| File name: | sclient.exe |
| Full analysis: | https://app.any.run/tasks/a1e11c05-44c0-4883-b572-65a35cfed16f |
| Verdict: | Malicious activity |
| Analysis date: | April 26, 2024, 16:01:10 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | FF217DAB57393592C6767DE1C6A999EB |
| SHA1: | CC580C52F4263803255D65DFB6AB208BE7F4A534 |
| SHA256: | B0903921E666CA3FFD45100A38C11D7E5C53AB38646715EAFC6D1851AD41B92E |
| SSDEEP: | 98304:0O6WSq1v6mQr4OytH9awXB0DXe3S+5OmxlGwP3AW5JTGG0DR/Wk1jKnBKK9Mh6Bw:JDA3+UB |
MALICIOUS
Drops the executable file immediately after the start
- sclient.exe (PID: 4084)
- msiexec.exe (PID: 124)
Creates a writable file in the system directory
- ScreenConnect.ClientService.exe (PID: 1928)
SCREENCONNECT has been detected (SURICATA)
- ScreenConnect.ClientService.exe (PID: 1928)
Connects to the CnC server
- ScreenConnect.ClientService.exe (PID: 1928)
SUSPICIOUS
Reads security settings of Internet Explorer
- sclient.exe (PID: 4084)
- ScreenConnect.ClientService.exe (PID: 1928)
- ScreenConnect.WindowsClient.exe (PID: 2600)
Reads the Internet Settings
- sclient.exe (PID: 4084)
- ScreenConnect.WindowsClient.exe (PID: 2600)
Uses RUNDLL32.EXE to load library
- msiexec.exe (PID: 2024)
Executable content was dropped or overwritten
- rundll32.exe (PID: 1112)
Executes as Windows Service
- VSSVC.exe (PID: 1768)
- ScreenConnect.ClientService.exe (PID: 1928)
The process creates files with name similar to system file names
- msiexec.exe (PID: 124)
Non-standard symbols in registry
- msiexec.exe (PID: 124)
Creates or modifies Windows services
- ScreenConnect.ClientService.exe (PID: 1928)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 124)
INFO
Reads the computer name
- sclient.exe (PID: 4084)
- msiexec.exe (PID: 124)
- msiexec.exe (PID: 2024)
- msiexec.exe (PID: 2272)
- msiexec.exe (PID: 2196)
- ScreenConnect.ClientService.exe (PID: 1928)
- ScreenConnect.WindowsClient.exe (PID: 2600)
- wmpnscfg.exe (PID: 2472)
Create files in a temporary directory
- sclient.exe (PID: 4084)
- rundll32.exe (PID: 1112)
- msiexec.exe (PID: 124)
Checks supported languages
- sclient.exe (PID: 4084)
- msiexec.exe (PID: 124)
- msiexec.exe (PID: 2024)
- msiexec.exe (PID: 2272)
- msiexec.exe (PID: 2196)
- ScreenConnect.ClientService.exe (PID: 1928)
- ScreenConnect.WindowsClient.exe (PID: 2600)
- wmpnscfg.exe (PID: 2472)
Reads the machine GUID from the registry
- sclient.exe (PID: 4084)
- msiexec.exe (PID: 124)
- msiexec.exe (PID: 2024)
- msiexec.exe (PID: 2196)
- ScreenConnect.ClientService.exe (PID: 1928)
- msiexec.exe (PID: 2272)
- ScreenConnect.WindowsClient.exe (PID: 2600)
Application launched itself
- msiexec.exe (PID: 124)
Drops the executable file immediately after the start
- msiexec.exe (PID: 820)
- rundll32.exe (PID: 1112)
Executable content was dropped or overwritten
- msiexec.exe (PID: 820)
- msiexec.exe (PID: 124)
Creates a software uninstall entry
- msiexec.exe (PID: 124)
Manual execution by a user
- wmpnscfg.exe (PID: 2472)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2022:11:18 20:10:20+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.33 |
| CodeSize: | 45568 |
| InitializedDataSize: | 5264384 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x14ad |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
