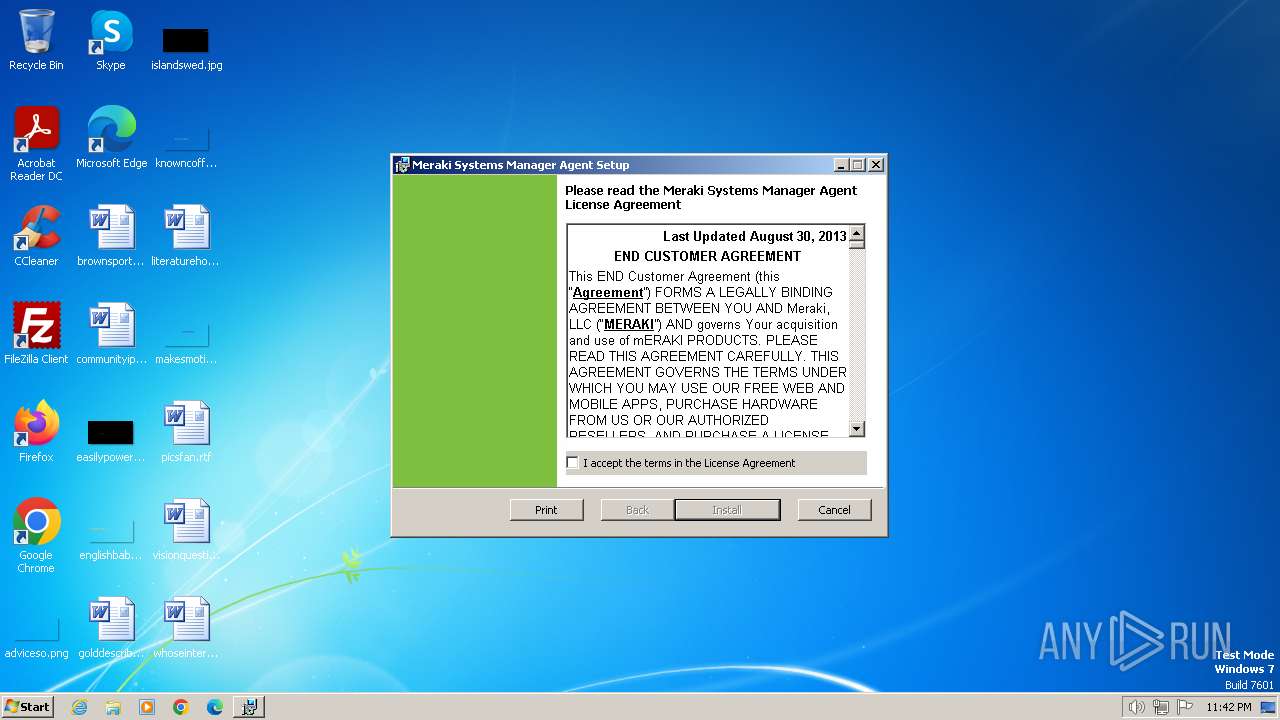
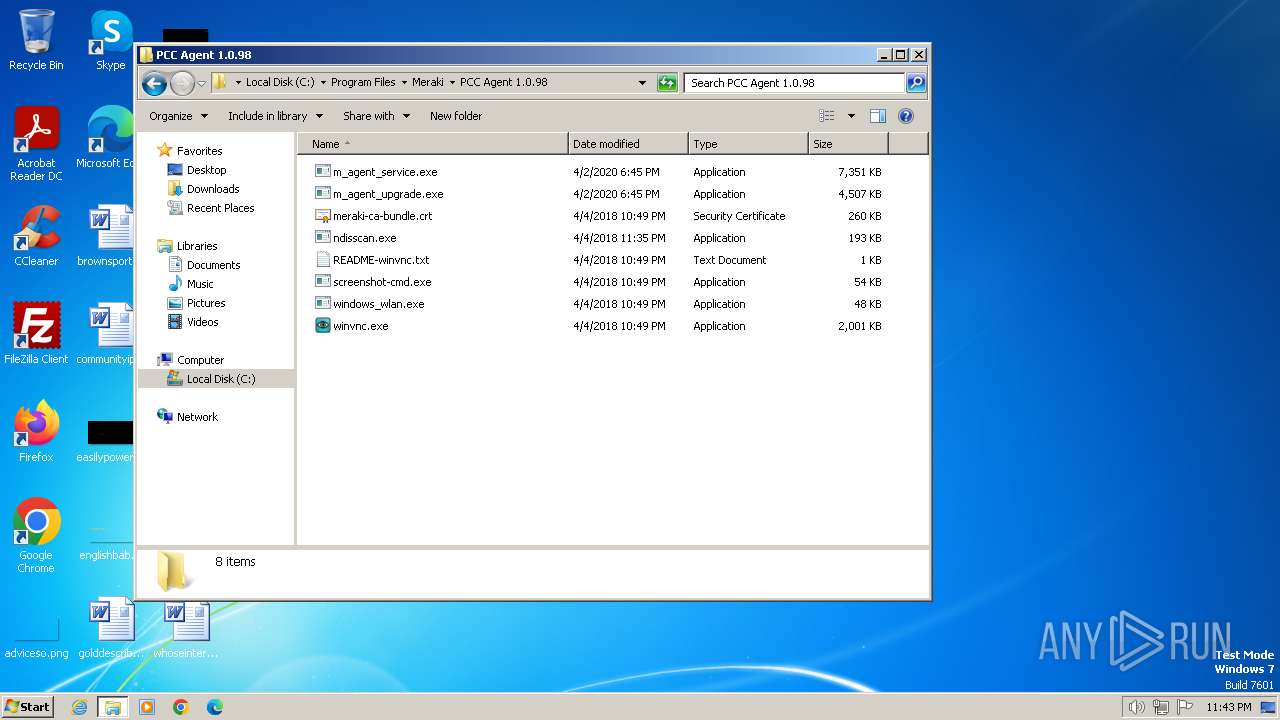
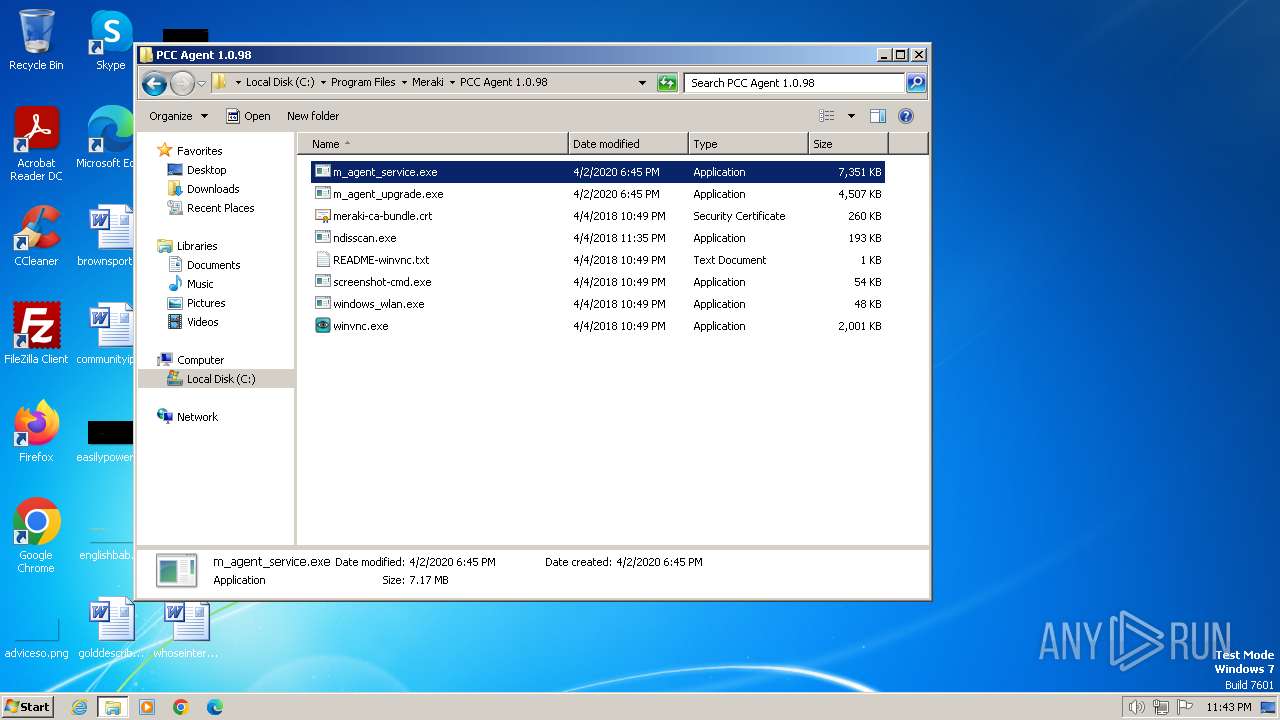
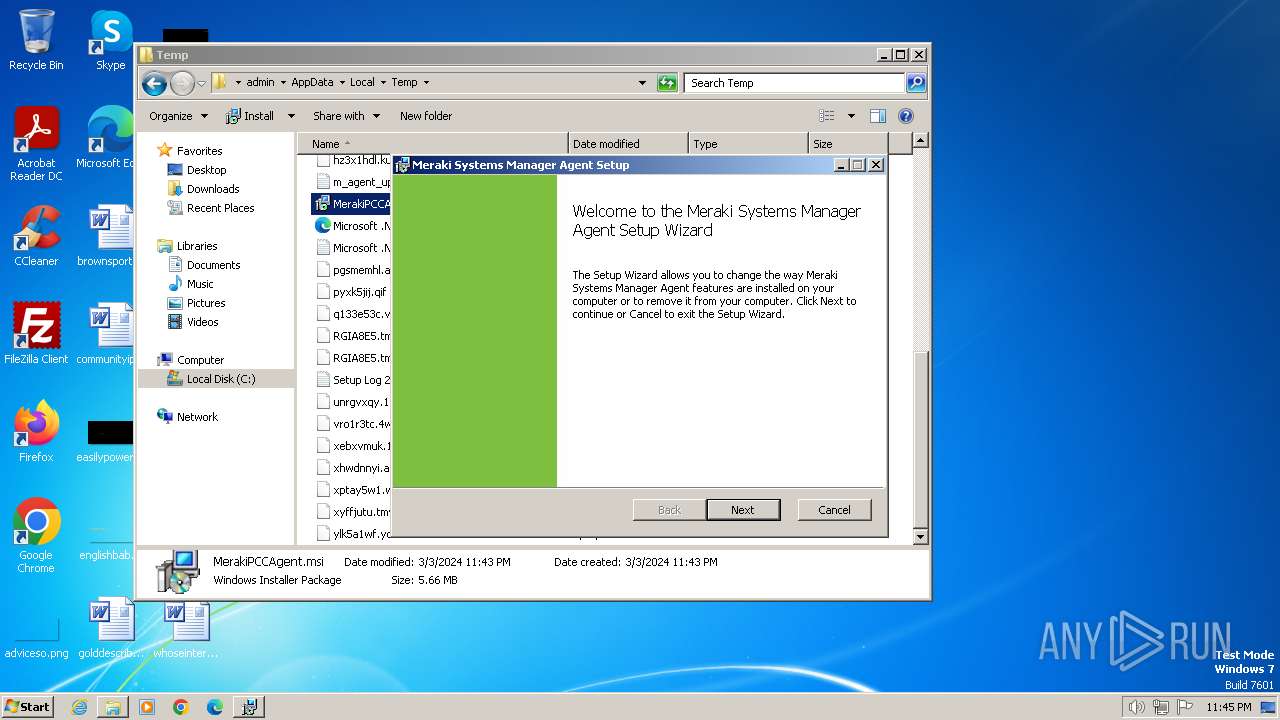
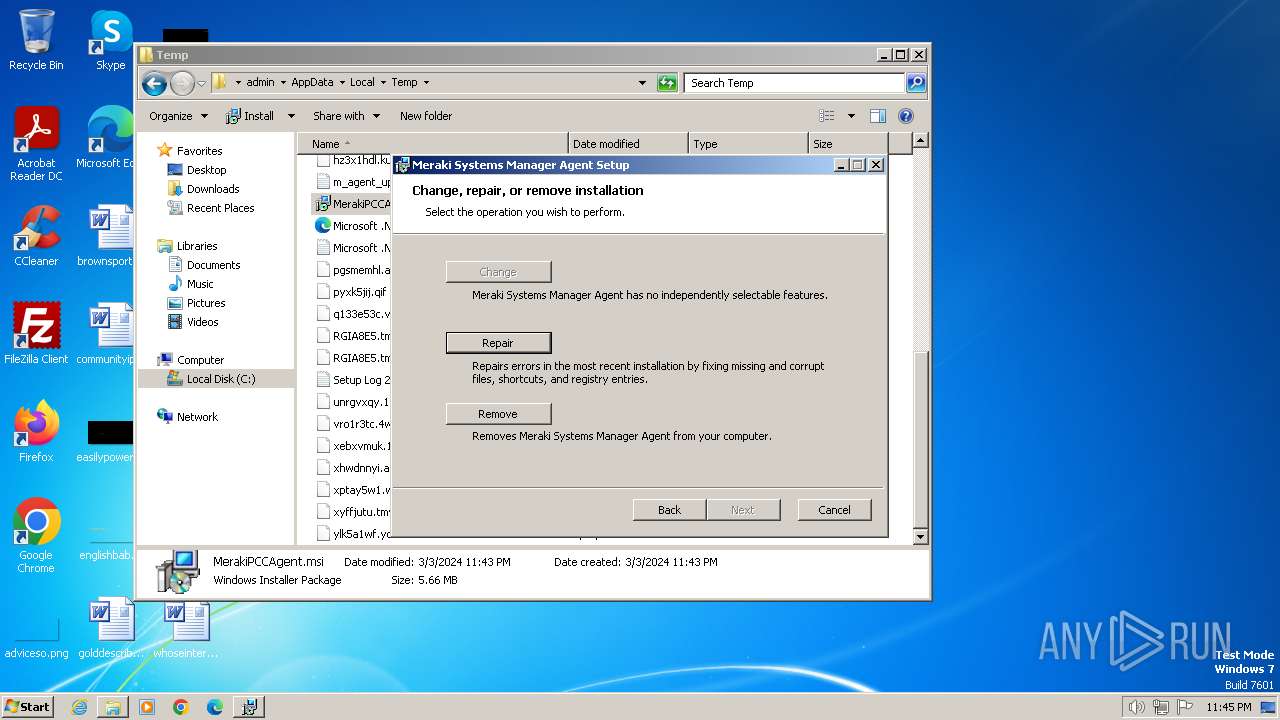
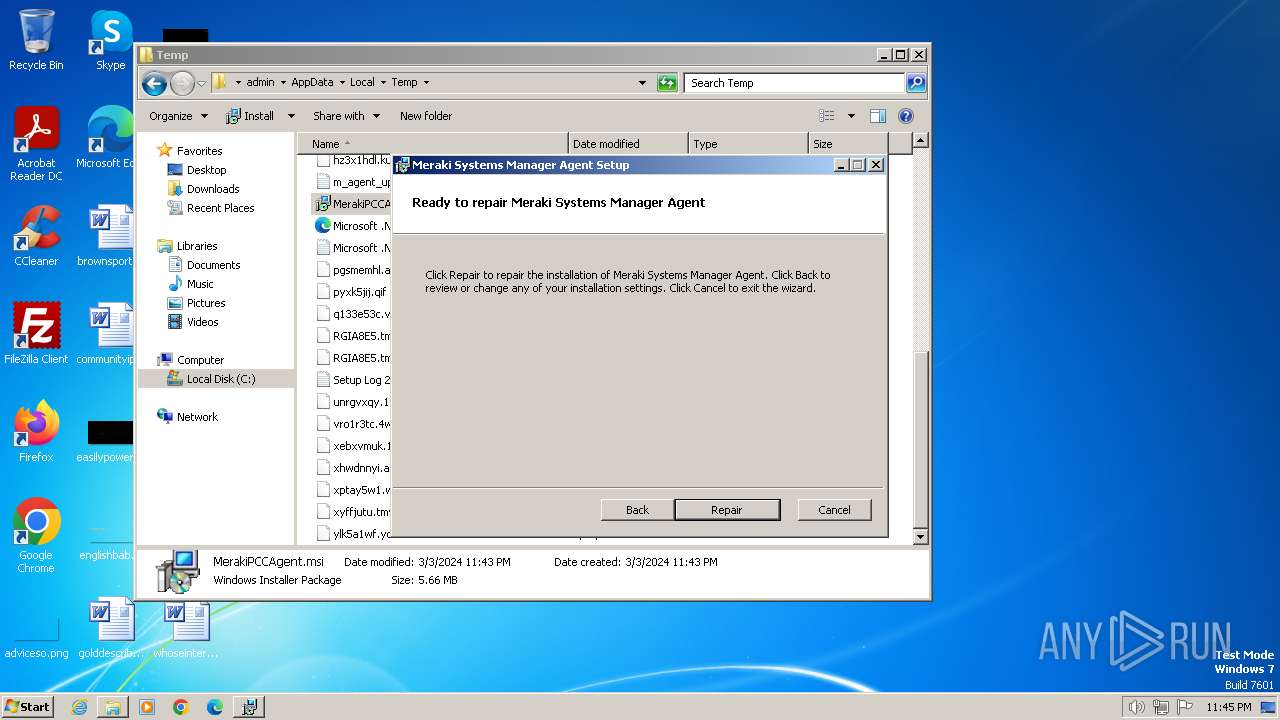
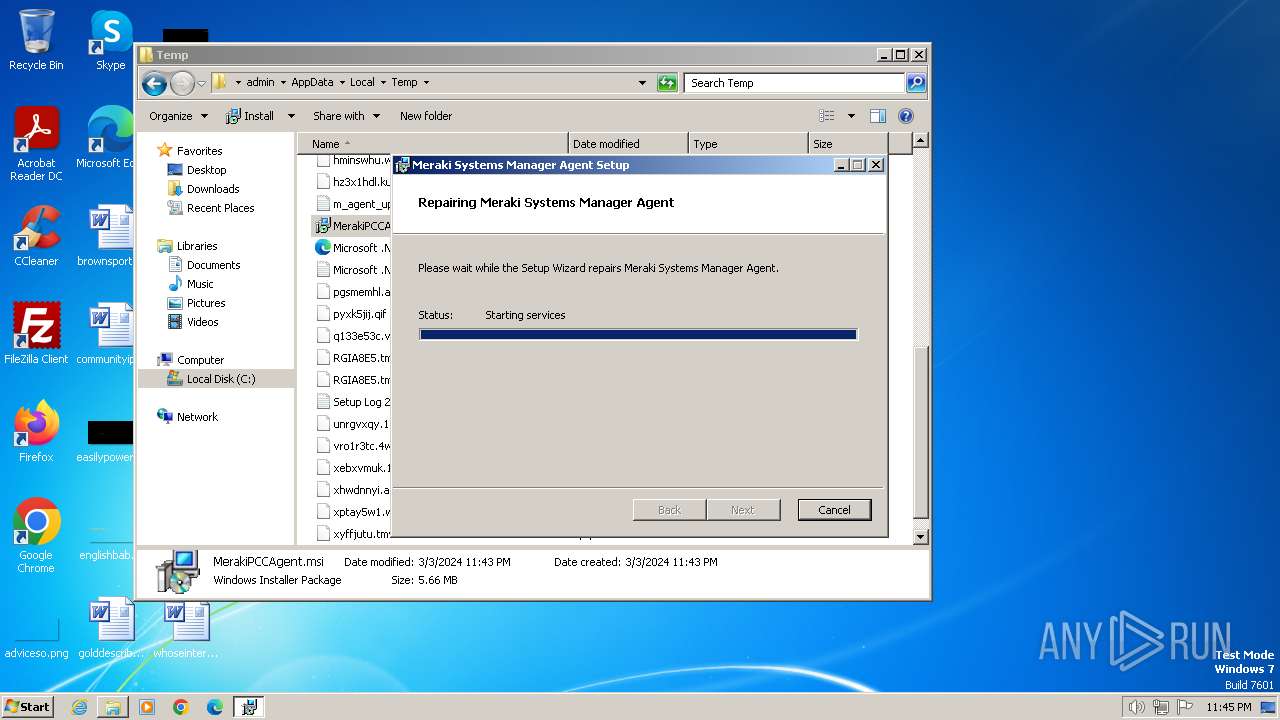
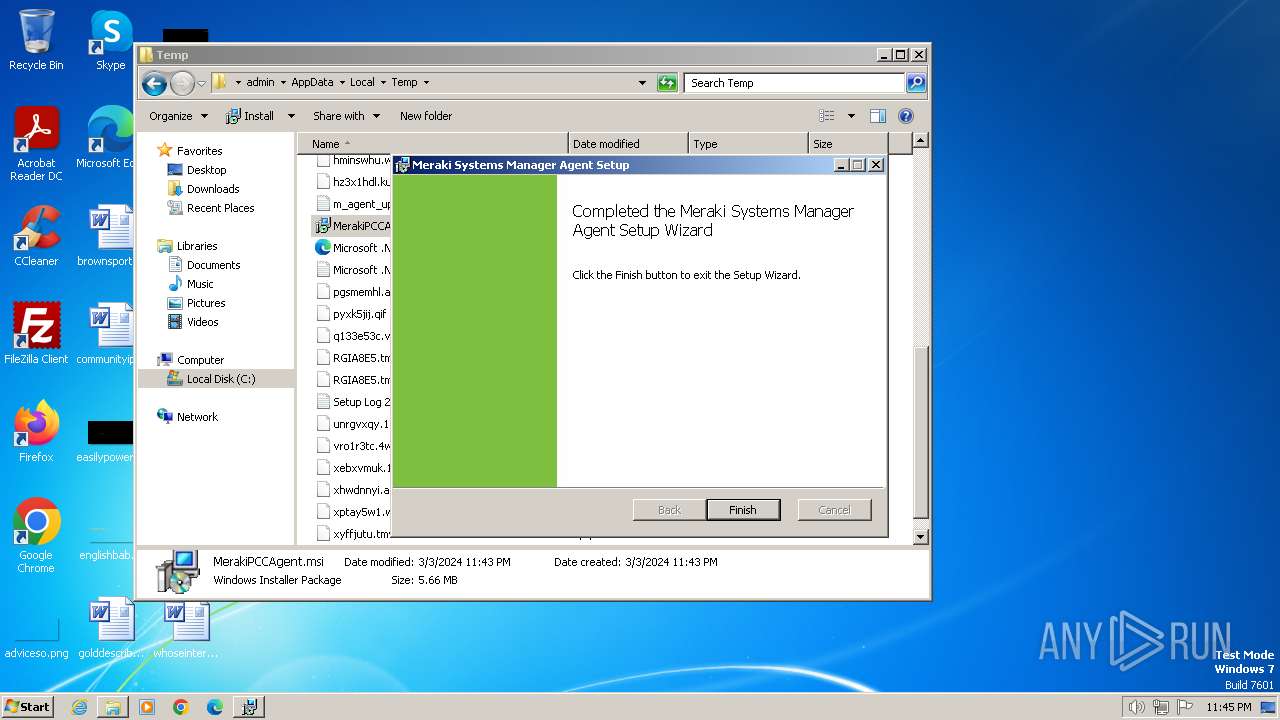
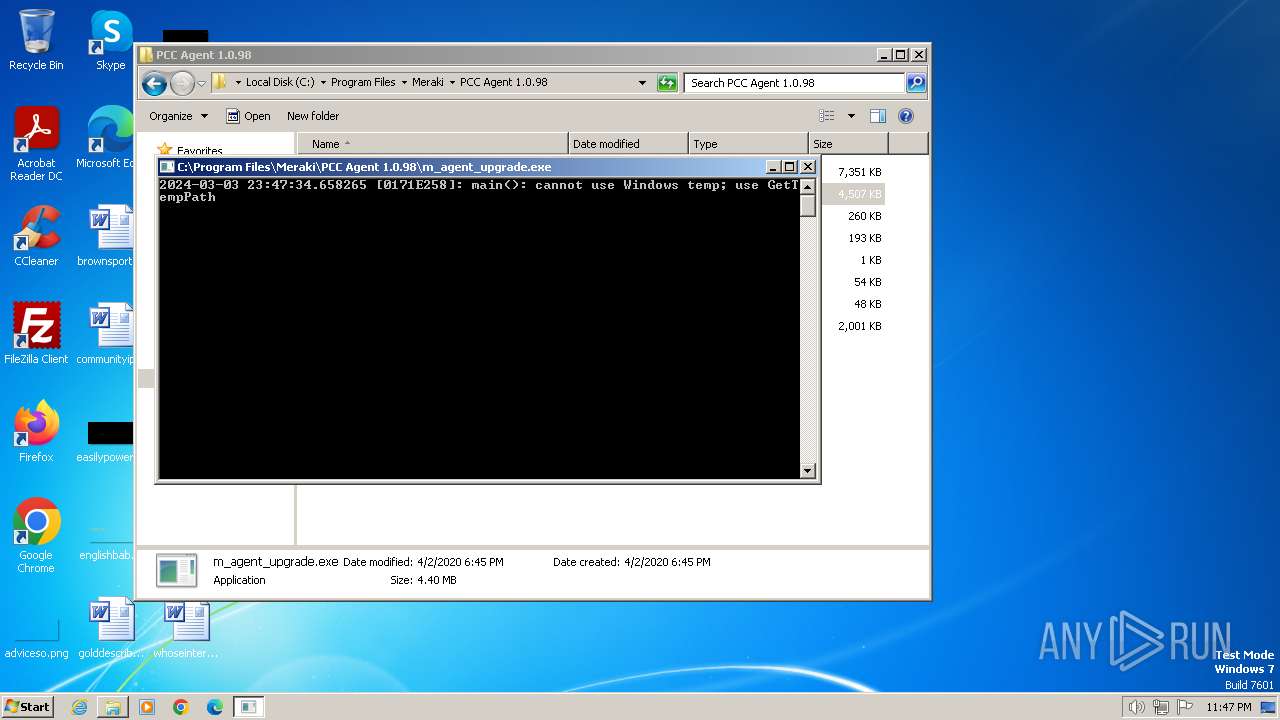
| File name: | MerakiPCCAgent.msi |
| Full analysis: | https://app.any.run/tasks/70a7cf10-c7ba-4b04-92fe-19386343717d |
| Verdict: | Malicious activity |
| Analysis date: | March 03, 2024, 23:42:45 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, MSI Installer, Code page: 1252, Title: Installation Database, Subject: Meraki Systems Manager Agent Installer, Author: Meraki, Inc., Keywords: Installer, Comments: This installer database contains the logic and data required to install Meraki Systems Manager Agent., Template: Intel;1033, Revision Number: {8BADE5C8-6202-41BB-A62F-2CB0C4616E8B}, Create Time/Date: Thu Apr 2 17:45:48 2020, Last Saved Time/Date: Thu Apr 2 17:45:48 2020, Number of Pages: 301, Number of Words: 2, Name of Creating Application: Windows Installer XML (3.0.5419.0), Security: 2 |
| MD5: | 65BB50089DD958C8D8E344E7EF1A02DF |
| SHA1: | F6D10F2944D6729172D32095CB0F95D3B9B81DEF |
| SHA256: | B0A62DF4EA644B180A8B46B54376043C12B7A6078F3E487EB1240F906844E7A6 |
| SSDEEP: | 98304:A3gw32bASRw+2wiRtoDwiuwsjLKZVB/fc4OIYY6oH7gXJwUaiIbctSVP8EHCmGJ3:A0ZM6sjMv |
MALICIOUS
Drops the executable file immediately after the start
- msiexec.exe (PID: 3668)
SUSPICIOUS
Executes as Windows Service
- VSSVC.exe (PID: 3720)
- m_agent_service.exe (PID: 1572)
- m_agent_service.exe (PID: 2496)
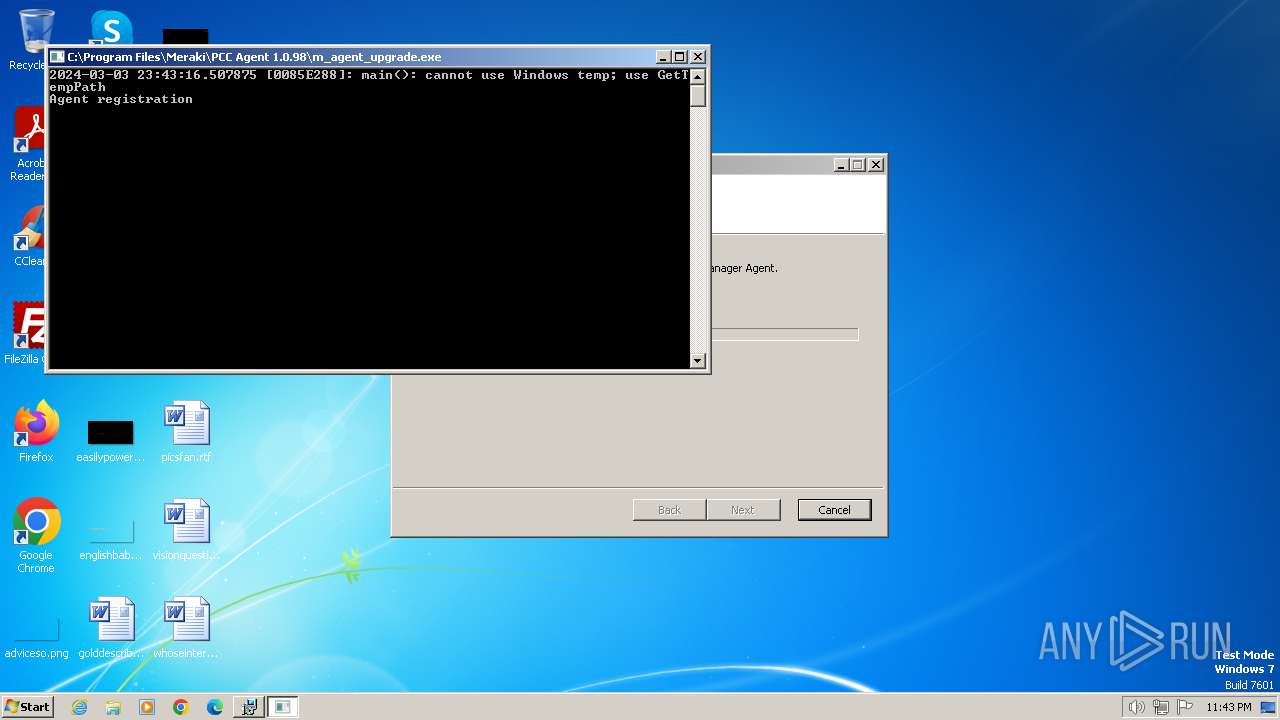
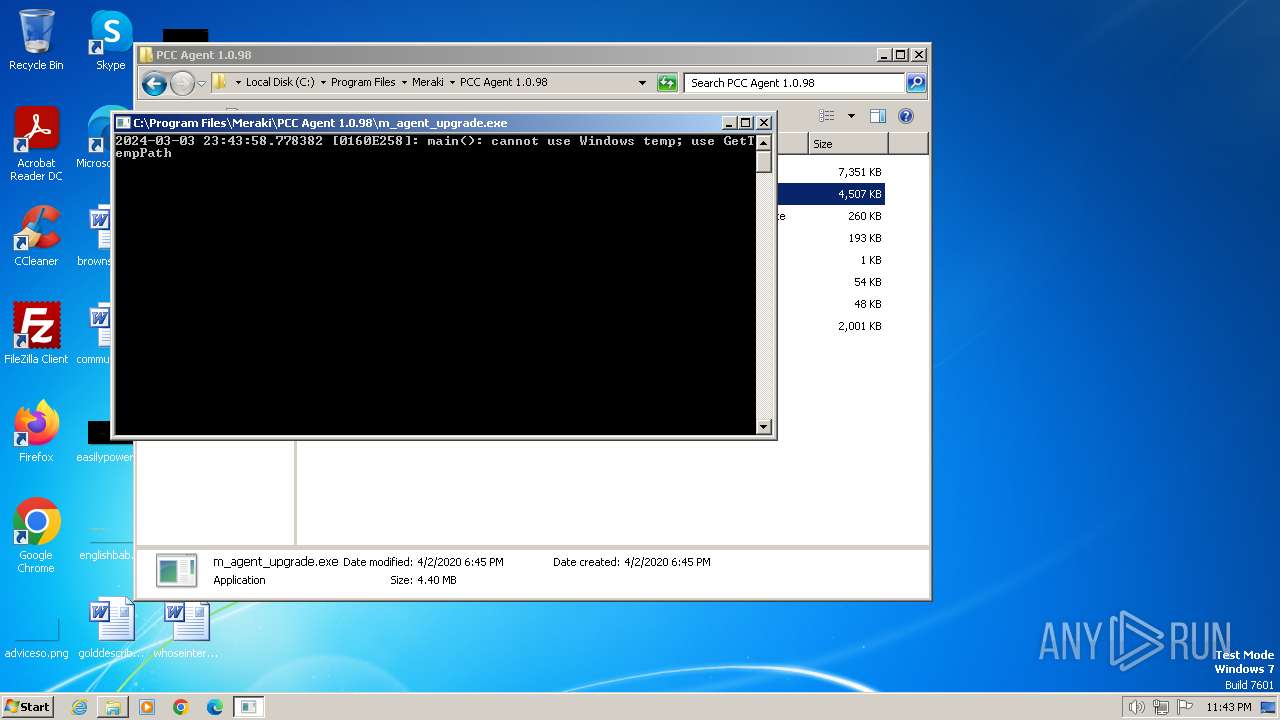
Starts CMD.EXE for commands execution
