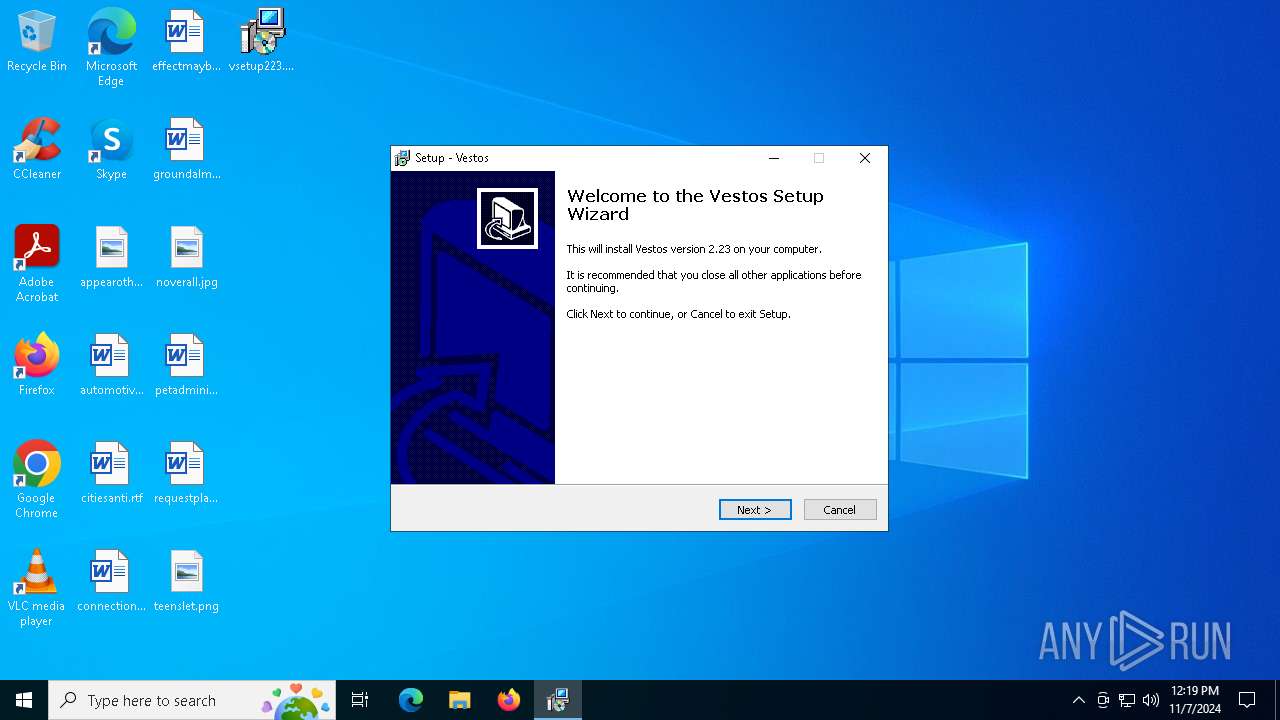
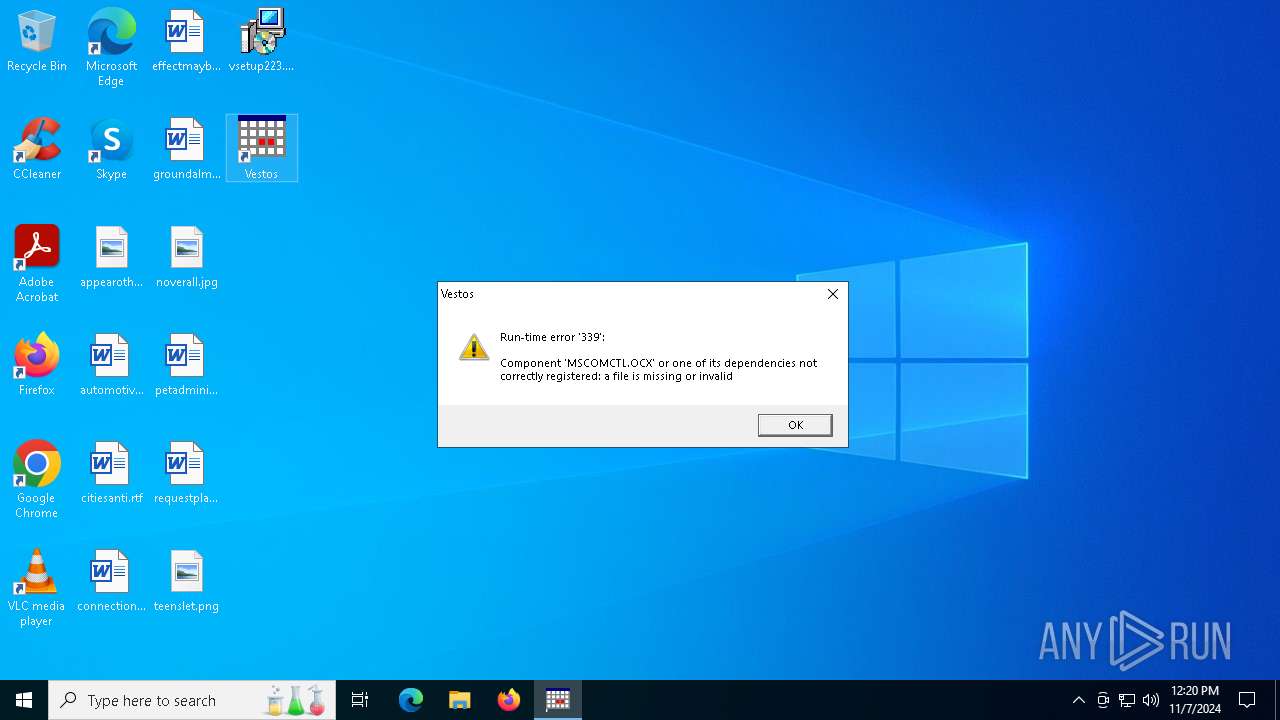
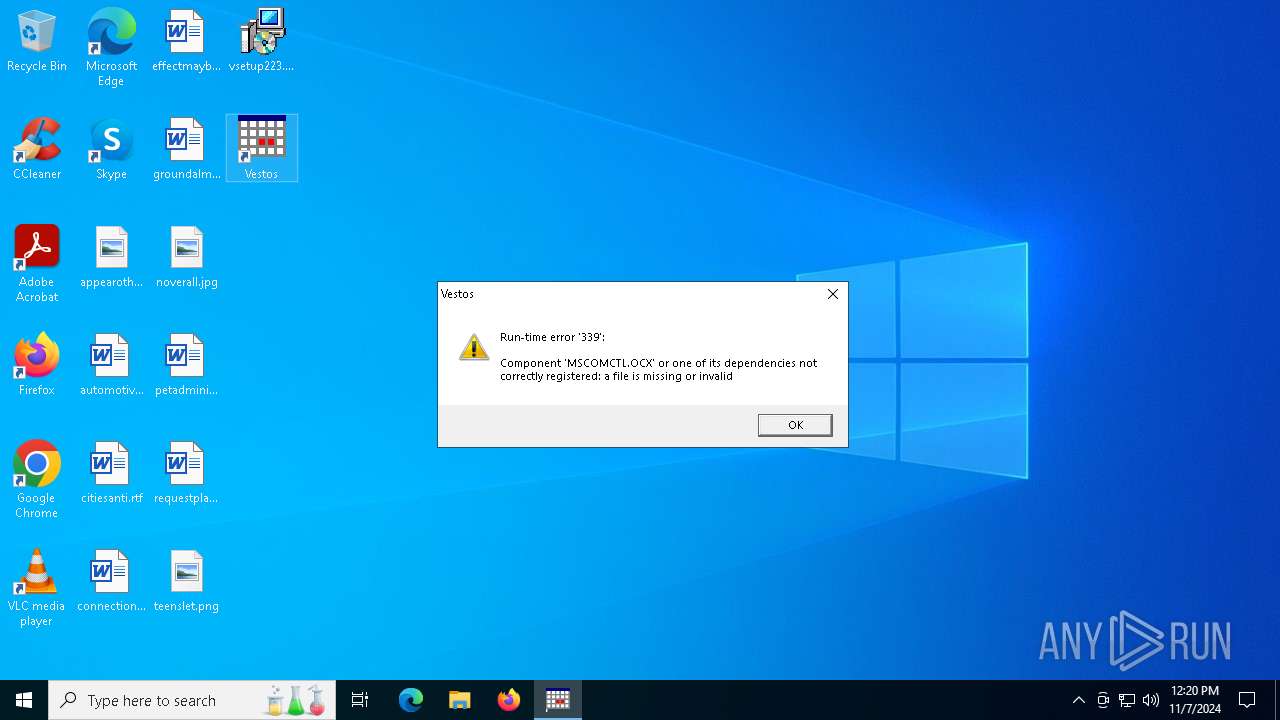
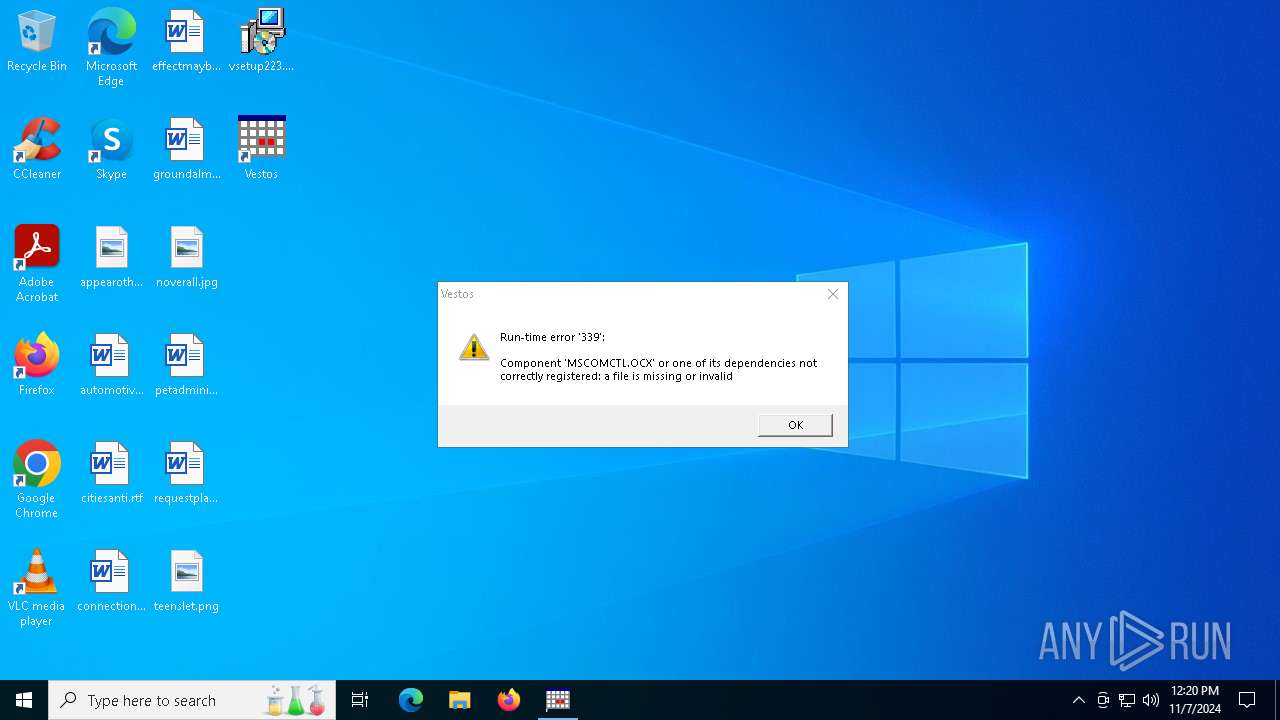
| File name: | vsetup223.exe |
| Full analysis: | https://app.any.run/tasks/44ec82a1-e3d6-4729-a4ea-ca74631209b0 |
| Verdict: | Malicious activity |
| Analysis date: | November 07, 2024, 12:19:47 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 8 sections |
| MD5: | E1EFDD655573A06F9FF200C354D7029D |
| SHA1: | D5140A95D5545F00220D79C07E5BC486492CE559 |
| SHA256: | B0A00B43BB07AF77C1BB32A20A96CF22B0EB9675F4F75F88663183142FC92BE3 |
| SSDEEP: | 98304:hSHV7ljTCPHiEHxNvhtUnyMhCdmPHn4gtLUBGzrRrZ6QYO/HNclbdp3whlsEfmh4:yrC2p |
MALICIOUS
Registers / Runs the DLL via REGSVR32.EXE
- vsetup223.tmp (PID: 6156)
SUSPICIOUS
Executable content was dropped or overwritten
- vsetup223.exe (PID: 4076)
- csc.exe (PID: 4348)
- vsetup223.tmp (PID: 6156)
- vsetup223.exe (PID: 6604)
- csc.exe (PID: 4476)
- csc.exe (PID: 4956)
Reads security settings of Internet Explorer
- vsetup223.tmp (PID: 2184)
Process drops legitimate windows executable
- vsetup223.tmp (PID: 6156)
Uses RUNDLL32.EXE to load library
- msdt.exe (PID: 5944)
Probably uses Microsoft diagnostics tool to execute malicious payload
- pcwrun.exe (PID: 764)
INFO
Process checks computer location settings