50
Monitored processes
12
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | C:\Windows\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
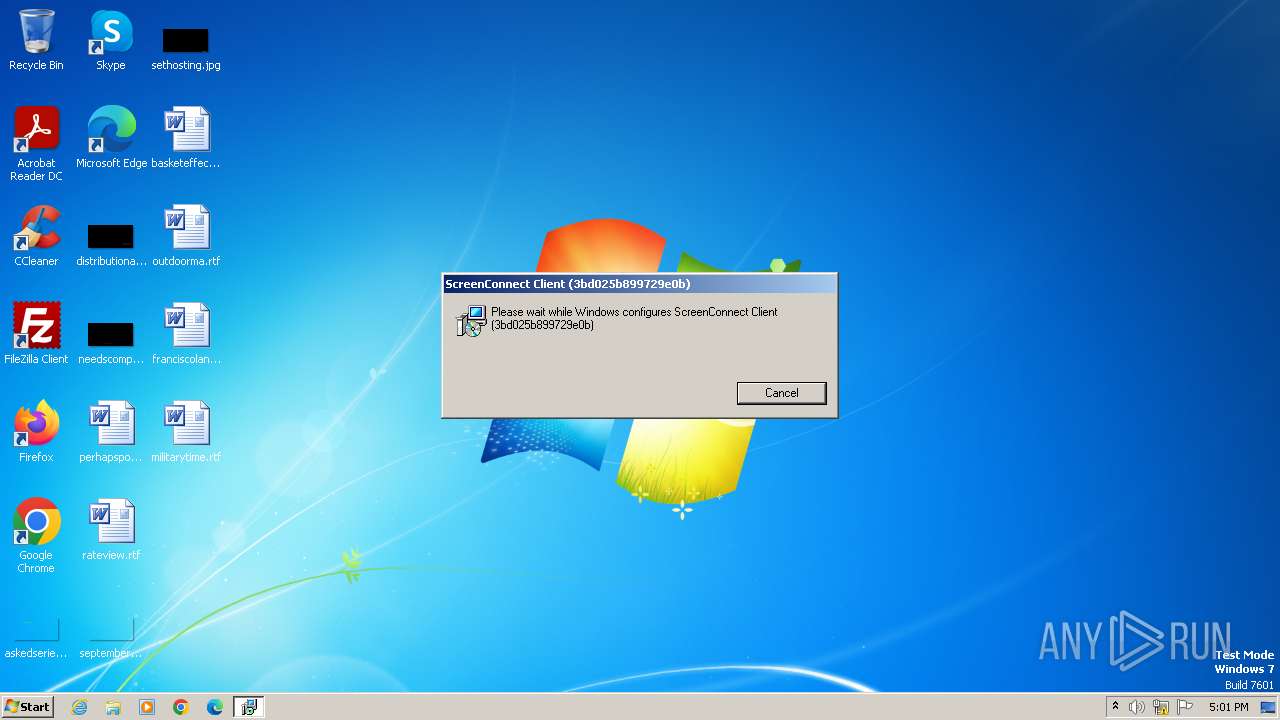
| 820 | "C:\Windows\System32\msiexec.exe" /i "C:\Users\admin\AppData\Local\Temp\ScreenConnect\3bd025b899729e0b\setup.msi" | C:\Windows\System32\msiexec.exe | sclient.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1112 | rundll32.exe "C:\Users\admin\AppData\Local\Temp\MSI3932.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_1063296 1 ScreenConnect.InstallerActions!ScreenConnect.ClientInstallerActions.FixupServiceArguments | C:\Windows\System32\rundll32.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1768 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1928 | "C:\Program Files\ScreenConnect Client (3bd025b899729e0b)\ScreenConnect.ClientService.exe" "?e=Access&y=Guest&h=instance-j6j3lm-relay.screenconnect.com&p=443&s=1c2012a8-b490-4ae9-b3ed-36b7eba73fe5&k=BgIAAACkAABSU0ExAAgAAAEAAQC1TmtnHOE8KBx2zPp%2fuJ%2by39l0NWWXy4hDwpp%2fLbmCFh5LK0SyDiXRm%2fTsND3dHdktOGdUBkofhti3sghfGqfVo6GP6Sg%2buHFcntPEuGDPR1Pgf6HCa7T9yXFofj9W1%2fCnU7E2qRO78Eg60Rg%2bnAM558GL6VW2HXSzjW4TIyleqQN2uzZ90v7j9qpImb9KxU5tUo75RqMp532OhGJmGxw6kdZlktuz2D%2frx86oirnZHMeuHLPkk2Gazr2Fj4pUNIUXhQykPJaTo%2bvj%2fj4BjIuDNHrkqKW9BrCTkQlF3r3GkVTekYAFjoQmeRfdofhEinrtxH6Vf%2frhM0YqQvaCMcK9" | C:\Program Files\ScreenConnect Client (3bd025b899729e0b)\ScreenConnect.ClientService.exe | services.exe | ||||||||||||
User: SYSTEM Integrity Level: SYSTEM Version: 23.8.5.8707 Modules
| |||||||||||||||
| 2024 | C:\Windows\system32\MsiExec.exe -Embedding E171F8D71829F3BAD40E8886B65CA45E C | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2196 | C:\Windows\system32\MsiExec.exe -Embedding CFB69ADEE45132B191C2A81E56965E42 E Global\MSI0000 | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2272 | C:\Windows\system32\MsiExec.exe -Embedding F574C0DDE9D0DCDF2E788527DCBBFC85 | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2472 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2600 | "C:\Program Files\ScreenConnect Client (3bd025b899729e0b)\ScreenConnect.WindowsClient.exe" "RunRole" "a4dfce83-98b4-4412-b00c-fa48330088c5" "User" | C:\Program Files\ScreenConnect Client (3bd025b899729e0b)\ScreenConnect.WindowsClient.exe | — | ScreenConnect.ClientService.exe | |||||||||||
User: admin Company: ScreenConnect Software Integrity Level: MEDIUM Description: ScreenConnect Client Version: 23.8.5.8707 Modules
| |||||||||||||||
Total events
8 395
Read events
8 123
Write events
252
Delete events
20
Modification events
| (PID) Process: | (4084) sclient.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (4084) sclient.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (4084) sclient.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (4084) sclient.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (124) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4000000000000000C40E8AFAF297DA017C000000EC060000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (124) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4000000000000000C40E8AFAF297DA017C000000EC060000D0070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (124) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 75 | |||