- m_agent_service.exe (PID: 1572)
- m_agent_upgrade.exe (PID: 2536)
- m_agent_service.exe (PID: 2496)
- m_agent_upgrade.exe (PID: 2784)
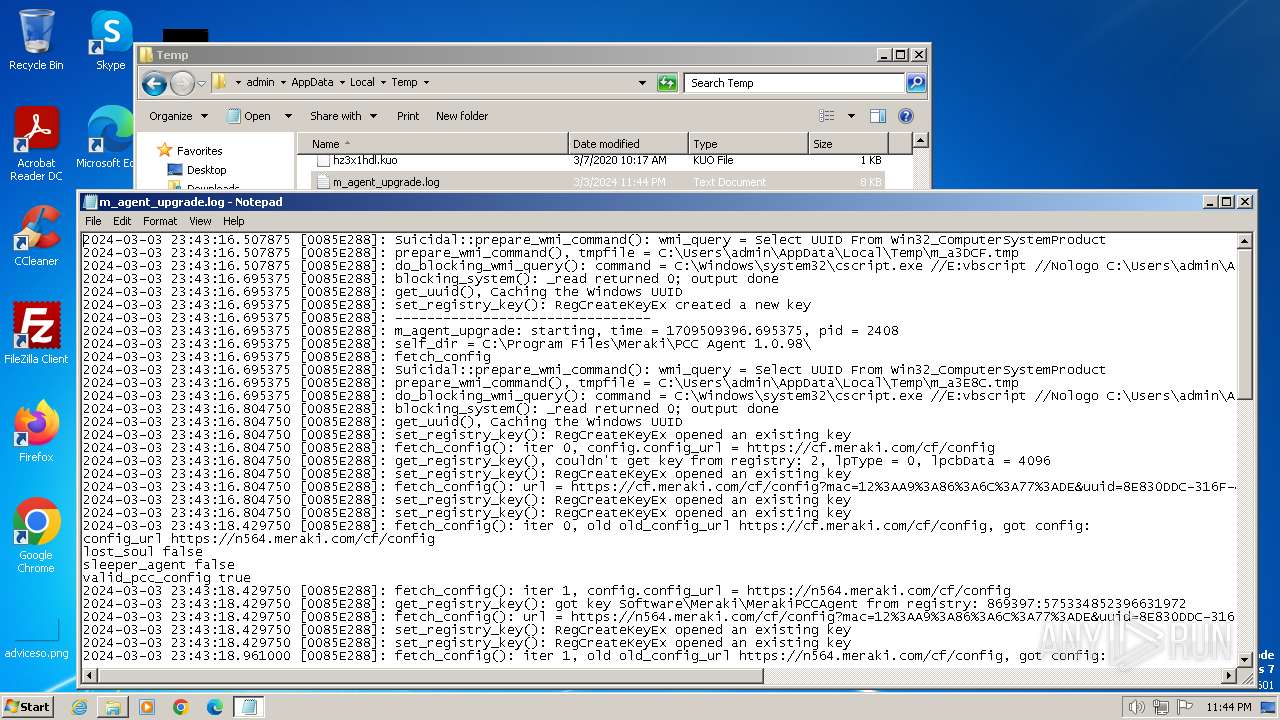
Accesses ComputerSystem(Win32_ComputerSystem) via WMI (SCRIPT)
- cscript.exe (PID: 2900)
- cscript.exe (PID: 2668)
- cscript.exe (PID: 2804)
- cscript.exe (PID: 3056)
- cscript.exe (PID: 3388)
- cscript.exe (PID: 3768)
- cscript.exe (PID: 2692)
- cscript.exe (PID: 2992)
- cscript.exe (PID: 2588)
- cscript.exe (PID: 2448)
- cscript.exe (PID: 2308)
- cscript.exe (PID: 880)
- cscript.exe (PID: 3136)
- cscript.exe (PID: 3584)
- cscript.exe (PID: 1020)
- cscript.exe (PID: 3236)
- cscript.exe (PID: 3056)
- cscript.exe (PID: 884)
- cscript.exe (PID: 2256)
Executes WMI query (SCRIPT)
- cscript.exe (PID: 2900)
- cscript.exe (PID: 2668)
- cscript.exe (PID: 3768)
- cscript.exe (PID: 2804)
- cscript.exe (PID: 3056)
- cscript.exe (PID: 3388)
- cscript.exe (PID: 2692)
- cscript.exe (PID: 2992)
- cscript.exe (PID: 2588)
- cscript.exe (PID: 2448)
- cscript.exe (PID: 2308)
- cscript.exe (PID: 3136)
- cscript.exe (PID: 3584)
- cscript.exe (PID: 880)
- cscript.exe (PID: 3236)
- cscript.exe (PID: 1020)
- cscript.exe (PID: 884)
- cscript.exe (PID: 3056)
- cscript.exe (PID: 2256)
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- cscript.exe (PID: 2900)
- cscript.exe (PID: 3768)
- cscript.exe (PID: 2804)
- cscript.exe (PID: 2668)
- cscript.exe (PID: 3056)
- cscript.exe (PID: 3388)
- cscript.exe (PID: 2692)
- cscript.exe (PID: 2992)
- cscript.exe (PID: 2588)
- cscript.exe (PID: 2448)
- cscript.exe (PID: 2308)
- cscript.exe (PID: 880)
- cscript.exe (PID: 3136)
- cscript.exe (PID: 3584)
- cscript.exe (PID: 1020)
- cscript.exe (PID: 3236)
- cscript.exe (PID: 3056)
- cscript.exe (PID: 884)
- cscript.exe (PID: 2256)