- vsetup223.tmp (PID: 2184)
Create files in a temporary directory
- vsetup223.exe (PID: 4076)
Checks supported languages
- vsetup223.exe (PID: 4076)
- vsetup223.tmp (PID: 2184)
Reads the computer name
- vsetup223.tmp (PID: 2184)
Manual execution by a user
- pcwrun.exe (PID: 764)
- vestos.exe (PID: 5508)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (77.7) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (10) |
| .dll | | | Win32 Dynamic Link Library (generic) (4.6) |
| .exe | | | Win32 Executable (generic) (3.1) |
| .exe | | | Win16/32 Executable Delphi generic (1.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 37888 |
| InitializedDataSize: | 17920 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x9c40 |
| OSVersion: | 1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Torah Software |
| FileDescription: | Vestos Setup |
| FileVersion: | |
| LegalCopyright: | |
| ProductName: | Vestos |
| ProductVersion: | 2.23 |
Total processes
158
Monitored processes
23
Malicious processes
2
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
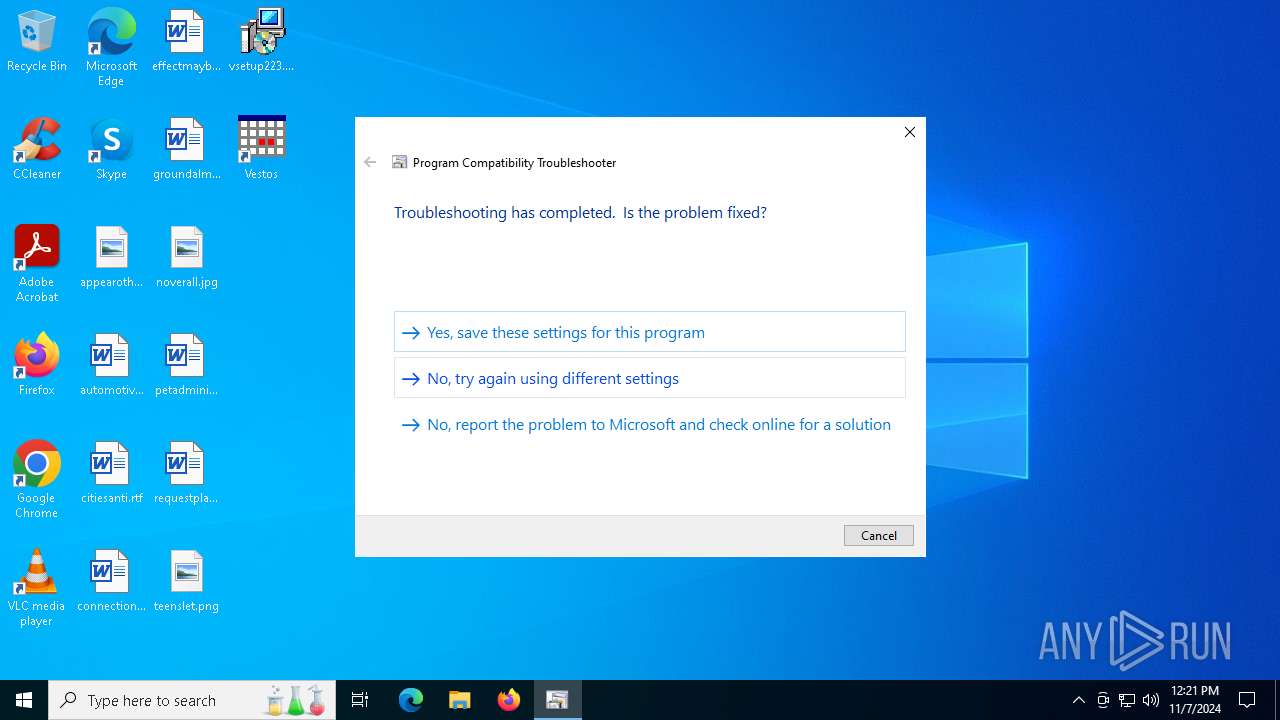
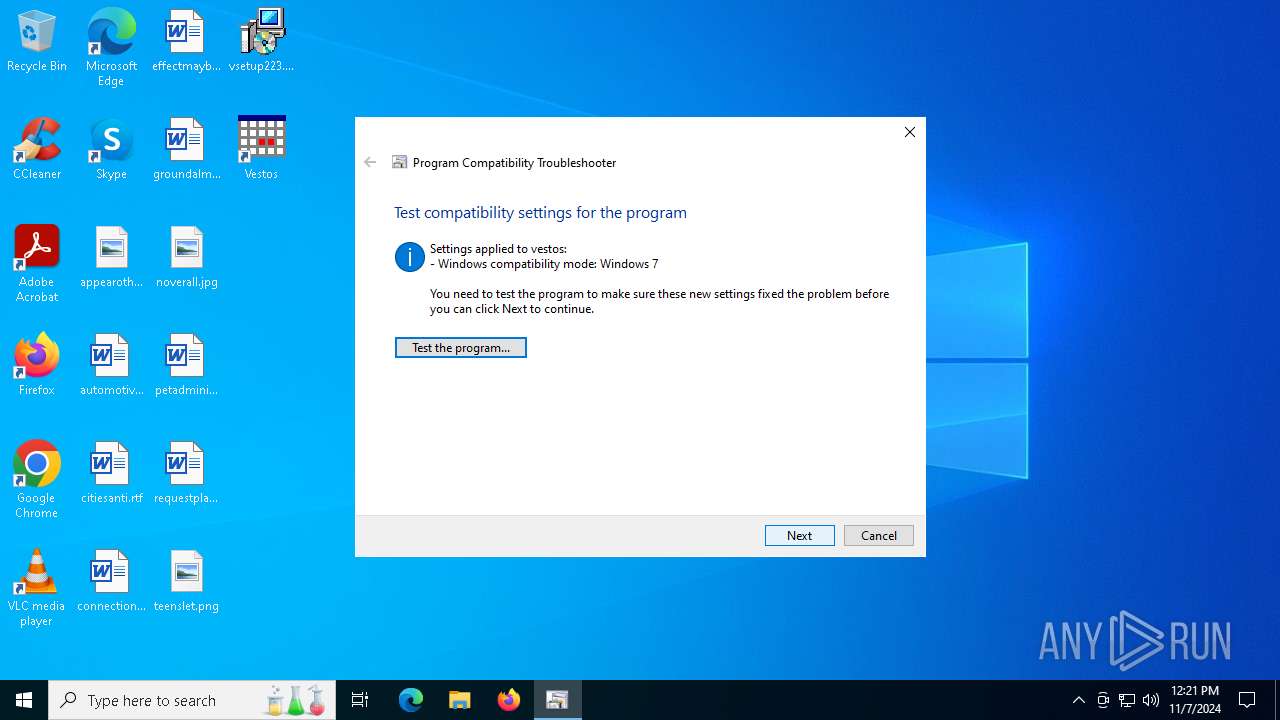