| (PID) Process: | (124) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 400000000000000006912EFBF297DA017C000000EC060000D3070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (124) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 400000000000000060F330FBF297DA017C00000048070000E8030000010000000000000000000000B530AB8951E57C4CAE166D0EE07D5BB00000000000000000 | |||
| (PID) Process: | (1768) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 400000000000000014B835FBF297DA01E806000038060000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
14
Suspicious files
6
Text files
6
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4084 | sclient.exe | C:\Users\admin\AppData\Local\Temp\ScreenConnect\3bd025b899729e0b\setup.msi | — | |
MD5:— | SHA256:— | |||
| 124 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 124 | msiexec.exe | C:\Windows\Installer\105054.msi | — | |
MD5:— | SHA256:— | |||
| 1112 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\MSI3932.tmp-\ScreenConnect.Windows.dll | executable | |
MD5:44B736A074B7E0BBE0C6C5F7DEBE0F3D | SHA256:F8C648E09FB42F145B581ED80B2A0C88E9F18041EFD03AD3187A6229F17A14B8 | |||
| 1112 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\MSI3932.tmp-\ScreenConnect.InstallerActions.dll | executable | |
MD5:41E8C80A7F1BF4911FCE55C0DE249302 | SHA256:569B267D8C4CEF1B26C9337F5A355F0040AD4D7E9610F28784E4AF05EFA3E4E9 | |||
| 1112 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\MSI3932.tmp-\ScreenConnect.Core.dll | executable | |
MD5:469A702D0861E2C63E6E6E575C58E399 | SHA256:AFFB342D2DCE754B4DDBEEB4ED344806FDA531D68346DF12629B7BD8C0FA753C | |||
| 124 | msiexec.exe | C:\Windows\Installer\MSI5576.tmp | executable | |
MD5:BA84DD4E0C1408828CCC1DE09F585EDA | SHA256:3CFF4AC91288A0FF0C13278E73B282A64E83D089C5A61A45D483194AB336B852 | |||
| 124 | msiexec.exe | C:\Windows\Installer\105055.ipi | binary | |
MD5:3A03AE14D0708A2E6A4CA77DC92C7E12 | SHA256:2B99678B9477DE1D85AD8CB2B88CB8645CBA5AAF25268A10A761728B4D1BAC0D | |||
| 124 | msiexec.exe | C:\Program Files\ScreenConnect Client (3bd025b899729e0b)\ScreenConnect.Core.dll | executable | |
MD5:469A702D0861E2C63E6E6E575C58E399 | SHA256:AFFB342D2DCE754B4DDBEEB4ED344806FDA531D68346DF12629B7BD8C0FA753C | |||
| 124 | msiexec.exe | C:\Windows\Installer\105057.msi | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
5
DNS requests
1
Threats
3
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1928 | ScreenConnect.ClientService.exe | 51.77.100.219:443 | instance-j6j3lm-relay.screenconnect.com | OVH SAS | FR | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
instance-j6j3lm-relay.screenconnect.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1088 | svchost.exe | Misc activity | ET INFO Observed DNS Query to Known ScreenConnect/ConnectWise Remote Desktop Service Domain |
1928 | ScreenConnect.ClientService.exe | Misc activity | ET INFO ScreenConnect/ConnectWise Initial Checkin Packet M2 |
1928 | ScreenConnect.ClientService.exe | Potential Corporate Privacy Violation | REMOTE [ANY.RUN] ScreenConnect Server Response |