Accesses product unique identifier via WMI (SCRIPT)
- cscript.exe (PID: 2900)
- cscript.exe (PID: 2804)
- cscript.exe (PID: 3056)
- cscript.exe (PID: 3388)
- cscript.exe (PID: 2308)
- cscript.exe (PID: 3136)
- cscript.exe (PID: 884)
- cscript.exe (PID: 3056)
Accesses computer name via WMI (SCRIPT)
- cscript.exe (PID: 2900)
- cscript.exe (PID: 2668)
- cscript.exe (PID: 3768)
- cscript.exe (PID: 2804)
- cscript.exe (PID: 3056)
- cscript.exe (PID: 3388)
- cscript.exe (PID: 2992)
- cscript.exe (PID: 2692)
- cscript.exe (PID: 2588)
- cscript.exe (PID: 2308)
- cscript.exe (PID: 2448)
- cscript.exe (PID: 3584)
- cscript.exe (PID: 880)
- cscript.exe (PID: 3136)
- cscript.exe (PID: 1020)
- cscript.exe (PID: 3236)
- cscript.exe (PID: 3056)
- cscript.exe (PID: 884)
- cscript.exe (PID: 2256)
Accesses current user name via WMI (SCRIPT)
- cscript.exe (PID: 2668)
- cscript.exe (PID: 3768)
- cscript.exe (PID: 2692)
- cscript.exe (PID: 2992)
- cscript.exe (PID: 2588)
- cscript.exe (PID: 2448)
- cscript.exe (PID: 3584)
- cscript.exe (PID: 880)
- cscript.exe (PID: 1020)
- cscript.exe (PID: 3236)
- cscript.exe (PID: 2256)
Uses NETSH.EXE to obtain data on the network
- m_agent_service.exe (PID: 1572)
- m_agent_service.exe (PID: 2496)
Reads the Internet Settings
- rundll32.exe (PID: 3560)
INFO
Reads security settings of Internet Explorer
- msiexec.exe (PID: 3668)
- cscript.exe (PID: 3056)
- cscript.exe (PID: 3388)
- rundll32.exe (PID: 3560)
- cscript.exe (PID: 884)
- cscript.exe (PID: 3056)
Checks supported languages
- m_agent_service.exe (PID: 1572)
- m_agent_service.exe (PID: 3396)
- m_agent_upgrade.exe (PID: 2536)
- m_agent_service.exe (PID: 2496)
- m_agent_upgrade.exe (PID: 2784)
- ndisscan.exe (PID: 1388)
Reads the computer name
- m_agent_service.exe (PID: 1572)