| 764 | C:\WINDOWS\system32\pcwrun.exe "C:\Program Files (x86)\Vestos\vestos.exe" ContextMenu | C:\Windows\System32\pcwrun.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Program Compatibility Troubleshooter Invoker Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1048 | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RESA83A.tmp" "c:\Users\admin\AppData\Local\Temp\CSC39BE41A4EA284C748C5EC22AB547A1CF.TMP" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 14.32.31326.0 Modules
| |||||||||||||||
| 2184 | "C:\Users\admin\AppData\Local\Temp\is-5O553.tmp\vsetup223.tmp" /SL5="$9027E,1696826,54272,C:\Users\admin\Desktop\vsetup223.exe" | C:\Users\admin\AppData\Local\Temp\is-5O553.tmp\vsetup223.tmp | — | vsetup223.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 2652 | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RESAC90.tmp" "c:\Users\admin\AppData\Local\Temp\CSCF564A8A824B74EB38138E95C80B66DC.TMP" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 14.32.31326.0 Modules
| |||||||||||||||
| 3396 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | sdiagnhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3728 | "C:\WINDOWS\system32\regsvr32.exe" /s "C:\Program Files (x86)\Vestos\msflxgrd.ocx" | C:\Windows\SysWOW64\regsvr32.exe | — | vsetup223.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3732 | "C:\Program Files (x86)\Vestos\vestos.exe" | C:\Program Files (x86)\Vestos\vestos.exe | — | vsetup223.tmp | |||||||||||
User: admin Company: The Drillicks Integrity Level: MEDIUM Exit code: 0 Version: 2.02.0003 Modules
| |||||||||||||||
| 3960 | "C:\WINDOWS\system32\regsvr32.exe" /s "C:\Program Files (x86)\Vestos\scrollerii.ocx" | C:\Windows\SysWOW64\regsvr32.exe | — | vsetup223.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4076 | "C:\Users\admin\Desktop\vsetup223.exe" | C:\Users\admin\Desktop\vsetup223.exe | explorer.exe | ||||||||||||
User: admin Company: Torah Software Integrity Level: MEDIUM Description: Vestos Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 4348 | "C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\dgij4yci.cmdline" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe | sdiagnhost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
Total events
10 325
Read events
10 245
Write events
62
Delete events
18
Modification events
| (PID) Process: | (3728) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{6262D3A0-531B-11CF-91F6-C2863C385E30} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3728) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{6262D3A0-531B-11CF-91F6-C2863C385E30}\InprocServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: Apartment | |||
| (PID) Process: | (3728) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{6319EEA0-531B-11CF-91F6-C2863C385E30} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3728) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{6319EEA0-531B-11CF-91F6-C2863C385E30}\InprocServer32 |
| Operation: | delete value | Name: | ThreadingModel |
Value: | |||
| (PID) Process: | (3728) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{275DBBA0-805A-11CF-91F7-C2863C385E30} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3728) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{275DBBA0-805A-11CF-91F7-C2863C385E30}\InprocServer32 |
| Operation: | delete value | Name: | ThreadingModel |
Value: | |||
| (PID) Process: | (3728) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\Interface\{2334D2B1-713E-11CF-8AE5-00AA00C00905}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.0 | |||
| (PID) Process: | (3728) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{2334D2B1-713E-11CF-8AE5-00AA00C00905}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.0 | |||
| (PID) Process: | (3728) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\Interface\{2334D2B3-713E-11CF-8AE5-00AA00C00905}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.0 | |||
| (PID) Process: | (3728) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{2334D2B3-713E-11CF-8AE5-00AA00C00905}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.0 | |||