- m_agent_service.exe (PID: 3396)
- m_agent_upgrade.exe (PID: 2536)
- m_agent_service.exe (PID: 2496)
- m_agent_upgrade.exe (PID: 2784)
Reads the software policy settings
- msiexec.exe (PID: 3668)
Manual execution by a user
- explorer.exe (PID: 2020)
- m_agent_upgrade.exe (PID: 2536)
- m_agent_service.exe (PID: 3396)
- notepad.exe (PID: 1848)
- msiexec.exe (PID: 3192)
- rundll32.exe (PID: 3864)
- notepad.exe (PID: 1556)
- rundll32.exe (PID: 3560)
- m_agent_upgrade.exe (PID: 2784)
- ndisscan.exe (PID: 1388)
Reads the machine GUID from the registry
- m_agent_service.exe (PID: 1572)
- m_agent_upgrade.exe (PID: 2536)
- m_agent_service.exe (PID: 2496)
- m_agent_upgrade.exe (PID: 2784)
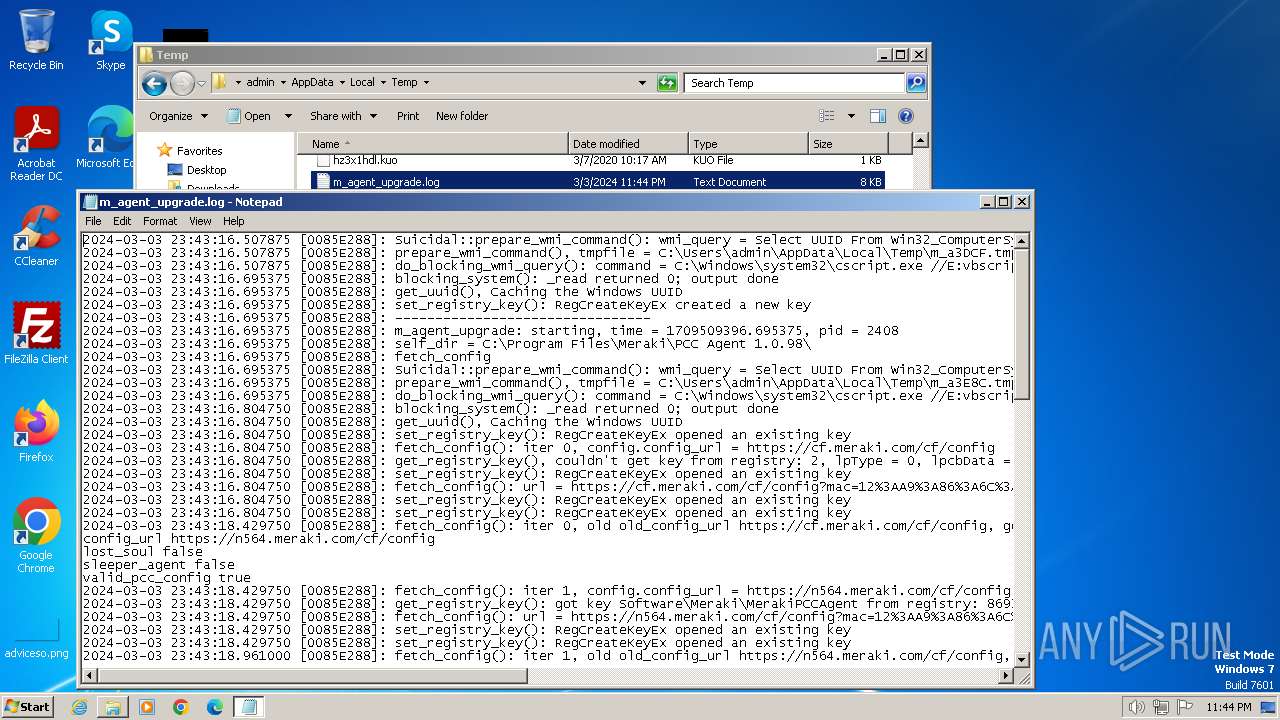
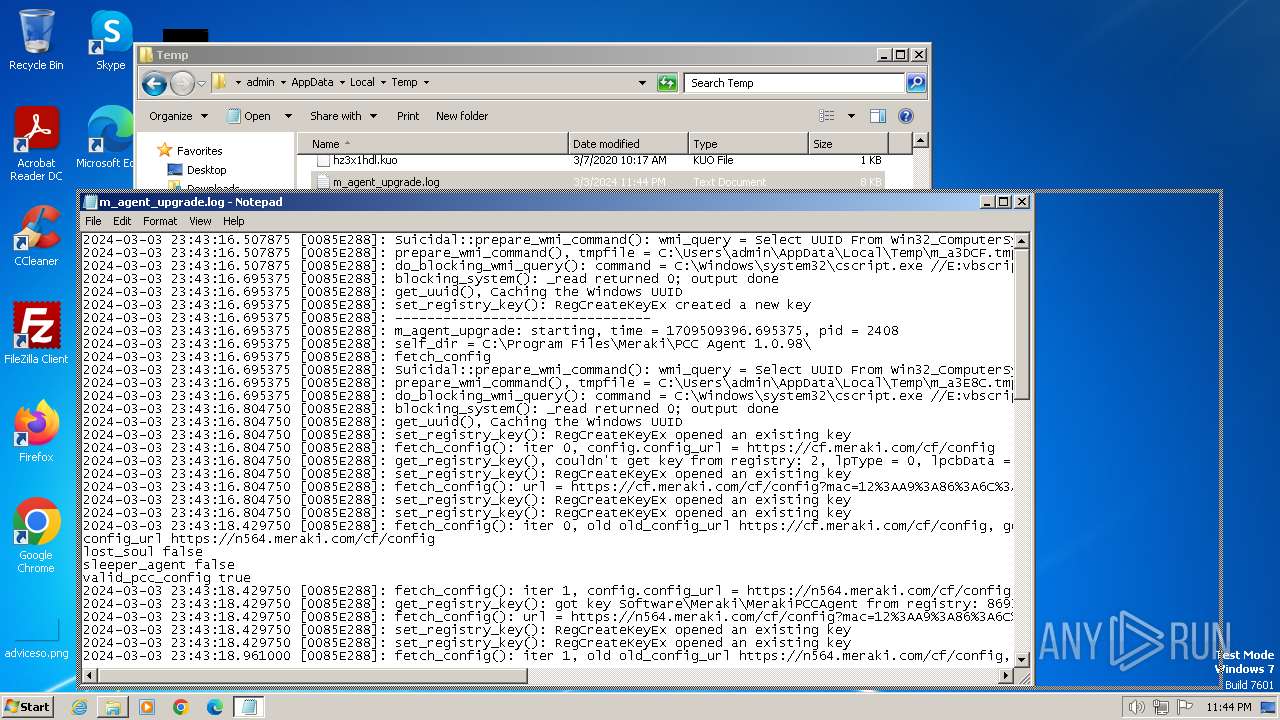
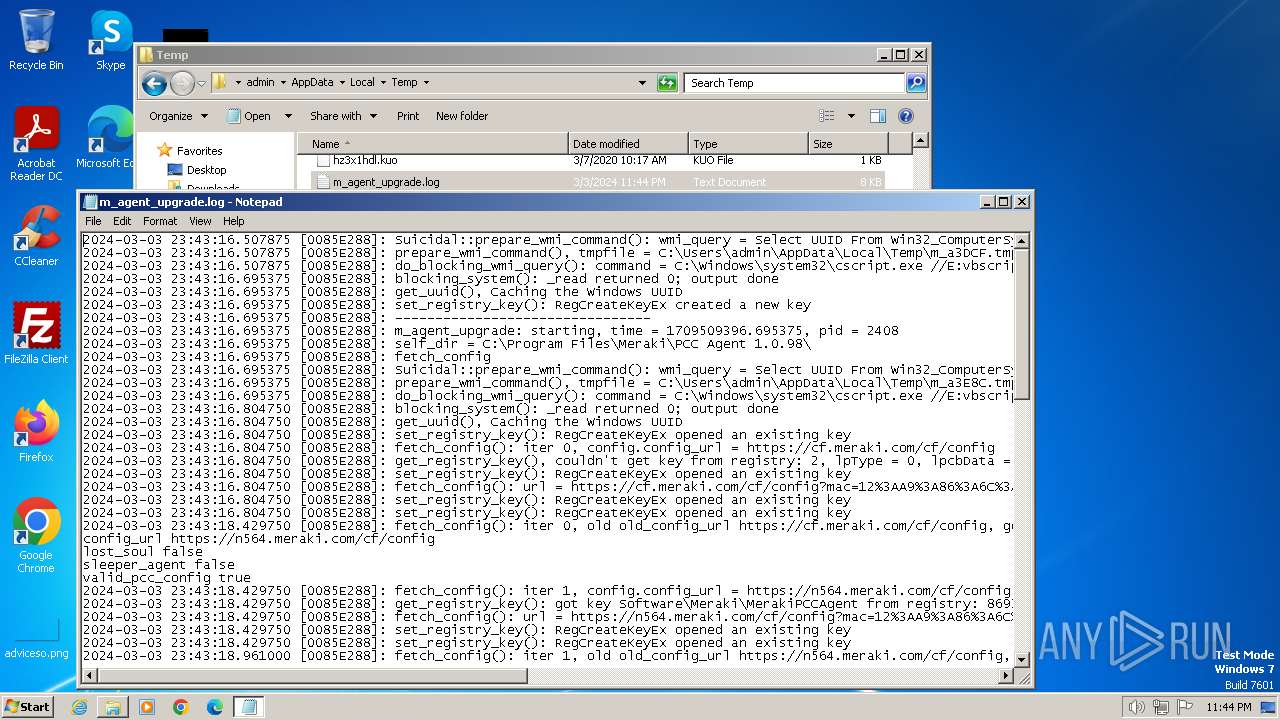
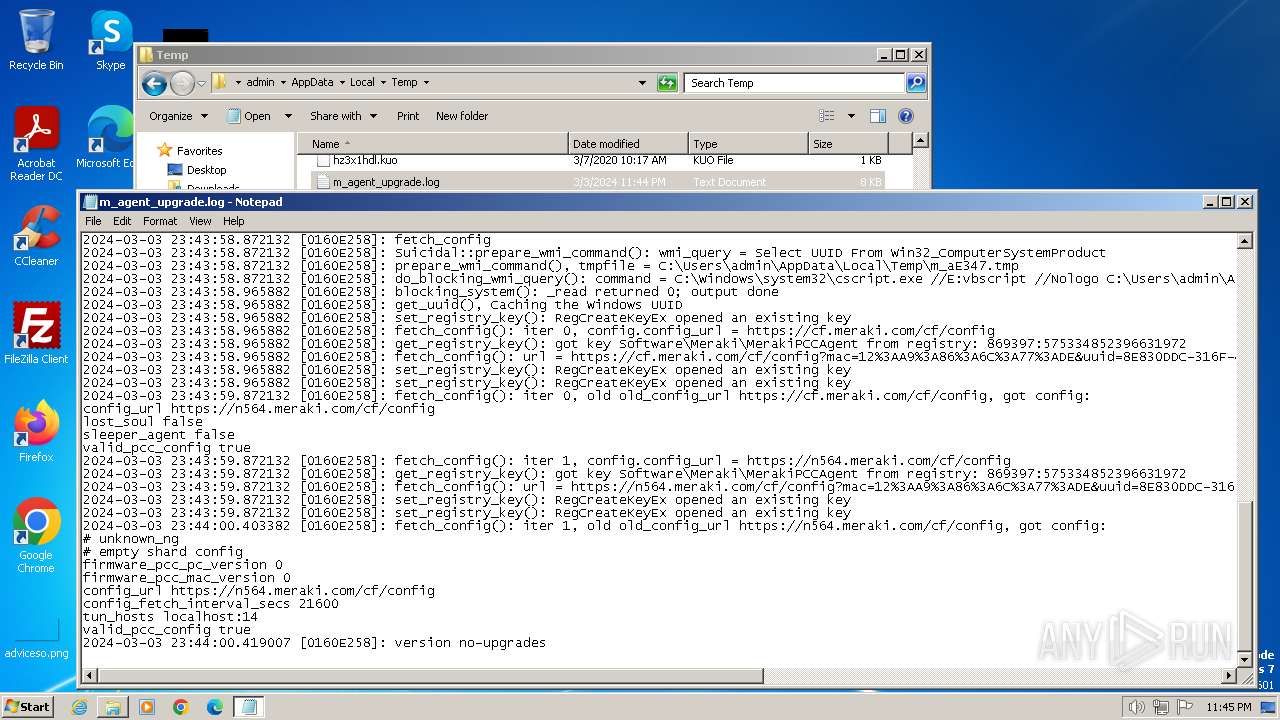
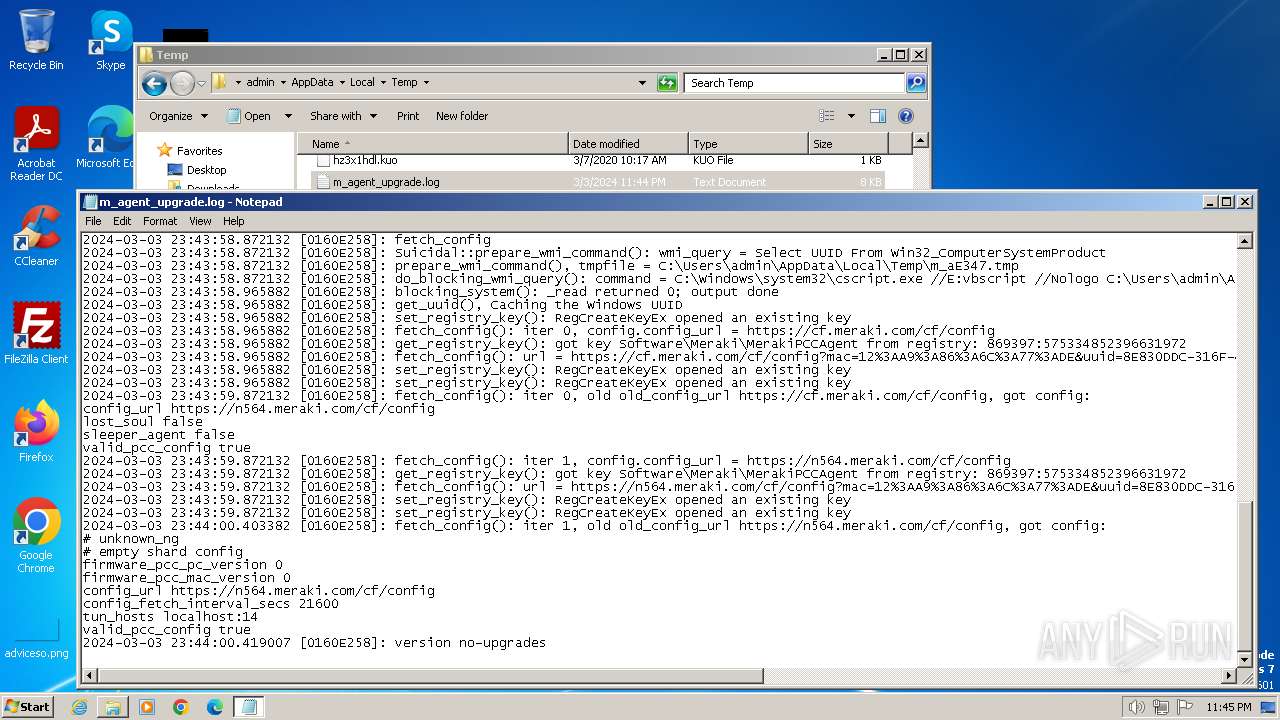
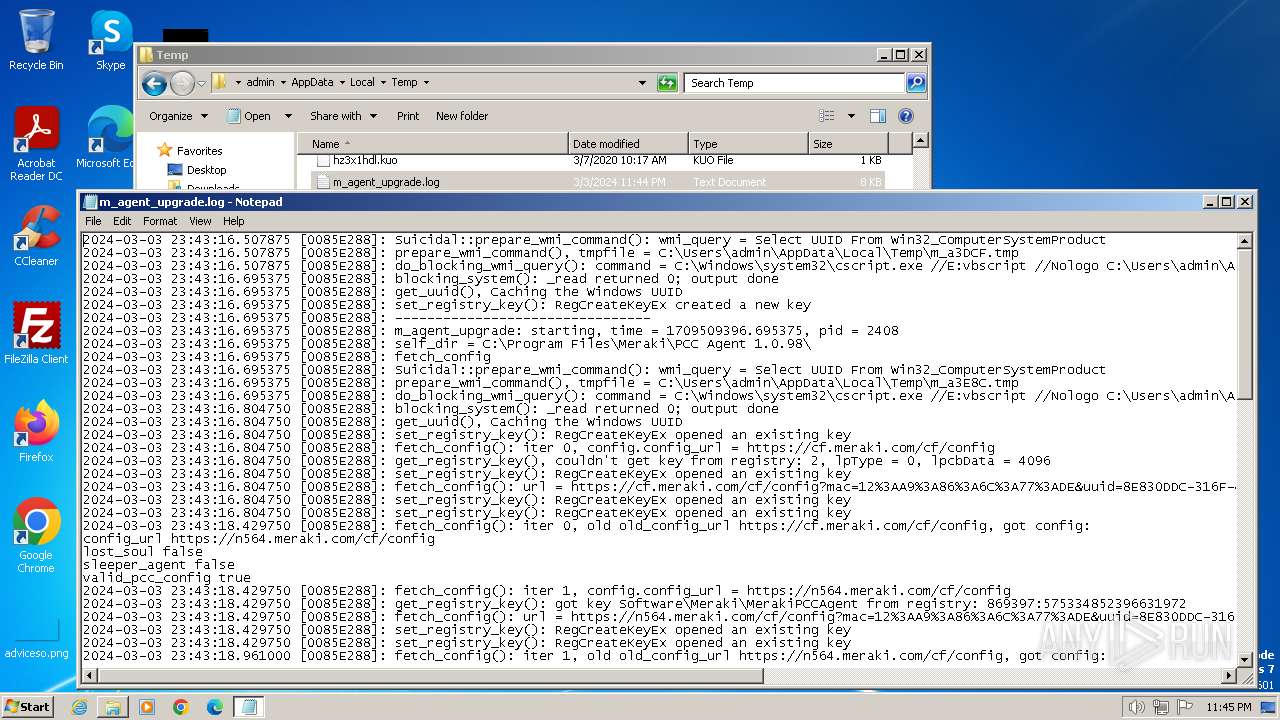
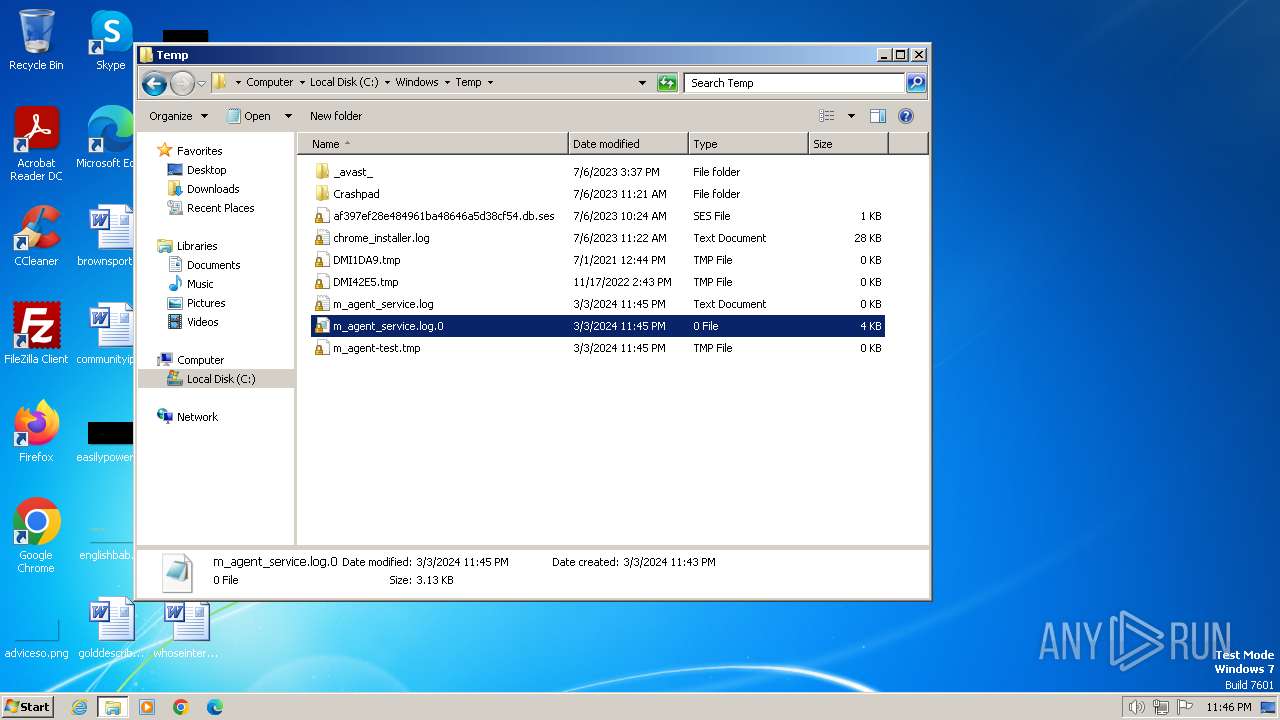
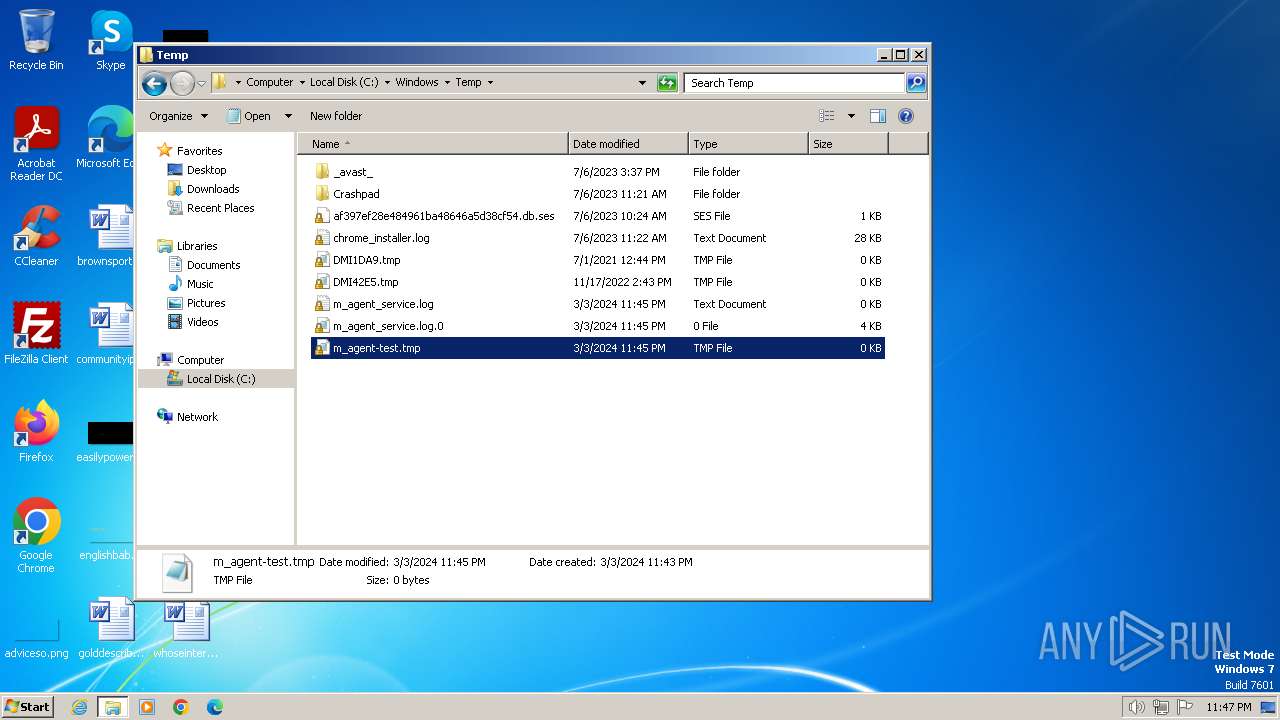
Create files in a temporary directory
- m_agent_upgrade.exe (PID: 2536)
- m_agent_upgrade.exe (PID: 2784)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (98.5) |
|---|---|---|
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| CodePage: | Windows Latin 1 (Western European) |
|---|---|
| Title: | Installation Database |
| Subject: | Meraki Systems Manager Agent Installer |
| Author: | Meraki, Inc. |
| Keywords: | Installer |
| Comments: | This installer database contains the logic and data required to install Meraki Systems Manager Agent. |
| Template: | Intel;1033 |
| RevisionNumber: | {8BADE5C8-6202-41BB-A62F-2CB0C4616E8B} |
| CreateDate: | 2020:04:02 17:45:48 |
| ModifyDate: | 2020:04:02 17:45:48 |
| Pages: | 301 |
| Words: | 2 |