Executable files
27
Suspicious files
31
Text files
25
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6156 | vsetup223.tmp | C:\Users\admin\AppData\Local\Temp\is-FI3FP.tmp\_isetup\_setup64.tmp | executable | |
MD5:4FF75F505FDDCC6A9AE62216446205D9 | SHA256:A4C86FC4836AC728D7BD96E7915090FD59521A9E74F1D06EF8E5A47C8695FD81 | |||
| 4076 | vsetup223.exe | C:\Users\admin\AppData\Local\Temp\is-5O553.tmp\vsetup223.tmp | executable | |
MD5:67C5A4F36E1C91A3B85E440EDD7AD026 | SHA256:99C299D6565AB53D9AF66E0146737DC0ECFBC52ECF4740825B552DB0CC4210C6 | |||
| 6156 | vsetup223.tmp | C:\Users\admin\AppData\Local\Temp\is-FI3FP.tmp\_isetup\_RegDLL.tmp | executable | |
MD5:0EE914C6F0BB93996C75941E1AD629C6 | SHA256:4DC09BAC0613590F1FAC8771D18AF5BE25A1E1CB8FDBF4031AA364F3057E74A2 | |||
| 6156 | vsetup223.tmp | C:\Program Files (x86)\Vestos\is-53BGP.tmp | executable | |
MD5:4309A1E4F17F925BB2B66AC12FDA46C3 | SHA256:A8ECD3DD266E8E2F62006B3B40FD60569FB3EA7DB4FEE871DEC5F2BF10355CB1 | |||
| 6604 | vsetup223.exe | C:\Users\admin\AppData\Local\Temp\is-2R74I.tmp\vsetup223.tmp | executable | |
MD5:67C5A4F36E1C91A3B85E440EDD7AD026 | SHA256:99C299D6565AB53D9AF66E0146737DC0ECFBC52ECF4740825B552DB0CC4210C6 | |||
| 6156 | vsetup223.tmp | C:\Users\admin\AppData\Local\Temp\is-FI3FP.tmp\_isetup\_shfoldr.dll | executable | |
MD5:92DC6EF532FBB4A5C3201469A5B5EB63 | SHA256:9884E9D1B4F8A873CCBD81F8AD0AE257776D2348D027D811A56475E028360D87 | |||
| 6156 | vsetup223.tmp | C:\Program Files (x86)\Vestos\unins000.exe | executable | |
MD5:4309A1E4F17F925BB2B66AC12FDA46C3 | SHA256:A8ECD3DD266E8E2F62006B3B40FD60569FB3EA7DB4FEE871DEC5F2BF10355CB1 | |||
| 6156 | vsetup223.tmp | C:\Program Files (x86)\Vestos\linedraw.ttf | binary | |
MD5:C9BA2F69C1ECB3F9DDCEF9EE36BF380D | SHA256:C81ADD0C4236A19EE278C8D1513BD5A68DA78E01CB1C10F4DBFD4A5C5360A7DA | |||
| 6156 | vsetup223.tmp | C:\Program Files (x86)\Vestos\fixed.kdf | ttf | |
MD5:5BAF82D7980F212A3FF53A2E4D7EBC5E | SHA256:BFD08A551B3CAB5B793FC32FF4765095BAEEB6A12F6952AFDDB324D5C431D36E | |||
| 6156 | vsetup223.tmp | C:\Program Files (x86)\Vestos\is-AV062.tmp | executable | |
MD5:69082B3ED710CE76884F3F40E22699FE | SHA256:DBA39B8FB98F2AD0A090682DF6C8B2AC466CF27124DBF683D2DEE7E376B9786F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
50
DNS requests
26
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6944 | svchost.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 23.32.185.