| Software: | Windows Installer XML (3.0.5419.0) |
| Security: | Read-only recommended |
Total processes
159
Monitored processes
65
Malicious processes
22
Suspicious processes
9
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 296 | C:\Windows\System32\netsh.exe wlan show drivers | C:\Windows\System32\netsh.exe | — | m_agent_service.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Network Command Shell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 548 | C:\Windows\System32\netsh.exe wlan show drivers | C:\Windows\System32\netsh.exe | — | m_agent_service.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Network Command Shell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 572 | C:\Windows\System32\netsh.exe wlan show drivers | C:\Windows\System32\netsh.exe | — | m_agent_service.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Network Command Shell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 572 | C:\Windows\System32\netsh.exe wlan show interfaces | C:\Windows\System32\netsh.exe | — | m_agent_service.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Network Command Shell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 880 | C:\Windows\system32\cscript.exe //E:vbscript //Nologo C:\Windows\TEMP\m_a2809.tmp | C:\Windows\System32\cscript.exe | — | m_agent_service.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 884 | C:\Windows\system32\cscript.exe //E:vbscript //Nologo C:\Users\admin\AppData\Local\Temp\m_a2E9A.tmp | C:\Windows\System32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 1020 | C:\Windows\system32\cscript.exe //E:vbscript //Nologo C:\Windows\TEMP\m_a9E73.tmp | C:\Windows\System32\cscript.exe | — | m_agent_service.