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1552 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4448 | SIHClient.exe | GET | 200 | 23.37.237.227:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4448 | SIHClient.exe | GET | 200 | 23.37.237.227:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4996 | sdiagnhost.exe | GET | 200 | 23.32.238.107:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1336 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
4996 | sdiagnhost.exe | GET | 200 | 23.37.237.227:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6944 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4360 | SearchApp.exe | 2.23.209.154:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
864 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5488 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6944 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6944 | svchost.exe | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
6944 | svchost.exe | 23.32.185.131:80 | www.microsoft.com | AKAMAI-AS | BR | whitelisted |
5488 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
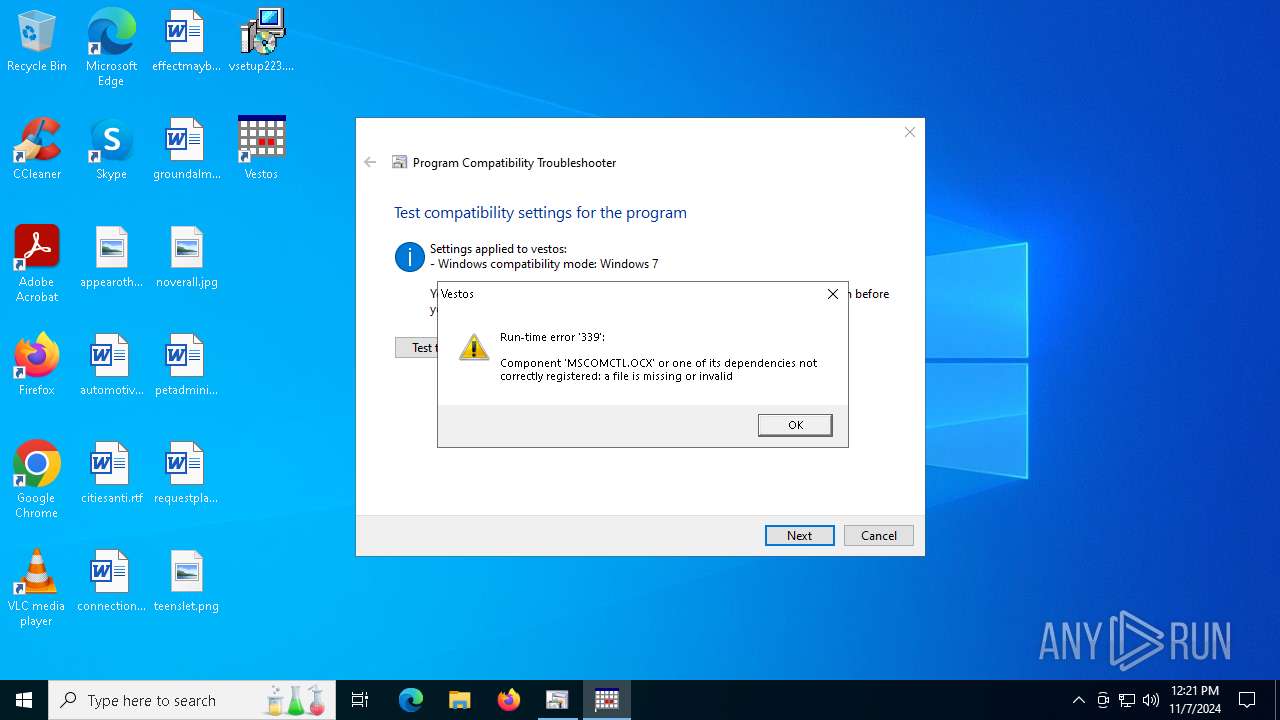
vestos.exe | FTH: (4584): *** Fault tolerant heap shim applied to current process. This is usually due to previous crashes. ***
|
vestos.exe | FTH: (6500): *** Fault tolerant heap shim applied to current process. This is usually due to previous crashes. ***
|