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 1112 | C:\Windows\system32\cmd.exe /c C:\Windows\system32\cscript.exe //E:vbscript //Nologo C:\Windows\TEMP\m_a4C85.tmp | C:\Windows\System32\cmd.exe | — | m_agent_service.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1112 | C:\Windows\System32\netsh.exe wlan show drivers | C:\Windows\System32\netsh.exe | — | m_agent_service.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Network Command Shell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1388 | "C:\Program Files\Meraki\PCC Agent 1.0.98\ndisscan.exe" | C:\Program Files\Meraki\PCC Agent 1.0.98\ndisscan.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
28 116
Read events
26 760
Write events
1 356
Delete events
0
Modification events
| (PID) Process: | (3668) msiexec.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3720) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000D841048DC46DDA01880E0000340F0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3720) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000D841048DC46DDA01880E0000200B0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3720) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000D841048DC46DDA01880E0000980E0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3720) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000D841048DC46DDA01880E00009C0C0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3720) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 400000000000000032A4068DC46DDA01880E0000980E0000E8030000000000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3720) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 400000000000000032A4068DC46DDA01880E0000200B0000E8030000000000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3720) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 400000000000000032A4068DC46DDA01880E00009C0C0000E8030000000000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3720) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 40000000000000008C06098DC46DDA01880E0000340F0000E8030000000000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3720) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SwProvider_{b5946137-7b9f-4925-af80-51abd60b20d5} |
| Operation: | write | Name: | PROVIDER_BEGINPREPARE (Enter) |
Value: 40000000000000002C59608EC46DDA01880E0000340F000001040000010000000000000000000000E1761A5DF564094FB33DD38BEFE22D2C0000000000000000 | |||
Executable files
0
Suspicious files
0
Text files
21
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1572 | m_agent_service.exe | C:\Windows\TEMP\m_a4C85.tmp | text | |
MD5:2421DD25D93CA43A874BB5134C32E8CA | SHA256:248111DF36380AA97FE981A5CD021F86A8B4A62B59D9793E2DDC2F14C4CEB405 | |||
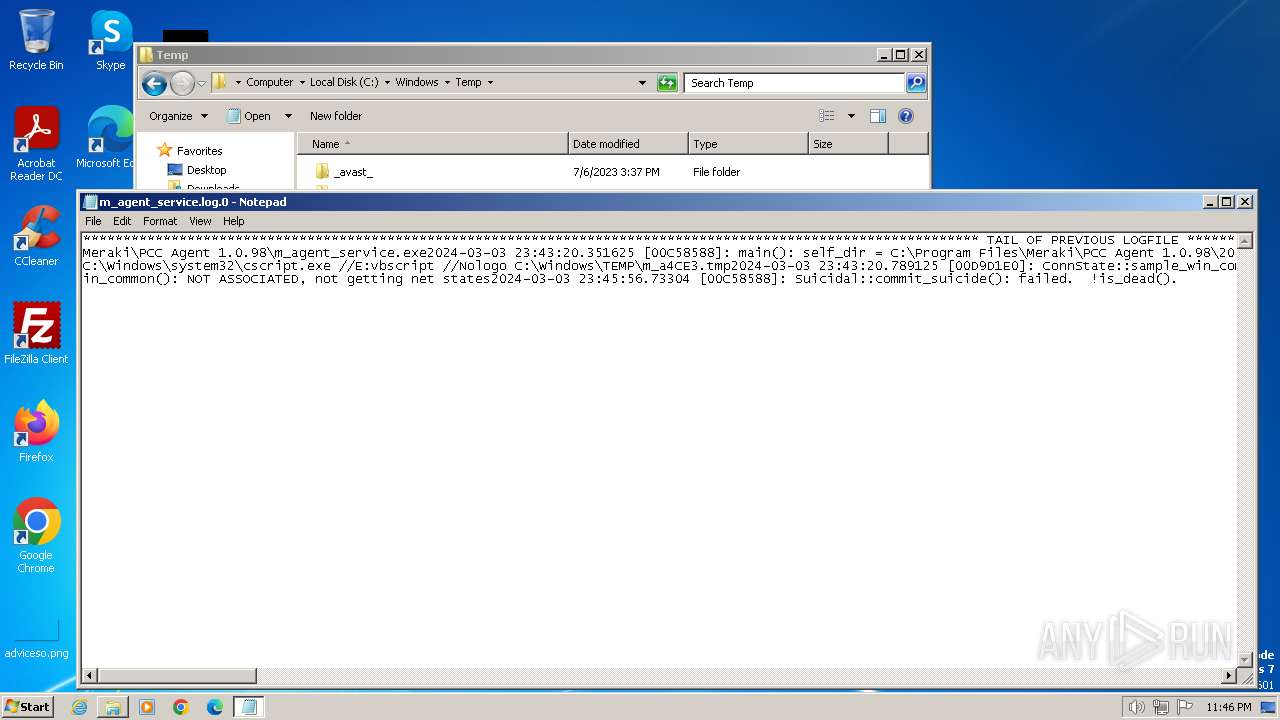
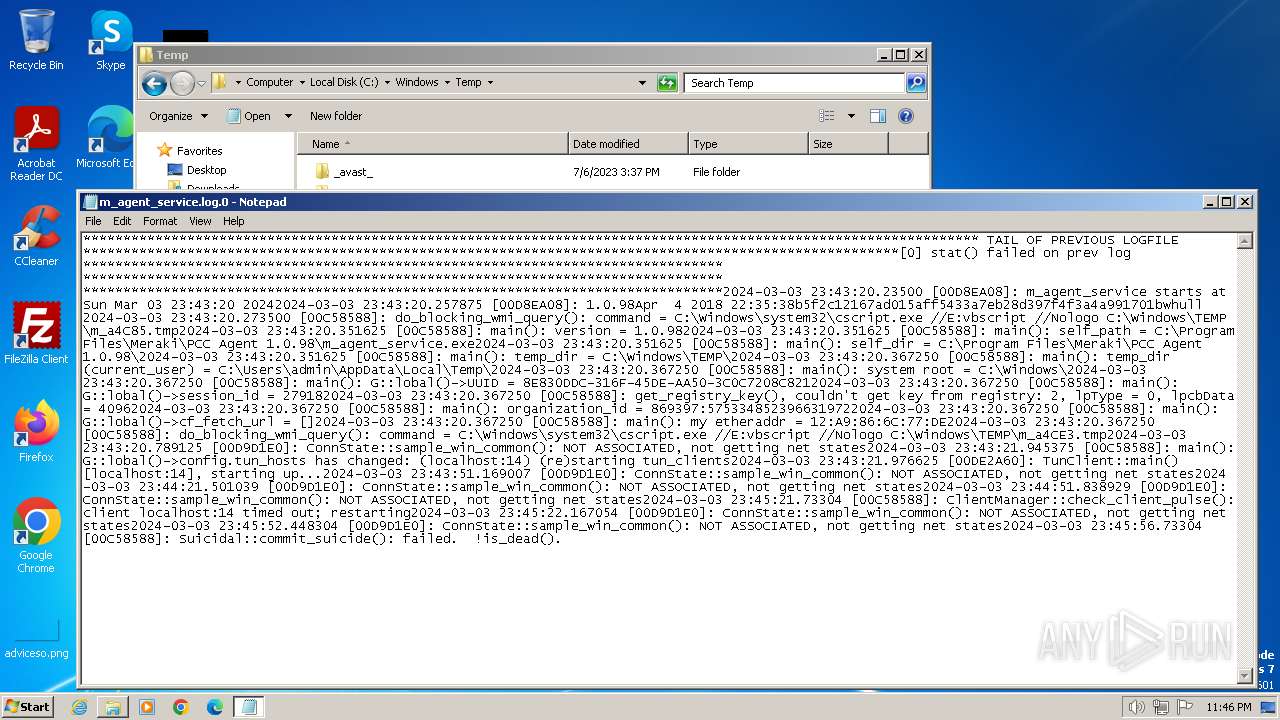
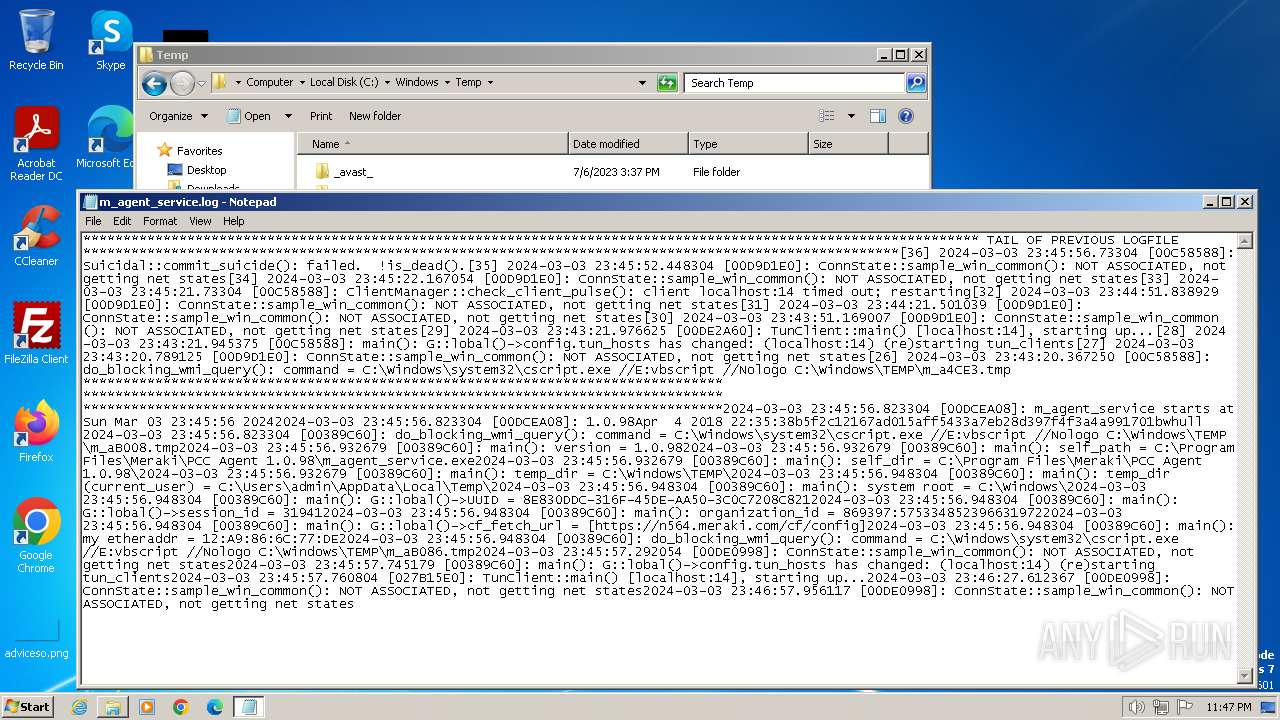
| 2496 | m_agent_service.exe | C:\Windows\Temp\m_agent_service.log.0 | text | |
MD5:D7E2DB68A0132F85B99367AA873E26C1 | SHA256:D3B58A9B357A7FEF776E173DD1B74292F91AA6C3B066EA350E6D39989A138704 | |||
| 1572 | m_agent_service.exe | C:\Windows\TEMP\m_aB1E6.tmp | text | |
MD5:79BC4B0230F5EF9F024E2133B1379F14 | SHA256:683FE7814C5C2E2AC910F5A041BD59EA69C2C860E521F8574211A11E26F05CAD | |||
| 2536 | m_agent_upgrade.exe | C:\Users\admin\AppData\Local\Temp\m_aE347.tmp | text | |
MD5:2421DD25D93CA43A874BB5134C32E8CA | SHA256:248111DF36380AA97FE981A5CD021F86A8B4A62B59D9793E2DDC2F14C4CEB405 | |||
| 1572 | m_agent_service.exe | C:\Windows\TEMP\m_a9EA9.tmp | text | |
MD5:79BC4B0230F5EF9F024E2133B1379F14 | SHA256:683FE7814C5C2E2AC910F5A041BD59EA69C2C860E521F8574211A11E26F05CAD | |||
| 1572 | m_agent_service.exe | C:\Windows\TEMP\m_aC4E4.tmp | text | |
MD5:79BC4B0230F5EF9F024E2133B1379F14 | SHA256:683FE7814C5C2E2AC910F5A041BD59EA69C2C860E521F8574211A11E26F05CAD | |||
| 2496 | m_agent_service.exe | C:\Windows\TEMP\m_aB086.tmp | text | |
MD5:2421DD25D93CA43A874BB5134C32E8CA | SHA256:248111DF36380AA97FE981A5CD021F86A8B4A62B59D9793E2DDC2F14C4CEB405 | |||
| 1572 | m_agent_service.exe | C:\Windows\TEMP\m_a4CE3.tmp | text | |
MD5:2421DD25D93CA43A874BB5134C32E8CA | SHA256:248111DF36380AA97FE981A5CD021F86A8B4A62B59D9793E2DDC2F14C4CEB405 | |||
| 2496 | m_agent_service.exe | C:\Windows\TEMP\m_a14FC.tmp | text | |
MD5:79BC4B0230F5EF9F024E2133B1379F14 | SHA256:683FE7814C5C2E2AC910F5A041BD59EA69C2C860E521F8574211A11E26F05CAD | |||
| 2496 | m_agent_service.exe | C:\Windows\TEMP\m_a9E73.tmp | text | |
MD5:79BC4B0230F5EF9F024E2133B1379F14 | SHA256:683FE7814C5C2E2AC910F5A041BD59EA69C2C860E521F8574211A11E26F05CAD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
14
DNS requests
5
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
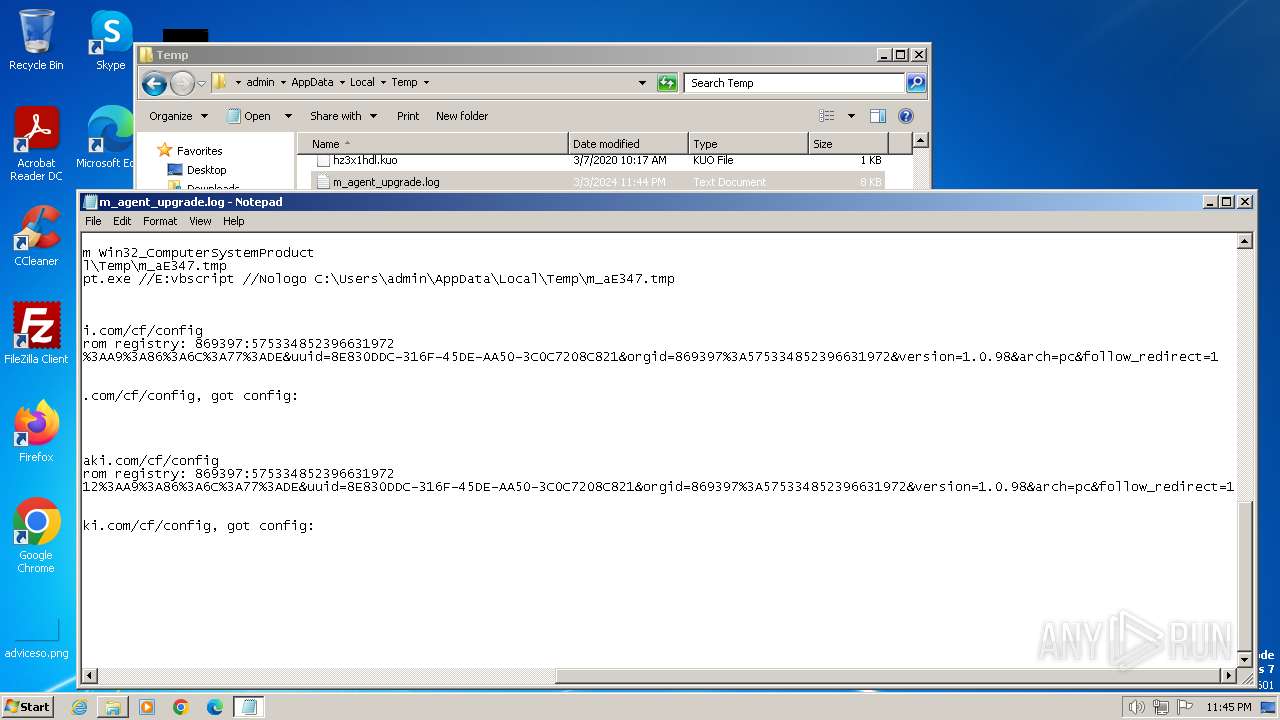
2408 | m_agent_upgrade.exe | 13.56.242.22:443 | cf.meraki.com | AMAZON-02 | US | unknown |
2408 | m_agent_upgrade.exe | 158.115.141.156:443 | n564.meraki.com | AMAZON-02 | US | unknown |
1572 | m_agent_service.exe | 13.56.242.22:443 | cf.meraki.com | AMAZON-02 | US | unknown |
1572 | m_agent_service.exe | 158.115.141.156:443 | n564.meraki.com | AMAZON-02 | US | unknown |
2536 | m_agent_upgrade.exe | 13.56.242.22:443 | cf.meraki.com | AMAZON-02 | US | unknown |
2536 | m_agent_upgrade.exe | 158.115.141.156:443 | n564.meraki.com | AMAZON-02 | US | unknown |
2496 | m_agent_service.exe | 158.115.141.156:443 | n564.meraki.com | AMAZON-02 | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
cf.meraki.com |
| unknown |
n564.meraki.com |
| unknown |